| File name: | sample.exe |
| Full analysis: | https://app.any.run/tasks/fd4de94a-758f-4b1e-9413-479a5351e82f |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 16:01:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B45F2BFE96D10FE21FE16CDA4E9C5EB |
| SHA1: | C2751E72BD5A8593F4EB4EBD000ACE791DB0A9C7 |
| SHA256: | 68ED565438E206E805F81980374E6439E6F4F60F63A3FCB6F0840C8A8DE189DA |
| SSDEEP: | 49152:KCd6LaUWF/9jKxuB6kXlLp4by6GkixB/dShTKlH8m2gkc8ApOhgbEOWI:KCMmFVjKITXxp4by6Pi7Y4SvgEjkr |
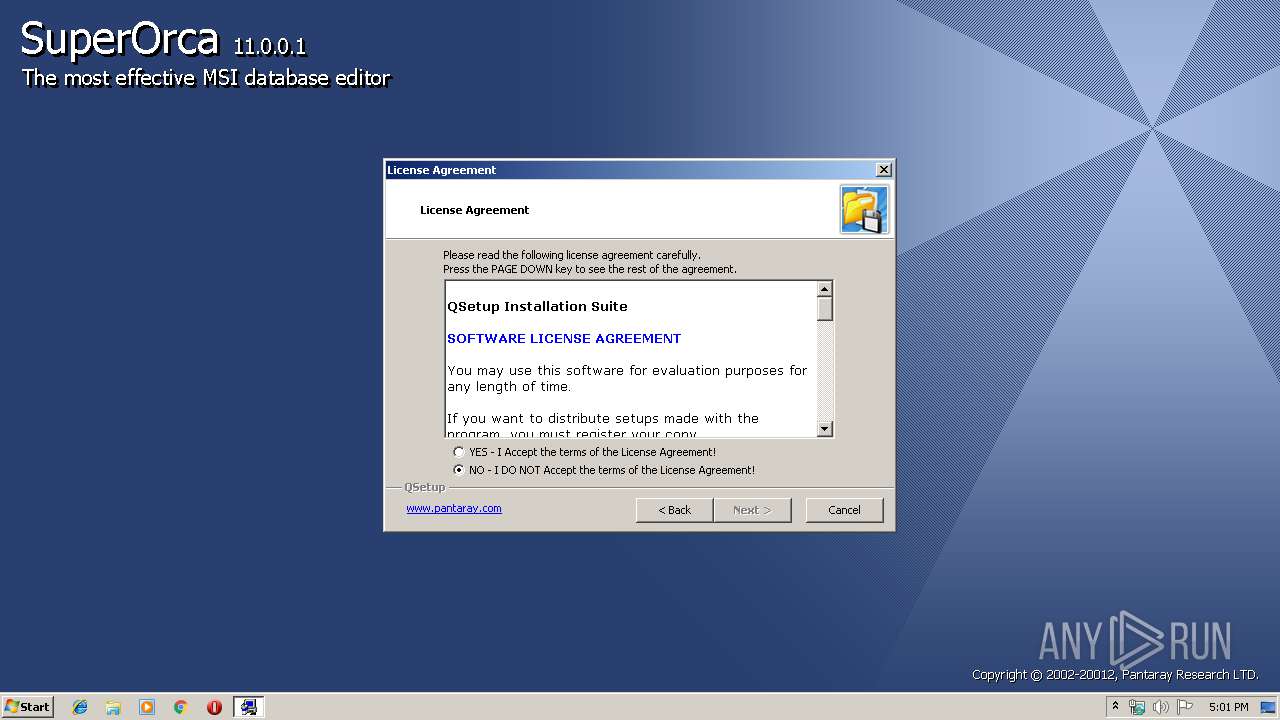
MALICIOUS
Application was dropped or rewritten from another process
- Engine.exe (PID: 2636)
- SuperOrca.exe (PID: 2832)
SUSPICIOUS
Executable content was dropped or overwritten
- sample.exe (PID: 3480)
- Engine.exe (PID: 2636)
Creates files in the program directory
- Engine.exe (PID: 2636)
Creates COM task schedule object
- Engine.exe (PID: 2636)
Creates a software uninstall entry
- Engine.exe (PID: 2636)
Creates files in the user directory
- Engine.exe (PID: 2636)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (49.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (16.2) |
| .scr | | | Windows screen saver (14.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 162816 |
| InitializedDataSize: | 31232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x28a6c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.0.1 |
| ProductVersionNumber: | 11.0.0.1 |
| FileFlagsMask: | 0x0002 |
| FileFlags: | Pre-release |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Pantaray Research Ltd. |
| FileDescription: | SuperOrca - Setup File |
| FileVersion: | 11.0.0.1 |
| InternalName: | SuperOrca |
| LegalCopyright: | Copyright © 2002-2008 Pantaray Research Ltd. |
| OriginalFileName: | SuperOrca.exe |
| ProductName: | SuperOrca |
| ProductVersion: | 11.0.0.1 |
Total processes
47
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2444 | C:\Windows\system32\cacls.exe "C:\Program Files\Common Files" /T /E /C /G Everyone:F | C:\Windows\system32\cacls.exe | — | Engine.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2636 | C:\Users\admin\AppData\Local\Temp\SETUP_34866\Engine.exe /TH_ID=_3496 /OriginExe="C:\Users\admin\AppData\Local\Temp\sample.exe" | C:\Users\admin\AppData\Local\Temp\SETUP_34866\Engine.exe | sample.exe | ||||||||||||
User: admin Company: Pantaray Research Ltd. Integrity Level: HIGH Description: Setup/Uninstall Engine Exit code: 0 Version: 11.0.0.1 Modules
| |||||||||||||||
| 2832 | "C:\Program Files\Pantaray\SuperOrca\SuperOrca.exe" | C:\Program Files\Pantaray\SuperOrca\SuperOrca.exe | — | Engine.exe | |||||||||||
User: admin Company: Pantaray Research Ltd. Integrity Level: HIGH Description: SuperOrca Exit code: 0 Version: 11.0.0.0 Modules
| |||||||||||||||
| 2888 | C:\Windows\system32\cacls.exe "C:\Program Files\Pantaray\SuperOrcaSetup_21233.exe" /E /C /G Everyone:F | C:\Windows\system32\cacls.exe | — | Engine.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\AppData\Local\Temp\sample.exe" | C:\Users\admin\AppData\Local\Temp\sample.exe | — | explorer.exe | |||||||||||
User: admin Company: Pantaray Research Ltd. Integrity Level: MEDIUM Description: SuperOrca - Setup File Exit code: 3221226540 Version: 11.0.0.1 Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\AppData\Local\Temp\sample.exe" | C:\Users\admin\AppData\Local\Temp\sample.exe | explorer.exe | ||||||||||||
User: admin Company: Pantaray Research Ltd. Integrity Level: HIGH Description: SuperOrca - Setup File Exit code: 0 Version: 11.0.0.1 Modules
| |||||||||||||||
| 3784 | C:\Windows\system32\cacls.exe "C:\Program Files\Pantaray" /T /E /C /G Everyone:F | C:\Windows\system32\cacls.exe | — | Engine.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3984 | C:\Windows\regedit.exe /S "C:\Users\admin\AppData\Local\Temp\SETUP_34866\evalcom2.reg" | C:\Windows\regedit.exe | — | Engine.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
255
Read events
218
Write events
37
Delete events
0
Modification events
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | DisplayName |
Value: SuperOrca | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | UnInstallString |
Value: "C:\Program Files\Pantaray\SuperOrcaSetup_21233.exe" | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | QuietUnInstallString |
Value: "C:\Program Files\Pantaray\SuperOrcaSetup_21233.exe" /silent | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | DisplayVersion |
Value: 11.0.0.1 | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | Publisher |
Value: Pantaray | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | Version |
Value: 184549376 | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | VersionMajor |
Value: 11 | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | VersionMinor |
Value: 0 | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | InstallLocation |
Value: "C:\Program Files\Pantaray" | |||
| (PID) Process: | (2636) Engine.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SuperOrca |
| Operation: | write | Name: | InstallDate |
Value: 20190515 | |||
Executable files
8
Suspicious files
2
Text files
119
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2636 | Engine.exe | C:\Program Files\Pantaray\SuperOrcaSetup_21233.txt | text | |
MD5:— | SHA256:— | |||
| 2636 | Engine.exe | C:\Program Files\Pantaray\SuperOrca\SuperOrca_Manual.pdf | ||
MD5:— | SHA256:— | |||
| 3480 | sample.exe | C:\Users\admin\AppData\Local\Temp\SETUP_34866\evalcom2.reg | text | |
MD5:— | SHA256:— | |||
| 3480 | sample.exe | C:\Users\admin\AppData\Local\Temp\SETUP_34866\LICENSE.RTF | text | |
MD5:— | SHA256:— | |||
| 2636 | Engine.exe | C:\Program Files\Pantaray\SuperOrcaSetup_21233.exe | executable | |
MD5:— | SHA256:— | |||
| 3480 | sample.exe | C:\Users\admin\AppData\Local\Temp\SETUP_34866\00003#SuperOrca_Manual.pdf | ||
MD5:— | SHA256:— | |||
| 3480 | sample.exe | C:\Users\admin\AppData\Local\Temp\SETUP_34866\Modern_Icon.bmp | image | |
MD5:1DD88F67F029710D5C5858A6293A93F1 | SHA256:B5DAD33CEB6EB1AC2A05FBDA76E29A73038403939218A88367925C3A20C05532 | |||
| 3480 | sample.exe | C:\Users\admin\AppData\Local\Temp\SETUP_34866\folder_blue_small.bmp | image | |
MD5:A14A183CE820E0ED7FE33A91A5E4B7DF | SHA256:38DC136C999991E17E9F1B8E151AF1A0B04E660371CE879DC20582BECCB35AD4 | |||
| 3480 | sample.exe | C:\Users\admin\AppData\Local\Temp\SETUP_34866\folder_blue_large.bmp | image | |
MD5:1C1C9CEEBF00CB863DA9787DA07404EC | SHA256:4F4B8717B45D7314100A7C3BCE5D4C6F98E56140F6BF696BEF1DE430F052B5A7 | |||
| 2636 | Engine.exe | C:\Program Files\Common Files\Microsoft Shared\MSI Tools\evalcom2.dll | executable | |
MD5:A599901D5148CD4D310C6A825F832616 | SHA256:3B4FE00F15C39CE4C80B2A1B29C04A28D8722BADC32ABAB4EC1C0A7D0E32D986 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report