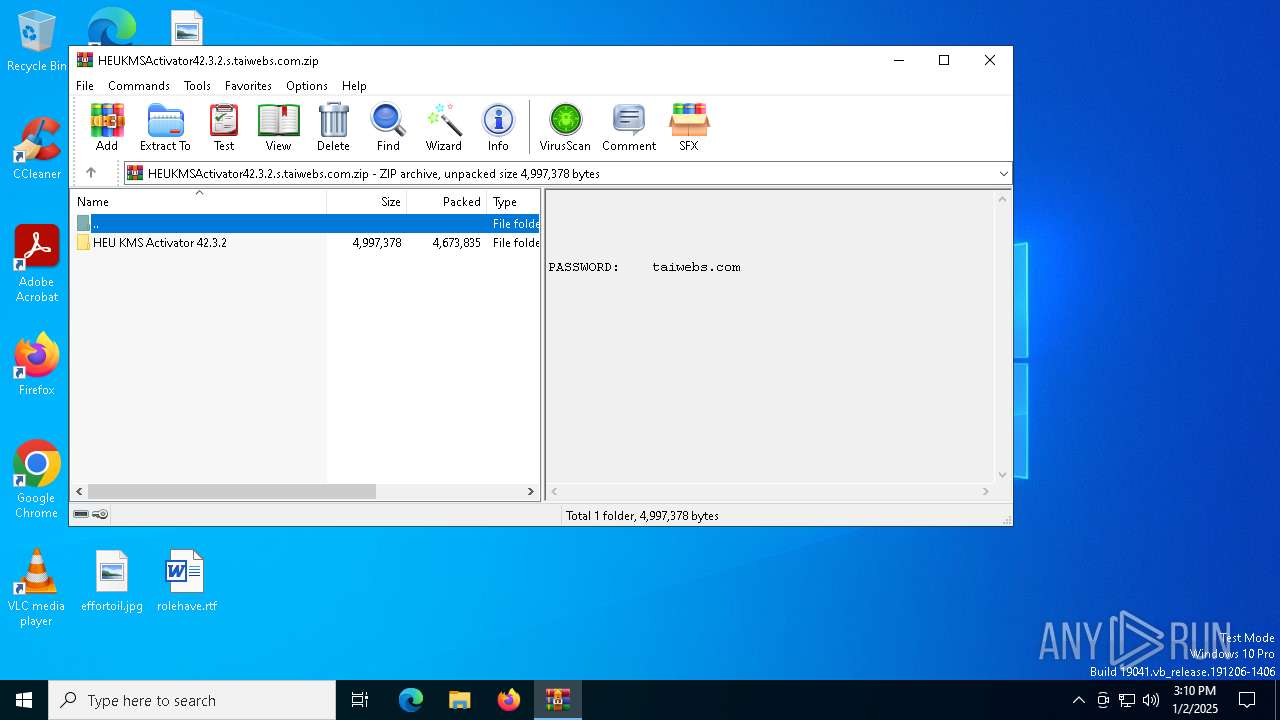
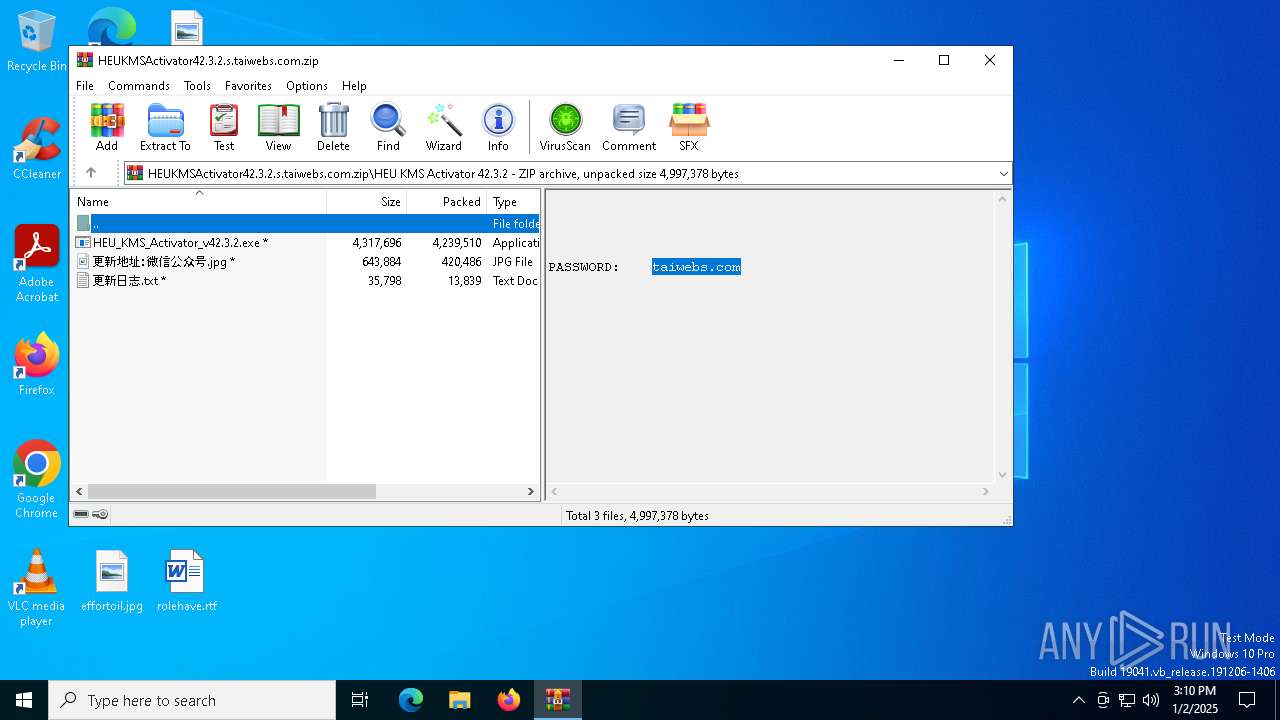
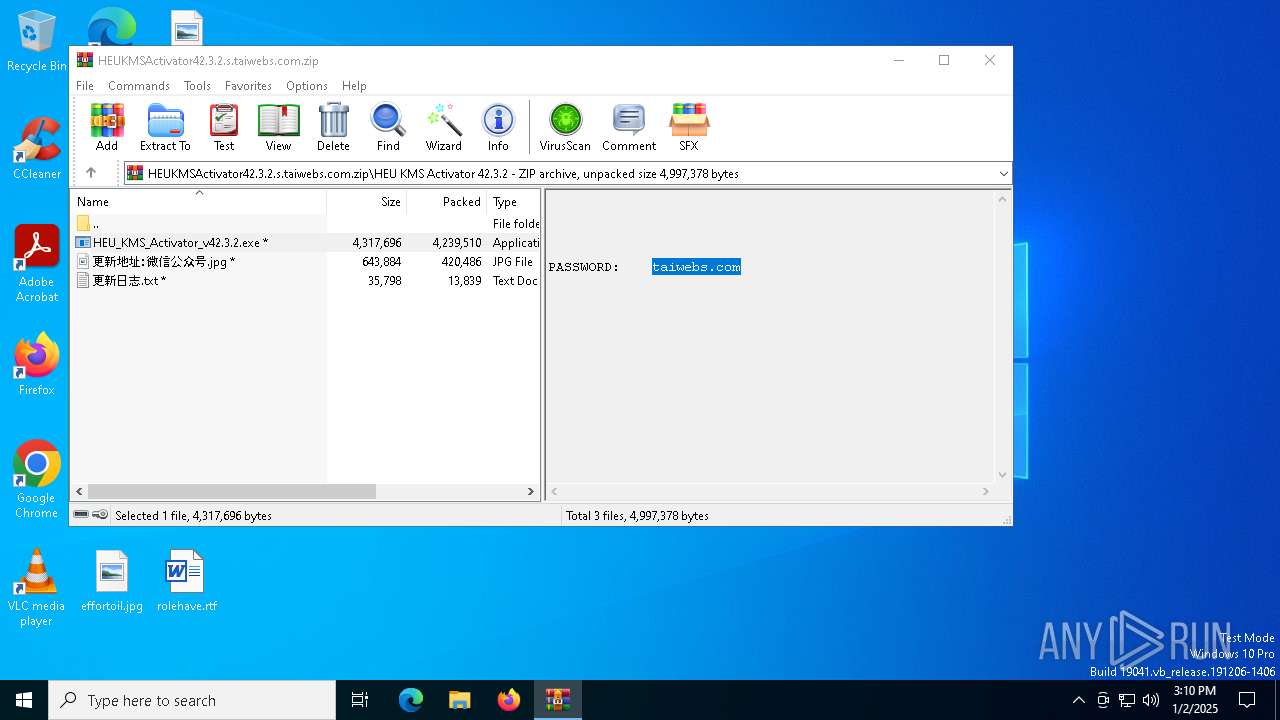
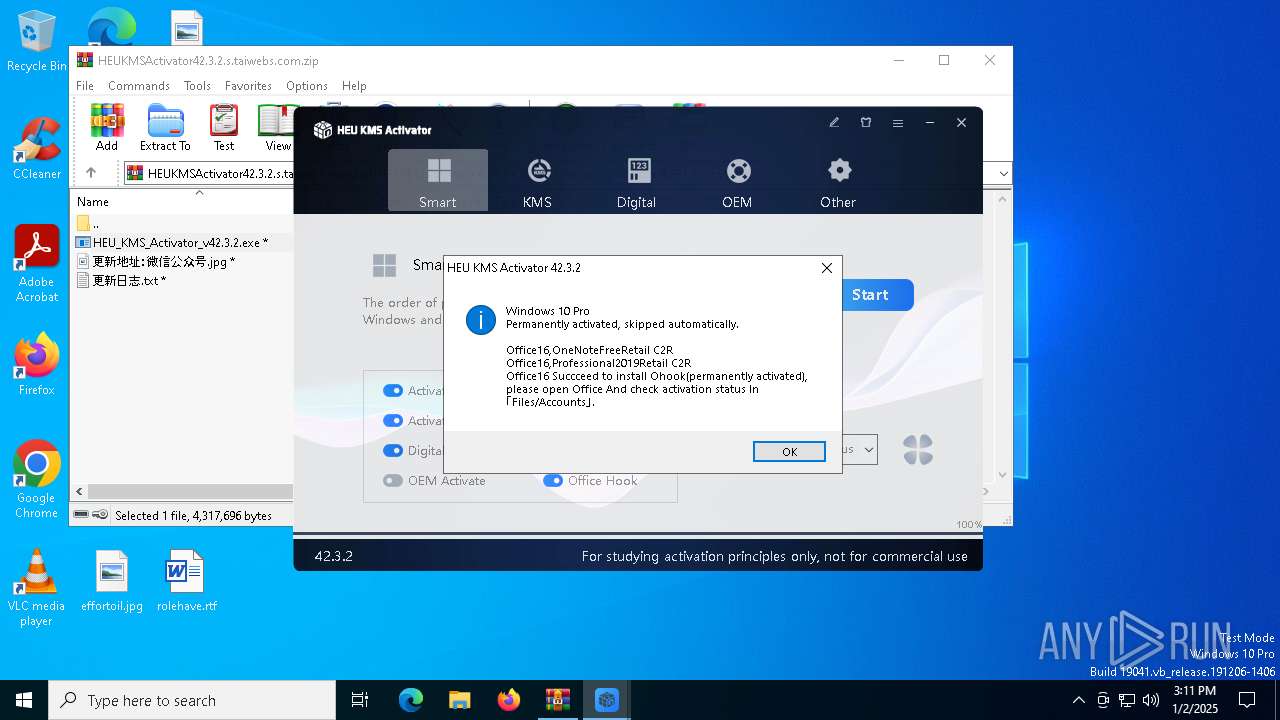
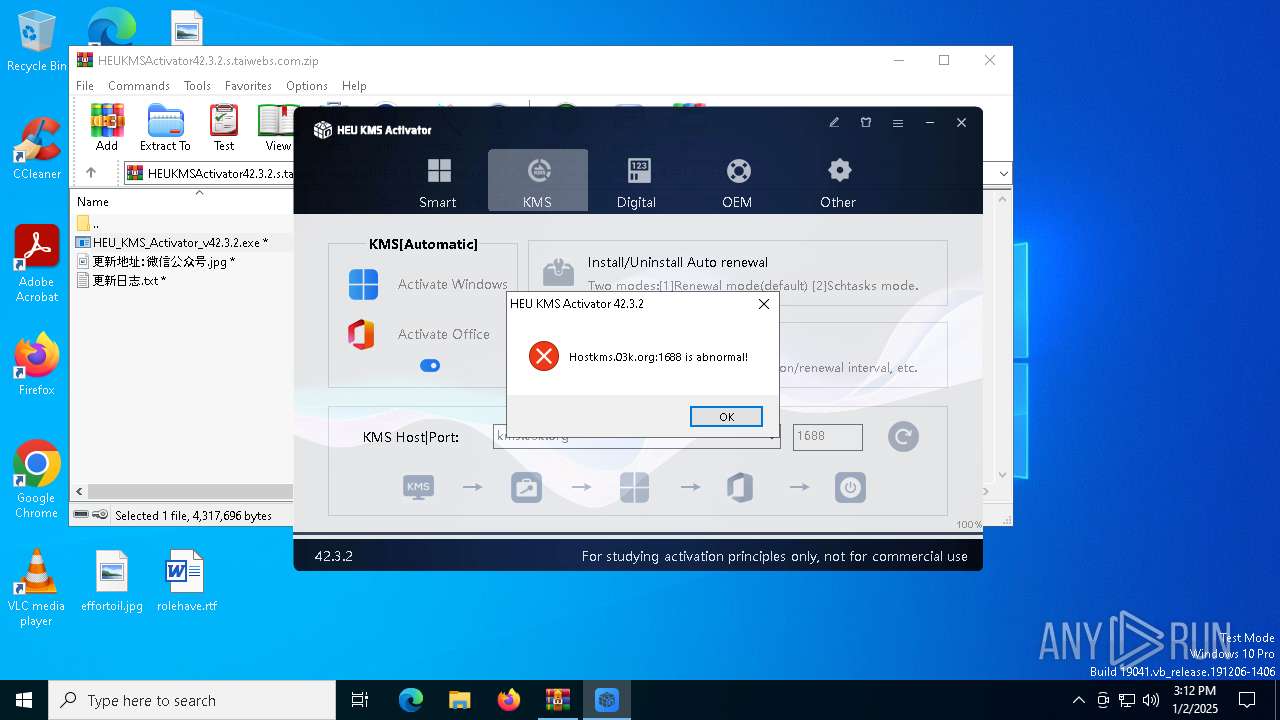
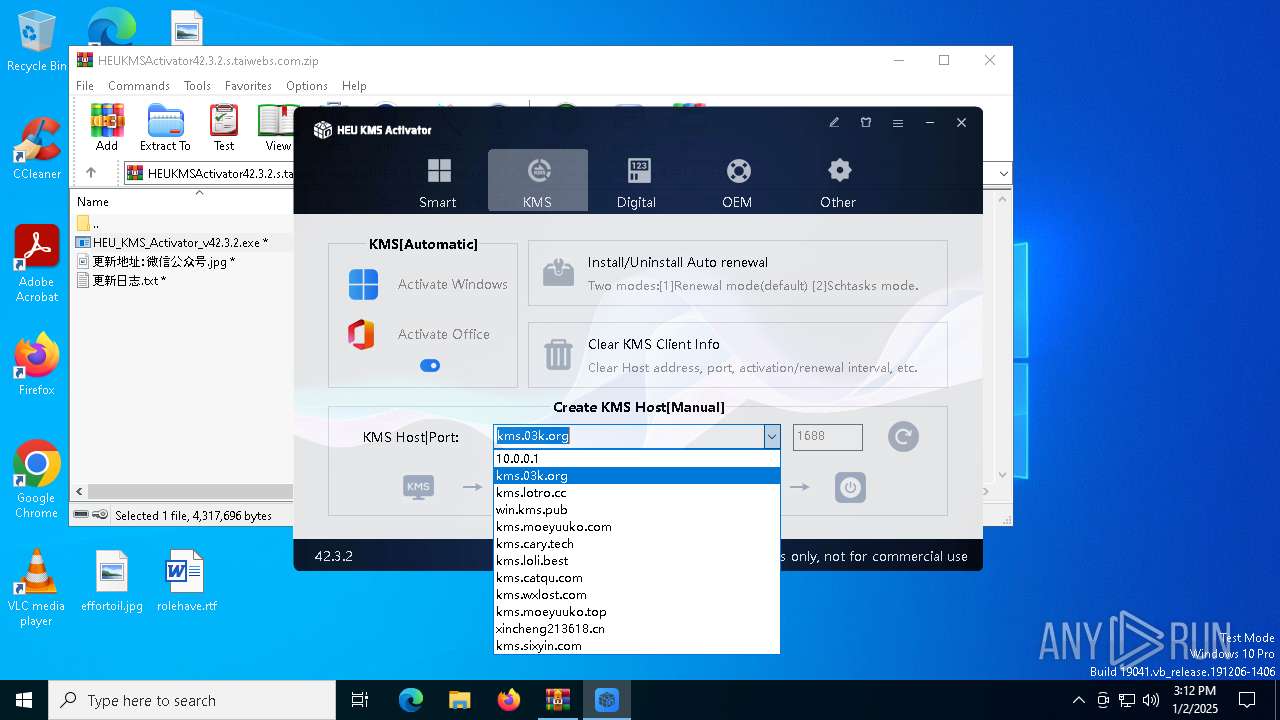
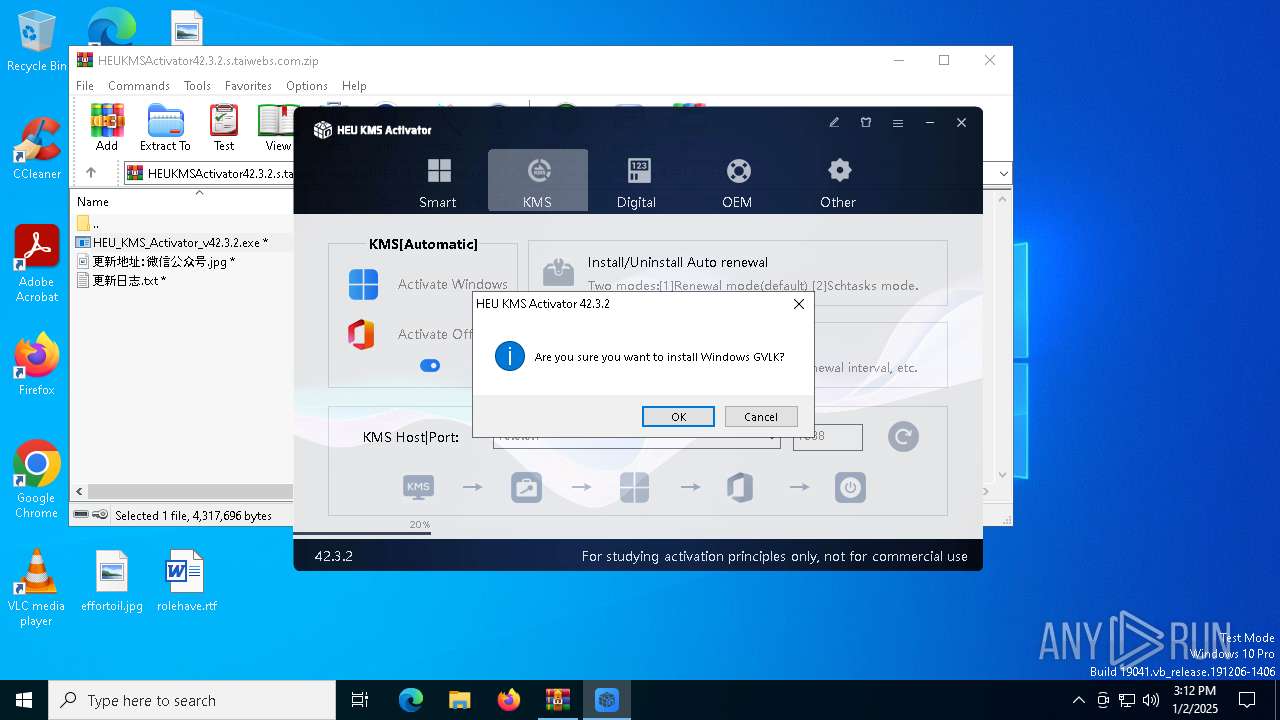
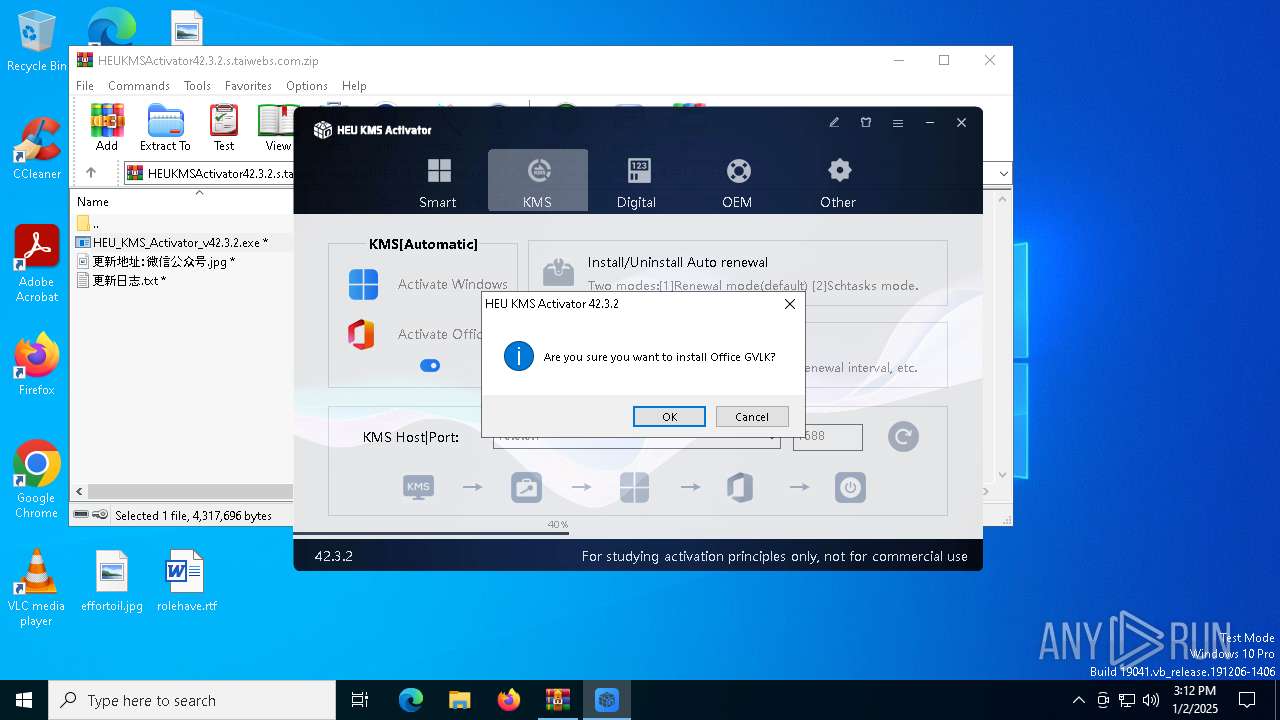
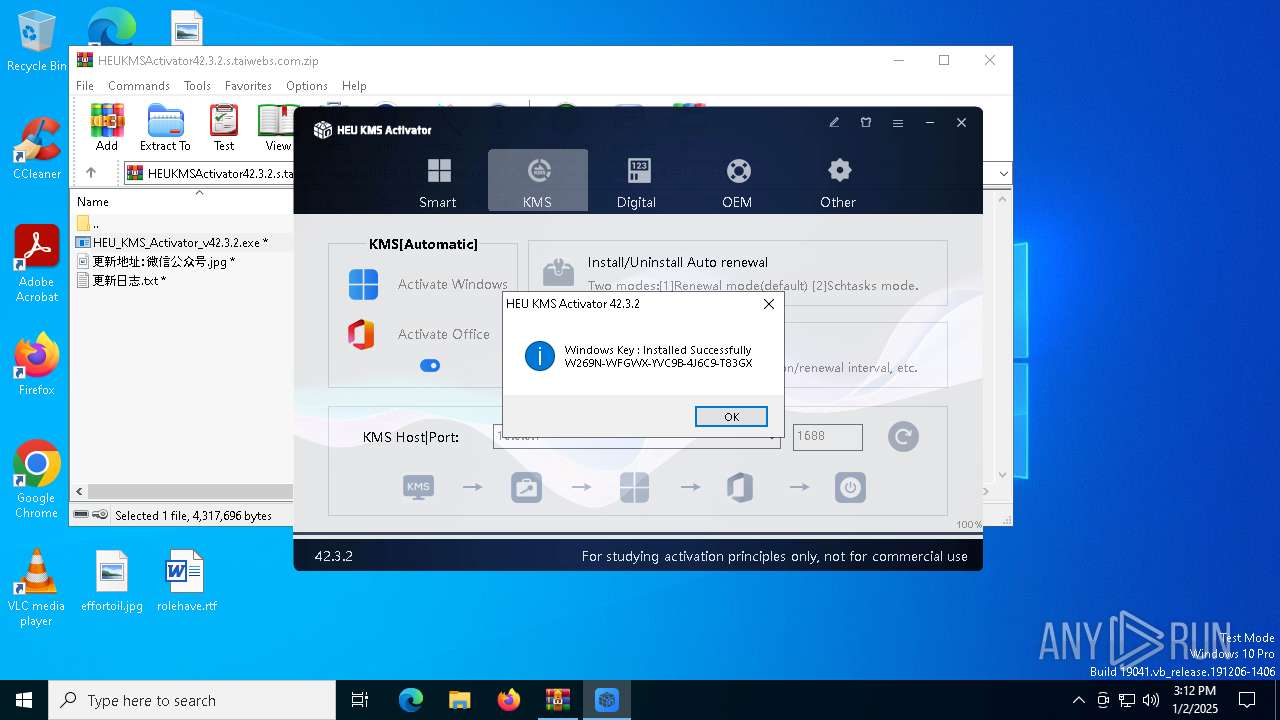
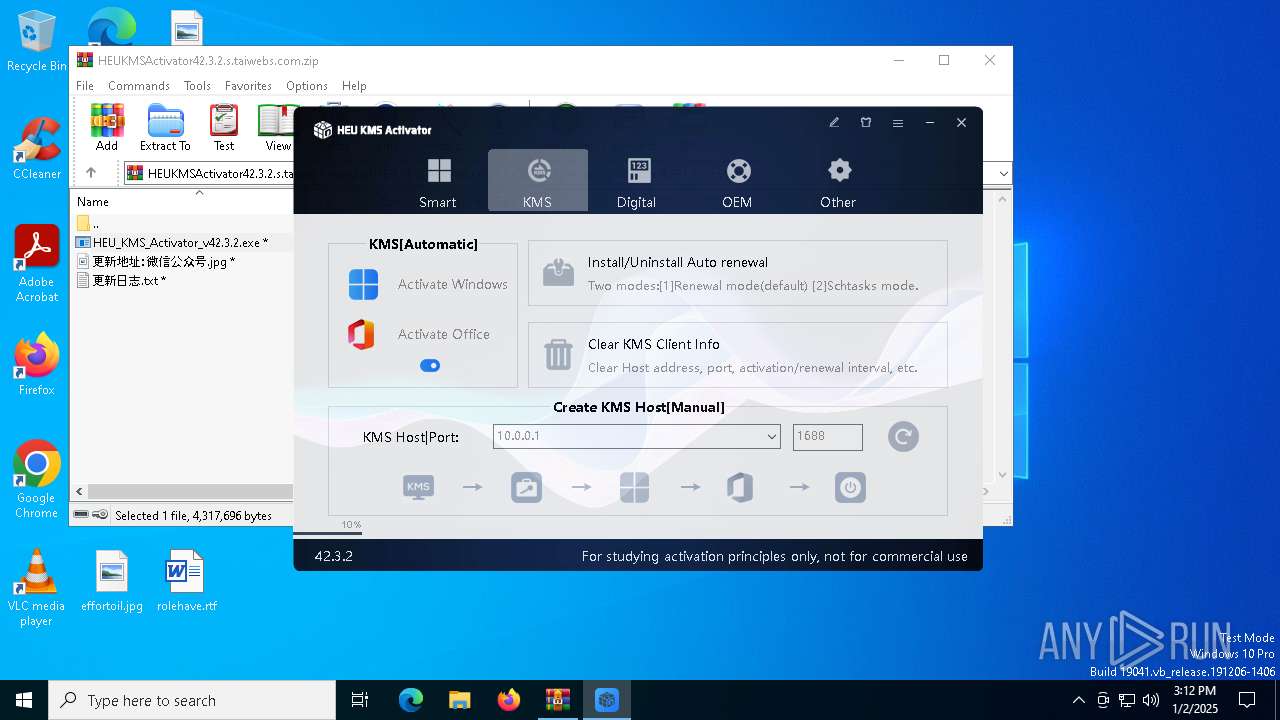
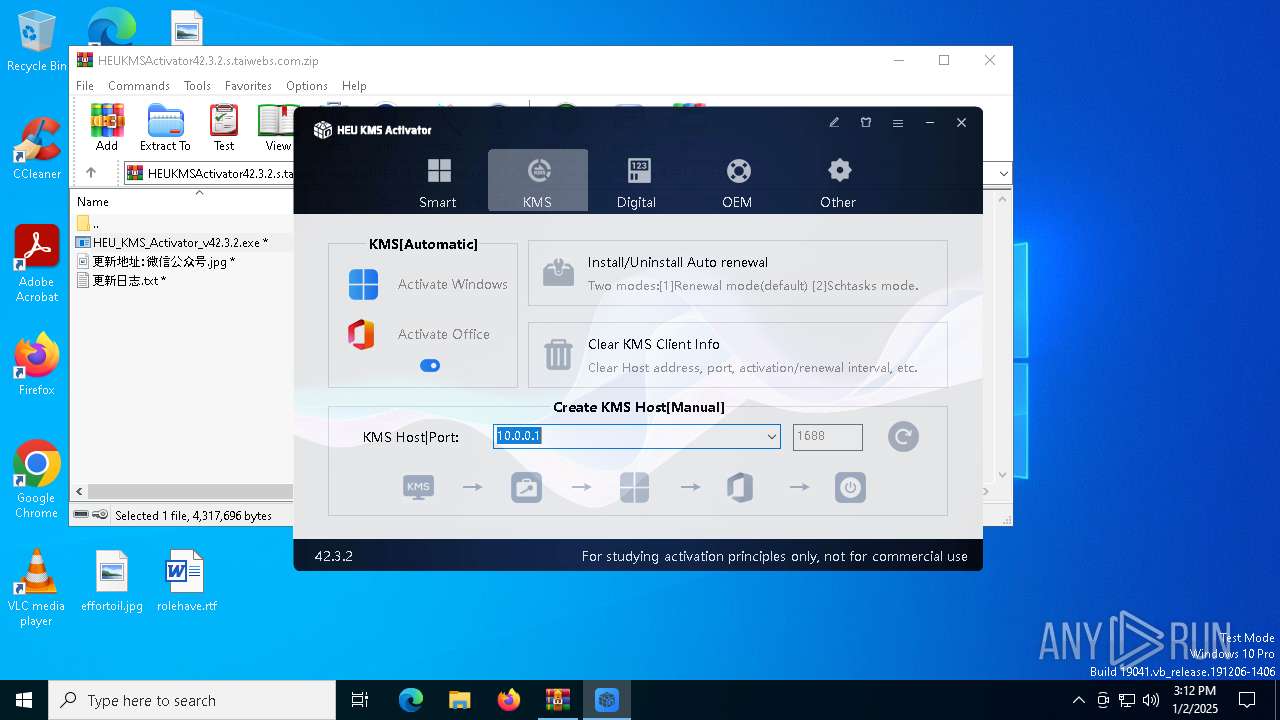
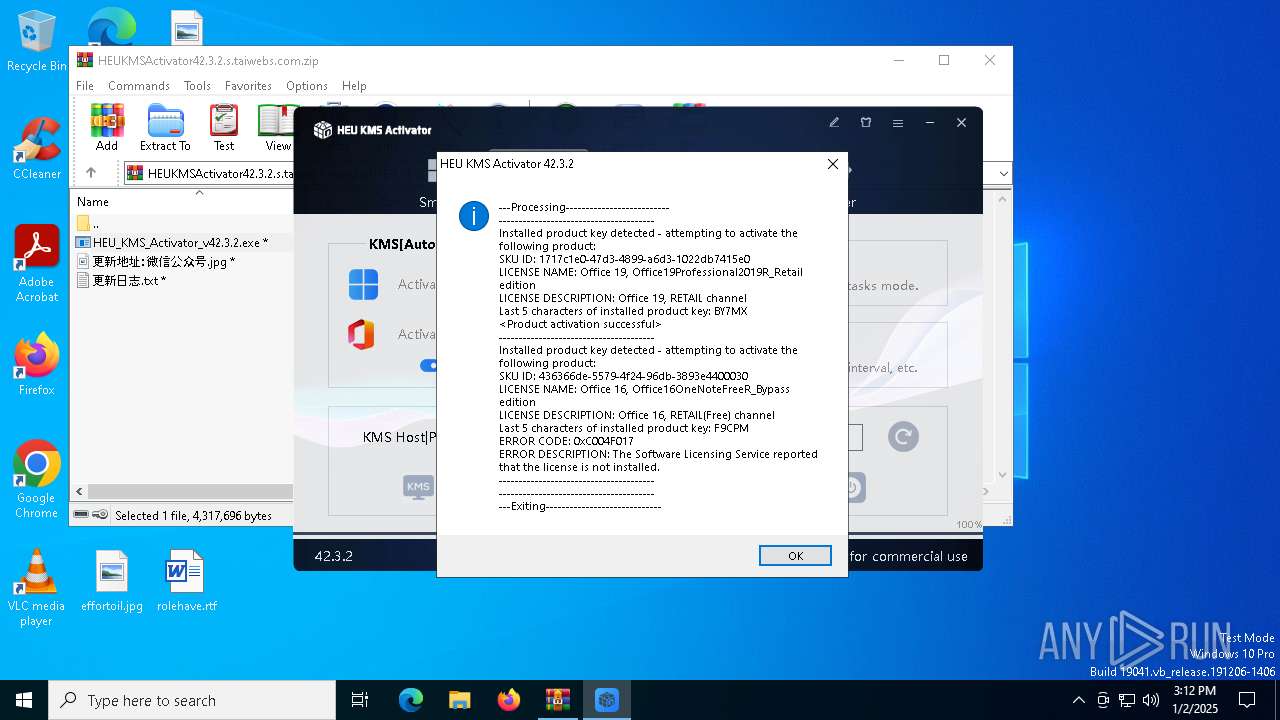
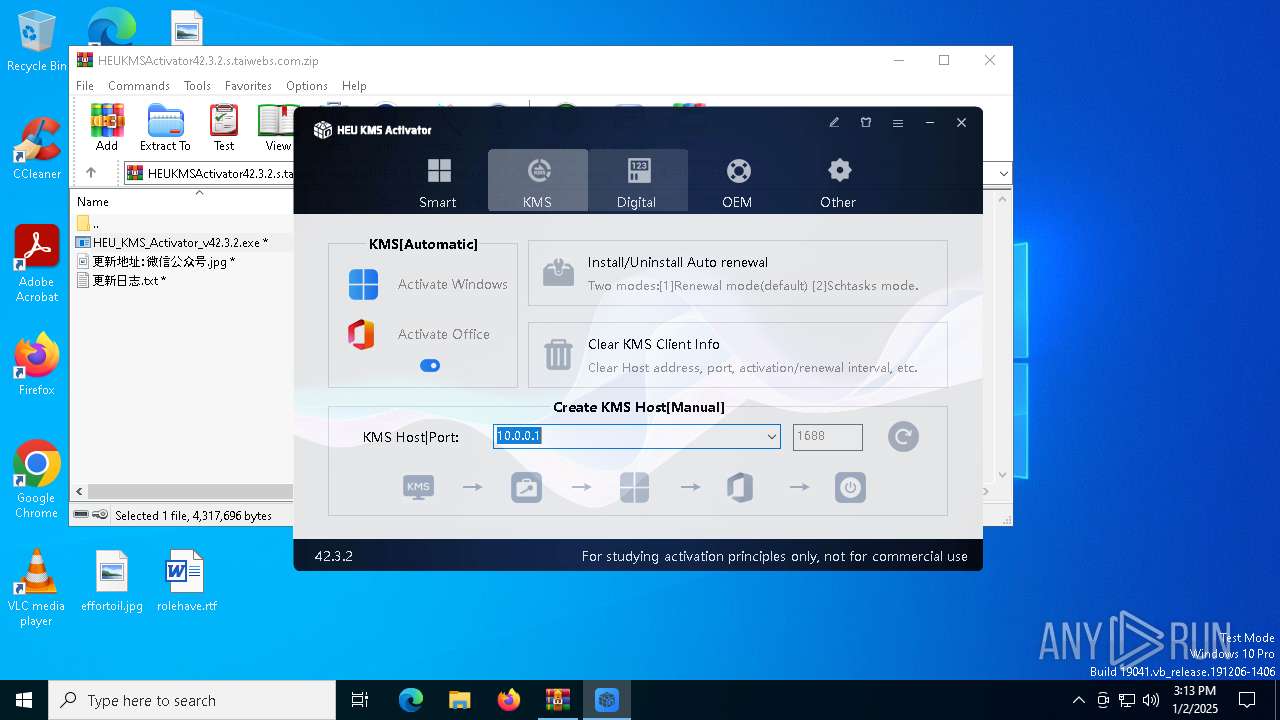
| File name: | HEUKMSActivator42.3.2.s.taiwebs.com.zip |
| Full analysis: | https://app.any.run/tasks/45c6929b-a3c3-4561-856b-1e392dca7ea1 |
| Verdict: | Malicious activity |
| Analysis date: | January 02, 2025, 15:10:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 51FC1B29CB01B1ED3D8146F775B99D3A |
| SHA1: | A096C96F841DCC2820CA835444A83AD209596791 |
| SHA256: | 691E4DB0B06CB8D6AB5AE8B29BF19677707FC530379E02A3B3671280F7D74A1A |
| SSDEEP: | 98304:yqdHujRiWoRg5LtSm6eO3udZ/r1ummFqZFscKvBvj91tPCYUzCsI5iqbsxGEfyKZ:diD7LTco |
MALICIOUS
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 2672)
Starts NET.EXE for service management
- cmd.exe (PID: 6736)
- net.exe (PID: 3124)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6448)
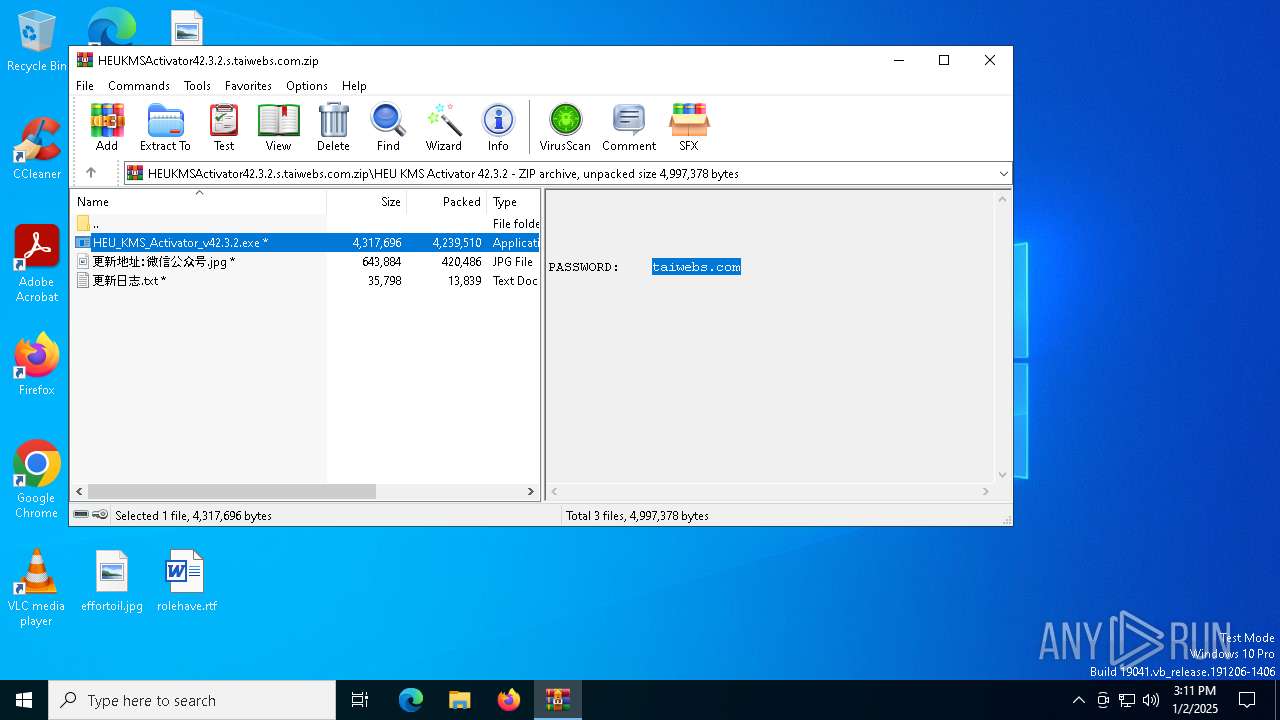
Executable content was dropped or overwritten
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- 7Z.EXE (PID: 6256)
- kms_x64.exe (PID: 132)
Drops 7-zip archiver for unpacking
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
Detected use of alternative data streams (AltDS)
- kms_x64.exe (PID: 132)
Starts CMD.EXE for commands execution
- kms_x64.exe (PID: 132)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4320)
- cscript.exe (PID: 5256)
- cscript.exe (PID: 7124)
- cscript.exe (PID: 5000)
- cscript.exe (PID: 4548)
- cscript.exe (PID: 2728)
- cscript.exe (PID: 7076)
- cscript.exe (PID: 6996)
- cscript.exe (PID: 3140)
- cscript.exe (PID: 6684)
- cscript.exe (PID: 6624)
- cscript.exe (PID: 6212)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 4592)
Windows service management via SC.EXE
- sc.exe (PID: 6728)
- sc.exe (PID: 6628)
- sc.exe (PID: 6980)
- sc.exe (PID: 3224)
- sc.exe (PID: 5300)
- sc.exe (PID: 5036)
- sc.exe (PID: 4708)
- sc.exe (PID: 6348)
- sc.exe (PID: 5780)
- sc.exe (PID: 3812)
- sc.exe (PID: 1216)
- sc.exe (PID: 7152)
- sc.exe (PID: 5252)
- sc.exe (PID: 4704)
- sc.exe (PID: 6676)
- sc.exe (PID: 6940)
- sc.exe (PID: 6584)
- sc.exe (PID: 6972)
- sc.exe (PID: 3840)
- sc.exe (PID: 6652)
- sc.exe (PID: 6336)
- sc.exe (PID: 3836)
- sc.exe (PID: 4972)
- sc.exe (PID: 5004)
- sc.exe (PID: 3680)
- sc.exe (PID: 4400)
- sc.exe (PID: 2216)
- sc.exe (PID: 4996)
- sc.exe (PID: 6228)
- sc.exe (PID: 1296)
- sc.exe (PID: 5160)
- sc.exe (PID: 4684)
- sc.exe (PID: 6324)
- sc.exe (PID: 4980)
- sc.exe (PID: 8)
- sc.exe (PID: 6388)
- sc.exe (PID: 4136)
- sc.exe (PID: 2436)
- sc.exe (PID: 3820)
- sc.exe (PID: 6892)
- sc.exe (PID: 4056)
- sc.exe (PID: 6724)
- sc.exe (PID: 5988)
- sc.exe (PID: 5684)
- sc.exe (PID: 6408)
- sc.exe (PID: 6580)
Starts SC.EXE for service management
- cmd.exe (PID: 6624)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 6012)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 5872)
- cmd.exe (PID: 640)
- cmd.exe (PID: 5560)
- cmd.exe (PID: 6444)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 1620)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 3732)
- cmd.exe (PID: 4500)
- cmd.exe (PID: 6424)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 6716)
- cmd.exe (PID: 4468)
- cmd.exe (PID: 1172)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 5572)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 1488)
- cmd.exe (PID: 1468)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 2120)
- cmd.exe (PID: 848)
- cmd.exe (PID: 2220)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 6924)
- cmd.exe (PID: 4992)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 4968)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 1620)
- cmd.exe (PID: 5208)
- cmd.exe (PID: 3040)
- cmd.exe (PID: 4840)
- cmd.exe (PID: 5912)
Connects to unusual port
- kms_x64.exe (PID: 132)
The executable file from the user directory is run by the CMD process
- kms-server.exe (PID: 6420)
- kms-server.exe (PID: 6748)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1856)
- cmd.exe (PID: 1400)
- cmd.exe (PID: 4876)
The process executes VB scripts
- cmd.exe (PID: 2408)
- cmd.exe (PID: 4640)
- cmd.exe (PID: 5028)
- cmd.exe (PID: 6740)
- cmd.exe (PID: 6860)
- cmd.exe (PID: 2484)
- cmd.exe (PID: 4360)
- cmd.exe (PID: 1292)
- cmd.exe (PID: 6652)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3140)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 6684)
- cscript.exe (PID: 6624)
- cscript.exe (PID: 6212)
- cscript.exe (PID: 4872)
- cscript.exe (PID: 1328)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 3140)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 6684)
- cscript.exe (PID: 6624)
- cscript.exe (PID: 6212)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 4640)
- cmd.exe (PID: 1292)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 1328)
- cscript.exe (PID: 4872)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 4872)
- cscript.exe (PID: 1328)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 4872)
- cscript.exe (PID: 1328)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1328)
- cscript.exe (PID: 4872)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6448)
The process uses the downloaded file
- WinRAR.exe (PID: 6448)
- cscript.exe (PID: 4320)
- cscript.exe (PID: 5256)
- cscript.exe (PID: 7124)
- cscript.exe (PID: 5000)
- cscript.exe (PID: 2144)
- cscript.exe (PID: 3436)
Reads mouse settings
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- kms_x64.exe (PID: 132)
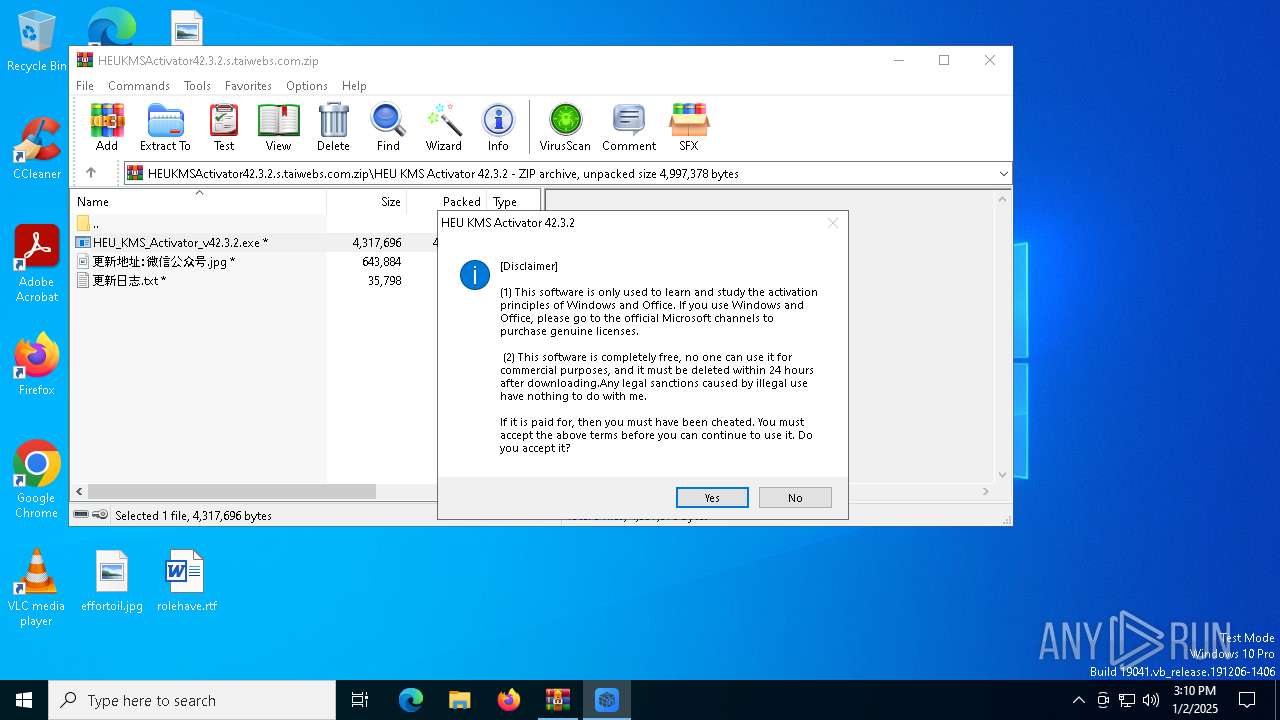
The sample compiled with chinese language support
- WinRAR.exe (PID: 6448)
- 7Z.EXE (PID: 6256)
Reads the computer name
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- 7Z.EXE (PID: 6256)
Checks supported languages
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- 7Z.EXE (PID: 6256)
- kms_x64.exe (PID: 132)
The sample compiled with english language support
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- kms_x64.exe (PID: 132)
Create files in a temporary directory
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- 7Z.EXE (PID: 6256)
- kms_x64.exe (PID: 132)
UPX packer has been detected
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- kms_x64.exe (PID: 132)
Reads security settings of Internet Explorer
- cscript.exe (PID: 4320)
- cscript.exe (PID: 5256)
- cscript.exe (PID: 7124)
- cscript.exe (PID: 5000)
- cscript.exe (PID: 4548)
- cscript.exe (PID: 2728)
- cscript.exe (PID: 6996)
- cscript.exe (PID: 7076)
- cscript.exe (PID: 6684)
- cscript.exe (PID: 6212)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 1328)
- cscript.exe (PID: 4012)
- cscript.exe (PID: 4592)
- cscript.exe (PID: 2144)
- cscript.exe (PID: 3436)
Reads Microsoft Office registry keys
- kms_x64.exe (PID: 132)
Reads Environment values
- kms_x64.exe (PID: 132)
Reads product name
- kms_x64.exe (PID: 132)
The process uses AutoIt
- HEU_KMS_Activator_v42.3.2.exe (PID: 6208)
- kms_x64.exe (PID: 132)
Creates files in the program directory
- cmd.exe (PID: 6848)
- kms_x64.exe (PID: 132)
Checks proxy server information
- cscript.exe (PID: 1328)
Creates files or folders in the user directory
- cscript.exe (PID: 1328)
Reads the software policy settings
- cscript.exe (PID: 2144)
- cscript.exe (PID: 1328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:02 20:41:54 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | HEU KMS Activator 42.3.2/ |
Total processes
363
Monitored processes
227
Malicious processes
10
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | sc query TrustedInstaller | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x64\kms_x64.exe | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\x64\kms_x64.exe | HEU_KMS_Activator_v42.3.2.exe | ||||||||||||
User: admin Company: 知彼而知己 Integrity Level: HIGH Description: HEU KMS Activator™ Version: 42.3.2.0 Modules
| |||||||||||||||
| 436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | icacls C:\WINDOWS\System32\SECOPatcher.dll /reset | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | C:\WINDOWS\system32\cmd.exe /c C:\WINDOWS\System32\cscript.exe //nologo //Job:WmiQuery "C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\xml\wim.xml?.wsf" SoftwareLicensingService Version | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | C:\WINDOWS\system32\cmd.exe /c sc query osppsvc | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 880
Read events
22 857
Write events
20
Delete events
3
Modification events
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\HEUKMSActivator42.3.2.s.taiwebs.com.zip | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (132) kms_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\Resiliency |
| Operation: | write | Name: | TimeOfLastHeartbeatFailure |
Value: 2040-01-01T00:00:00Z | |||
Executable files
11
Suspicious files
11
Text files
87
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6448.46071\HEU KMS Activator 42.3.2\更新日志.txt | text | |
MD5:A0210CF26F7ACC67DFB9CAF6B928D0E1 | SHA256:7FF77278A7A420EBBCF19C74F45C9856D2ECBC14496D2535B6D2C45A95C10839 | |||
| 6448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6448.46071\HEU KMS Activator 42.3.2\更新地址:微信公众号.jpg | image | |
MD5:123A56F34EEE911CF7947E67082643A5 | SHA256:36483CEA085373955D9C504FAF8D0A608A4109760A7BCC36FC38887C8C45DDEC | |||
| 6448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6448.46071\HEU KMS Activator 42.3.2\HEU_KMS_Activator_v42.3.2.exe | executable | |
MD5:2C1D71A76EA8928500291D4972ADFAF1 | SHA256:E12852FF90376F907F0FA17FD48919EF1D1DB76ECE121879B55B67DD311B3060 | |||
| 6208 | HEU_KMS_Activator_v42.3.2.exe | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\7Z.EXE | executable | |
MD5:43141E85E7C36E31B52B22AB94D5E574 | SHA256:EA308C76A2F927B160A143D94072B0DCE232E04B751F0C6432A94E05164E716D | |||
| 6256 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\pic\1-1.bmp | image | |
MD5:854FDB63B26F58D482A85F4A7D87EB75 | SHA256:8D3B094B0984A03453F11D7D587226F4E29665E1B0E04B76F009A8E8268FE18C | |||
| 6256 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Office2010OSPP\OSPP.VBS | text | |
MD5:572E9A87757AC96C7677FD1B1B113C55 | SHA256:008CF05944053116A095AD466561D3FD4BE8A7DE79E5ADA7C5DAAB492F730465 | |||
| 6208 | HEU_KMS_Activator_v42.3.2.exe | C:\Users\admin\AppData\Local\Temp\autBB86.tmp | binary | |
MD5:E25E09DF3DB990F98A165990B2F48B02 | SHA256:52F64C84948068514240283D6C7FA1204E81CA0549CF0159FCACC556A950CD94 | |||
| 6256 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\Office2010OSPP\SLERROR.XML | text | |
MD5:DF1EF05879E06C5F09F3E1022F37B5CB | SHA256:D49ADF2DABBBF6AA43CE4E336AF4F768207DF75302EBF568A94A5350AAC988C5 | |||
| 6256 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\_temp_heu168yyds\OtherOfficeOSPP\slerror.xml | text | |
MD5:36F7DADFE84E62DA00292D0569C3F523 | SHA256:B3378A3178F3E52094DB20E8A828011CD8882017919522A544BAEF3057BD11D3 | |||
| 6208 | HEU_KMS_Activator_v42.3.2.exe | C:\Users\admin\AppData\Local\Temp\splashlogo.jpg | image | |
MD5:03361B7B3BAB104DFF232D8AB607319F | SHA256:81FF582D54D96E22AC5E54B0BC914560B2D0E85EB775DCF500EEBA1BFD9F72F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
37
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6376 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2548 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2548 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1328 | cscript.exe | GET | 200 | 23.48.23.181:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3508 | svchost.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3508 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.168:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |