| File name: | Ninite ImgBurn Installer.exe |
| Full analysis: | https://app.any.run/tasks/0d3b3357-5350-48d1-9b7a-ba6cbb7dfc2d |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 16:26:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CEF6B6B2D02DBD3B97BFF6CF06602BD8 |
| SHA1: | CBC30CBB4388CCC2291E56F961CC567FE8859CDE |
| SHA256: | 6811558CFB6356BA93C23599E4F4C89BC216C9288C8AA747C64C2DEBE480D12C |
| SSDEEP: | 12288:ZLVP603RQX2pyf+cnci2N9pKKfyeo+pW1KKRyzE9:dVP60BM2pMUN9keo+c+zE9 |
MALICIOUS
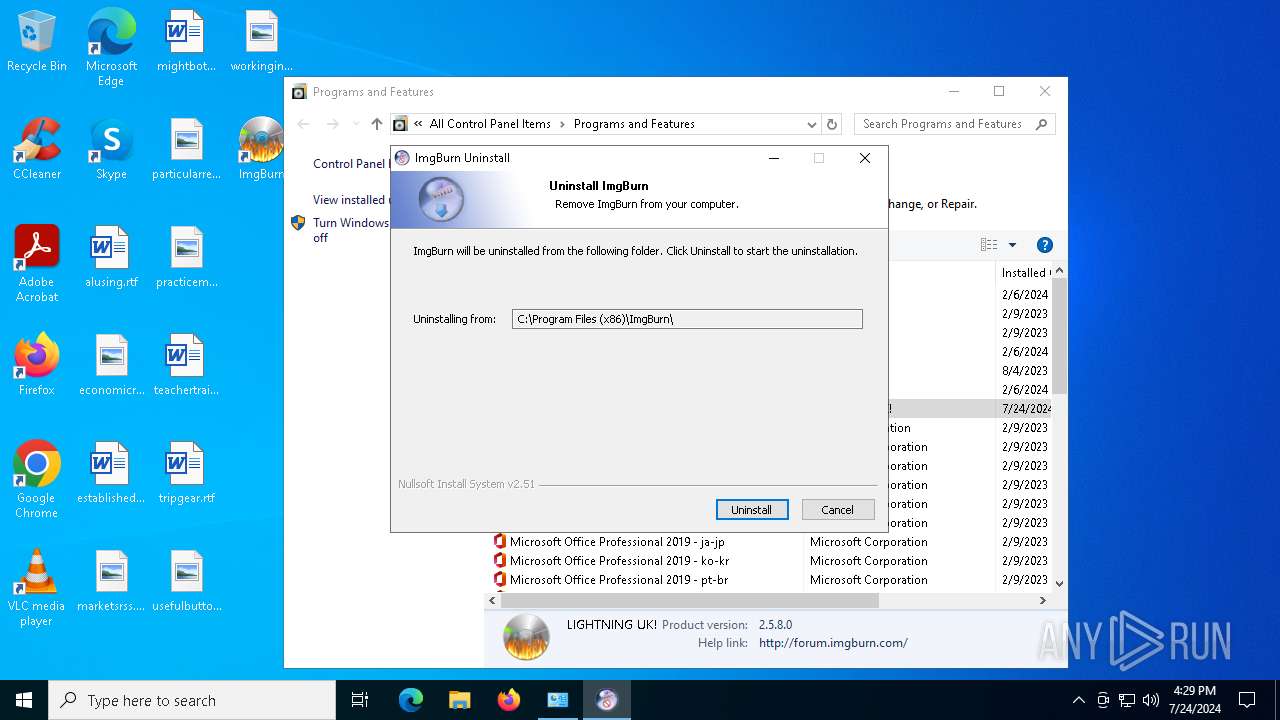
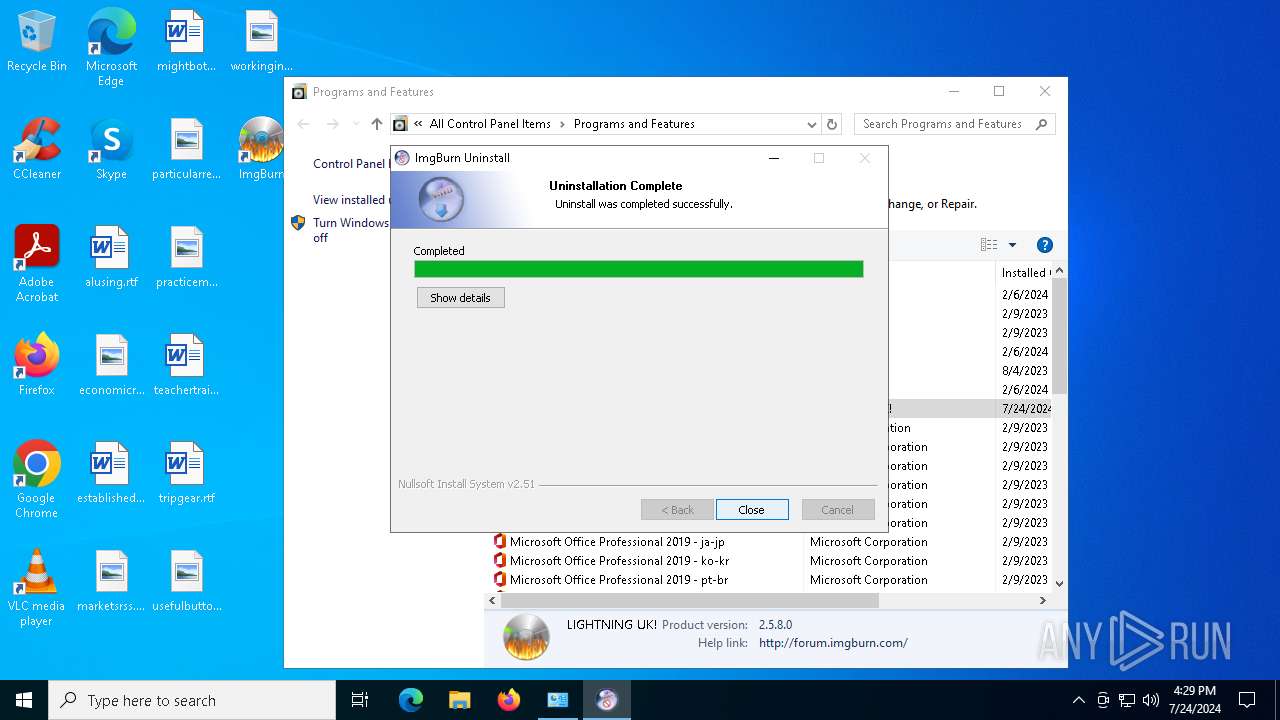
Drops the executable file immediately after the start
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
- target.exe (PID: 1952)
- uninstall.exe (PID: 6772)
- Au_.exe (PID: 2596)
SUSPICIOUS
Executable content was dropped or overwritten
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
- target.exe (PID: 1952)
- uninstall.exe (PID: 6772)
- Au_.exe (PID: 2596)
Reads security settings of Internet Explorer
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 6860)
- Ninite.exe (PID: 2120)
Reads the date of Windows installation
- Ninite.exe (PID: 6860)
Checks Windows Trust Settings
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
Application launched itself
- Ninite.exe (PID: 6860)
The process creates files with name similar to system file names
- target.exe (PID: 1952)
- Au_.exe (PID: 2596)
Searches for installed software
- Ninite.exe (PID: 2120)
- explorer.exe (PID: 7040)
- dllhost.exe (PID: 5004)
- Au_.exe (PID: 2596)
Malware-specific behavior (creating "System.dll" in Temp)
- target.exe (PID: 1952)
- Au_.exe (PID: 2596)
Creates a software uninstall entry
- target.exe (PID: 1952)
Starts itself from another location
- uninstall.exe (PID: 6772)
INFO
Reads the computer name
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 6860)
- Ninite.exe (PID: 2120)
- target.exe (PID: 1952)
- ImgBurn.exe (PID: 4252)
- TextInputHost.exe (PID: 6636)
- Au_.exe (PID: 2596)
Reads the software policy settings
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
Creates files or folders in the user directory
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
- ImgBurn.exe (PID: 4252)
Create files in a temporary directory
- Ninite ImgBurn Installer.exe (PID: 528)
- target.exe (PID: 1952)
- Ninite.exe (PID: 2120)
- uninstall.exe (PID: 6772)
- Au_.exe (PID: 2596)
Reads the machine GUID from the registry
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
Checks supported languages
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 6860)
- Ninite.exe (PID: 2120)
- target.exe (PID: 1952)
- ImgBurn.exe (PID: 4252)
- TextInputHost.exe (PID: 6636)
- Au_.exe (PID: 2596)
- uninstall.exe (PID: 6772)
- unzip.exe (PID: 2824)
Checks proxy server information
- Ninite ImgBurn Installer.exe (PID: 528)
- Ninite.exe (PID: 2120)
- slui.exe (PID: 6136)
Process checks computer location settings
- Ninite.exe (PID: 6860)
Creates files in the program directory
- target.exe (PID: 1952)
- Ninite.exe (PID: 2120)
UPX packer has been detected
- ImgBurn.exe (PID: 4252)
Checks transactions between databases Windows and Oracle
- explorer.exe (PID: 7040)
Manual execution by a user
- ImgBurn.exe (PID: 4252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:04:12 00:19:47+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 233472 |
| InitializedDataSize: | 182272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1a53a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.1.1.1183 |
| ProductVersionNumber: | 0.1.1.1183 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Secure By Design Inc. |
| FileDescription: | Ninite |
| FileVersion: | 0,1,1,1183 |
| InternalName: | Ninite |
| LegalCopyright: | Copyright (C) 2009 Secure By Design Inc |
| OriginalFileName: | - |
| ProductName: | Ninite |
| ProductVersion: | 0,1,1,1183 |
Total processes
160
Monitored processes
15
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Users\admin\Downloads\Ninite ImgBurn Installer.exe" | C:\Users\admin\Downloads\Ninite ImgBurn Installer.exe | explorer.exe | ||||||||||||
User: admin Company: Secure By Design Inc. Integrity Level: MEDIUM Description: Ninite Exit code: 0 Version: 0,1,1,1183 Modules
| |||||||||||||||
| 1952 | target.exe /S /NOCANDY | C:\Users\admin\AppData\Local\Temp\7ff6b5a6-49d9-11ef-b4e2-18f7786f96ee\target.exe | Ninite.exe | ||||||||||||
User: admin Company: LIGHTNING UK! Integrity Level: HIGH Description: ImgBurn Installer Exit code: 0 Version: 2.5.8.0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\7ab8896b-49d9-11ef-b4e2-18f7786f96ee\Ninite.exe" "d8c647058c49d4ead08af28c81017df1961f079e" /fullpath "C:\Users\admin\Downloads\Ninite ImgBurn Installer.exe" /relaunch | C:\Users\admin\AppData\Local\Temp\7ab8896b-49d9-11ef-b4e2-18f7786f96ee\Ninite.exe | Ninite.exe | ||||||||||||
User: admin Company: Secure By Design Inc. Integrity Level: HIGH Description: Ninite Exit code: 0 Version: 0,1,1,1461 Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | unzip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Users\admin\AppData\Local\Temp\~nsuA.tmp\Au_.exe" _?=C:\Program Files (x86)\ImgBurn\ | C:\Users\admin\AppData\Local\Temp\~nsuA.tmp\Au_.exe | uninstall.exe | ||||||||||||
User: admin Company: LIGHTNING UK! Integrity Level: HIGH Description: ImgBurn Installer Exit code: 0 Version: 2.5.8.0 Modules
| |||||||||||||||
| 2824 | "C:\Users\admin\AppData\Local\Temp\7FF6B5~1\unzip.exe" -o translation.zip | C:\Users\admin\AppData\Local\Temp\7ff6b5a6-49d9-11ef-b4e2-18f7786f96ee\unzip.exe | — | Ninite.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 4252 | "C:\Program Files (x86)\ImgBurn\ImgBurn.exe" | C:\Program Files (x86)\ImgBurn\ImgBurn.exe | explorer.exe | ||||||||||||
User: admin Company: LIGHTNING UK! Integrity Level: MEDIUM Description: ImgBurn - The Ultimate Image Burner! Exit code: 0 Version: 2.5.8.0 Modules
| |||||||||||||||
| 4340 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5004 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{FCC74B77-EC3E-4DD8-A80B-008A702075A9} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 416
Read events
37 393
Write events
688
Delete events
335
Modification events
| (PID) Process: | (528) Ninite ImgBurn Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (528) Ninite ImgBurn Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (528) Ninite ImgBurn Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (528) Ninite ImgBurn Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6860) Ninite.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6860) Ninite.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6860) Ninite.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6860) Ninite.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2120) Ninite.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2120) Ninite.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
12
Suspicious files
25
Text files
3
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | der | |
MD5:F5A0556954947C0CE287DB0FB3D1B25A | SHA256:4DF33EDCC9EC088CA370F6B685836A0CC99F8EB2404EC5C0637F77EAA3104032 | |||
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:C8A33F4343FE87405A53F823BD6371C1 | SHA256:824F0D159A1437DEB7A35DAB9588E17AAC6C34A1E614DB88CDED698335152384 | |||
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50385F8EB1F713E33924A830D7A2A41C | der | |
MD5:4DCA8A84E4705AFEDBDFF3DF535C8FE8 | SHA256:ADD93B6A9B5DB4855A5F4CE4FC3800C93F6F6C8690EAC66CF09B574FD51A09B1 | |||
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A1D627669EFC8CD4F21BCF387D97F9B5_BCCFCBC66B448214318C9391CA0E275F | der | |
MD5:96FFD115D2FDCE7D61872F0D93C26D53 | SHA256:F9235763A789B81028BCF3E700E5E220CF11ADFA8A95758DD33032F2C5F055A8 | |||
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_6C354C532D063DF5607A63BA827F5164 | binary | |
MD5:B40487F09391FF23D0EAA79618D0E054 | SHA256:F2953DFA96B8CAB5DABA1658B6C24DAEB08A6A9A174CABD5B4ABAD52CC6761A1 | |||
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_6C354C532D063DF5607A63BA827F5164 | der | |
MD5:C8D159D74D86AC6A559229305D877530 | SHA256:A2BD5E246E6CAA92F2E45DB1DE405FC9480879CB7C780BE1696A79F5D7E216ED | |||
| 528 | Ninite ImgBurn Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_50385F8EB1F713E33924A830D7A2A41C | binary | |
MD5:D78C65CD533023A39D357F869CC05FB6 | SHA256:BB24B0BF73E56ABE86B989D5A8A05ED5E471D8CBB9F0AAD1802A3D9420058392 | |||
| 2120 | Ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 2120 | Ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D03E46CD585BBE111C712E6577BC5F07_56B2A1FF8D0F5C5B4060FCF88A1654FE | binary | |
MD5:A18D94301BB9DB31C884591FA018D404 | SHA256:3BA3EAA36A103BDA41103406C7D451FAF7819DEF451F3F2D27E1AD3548440105 | |||
| 2120 | Ninite.exe | C:\Users\admin\AppData\Local\Temp\7ff6b5a6-49d9-11ef-b4e2-18f7786f96ee\translation.zip_7ff6b5a7-49d9-11ef-b4e2-18f7786f96ee | compressed | |
MD5:76CDB2BAD9582D23C1F6F4D868218D6C | SHA256:8739C76E681F900923B900C9DF0EF75CF421D39CABB54650C4B9AD19B6A76D85 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
68
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
528 | Ninite ImgBurn Installer.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
528 | Ninite ImgBurn Installer.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
528 | Ninite ImgBurn Installer.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgOhtwj4VKsGchDZBEc%3D | unknown | — | — | whitelisted |
528 | Ninite ImgBurn Installer.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gsgccr45codesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLuA3ygnKW%2F7xuSx%2F09F%2BhHVuEUQQU2rONwCSQo2t30wygWd0hZ2R2C3gCDGPUxoqhhiZifL455A%3D%3D | unknown | — | — | whitelisted |
2120 | Ninite.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
2120 | Ninite.exe | GET | 200 | 13.224.191.223:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAO9ExOMvLBqk2jkjdZnyjA%3D | unknown | — | — | whitelisted |
2376 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5032 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2120 | Ninite.exe | GET | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgSKzUNgjhNLQ14AiZMv1WtnkQ%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4136 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.33:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4548 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
528 | Ninite ImgBurn Installer.exe | 13.32.27.127:443 | ninite.com | AMAZON-02 | US | unknown |
528 | Ninite ImgBurn Installer.exe | 18.245.39.64:80 | ocsp.rootca1.amazontrust.com | — | US | unknown |
5368 | SearchApp.exe | 92.123.104.33:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ninite.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ninite-tools.s3.amazonaws.com |
| shared |