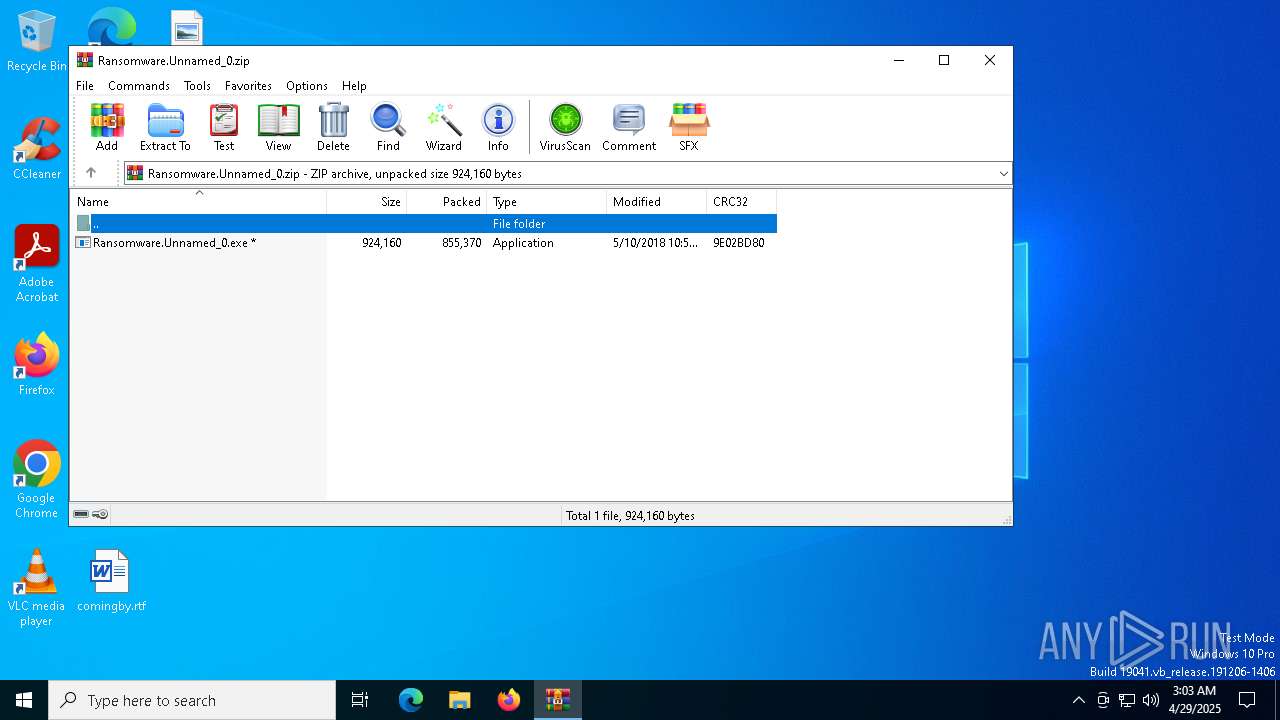
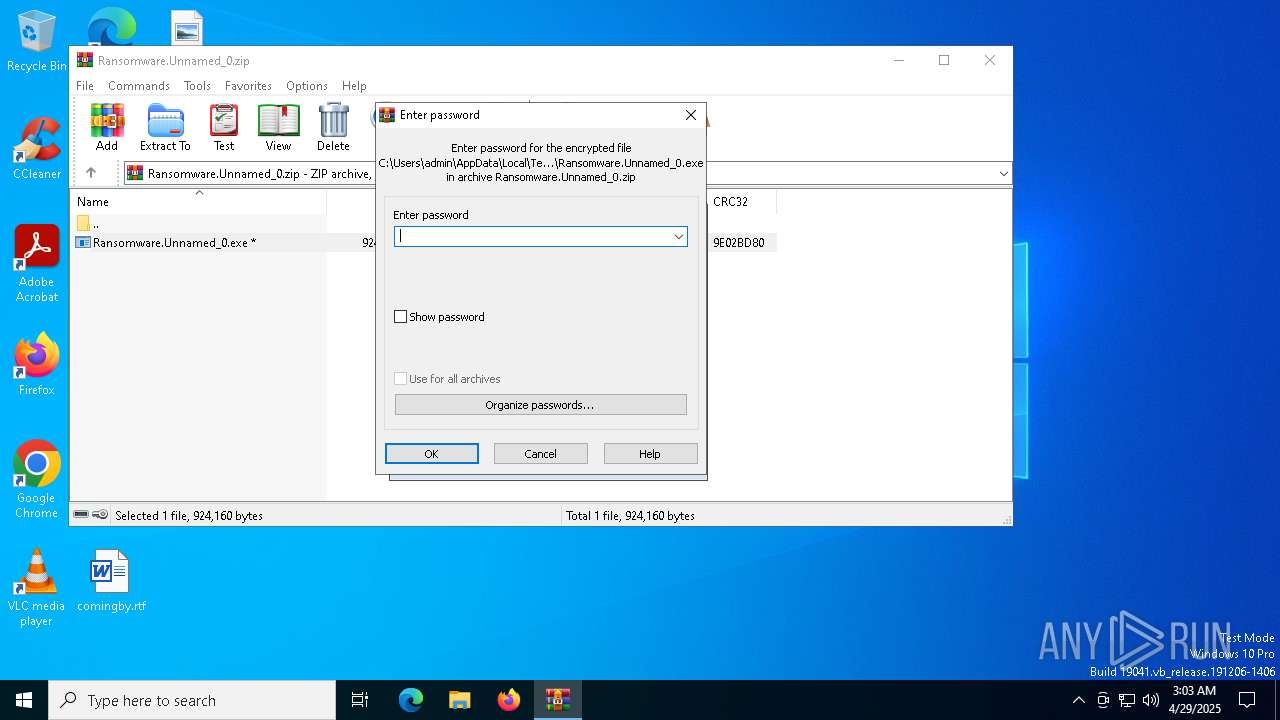
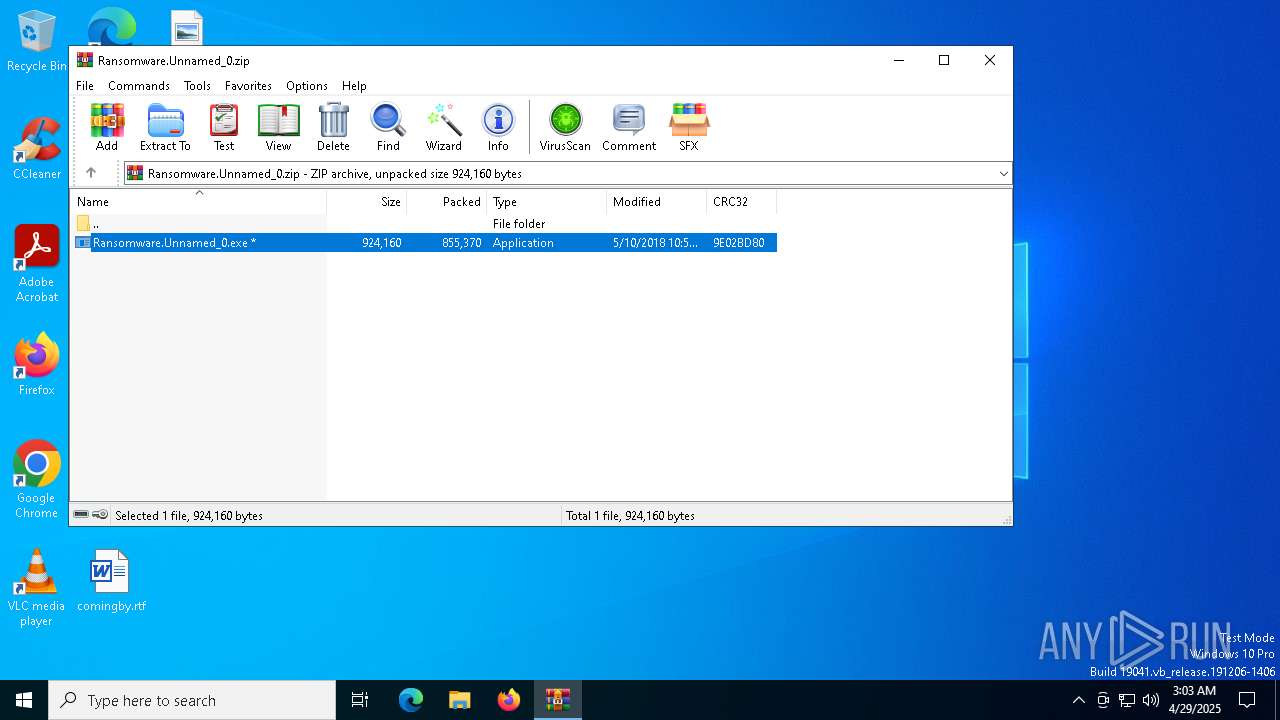
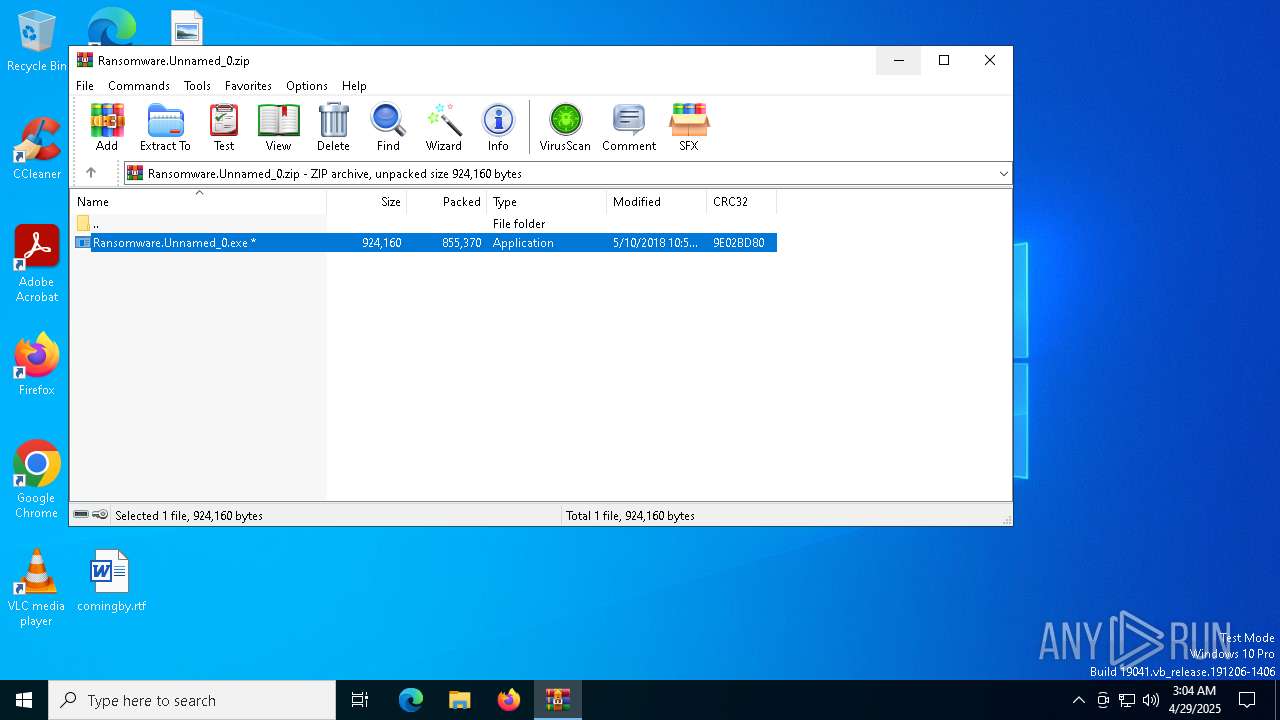
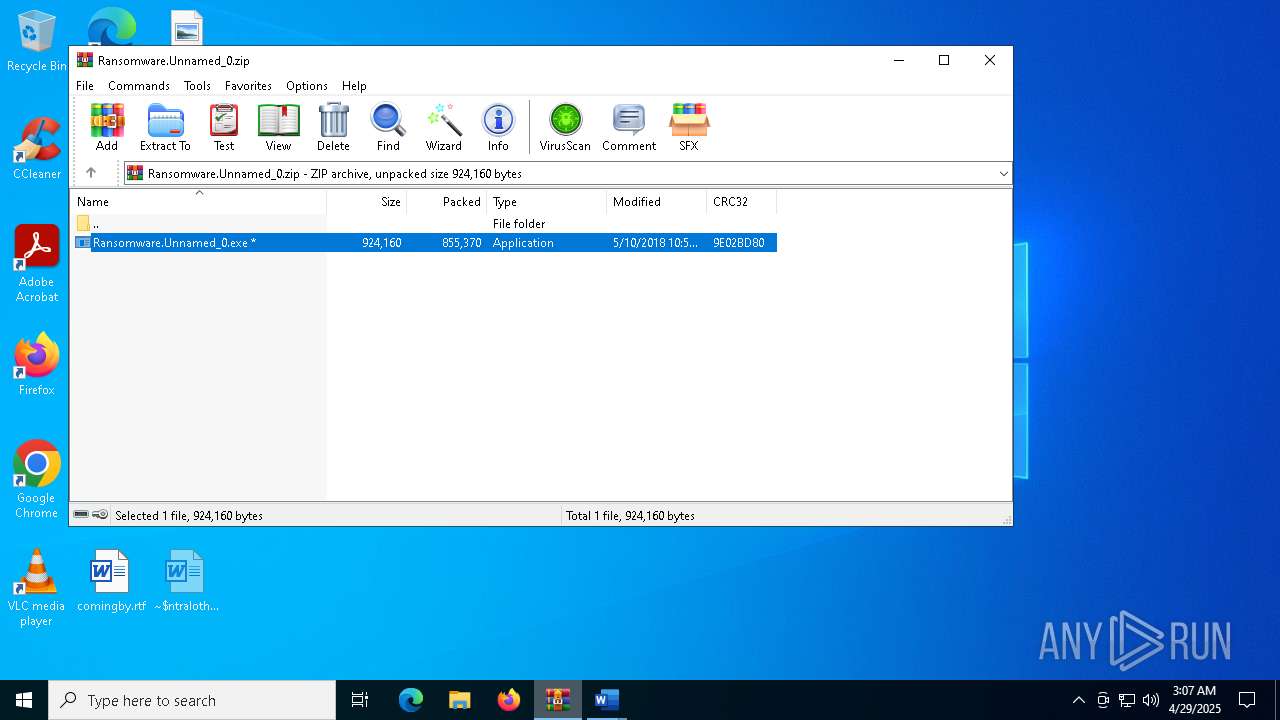
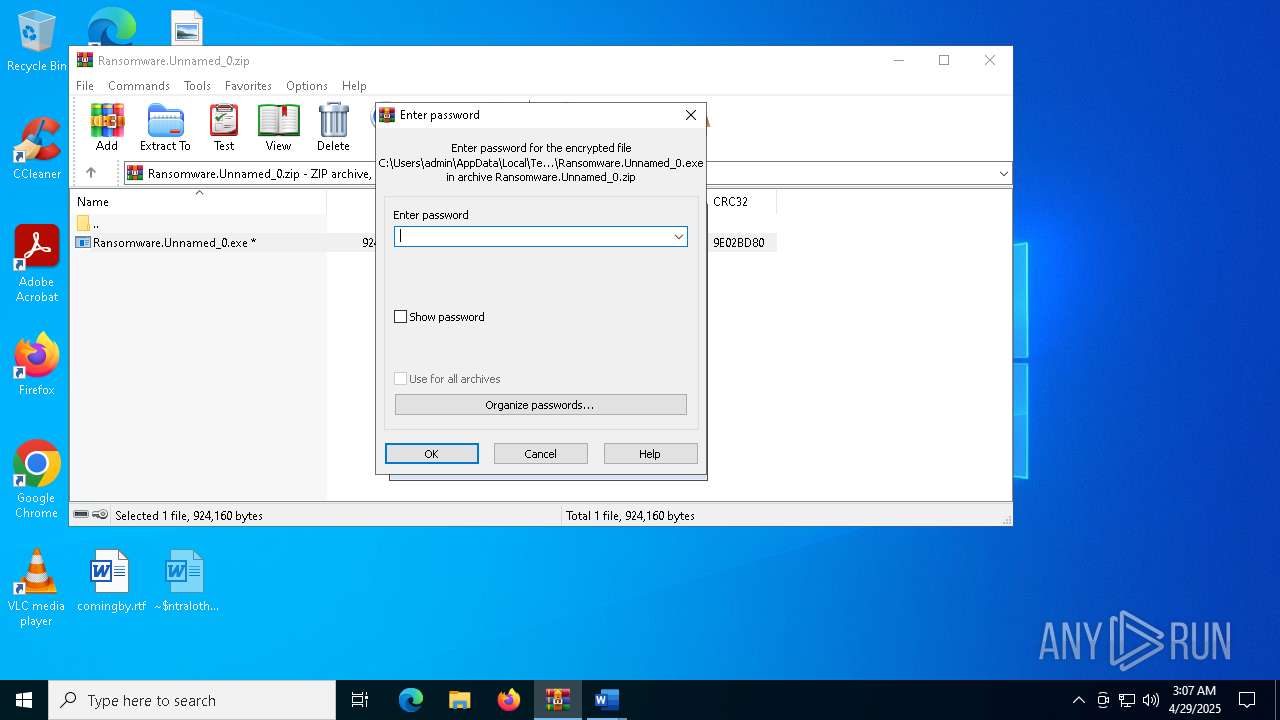
| File name: | Ransomware.Unnamed_0.zip |
| Full analysis: | https://app.any.run/tasks/bab8b069-3411-4a86-b28e-3b9b51d104a1 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 03:03:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
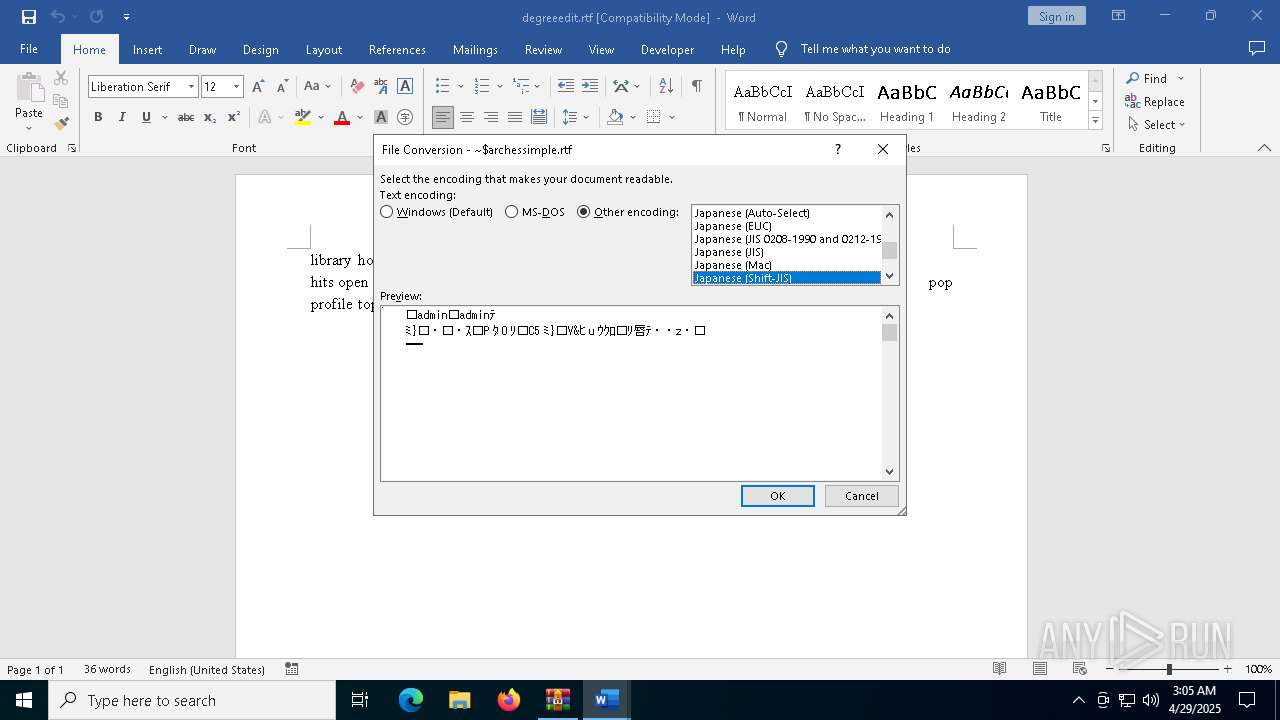
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | ABC651B27B067FB13CB11E00D33E5226 |
| SHA1: | 1869459025FCF845B90912236AF43A5D8D0F14DD |
| SHA256: | 690339E6D19DA0B5C63406D68484A4984736F6C7159235AFD9EEB2AE00CAFC36 |
| SSDEEP: | 12288:9nmNxspjOW6b5EVZTf2qDByG/WNGeWnwnpiVdnBQzXwBdn+TMLCAZn23dr+/TaNT:MNO1OnbElqCnwni7cXo+ECYnq2Jd4l |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4448)
Starts Visual C# compiler
- Ransomware.Unnamed_0.exe (PID: 7152)
- Ransomware.Unnamed_0.exe (PID: 4896)
Create files in the Startup directory
- Ransomware.Unnamed_0.exe (PID: 7152)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4448)
Uses .NET C# to load dll
- Ransomware.Unnamed_0.exe (PID: 7152)
- Ransomware.Unnamed_0.exe (PID: 4896)
Executable content was dropped or overwritten
- csc.exe (PID: 3180)
- Ransomware.Unnamed_0.exe (PID: 7152)
- csc.exe (PID: 1616)
The process executes VB scripts
- Ransomware.Unnamed_0.exe (PID: 7152)
- Ransomware.Unnamed_0.exe (PID: 4896)
Start notepad (likely ransomware note)
- vbc.exe (PID: 4724)
- vbc.exe (PID: 5044)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4448)
Reads the computer name
- Ransomware.Unnamed_0.exe (PID: 7152)
Checks supported languages
- Ransomware.Unnamed_0.exe (PID: 7152)
- csc.exe (PID: 3180)
- cvtres.exe (PID: 5064)
- vbc.exe (PID: 4724)
Reads the machine GUID from the registry
- Ransomware.Unnamed_0.exe (PID: 7152)
- csc.exe (PID: 3180)
Create files in a temporary directory
- Ransomware.Unnamed_0.exe (PID: 7152)
- csc.exe (PID: 3180)
- cvtres.exe (PID: 5064)
Creates files or folders in the user directory
- Ransomware.Unnamed_0.exe (PID: 7152)
- vbc.exe (PID: 4724)
Manual execution by a user
- WINWORD.EXE (PID: 2552)
- WINWORD.EXE (PID: 5048)
- WINWORD.EXE (PID: 7000)
- WINWORD.EXE (PID: 5008)
- WINWORD.EXE (PID: 6728)
- WINWORD.EXE (PID: 4884)
- WINWORD.EXE (PID: 2148)
- WINWORD.EXE (PID: 3028)
- WINWORD.EXE (PID: 5400)
Checks proxy server information
- slui.exe (PID: 6416)
Reads the software policy settings
- slui.exe (PID: 6632)
- slui.exe (PID: 6416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:05:10 17:57:14 |
| ZipCRC: | 0x9e02bd80 |
| ZipCompressedSize: | 855370 |
| ZipUncompressedSize: | 924160 |
| ZipFileName: | Ransomware.Unnamed_0.exe |
Total processes
171
Monitored processes
26
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "9AFB8776-90A5-4EAE-8C0B-3DA4DD5C9DB6" "B7746D8D-949E-49BD-91DB-1F0F6E0AB0B3" "2552" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1616 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\j5gr5te2.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | Ransomware.Unnamed_0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\~$greeedit.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2416 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES394E.tmp" "c:\Users\admin\AppData\Local\Temp\CSC97BC2098753C457A9E3ACDE1ED59F9E.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\centralotherwise.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\~$archessimple.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3180 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\3nm3eeqo.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | Ransomware.Unnamed_0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4448 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Ransomware.Unnamed_0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4724 | "C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | Ransomware.Unnamed_0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 3221225477 Version: 8.0.50727.9149 Modules
| |||||||||||||||
Total events
26 596
Read events
25 843
Write events
676
Delete events
77
Modification events
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.Unnamed_0.zip | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2552) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
Executable files
39
Suspicious files
171
Text files
23
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4448.13008\Ransomware.Unnamed_0.exe | executable | |
MD5:96AFC9CDEF3C623E0C5420E339C57283 | SHA256:517AC5506A5488A1193686F66CB57AD3288C2258C510004EDB2F361B674526CC | |||
| 7152 | Ransomware.Unnamed_0.exe | C:\Users\admin\AppData\Local\Temp\3nm3eeqo.0.cs | text | |
MD5:BE0C48FC5057A467514EEC58F1B1264B | SHA256:8685FC1EF0FF239F59289B26D9AA7134998F4CC4A15B22C9A8922C071BB32639 | |||
| 3180 | csc.exe | C:\Users\admin\AppData\Local\Temp\3nm3eeqo.pdb | binary | |
MD5:F0F433C9638FEF723D8D3B09B4534786 | SHA256:13F3BB18C3ACBD35C45D4B78F85D0947B74A5E6E3C43F3B7B17FBF15BEA6A368 | |||
| 5064 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESFE86.tmp | o | |
MD5:E33FD54F13511F586528D60DBBC2062C | SHA256:D046ACC61AB76F30B3E555057CDBBE4DA73D8752016827643B03C9D02D55E8FA | |||
| 3180 | csc.exe | C:\Users\admin\AppData\Local\Temp\3nm3eeqo.dll | executable | |
MD5:9F0CF94D2E0F38160AA4875ADFA5A921 | SHA256:CE7829CD7507C4AB039910FDB18A9EB8154081EC8B90F7334A4AD925136547D9 | |||
| 4724 | vbc.exe | C:\Users\admin\AppData\Local\JesYXqkYNx\cfgi | binary | |
MD5:AA5F6CF234B17E2886FE3E2401144756 | SHA256:AA70A43127E83304881487A45D9496EFCE45B8D0FA7CB3D52EF647A0D282EA39 | |||
| 4724 | vbc.exe | C:\Users\admin\AppData\Local\JesYXqkYNx\cfg | binary | |
MD5:560E63AD721FF461B61A43CFC54EF909 | SHA256:0C5FC323873FBE693C1FF860282F035AD447050F8EC37FF2E662D087A949DFC9 | |||
| 2552 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:B5D6E2CAAB3D9016CF913F9B303B5B00 | SHA256:C9184B20185770299C3122DE00EF7AC2A13A3AA9159AD8644CCFB14E92A1BB0B | |||
| 2552 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:9D4951F94104C737606C5993B9F92208 | SHA256:E1831B871A26E8476AB504757C9F50632488C08704DF99C6BD654F1FCA94878C | |||
| 2552 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:DCC5748001664E2EBE51F1B8F5AA4186 | SHA256:71B031EF6070AB1653520C823E5D9392D08B13F3DB3366DBA44A301F0E429062 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
69
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2552 | WINWORD.EXE | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
2552 | WINWORD.EXE | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
2092 | backgroundTaskHost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5428 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5428 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2552 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2552 | WINWORD.EXE | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5428 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |