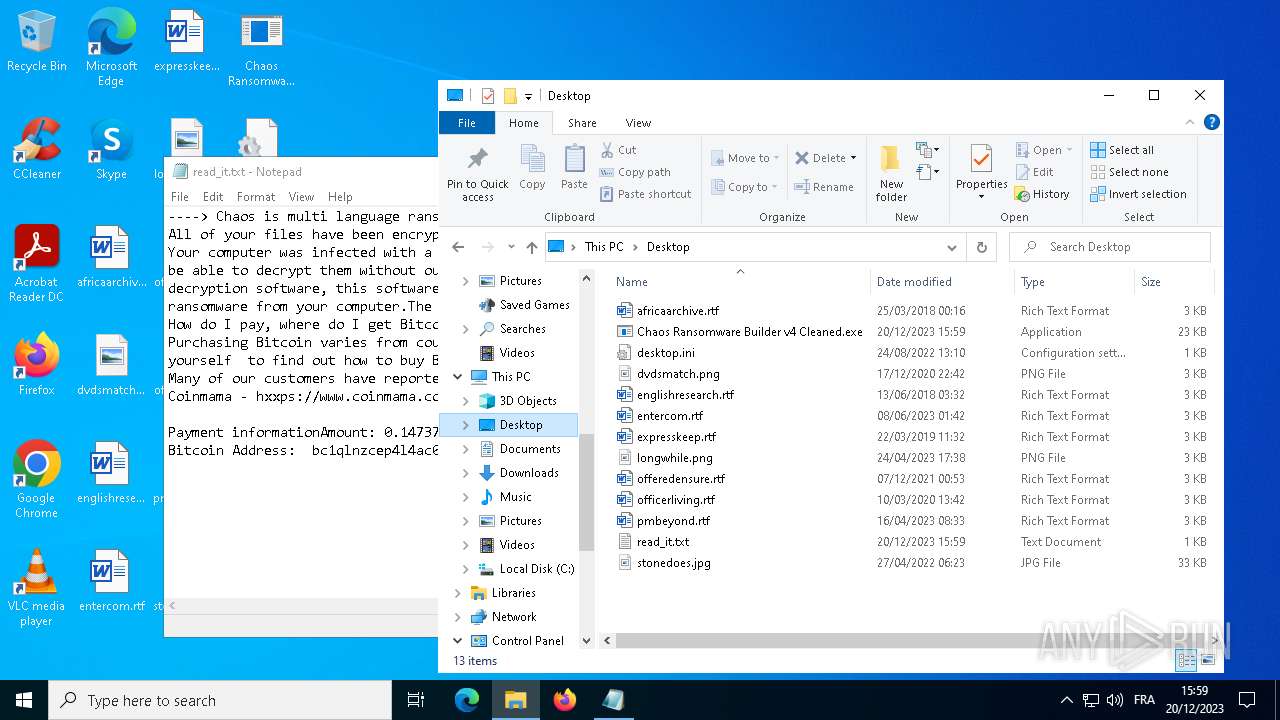
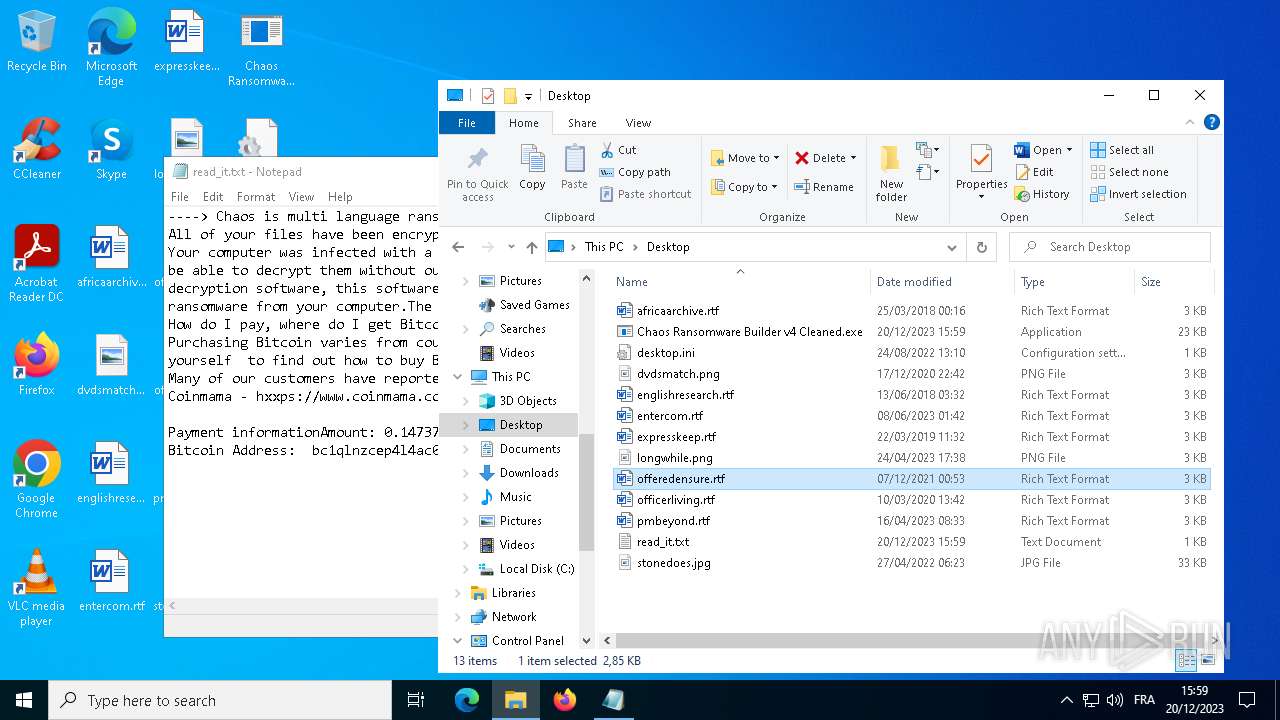
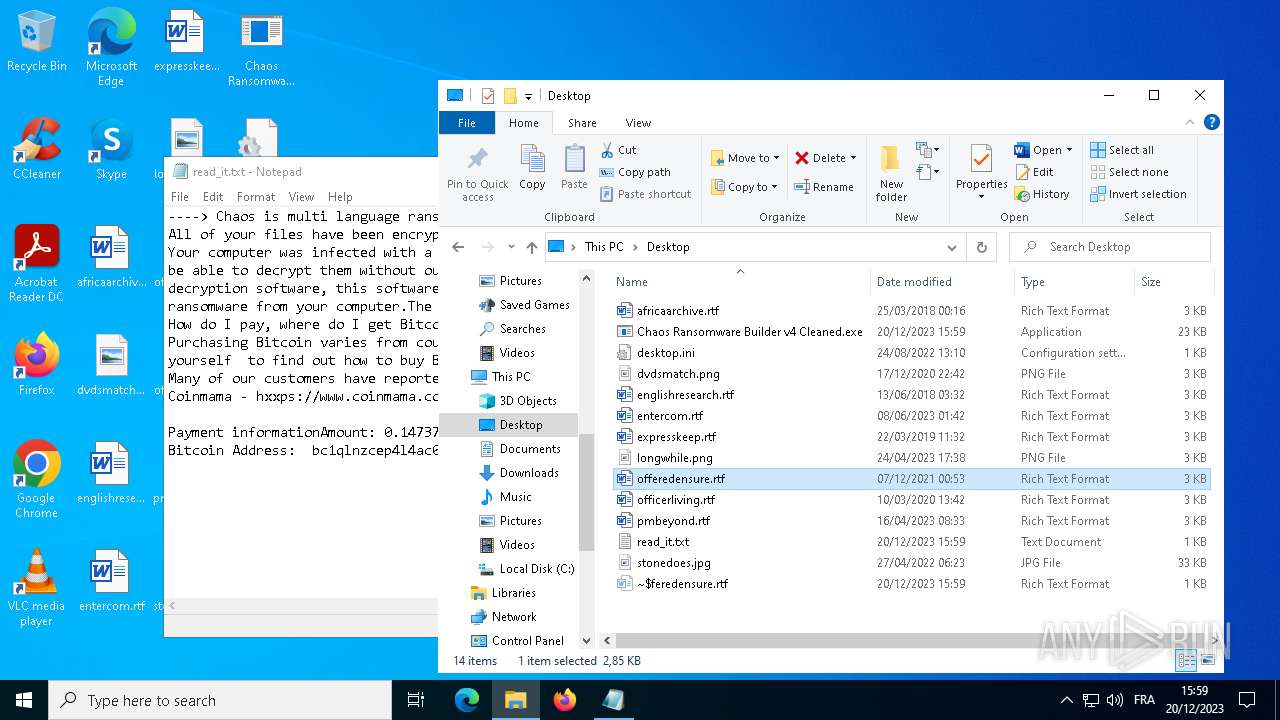
| File name: | Chaos Ransomware Builder v4 Cleaned.exe |
| Full analysis: | https://app.any.run/tasks/ebd2ad01-f43d-4f82-8b11-573d2d440b5b |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2023, 14:59:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F58B7A3390B3C754D0552E17BAC36A2C |
| SHA1: | 1E9EB8AB27759EA8AEA8F42533001B58CB43DB14 |
| SHA256: | 6822025C1206B527C867880C647E5861DDEBBD5BF25DAF396BAEDBAADE2FA0FD |
| SSDEEP: | 384:nuh9yeBxz0zfoeByL+/wC+YyFRRzJor91CM4b5prhtw:Xkxz0zfo4yS/wCCnVor9h4b7r8 |
MALICIOUS
Drops the executable file immediately after the start
- Chaos Ransomware Builder v4 Cleaned.exe (PID: 1828)
Create files in the Startup directory
- svchost.exe (PID: 2292)
Actions looks like stealing of personal data
- svchost.exe (PID: 2292)
SUSPICIOUS
The process creates files with name similar to system file names
- Chaos Ransomware Builder v4 Cleaned.exe (PID: 1828)
Starts itself from another location
- Chaos Ransomware Builder v4 Cleaned.exe (PID: 1828)
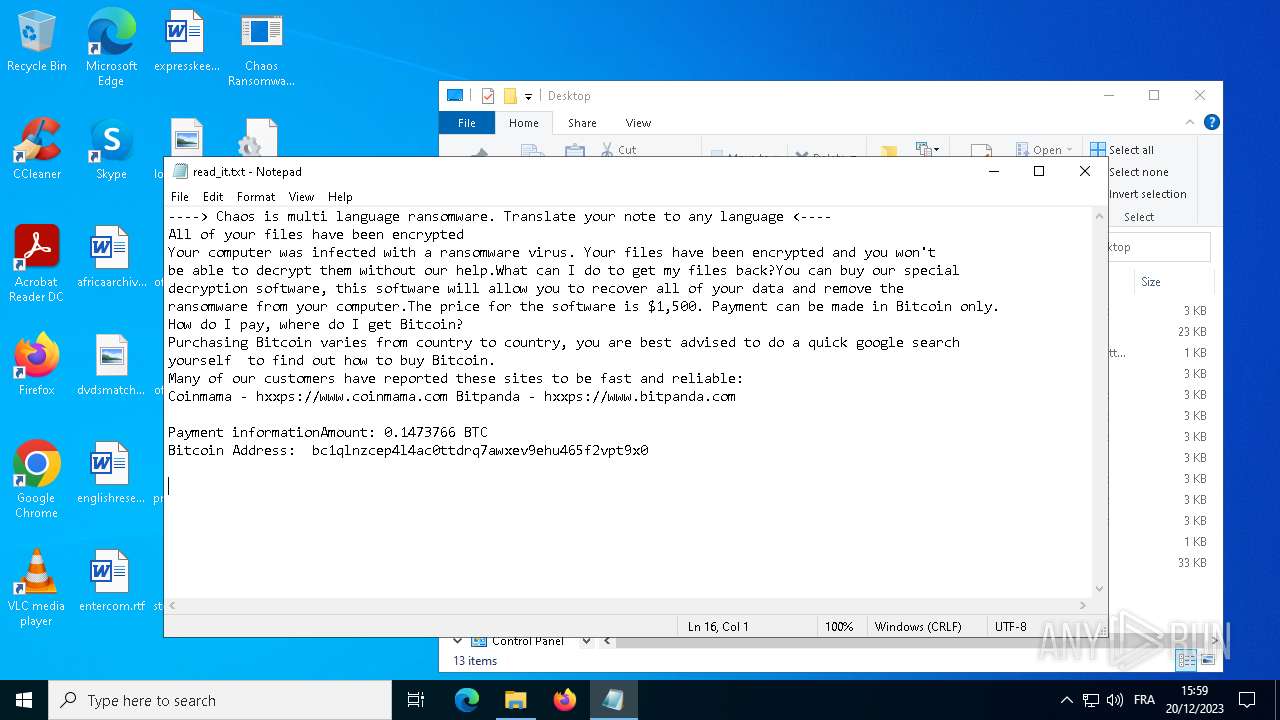
Start notepad (likely ransomware note)
- svchost.exe (PID: 2292)
INFO
Reads the computer name
- Chaos Ransomware Builder v4 Cleaned.exe (PID: 1828)
- svchost.exe (PID: 2292)
Checks supported languages
- Chaos Ransomware Builder v4 Cleaned.exe (PID: 1828)
- svchost.exe (PID: 2292)
Creates files or folders in the user directory
- Chaos Ransomware Builder v4 Cleaned.exe (PID: 1828)
- svchost.exe (PID: 2292)
Reads the machine GUID from the registry
- svchost.exe (PID: 2292)
Manual execution by a user
- WINWORD.EXE (PID: 6608)
- mspaint.exe (PID: 2164)
- mspaint.exe (PID: 5324)
Reads the software policy settings
- slui.exe (PID: 4048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:15 23:27:29+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 20992 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x702e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | Chaos Ransomware Builder v4 Cleaned.exe |
| LegalCopyright: | |
| OriginalFileName: | Chaos Ransomware Builder v4 Cleaned.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
136
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\read_it.txt | C:\Windows\System32\notepad.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1828 | "C:\Users\admin\Desktop\Chaos Ransomware Builder v4 Cleaned.exe" | C:\Users\admin\Desktop\Chaos Ransomware Builder v4 Cleaned.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2164 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Pictures\meancross.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | Chaos Ransomware Builder v4 Cleaned.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3968 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.1202 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4048 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5128 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
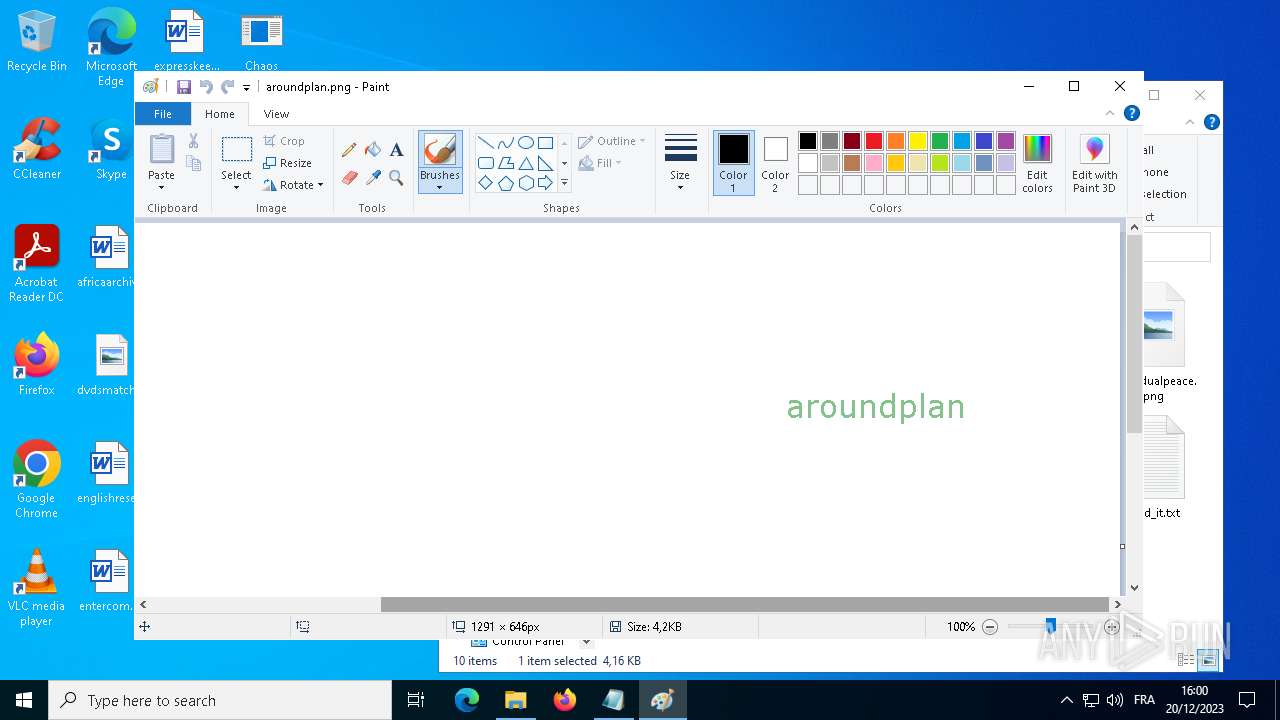
| 5324 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Pictures\aroundplan.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6368 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6608 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\offeredensure.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
9 719
Read events
9 493
Write events
197
Delete events
29
Modification events
| (PID) Process: | (1828) Chaos Ransomware Builder v4 Cleaned.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1828) Chaos Ransomware Builder v4 Cleaned.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1828) Chaos Ransomware Builder v4 Cleaned.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1828) Chaos Ransomware Builder v4 Cleaned.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2292) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2292) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2292) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2292) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6608) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E03000000000000000400000000000000 | |||
| (PID) Process: | (6608) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\5932 |
| Operation: | delete value | Name: | 0 |
Value: 0B0E10ADBA6B0608DEAB45A7BC832DECF38DFA230546E7F0C9D58DAFC6EB016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC90600C50BD98CB314C50CAB800800 | |||
Executable files
2
Suspicious files
33
Text files
86
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1828 | Chaos Ransomware Builder v4 Cleaned.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\Chaos Ransomware Builder v4 Cleaned.exe.log | binary | |
MD5:89E7F177B4D915F4928F903DC439DB5A | SHA256:879E73CE214845BF2331D435523648B503C092F7BC18E301934D5E13C8B767D9 | |||
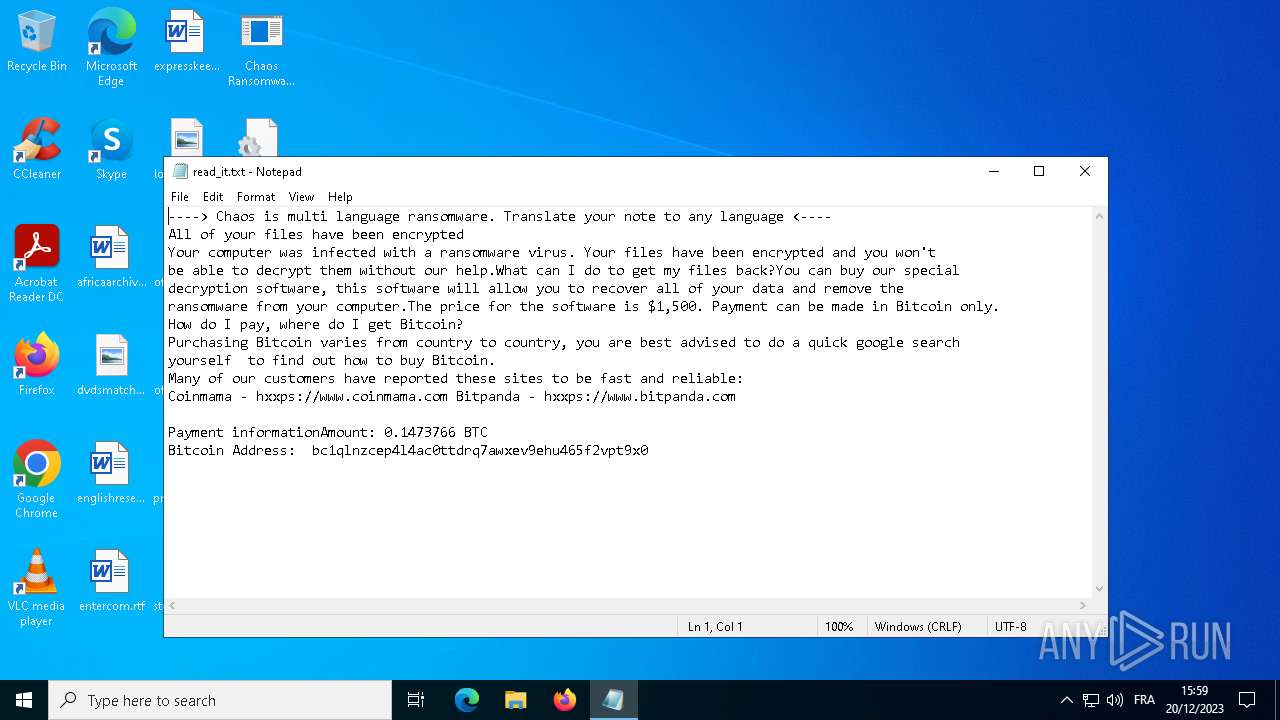
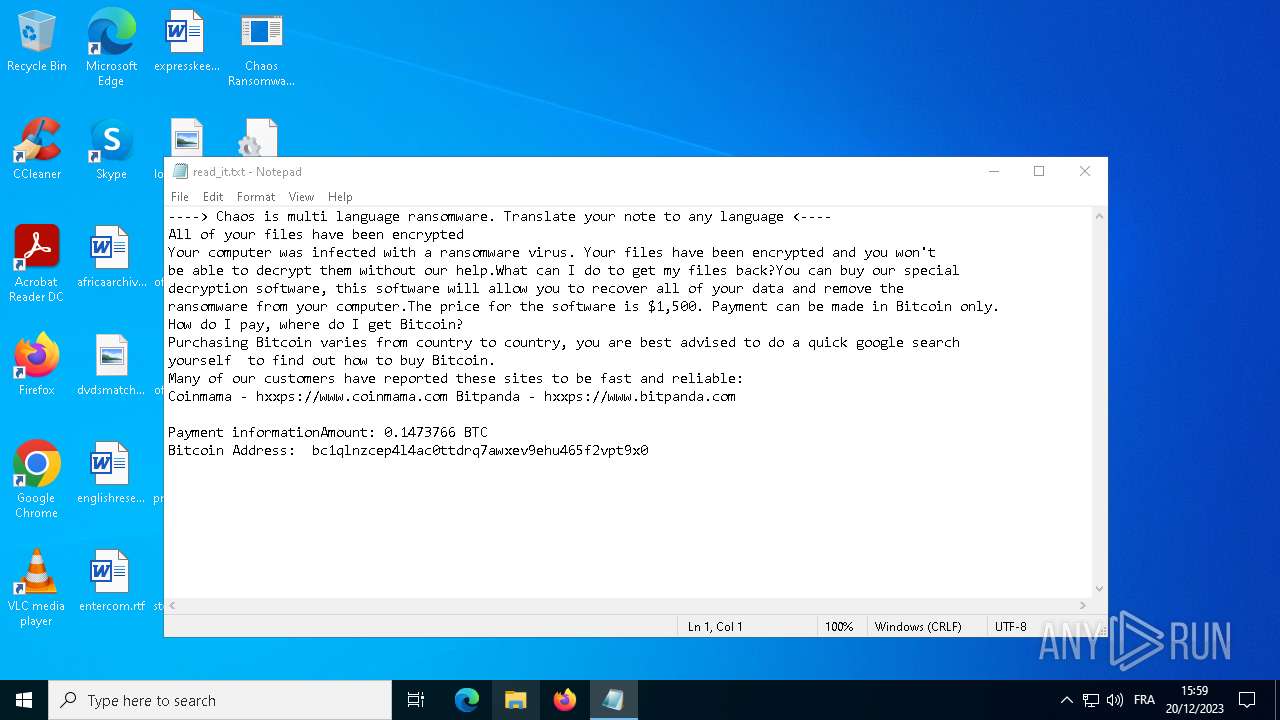
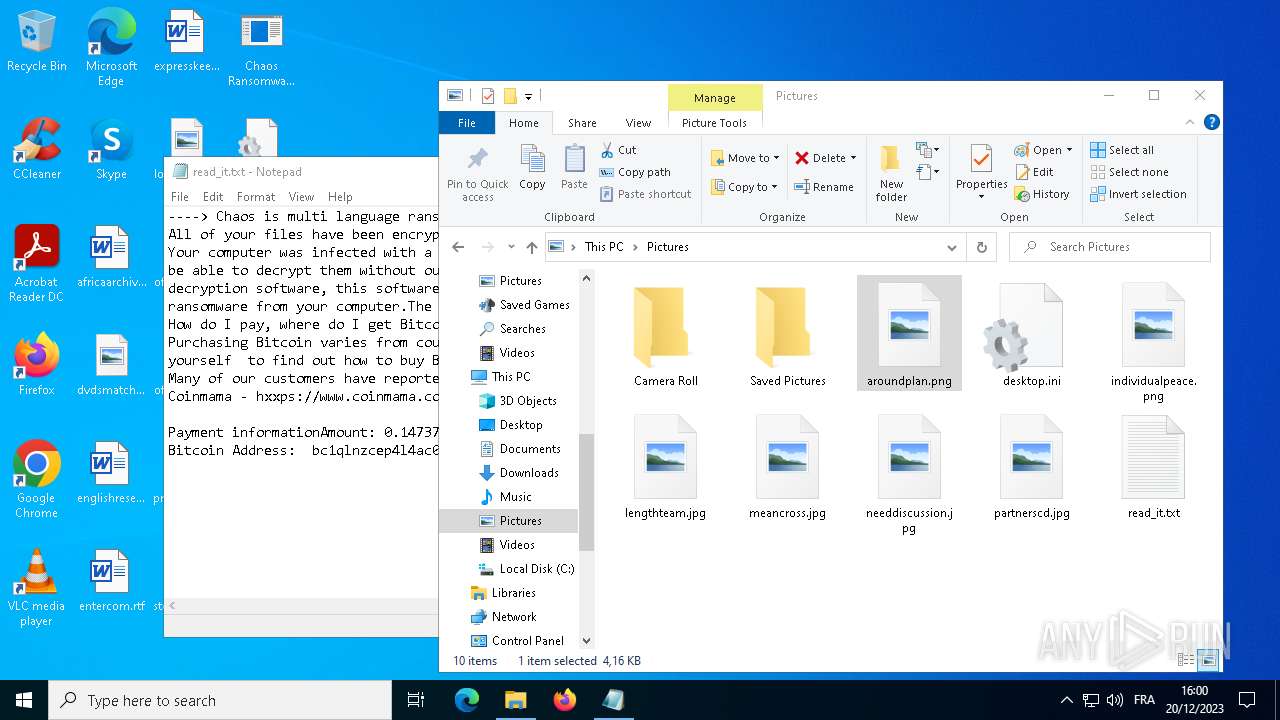
| 2292 | svchost.exe | C:\Users\admin\Desktop\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\Documents\OneNote Notebooks\My Notebook\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.url | text | |
MD5:83660DEB1A47E0B191FDA82BDFD61827 | SHA256:87089BD6FEDDA43B5E4D738B5BF246BA1B2E5C248B9220F0D1E742B827F30B0D | |||
| 2292 | svchost.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\Pictures\Saved Pictures\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\Documents\Outlook Files\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\Pictures\Camera Roll\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\Pictures\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 2292 | svchost.exe | C:\Users\admin\Saved Games\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
44
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4964 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
6404 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
6404 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
6608 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2908 | svchost.exe | GET | 200 | 23.201.254.55:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
6608 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5612 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
784 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4964 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4964 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1092 | svchost.exe | 184.30.17.189:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
1092 | svchost.exe | 138.91.171.81:80 | dmd.metaservices.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
784 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2160 | backgroundTaskHost.exe | 104.126.37.178:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|