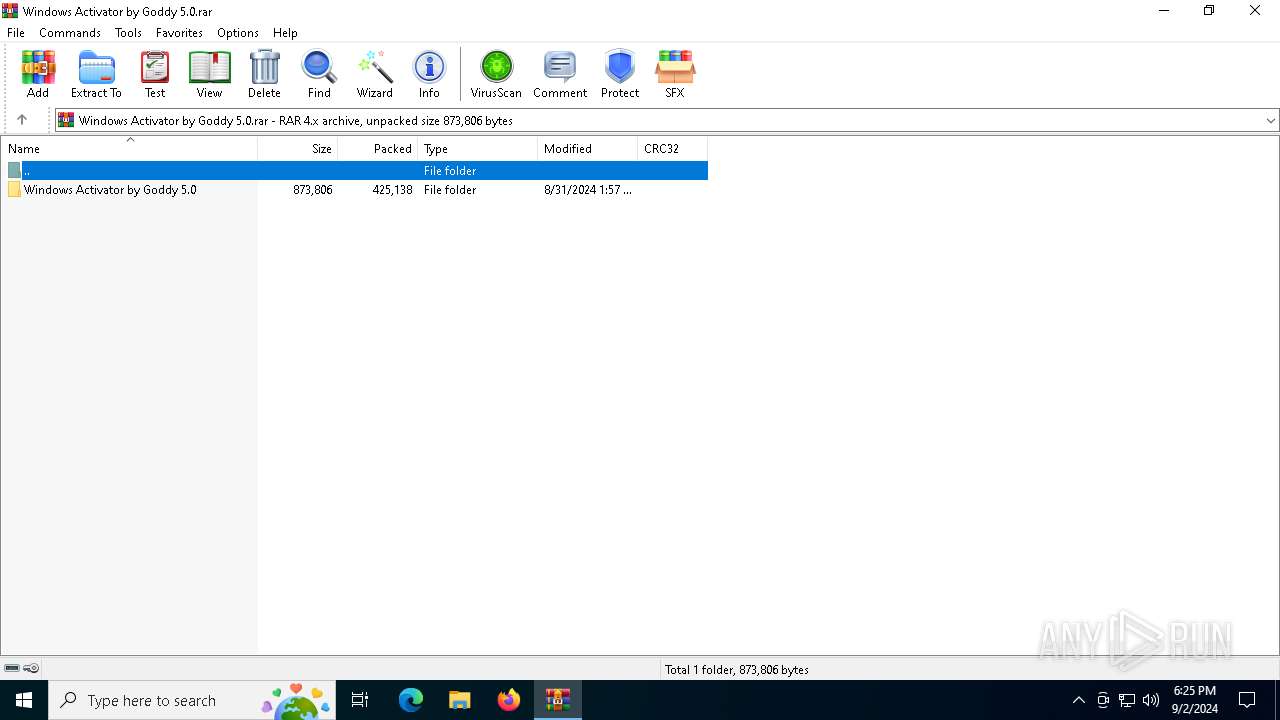
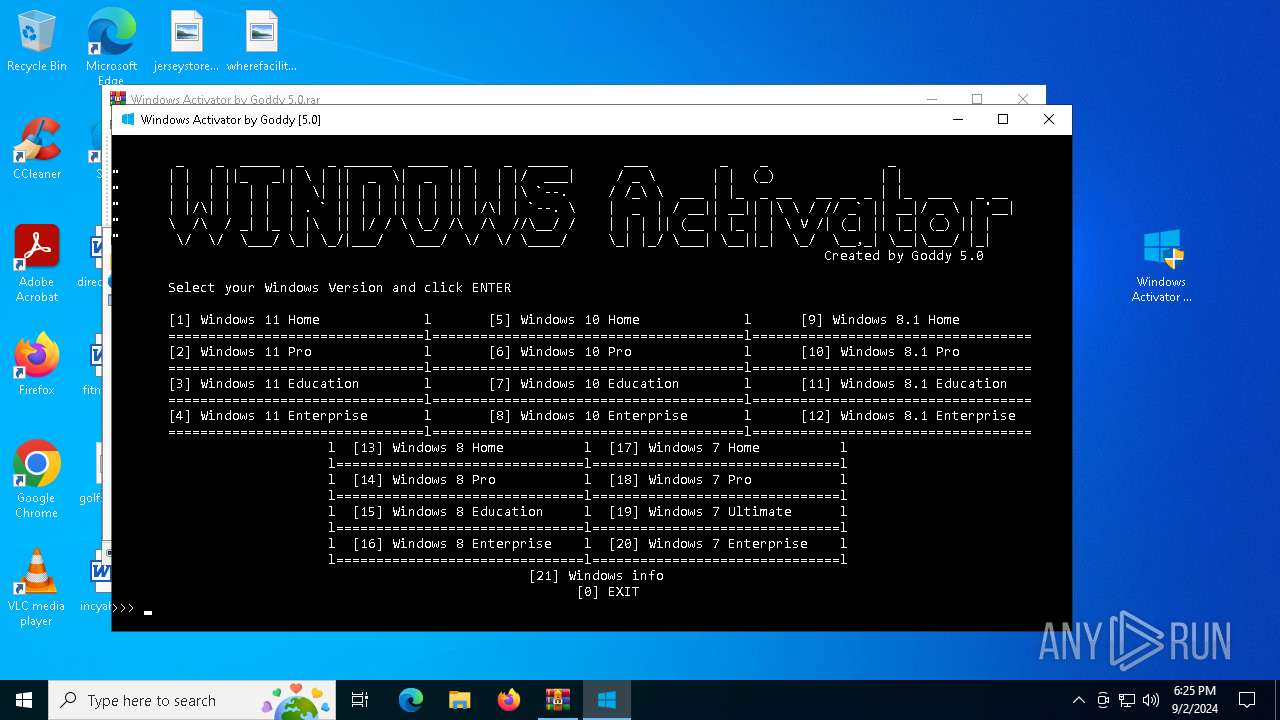
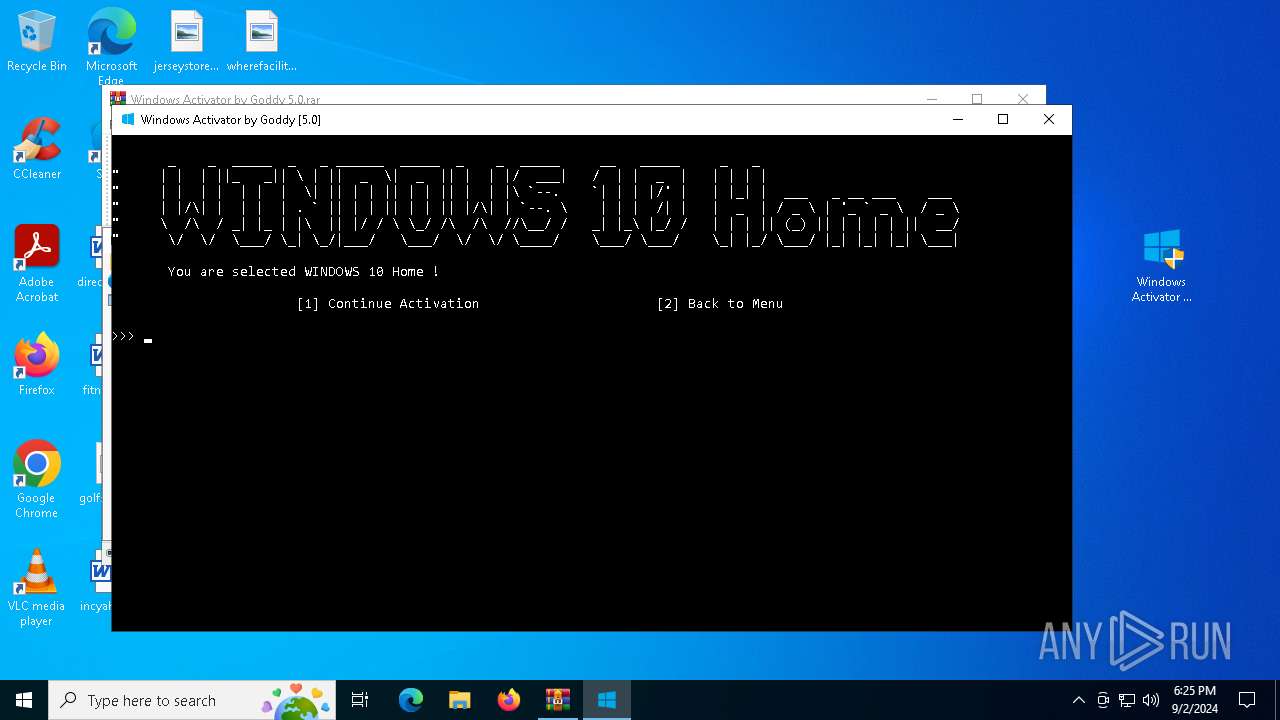
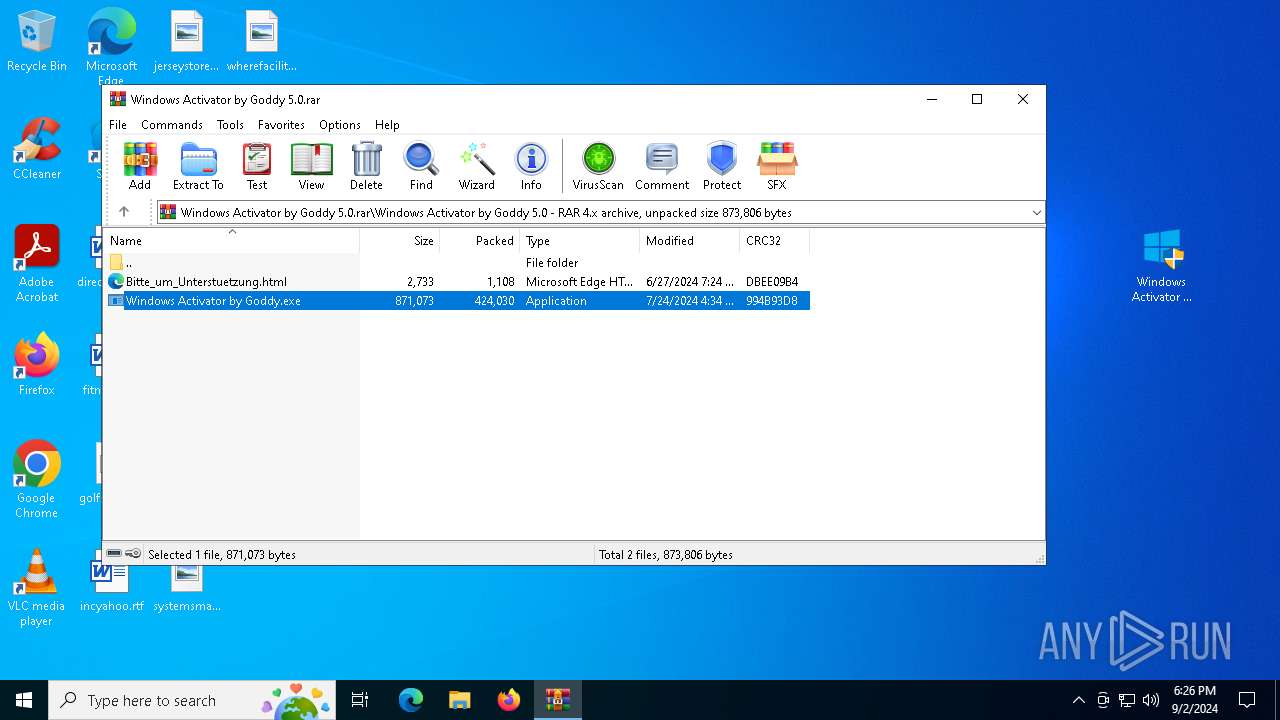
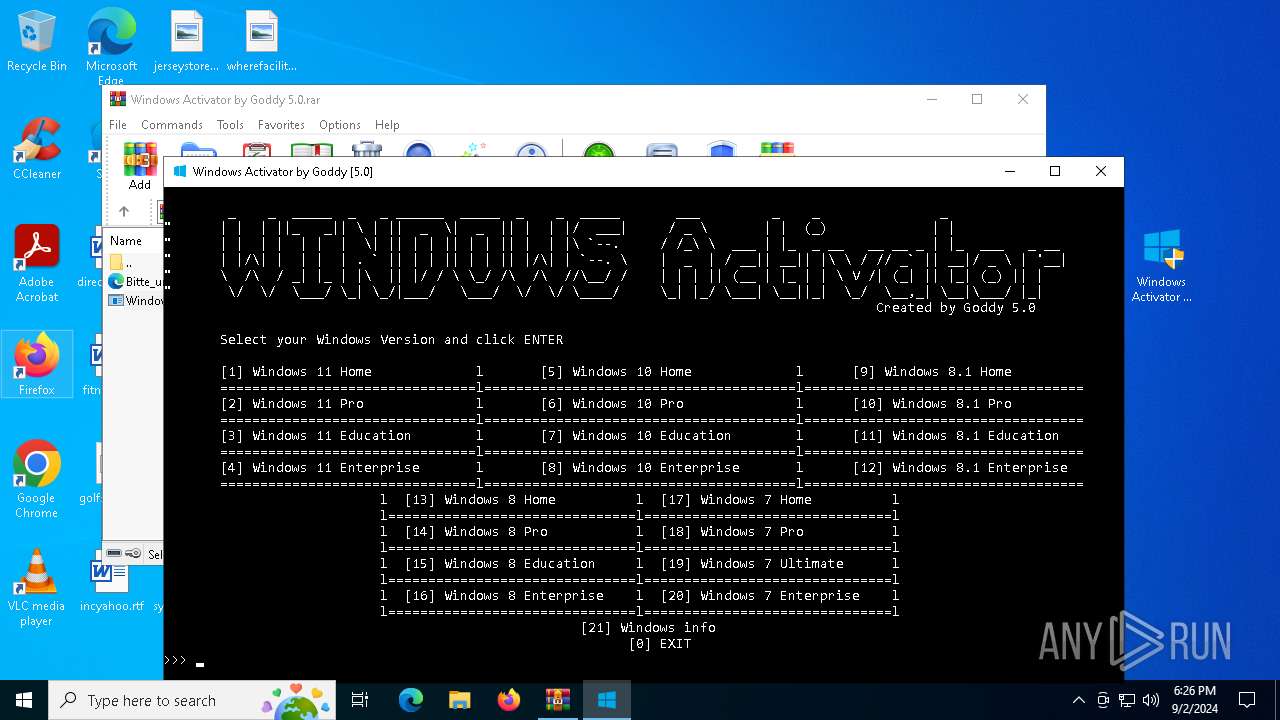
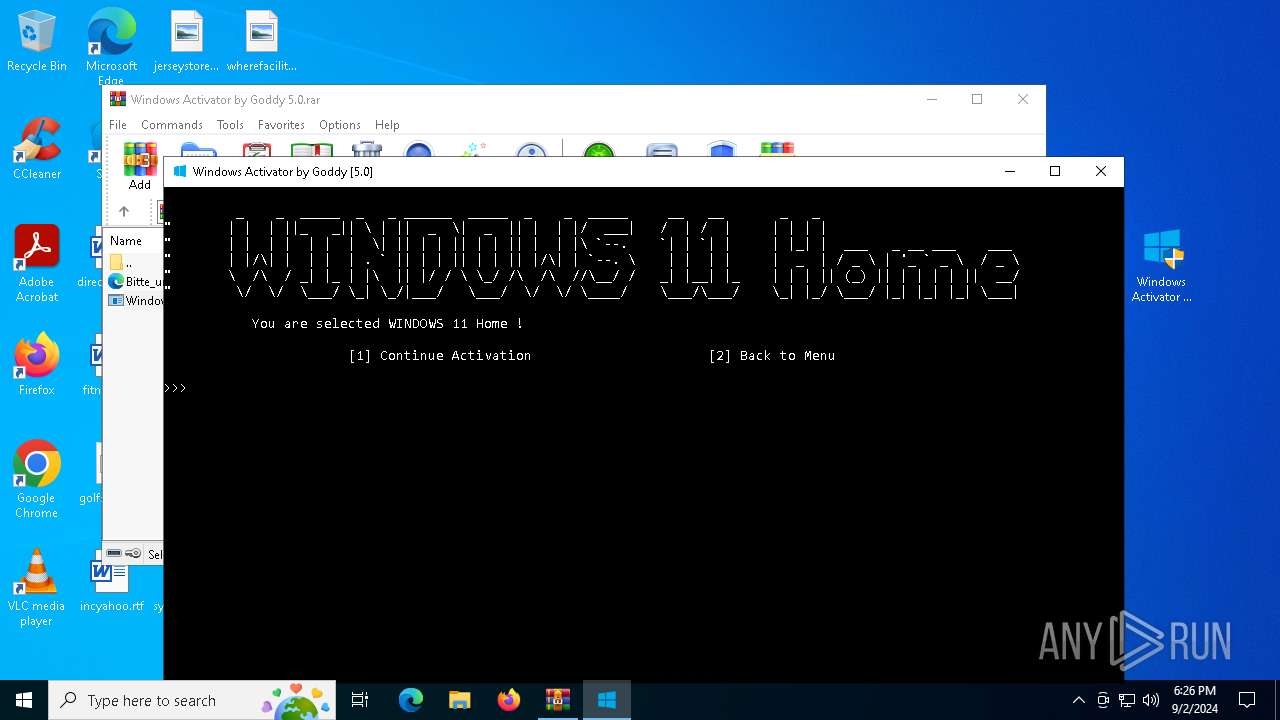
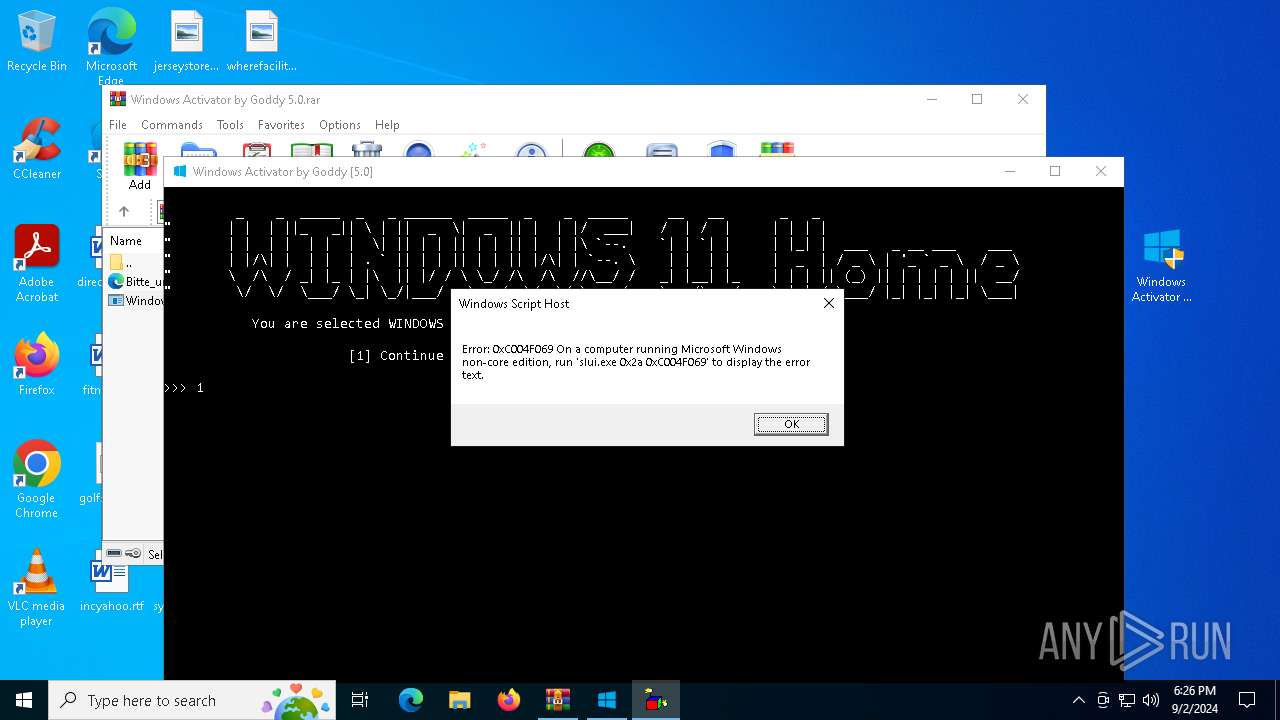
| File name: | Windows Activator by Goddy 5.0.rar |
| Full analysis: | https://app.any.run/tasks/a596810e-7773-4aa4-80c5-26086fc943f0 |
| Verdict: | Malicious activity |
| Analysis date: | September 02, 2024, 18:25:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | F4CE977B205649E0858FC14B359F00D1 |
| SHA1: | 286C92D1D250D9F607699A0F0DF1BE30D59B7D70 |
| SHA256: | 688BC9DD64653E06294C0A78AC70D28873867AC1620464ED63795E6AA3B04AC0 |
| SSDEEP: | 12288:korw+Cf09UbzIP8PejXSiMW9qSmghh5WG7f:kKw+Cf0mbzIMRiMW9qrghSG7f |
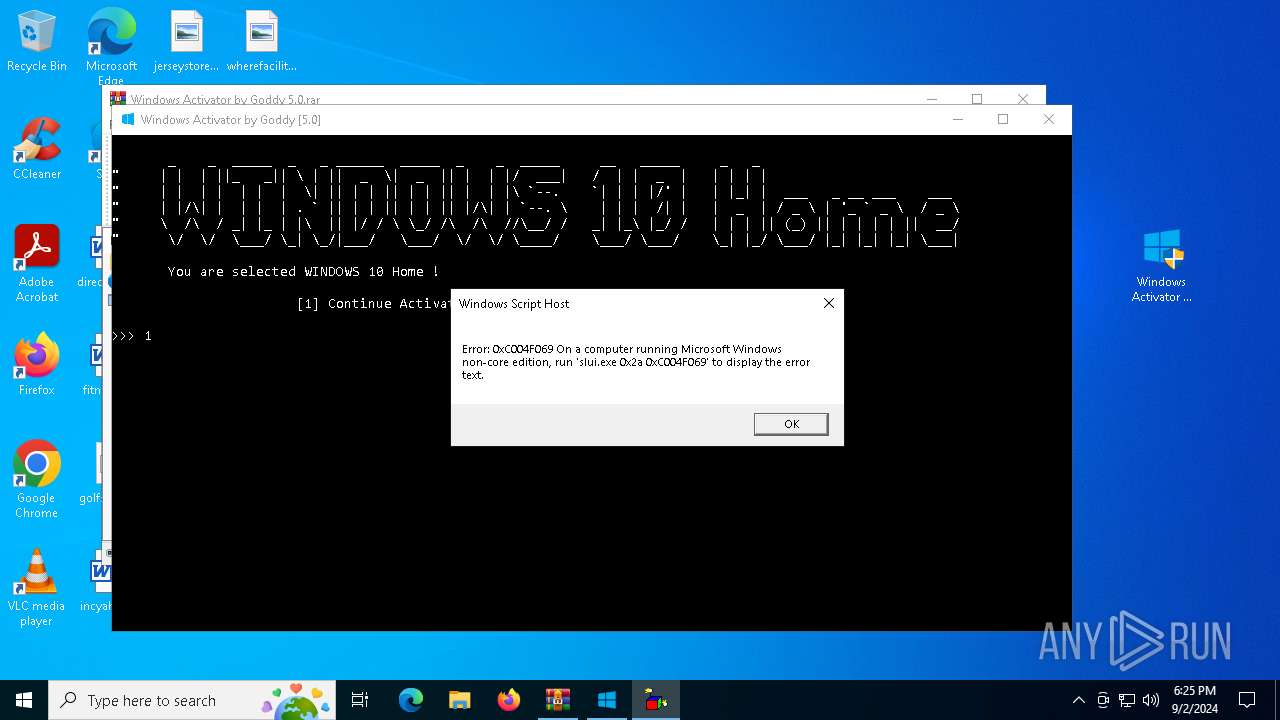
MALICIOUS
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- wscript.exe (PID: 6324)
SUSPICIOUS
The executable file from the user directory is run by the CMD process
- gkey.exe (PID: 7008)
- 7z2201.exe (PID: 1116)
- gkey.exe (PID: 6168)
Get information on the list of running processes
- cmd.exe (PID: 5172)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 3112)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 6004)
- cmd.exe (PID: 5148)
Starts CMD.EXE for commands execution
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
- gkey.exe (PID: 6168)
- gkey.exe (PID: 7008)
- cmd.exe (PID: 5172)
- cmd.exe (PID: 5148)
The process verifies whether the antivirus software is installed
- cmd.exe (PID: 5172)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5172)
Hides command output
- cmd.exe (PID: 6000)
- cmd.exe (PID: 736)
- cmd.exe (PID: 6536)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 3540)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6000)
- cmd.exe (PID: 6536)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 736)
- cmd.exe (PID: 3540)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 6016)
- WMIC.exe (PID: 6656)
- WMIC.exe (PID: 6400)
- WMIC.exe (PID: 6796)
- WMIC.exe (PID: 1932)
Executable content was dropped or overwritten
- curl.exe (PID: 6576)
- 7z2201.exe (PID: 1116)
Drops 7-zip archiver for unpacking
- curl.exe (PID: 6576)
- 7z2201.exe (PID: 1116)
Creates a software uninstall entry
- 7z2201.exe (PID: 1116)
Checks for external IP
- curl.exe (PID: 6284)
- curl.exe (PID: 6784)
- svchost.exe (PID: 2256)
Creates/Modifies COM task schedule object
- 7z2201.exe (PID: 1116)
Runs PING.EXE to delay simulation
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
Reads security settings of Internet Explorer
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
Reads the date of Windows installation
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
The process executes VB scripts
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
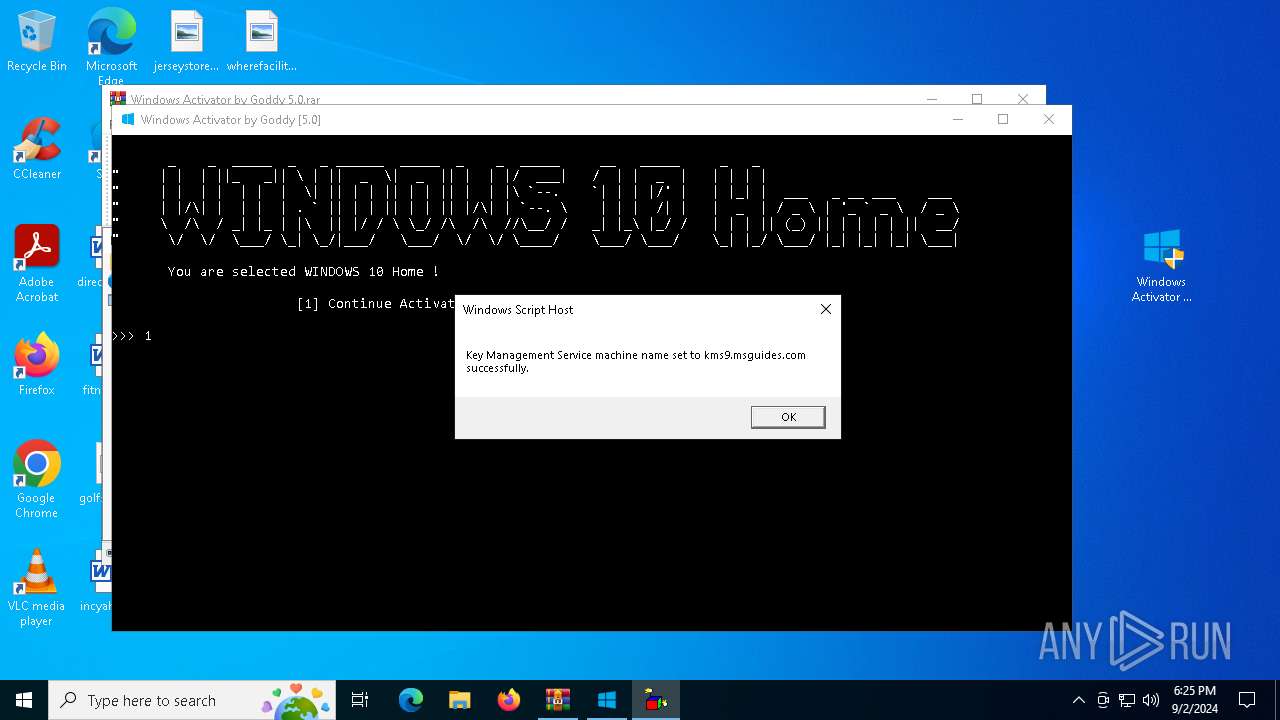
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6324)
- wscript.exe (PID: 4364)
- wscript.exe (PID: 6100)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6324)
- wscript.exe (PID: 4364)
- wscript.exe (PID: 6100)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6324)
- wscript.exe (PID: 4364)
- wscript.exe (PID: 6100)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5172)
- cmd.exe (PID: 5148)
Executing commands from a ".bat" file
- gkey.exe (PID: 7008)
- gkey.exe (PID: 6168)
Application launched itself
- cmd.exe (PID: 5172)
- cmd.exe (PID: 5148)
Uses WMIC.EXE
- cmd.exe (PID: 6736)
- cmd.exe (PID: 2684)
INFO
Manual execution by a user
- Windows Activator by Goddy.exe (PID: 6744)
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 6396)
- Windows Activator by Goddy.exe (PID: 3540)
Create files in a temporary directory
- Windows Activator by Goddy.exe (PID: 4680)
- gkey.exe (PID: 7008)
- curl.exe (PID: 6576)
- curl.exe (PID: 7160)
- Windows Activator by Goddy.exe (PID: 3540)
- gkey.exe (PID: 6168)
Checks supported languages
- Windows Activator by Goddy.exe (PID: 4680)
- gkey.exe (PID: 7008)
- mode.com (PID: 1932)
- curl.exe (PID: 6284)
- curl.exe (PID: 6784)
- curl.exe (PID: 7020)
- curl.exe (PID: 6576)
- 7z2201.exe (PID: 1116)
- curl.exe (PID: 7160)
- Windows Activator by Goddy.exe (PID: 3540)
- gkey.exe (PID: 6168)
- mode.com (PID: 3144)
The process uses the downloaded file
- WinRAR.exe (PID: 6592)
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7020)
- WMIC.exe (PID: 6016)
- WMIC.exe (PID: 6656)
- WMIC.exe (PID: 6400)
- WMIC.exe (PID: 6796)
- WMIC.exe (PID: 1932)
- WMIC.exe (PID: 1076)
Reads the computer name
- curl.exe (PID: 6784)
- curl.exe (PID: 6284)
- curl.exe (PID: 7020)
- curl.exe (PID: 6576)
- curl.exe (PID: 7160)
- 7z2201.exe (PID: 1116)
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
Creates files in the program directory
- 7z2201.exe (PID: 1116)
Reads Microsoft Office registry keys
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
Process checks computer location settings
- Windows Activator by Goddy.exe (PID: 4680)
- Windows Activator by Goddy.exe (PID: 3540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1193 |
|---|---|
| UncompressedSize: | 2733 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2024:06:27 19:24:50 |
| PackingMethod: | Normal |
| ArchivedFileName: | Windows Activator by Goddy 5.0\Bitte_um_Unterstuetzung.html |
Total processes
199
Monitored processes
73
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | tasklist /fi "imagename eq SbieSvc.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | net session | C:\Windows\System32\net.exe | — | Windows Activator by Goddy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /S /D /c" ( findstr /ilc:"Windows 8" 1>nul )" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | wmic path win32_LocalTime Get Day,Month,Year /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\AppData\Local\Temp\7z2201.exe" /S | C:\Users\admin\AppData\Local\Temp\7z2201.exe | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 22.01 Modules
| |||||||||||||||
| 1164 | reg query "HKLM\SOFTWARE\Microsoft\Alu" /s /reg:32 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | C:\WINDOWS\system32\cmd.exe /c tasklist /fi "imagename eq QHActiveDefense.exe" /fo csv /nh | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1932 | mode 120, 31 | C:\Windows\System32\mode.com | — | Windows Activator by Goddy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1932 | wmic os get caption | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | tasklist /fi "imagename eq ekrn.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 560
Read events
17 513
Write events
47
Delete events
0
Modification events
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows Activator by Goddy 5.0.rar | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1116) 7z2201.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path32 |
Value: C:\Program Files (x86)\7-Zip\ | |||
| (PID) Process: | (1116) 7z2201.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files (x86)\7-Zip\ | |||
Executable files
9
Suspicious files
6
Text files
103
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | 7z2201.exe | C:\Program Files (x86)\7-Zip\7-zip.chm | chm | |
MD5:34208890A28244903621CD32CC3FBDFC | SHA256:4B6939646570C9DDB5BFD39B8503EED99D8C64337E72F6DD4F9DDCFB4AC76703 | |||
| 6592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6592.34067\Windows Activator by Goddy 5.0\Windows Activator by Goddy.exe | compressed | |
MD5:A99FF6B3A46D09197AA217FA0EECD8DA | SHA256:B212D71F422A7E17FED6E046E47A2337BA30DFAF63223D6CFA70E6F0751419BC | |||
| 7008 | gkey.exe | C:\Users\admin\AppData\Local\Temp\qb12D624.C2\cnf | text | |
MD5:A6A4651EE111B5A171E45C4248E2F98C | SHA256:4EEAFFBFD77C858DE4845D80BB079DE90F1088A30DBEE85AE1377EEF4B6C8675 | |||
| 1116 | 7z2201.exe | C:\Program Files (x86)\7-Zip\Lang\af.txt | text | |
MD5:FBBE51ACB879B525CC6B19D386697924 | SHA256:3793FB69EE9FD958CF15A272B1ED54E4B3D75592836EBCD085DC0E7B1400D1CB | |||
| 5172 | cmd.exe | C:\Users\admin\AppData\Local\Temp\cnf | text | |
MD5:A6A4651EE111B5A171E45C4248E2F98C | SHA256:4EEAFFBFD77C858DE4845D80BB079DE90F1088A30DBEE85AE1377EEF4B6C8675 | |||
| 1116 | 7z2201.exe | C:\Program Files (x86)\7-Zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 6576 | curl.exe | C:\Users\admin\AppData\Local\Temp\7z2201.exe | executable | |
MD5:734E95CDBE04F53FE7C28EEAAAAD7327 | SHA256:8C8FBCF80F0484B48A07BD20E512B103969992DBF81B6588832B08205E3A1B43 | |||
| 7008 | gkey.exe | C:\Users\admin\AppData\Local\Temp\02M0PYPS.bat | text | |
MD5:2FA8921F764DCD0C06343FE7A892599D | SHA256:87C38F89B60880617CC295B79E93747A62ECC23E4A466DDDB054A4DD5A9B40AE | |||
| 1116 | 7z2201.exe | C:\Program Files (x86)\7-Zip\Lang\be.txt | text | |
MD5:3C21135144AC7452E7DB66F0214F9D68 | SHA256:D095879B8BBC67A1C9875C5E9896942BACF730BD76155C06105544408068C59E | |||
| 1116 | 7z2201.exe | C:\Program Files (x86)\7-Zip\Lang\bg.txt | text | |
MD5:833AFB4F88FDB5F48245C9B65577DC19 | SHA256:4DCABCC8AB8069DB79143E4C62B6B76D2CF42666A09389EACFC35074B61779E3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
28
DNS requests
18
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6816 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2584 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2584 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6056 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6816 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6816 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6784 | curl.exe | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ipinfo.io |
| shared |
c.zeltitmp.net |
| unknown |
www.7-zip.org |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6784 | curl.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
6784 | curl.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
6284 | curl.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
6284 | curl.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |