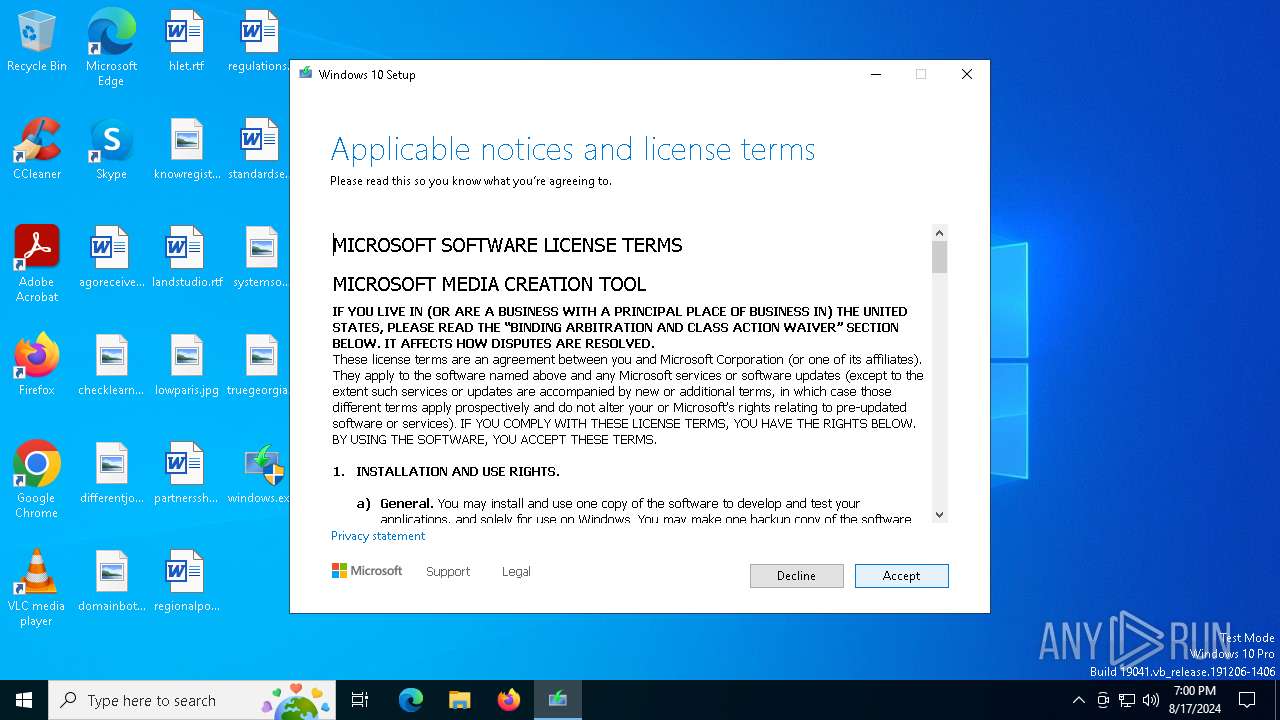
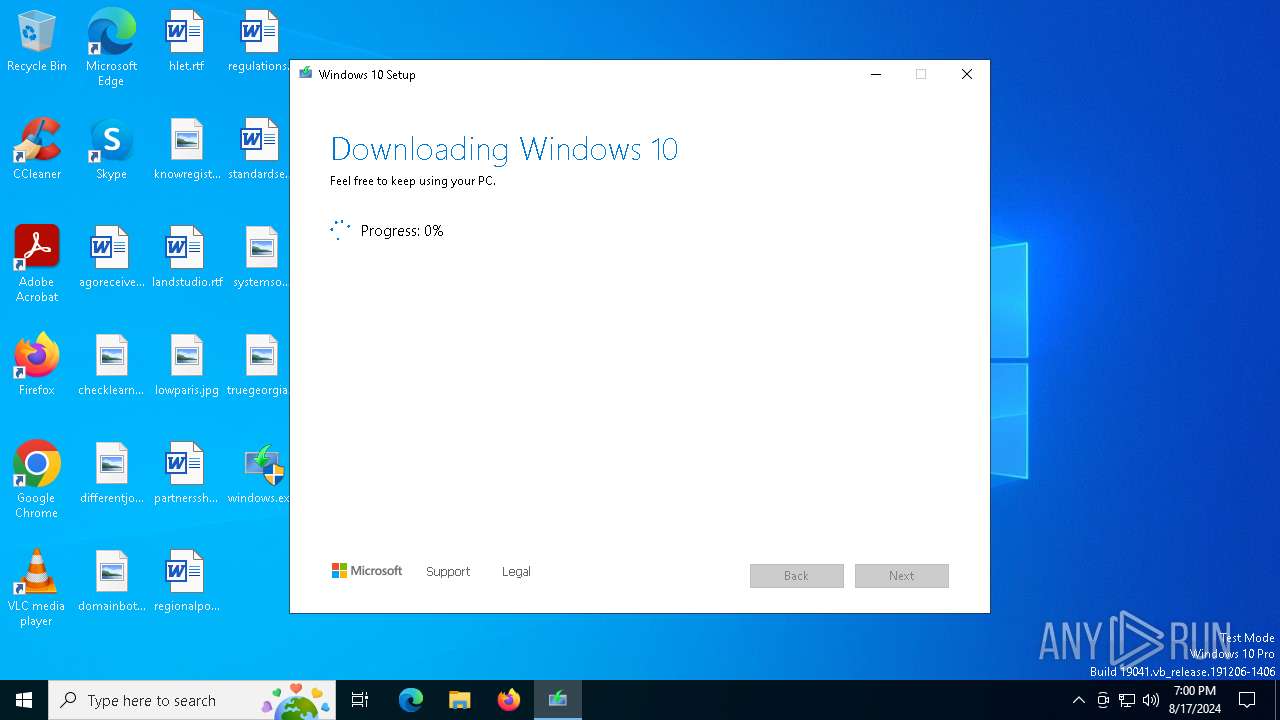
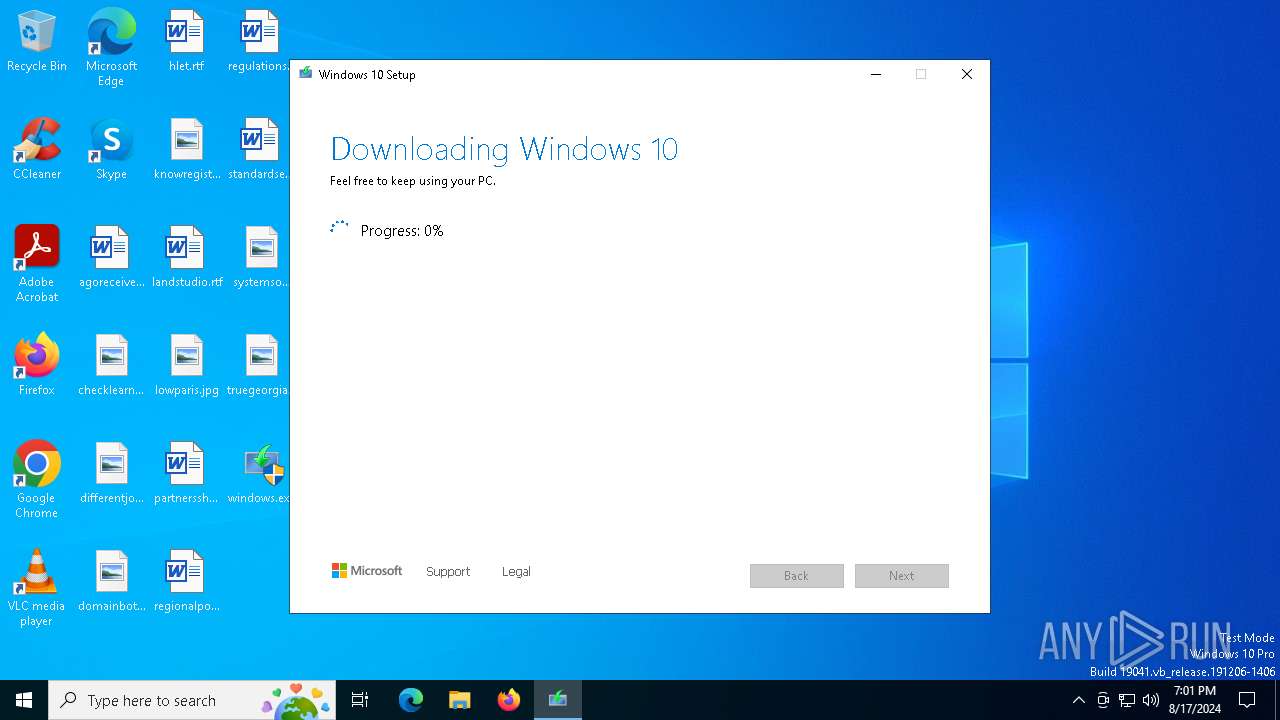
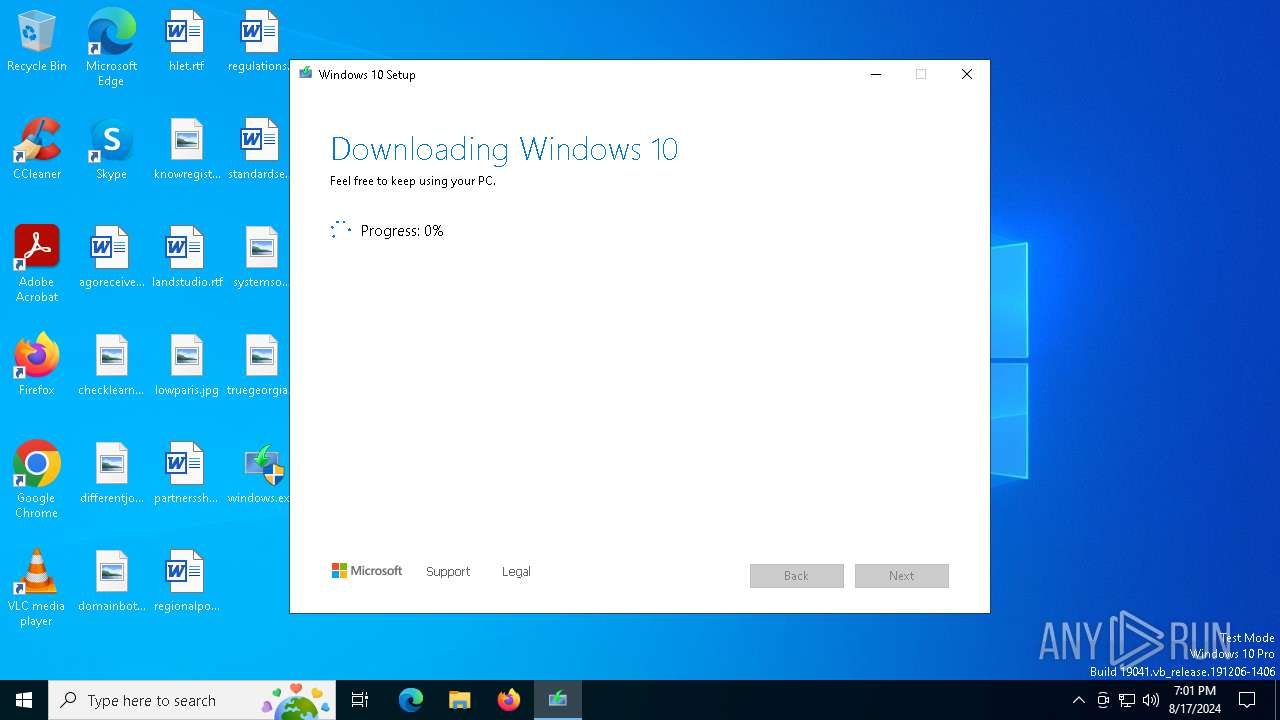
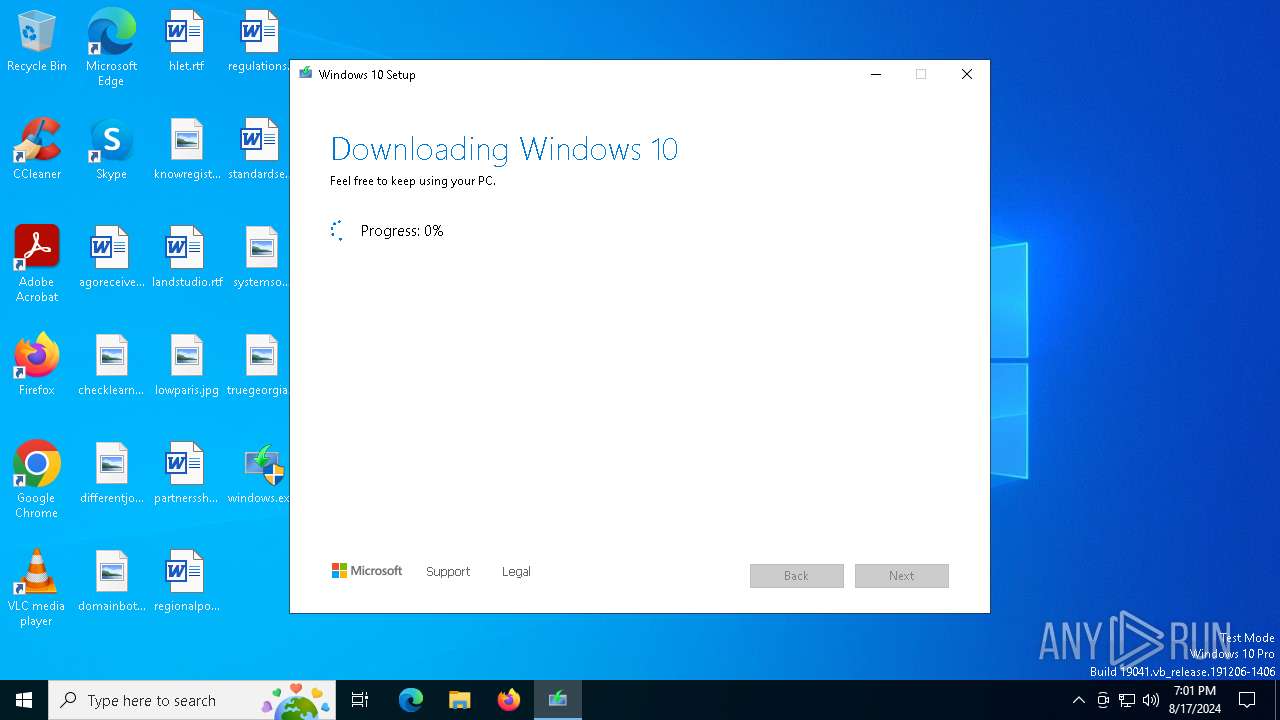
| File name: | windows.exe |
| Full analysis: | https://app.any.run/tasks/86a5f96b-495e-4d95-a1f4-e43d811e1e85 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2024, 18:59:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | AA2AD37BB74C05A49417E3D2F1BD89CE |
| SHA1: | 1BF5F814FFE801B4E6F118E829C0D2821D78A60A |
| SHA256: | 690C8A63769D444FAD47B7DDECEE7F24C9333AA735D0BD46587D0DF5CF15CDE5 |
| SSDEEP: | 196608:MmtHa+5hH1km/Sf7byFXKEBmih9S5rQ5FNFl001p4Ki:Y+5RB/SDbyFBH9eQD/l00/4 |
MALICIOUS
The DLL Hijacking
- SetupHost.exe (PID: 6748)
SUSPICIOUS
Process drops legitimate windows executable
- windows.exe (PID: 6636)
Drops the executable file immediately after the start
- windows.exe (PID: 6636)
The process creates files with name similar to system file names
- windows.exe (PID: 6636)
Starts a Microsoft application from unusual location
- windows.exe (PID: 6588)
- windows.exe (PID: 6636)
Executable content was dropped or overwritten
- windows.exe (PID: 6636)
INFO
Reads the computer name
- windows.exe (PID: 6636)
- SetupHost.exe (PID: 6748)
Checks supported languages
- windows.exe (PID: 6636)
- SetupHost.exe (PID: 6748)
Reads the machine GUID from the registry
- SetupHost.exe (PID: 6748)
Reads Environment values
- SetupHost.exe (PID: 6748)
Checks proxy server information
- SetupHost.exe (PID: 6748)
Process checks computer location settings
- SetupHost.exe (PID: 6748)
Reads the software policy settings
- SetupHost.exe (PID: 6748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1974:05:29 19:08:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.2 |
| CodeSize: | 490496 |
| InitializedDataSize: | 11057152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x729b0 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.572 |
| ProductVersionNumber: | 10.0.19041.572 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Arabic |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | إعداد Windows 10 |
| FileVersion: | 10.0.19041.572 (vb_release_svc_prod1.201007-1724) |
| InternalName: | SetupPrep.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | SetupPrep.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.572 |
Total processes
124
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6588 | "C:\Users\admin\Desktop\windows.exe" | C:\Users\admin\Desktop\windows.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows 10 Setup Exit code: 3221226540 Version: 10.0.19041.572 (vb_release_svc_prod1.201007-1724) Modules
| |||||||||||||||
| 6636 | "C:\Users\admin\Desktop\windows.exe" | C:\Users\admin\Desktop\windows.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows 10 Setup Version: 10.0.19041.572 (vb_release_svc_prod1.201007-1724) Modules
| |||||||||||||||
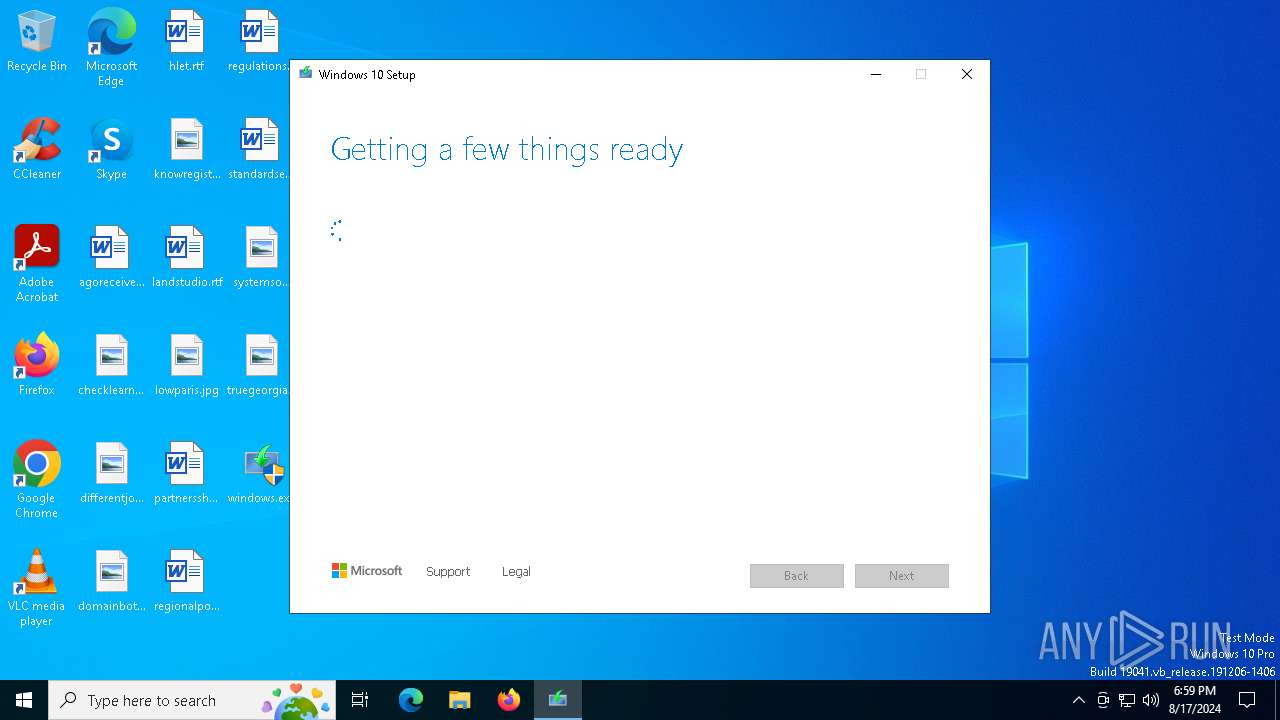
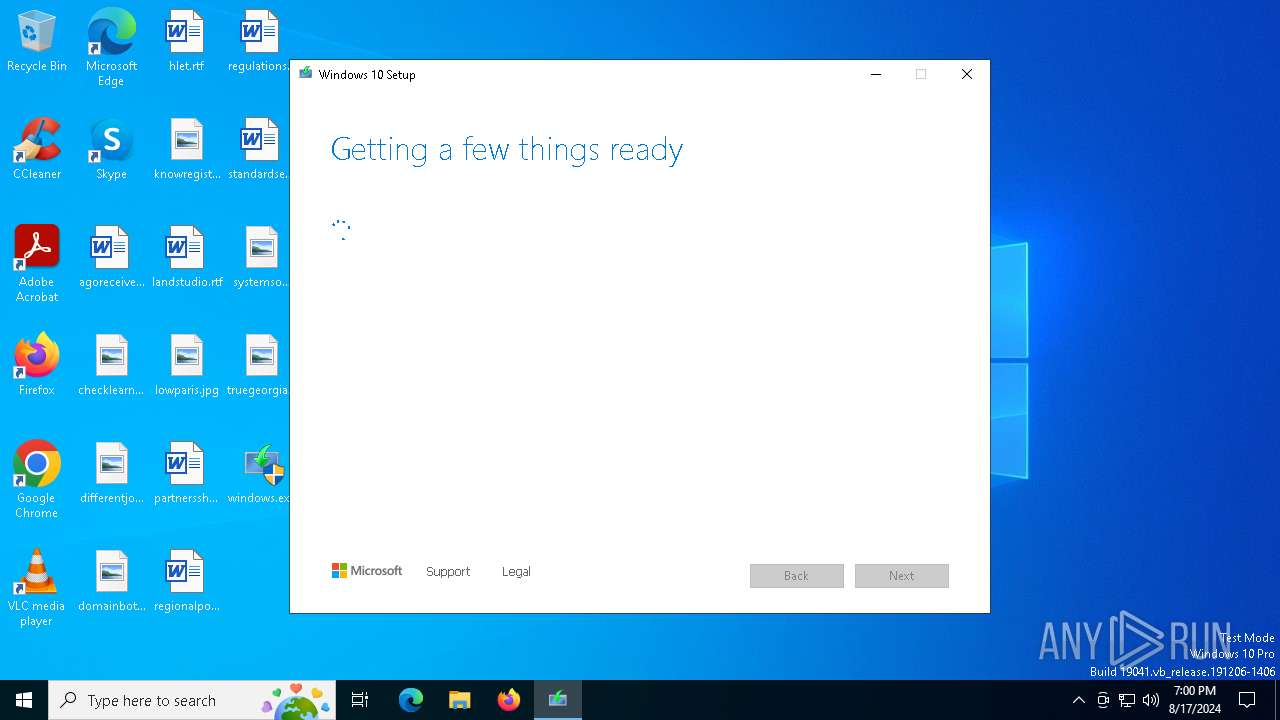
| 6748 | "C:\$Windows.~WS\Sources\SetupHost.Exe" /Download /Web | C:\$Windows.~WS\Sources\SetupHost.exe | windows.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Modern Setup Host Version: 10.0.19041.572 (vb_release_svc_prod1.201007-1724) Modules
| |||||||||||||||
| 7136 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 352
Read events
4 302
Write events
48
Delete events
2
Modification events
| (PID) Process: | (6636) windows.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\MoSetup\Volatile |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6636) windows.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\MoSetup |
| Operation: | delete value | Name: | CorrelationVector |
Value: IYXEGxww/0WC95lB.37 | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\MoSetup |
| Operation: | write | Name: | CorrelationVector |
Value: jg0IwS7iik+shQHs.0 | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360 |
| Operation: | write | Name: | ETag |
Value: 880:66A2A386 | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360 |
| Operation: | write | Name: | RefreshInterval |
Value: 880 | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360\QueryParameters |
| Operation: | write | Name: | os |
Value: windows | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360\QueryParameters |
| Operation: | write | Name: | osver |
Value: 10.0.19041.4046.amd64fre.vb_release.191206-1406 | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360\QueryParameters |
| Operation: | write | Name: | scenarioId |
Value: 7 | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360\QueryParameters |
| Operation: | write | Name: | platformEdition |
Value: Professional | |||
| (PID) Process: | (6748) SetupHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\OneSettings\WSD\Setup360\QueryParameters |
| Operation: | write | Name: | platformInstallationType |
Value: Client | |||
Executable files
19
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6636 | windows.exe | C:\$Windows.~WS\Sources\wdsclientapi.dll | executable | |
MD5:C8622591EA490127898FF612C4D0FCE8 | SHA256:00436605B013E26F39B3FF6AAB1E5577FE6E4950C4C803D534D0BBD912B3F7E0 | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\setupplatform.dll | executable | |
MD5:0DB2EB7B159D7289DFBDF3CA29D44704 | SHA256:CBEEC25C578F4E8EAE81BB8829C3B7BC81648DA6F63EEB4A606B9A66660D6D91 | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\wpx.dll | executable | |
MD5:15E92D3769E6EEFA80DAAC3085741BF6 | SHA256:08C8A6B2F76F9D9152E01FF3118990FDCDBB0D2E8C57DBFE43568367493187D4 | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\unbcl.dll | executable | |
MD5:5D52A4EFAC5B4B7530B388AEB6F9CB67 | SHA256:137ECA75B268556503E26CD5987DDDAC5EB0831ED4CE5EA3B0D34B5645A31ABD | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\wdstptc.dll | executable | |
MD5:7A020A931614E1A7CA1DB482D1C00EDE | SHA256:48EE94546C9345FBE5AD1A51F4826B131DA554A8E4395E5D22E4CDE09B3816D5 | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\wdscore.dll | executable | |
MD5:07F3FAC5518C90B22DFB9778EA280D0A | SHA256:65467BF1FBF10C2A399FE532B780F3604FDA5B00DB8319787CB6867BEDE4B90E | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\MediaSetupUIMgr.dll | executable | |
MD5:BDBD14F60FC78EDCA16A022C9801CF70 | SHA256:A2679D717DB07F43D81F895E508520E01CD0262F1BE5870333D12CE71FE02DB4 | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\wdscsl.dll | executable | |
MD5:0B778AD42D5E17CE89936F6D4C42957D | SHA256:D5BCFDAB29EA1DEEA22679A4A4473A9CC84871A5D707C006EB99FACB4AF9081B | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\SetupCore.dll | executable | |
MD5:55A4344E76136460BE2C8547C38567B4 | SHA256:A9AC64EC515D04589DFC38B25D68D01F281BBB794D0DF9EC4205FE473703AEF5 | |||
| 6636 | windows.exe | C:\$Windows.~WS\Sources\SetupMgr.dll | executable | |
MD5:59D1A173F6B27A8A1CC367CA9FF6E560 | SHA256:45C2EE2387026A50F0C6B9C9119F39B6D2B6505312DBDF352399FD41E8DEB78F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6880 | svchost.exe | GET | — | 217.20.57.40:80 | http://dl.delivery.mp.microsoft.com/filestreamingservice/files/f7d48c2e-eb2c-4f13-97e1-45a08c90bcfe/19045.3803.231204-0204.22h2_release_svc_refresh_CLIENTCONSUMER_RET_x64FRE_en-us.esd | unknown | — | — | whitelisted |
— | — | GET | 206 | 184.30.21.171:443 | https://download.microsoft.com/download/7/9/c/79cbc22a-0eea-4a0d-89c0-054a1b3aa8e0/products.cab | unknown | — | — | unknown |
— | — | GET | 302 | 184.30.21.171:443 | https://go.microsoft.com/fwlink/?LinkId=841361 | unknown | — | — | unknown |
— | — | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v2.0/WSD/Setup360?os=windows&osver=10.0.19041.4046.amd64fre.vb_release.191206-1406&scenarioId=7&platformEdition=Professional&platformInstallationType=Client&sku=48&deviceId=%7BBAD99146-31D3-4EC6-A1A4-BE76F32BA5D4%7D&appver=10.0.19041.572&appBuildLab=vb_release_svc_prod1 | unknown | binary | 66 b | unknown |
6880 | svchost.exe | HEAD | 200 | 217.20.57.40:80 | http://dl.delivery.mp.microsoft.com/filestreamingservice/files/f7d48c2e-eb2c-4f13-97e1-45a08c90bcfe/19045.3803.231204-0204.22h2_release_svc_refresh_CLIENTCONSUMER_RET_x64FRE_en-us.esd | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4664 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6748 | SetupHost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4664 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6748 | SetupHost.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
dl.delivery.mp.microsoft.com |
| whitelisted |