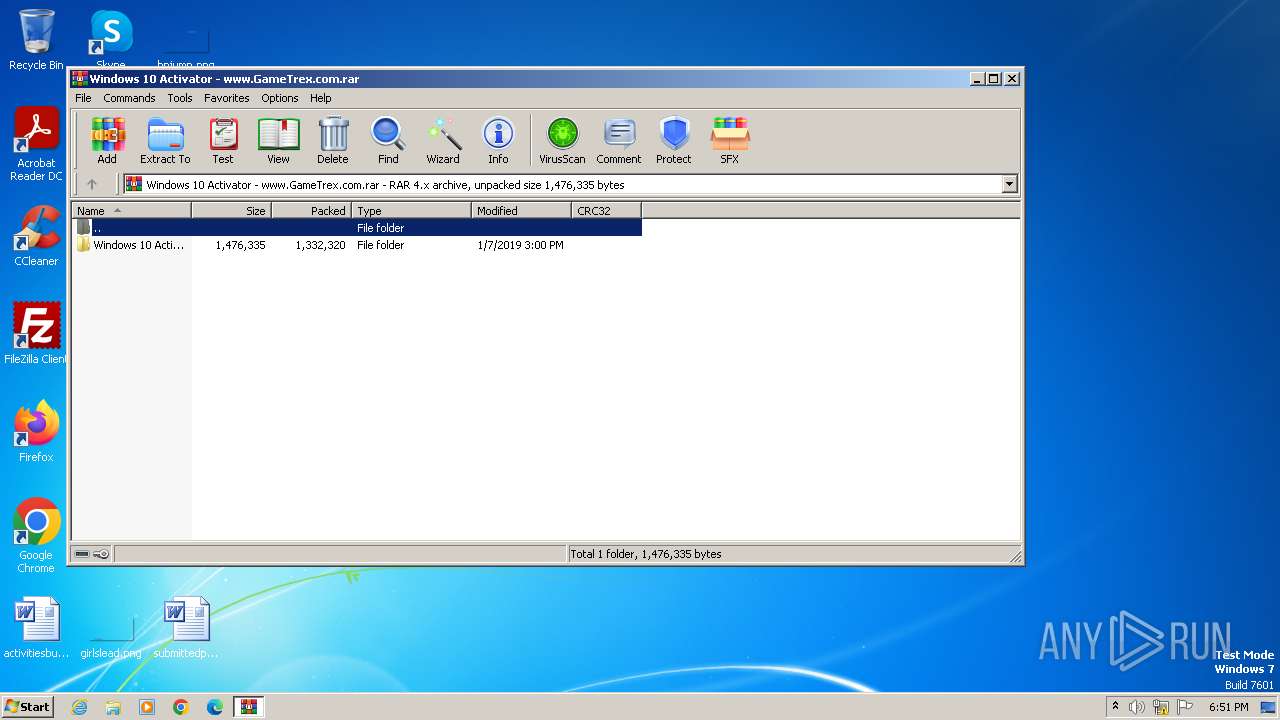
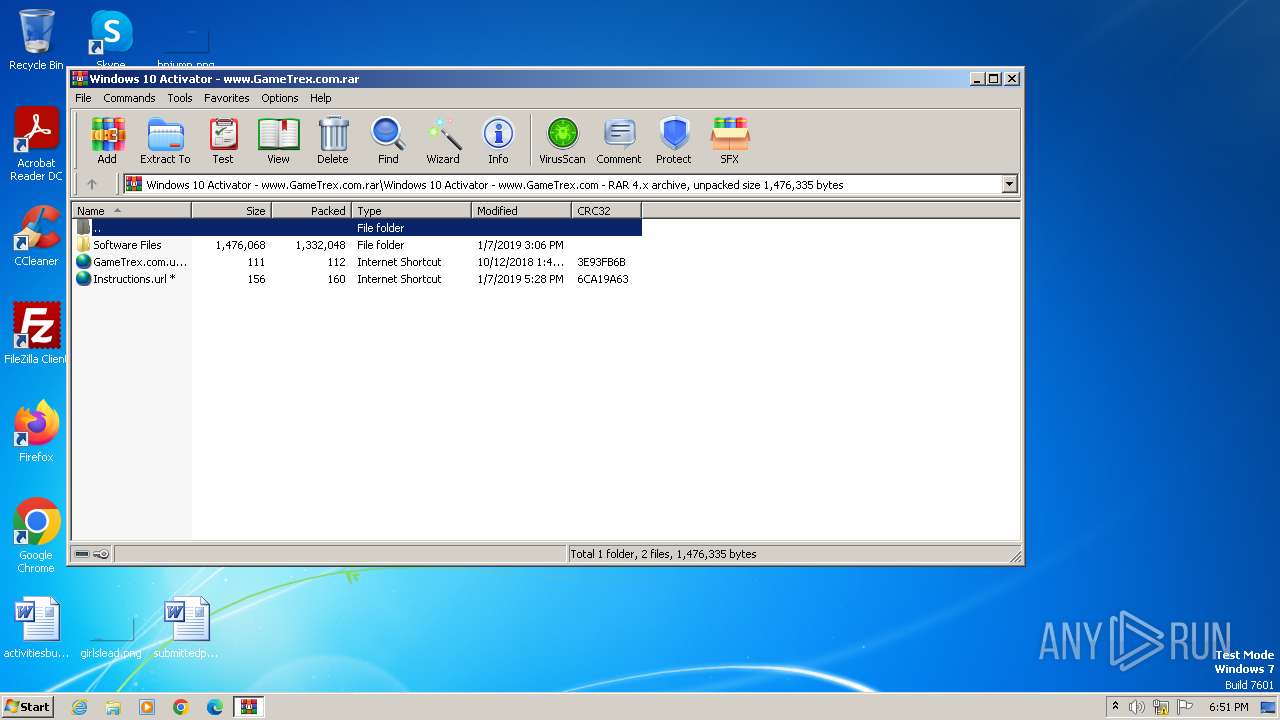
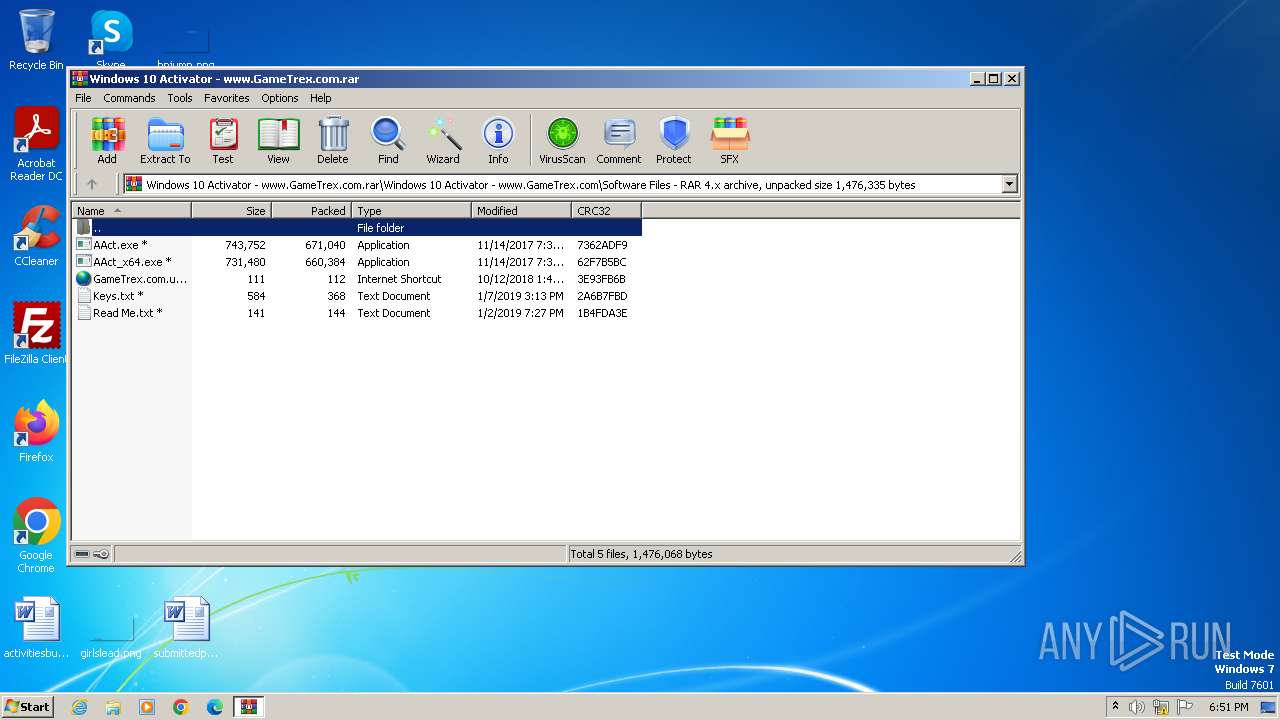
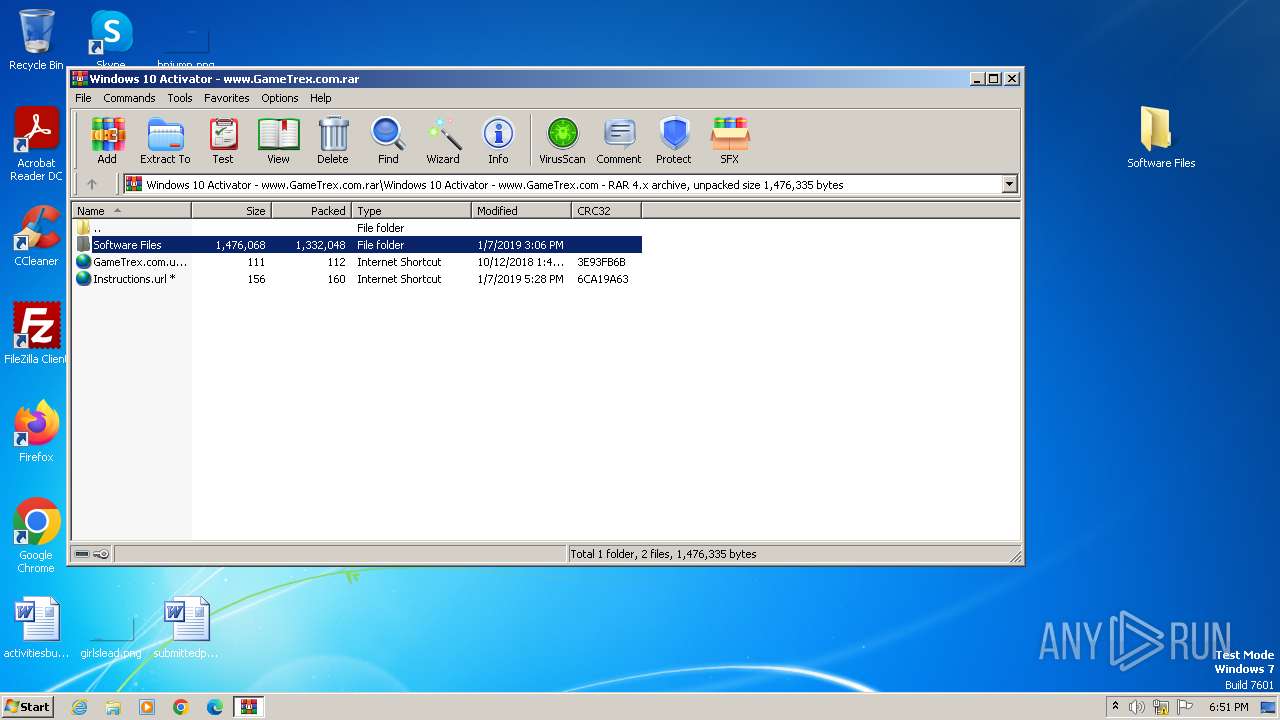
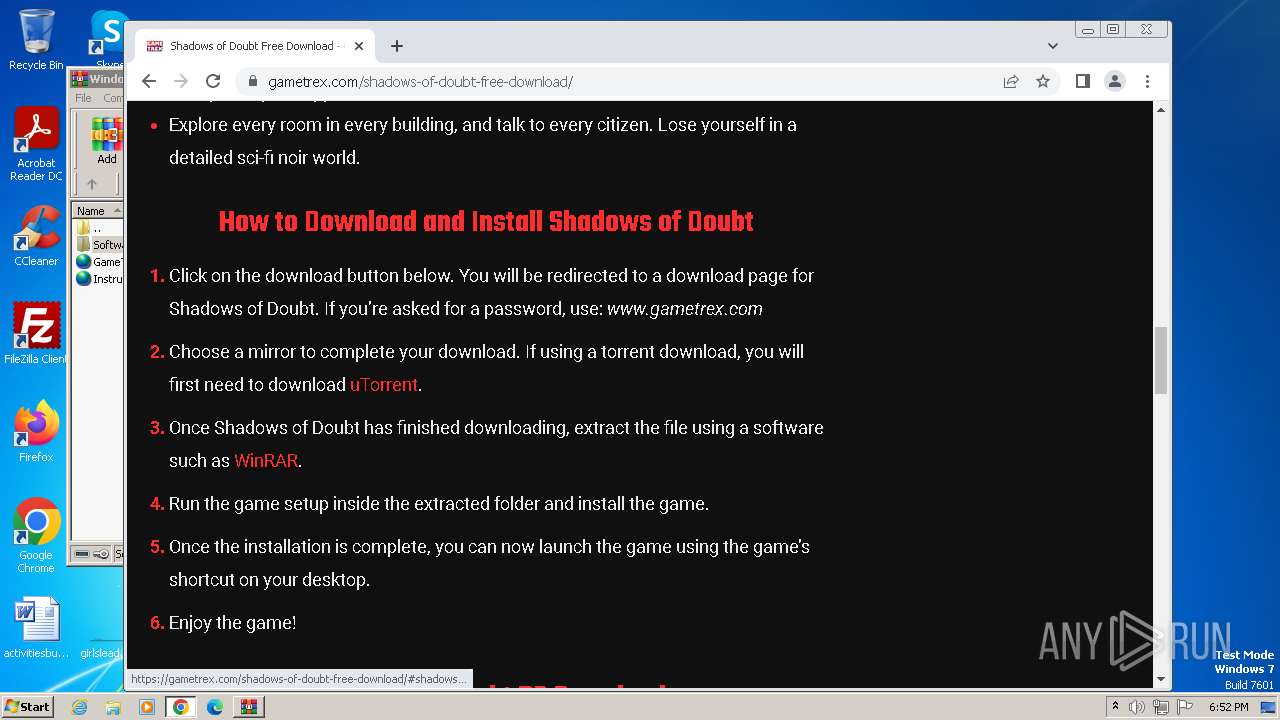
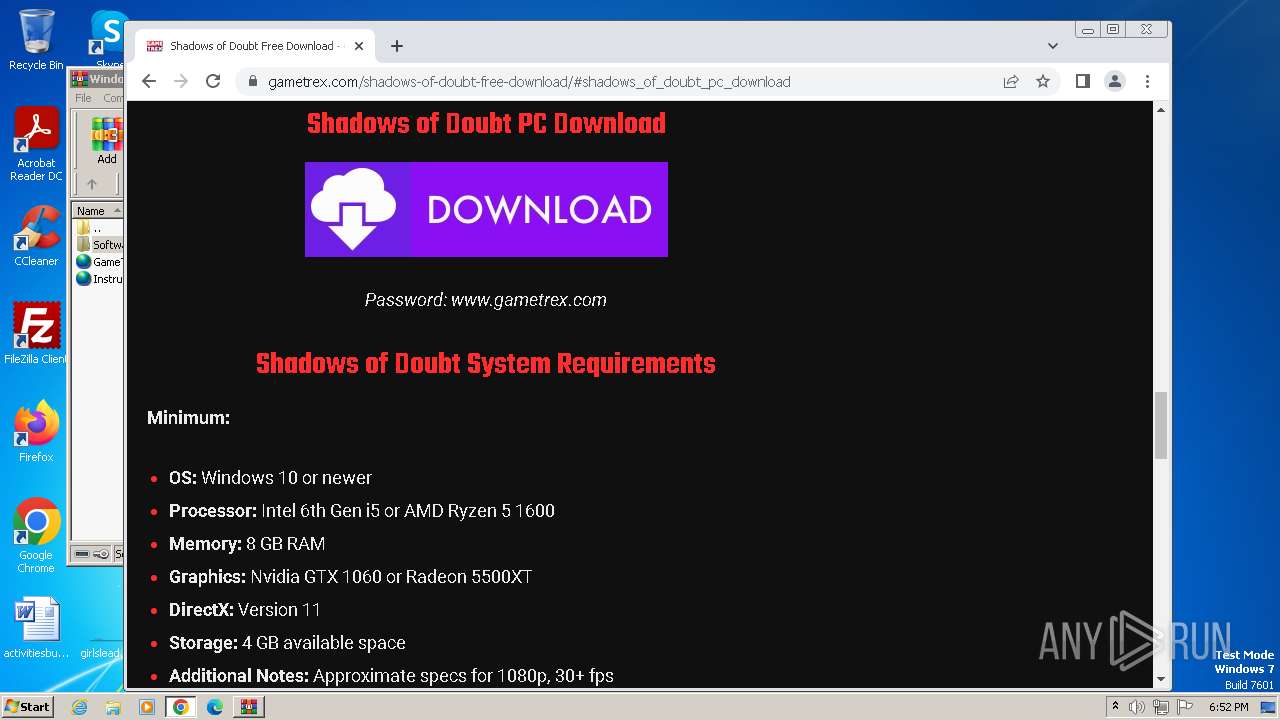
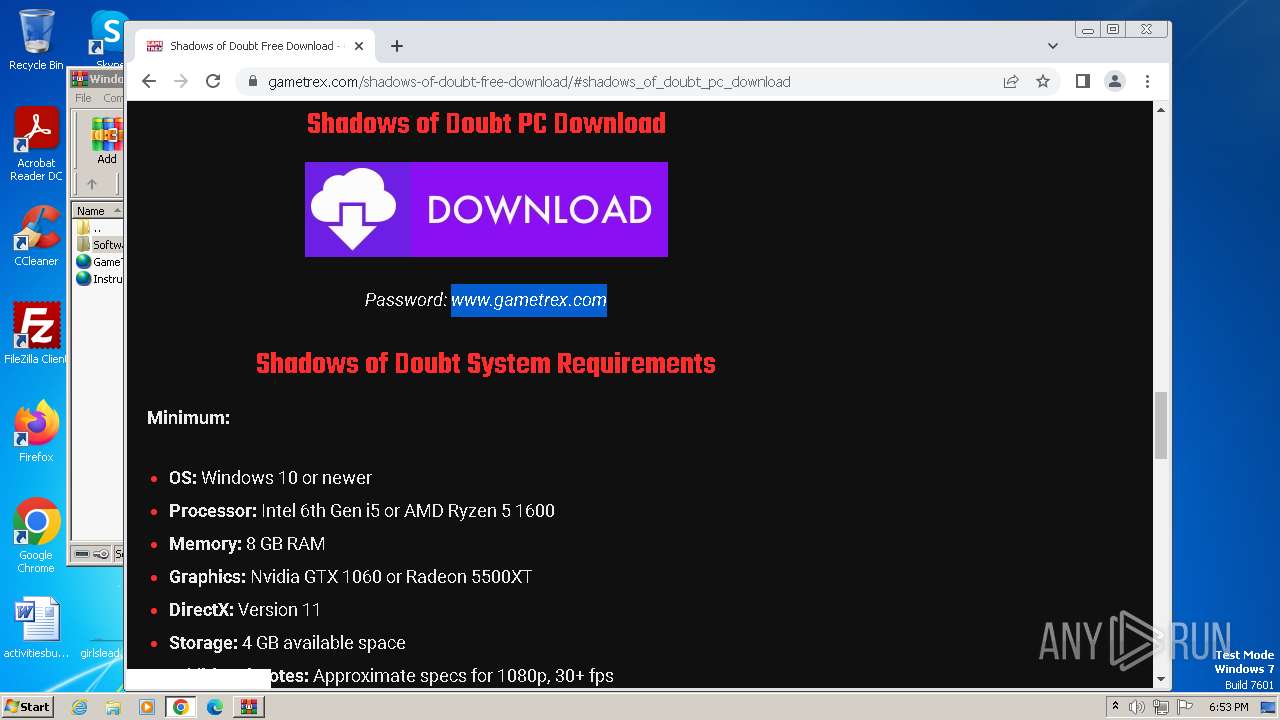
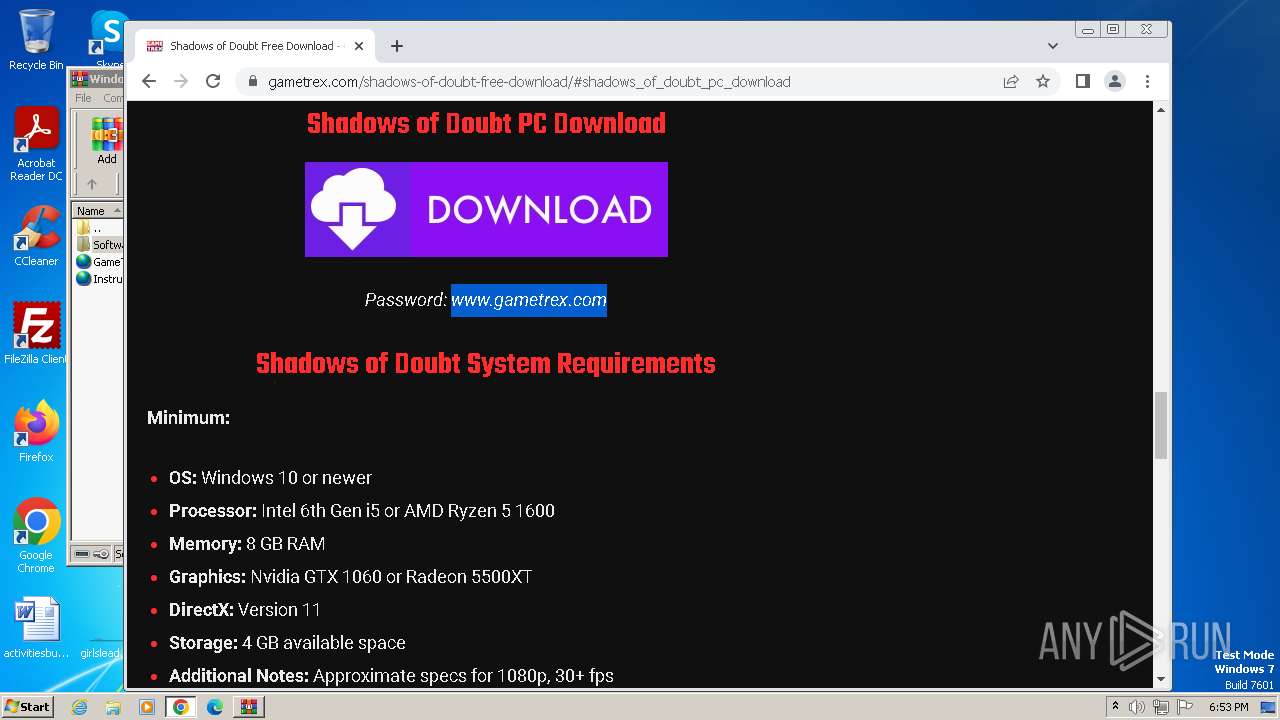
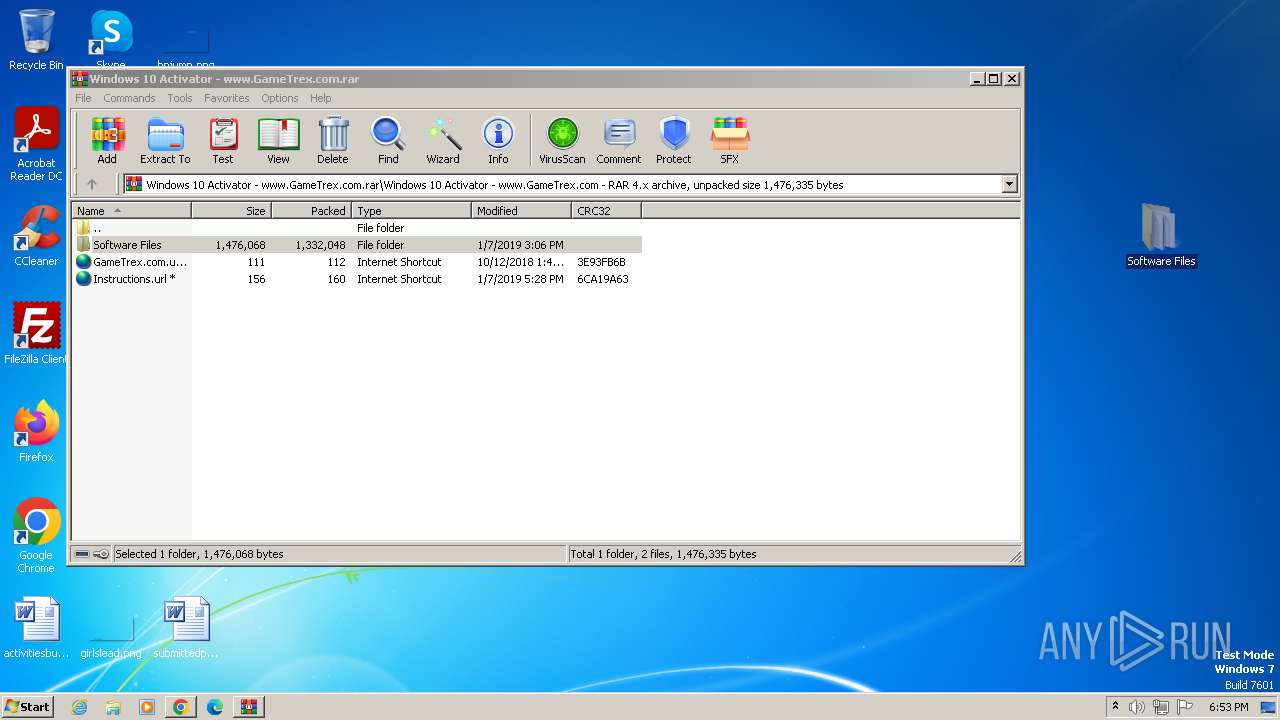
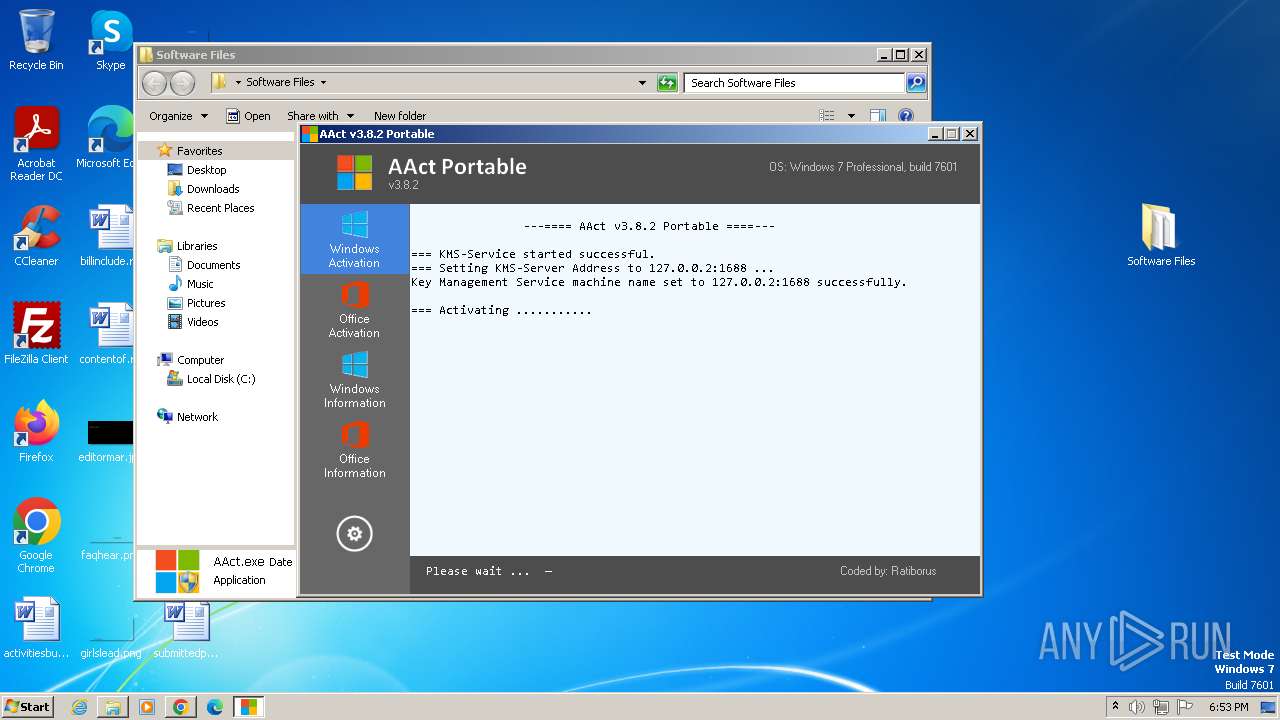
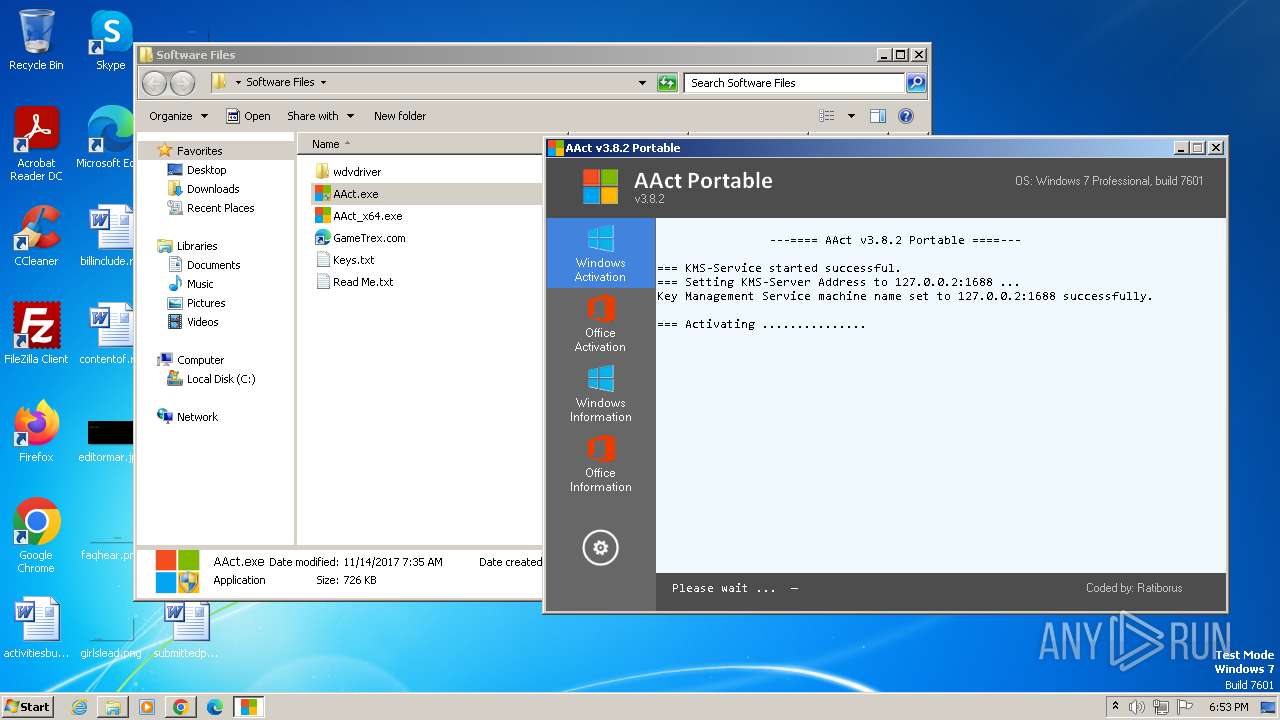
| File name: | Windows 10 Activator - www.GameTrex.com.rar |
| Full analysis: | https://app.any.run/tasks/680a115b-a200-43c0-b32f-662b6e39685d |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 17:51:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | B4404EAF4C958E513618141AA3797F05 |
| SHA1: | 7C14138D92080467233D62D0B20611E215EDA1E1 |
| SHA256: | 699979E19175257D4B867990013317C6B059EFA6A30FC2F88DB6C0572E8569B5 |
| SSDEEP: | 49152:iXgYP5CvMfuGoPJY/wb3BajfXMRHrMtEs6bSHG6iVNtNY2tJm8mD+CvKVHi1HE7V:iQYP5CvGu9U7DXMBYt6SmhntdLm8U+AI |
MALICIOUS
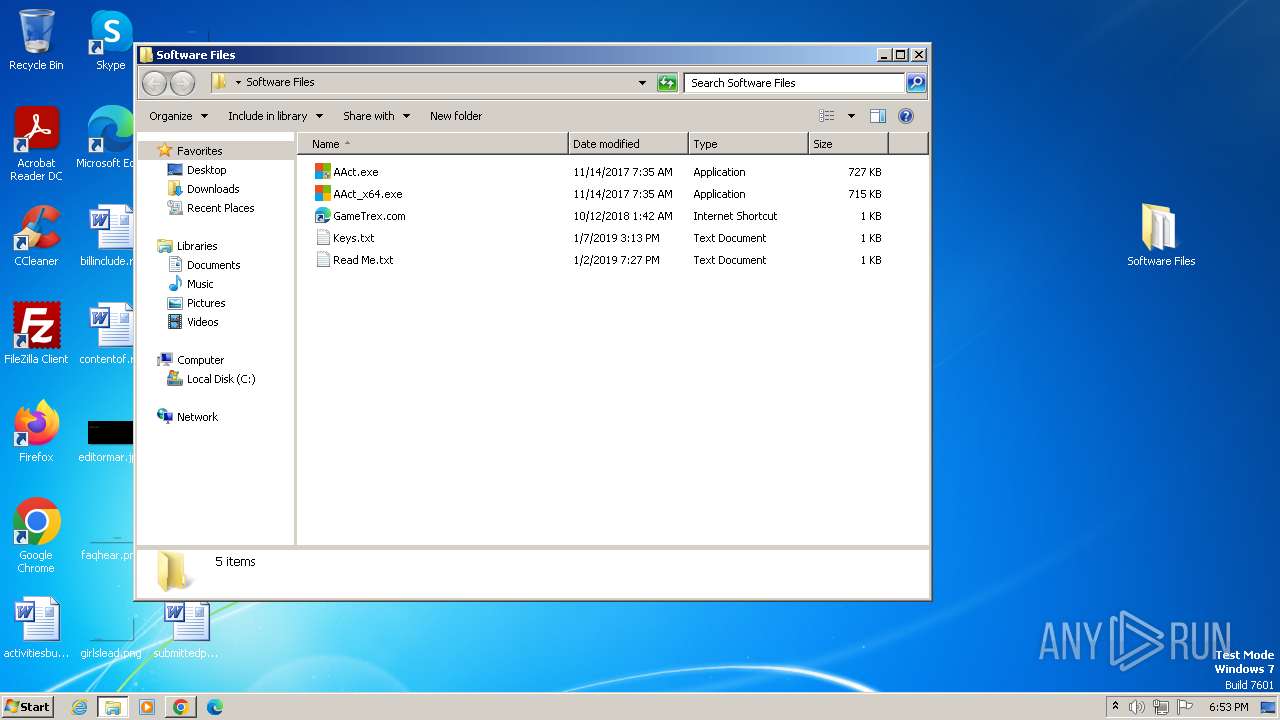
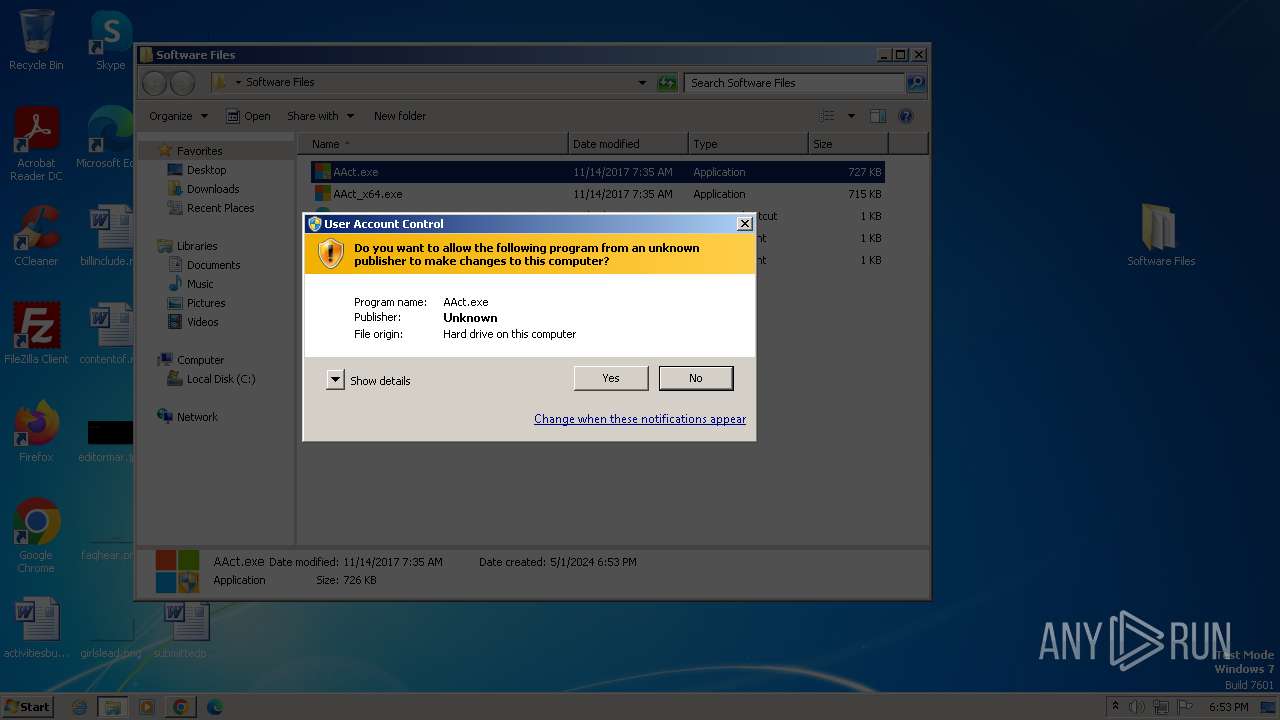
Drops the executable file immediately after the start
- AAct.exe (PID: 3252)
Opens a text file (SCRIPT)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 324)
- cscript.exe (PID: 1132)
SUSPICIOUS
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 3412)
- cmd.exe (PID: 2828)
Executable content was dropped or overwritten
- AAct.exe (PID: 3252)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 3572)
Starts application with an unusual extension
- AAct.exe (PID: 3252)
Starts CMD.EXE for commands execution
- AAct.exe (PID: 3252)
The process executes VB scripts
- cmd.exe (PID: 3800)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 588)
- cmd.exe (PID: 580)
- cmd.exe (PID: 1520)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 324)
- cscript.exe (PID: 1132)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 324)
- cscript.exe (PID: 1132)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 324)
- cscript.exe (PID: 1132)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 1132)
- cscript.exe (PID: 324)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 324)
- cscript.exe (PID: 1132)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 324)
- cscript.exe (PID: 1132)
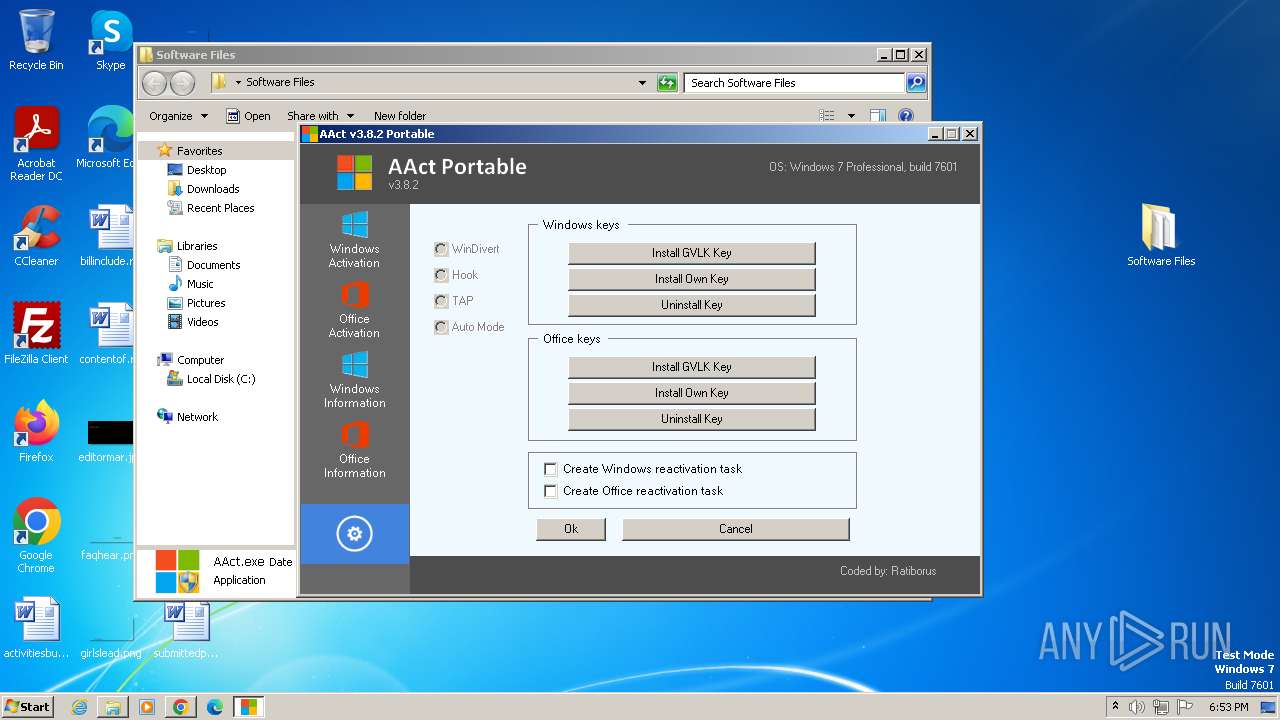
Uses REG/REGEDIT.EXE to modify registry
- AAct.exe (PID: 3252)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 1520)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2668)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
Reads the computer name
- wmpnscfg.exe (PID: 2632)
- AAct.dll (PID: 3512)
Checks supported languages
- wmpnscfg.exe (PID: 2632)
- AAct.exe (PID: 3252)
- AAct.dll (PID: 3512)
Manual execution by a user
- AAct.exe (PID: 3252)
- AAct.exe (PID: 3008)
- wmpnscfg.exe (PID: 2632)
- chrome.exe (PID: 820)
Reads product name
- AAct.exe (PID: 3252)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Reads Environment values
- AAct.exe (PID: 3252)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3820)
- cscript.exe (PID: 3628)
- cscript.exe (PID: 1072)
- cscript.exe (PID: 3616)
- cscript.exe (PID: 1132)
- cscript.exe (PID: 324)
Application launched itself
- chrome.exe (PID: 820)
Reads the machine GUID from the registry
- AAct.dll (PID: 3512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 202 |
|---|---|
| UncompressedSize: | 111 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:10:12 01:42:42 |
| PackingMethod: | Best Compression |
| ArchivedFileName: | Windows 10 Activator - www.GameTrex.com\GameTrex.com.url |
Total processes
101
Monitored processes
46
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1340 --field-trial-handle=1164,i,12913168740267606399,13491368707034108055,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1616 --field-trial-handle=1164,i,12913168740267606399,13491368707034108055,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3612 --field-trial-handle=1164,i,12913168740267606399,13491368707034108055,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 324 | cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /skms 127.0.0.2:1688 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 580 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /ato | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221536791 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 588 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /ckms-domain | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3696 --field-trial-handle=1164,i,12913168740267606399,13491368707034108055,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6da48b38,0x6da48b48,0x6da48b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1536 --field-trial-handle=1164,i,12913168740267606399,13491368707034108055,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
11 850
Read events
11 599
Write events
250
Delete events
1
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows 10 Activator - www.GameTrex.com.rar | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
75
Text files
42
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.25196\Windows 10 Activator - www.GameTrex.com\Software Files\GameTrex.com.url | binary | |
MD5:A63C90CC3684AD8B0A2176A6A8FE9005 | SHA256:01D448AFD928065458CF670B60F5A594D735AF0172C8D67F22A81680132681CA | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.19213\Windows 10 Activator - www.GameTrex.com\Software Files\AAct.exe | binary | |
MD5:BDF8C70B7B6A4BD595FE3E9A0B32C5D5 | SHA256:2C15E0A1F4F1BECDB5CE3BCDBDCC225D78D32C038DD8B43256E45C2CD4DFF185 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.22549\Windows 10 Activator - www.GameTrex.com\Software Files\AAct_x64.exe | gmc | |
MD5:72B591193E5F7ADEEE8E2AB8119B49E7 | SHA256:BE34EBA895D4F3039759AB12FDB1B1B39D16AD16A9D222BA9FE1A94C12FBB214 | |||
| 820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1168d9.TMP | — | |
MD5:— | SHA256:— | |||
| 820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.19213\Windows 10 Activator - www.GameTrex.com\Software Files\Keys.txt | binary | |
MD5:18E4F0294929A01BA93A51B04E6E70EA | SHA256:C123437982DEA3F4A158AFF5D542ACC4AA571C20D1AD6C2E844DDC10192E2A4A | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.20517\Windows 10 Activator - www.GameTrex.com\Software Files\Keys.txt | binary | |
MD5:2B05AF7B799B207CF91587B4CA8459E6 | SHA256:6A357553C26E1203732A80FA8253505CE0875889BC326117BCEE69A98BFEA5C3 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.22549\Windows 10 Activator - www.GameTrex.com\Software Files\Keys.txt | abr | |
MD5:9E292E386B7CEBD21E02AD51F7ACE213 | SHA256:F147DFC00BC88266987B75F69065432C7C9730DBECE276E2C913B47080C7C0BA | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.20517\Windows 10 Activator - www.GameTrex.com\Software Files\AAct_x64.exe | binary | |
MD5:46C3F7912C2BC8954A5DABD1B85E8663 | SHA256:282AF933F06B38C40A1CDA8B989AC72111E770C91F1CA93AD85923BAA5DCA8AA | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.19213\Windows 10 Activator - www.GameTrex.com\Software Files\Read Me.txt | binary | |
MD5:CAB61590B4C510D2A816D1DC26082F09 | SHA256:C6E1F921F960FB6749E48C6C0914D3528DD299ED966FF9EBE066525290413357 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
37
DNS requests
51
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
3240 | WmiPrvSE.exe | POST | 302 | 88.221.126.57:80 | http://go.microsoft.com/fwlink/?LinkID=88339 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
3240 | WmiPrvSE.exe | POST | 302 | 88.221.126.57:80 | http://go.microsoft.com/fwlink/?LinkID=88340 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
3240 | WmiPrvSE.exe | POST | 302 | 88.221.126.57:80 | http://go.microsoft.com/fwlink/?LinkID=88341 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
304 | chrome.exe | 64.233.184.84:443 | accounts.google.com | GOOGLE | US | unknown |
820 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
304 | chrome.exe | 142.250.186.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
304 | chrome.exe | 216.58.206.68:443 | www.google.com | GOOGLE | US | whitelisted |
304 | chrome.exe | 142.250.185.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
304 | chrome.exe | 142.250.184.238:443 | apis.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
update.googleapis.com |
| unknown |
gametrex.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
304 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |