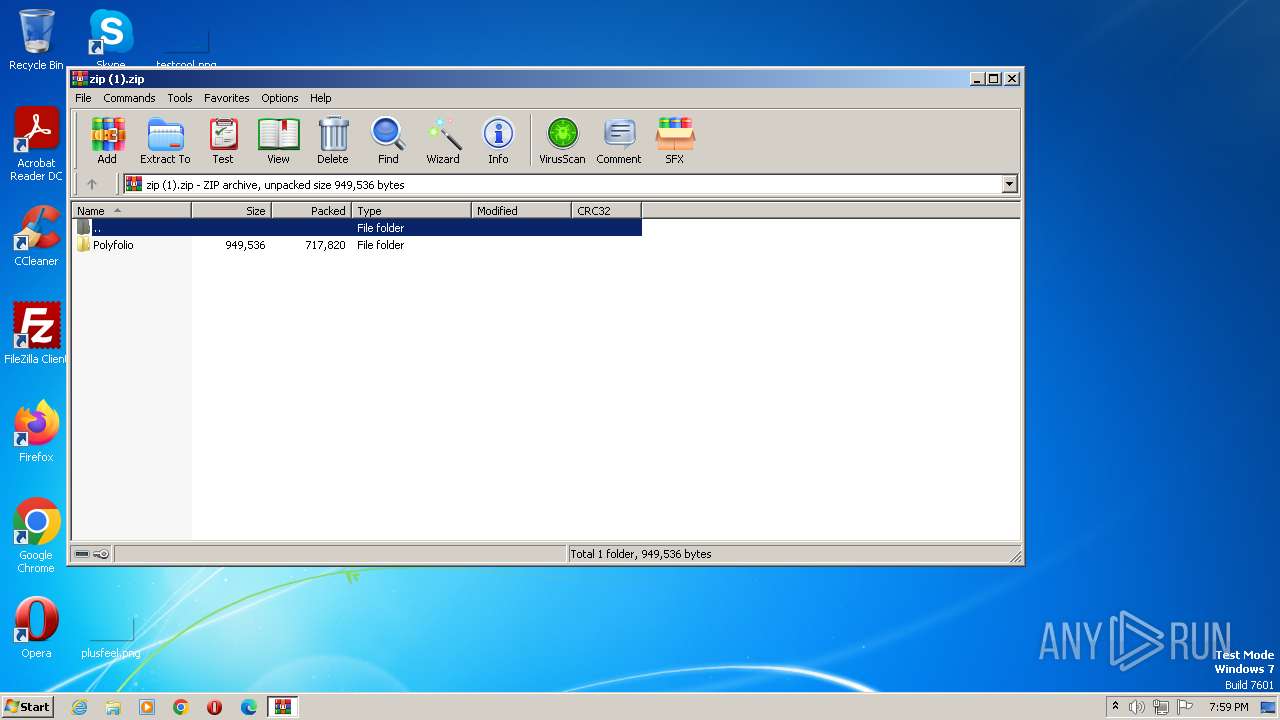
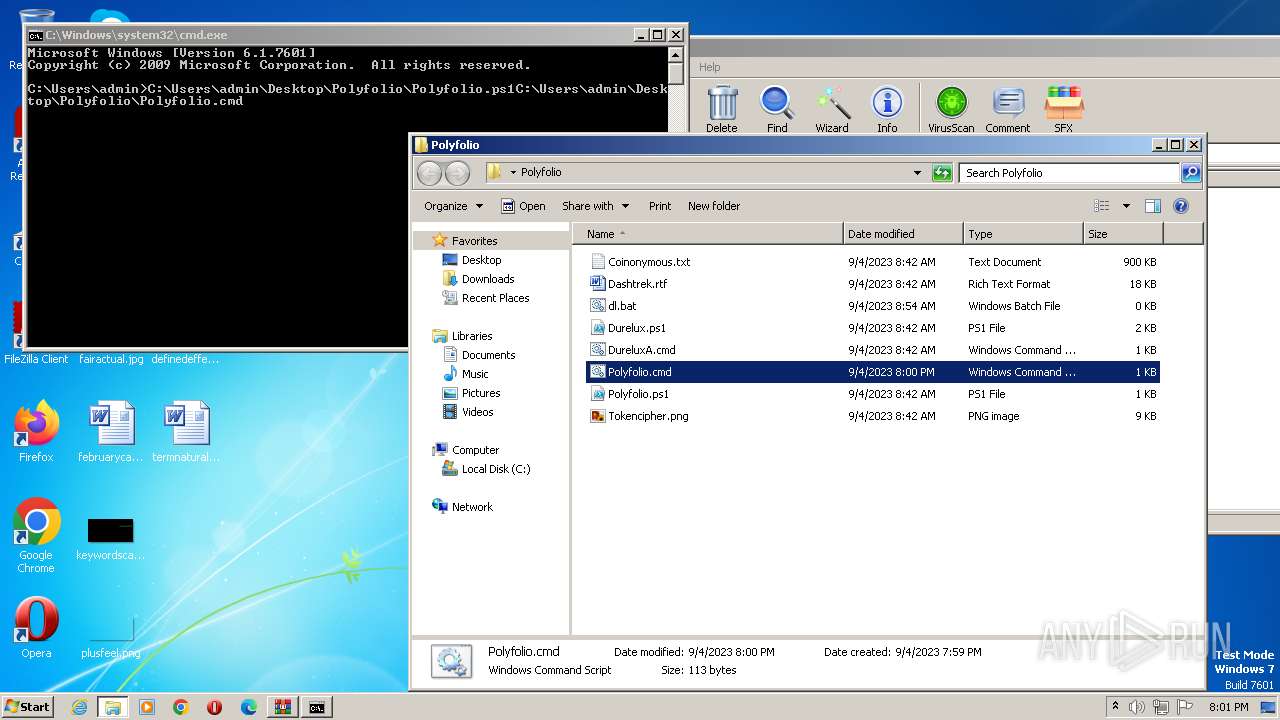
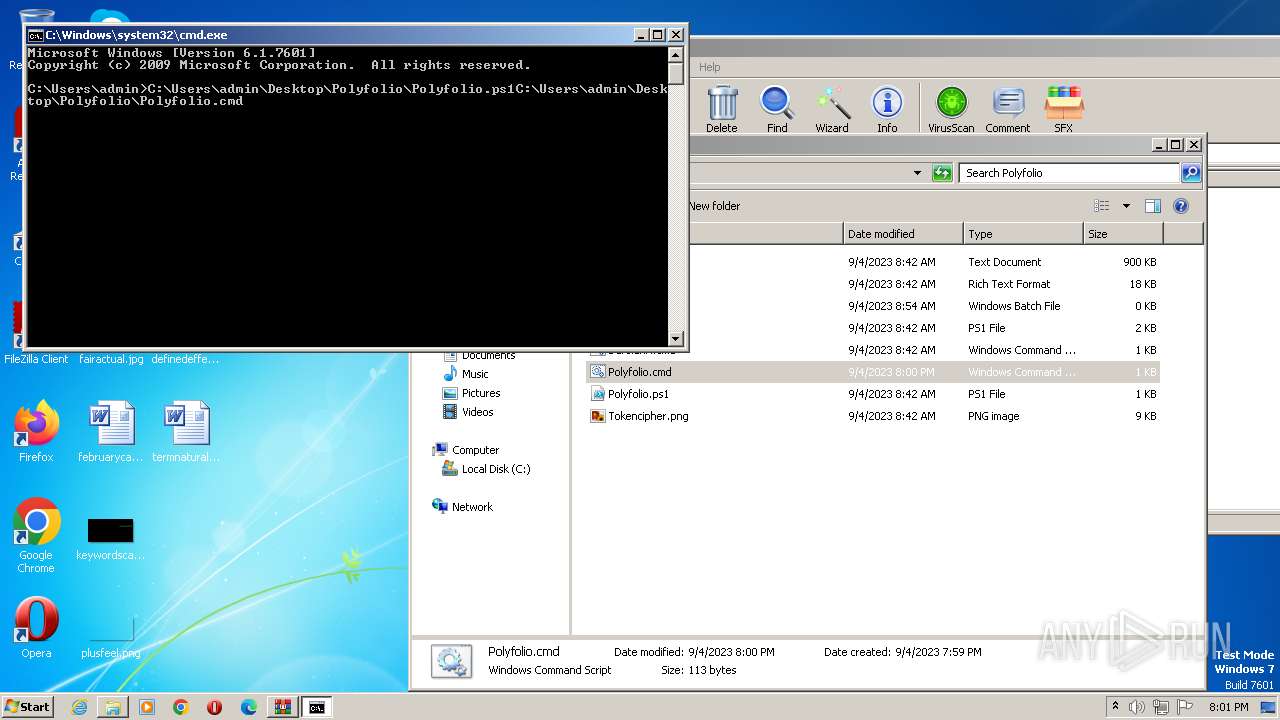
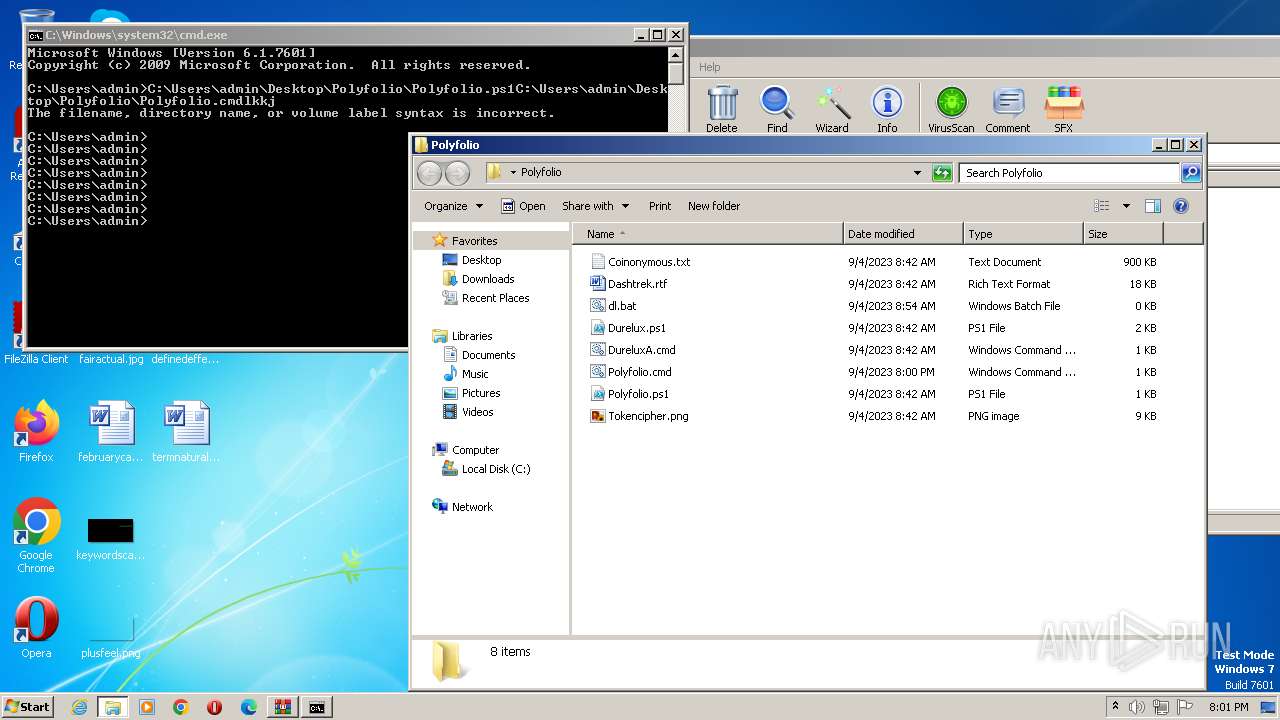
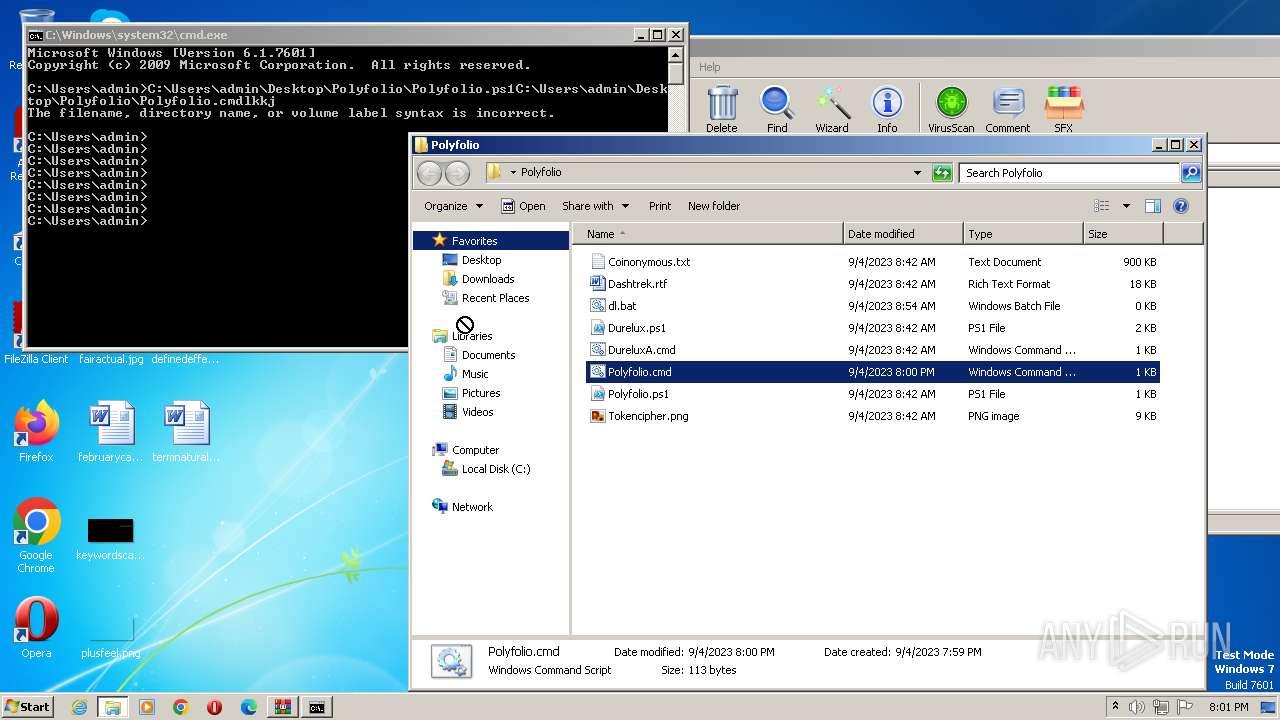
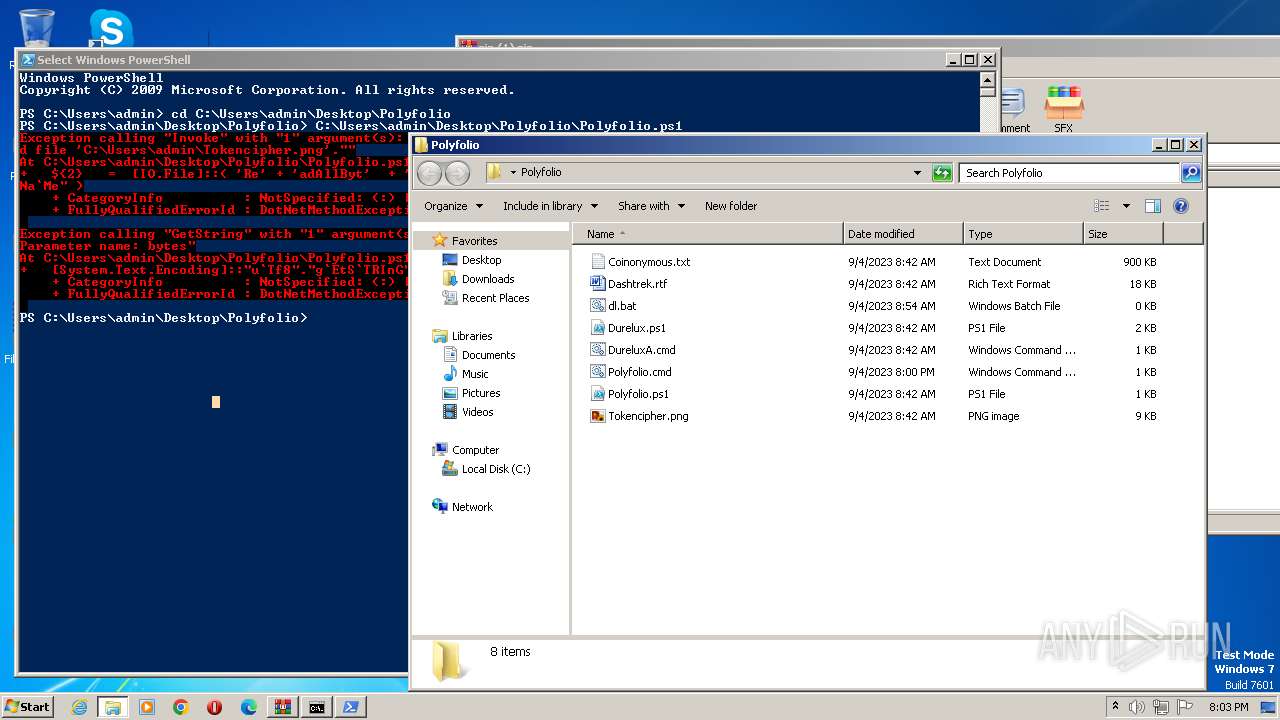
| File name: | zip (1).zip |
| Full analysis: | https://app.any.run/tasks/666c165e-fbef-4945-b5e6-f74c927a0cf1 |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2023, 18:58:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 7FCA24D8C1F25D77AD124CCF0A31DD02 |
| SHA1: | 7D9A0CBB0BA8F450D64756084DF5A44C3B7798B8 |
| SHA256: | 689C7C17DF219FB1B3E73CCC47184AAA4B1811C547C4263C3B6CA0AE8602E1CB |
| SSDEEP: | 12288:WQuEr43zhhHOsjScflG2Gi5asyLJQfxGnXfyC1np+7lQe+RZ:NuECnOILfJGGaNLFnXfyPQe+RZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
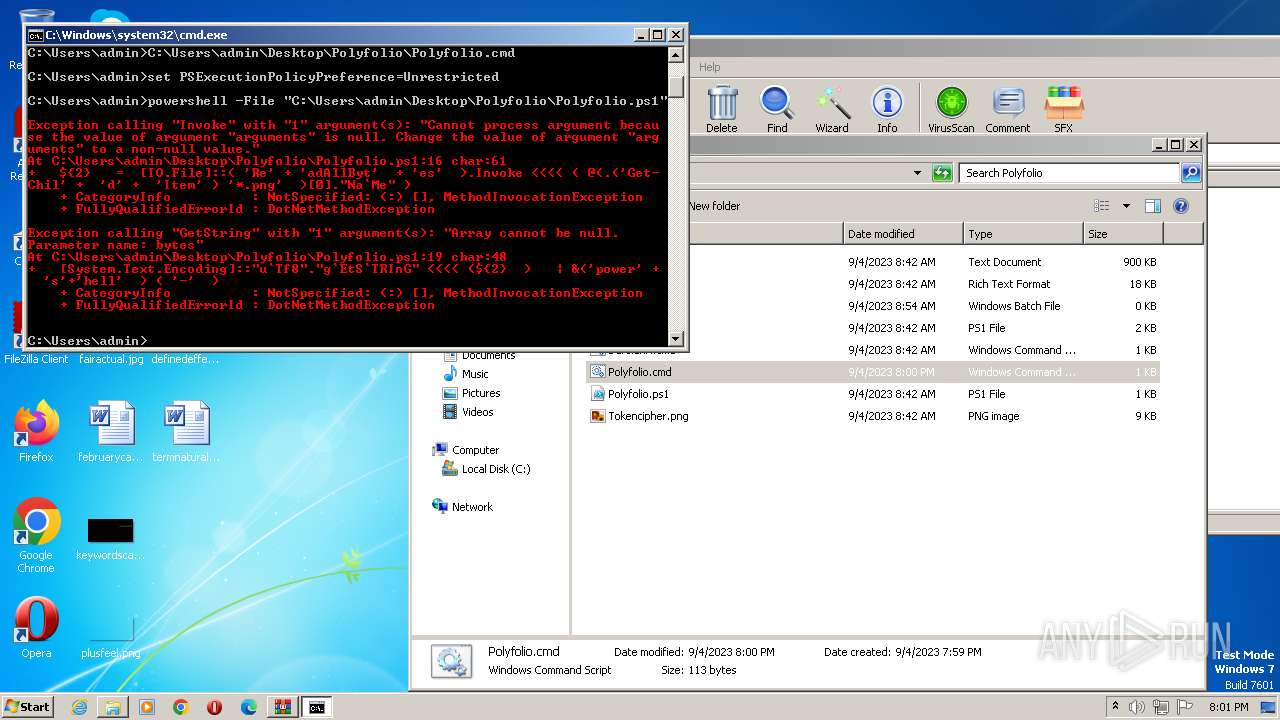
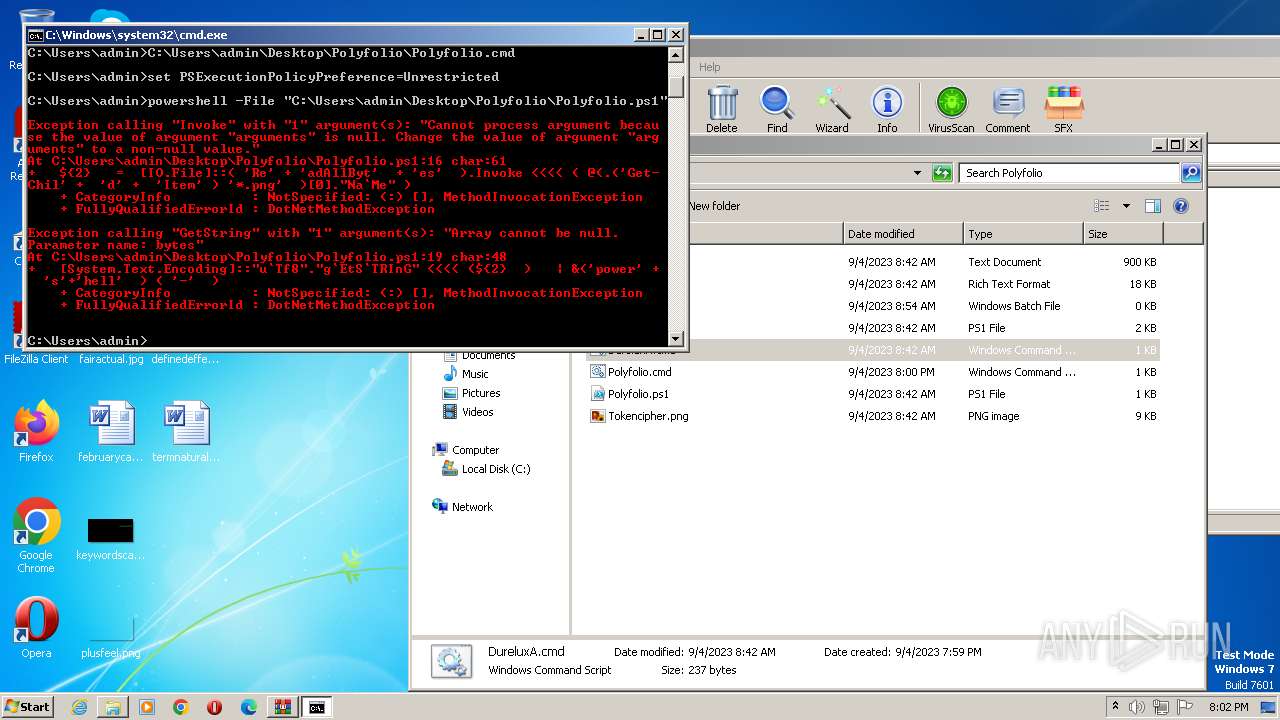
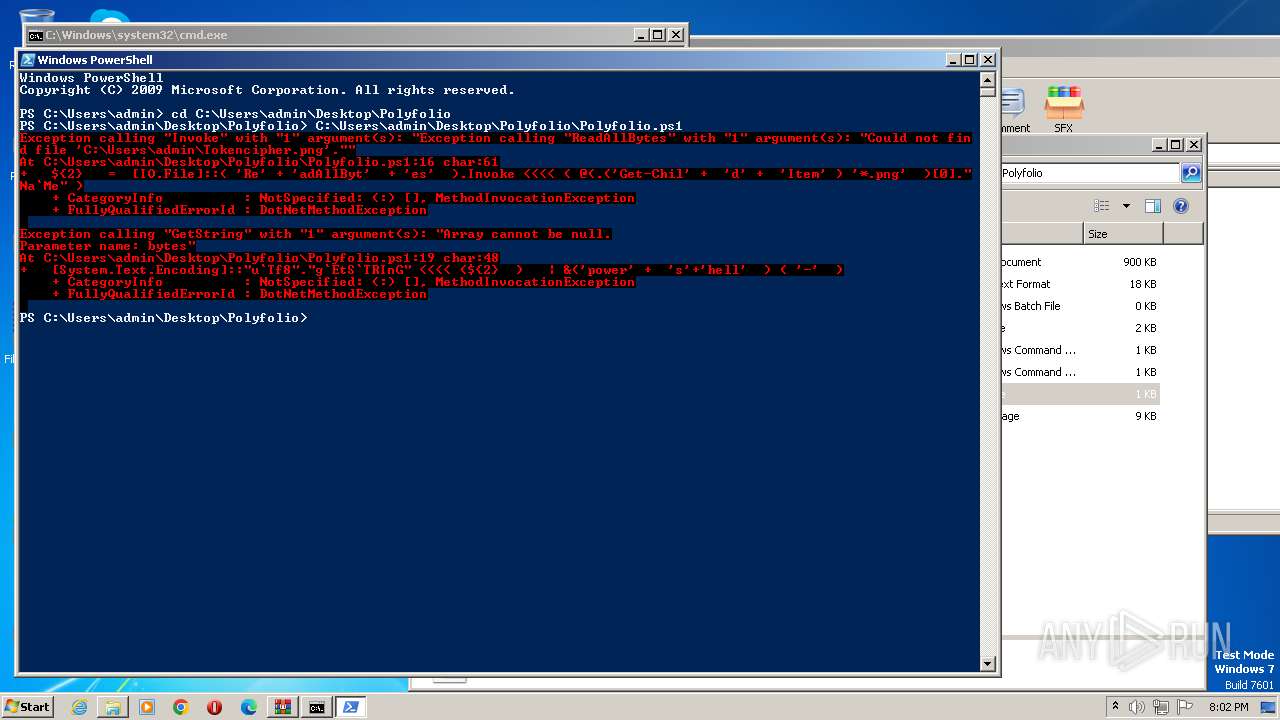
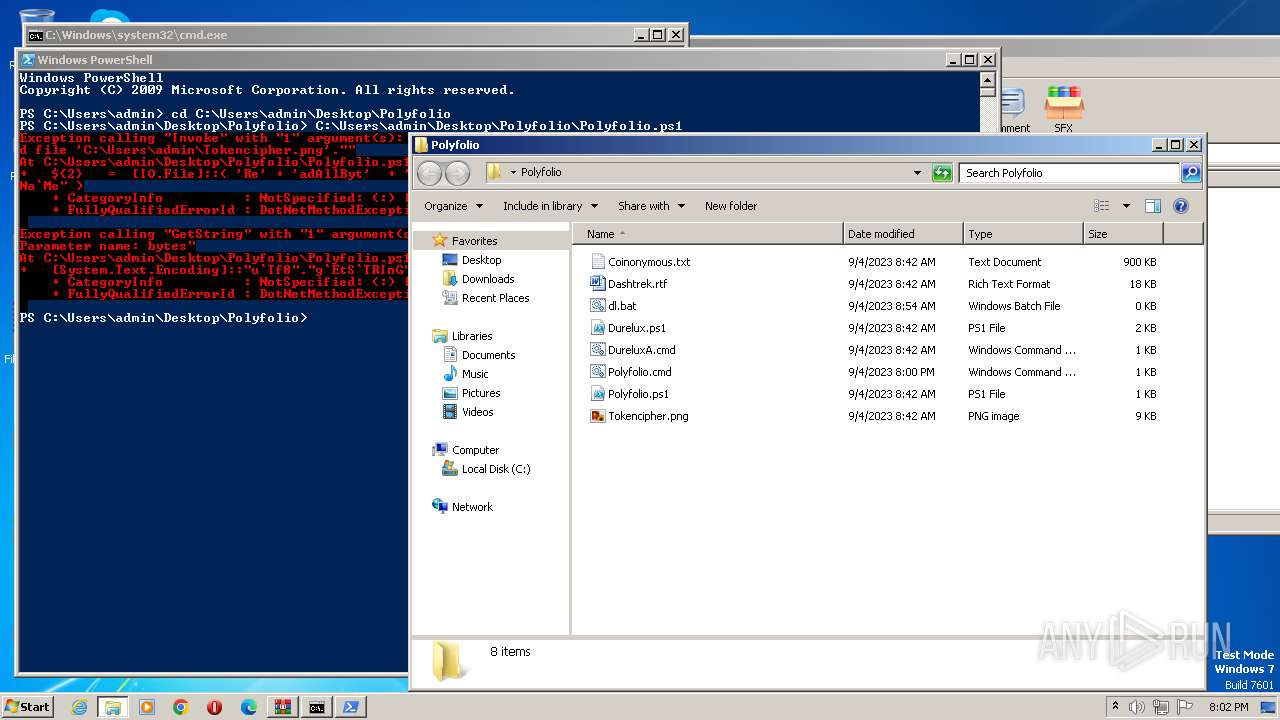
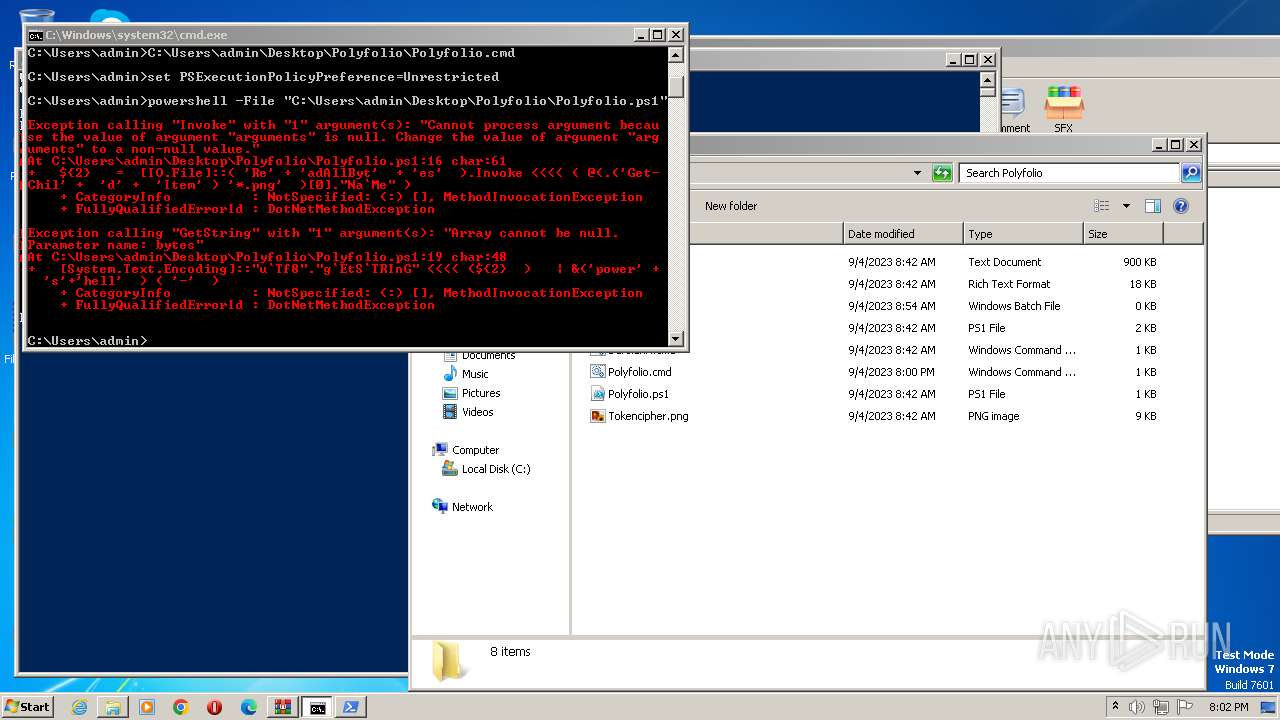
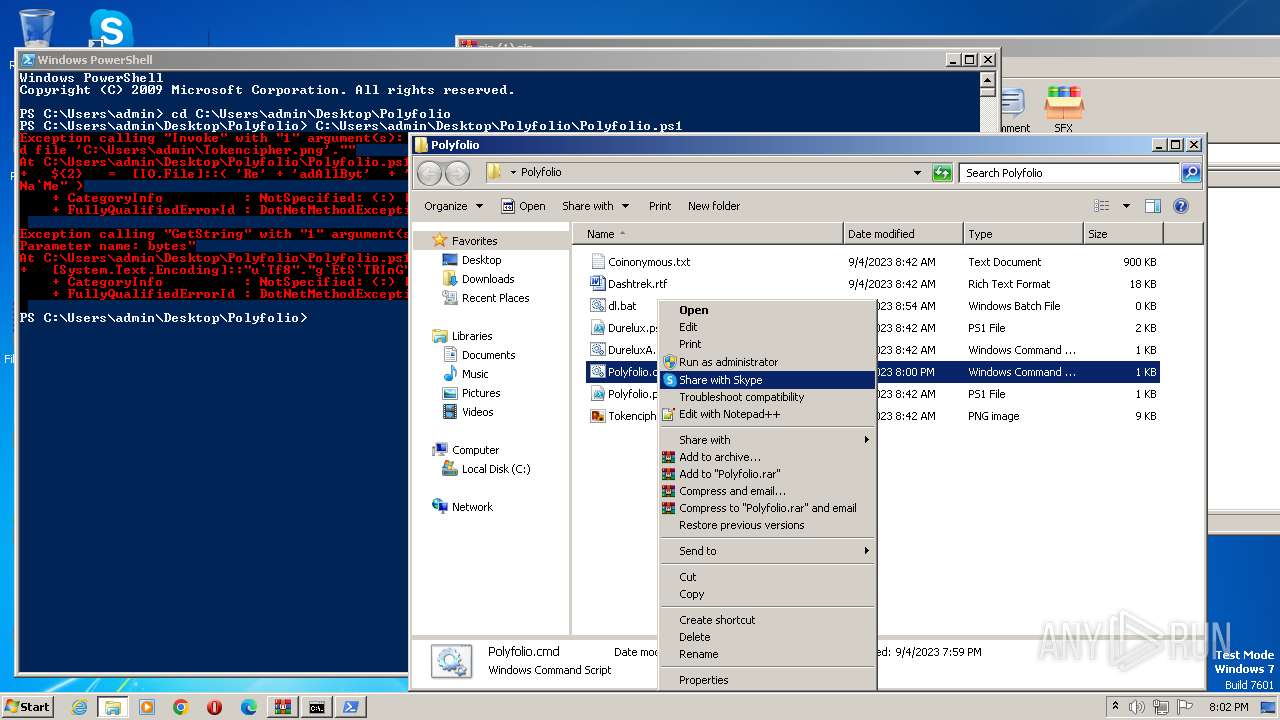
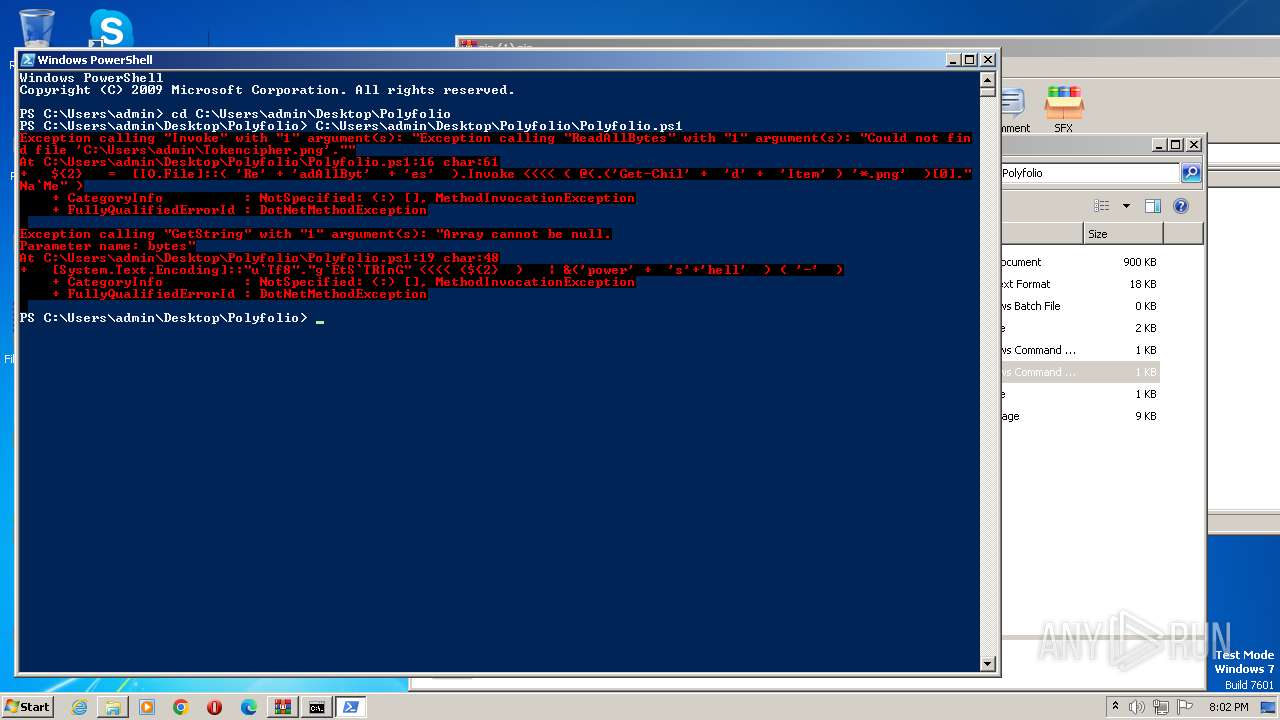
Powershell version downgrade attack
- powershell.exe (PID: 1864)
- powershell.exe (PID: 2668)
- powershell.exe (PID: 3860)
- powershell.exe (PID: 2384)
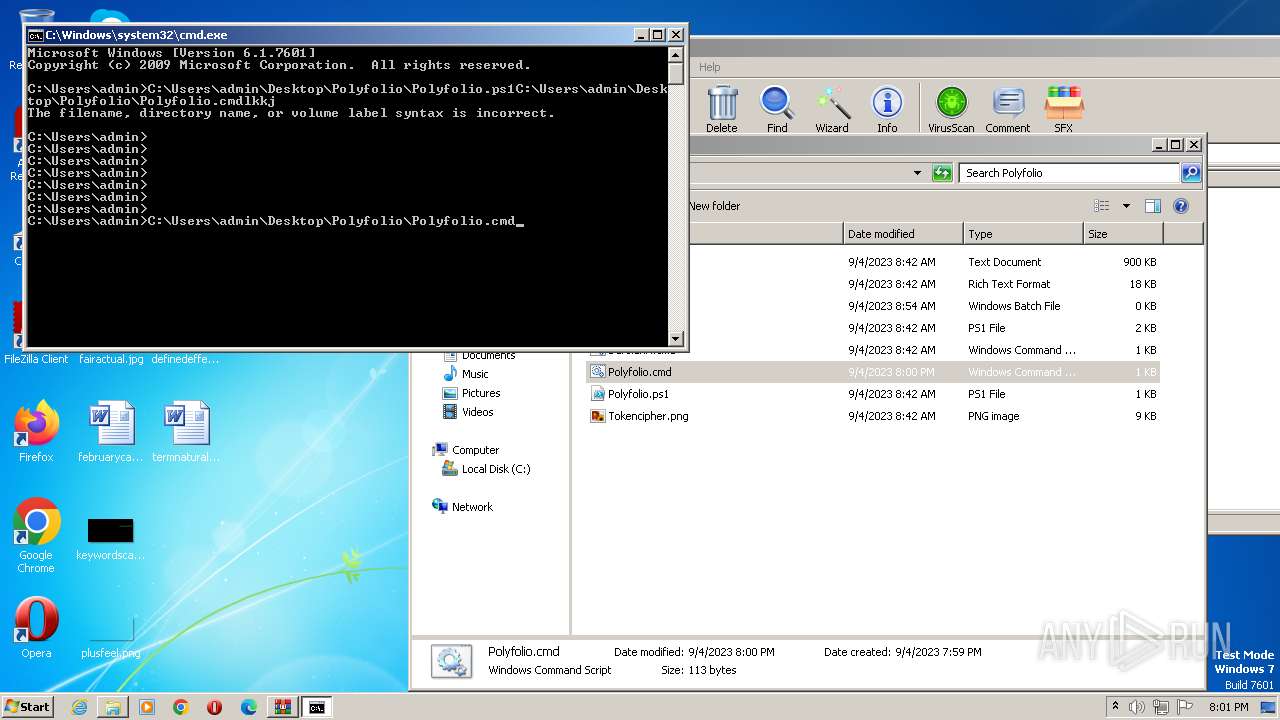
The process executes Powershell scripts
- cmd.exe (PID: 3388)
- cmd.exe (PID: 1832)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 1864)
- cmd.exe (PID: 3388)
- cmd.exe (PID: 1832)
Reads the Internet Settings
- powershell.exe (PID: 1864)
- powershell.exe (PID: 3860)
- powershell.exe (PID: 2384)
Application launched itself
- powershell.exe (PID: 1864)
The process creates files with name similar to system file names
- dw20.exe (PID: 1268)
INFO
Manual execution by a user
- notepad++.exe (PID: 3136)
- cmd.exe (PID: 1832)
- cmd.exe (PID: 3388)
- powershell.exe (PID: 2384)
- notepad++.exe (PID: 1972)
Checks supported languages
- dw20.exe (PID: 1268)
Reads the computer name
- dw20.exe (PID: 1268)
Create files in a temporary directory
- notepad++.exe (PID: 3136)
Creates files or folders in the user directory
- dw20.exe (PID: 1268)
Reads the machine GUID from the registry
- dw20.exe (PID: 1268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Polyfolio\Coinonymous.txt |
|---|---|
| ZipUncompressedSize: | 921483 |
| ZipCompressedSize: | 692510 |
| ZipCRC: | 0x718db61c |
| ZipModifyDate: | 2023:09:04 08:42:24 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
55
Monitored processes
10
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1268 | dw20.exe -x -s 1980 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1832 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
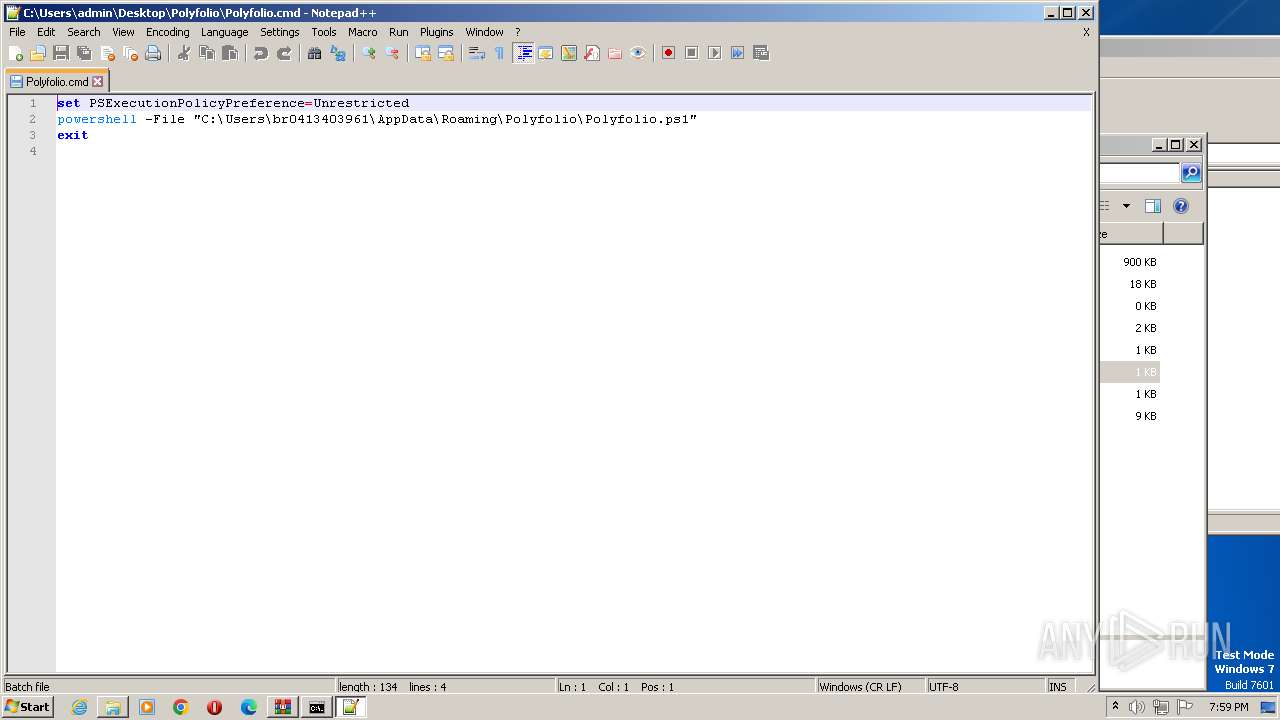
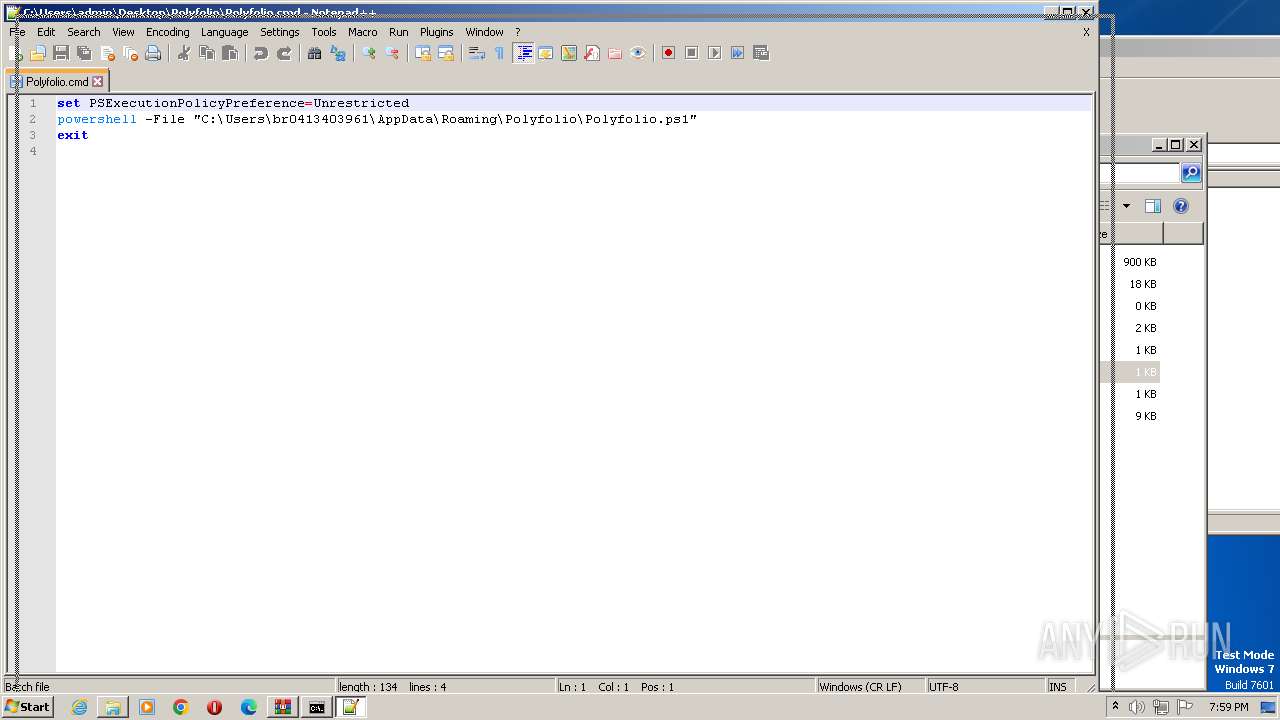
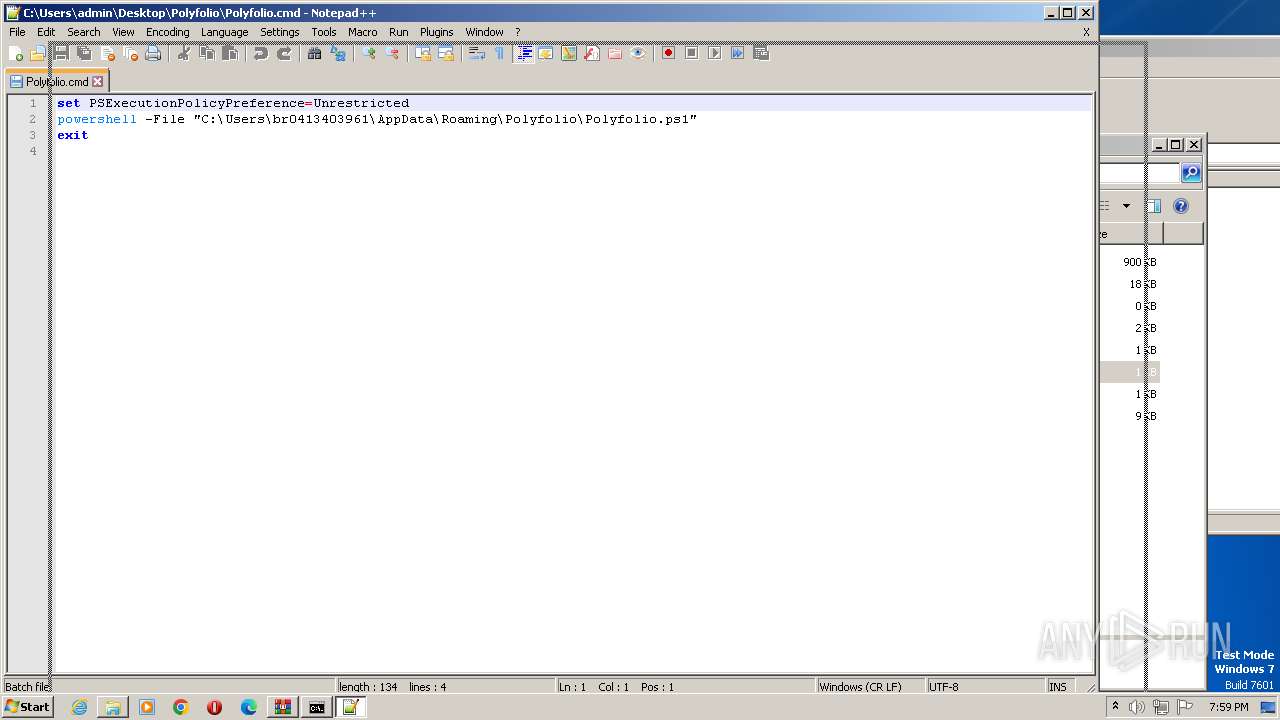
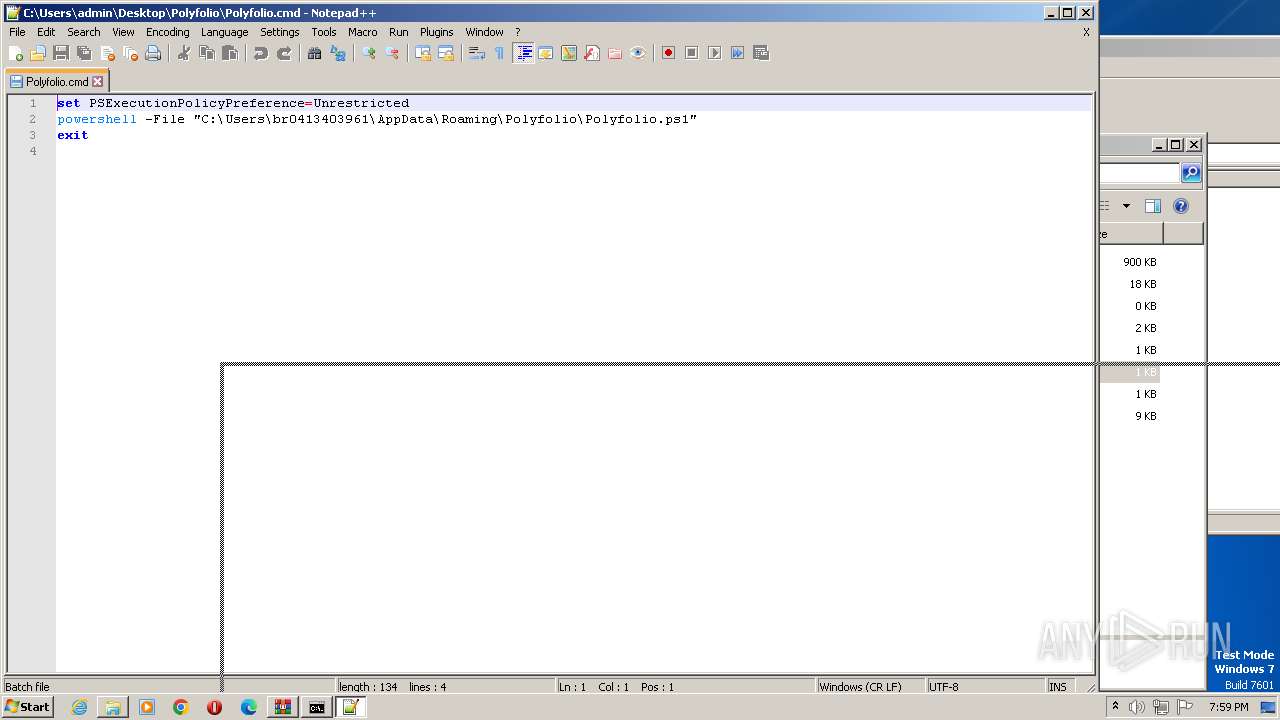
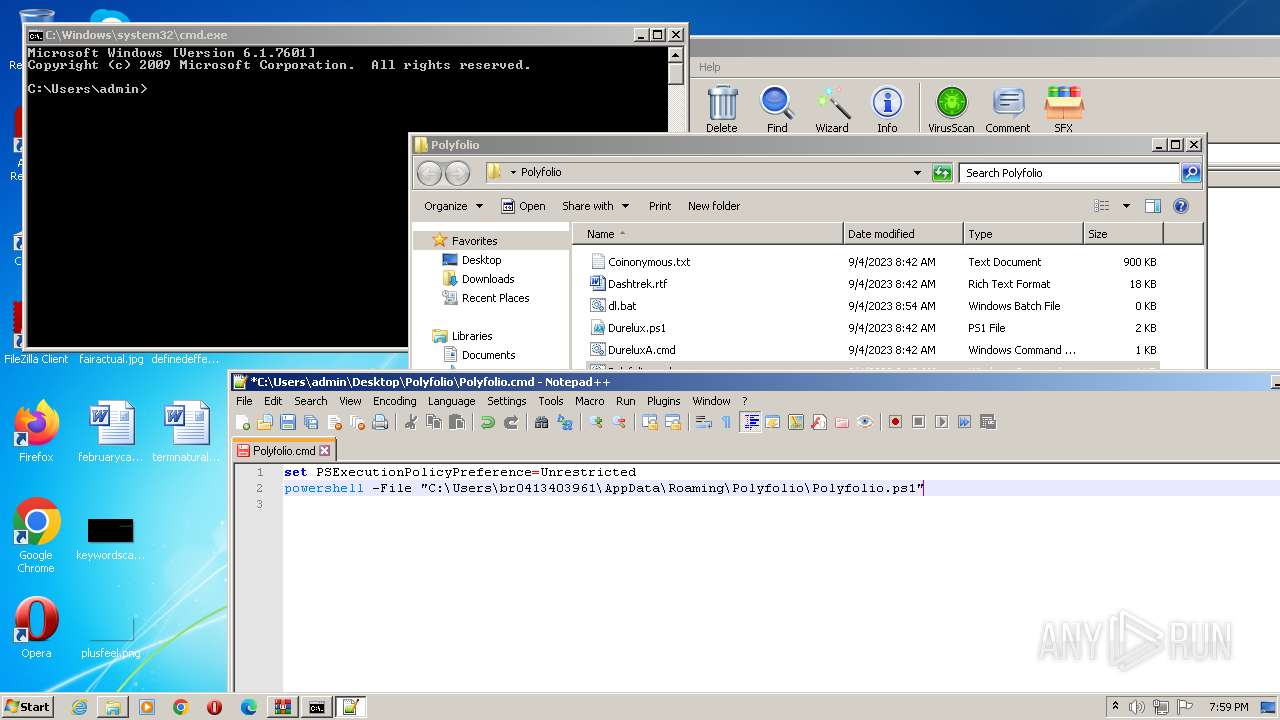
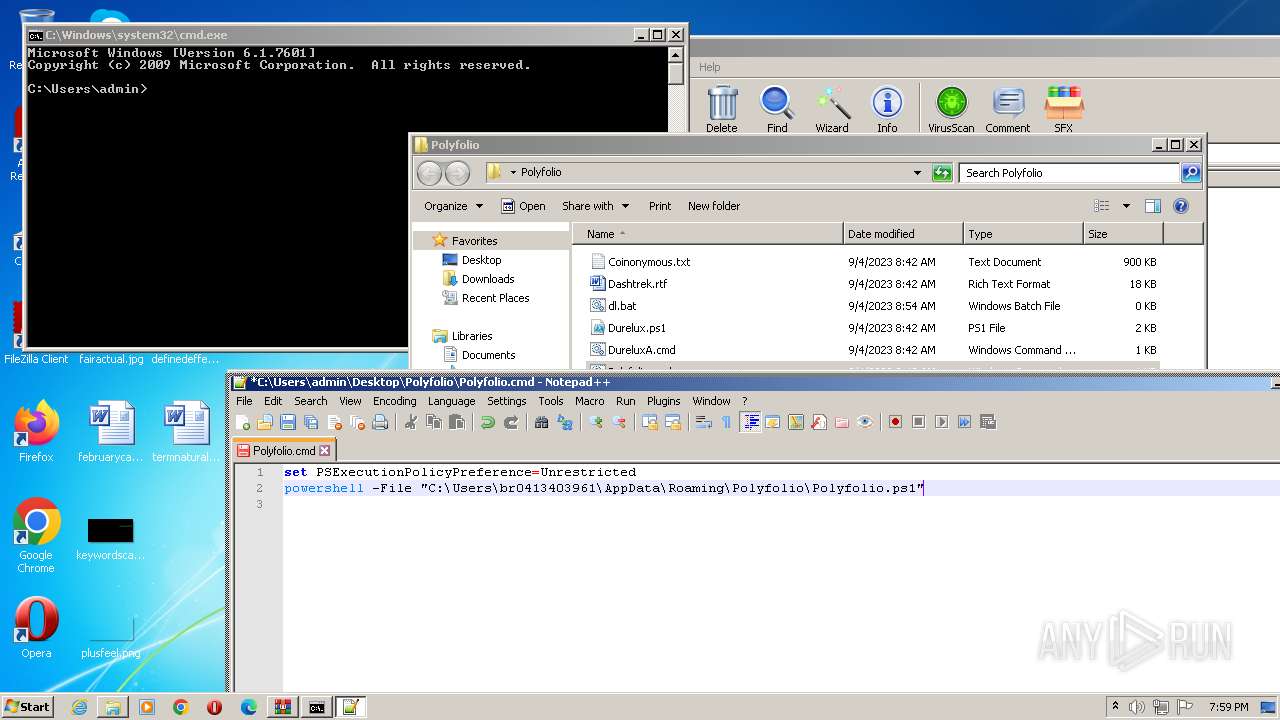
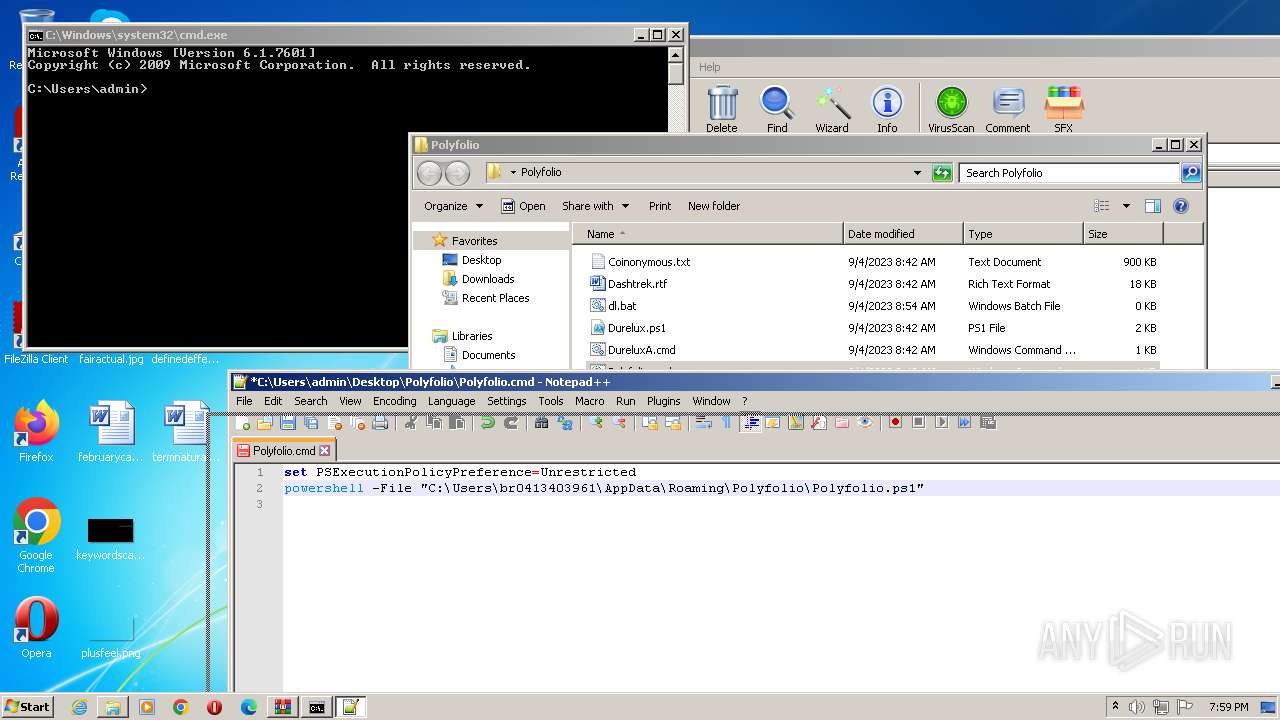
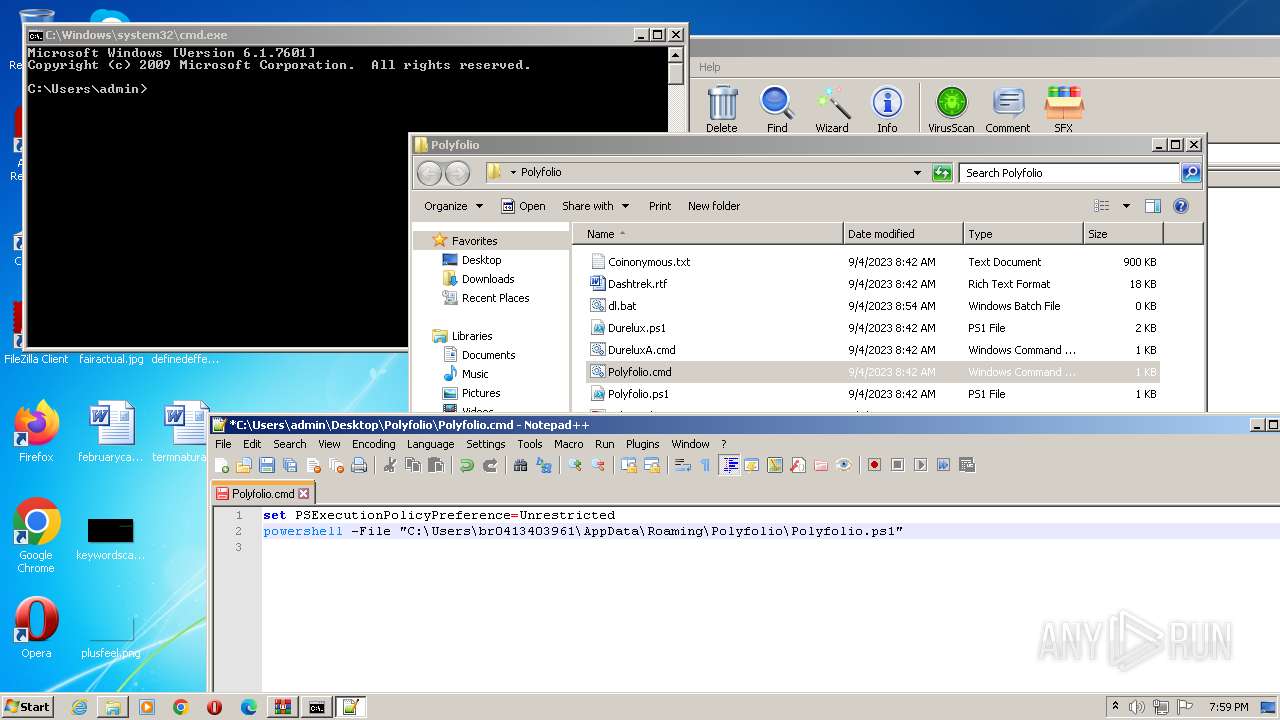
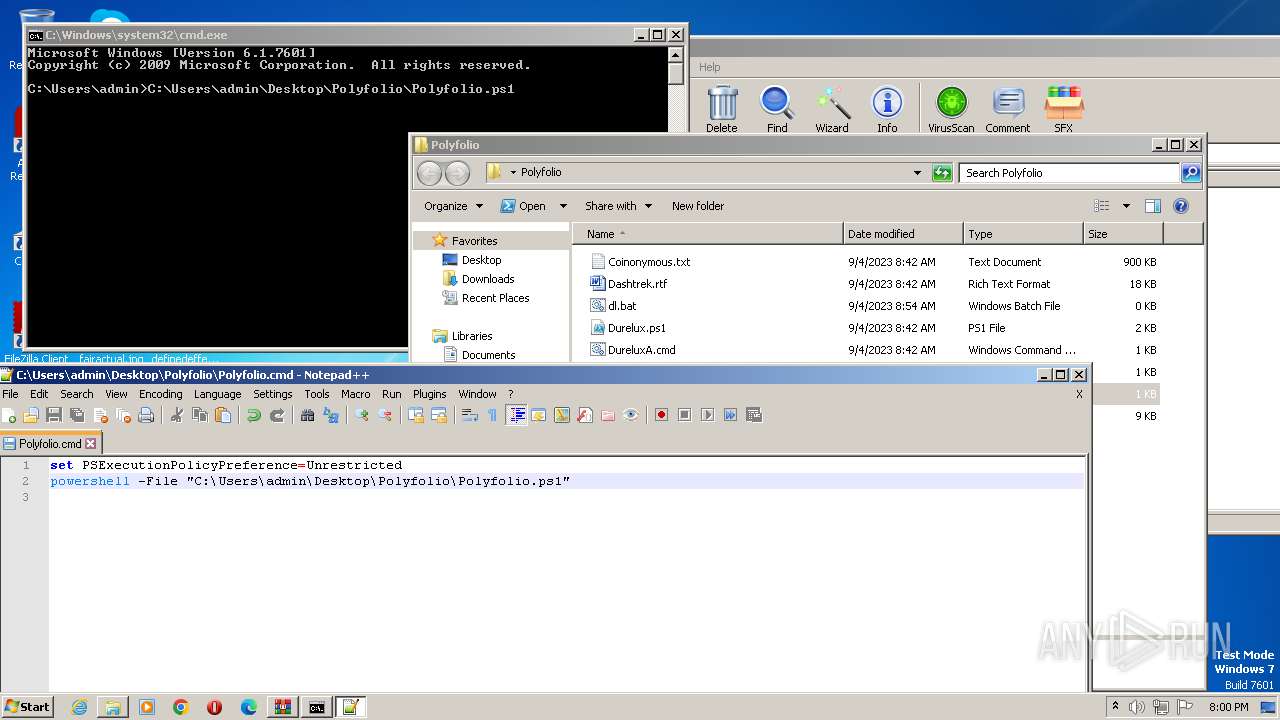
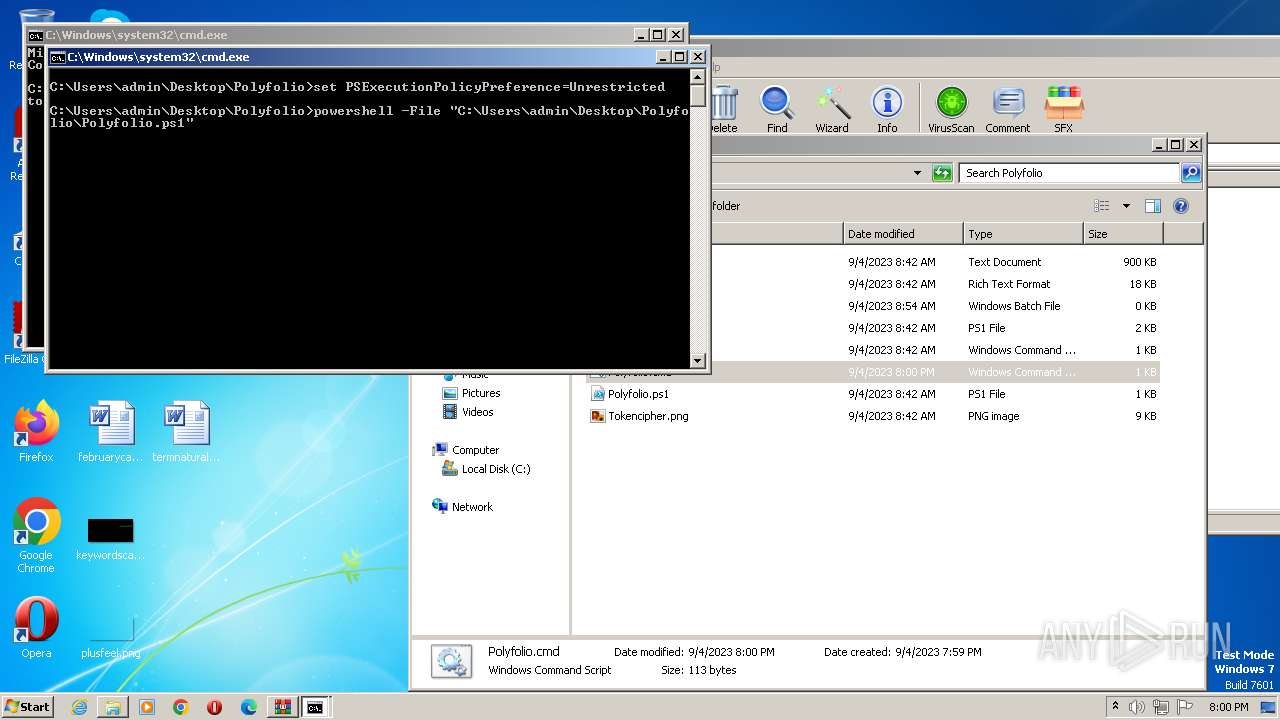
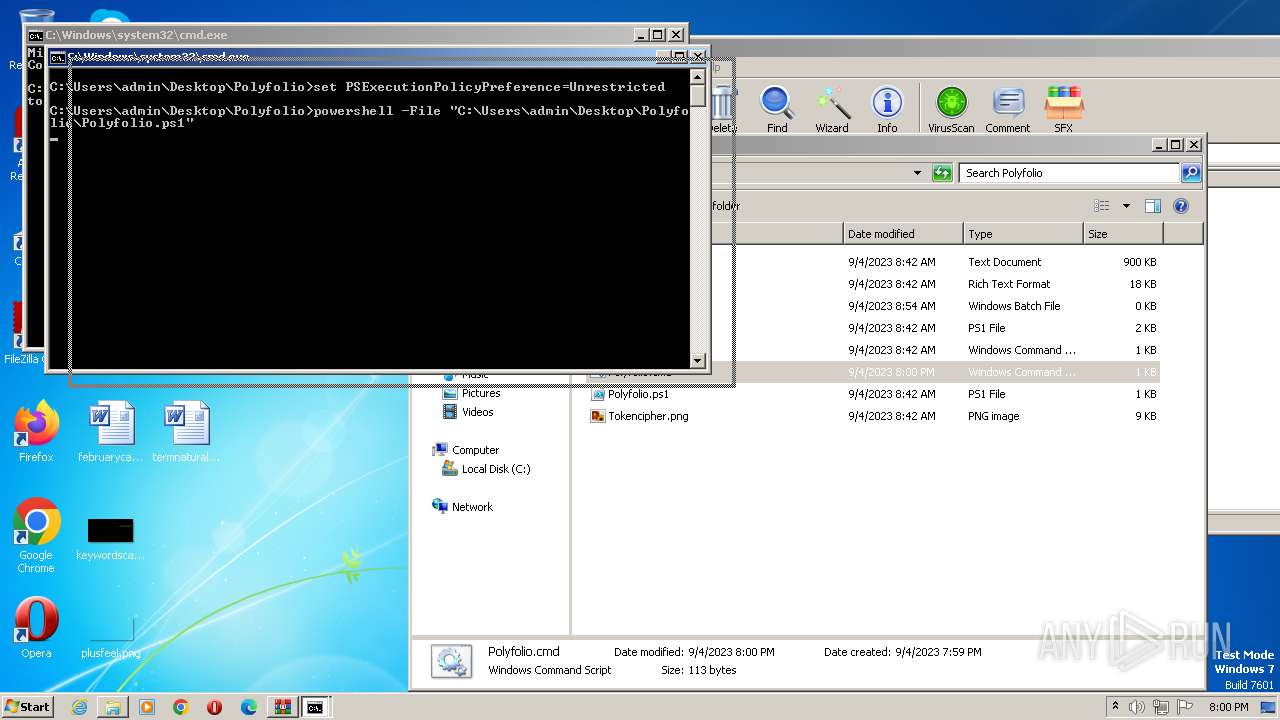
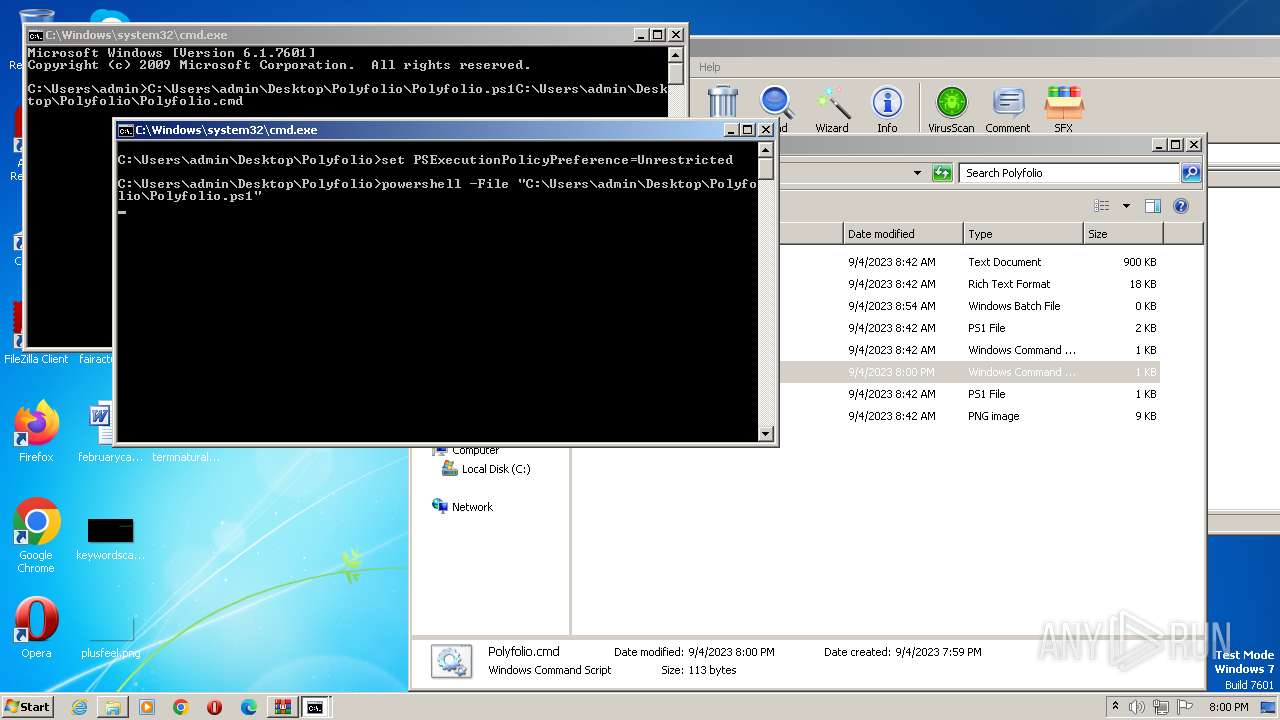
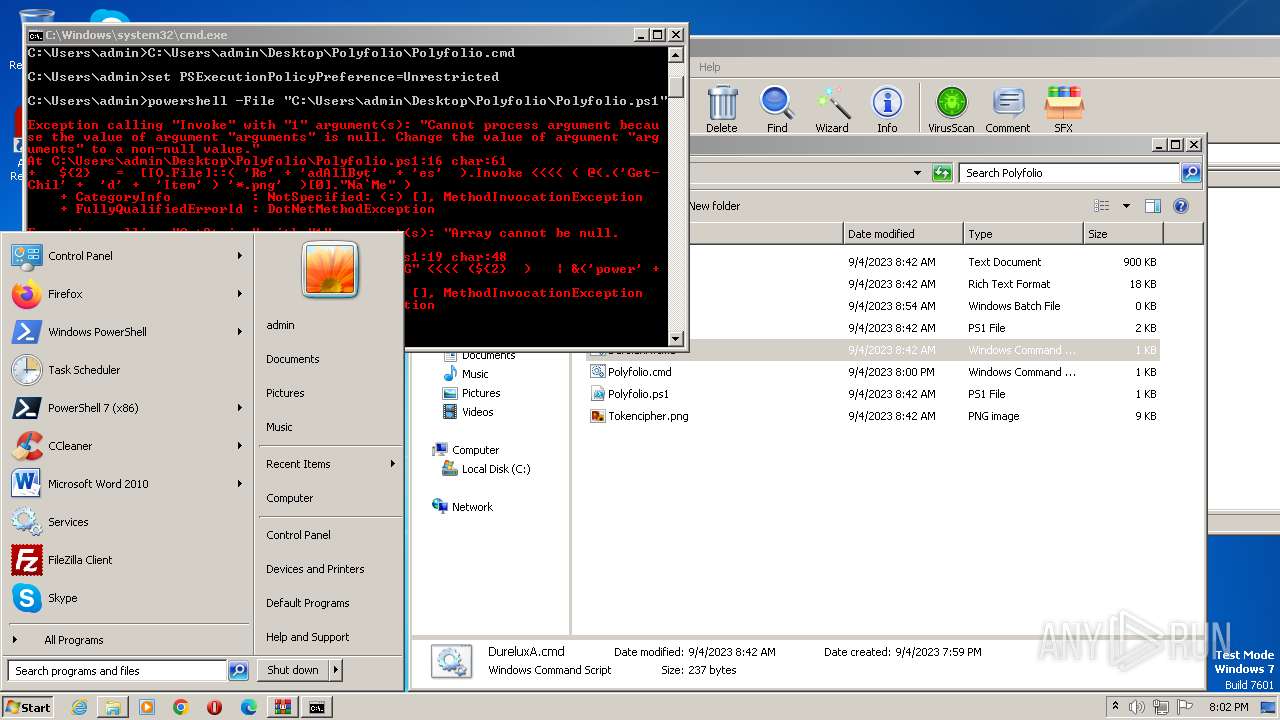
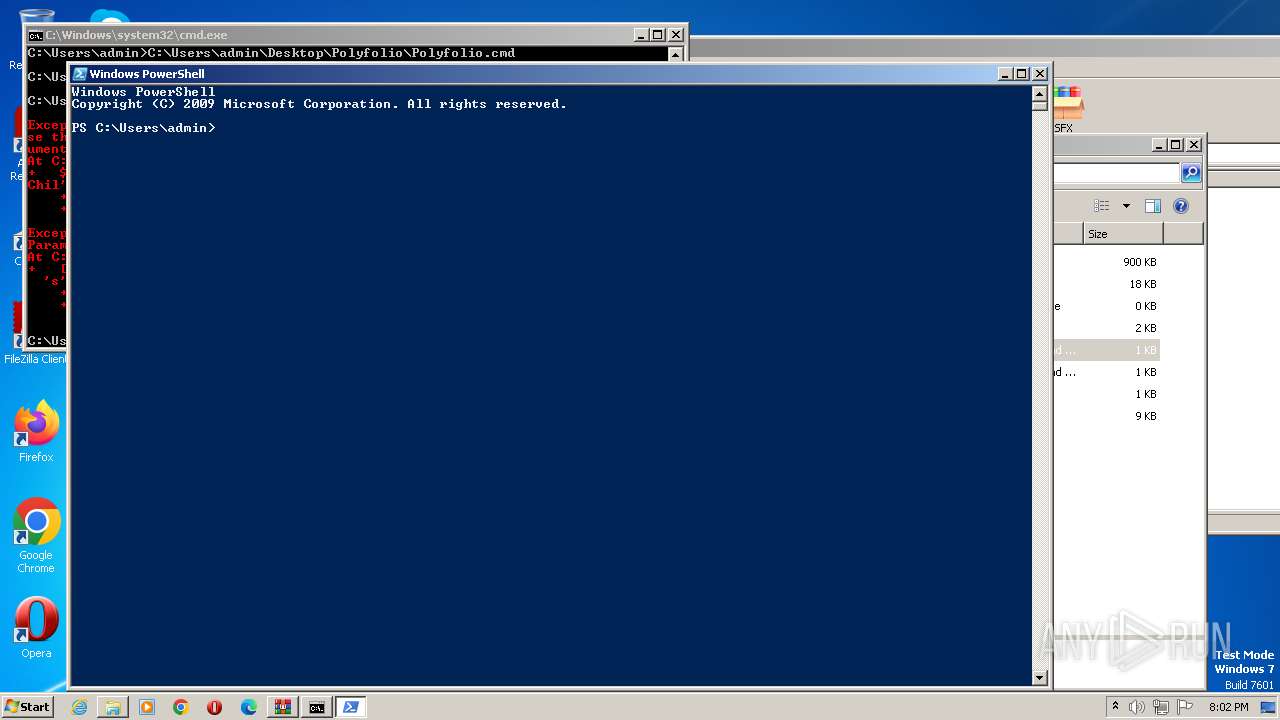
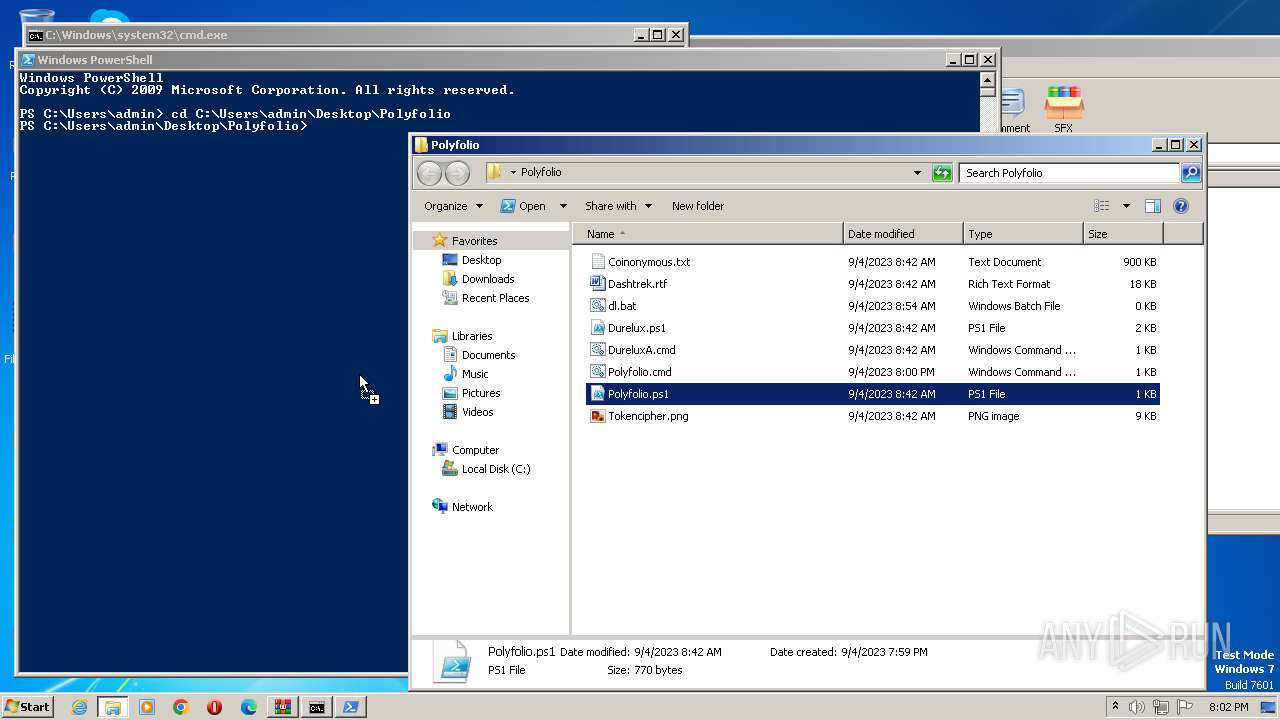
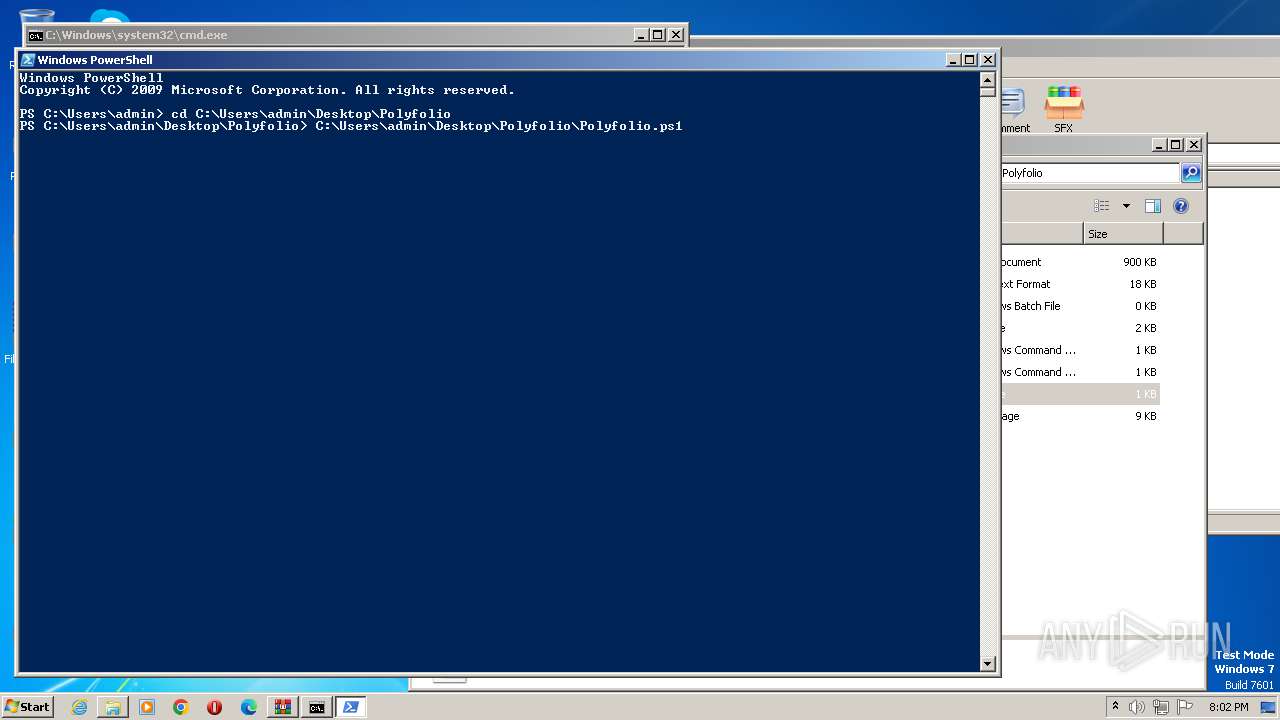
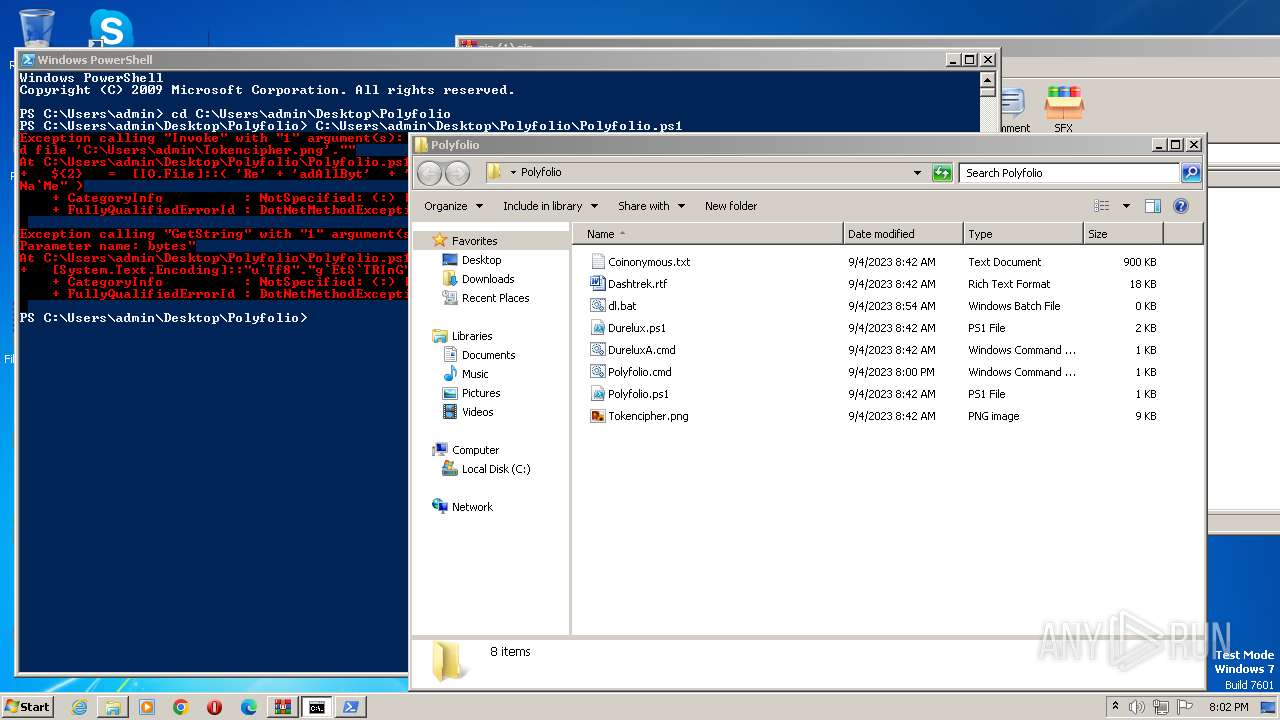
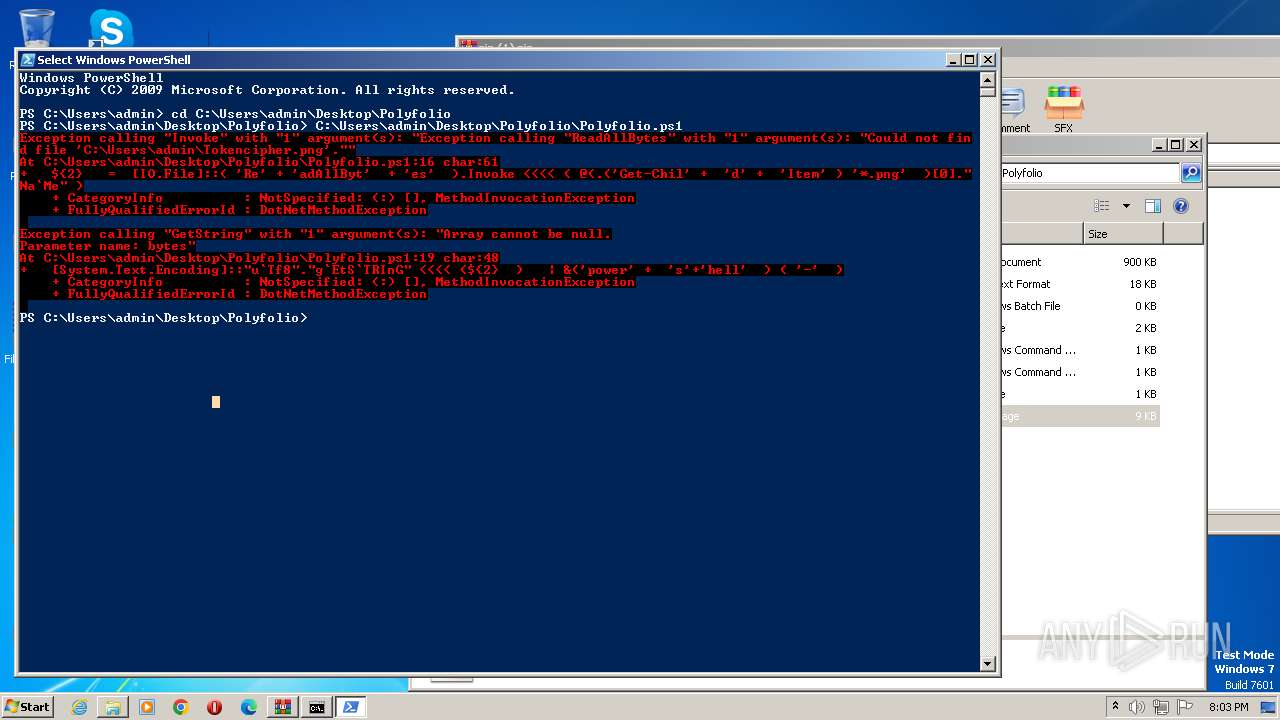
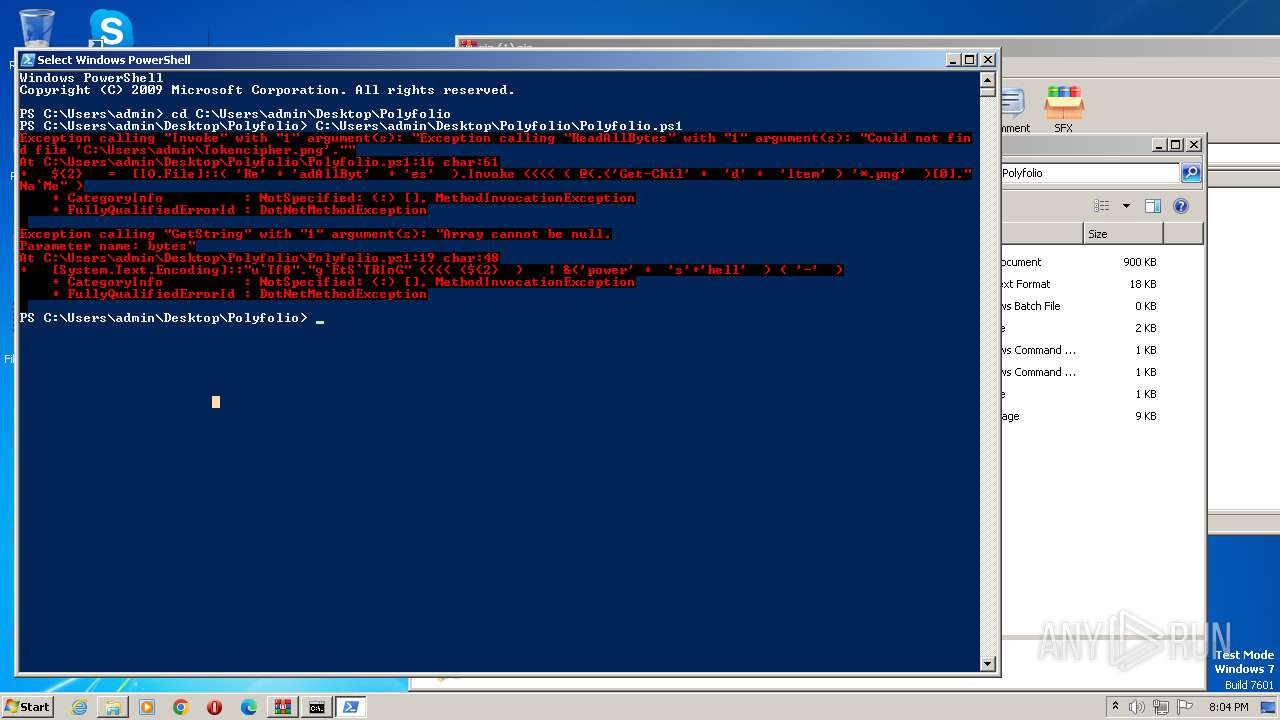
| 1864 | powershell -File "C:\Users\admin\Desktop\Polyfolio\Polyfolio.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
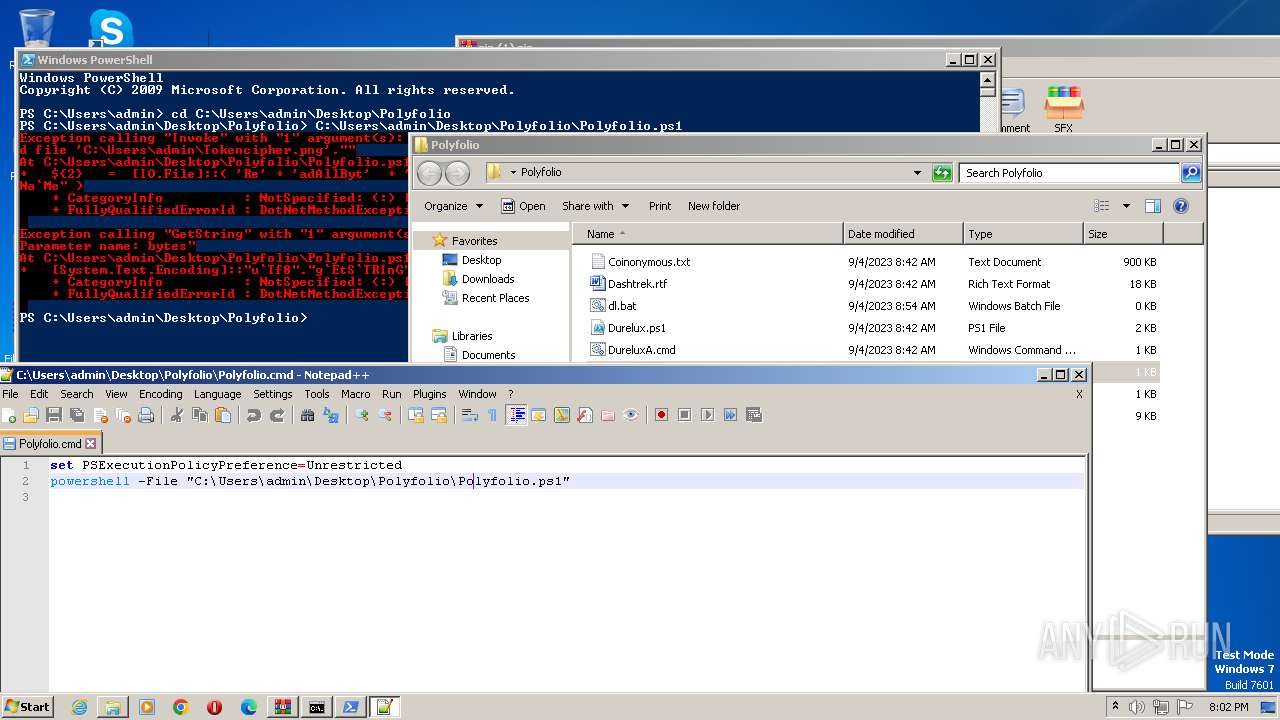
| 1972 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Polyfolio\Polyfolio.cmd" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2384 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
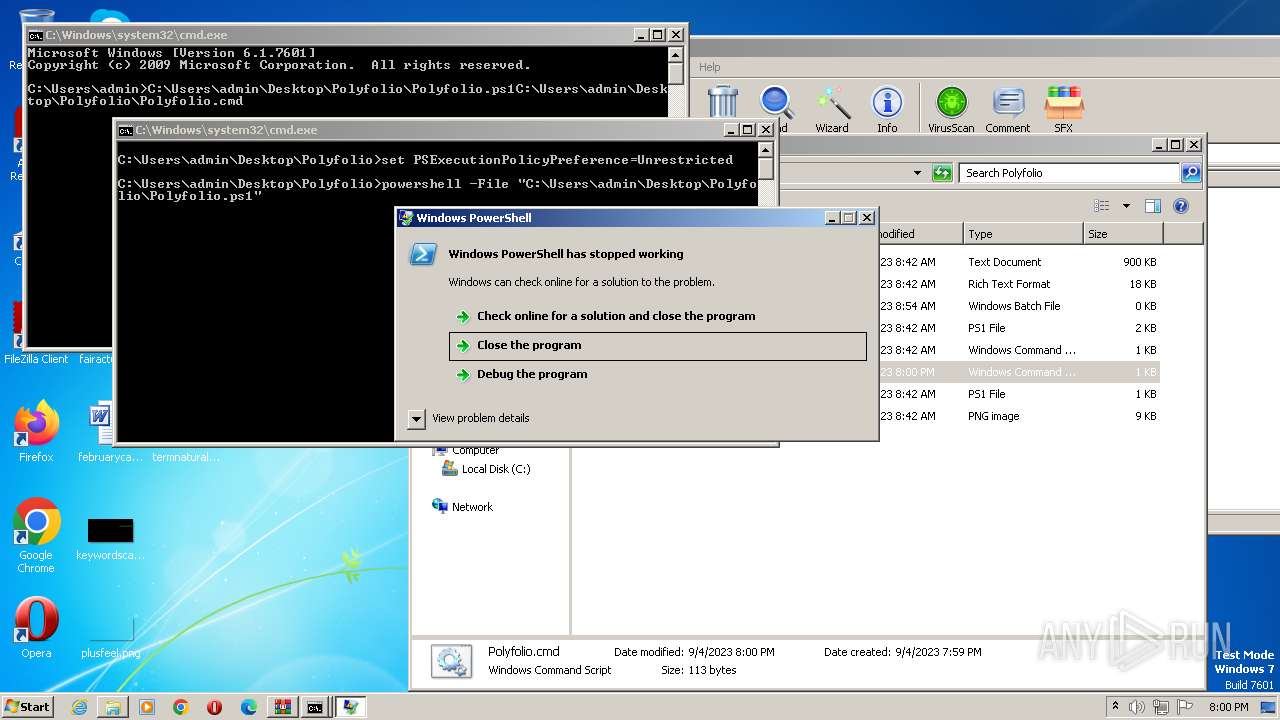
| 2668 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
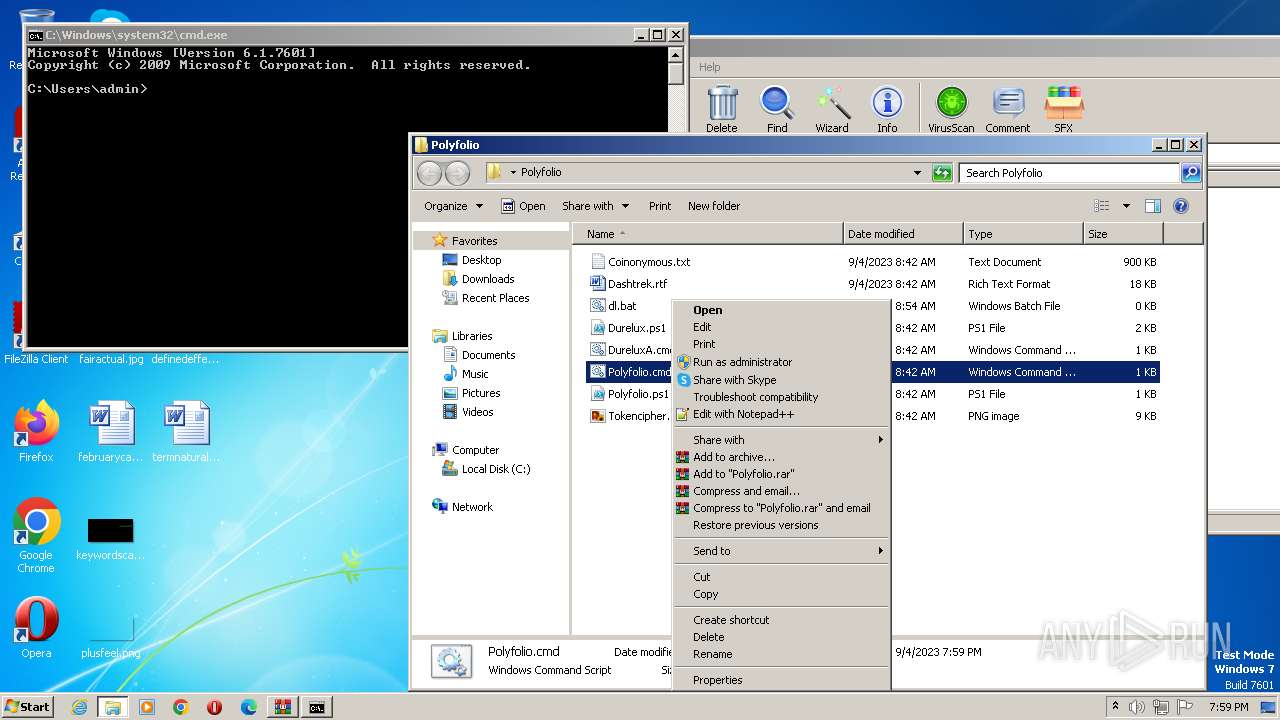
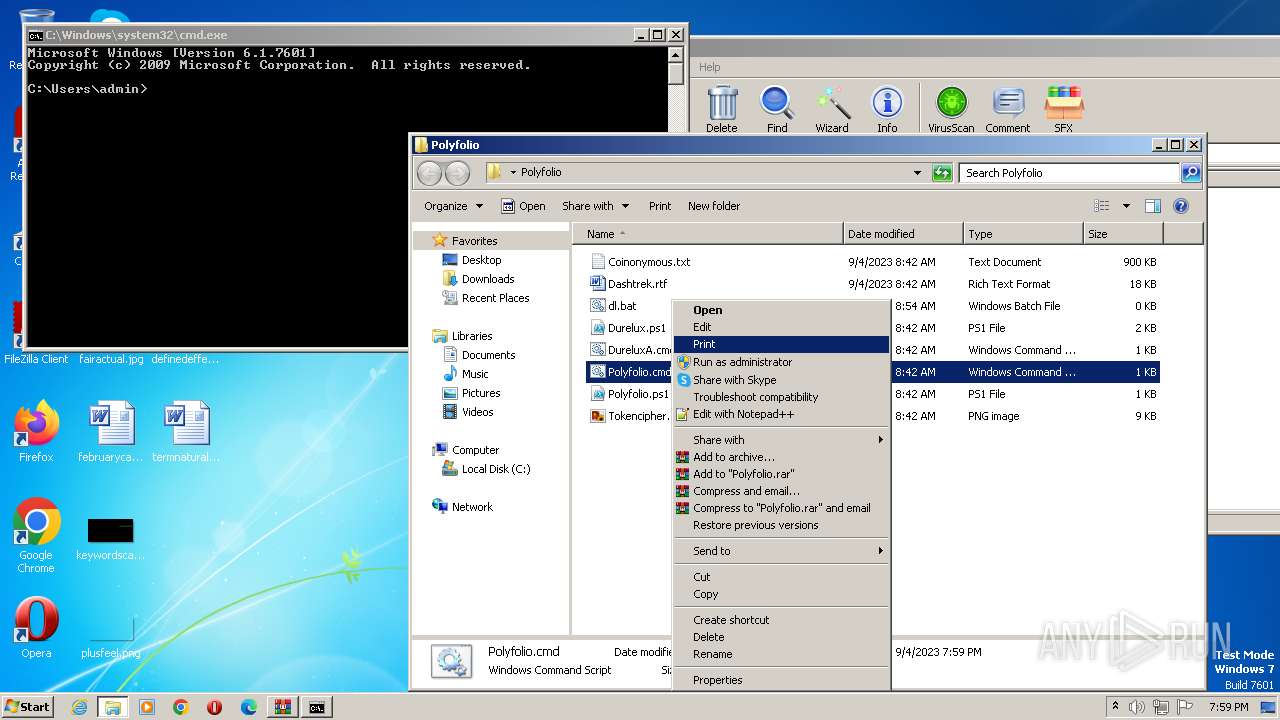
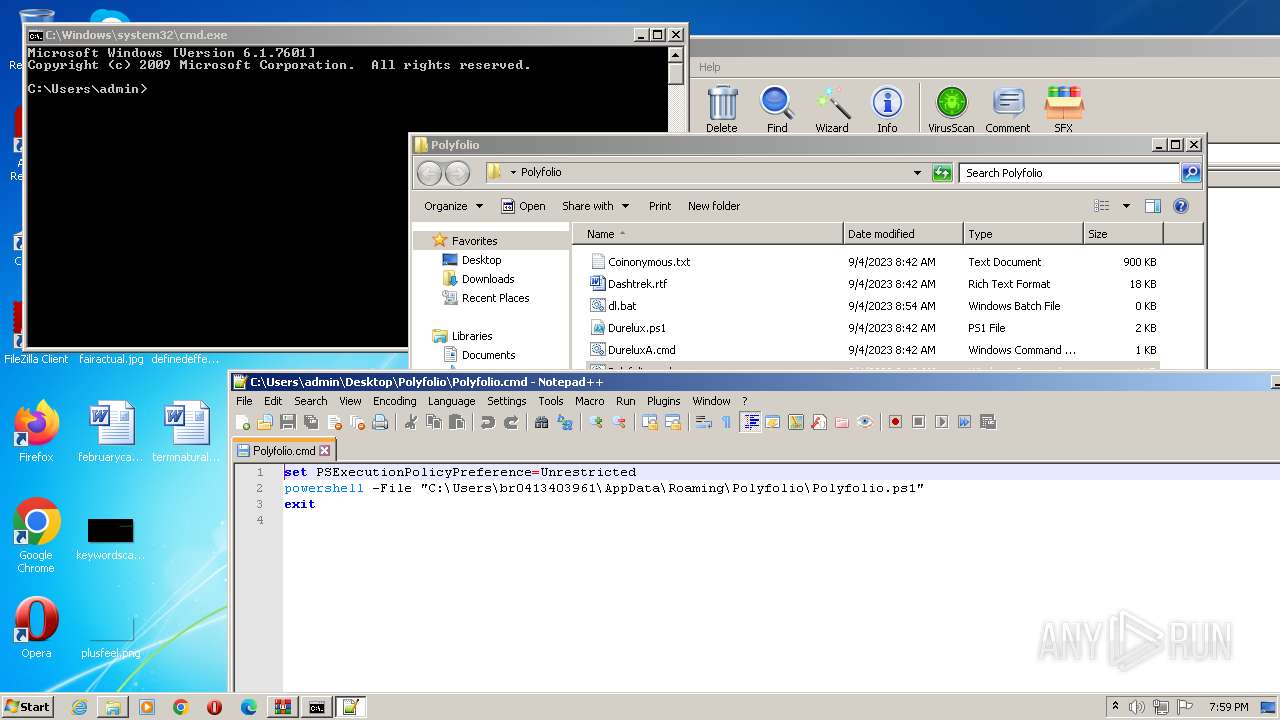
| 2968 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\zip (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3136 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Polyfolio\Polyfolio.cmd" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3388 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Polyfolio\Polyfolio.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3860 | powershell -File "C:\Users\admin\Desktop\Polyfolio\Polyfolio.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 720
Read events
5 449
Write events
271
Delete events
0
Modification events
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3136) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1864) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
15
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1268 | dw20.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_powershell.exe_e86e279543c8118e7f3940338d2b1827dcc634_04e560e9\Report.wer | — | |
MD5:— | SHA256:— | |||
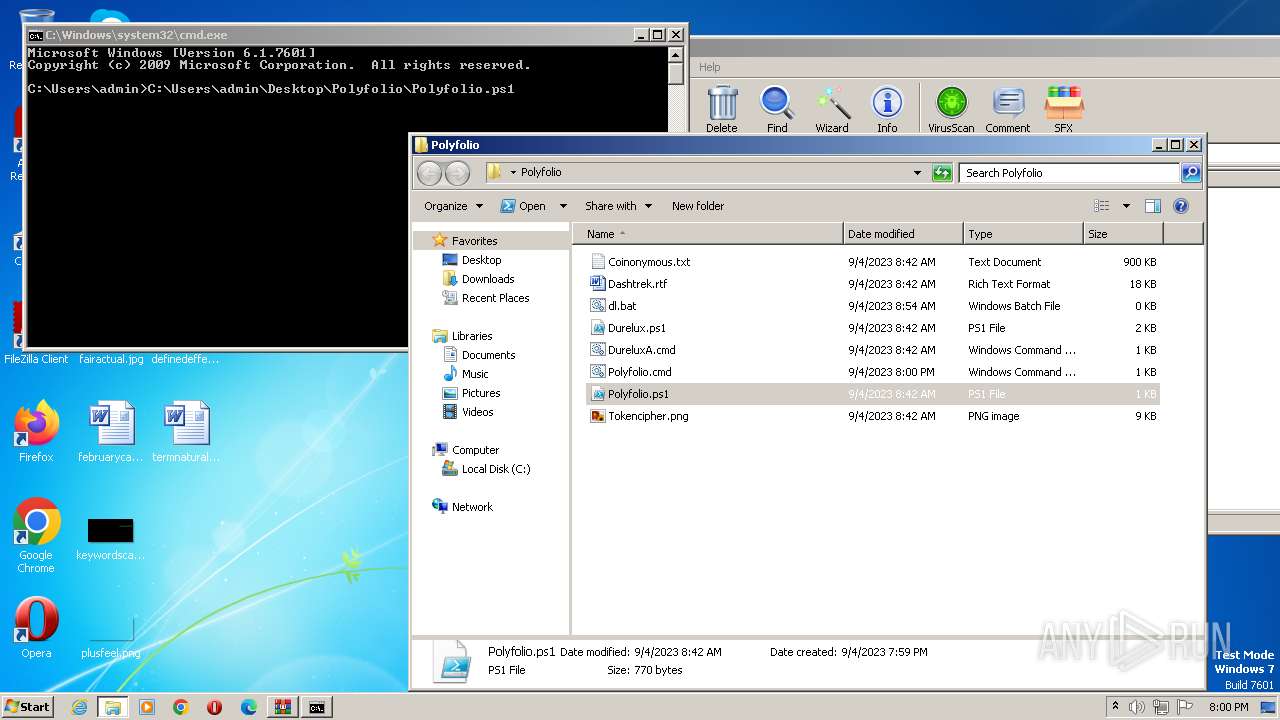
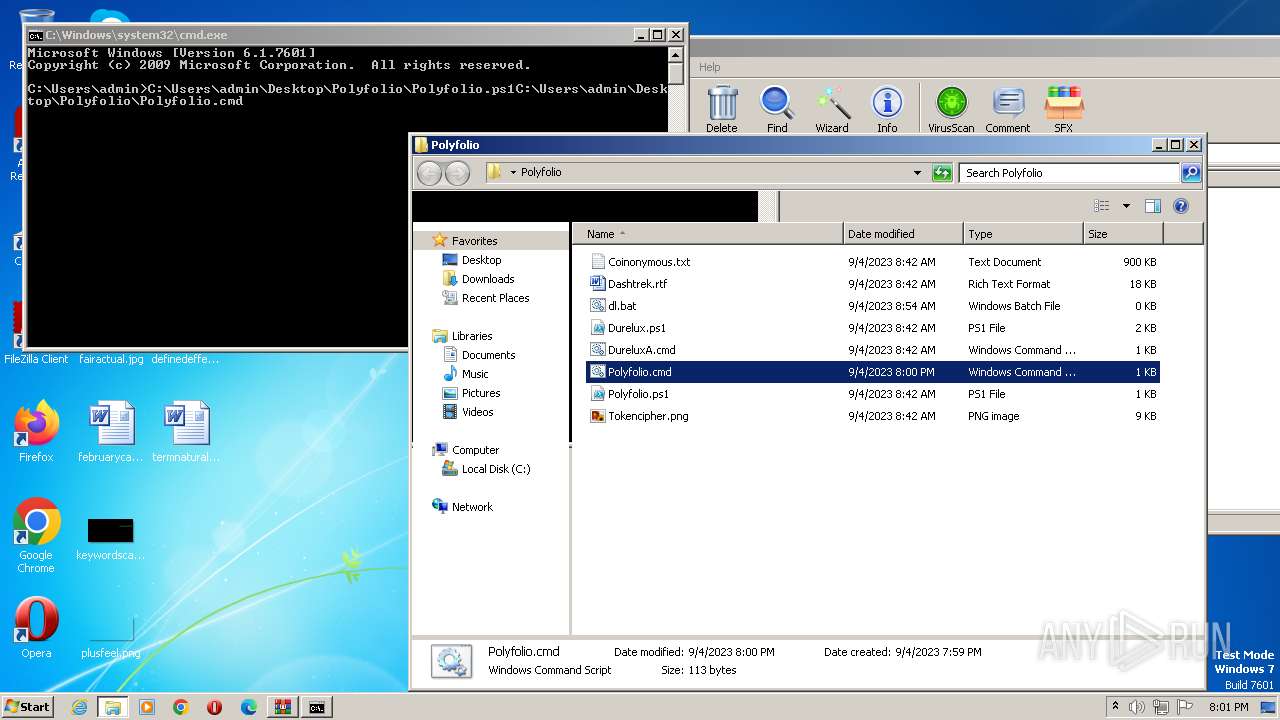
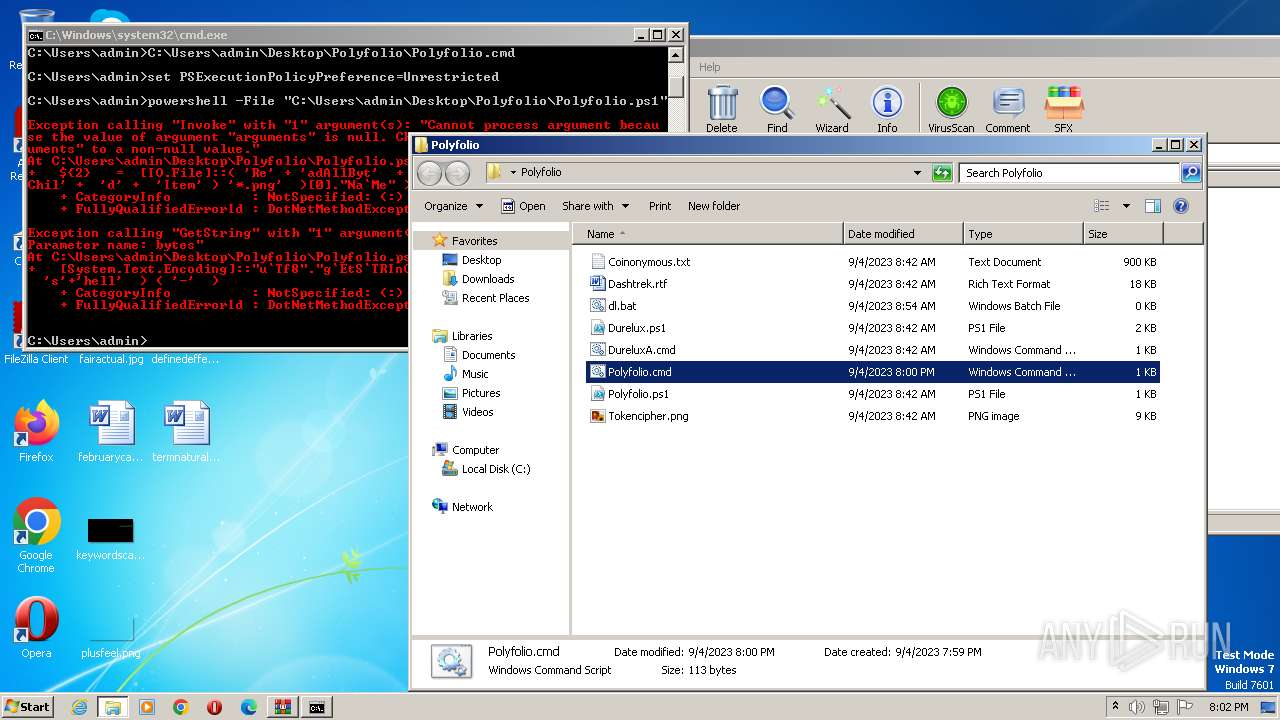
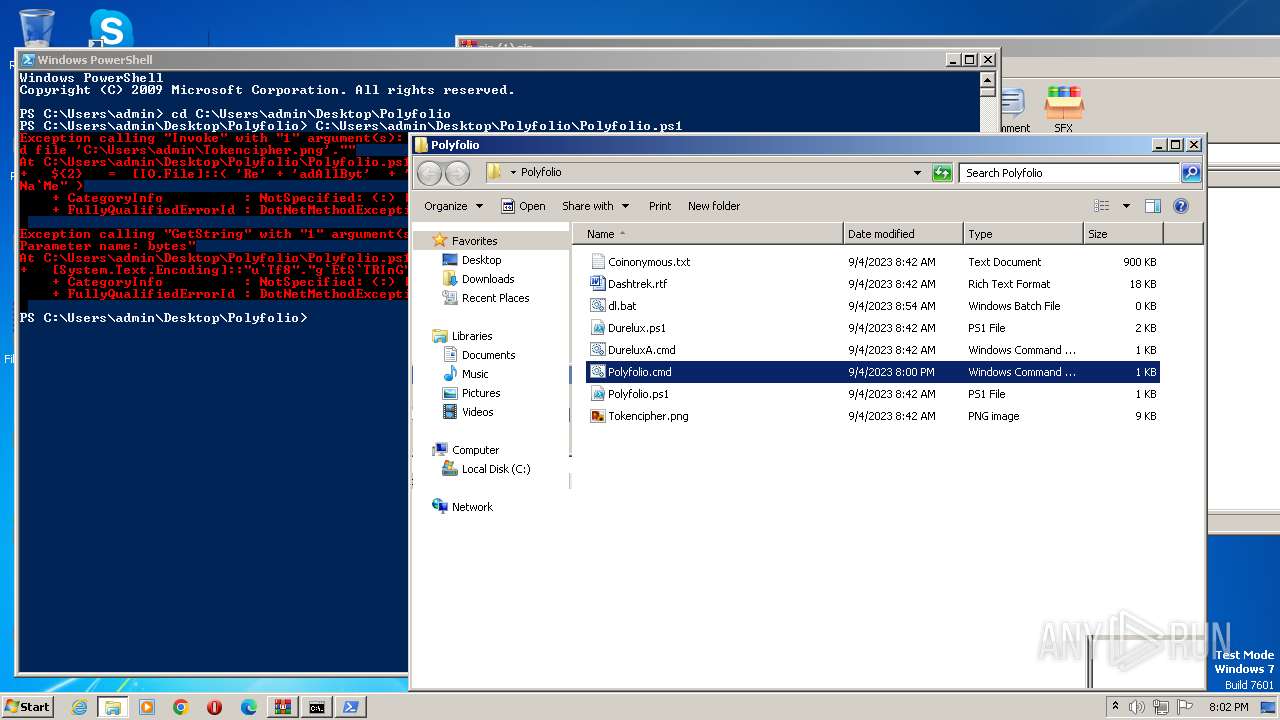
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.43834\Polyfolio\Coinonymous.txt | binary | |
MD5:E10FF83E1B10B0D319180DE2FC6EFD46 | SHA256:B918E9F72FE477E01816DFD2AD93990879111337559CB90ADBE8202EE86AAA7D | |||
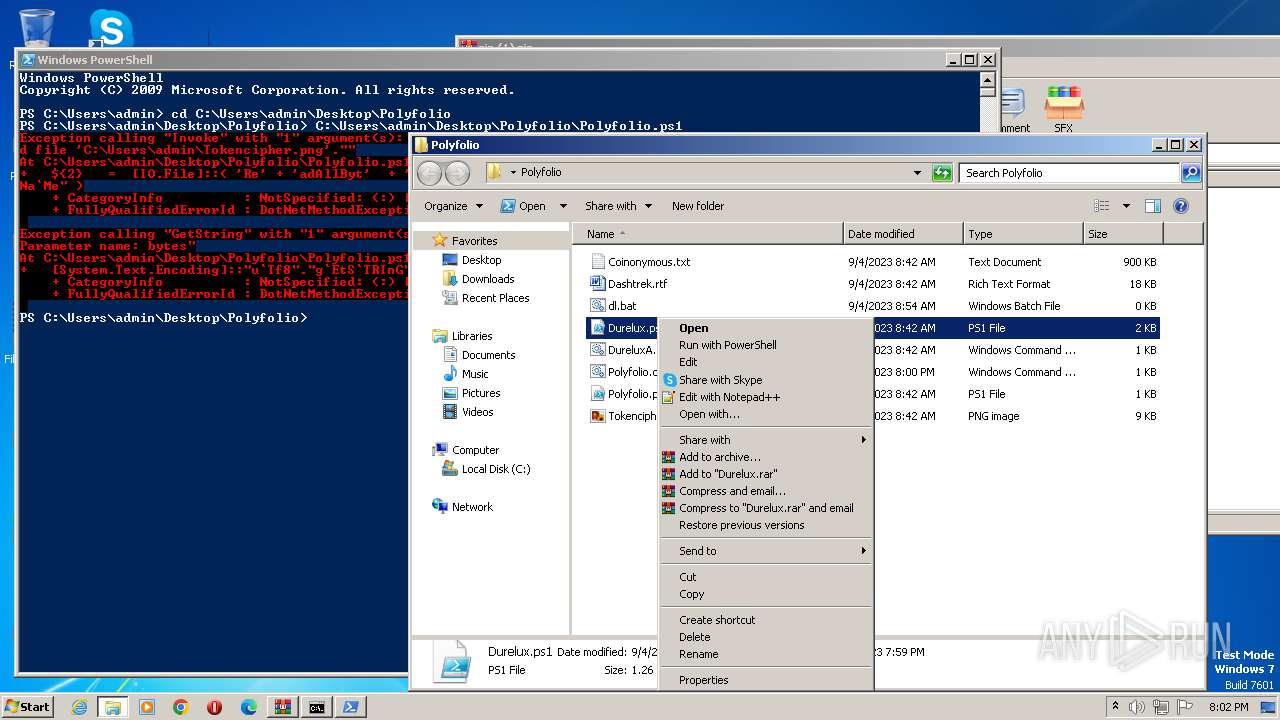
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.43834\Polyfolio\Durelux.ps1 | text | |
MD5:8BF61835C9A719F6D4704AEC6B285B6B | SHA256:7D27DEA8721F42B5B23C3D659F1164A84B9BD58A3B8F5B770F5793D0DC70823A | |||
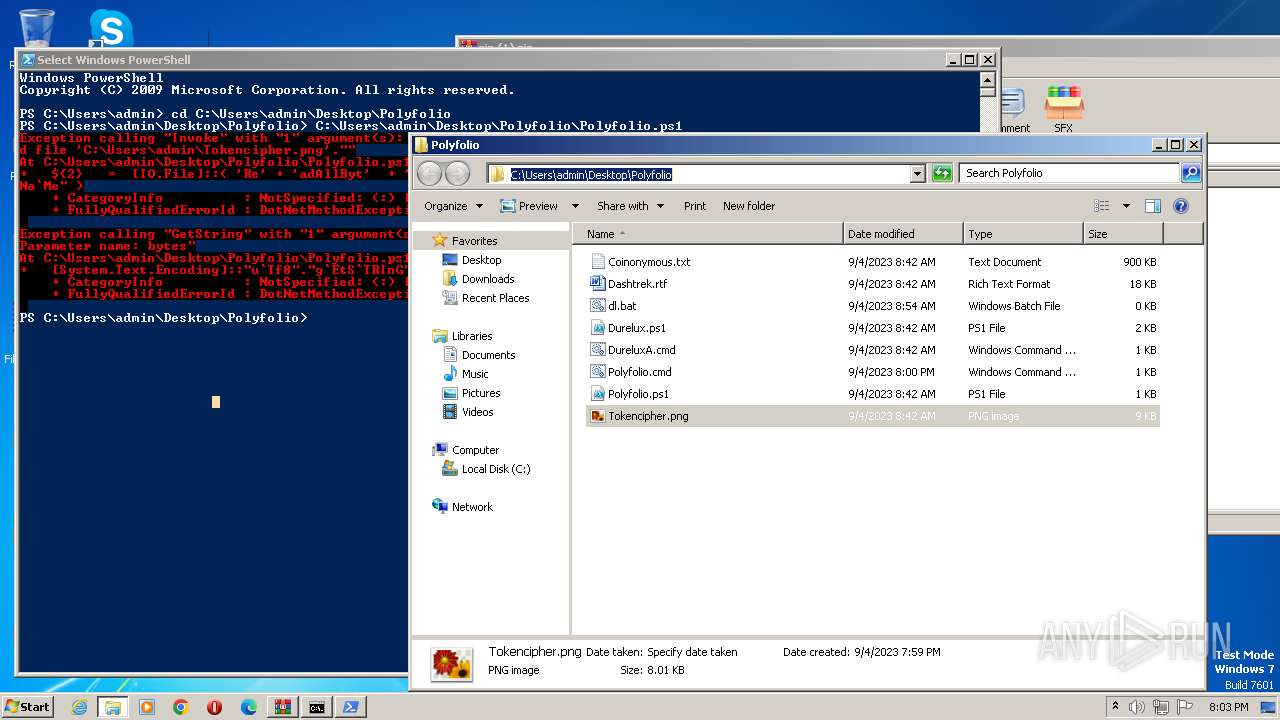
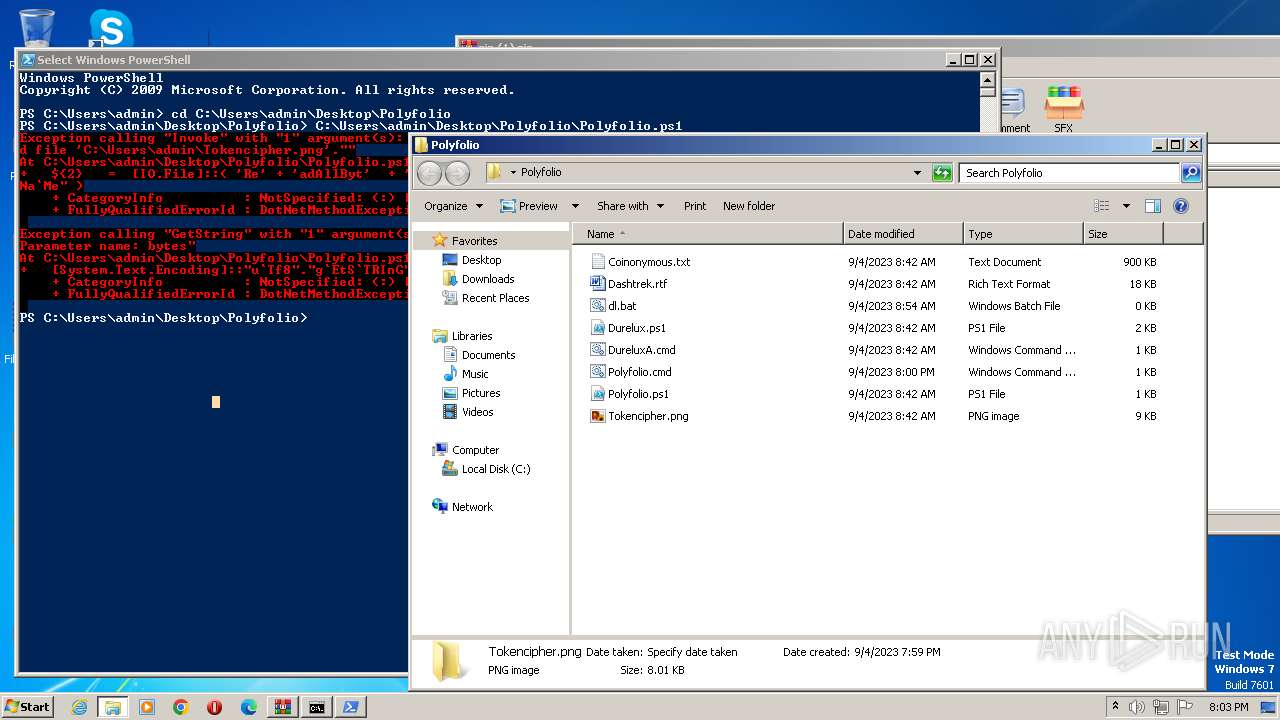
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.43834\Polyfolio\Tokencipher.png | binary | |
MD5:B8EF5019F33EA6A23E33B08B06FEE2A0 | SHA256:F237CC787EB27187F2D6E050D5A8B8B5BA660D548A056224710AF9A37C1A7EF7 | |||
| 3136 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:3E781ED98F8A497BCBFBB12A02663EF8 | SHA256:BEF2C1600119E51EC448161584D59C3C5AB66467416895DA56705E4CB8694B67 | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FXDASO1MMFF4WJQOGM5L.temp | binary | |
MD5:219900F4E3A0B4B3E1BDF364167D697E | SHA256:F953A7C5F1662C04D86C12EBA0D22A135CC0AE11BAEEE80CC5EFD325582B5F36 | |||
| 3136 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\backup\Polyfolio.cmd@2023-09-04_195950 | text | |
MD5:8D17C428FDBBB06715FBF2F19F934B3A | SHA256:024318C623591D74FB063E5A685023B9AEC01E6F33D6C0271B5D9C66F7256C80 | |||
| 3860 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:219900F4E3A0B4B3E1BDF364167D697E | SHA256:F953A7C5F1662C04D86C12EBA0D22A135CC0AE11BAEEE80CC5EFD325582B5F36 | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.43834\Polyfolio\Dashtrek.rtf | binary | |
MD5:83B5AF22BABB824846DE5DDD35910057 | SHA256:6E1681F56BF2E9641DC04A2815873D3F11FF72D139253889D43A5B8C19B704D3 | |||
| 3136 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:139765B8B8E9974945FEF221BB082CFE | SHA256:A55151DA28F28E27B539587FE811F4759EFBD1E8CE00F1236DEBE826891354CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|