| File name: | Discord Auto Typer.exe |
| Full analysis: | https://app.any.run/tasks/7a50d204-3d87-4997-88c2-562a7b4016d6 |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 20:02:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | AE6CC2261D637FDB625FA9080F309E47 |
| SHA1: | 748803AB927A74DE55E0E4D99937634CCB597CE8 |
| SHA256: | 68832075FBC41BF7754A809B6781B13D85B131677ABFA38AEAA65954D4B4EE36 |
| SSDEEP: | 768:2vpQF6Z9Vl9kPwiUXt68t3O7+kB1bA/LwGxkq:2vja2U8t3OikB6jwlq |
MALICIOUS
Actions looks like stealing of personal data
- Discord Auto Typer.exe (PID: 116)
SUSPICIOUS
Reads the Internet Settings
- Discord Auto Typer.exe (PID: 116)
INFO
Checks supported languages
- Discord Auto Typer.exe (PID: 116)
Drops the executable file immediately after the start
- Discord Auto Typer.exe (PID: 116)
Reads the machine GUID from the registry
- Discord Auto Typer.exe (PID: 116)
Manual execution by a user
- control.exe (PID: 296)
- rundll32.exe (PID: 268)
- control.exe (PID: 1804)
Checks transactions between databases Windows and Oracle
- rundll32.exe (PID: 268)
Reads the computer name
- Discord Auto Typer.exe (PID: 116)
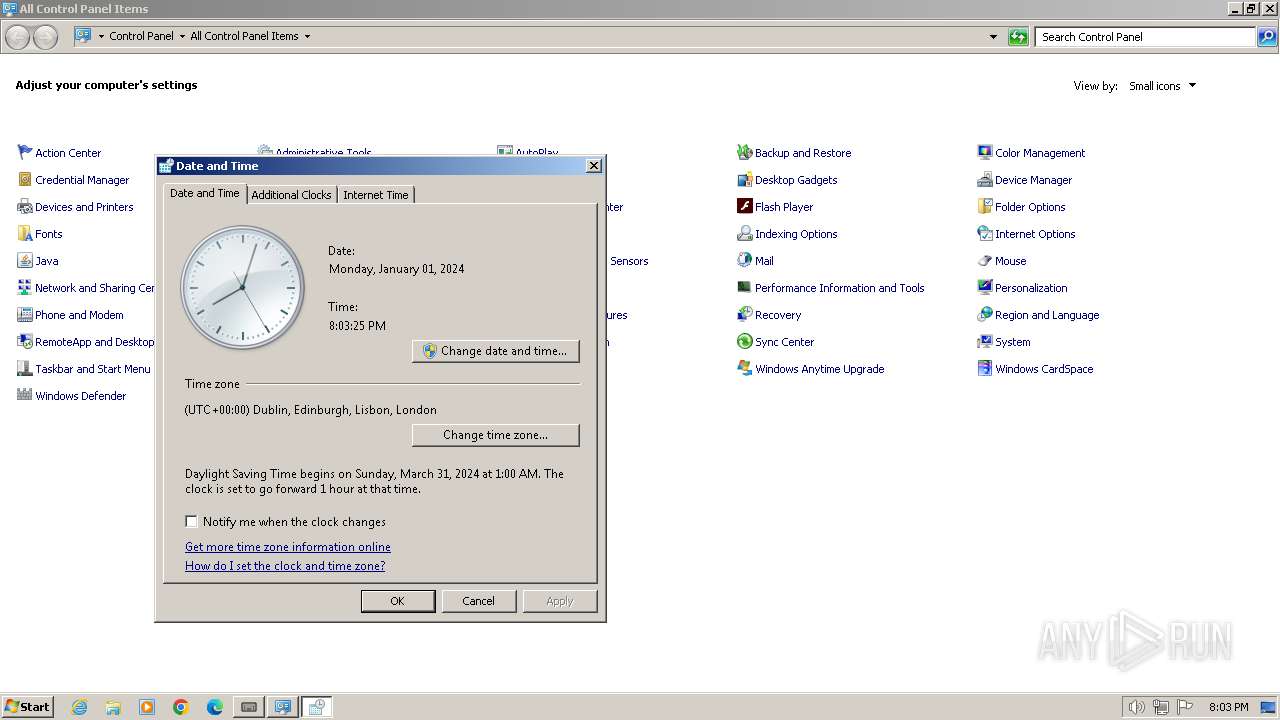
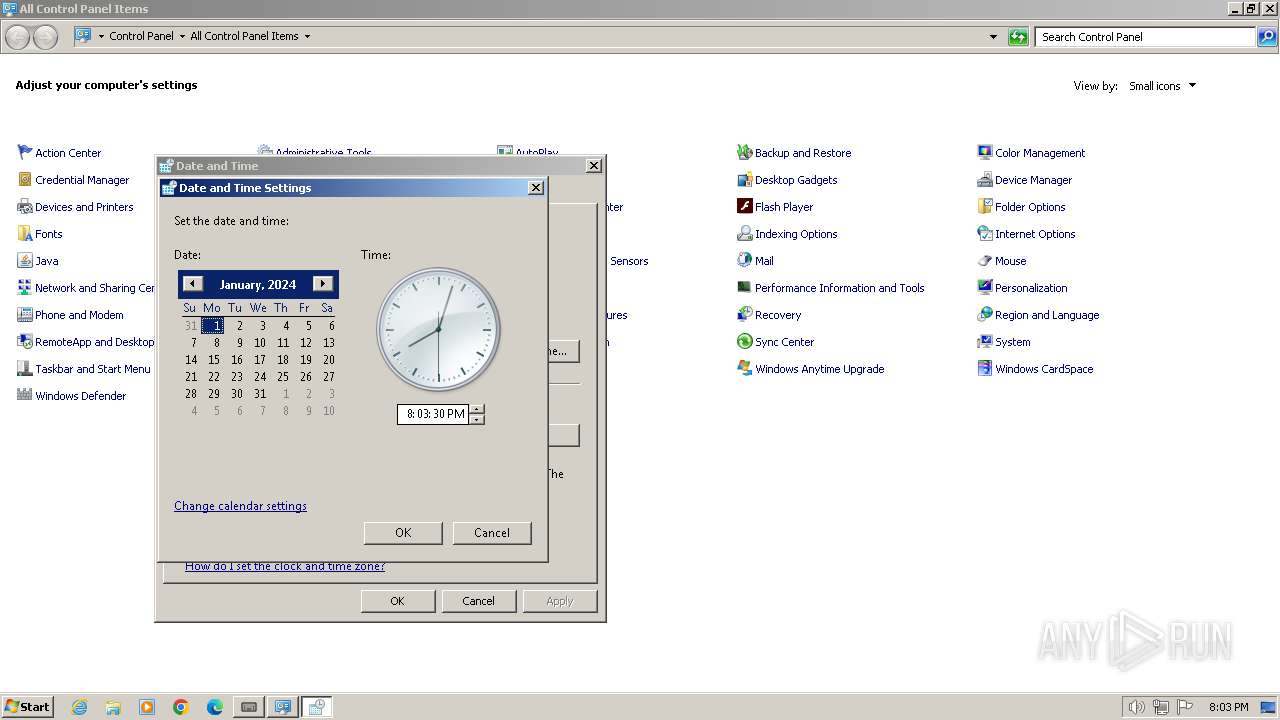
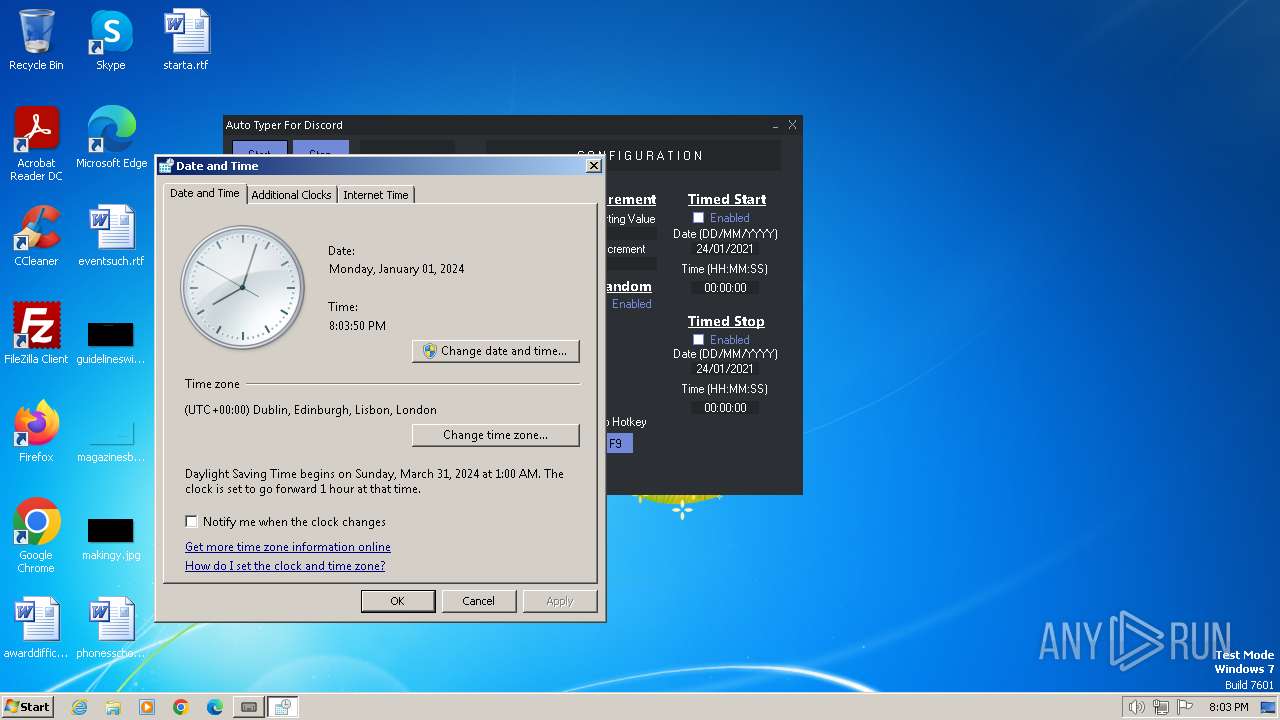
Reads the time zone
- rundll32.exe (PID: 268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (72.2) |
|---|---|---|
| .scr | | | Windows screen saver (12.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.4) |
| .exe | | | Win32 Executable (generic) (4.4) |
| .exe | | | Generic Win/DOS Executable (1.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2070:04:18 14:36:06+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 58880 |
| InitializedDataSize: | 6656 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1045e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
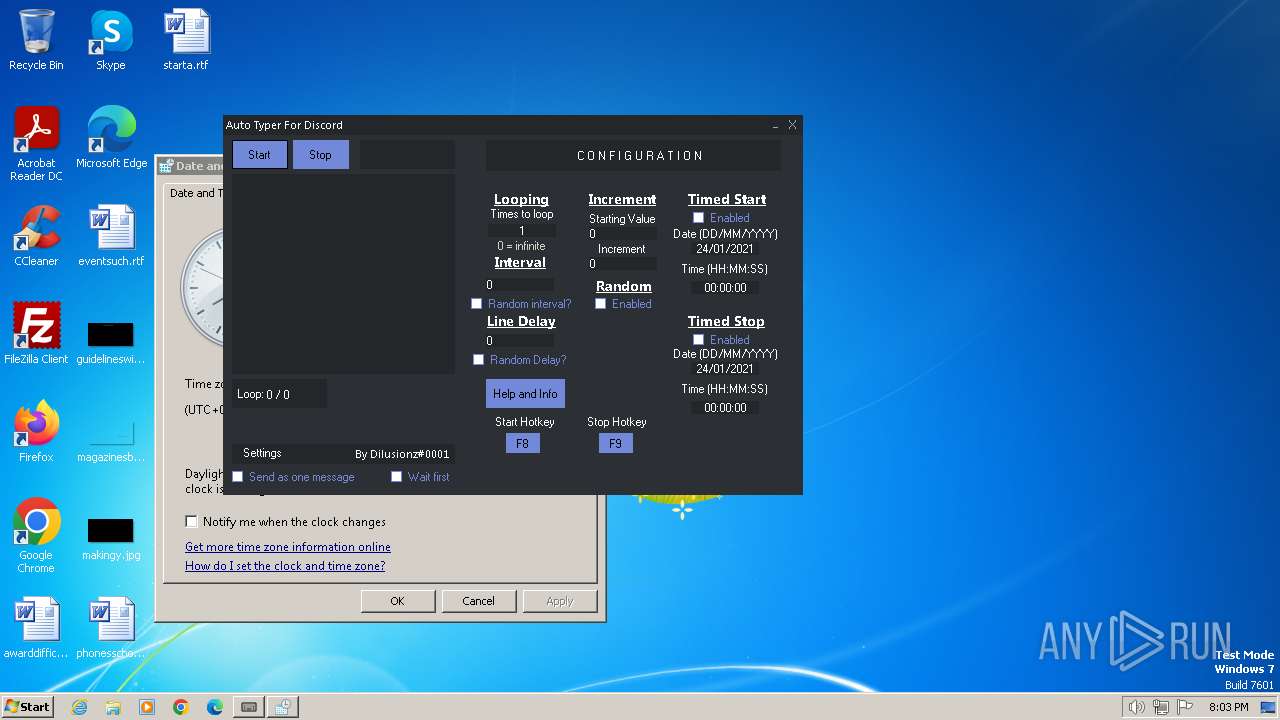
| FileDescription: | Dilusionz Discord Auto Typer |
| FileVersion: | 1.0.0.0 |
| InternalName: | Dilusionz Discord Auto Typer.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | Dilusionz Discord Auto Typer.exe |
| ProductName: | Dilusionz Discord Auto Typer |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
39
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\Discord Auto Typer.exe" | C:\Users\admin\AppData\Local\Temp\Discord Auto Typer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Dilusionz Discord Auto Typer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 268 | "C:\Windows\System32\rundll32.exe" C:\Windows\System32\shell32.dll,Control_RunDLL C:\Windows\System32\timedate.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | "C:\Windows\System32\control.exe" | C:\Windows\System32\control.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1316 | C:\Windows\system32\DllHost.exe /Processid:{9DF523B0-A6C0-4EA9-B5F1-F4565C3AC8B8} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1804 | "C:\Windows\System32\control.exe" | C:\Windows\System32\control.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
415
Read events
407
Write events
8
Delete events
0
Modification events
| (PID) Process: | (116) Discord Auto Typer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) Discord Auto Typer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) Discord Auto Typer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) Discord Auto Typer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |