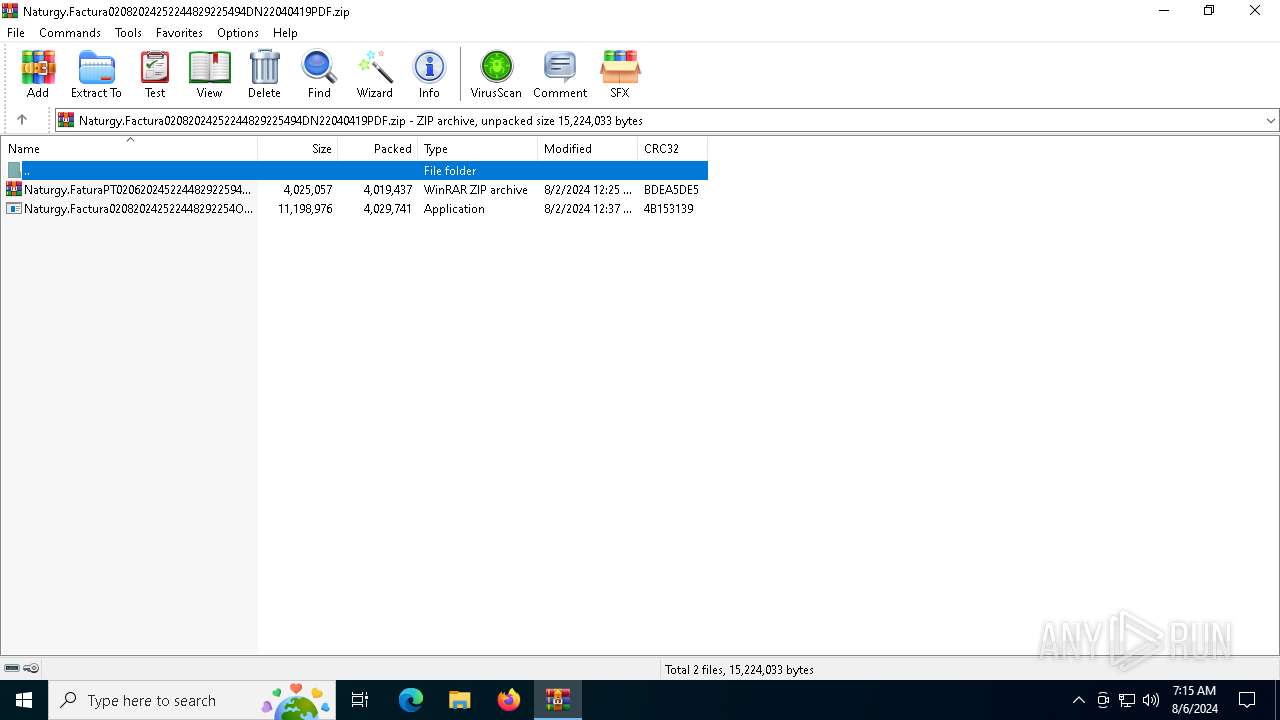
| download: | /dl/download/00015d58-b682-4e0c-afb2-055cd15cece4/Naturgy.Factura02082024252244829225494DN22040419PDF.zip |
| Full analysis: | https://app.any.run/tasks/0d31f3d6-1e30-4e76-9ef3-fb9ad9581f47 |
| Verdict: | Malicious activity |
| Analysis date: | August 06, 2024, 07:15:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C26CD14F500386764CDDF3252EA15132 |
| SHA1: | 87D3BD7F1CBD5D8426410DAC6E88E75E7D90AAE5 |
| SHA256: | 68FB11E840EF29A833A361270633A806C7068DB72A094C9A2564938B96684314 |
| SSDEEP: | 98304:m2AQcCqsuNTbePQwE/P5hQMjcSYHXLlAYCf0hAhJwoJCNGlQi7hc1//DRtu2tVlR:XdsGtF/ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6564)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Scans artifacts that could help determine the target
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Changes the autorun value in the registry
- zanhh.exe (PID: 6436)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6564)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Checks Windows Trust Settings
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Executable content was dropped or overwritten
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Reads the date of Windows installation
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 6232)
Reads Internet Explorer settings
- mmc.exe (PID: 6232)
INFO
Checks proxy server information
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
- mmc.exe (PID: 6232)
Reads the machine GUID from the registry
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Creates files or folders in the user directory
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
- mmc.exe (PID: 6232)
Reads the software policy settings
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Reads the computer name
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6220)
- zanhh.exe (PID: 6436)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 2580)
- TextInputHost.exe (PID: 6240)
Reads Environment values
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6220)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 2580)
- zanhh.exe (PID: 6436)
Checks supported languages
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6220)
- zanhh.exe (PID: 6436)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 2580)
- TextInputHost.exe (PID: 6240)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6564)
Manual execution by a user
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6220)
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 2580)
- mmc.exe (PID: 6184)
- mmc.exe (PID: 6232)
Process checks computer location settings
- Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe (PID: 6148)
Reads security settings of Internet Explorer
- mmc.exe (PID: 6232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:02 09:37:42 |
| ZipCRC: | 0x4b153139 |
| ZipCompressedSize: | 4029741 |
| ZipUncompressedSize: | 11198976 |
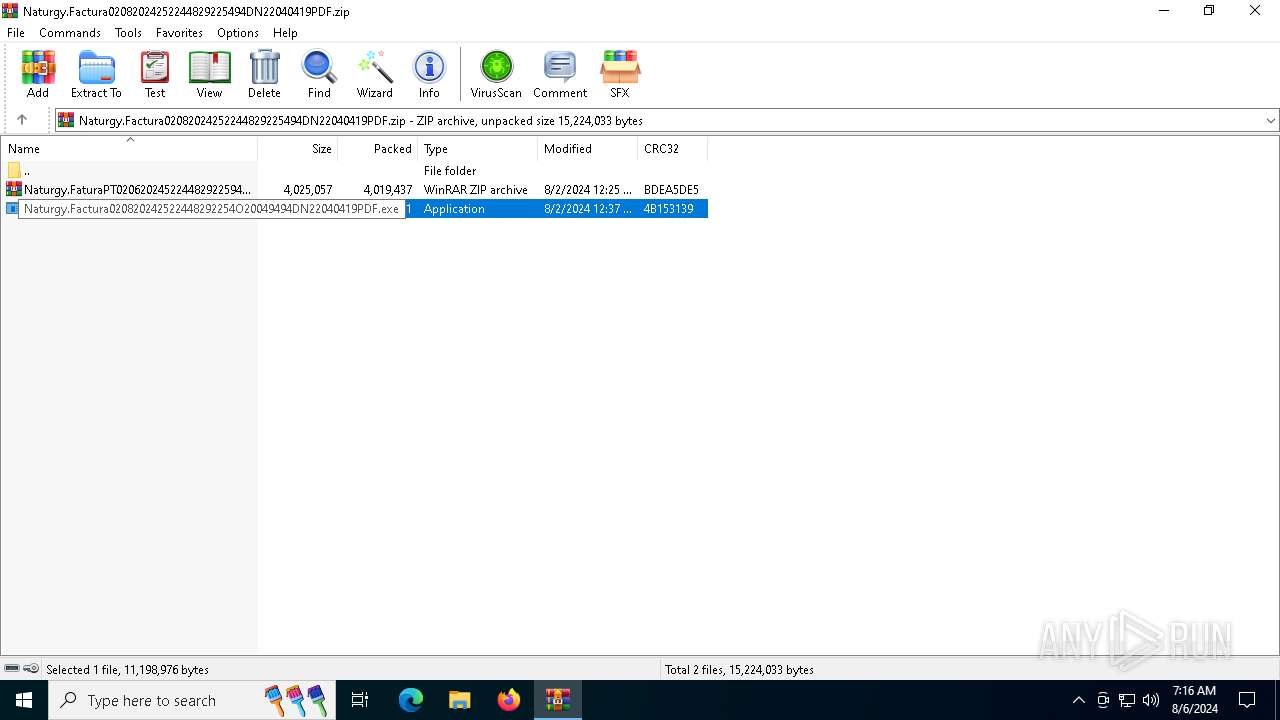
| ZipFileName: | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe |
Total processes
142
Monitored processes
9
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\Desktop\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe" | C:\Users\admin\Desktop\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: HUNHHGSD87484985 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6148 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.37960\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.37960\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: HUNHHGSD87484985 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6184 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\services.msc" | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6220 | "C:\Users\admin\Desktop\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe" | C:\Users\admin\Desktop\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: HUNHHGSD87484985 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6232 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\services.msc" | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
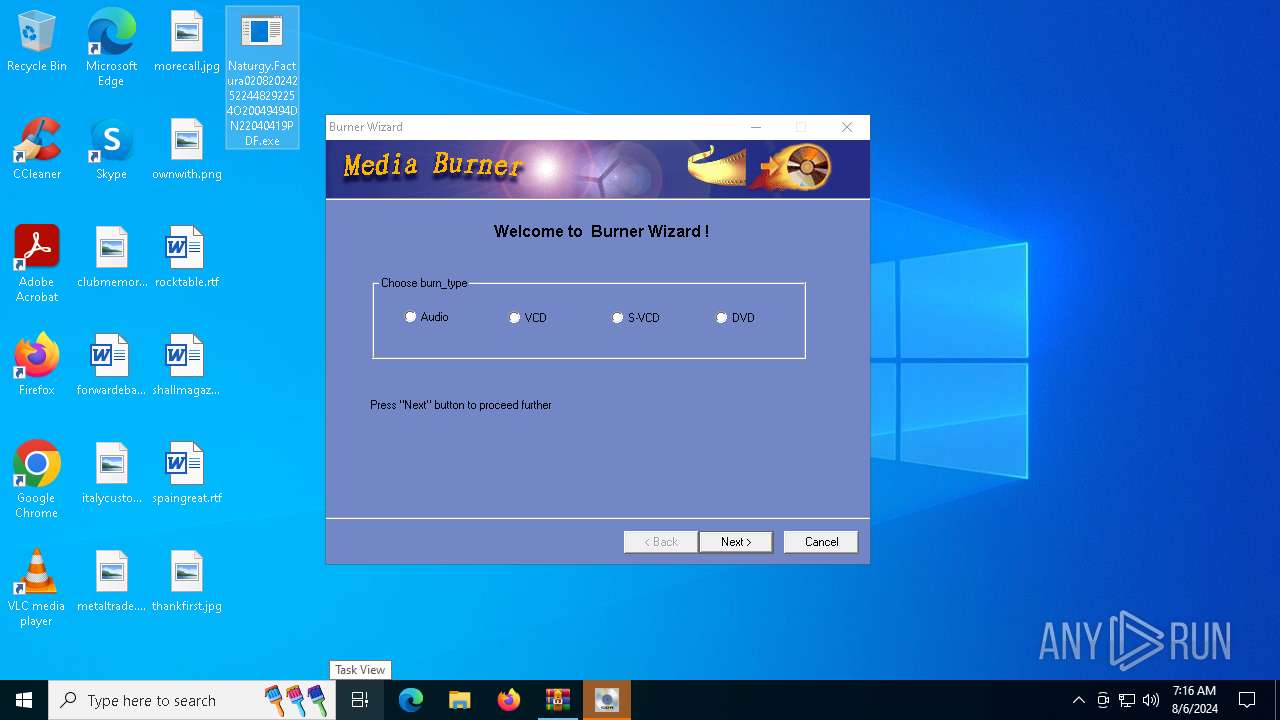
| 6436 | "C:\Nvholdnow\zanhh.exe" | C:\Nvholdnow\zanhh.exe | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | ||||||||||||
User: admin Company: iTinySoft Integrity Level: MEDIUM Description: Media Burner Version: 1.0.0.1 Modules
| |||||||||||||||
| 6564 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Naturgy.Factura02082024252244829225494DN22040419PDF.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
24 382
Read events
24 342
Write events
40
Delete events
0
Modification events
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Naturgy.Factura02082024252244829225494DN22040419PDF.zip | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\24[1].zip | — | |
MD5:— | SHA256:— | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Nvholdnow\20240806071611_333080.zip | — | |
MD5:— | SHA256:— | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Nvholdnow\vcen.dll | — | |
MD5:— | SHA256:— | |||
| 6564 | WinRAR.exe | C:\Users\admin\Desktop\Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | executable | |
MD5:89E23114C4C8241F363F83B059F046AF | SHA256:A75BEAA2D722E5084A465216494B082EFB5C95D75D6F106D2627E368AFC38F18 | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Nvholdnow\dvdau.dll | executable | |
MD5:EC13C0CA17FF65CF05C04B86A640072A | SHA256:9F649C766B673DDEE2EDEADF171EF7AFC87DFBAE2AE1B2835B5AF81EE389C707 | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\35DDEDF268117918D1D277A171D8DF7B_39B30C223D9DBB1BF84FABB17C3B3563 | binary | |
MD5:A395BB9B08981F4E23BB42E17787C0C6 | SHA256:F8ABB2C314A10365BB7AA03067A03865A310B64935DCD12D85C694CCF264C653 | |||
| 6564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.37960\Naturgy.FaturaPT020620245224482922594DN22040419PDF.zip | compressed | |
MD5:09B0C7EF2E411C0210DB0F33CAE7727A | SHA256:F828F9626A29EF6BAC2C75917B739051768EF3D26135D2FF27E4C6C568C44D75 | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:94C332CF13697F45EA00A88B81561FC6 | SHA256:8A285AE72147DBFCBCDA9D481FC6E3C396ACB499C8EBDFE3FB2377E2FC2313BF | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_39B30C223D9DBB1BF84FABB17C3B3563 | binary | |
MD5:F2EB9D978E2060AA9156B6C19D2C95D7 | SHA256:EA8914D36503E5182D4AF3954CBDFE63FE7BCDDEA2681B8D7BBAB8A0F800F176 | |||
| 6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:70DE7DF34CD73752DD88D8B757351262 | SHA256:BED967A149644D1AD6EAAEA7B05378E7893B9748B28791C93A8EC0B1D42A6628 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
53
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6872 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6920 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA5LESwT1wyG%2B8R6iu4iTyM%3D | unknown | — | — | whitelisted |
6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4788 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3044 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5336 | SearchApp.exe | 95.100.146.27:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5924 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5924 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO Public Cloud Domain in DNS Lookup (cld .pt) |
6148 | Naturgy.Factura020820242522448292254O20049494DN22040419PDF.exe | Potentially Bad Traffic | ET INFO Observed Public Cloud Domain (cld .pt in TLS SNI) |
Process | Message |
|---|---|
zanhh.exe |
StarBurn:StarBurn_UpStart(): Call is obsolete
|
zanhh.exe | StarBurn CD/DVD Burning, Grabbing and Mastering Toolkit for Windows 95/98/Me/NT/2000/XP/2003 Version 6.2.24 ( 0x20060410 )
Copyright (c) Rocket Division Software 2001-2006. All rights reserved.
|
zanhh.exe |
This PERSONAL copy of StarBurn should be used in personal or shareware projects only.
|
zanhh.exe |
License number: 64375825, licensed to 'wu_zhi_qiang' on Tue Jun 13 19:43:02 2006
|
zanhh.exe |
Please report all licensing violations to info@rocketdivision.com software piracy fighting team.
|
zanhh.exe |
StarWave Media Streaming Toolkit for Windows 95/98/Me/NT/2000/XP/2003 Version 6.2.24 ( 0x20060224 )
Copyright (c) Rocket Division Software 2001-2006. All rights reserved.
|