| File name: | MobaXterm_Personal_12.4.exe |
| Full analysis: | https://app.any.run/tasks/81680cf3-ef76-40d2-9e34-637787070200 |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2020, 16:02:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3420955385C80C089F0EBA2A9A7B7948 |
| SHA1: | BAAB067725D37A3B02D879BF07217408DCF43E04 |
| SHA256: | 6875EACD0320931BFCB3F3676771CDDA3F9DE4B5A0F1DBC1B9AA3CA2D3DA1951 |
| SSDEEP: | 196608:sWho9veLQgwChH22Jc+gi4qij7FKPgWSik8R9FIshnM6jcG2oQ+iE:sA8WC2uUlijROgWSikqVfjaoJ |
MALICIOUS
Application was dropped or rewritten from another process
- motty.exe (PID: 3248)
- motty.exe (PID: 3168)
- xkbcomp_w32.exe (PID: 4088)
- XWin_MobaX.exe (PID: 2372)
Loads dropped or rewritten executable
- xkbcomp_w32.exe (PID: 4088)
- XWin_MobaX.exe (PID: 2372)
SUSPICIOUS
Connects to unusual port
- motty.exe (PID: 3168)
- motty.exe (PID: 3248)
Executable content was dropped or overwritten
- MobaXterm_Personal_12.4.exe (PID: 2876)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (53.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (17.5) |
| .scr | | | Windows screen saver (16.1) |
| .exe | | | Win32 Executable (generic) (5.5) |
| .exe | | | Win16/32 Executable Delphi generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:11:11 01:00:00+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 6213120 |
| InitializedDataSize: | 8410624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5ebe8c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.4.0.4248 |
| ProductVersionNumber: | 12.4.0.4248 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Mobatek |
| FileDescription: | MobaXterm |
| FileVersion: | 12.4.0.4248 |
| InternalName: | MobaXterm |
| LegalCopyright: | Mobatek - https://mobaxterm.mobatek.net |
| LegalTrademarks: | Mobatek - https://mobaxterm.mobatek.net |
| OriginalFileName: | MobaXterm |
| ProductName: | MobaXterm |
| ProductVersion: | 12.4 |
| Comments: | https://mobaxterm.mobatek.net |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Nov-2019 00:00:00 |
| Detected languages: |
|
| CompanyName: | Mobatek |
| FileDescription: | MobaXterm |
| FileVersion: | 12.4.0.4248 |
| InternalName: | MobaXterm |
| LegalCopyright: | Mobatek - https://mobaxterm.mobatek.net |
| LegalTrademarks: | Mobatek - https://mobaxterm.mobatek.net |
| OriginalFilename: | MobaXterm |
| ProductName: | MobaXterm |
| ProductVersion: | 12.4 |
| Comments: | https://mobaxterm.mobatek.net |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 11-Nov-2019 00:00:00 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x005ECC8C | 0x005ECE00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59179 |
DATA | 0x005EE000 | 0x00086120 | 0x00086200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.17796 |
BSS | 0x00675000 | 0x000288F5 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0069E000 | 0x00004AC0 | 0x00004C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.04394 |
.tls | 0x006A3000 | 0x00000040 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x006A4000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.20692 |
.reloc | 0x006A5000 | 0x00056148 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x006FC000 | 0x00724400 | 0x00724400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 7.96278 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.03446 | 1738 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.27987 | 9640 | UNKNOWN | French - France | RT_ICON |
3 | 3.60944 | 4264 | UNKNOWN | French - France | RT_ICON |
4 | 3.77446 | 2440 | UNKNOWN | French - France | RT_ICON |
5 | 4.01242 | 1128 | UNKNOWN | French - France | RT_ICON |
6 | 2.62527 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
7 | 2.91604 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
8 | 1.0999 | 4268 | UNKNOWN | English - United States | RT_CURSOR |
9 | 1.95679 | 4268 | UNKNOWN | English - United States | RT_CURSOR |
10 | 1.07477 | 4268 | UNKNOWN | English - United States | RT_CURSOR |
Imports
IPHLPAPI.DLL |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
crypt32.dll |
gdi32.dll |
gdiplus.dll |
imm32.dll |
kernel32.dll |
netapi32.dll |
Total processes
39
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
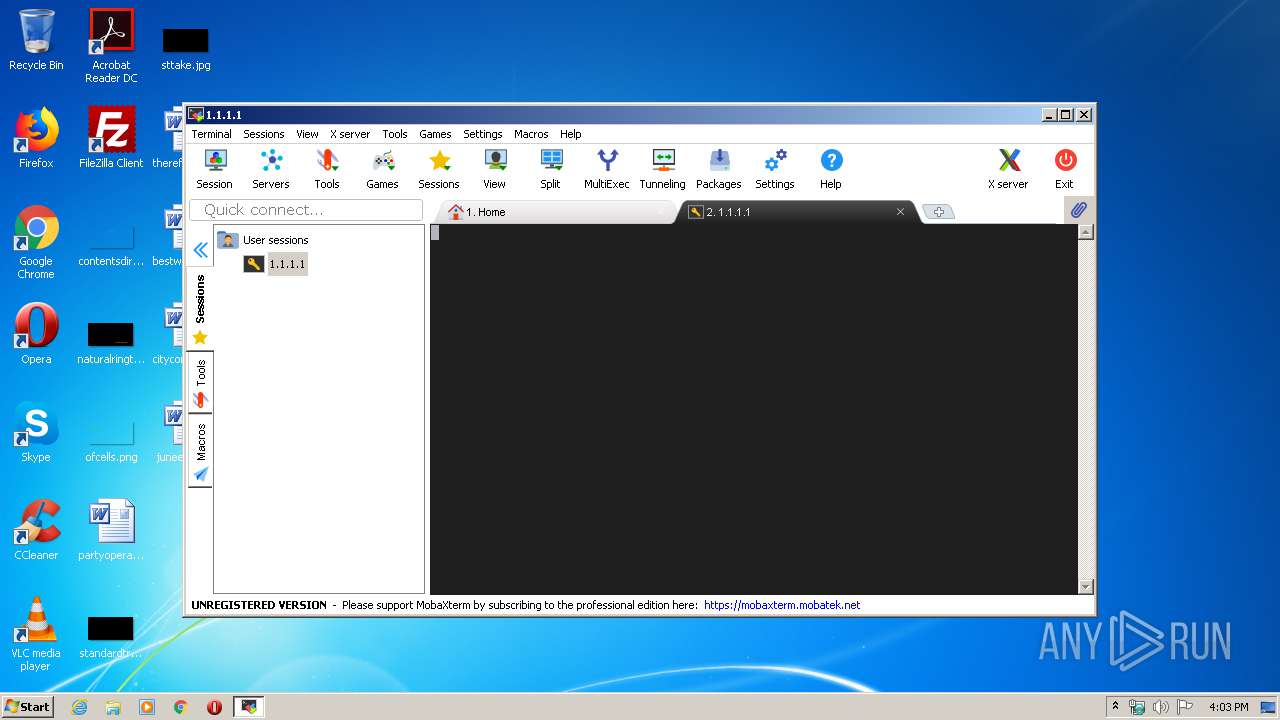
| 2372 | "C:\Users\admin\AppData\Local\Temp\Mxt124\bin\XWin_MobaX.exe" -silent-dup-error -notrayicon -nolisten inet6 -hostintitle +bs -clipboard -nowgl -multiwindow -noreset :0 | C:\Users\admin\AppData\Local\Temp\Mxt124\bin\XWin_MobaX.exe | MobaXterm_Personal_12.4.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\AppData\Local\Temp\MobaXterm_Personal_12.4.exe" | C:\Users\admin\AppData\Local\Temp\MobaXterm_Personal_12.4.exe | explorer.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaXterm Exit code: 0 Version: 12.4.0.4248 Modules
| |||||||||||||||
| 3168 | "C:\Users\admin\AppData\Local\Temp\Mxt124\bin\motty.exe" -load "TERM2626262" | C:\Users\admin\AppData\Local\Temp\Mxt124\bin\motty.exe | MobaXterm_Personal_12.4.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: Terminal emulator based on PuTTY Exit code: 0 Version: Release 0.71 (without embedded help) Modules
| |||||||||||||||
| 3248 | "C:\Users\admin\AppData\Local\Temp\Mxt124\bin\motty.exe" -load "TERM2626263" | C:\Users\admin\AppData\Local\Temp\Mxt124\bin\motty.exe | MobaXterm_Personal_12.4.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: Terminal emulator based on PuTTY Exit code: 0 Version: Release 0.71 (without embedded help) Modules
| |||||||||||||||
| 4088 | "C:\Users\admin\AppData\Local\Temp\Mxt124\bin\xkbcomp_w32.exe" -w 1 "-RC:\Users\admin\AppData\Local\Temp\Mxt124\usr\share\X11\xkb" -xkm "C:\Users\admin\AppData\Local\Temp\Mxt124\var\log\xwin\xkb_a02936" -em1 "The XKEYBOARD keymap compiler (xkbcomp) reports:" -emp "> " -eml "Errors from xkbcomp are not fatal to the X server" "C:\Users\admin\AppData\Local\Temp\Mxt124\var\log\xwin\server-0.xkm" | C:\Users\admin\AppData\Local\Temp\Mxt124\bin\xkbcomp_w32.exe | — | XWin_MobaX.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
925
Read events
383
Write events
542
Delete events
0
Modification events
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | WindowClass |
Value: CMoTTY | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | DarkMode |
Value: 0 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | LogguerDansMobaXterm |
Value: 0 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | utf8linedraw |
Value: 1 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | NoRemoteResize |
Value: 1 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | ScrollbarOnLeft |
Value: 0 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | EraseToScrollback |
Value: 1 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | ScrollOnDisp |
Value: 0 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | ScrollOnKey |
Value: 1 | |||
| (PID) Process: | (2876) MobaXterm_Personal_12.4.exe | Key: | HKEY_CURRENT_USER\Software\MobaXterm\MoTTY\Sessions\TERM2626261 |
| Operation: | write | Name: | ScrollBarFullScreen |
Value: 1 | |||
Executable files
40
Suspicious files
61
Text files
473
Unknown types
113
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\etc\profile | text | |
MD5:— | SHA256:— | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\etc\fstab | text | |
MD5:7EE8890036F42CCAE32C7490178AF453 | SHA256:83D65C81E692BF7C285B2272391C0E863CEA11A94CC13056AFE40CEECDAE60BD | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\cygdrive | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\etc\ssh_config | text | |
MD5:7CEB8529CB9FBE96FA321424D4C2681B | SHA256:8F1265583B3480A2F0D3F2FA6AFE347E26FDD5C975CB3285F4C74FB2335F9C49 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\mnt | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\mx86_64b\media | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\registry | binary | |
MD5:12DCC755A41FFE9983DFC47E545B132D | SHA256:8D7D8B8FDEC94104B0EE6A90665106B02A8ECC705EAF33DAA91FC83AEDD7CF18 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\mx86_64b\mnt | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\mx86_64b\registry | binary | |
MD5:12DCC755A41FFE9983DFC47E545B132D | SHA256:8D7D8B8FDEC94104B0EE6A90665106B02A8ECC705EAF33DAA91FC83AEDD7CF18 | |||
| 2876 | MobaXterm_Personal_12.4.exe | C:\Users\admin\AppData\Local\Temp\Mxt124\mx86_64b\cygdrive | binary | |
MD5:2064A8DFFC77A2130D9F64018604769E | SHA256:D7F3656E9078257BD9B7558EE2D01E94D3C30B81F035FA3417B745139C9ECCB8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
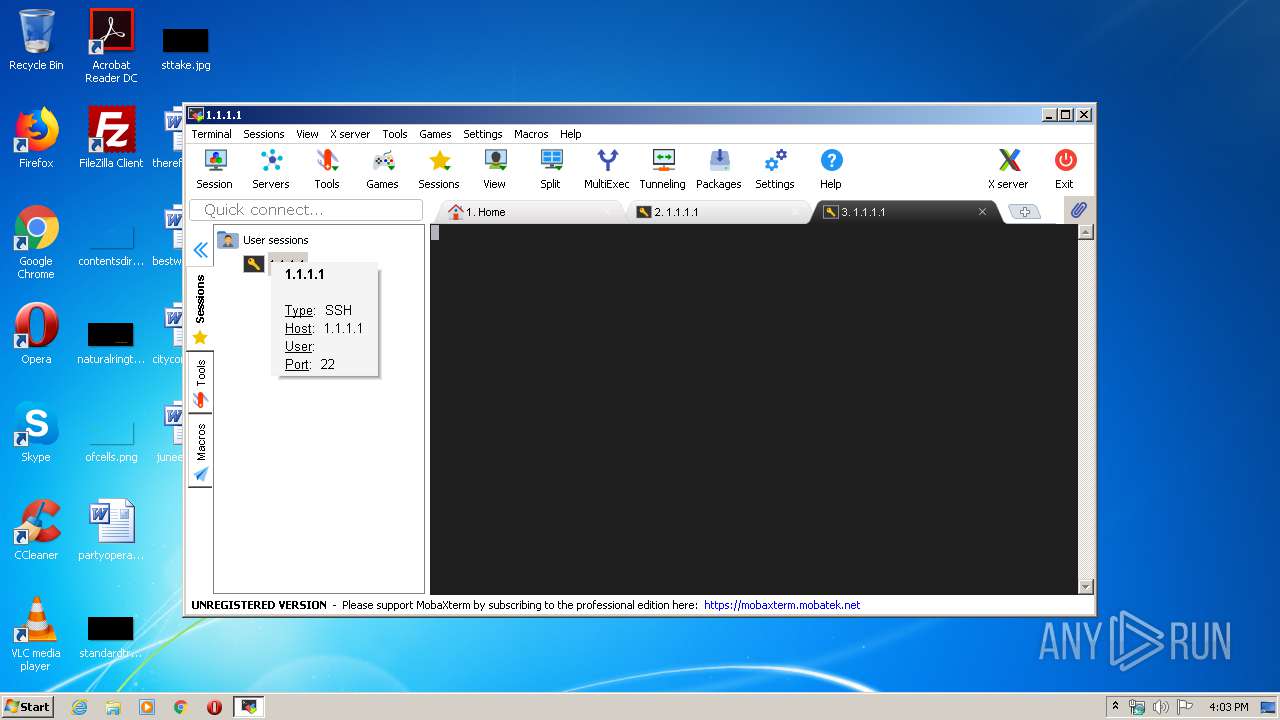
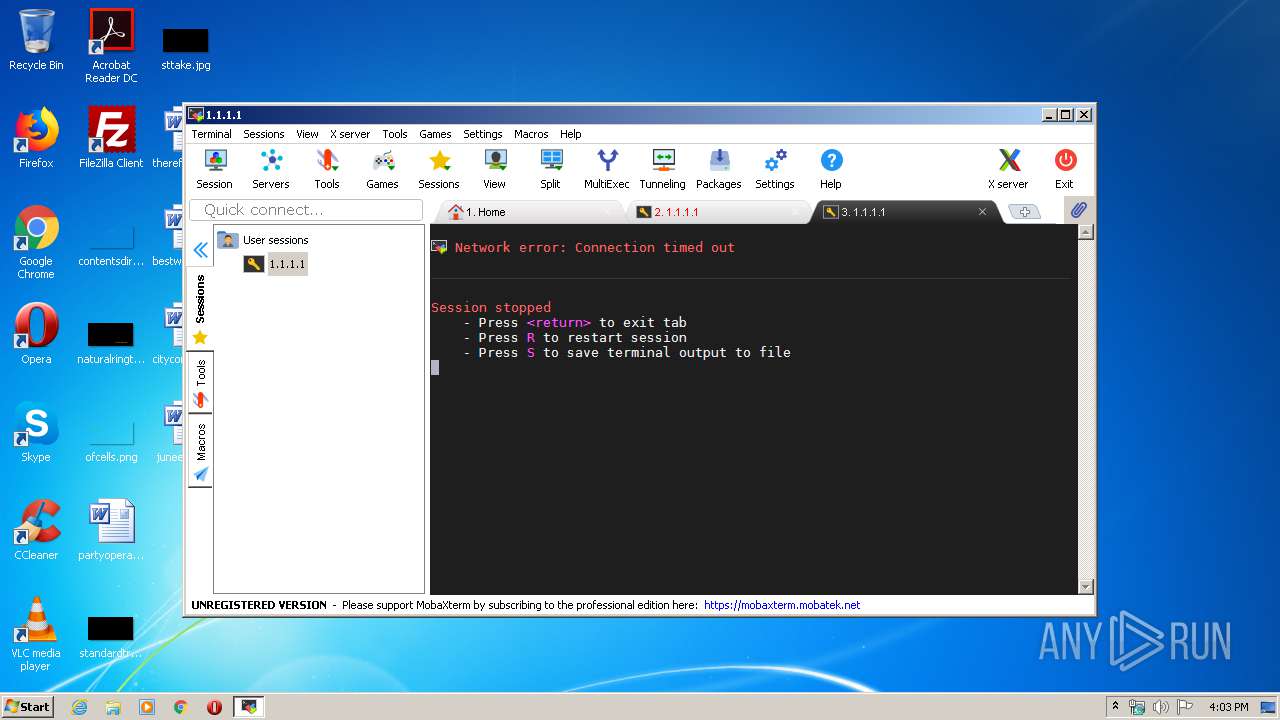
3248 | motty.exe | 1.1.1.1:22 | — | — | AU | malicious |
3168 | motty.exe | 1.1.1.1:22 | — | — | AU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3168 | motty.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |