| download: | free-tools |
| Full analysis: | https://app.any.run/tasks/66e59daf-2642-48dc-bc9e-67b838845657 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2020, 09:29:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | 52BC8D5F4D5A5A311D0D688E3A89F0CA |
| SHA1: | 72716448C0B260A7008617DE777D422A03BF8904 |
| SHA256: | 69396454435394C58E697635B95571C21FAA406706D9371D5FEC96725099B0B1 |
| SSDEEP: | 1536:uvgGEws7HOVTMJmpJWr7ZKEr/S88GwlWL12ZX7tC:uvgGEEMJmpJWr7gEr/S88GSWL12ZLtC |
MALICIOUS
Starts NET.EXE for service management
- GearsInstaller.exe (PID: 3316)
Application was dropped or rewritten from another process
- GearsSdkInstaller.EXE (PID: 1928)
- GearsInstaller.exe (PID: 3316)
- 7z.exe (PID: 3648)
- GearsHelper.exe (PID: 4056)
- GearsHelper.exe (PID: 968)
- waodwd.exe (PID: 2984)
- Gears.exe (PID: 1832)
- wabpoes.exe (PID: 2380)
- GearsAgentService.exe (PID: 2532)
- RefreshNotificationArea.exe (PID: 3812)
- GearsAgentService.exe (PID: 3004)
- GearsAgentService.exe (PID: 3264)
- RefreshNotificationArea.exe (PID: 3876)
- GearsAgentService.exe (PID: 3944)
- Gears.exe (PID: 2512)
- RefreshNotificationArea.exe (PID: 2308)
- RefreshNotificationArea.exe (PID: 1492)
- Installer.exe (PID: 4092)
- wa_3rd_party_host_32.exe (PID: 3840)
Loads dropped or rewritten executable
- GearsAgentService.exe (PID: 3264)
- GearsHelper.exe (PID: 4056)
- GearsAgentService.exe (PID: 2532)
- GearsAgentService.exe (PID: 3004)
- GearsHelper.exe (PID: 968)
- Gears.exe (PID: 1832)
- RefreshNotificationArea.exe (PID: 3812)
- wabpoes.exe (PID: 2380)
- RefreshNotificationArea.exe (PID: 3876)
- GearsAgentService.exe (PID: 3944)
- Gears.exe (PID: 2512)
- RefreshNotificationArea.exe (PID: 2308)
Changes the autorun value in the registry
- GearsInstaller.exe (PID: 3316)
- GearsAgentService.exe (PID: 3004)
Starts NET.EXE to view/change login properties
- cmd.exe (PID: 3216)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 3852)
- cmd.exe (PID: 3228)
Actions looks like stealing of personal data
- GearsAgentService.exe (PID: 3004)
- wabpoes.exe (PID: 2380)
Changes settings of System certificates
- wabpoes.exe (PID: 2380)
- GearsAgentService.exe (PID: 3004)
SUSPICIOUS
Executed as Windows Service
- vssvc.exe (PID: 3508)
- GearsAgentService.exe (PID: 3004)
- GearsHelper.exe (PID: 968)
Starts Microsoft Installer
- iexplore.exe (PID: 1388)
Creates files in the program directory
- GearsInstaller.exe (PID: 3316)
- Installer.exe (PID: 4092)
- 7z.exe (PID: 3648)
- GearsHelper.exe (PID: 4056)
- GearsAgentService.exe (PID: 3004)
- waodwd.exe (PID: 2984)
- wabpoes.exe (PID: 2380)
Starts CMD.EXE for commands execution
- GearsInstaller.exe (PID: 3316)
- Gears.exe (PID: 1832)
- wabpoes.exe (PID: 2380)
- Gears.exe (PID: 2512)
Executable content was dropped or overwritten
- GearsInstaller.exe (PID: 3316)
- MSIF344.tmp (PID: 1564)
- GearsSdkInstaller.EXE (PID: 1928)
- Installer.exe (PID: 4092)
- 7z.exe (PID: 3648)
- GearsAgentService.exe (PID: 3004)
Uses TASKKILL.EXE to kill process
- GearsInstaller.exe (PID: 3316)
Application launched itself
- GearsAgentService.exe (PID: 3004)
- Gears.exe (PID: 1832)
Modifies the open verb of a shell class
- GearsAgentService.exe (PID: 3264)
Creates a software uninstall entry
- GearsInstaller.exe (PID: 3316)
Searches for installed software
- GearsInstaller.exe (PID: 3316)
- wabpoes.exe (PID: 2380)
- GearsAgentService.exe (PID: 3004)
Executed via COM
- unsecapp.exe (PID: 3780)
Creates files in the Windows directory
- GearsAgentService.exe (PID: 3004)
Starts application with an unusual extension
- cmd.exe (PID: 1948)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 2632)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1948)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 2632)
Removes files from Windows directory
- GearsAgentService.exe (PID: 3004)
Adds / modifies Windows certificates
- wabpoes.exe (PID: 2380)
- GearsAgentService.exe (PID: 3004)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 940)
Changes internet zones settings
- iexplore.exe (PID: 1388)
Application launched itself
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 2136)
Reads internet explorer settings
- iexplore.exe (PID: 2136)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 940)
Creates files in the user directory
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 940)
- iexplore.exe (PID: 2136)
Reads settings of System Certificates
- iexplore.exe (PID: 2136)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 940)
- wabpoes.exe (PID: 2380)
- GearsAgentService.exe (PID: 3004)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1388)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3508)
Dropped object may contain Bitcoin addresses
- MSIF344.tmp (PID: 1564)
- GearsInstaller.exe (PID: 3316)
- GearsSdkInstaller.EXE (PID: 1928)
- Installer.exe (PID: 4092)
Application was dropped or rewritten from another process
- MSIF344.tmp (PID: 1564)
Changes settings of System certificates
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 2136)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 2136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| HTTPEquivXUACompatible: | IE=edge |
|---|---|
| ContentType: | text/html; charset=UTF-8 |
| viewport: | width=device-width, initial-scale=1.0 |
| Keywords: | free tools, threat prevention, endpoint security |
| Description: | Use our free tools to prototype OPSWAT's enterprise-level products, or to protect your personal computer from advanced threats. Our industry-leading threat detection and prevention technology is available for limited free usage. |
| twitterCard: | summary_large_image |
| twitterSite: | @OPSWAT |
| twitterTitle: | Free Tools - We offer a number of free tools to home users for their personal use and to IT admins to prototype OPSWAT products. |
| twitterDescription: | Use our free tools to prototype OPSWAT's enterprise-level products, or to protect your personal computer from advanced threats. Our industry-leading threat detection and prevention technology is available for limited free usage. |
| twitterImageSrc: | https://www.opswat.com/uploads/assets/images/Socialimage300.png |
| twitterUrl: | https://www.opswat.com/free-tools |
| googleSiteVerification: | nVnUgP0k1RrYMJFzYCviW_fZ0sbi-JYiYb4XJpThRBU |
| Title: | Free Tools - We offer a number of free tools to home users for their personal use and to IT admins to prototype OPSWAT products. | OPSWAT |
Total processes
177
Monitored processes
57
Malicious processes
19
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Windows\system32\net.exe" stop WAOnDemand | C:\Windows\system32\net.exe | — | GearsInstaller.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 528 | "C:\Windows\system32\cmd.exe" /s /c ""C:\Program Files\OPSWAT\GEARS Client\RefreshNotificationArea.exe" " | C:\Windows\system32\cmd.exe | — | Gears.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 820 | "chcp" 437 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
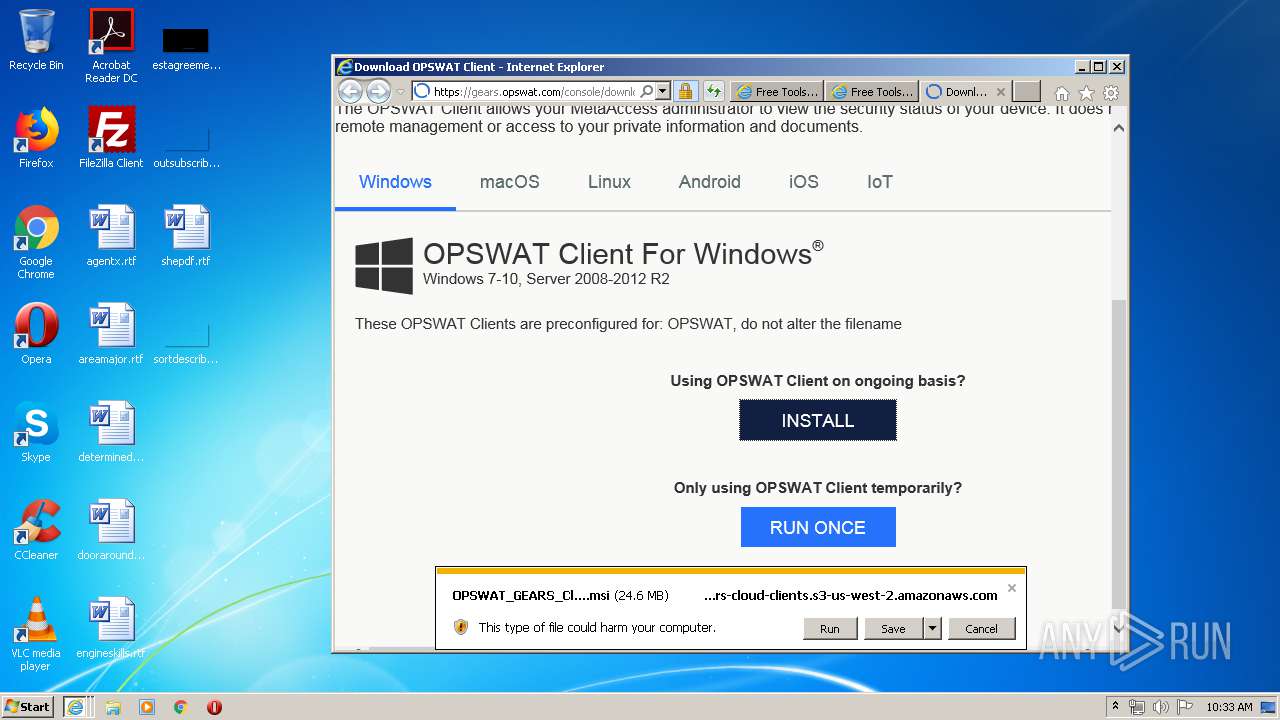
| 848 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Downloads\OPSWAT_GEARS_Client_3445-7c867995737c1853977386e89a5560c5-0.msi" | C:\Windows\System32\msiexec.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 940 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1388 CREDAT:464129 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 968 | "C:\Program Files\OPSWAT\GEARS Client\GearsHelper.exe" | C:\Program Files\OPSWAT\GEARS Client\GearsHelper.exe | — | services.exe | |||||||||||
User: SYSTEM Company: OPSWAT, Inc. Integrity Level: SYSTEM Description: OPSWAT Client Helper Exit code: 0 Version: 2, 3, 1, 0 Modules
| |||||||||||||||
| 984 | "netsh" advfirewall show currentprofile | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1024 | "netsh" advfirewall show allprofiles | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | C:\Windows\system32\net1 user admin | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1168 | "net" user admin | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 641
Read events
2 919
Write events
14 825
Delete events
5 897
Modification events
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1501261932 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30813833 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
269
Suspicious files
91
Text files
85
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab325F.tmp | — | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar3260.tmp | — | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver32CF.tmp | — | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | — | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\EM1SUQH1.txt | — | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\AI6REYBF.txt | — | |
MD5:— | SHA256:— | |||
| 3284 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab331B.tmp | — | |
MD5:— | SHA256:— | |||
| 3284 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar332B.tmp | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab3359.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
106
TCP/UDP connections
121
DNS requests
46
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3284 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2136 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2136 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3284 | iexplore.exe | GET | 200 | 172.217.18.163:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDj2UaWckc6EQIAAAAAZeIf | US | der | 472 b | whitelisted |
2136 | iexplore.exe | GET | — | 172.217.18.99:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDj2UaWckc6EQIAAAAAZeIf | US | — | — | whitelisted |
2136 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 104.17.211.204:445 | js.hs-scripts.com | Cloudflare Inc | US | shared |
4 | System | 104.17.214.204:445 | js.hs-scripts.com | Cloudflare Inc | US | shared |
4 | System | 104.17.212.204:139 | js.hs-scripts.com | Cloudflare Inc | US | shared |
4 | System | 104.17.210.204:445 | js.hs-scripts.com | Cloudflare Inc | US | shared |
2136 | iexplore.exe | 172.217.18.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
4 | System | 104.17.213.204:445 | js.hs-scripts.com | Cloudflare Inc | US | shared |
1388 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1388 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3284 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4 | System | 104.17.212.204:445 | js.hs-scripts.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
js.hs-scripts.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.googletagmanager.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
GearsInstaller.exe | |
GearsInstaller.exe | C:\ProgramData |
GearsInstaller.exe | C:\ProgramData\OPSWAT\Gears\logs\install.log |
GearsInstaller.exe | |
GearsInstaller.exe | |
GearsInstaller.exe | |
GearsInstaller.exe | |
GearsInstaller.exe | C:\ProgramData |
GearsInstaller.exe | |
GearsInstaller.exe | C:\ProgramData |