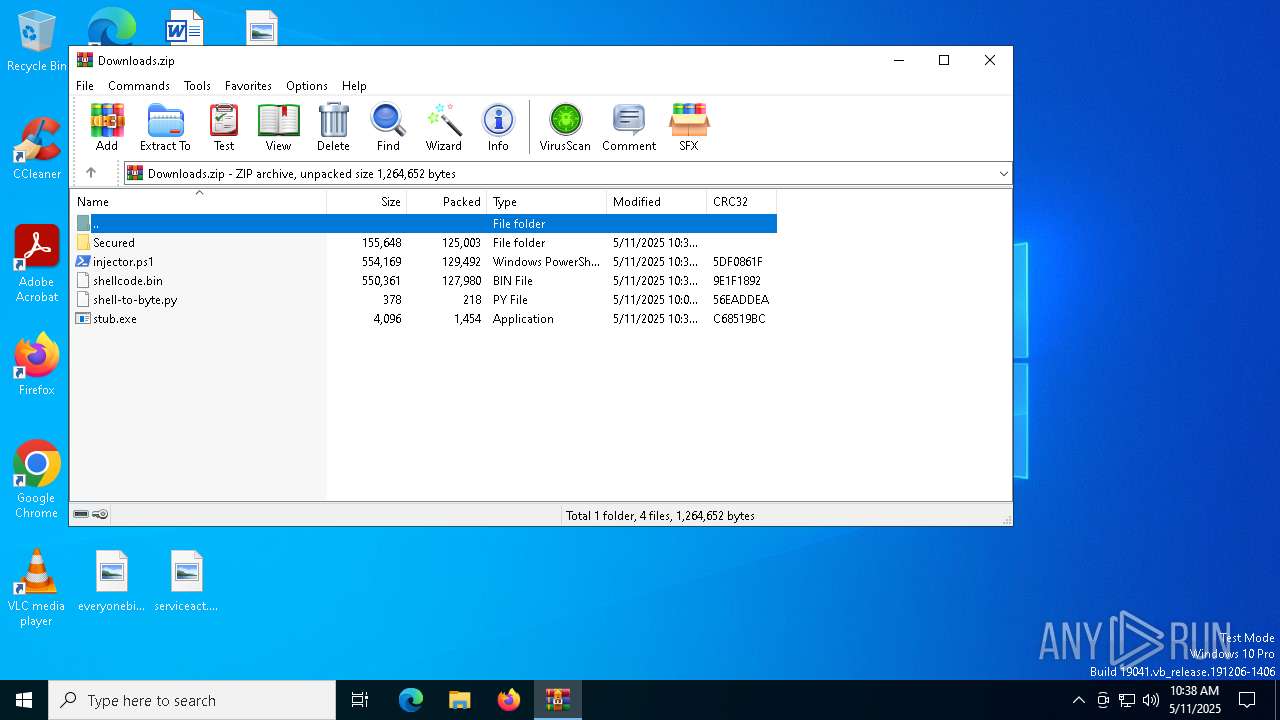
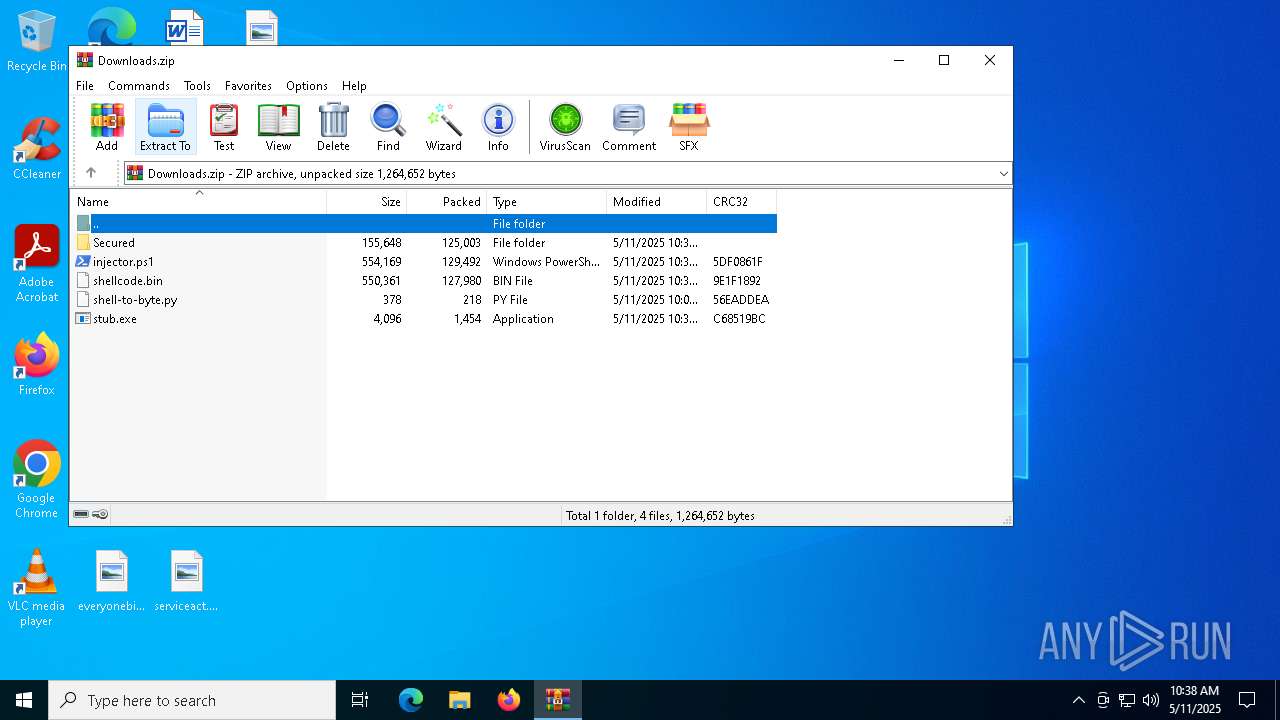
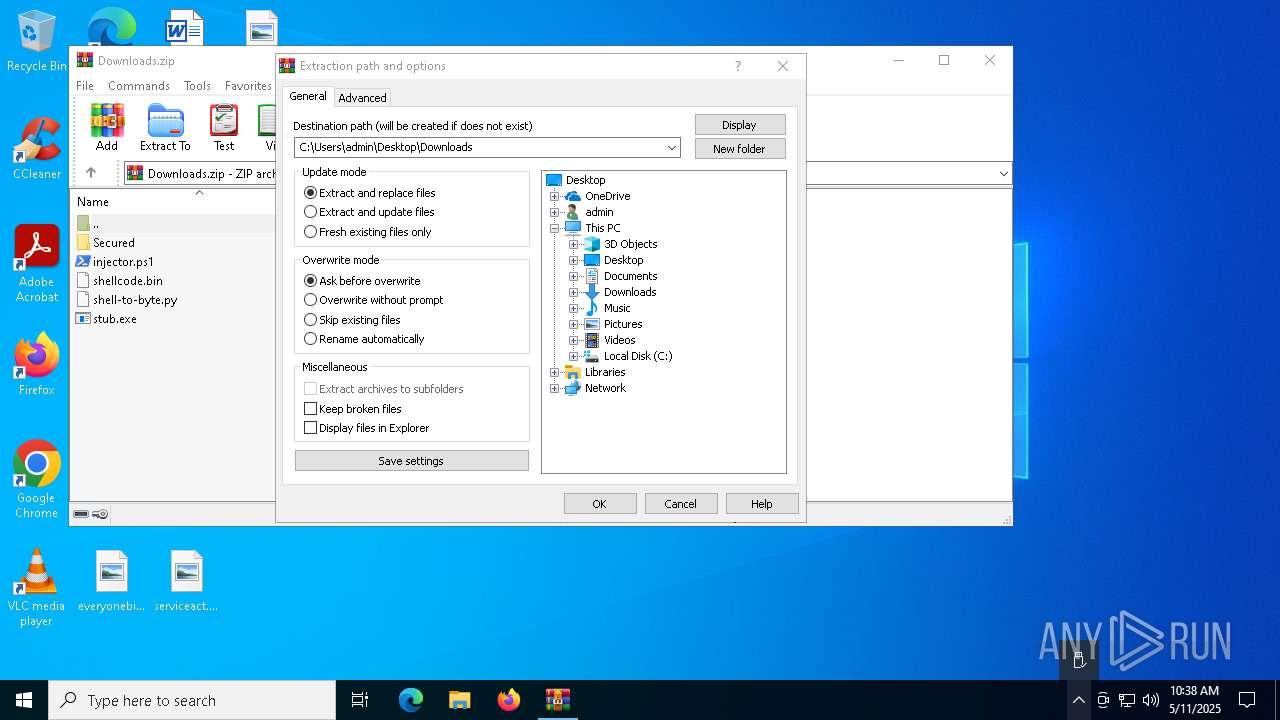
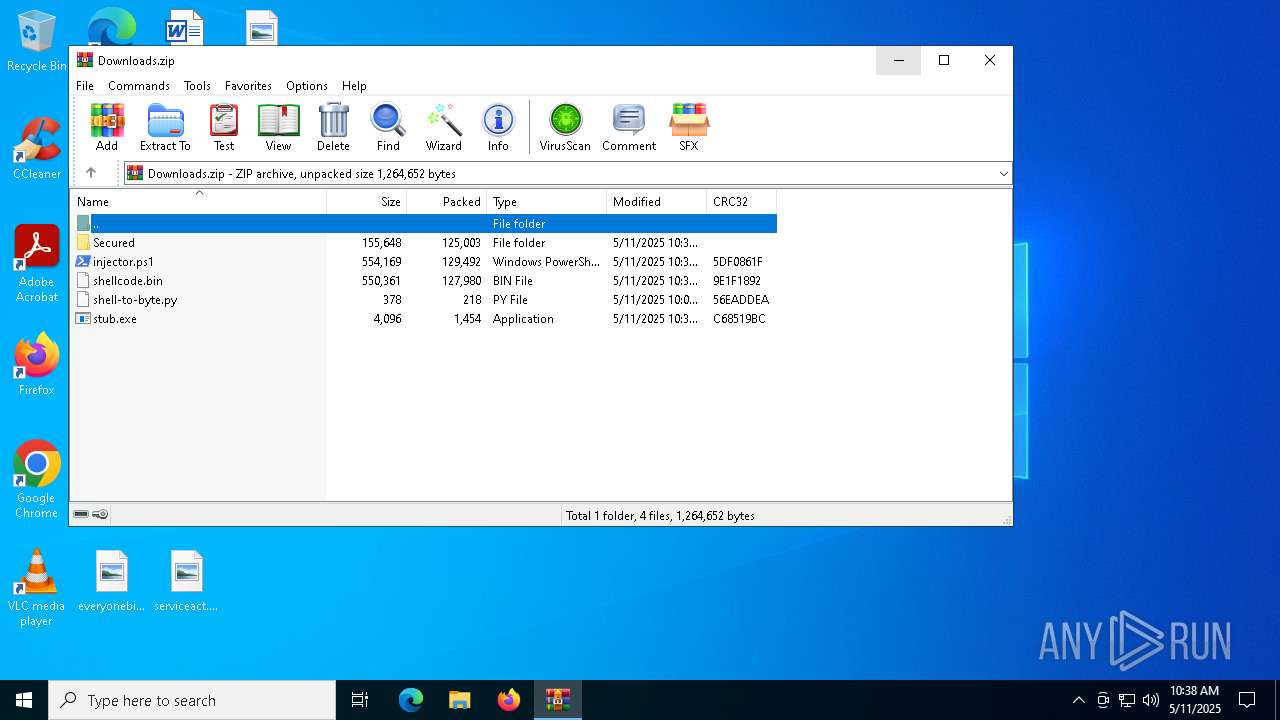
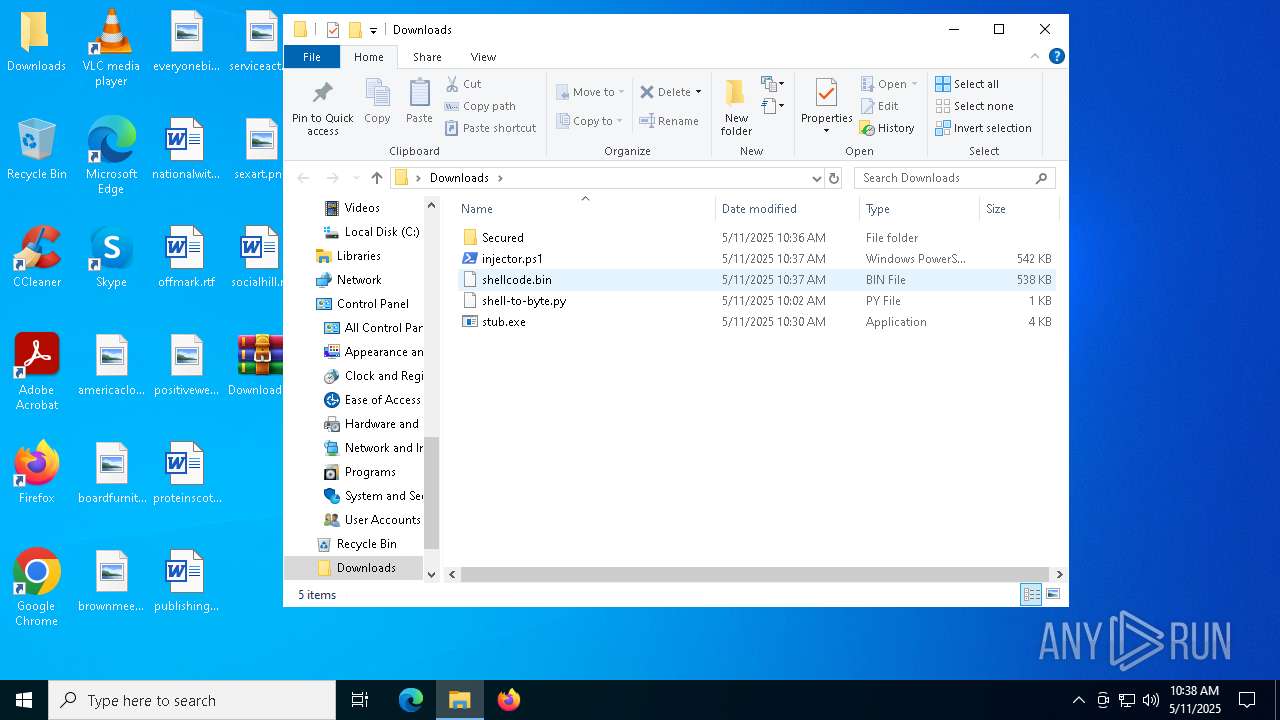
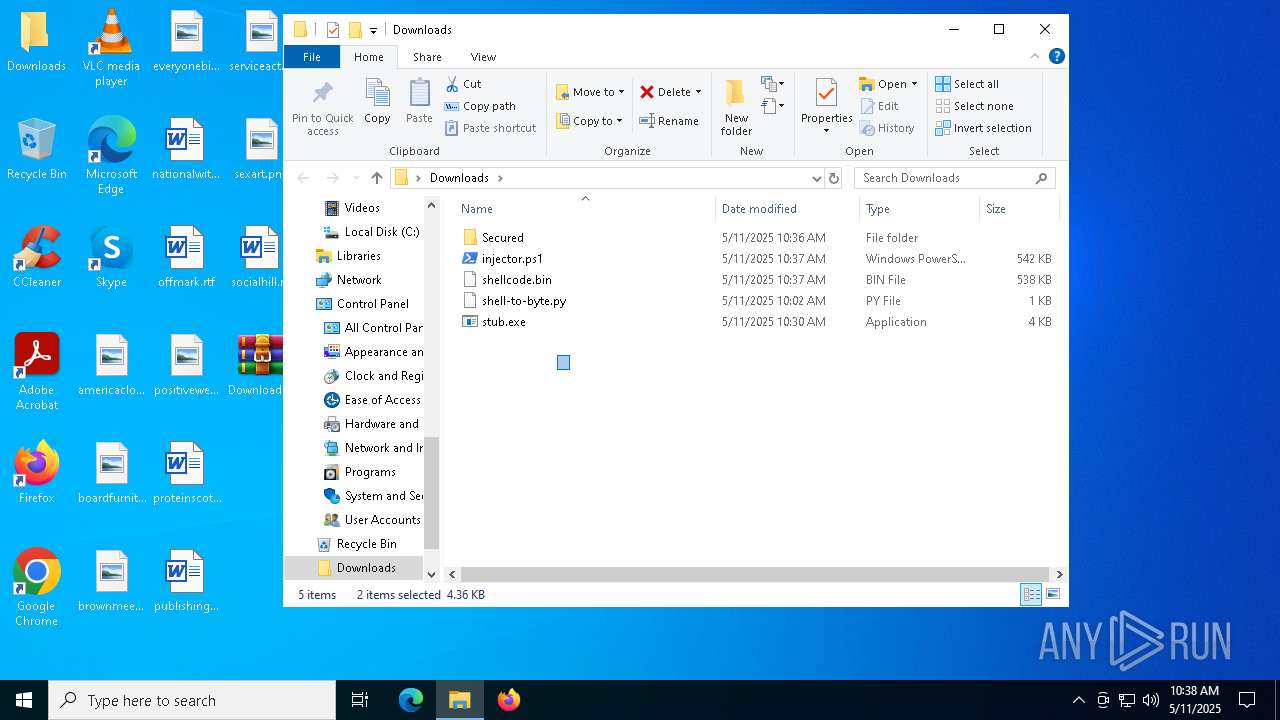
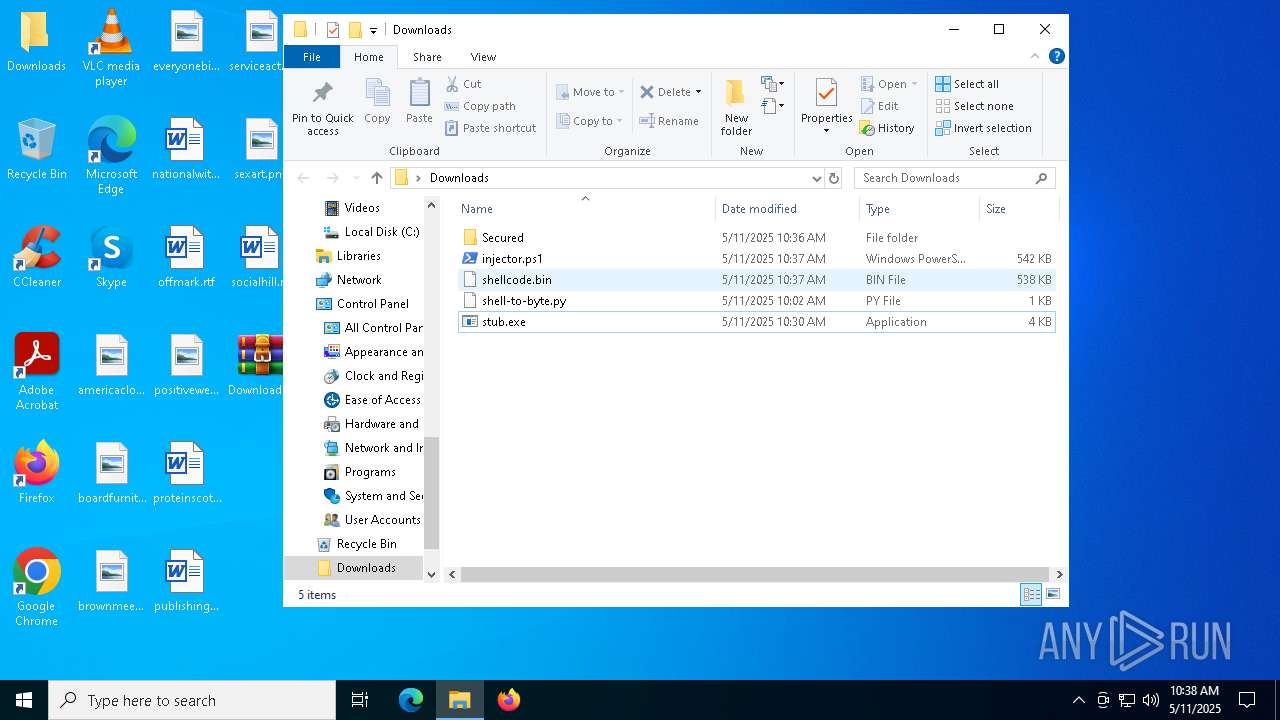
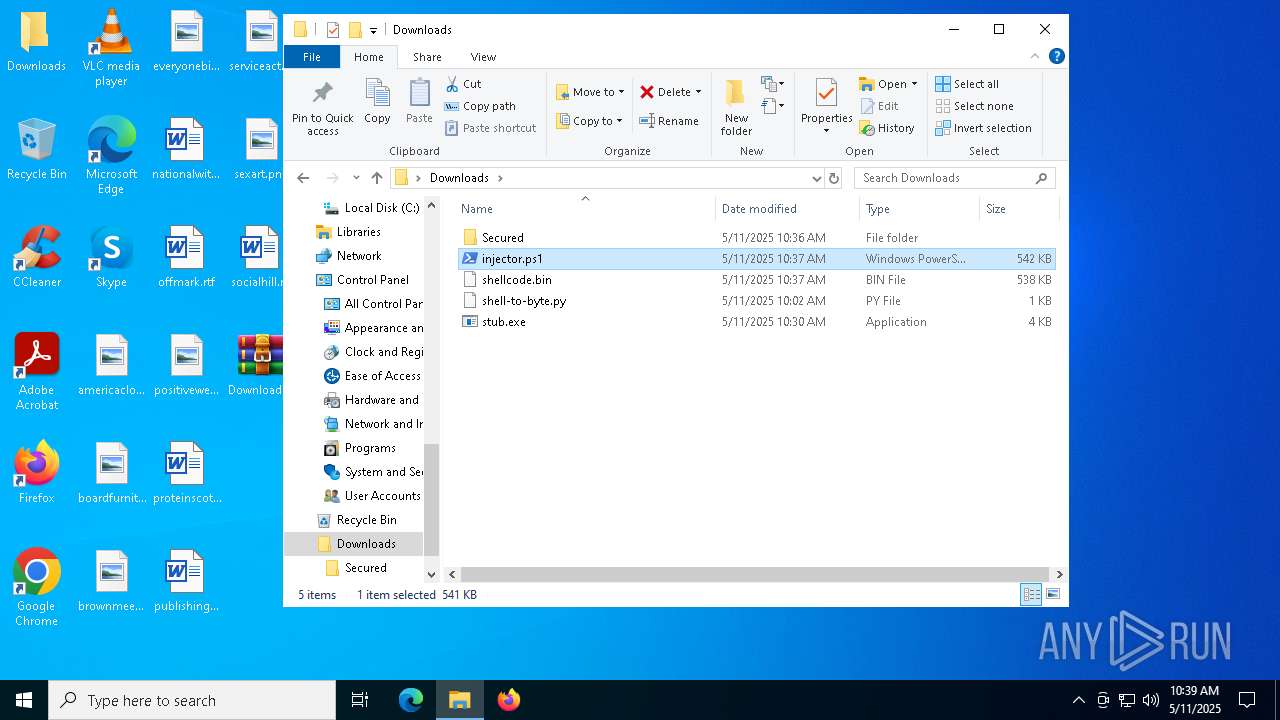
| File name: | Downloads.zip |
| Full analysis: | https://app.any.run/tasks/5fd1b0ee-8c03-46cc-8dbd-694c16ef8ef7 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 10:38:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 17F8E693CF0459AF2129B3B6CB283339 |
| SHA1: | 94929FBD575DE126C6FE03D338B1C6681D64CC46 |
| SHA256: | 680E349526DDB6C3F4CC9C7AB9B9260561B1DF7EFEB64D5697D11DF99C827D10 |
| SSDEEP: | 12288:FJcohR+OC6VFxfLv2SY94TZVXc9iVL2SY94TJmjK:FmohR+OC6tLv2v4vXc9ix2v49mjK |
MALICIOUS
Generic archive extractor
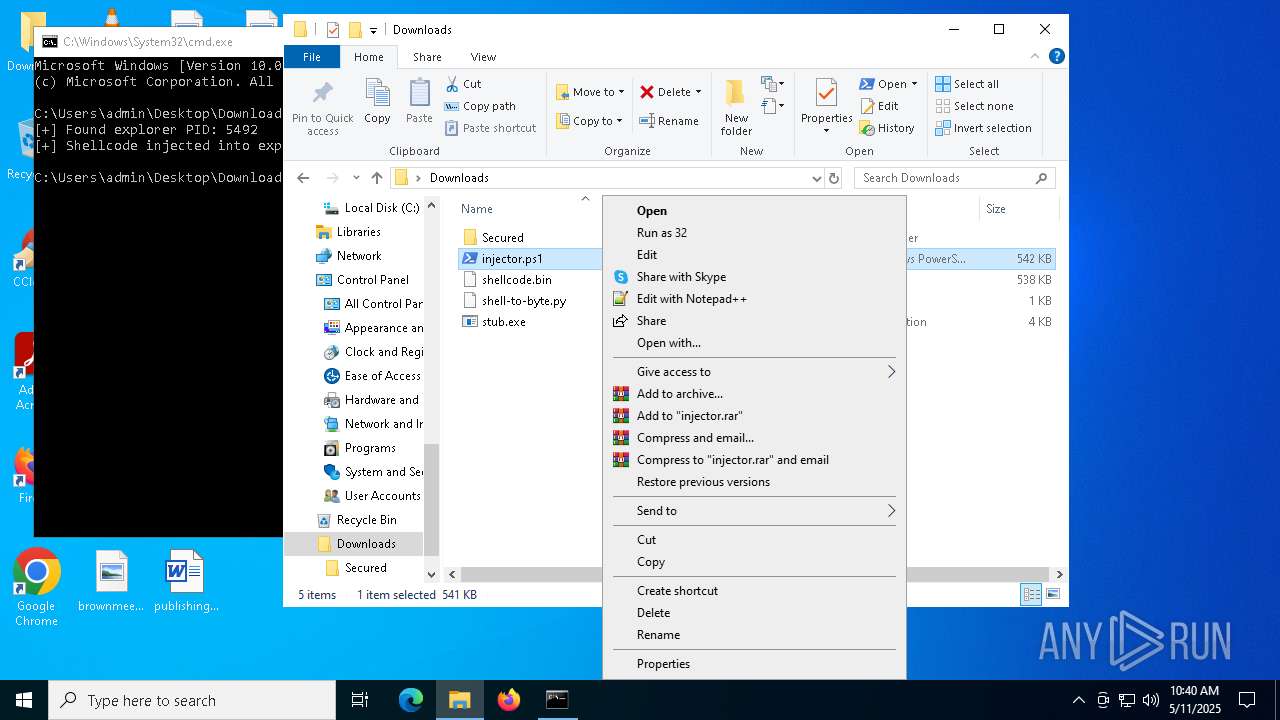
- WinRAR.exe (PID: 4180)
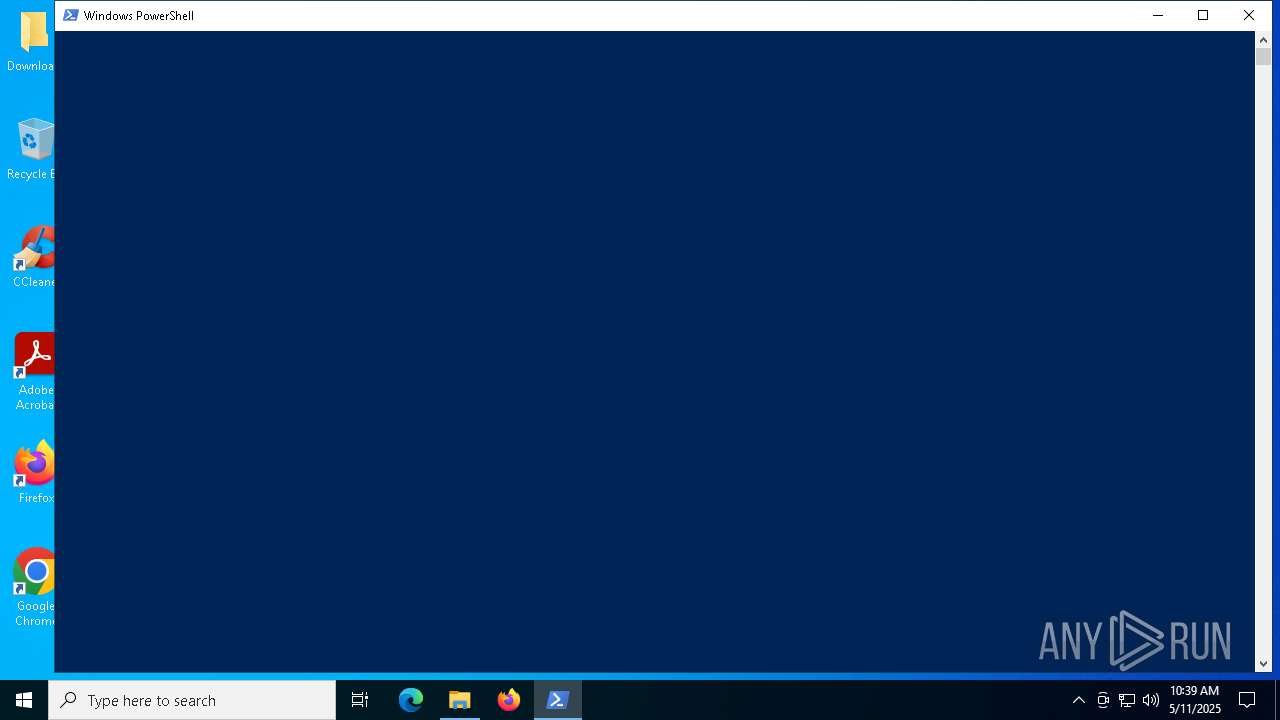
Bypass execution policy to execute commands
- powershell.exe (PID: 920)
- powershell.exe (PID: 4736)
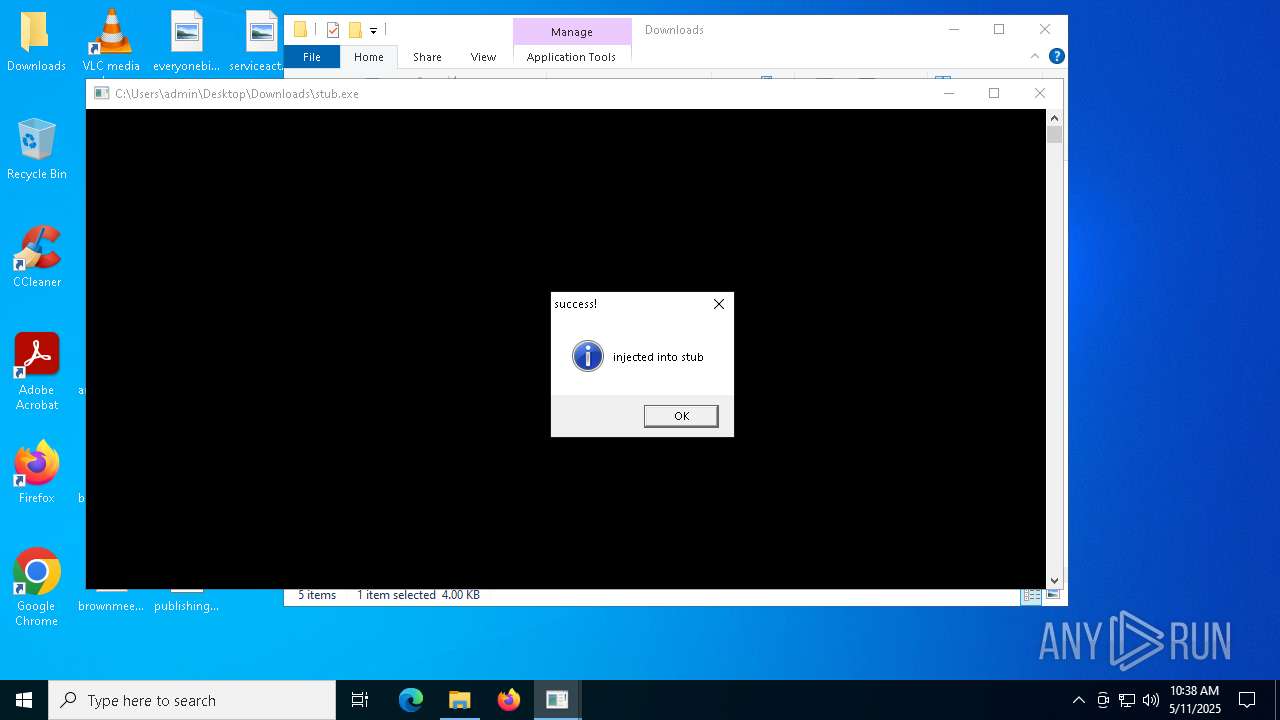
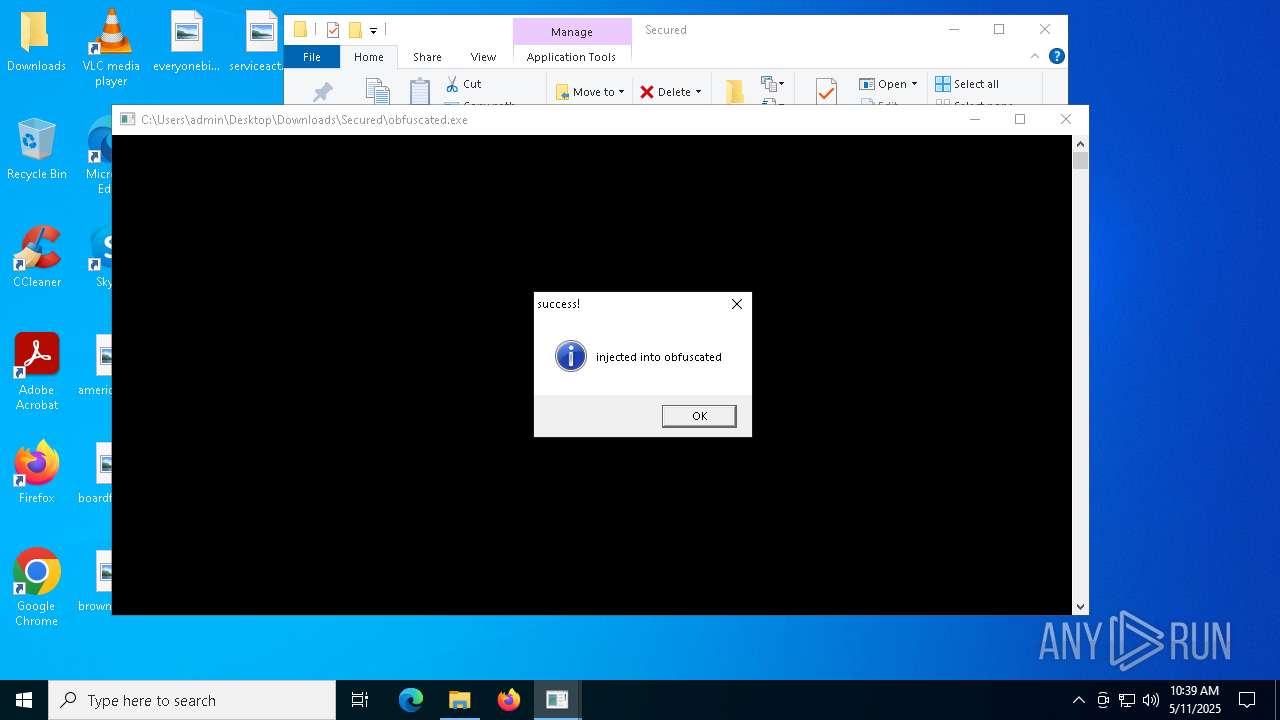
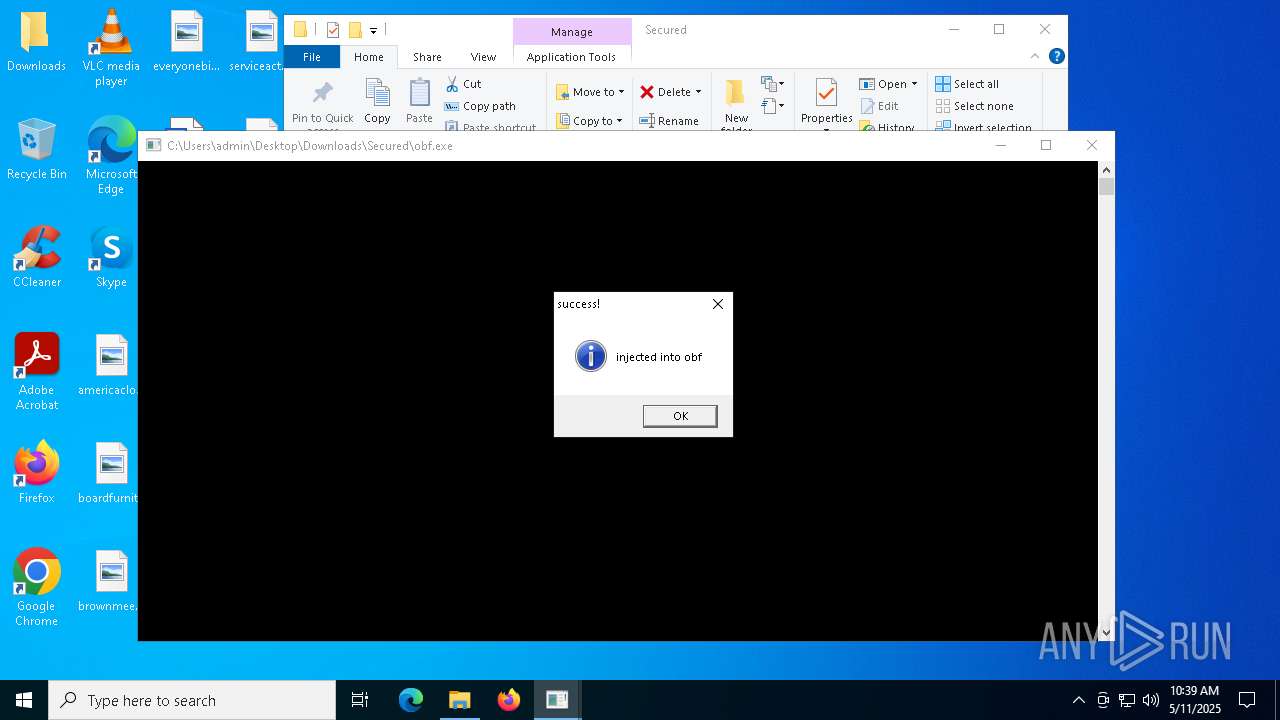
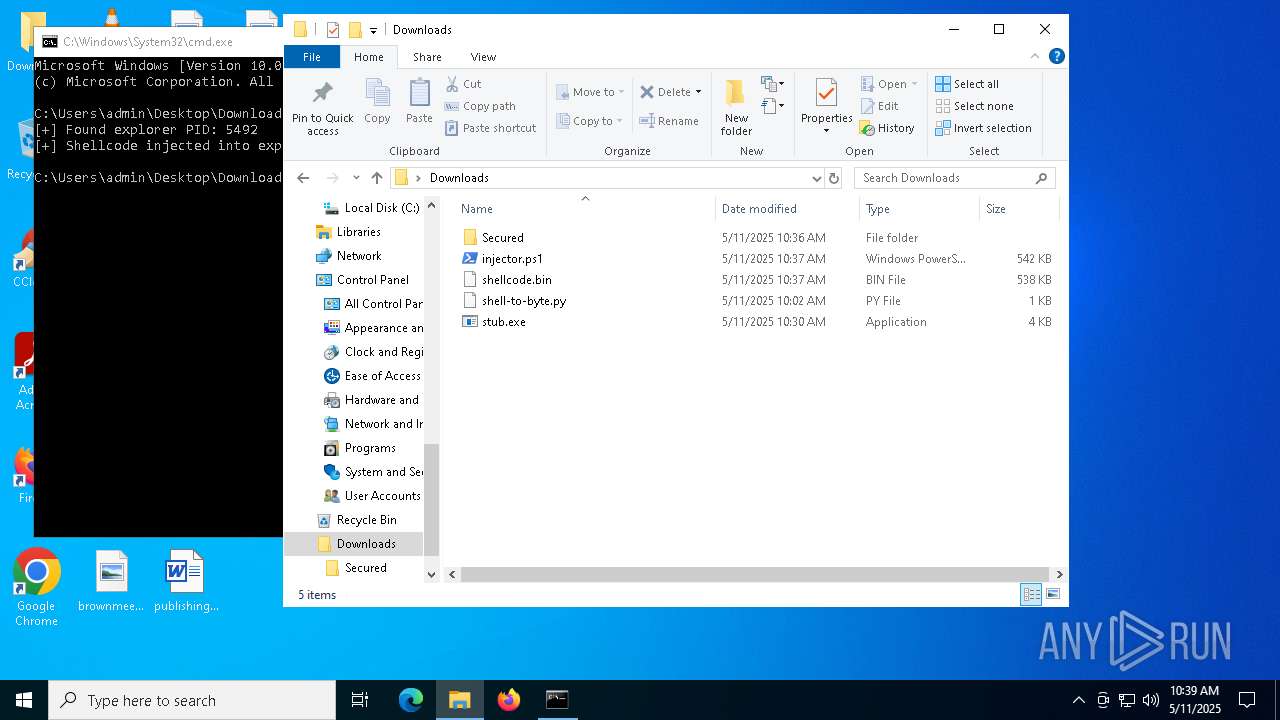
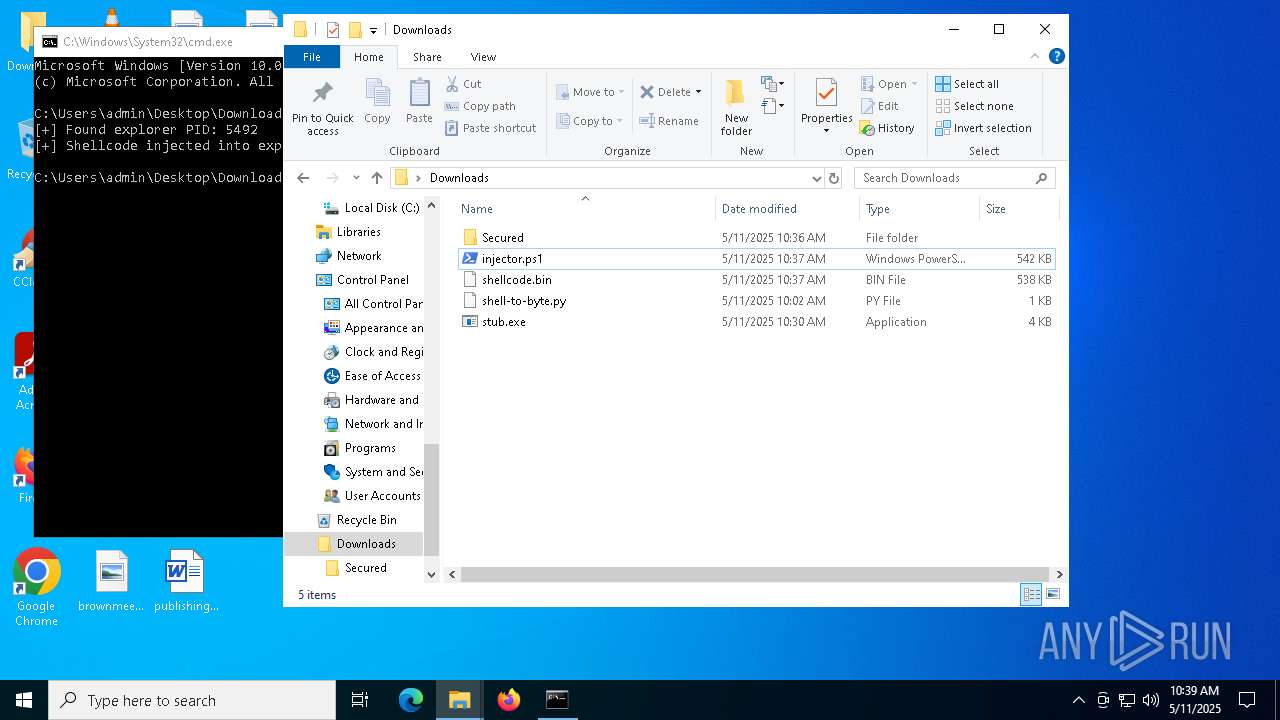
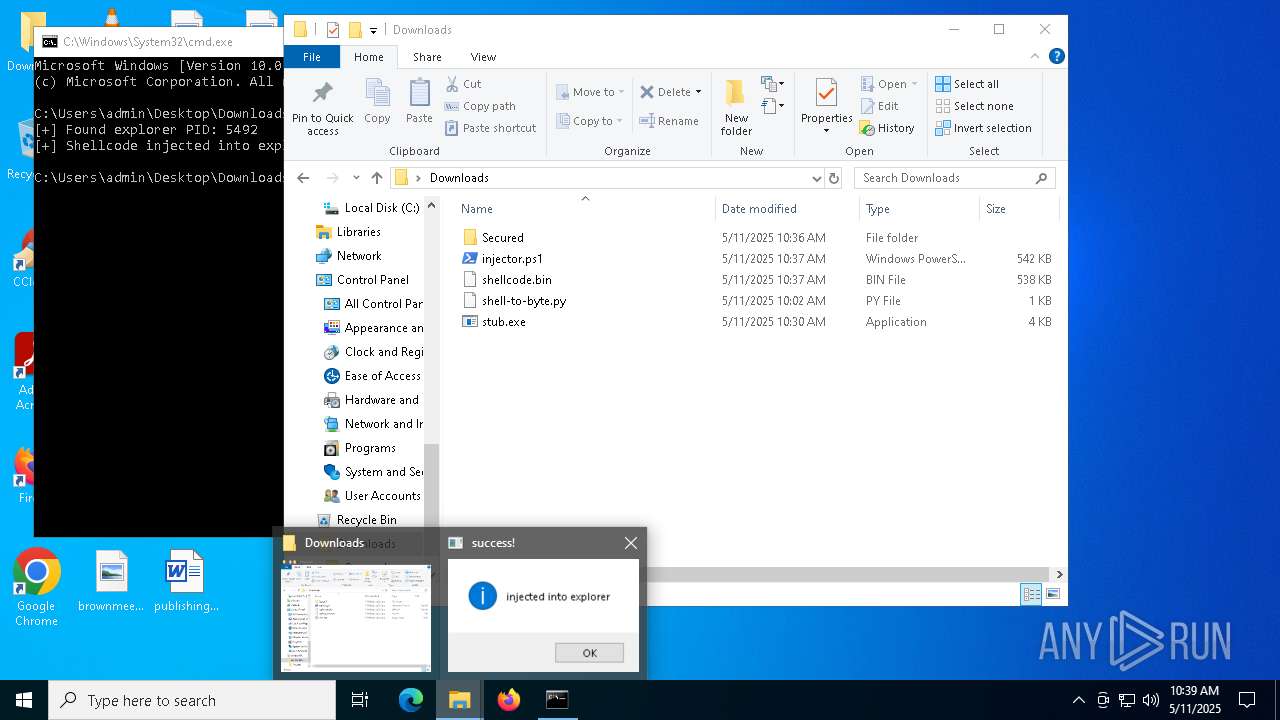
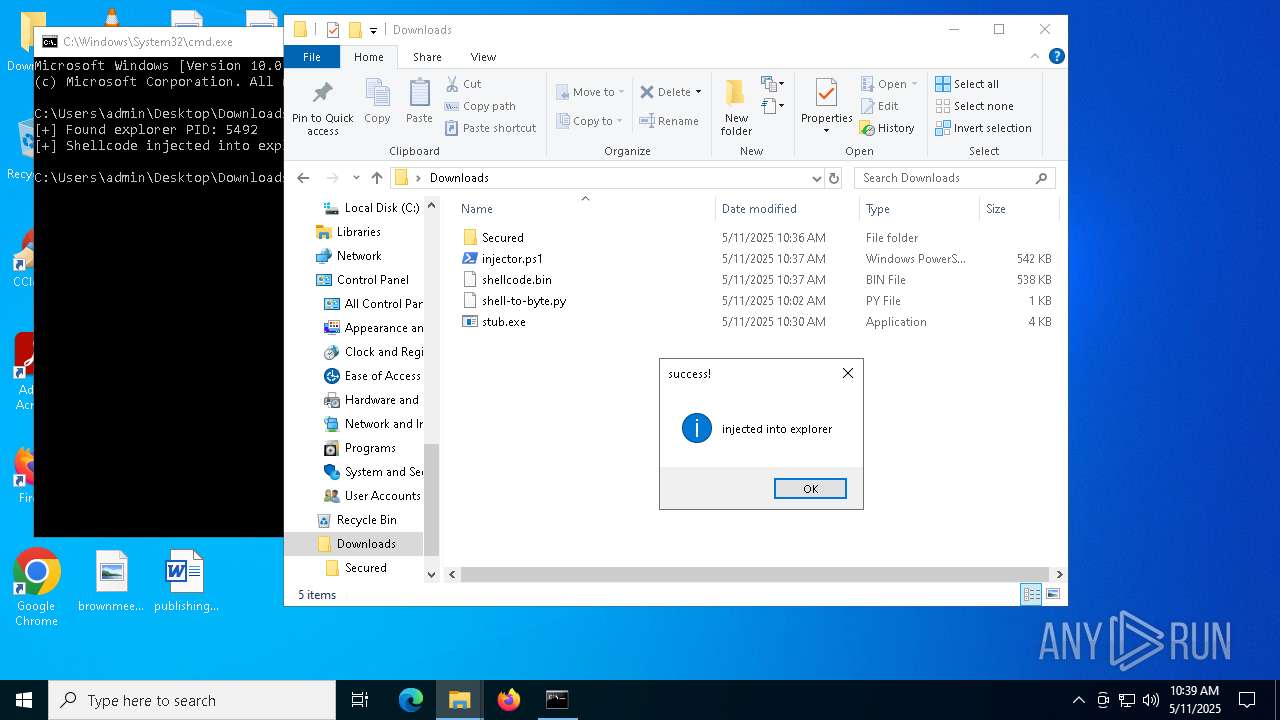
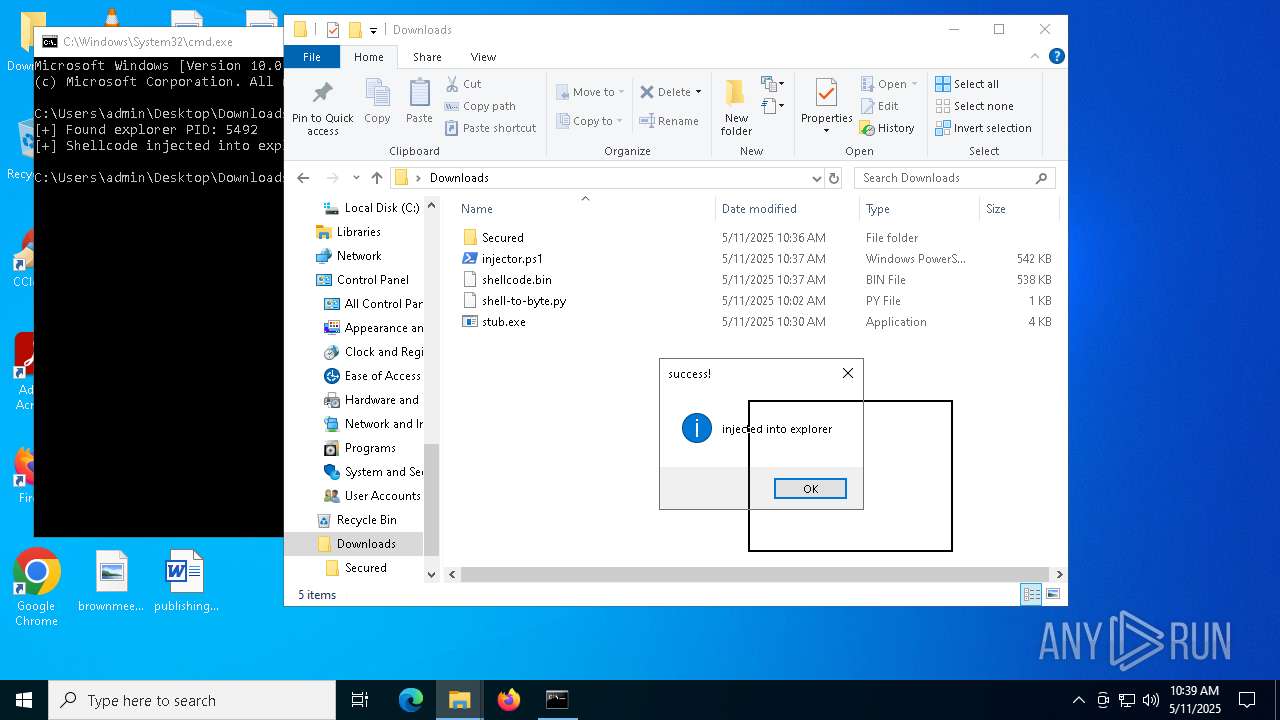
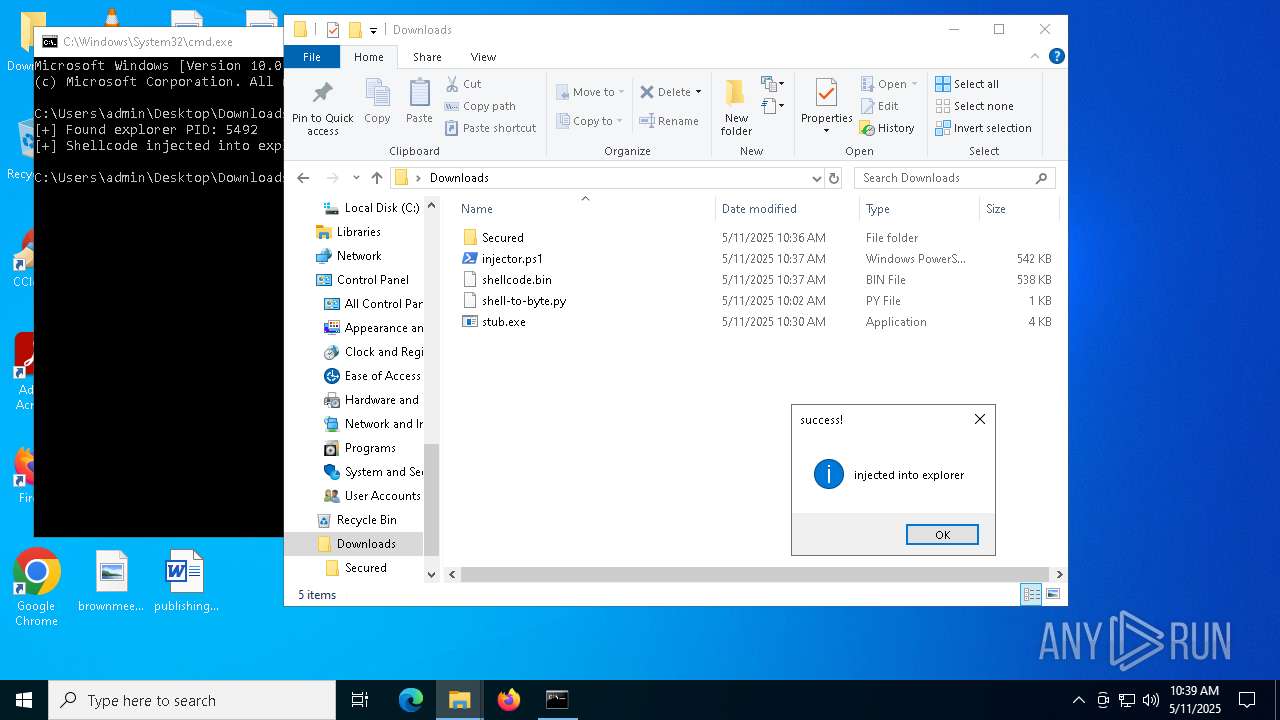
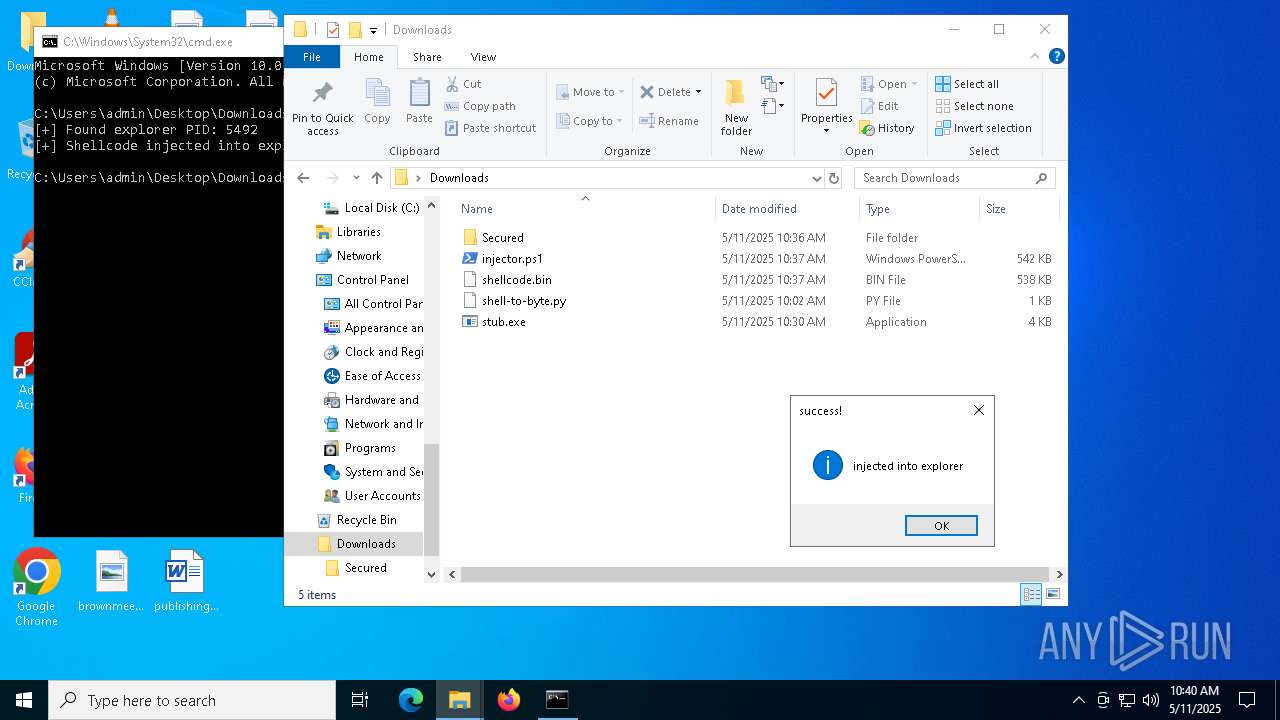
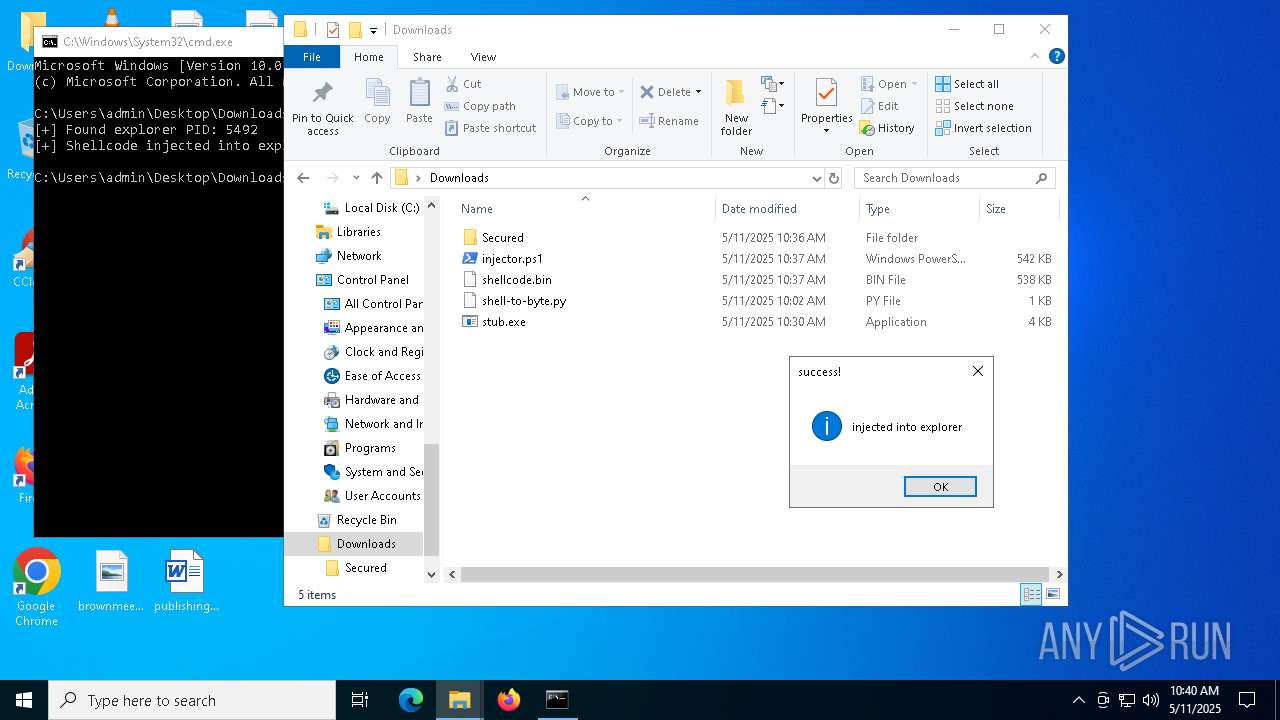
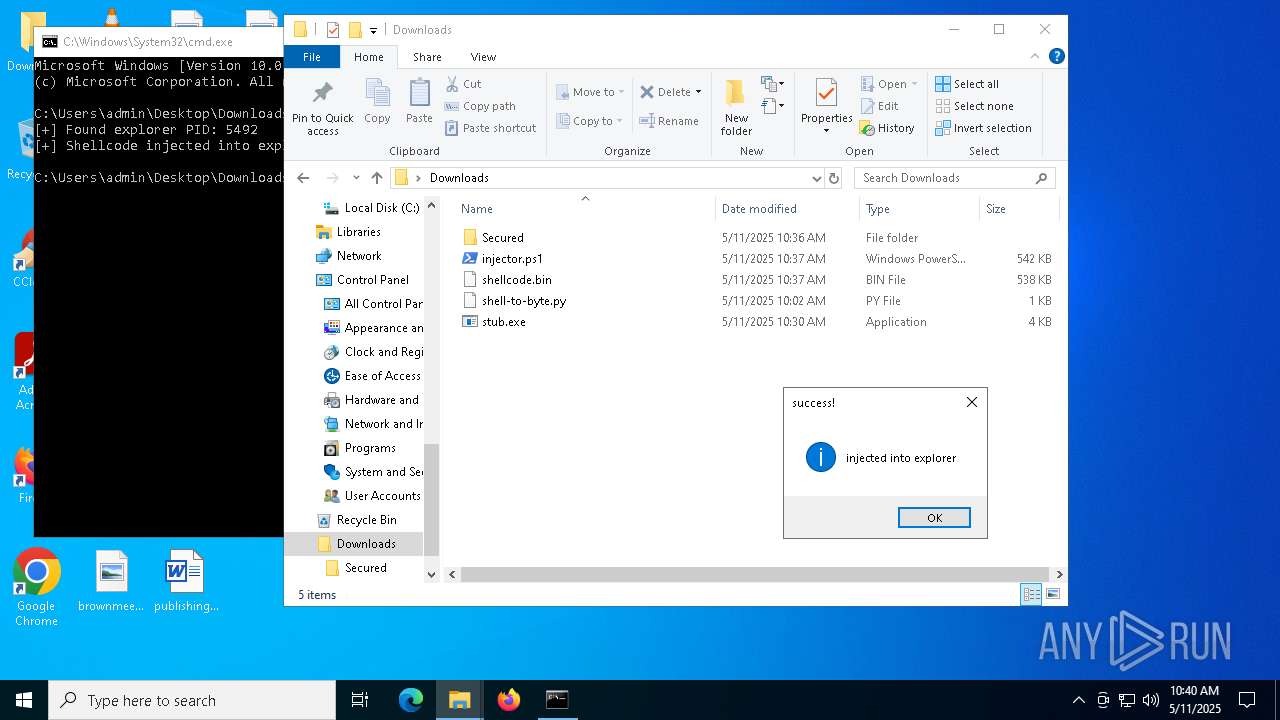
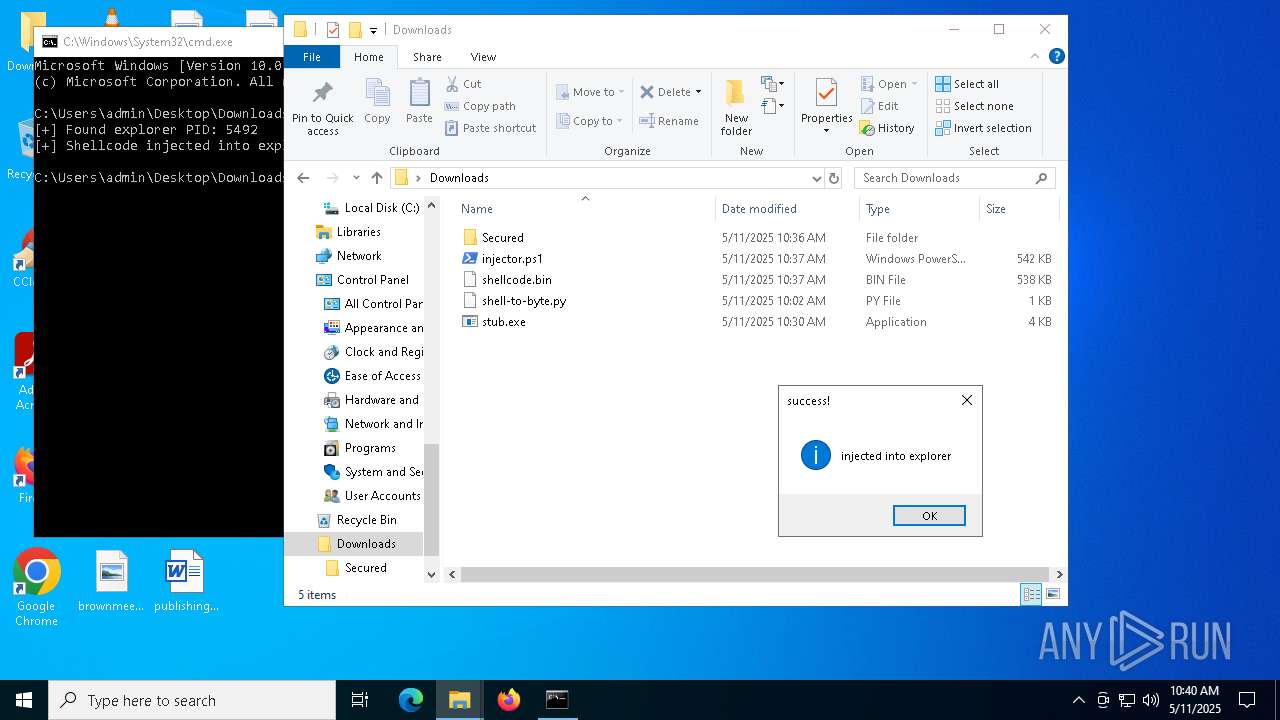
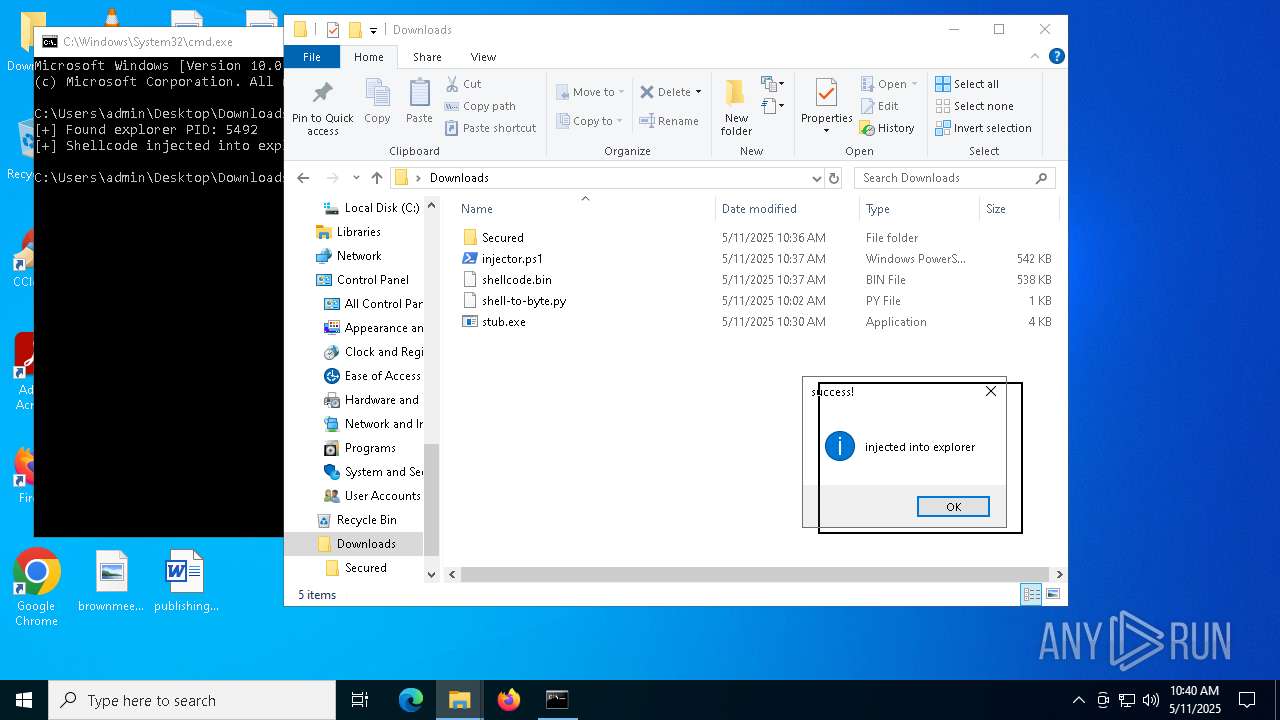
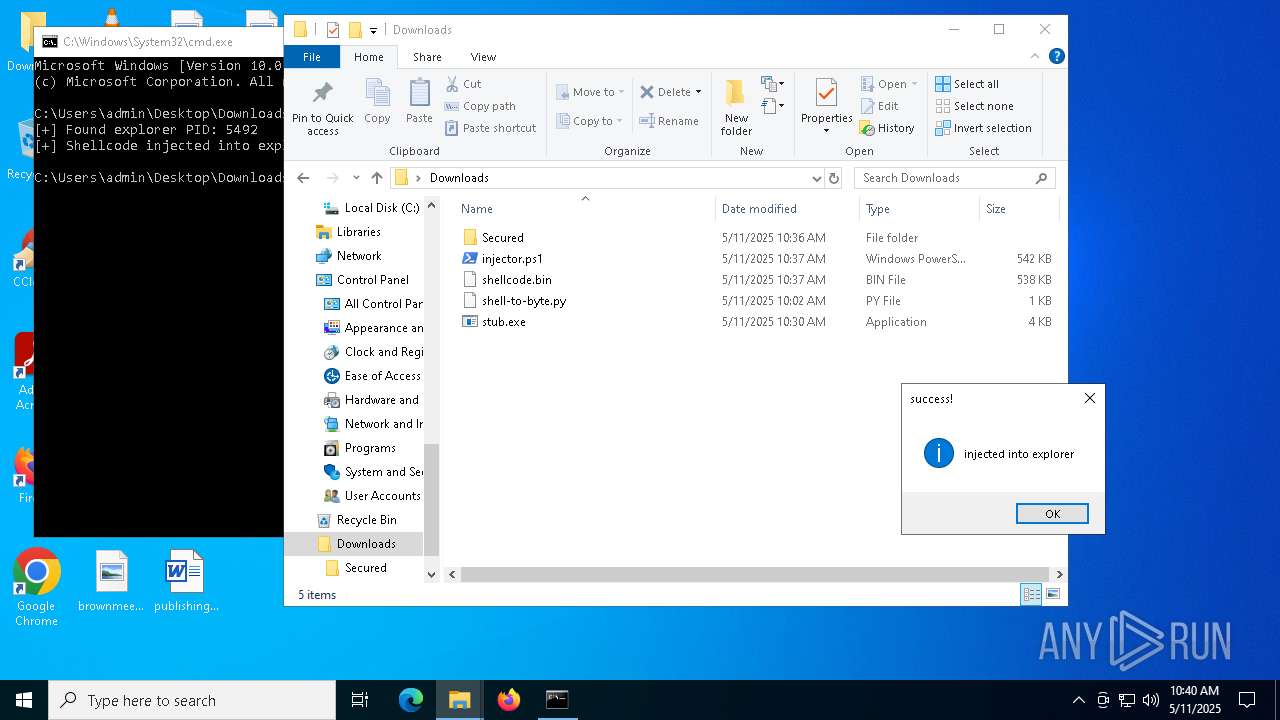
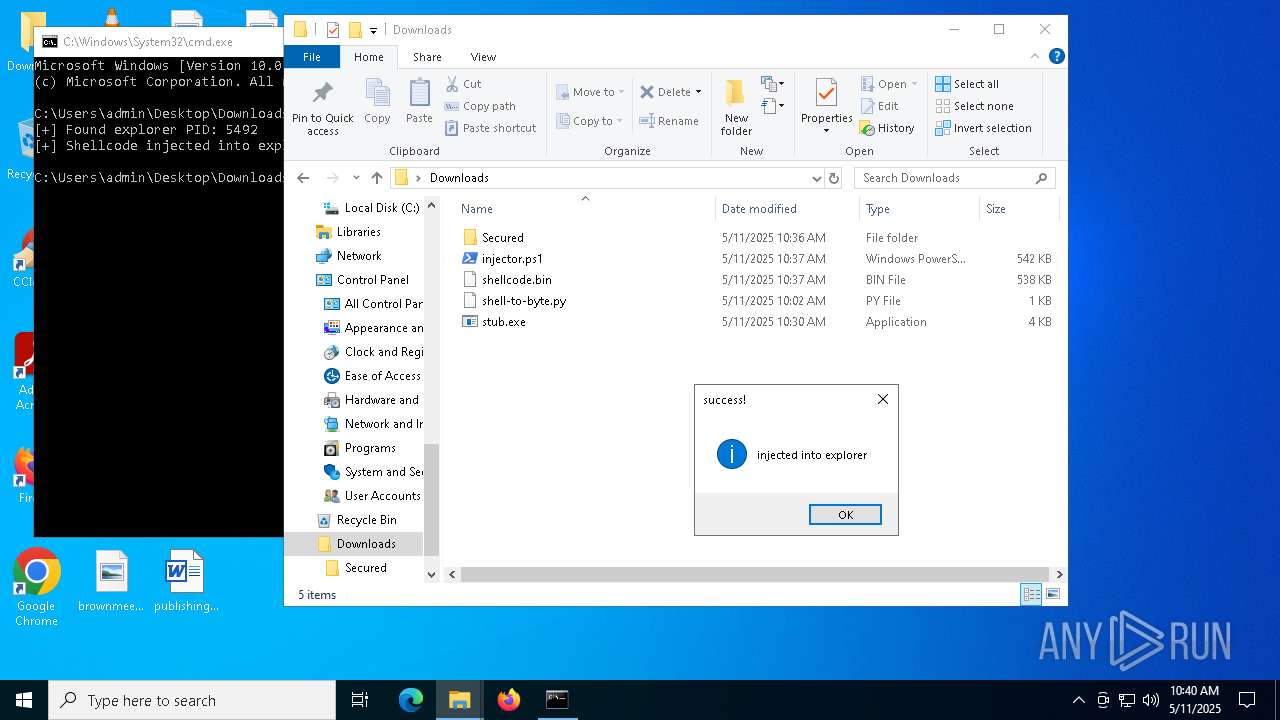
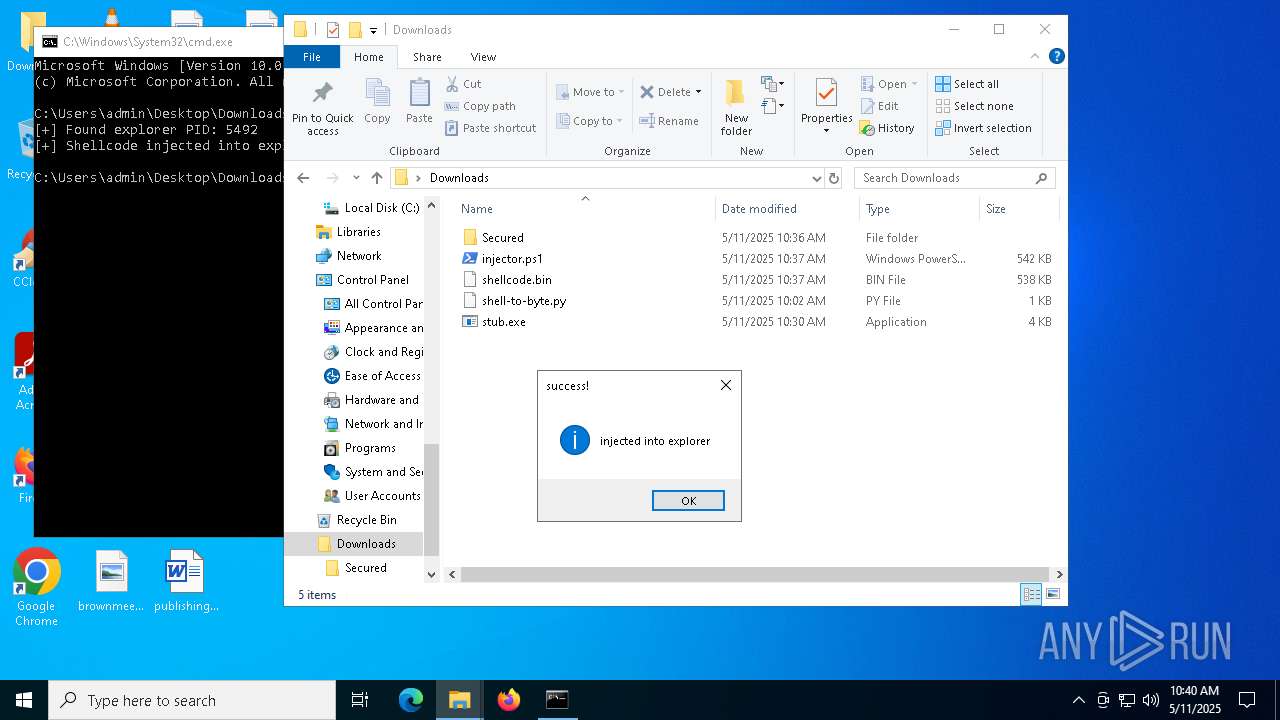
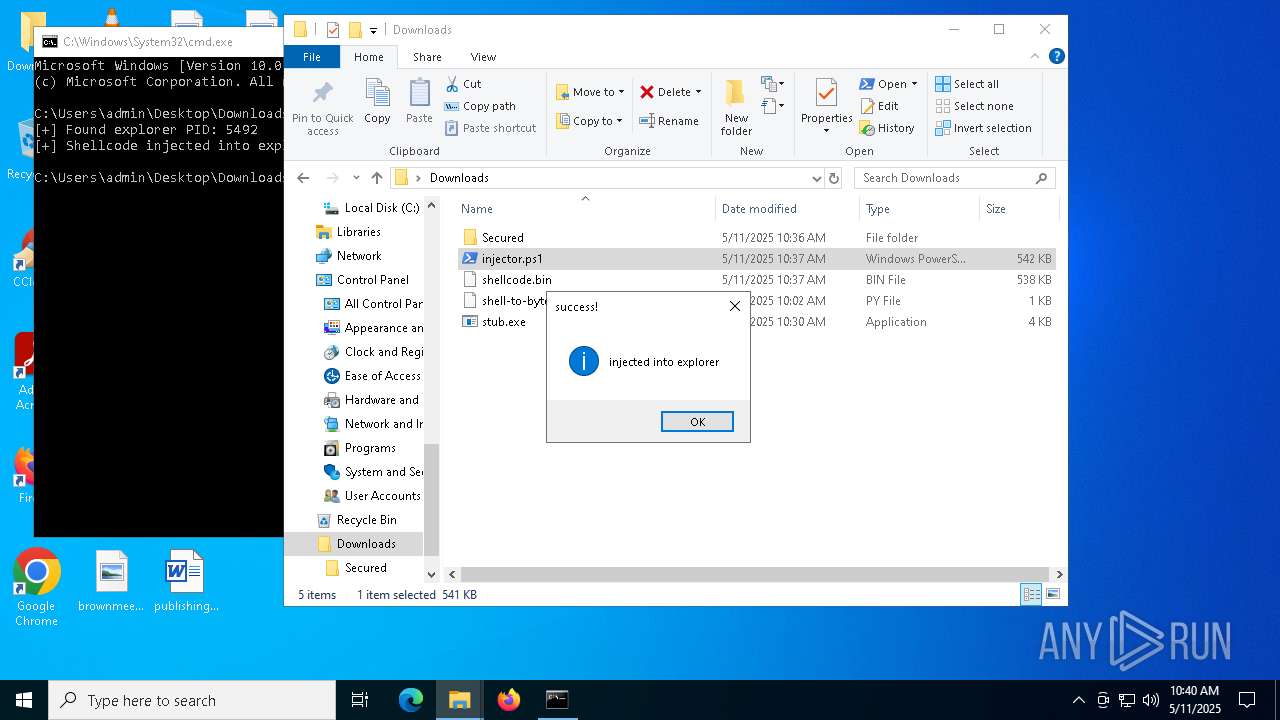
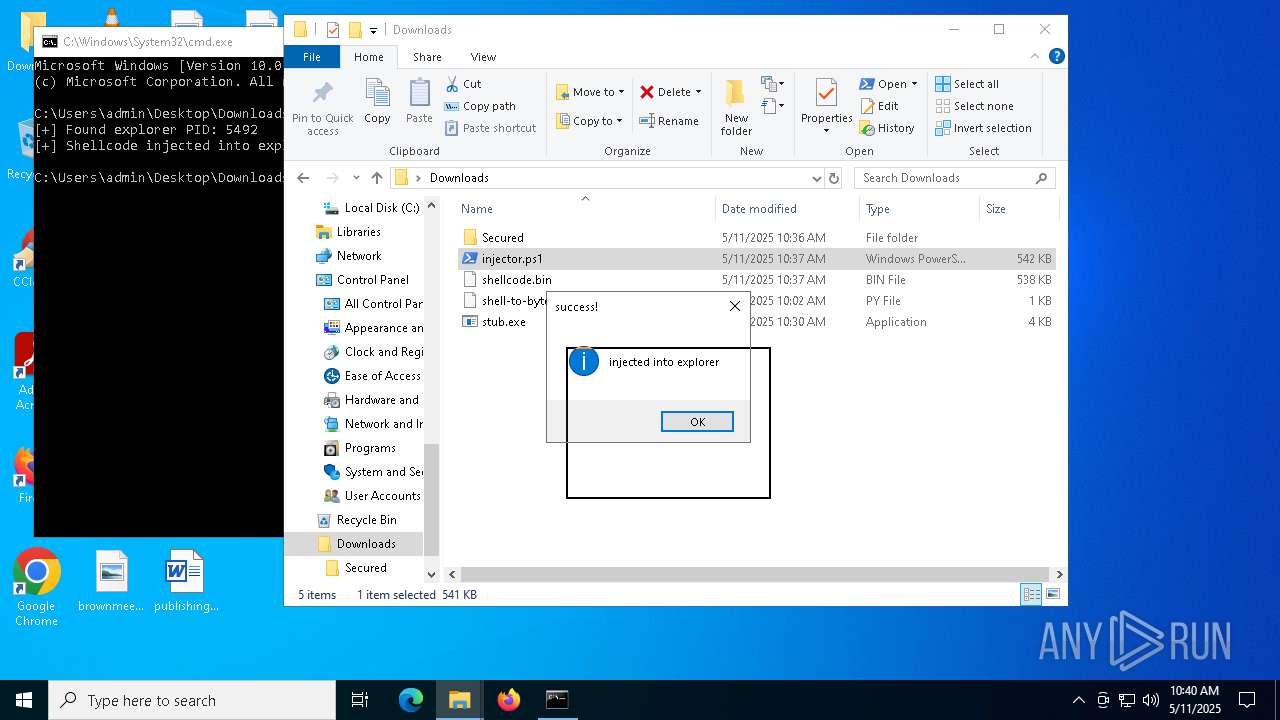
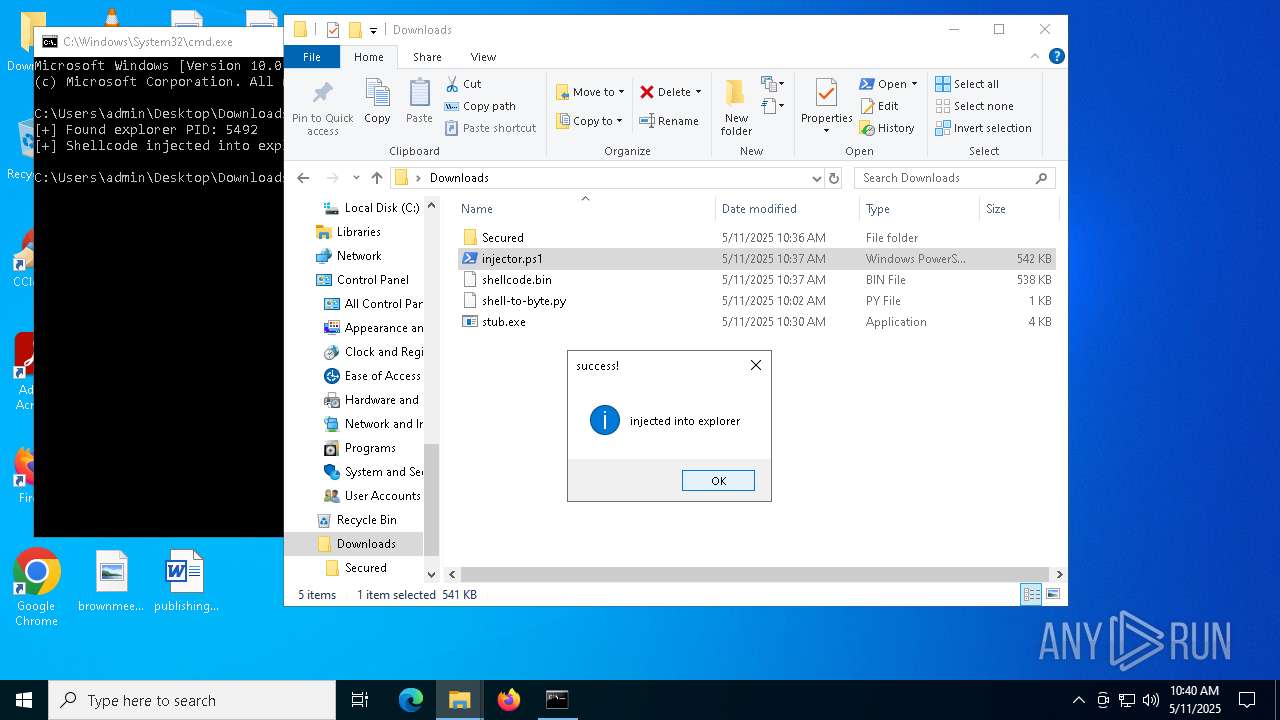
Runs injected code in another process
- powershell.exe (PID: 5600)
- powershell.exe (PID: 4736)
Application was injected by another process
- explorer.exe (PID: 5492)
Changes powershell execution policy (Bypass)
- explorer.exe (PID: 5492)
SUSPICIOUS
Reads the BIOS version
- obfuscated.exe (PID: 5260)
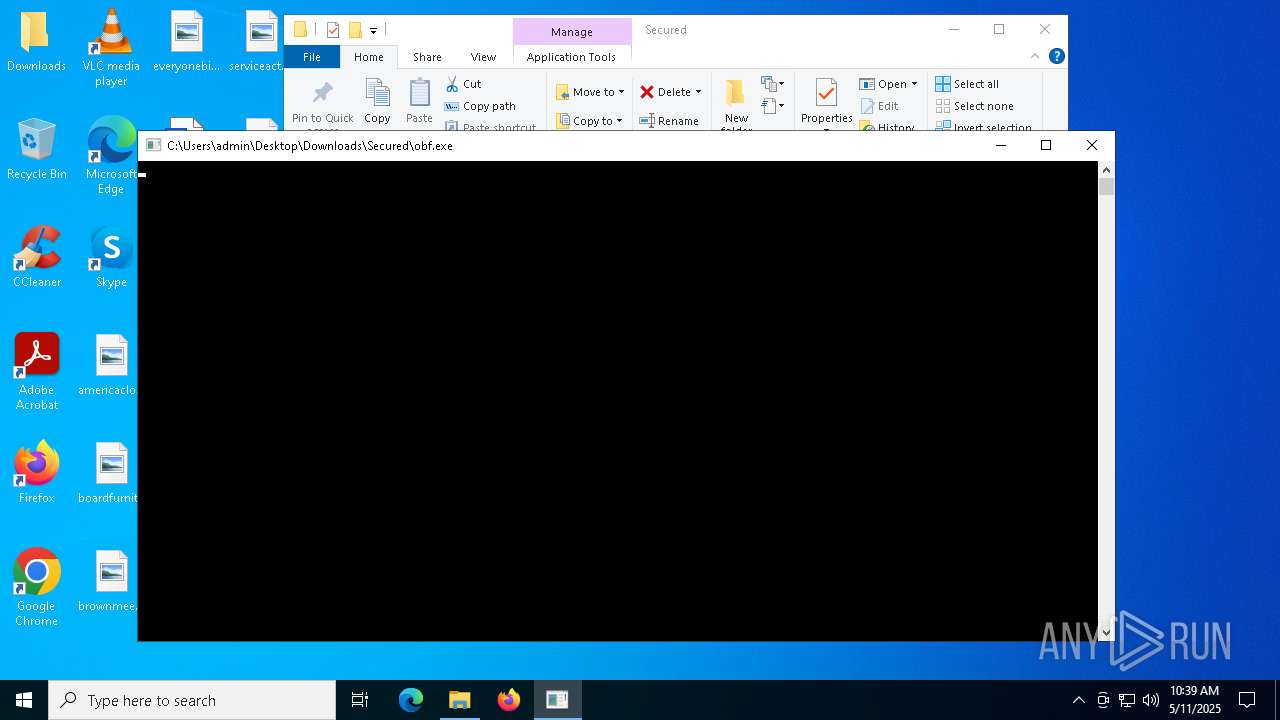
- obf.exe (PID: 4200)
Read disk information to detect sandboxing environments
- obfuscated.exe (PID: 5260)
- obf.exe (PID: 4200)
- explorer.exe (PID: 5492)
The process checks if it is being run in the virtual environment
- obfuscated.exe (PID: 5260)
- obf.exe (PID: 4200)
- explorer.exe (PID: 5492)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 5492)
- cmd.exe (PID: 632)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 5492)
The process executes Powershell scripts
- explorer.exe (PID: 5492)
- cmd.exe (PID: 632)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4180)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Manual execution by a user
- stub.exe (PID: 5972)
- obfuscated.exe (PID: 5260)
- obf.exe (PID: 4200)
- powershell.exe (PID: 920)
- cmd.exe (PID: 632)
- powershell.exe (PID: 4736)
Checks supported languages
- stub.exe (PID: 5972)
- obfuscated.exe (PID: 5260)
- obf.exe (PID: 4200)
Reads the computer name
- stub.exe (PID: 5972)
- obfuscated.exe (PID: 5260)
- obf.exe (PID: 4200)
Reads the machine GUID from the registry
- obf.exe (PID: 4200)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Gets data length (POWERSHELL)
- powershell.exe (PID: 920)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 4736)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 920)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 4736)
Reads the software policy settings
- slui.exe (PID: 6184)
- slui.exe (PID: 7020)
Checks proxy server information
- slui.exe (PID: 7020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:11 11:36:52 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
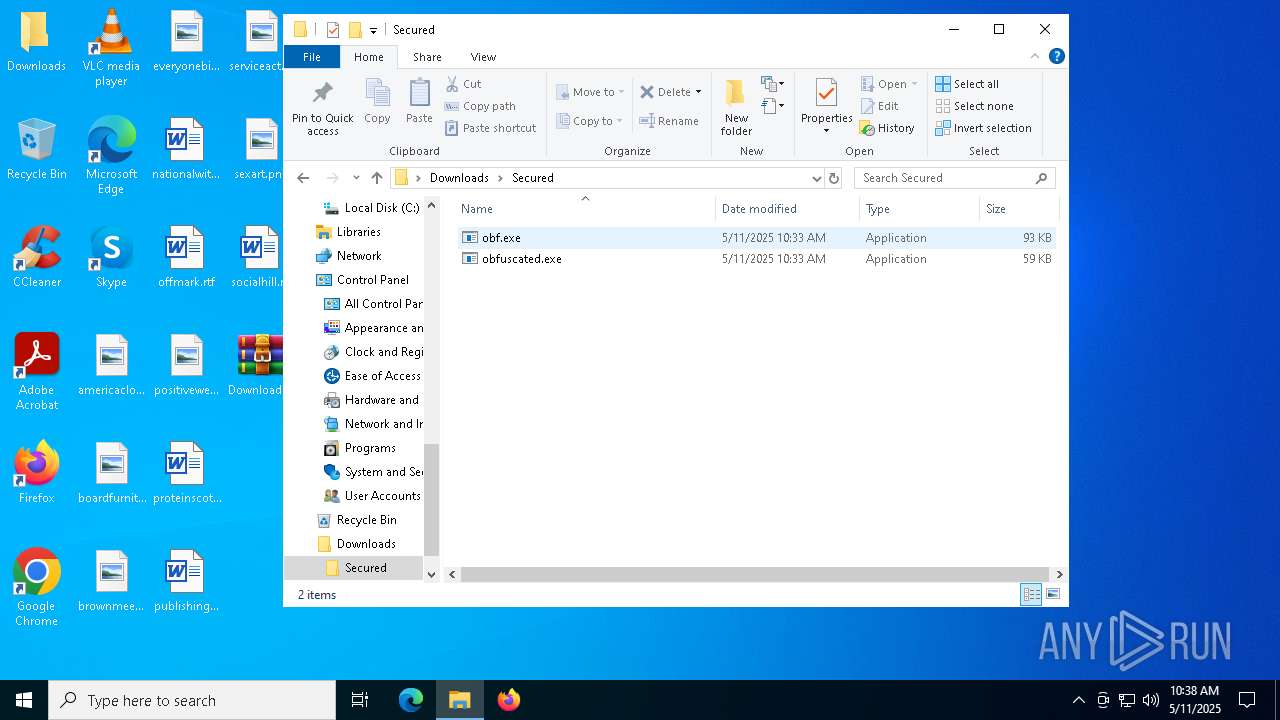
| ZipFileName: | Secured/ |
Total processes
148
Monitored processes
19
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | obfuscated.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | obf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
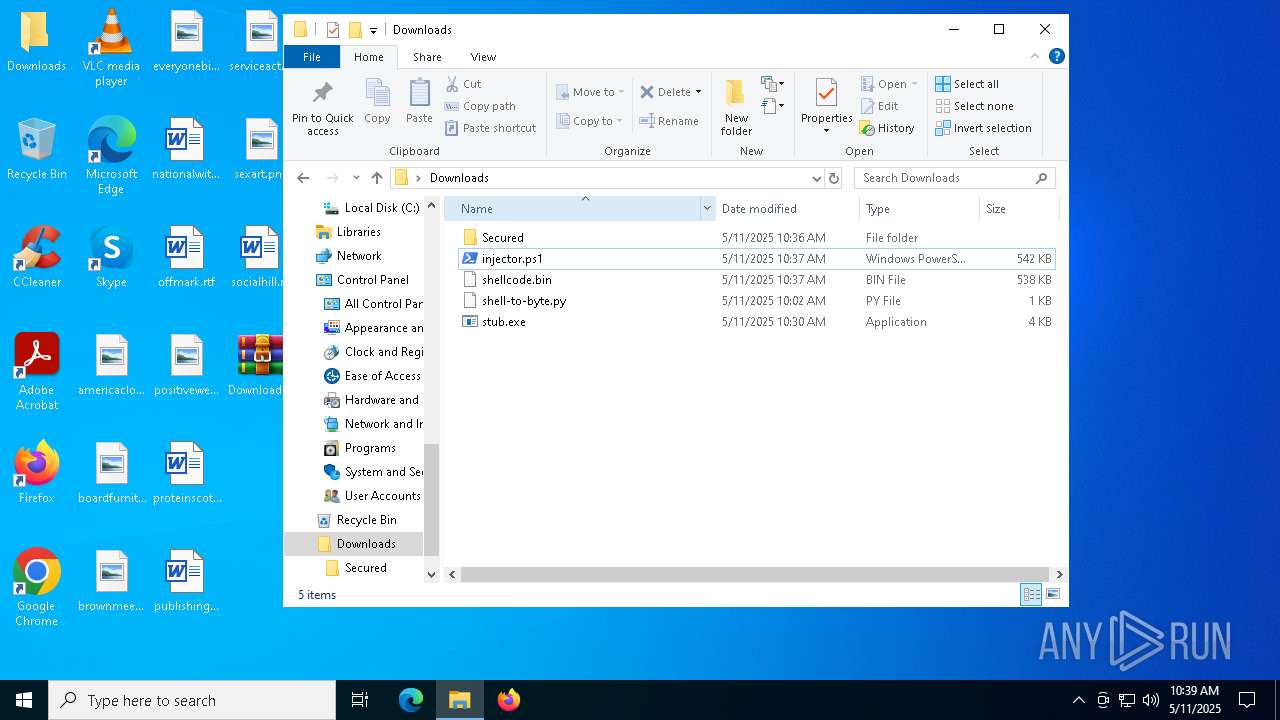
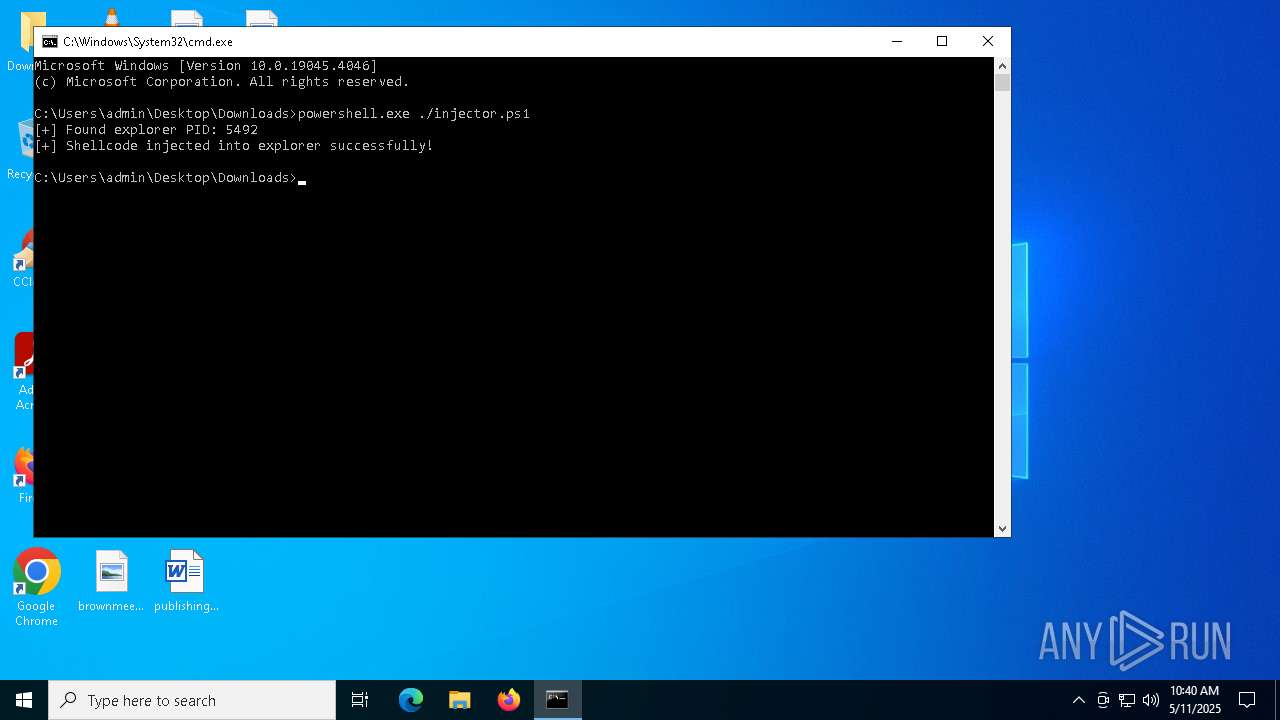
| 920 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\Downloads\injector.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Downloads.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4200 | "C:\Users\admin\Desktop\Downloads\Secured\obf.exe" | C:\Users\admin\Desktop\Downloads\Secured\obf.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4736 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\Downloads\injector.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 718
Read events
46 496
Write events
174
Delete events
48
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000040348 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C000000170000000000000061006D006500720069006300610063006C006F007400680069006E0067002E006A00700067003E00200020000000160000000000000062006F006100720064006600750072006E00690074007500720065002E0070006E0067003E002000200000001100000000000000620072006F0077006E006D006500650074002E006A00700067003E002000200000001400000000000000650076006500720079006F006E006500620069006C006C002E0070006E0067003E0020002000000014000000000000006E006100740069006F006E0061006C0077006900740068002E007200740066003E002000200000000F000000000000006F00660066006D00610072006B002E007200740066003E00200020000000150000000000000070006F007300690074006900760065007700650065006B0073002E006A00700067003E002000200000001400000000000000700072006F007400650069006E00730063006F00740074002E007200740066003E0020002000000015000000000000007000750062006C0069007300680069006E0067006F006E0065002E007200740066003E00200020000000120000000000000073006500720076006900630065006100630074002E0070006E0067003E002000200000000E000000000000007300650078006100720074002E0070006E0067003E00200020000000120000000000000073006F006300690061006C00680069006C006C002E007200740066003E00200020000000110000000000000044006F0077006E006C006F006100640073002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000040400000803F1300000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000004040000000401400 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 287E206800000000 | |||
| (PID) Process: | (4180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Downloads.zip | |||
| (PID) Process: | (4180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
3
Suspicious files
7
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
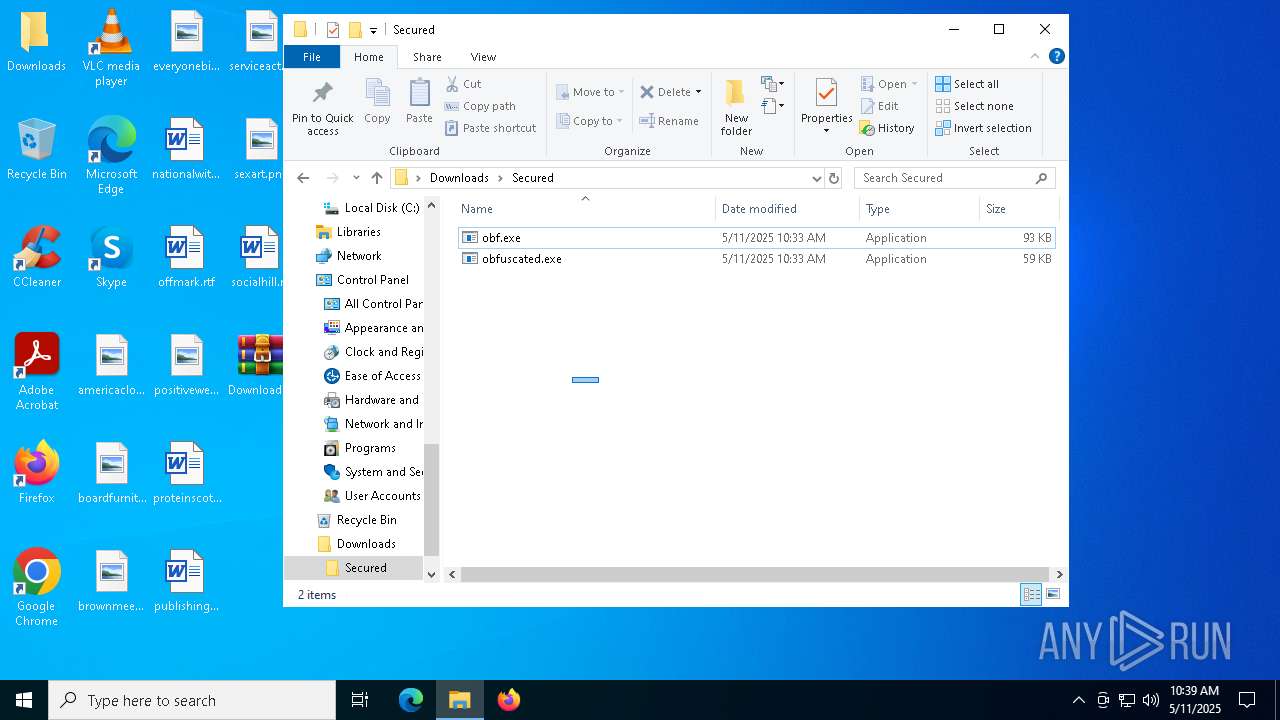
| 4180 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\Secured\obfuscated.exe | executable | |
MD5:8B868C2F8A0C31F81C6359DD2B028460 | SHA256:D5D0FFB88CB1B4E32A4D92403B33A572B35DBD0FEB4CDB0325E66A2FE2D22B4B | |||
| 4180 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\Secured\obf.exe | executable | |
MD5:CDE05FF0BAC93BE93B167484474F265B | SHA256:2FBDE60A730C6D61F248DE03297616534BACDCB04D54A9C93DA282B65718C67D | |||
| 5600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jha5eivv.wlf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
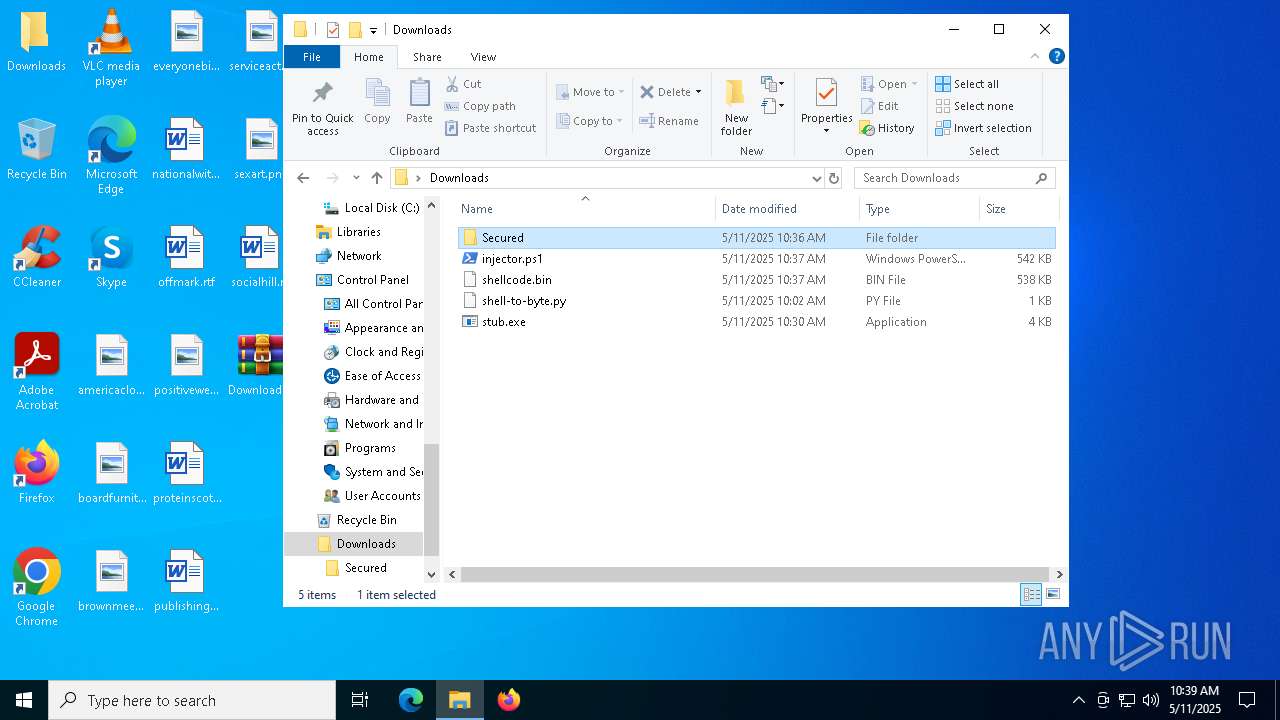
| 4180 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\shell-to-byte.py | text | |
MD5:C3359E6F992E3D2EC749D958B99F07B4 | SHA256:85C49898CB2C4981243E2CADE9996BDB5718691BAA54DD240CC15CCDDDE87F51 | |||
| 4180 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\stub.exe | executable | |
MD5:27717C3E5ED25DD205012203EC2EAD8D | SHA256:71368A53759F3BD1C2A6892D38A110B96CE01B15440A81C234785CE3C23E8EFD | |||
| 920 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:39DCBD8E624591253B968EDC1BA854E2 | SHA256:6EEE75C5C856BFA0E6C2766139C89429EBF90072C1576A952125F45B76700327 | |||
| 4180 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\shellcode.bin | text | |
MD5:D86F4EC4A3F451FE557616DBF42768E2 | SHA256:2D5A1D9FE381973E8191CD0E24EA789E57F000EAED07AFDC7E1A8F6A7DA1AABA | |||
| 5600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_b54ybgld.lze.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 920 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:AAA9F9D599C8671D2943BF36D815A6A7 | SHA256:500E2DA24140910AC06D8D252642D26B2C289AFB112D9BEBF99C8FD0F0F46666 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5868 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5868 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5868 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |