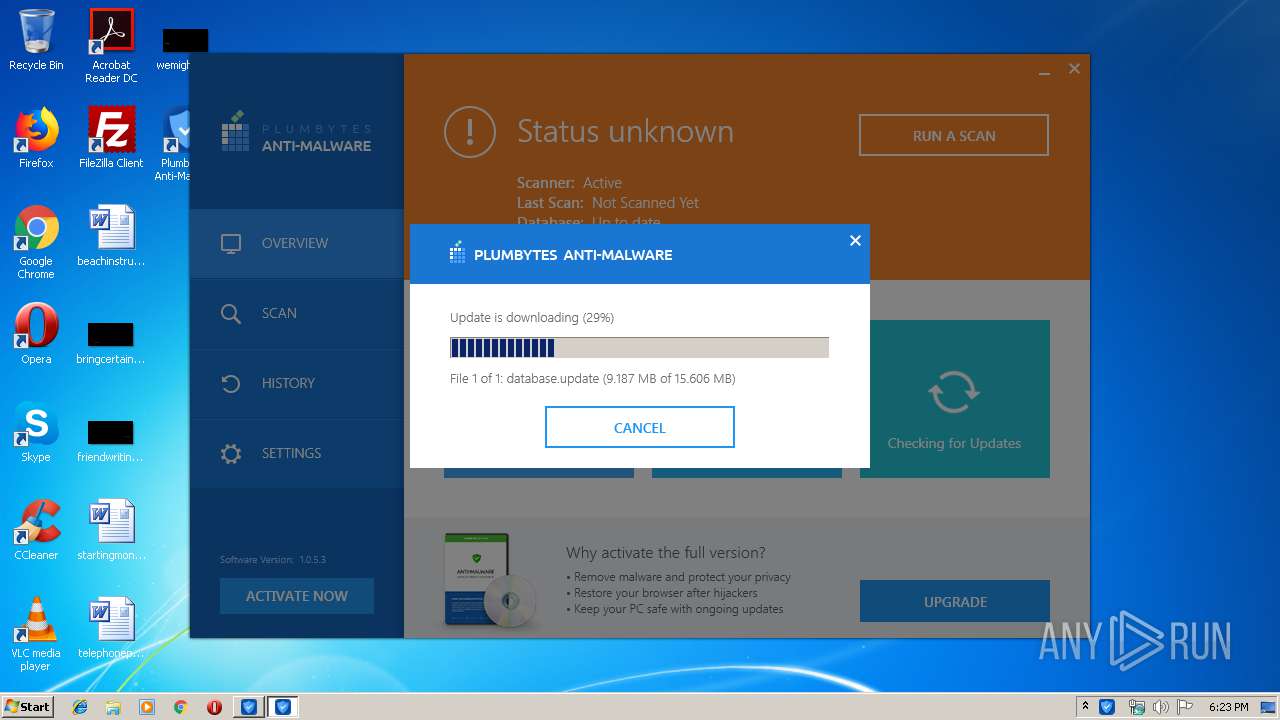
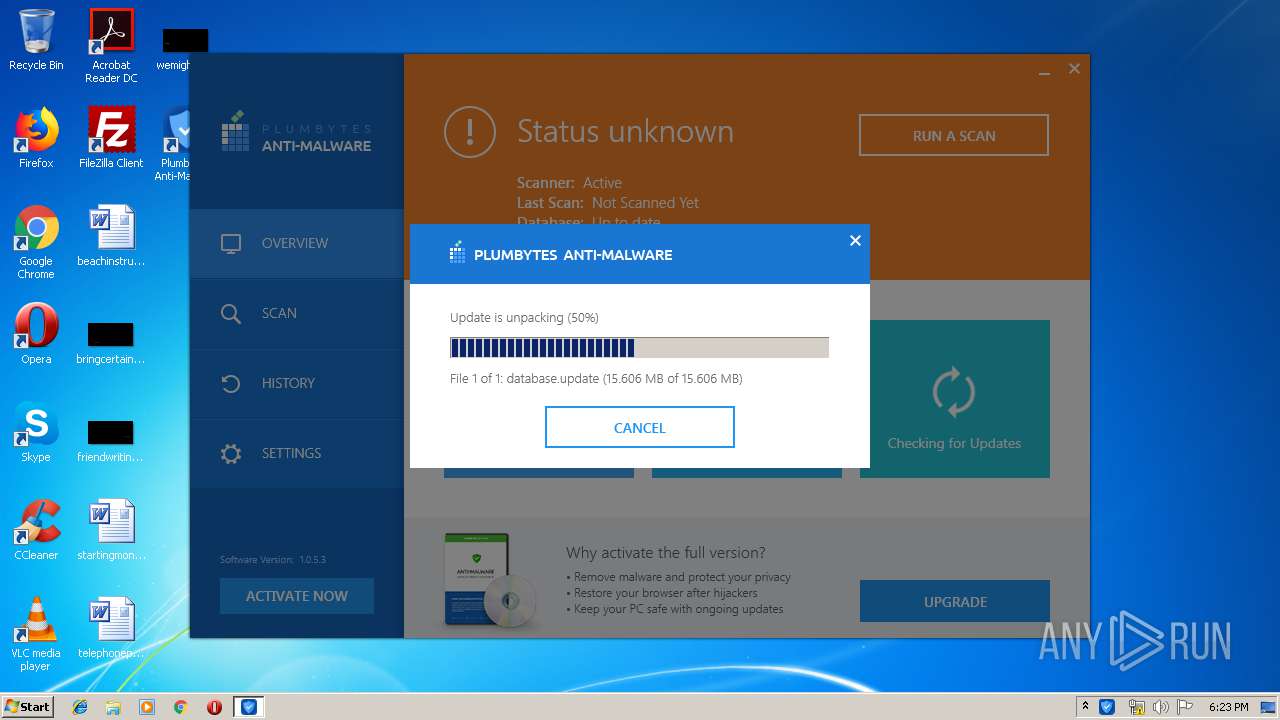
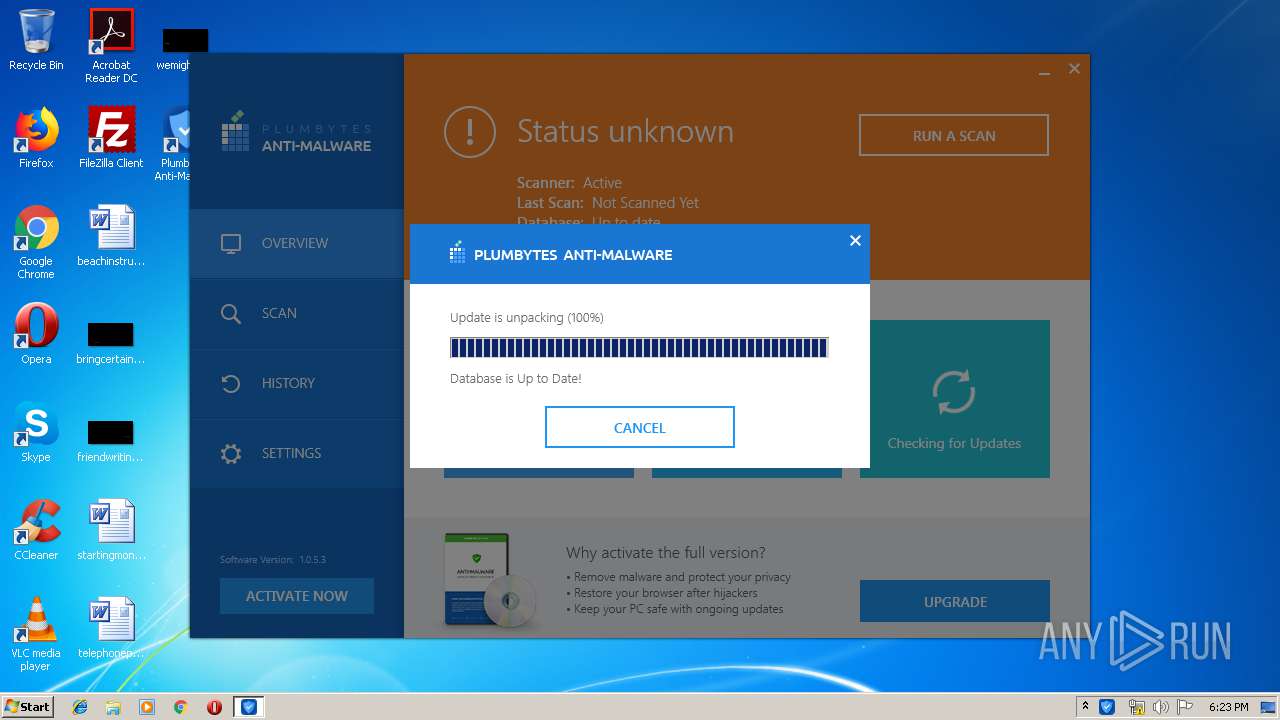
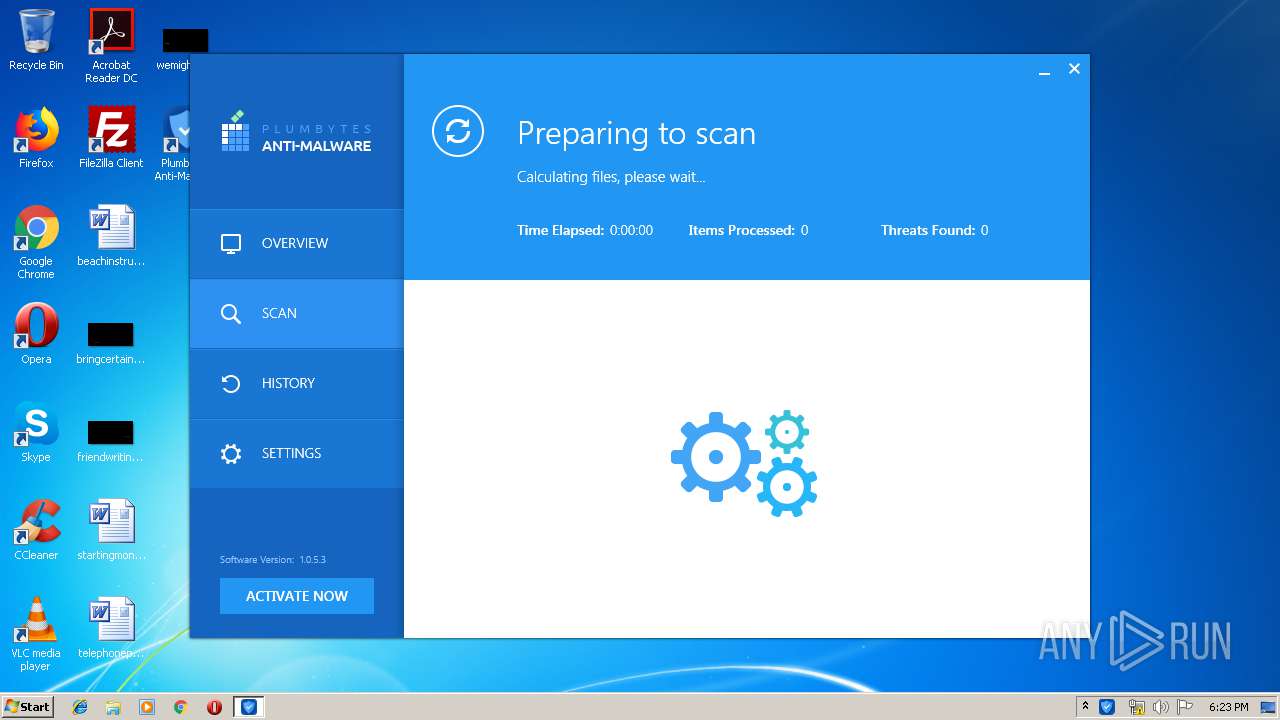
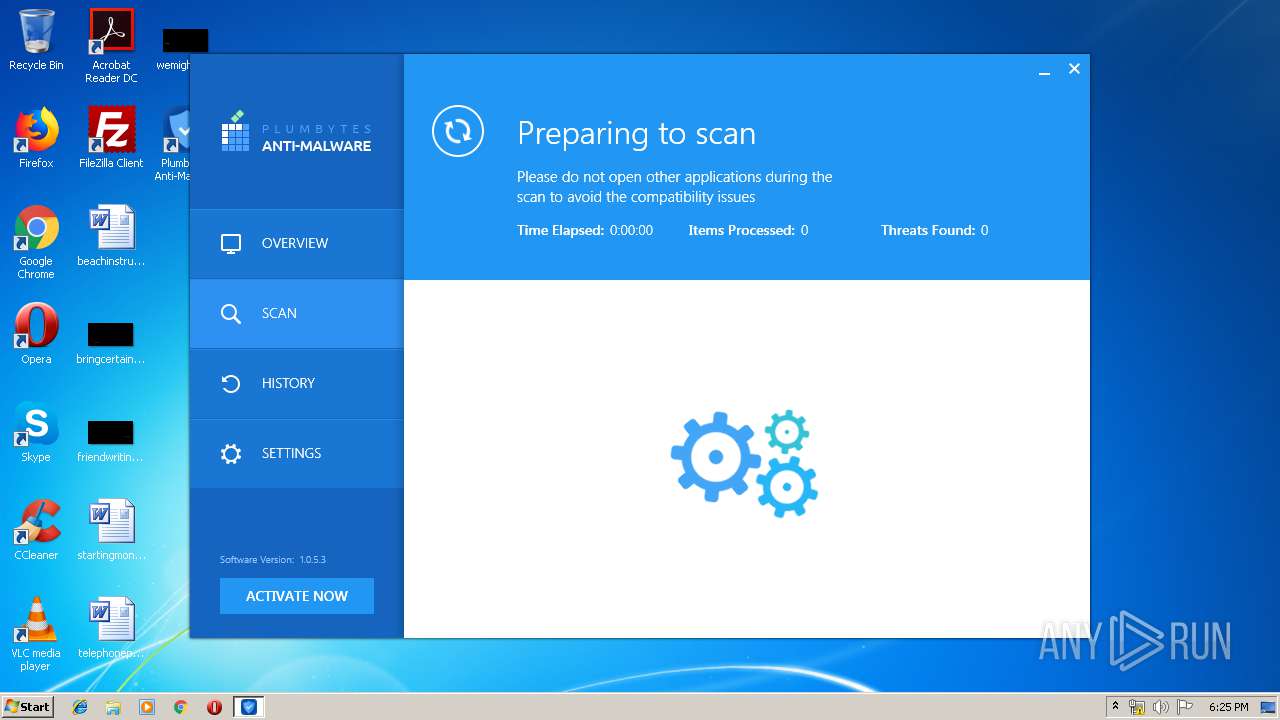
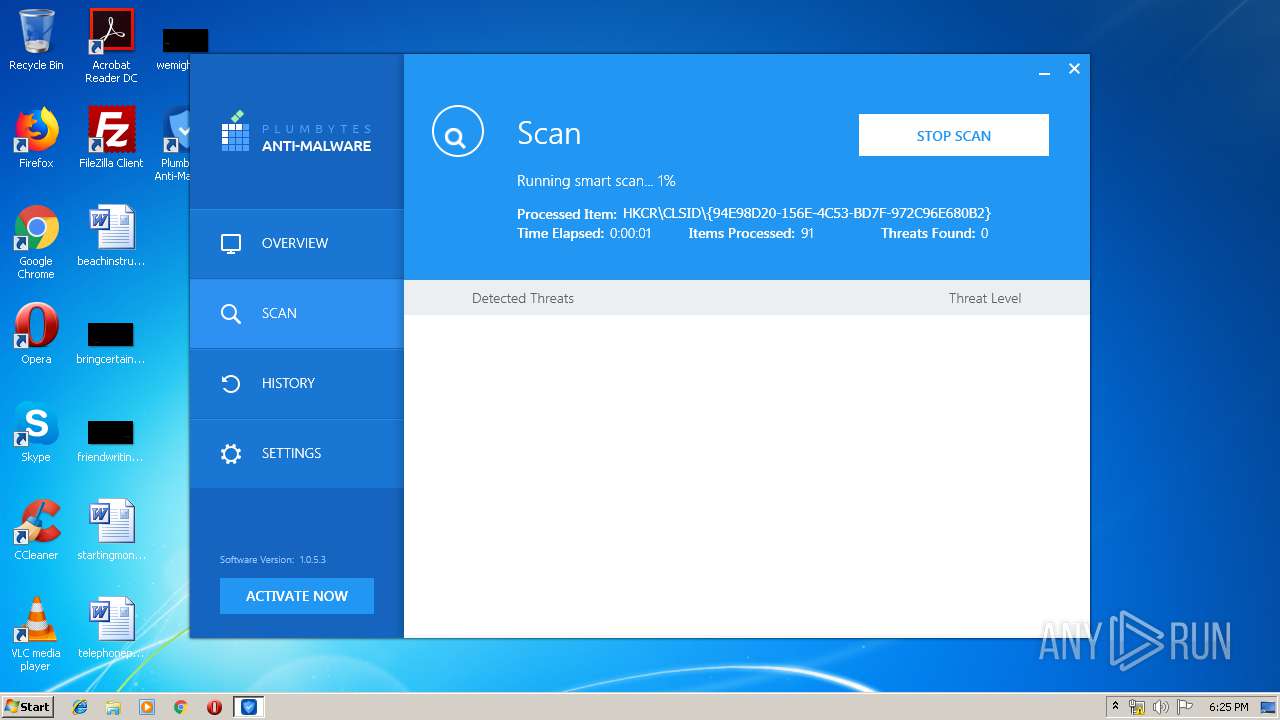
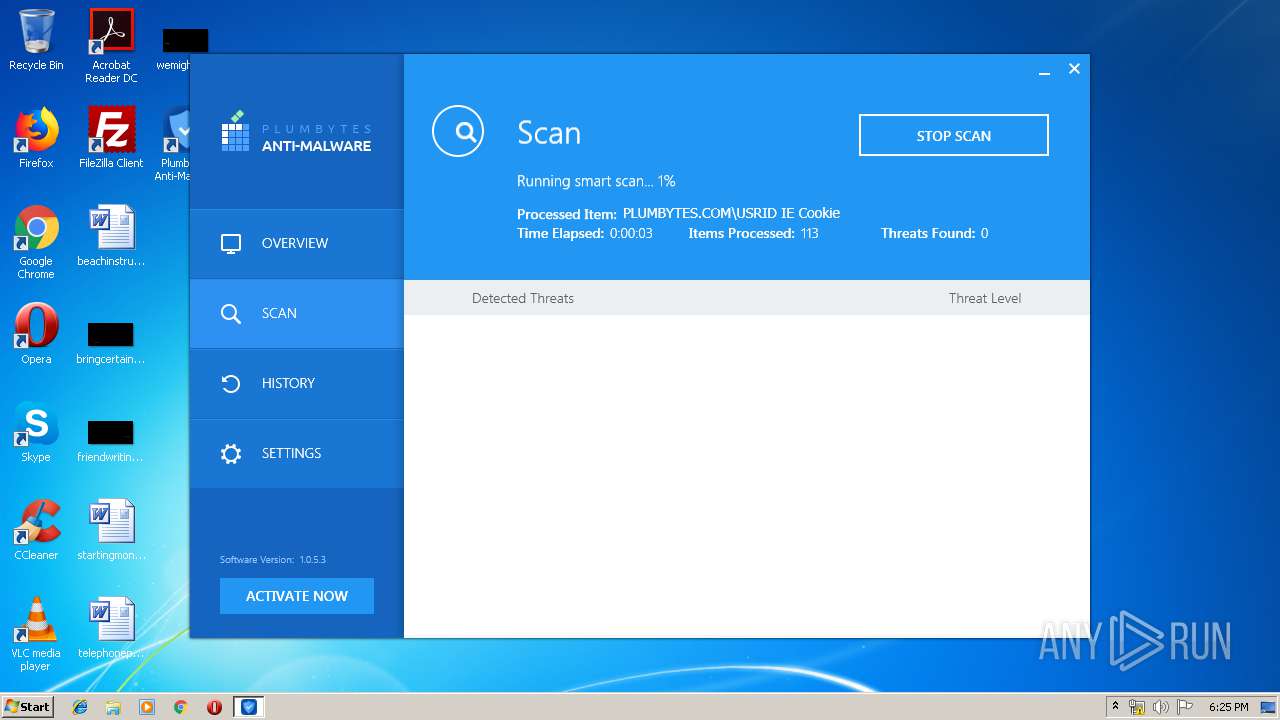
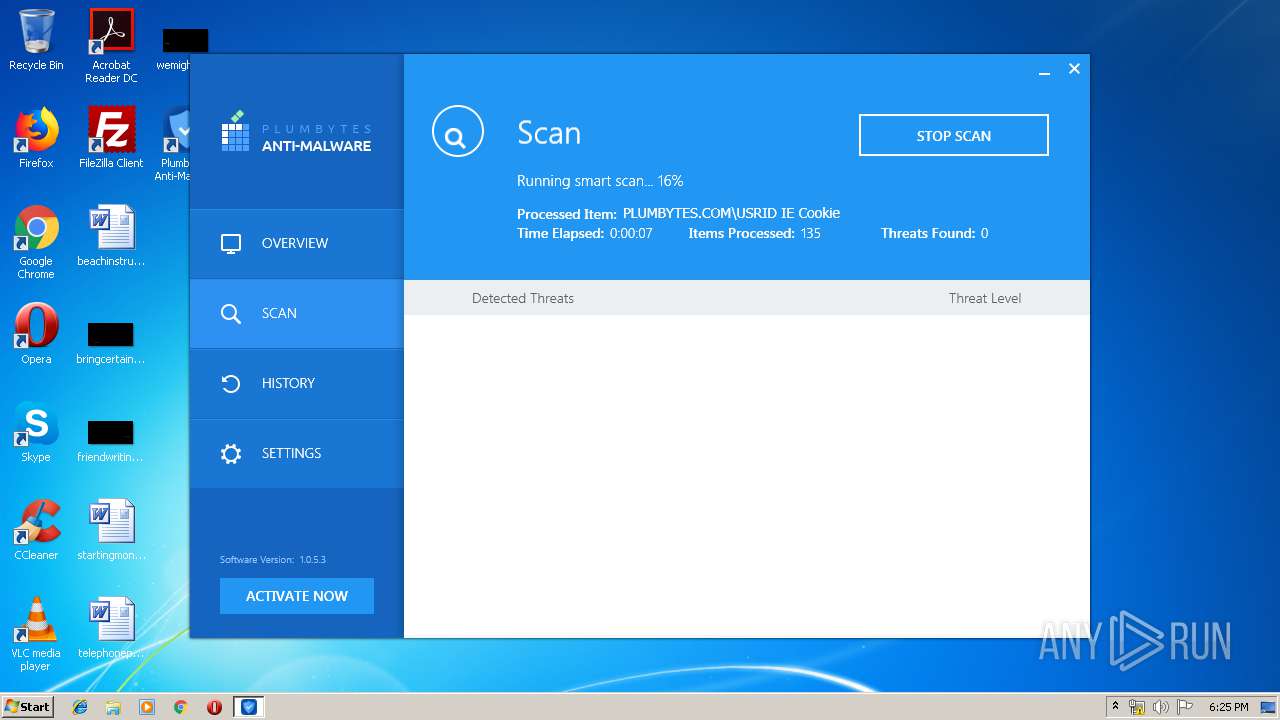
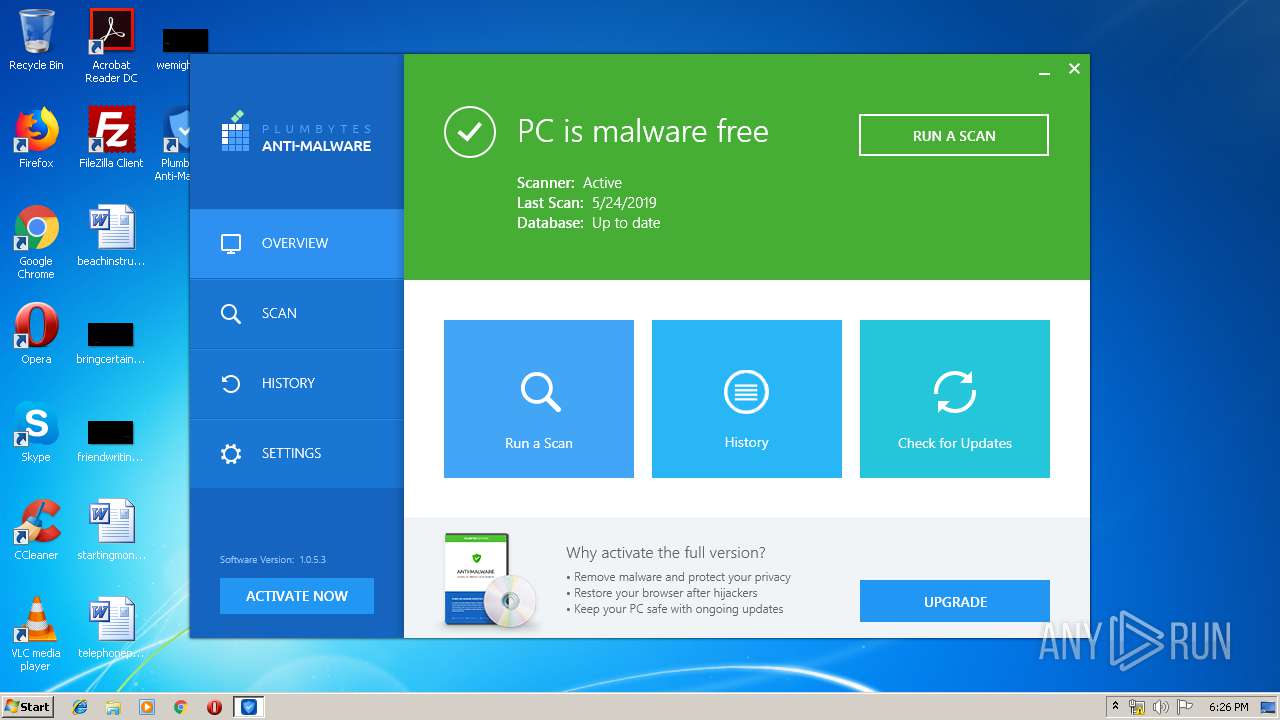
| URL: | http://www.plumbytes.com/download/cuid/?tid=rwid_p00000 |
| Full analysis: | https://app.any.run/tasks/f035cc5c-5926-4d50-8ec5-900948826c92 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2019, 17:22:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FB272237645C97D5C553376D8DCBDAA4 |
| SHA1: | 48F28A6C7F1F990EDDF86FBCAFC7F270B088BC16 |
| SHA256: | 67F1CC45583ECFB089FF1E8DC279FFCEB7030860BC11212D1AA02F178DCFC96B |
| SSDEEP: | 3:N1KJS4pdWKL2X0d/V:Cc4pdNk0FV |
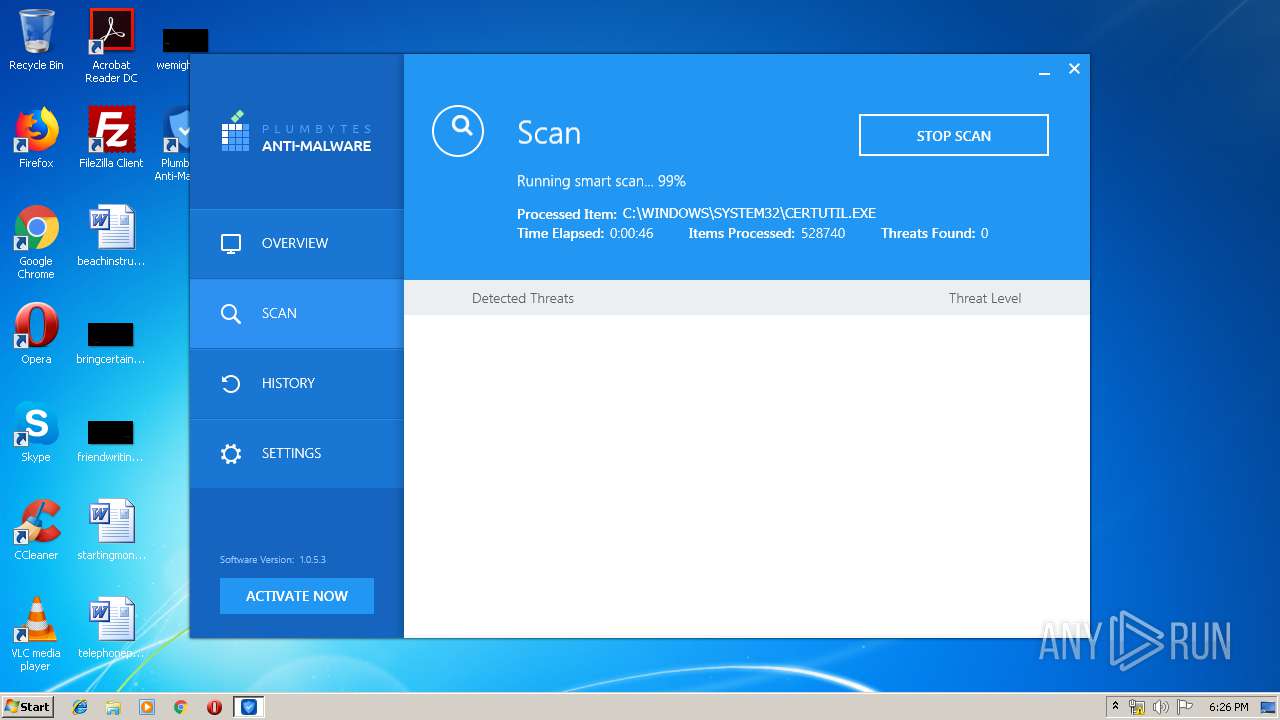
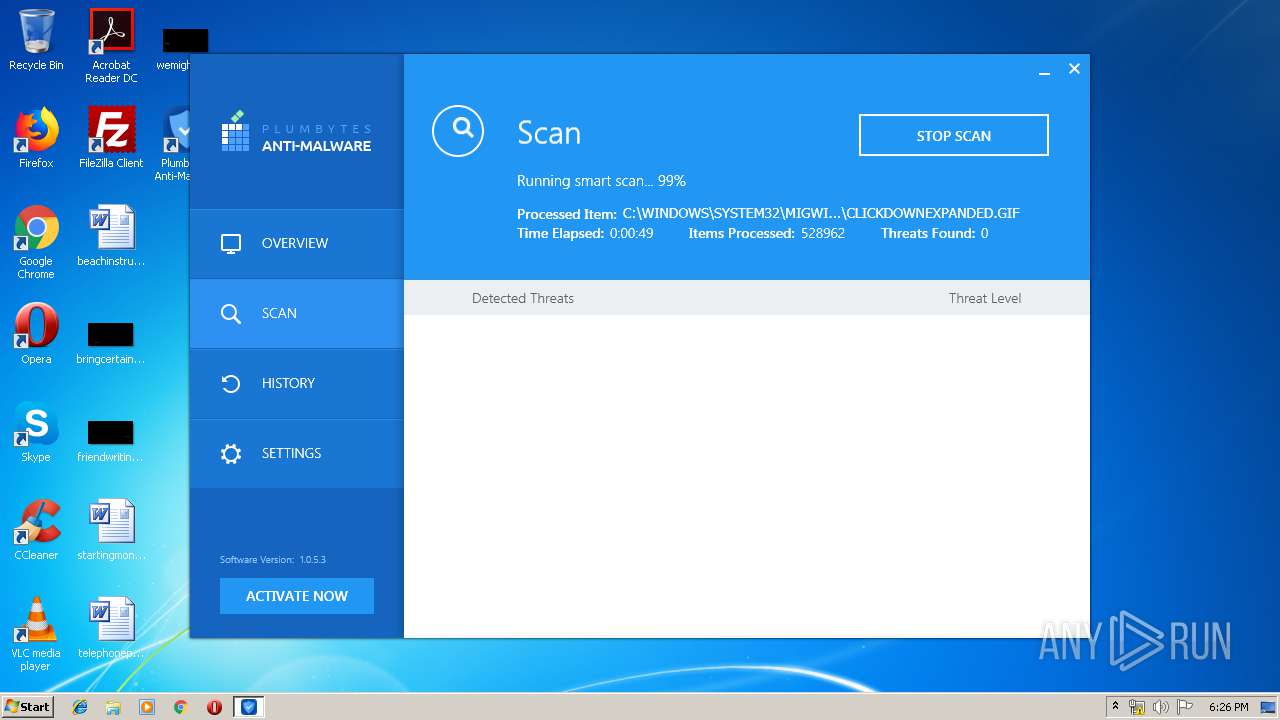
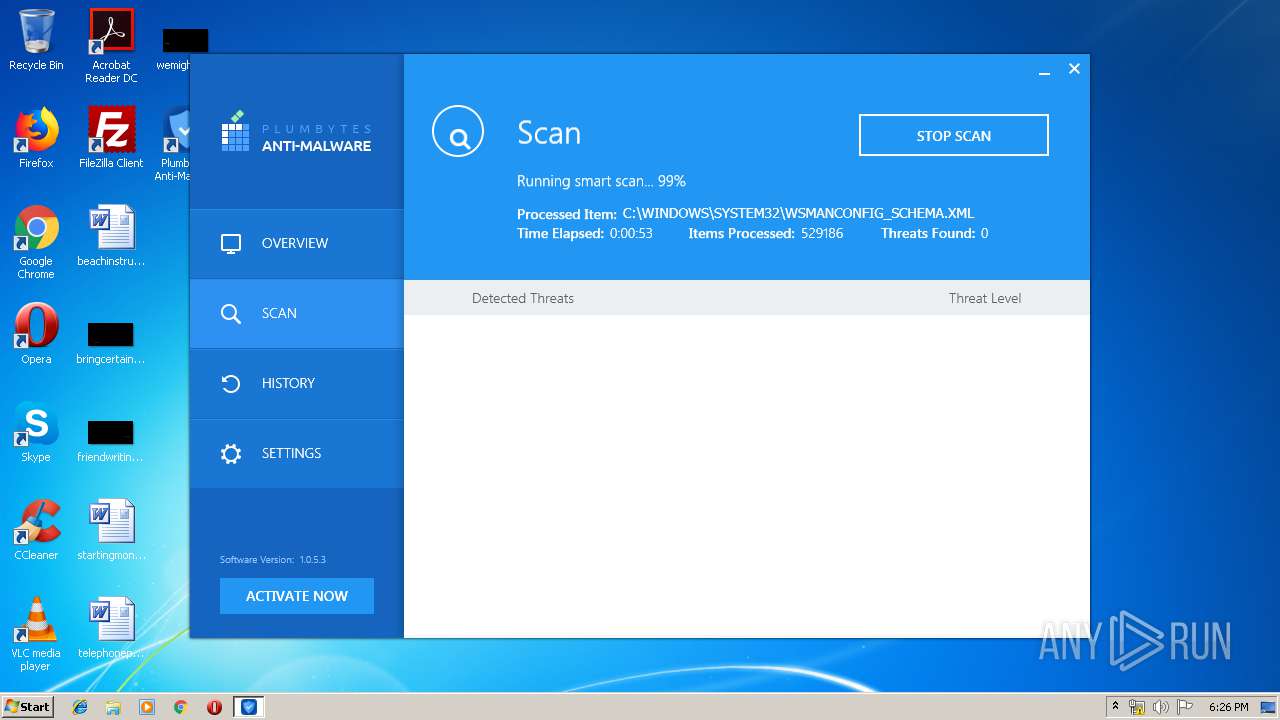
MALICIOUS
Application was dropped or rewritten from another process
- cuid[1].exe (PID: 3660)
- cuid[1].exe (PID: 2748)
- pai364C.tmp (PID: 3928)
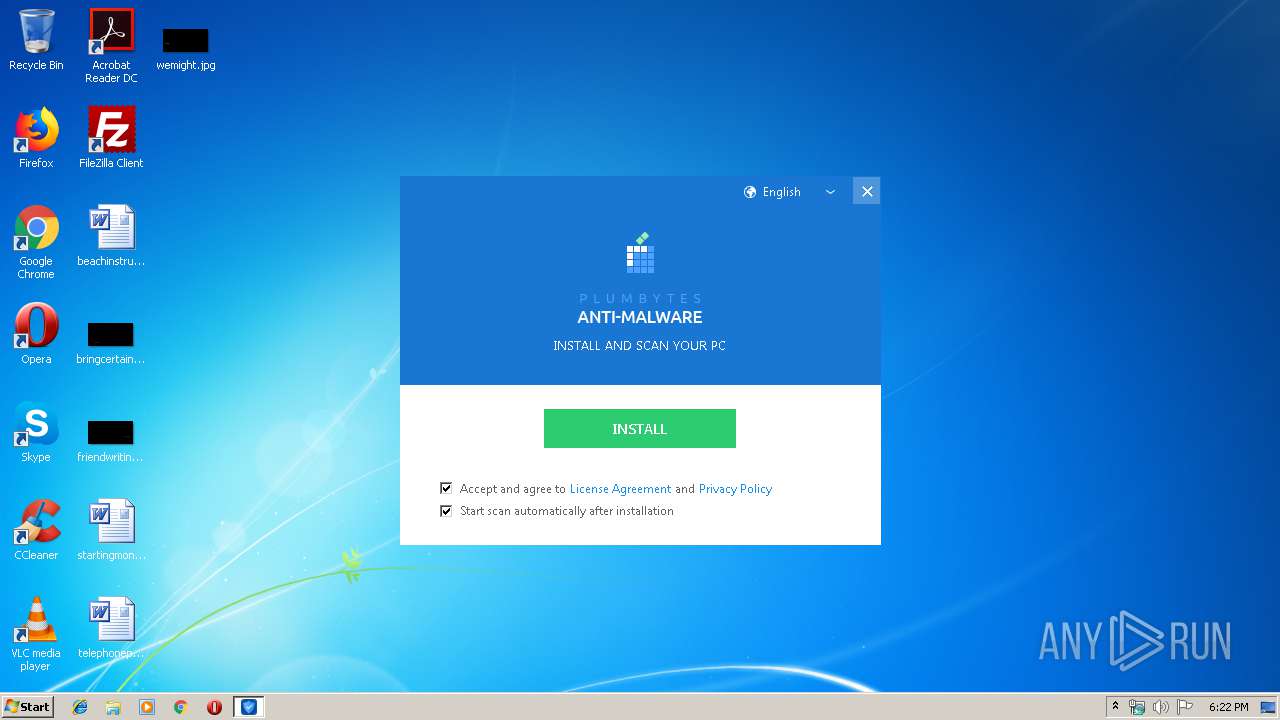
- Plumbytes.exe (PID: 2712)
- AmwService.exe (PID: 3404)
- AmwService.exe (PID: 3120)
- AmwService.exe (PID: 2572)
Changes settings of System certificates
- pai364C.tmp (PID: 3928)
- AmwService.exe (PID: 3120)
Loads dropped or rewritten executable
- pai364C.tmp (PID: 3928)
- AmwService.exe (PID: 3120)
- Plumbytes.exe (PID: 2712)
- AmwService.exe (PID: 3404)
- AmwService.exe (PID: 2572)
Changes the autorun value in the registry
- pai364C.tmp (PID: 3928)
Actions looks like stealing of personal data
- AmwService.exe (PID: 3120)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 3228)
- pai364C.tmp (PID: 3928)
- cuid[1].exe (PID: 2748)
Uses RUNDLL32.EXE to load library
- cuid[1].exe (PID: 2748)
Adds / modifies Windows certificates
- pai364C.tmp (PID: 3928)
- AmwService.exe (PID: 3120)
Reads Internet Cache Settings
- rundll32.exe (PID: 3572)
- pai364C.tmp (PID: 3928)
Starts application with an unusual extension
- cuid[1].exe (PID: 2748)
Creates files in the program directory
- pai364C.tmp (PID: 3928)
- AmwService.exe (PID: 3120)
Creates files in the user directory
- pai364C.tmp (PID: 3928)
Creates a software uninstall entry
- pai364C.tmp (PID: 3928)
Reads Environment values
- Plumbytes.exe (PID: 2712)
Creates files in the Windows directory
- AmwService.exe (PID: 3120)
Application launched itself
- AmwService.exe (PID: 3120)
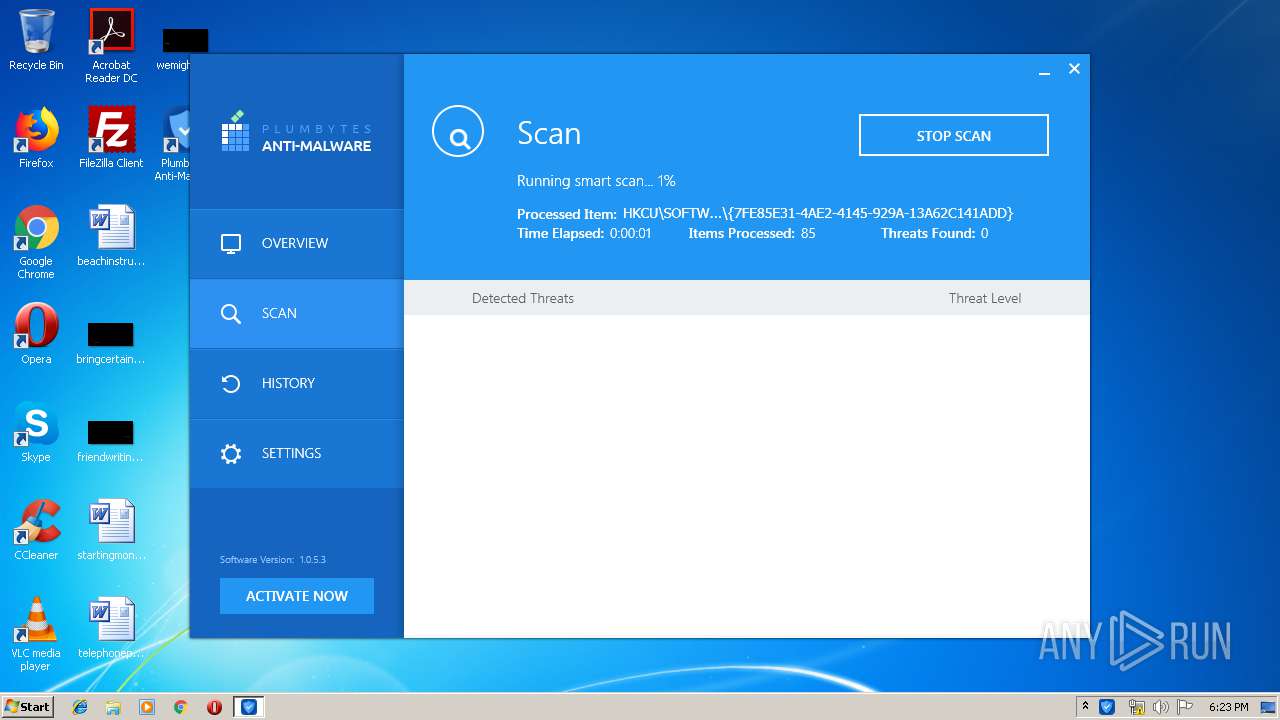
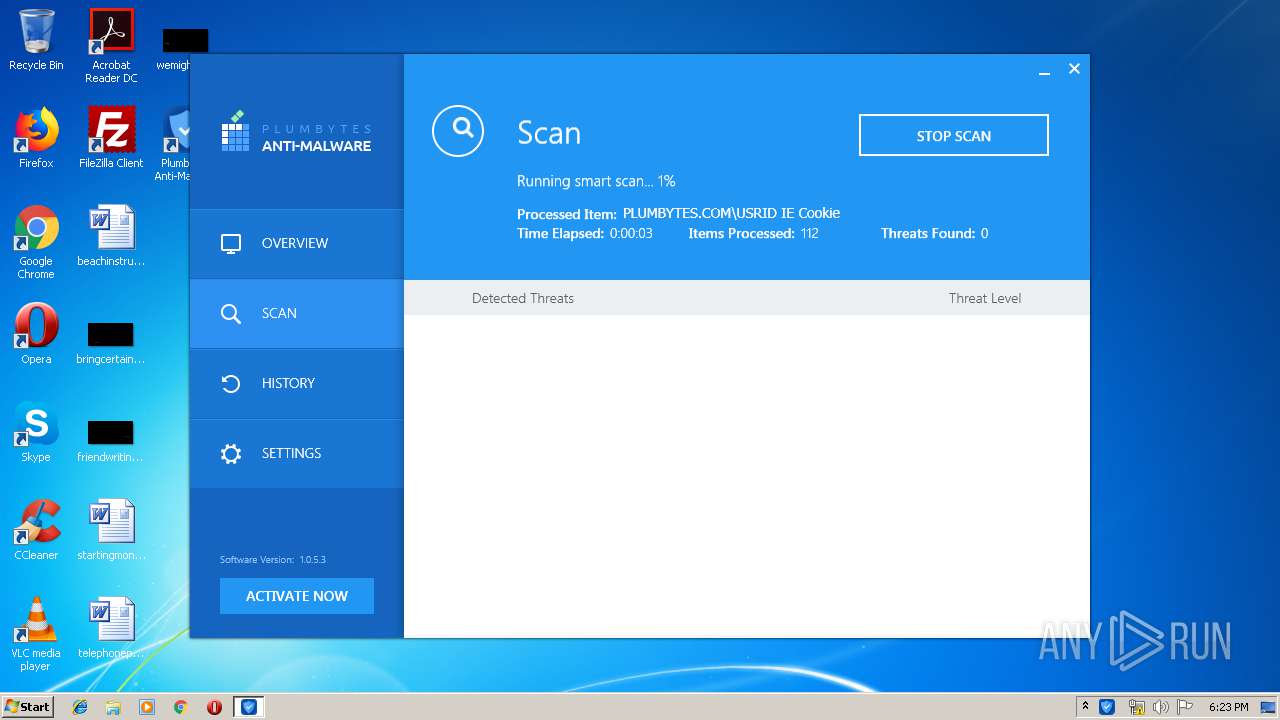
Reads the cookies of Google Chrome
- AmwService.exe (PID: 3404)
- AmwService.exe (PID: 3120)
- AmwService.exe (PID: 2572)
Removes files from Windows directory
- AmwService.exe (PID: 3120)
Reads the cookies of Mozilla Firefox
- AmwService.exe (PID: 3120)
Executed as Windows Service
- AmwService.exe (PID: 3120)
INFO
Creates files in the user directory
- iexplore.exe (PID: 3228)
Application launched itself
- iexplore.exe (PID: 2940)
Reads Internet Cache Settings
- iexplore.exe (PID: 3228)
- iexplore.exe (PID: 2940)
Changes internet zones settings
- iexplore.exe (PID: 2940)
Reads settings of System Certificates
- Plumbytes.exe (PID: 2712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
10
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2572 | "C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\AmwService.exe" getenv 2 | C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\AmwService.exe | — | AmwService.exe | |||||||||||
User: admin Company: Plumbytes Software Lp Integrity Level: MEDIUM Description: Anti-Malware Service Exit code: 0 Version: 0.9.0.648 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\Plumbytes.exe" | C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\Plumbytes.exe | pai364C.tmp | ||||||||||||
User: admin Company: Plumbytes Software Lp Integrity Level: HIGH Description: Plumbytes Anti-Malware Exit code: 0 Version: 1.0.5.3 Modules
| |||||||||||||||
| 2748 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\cuid[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\cuid[1].exe | iexplore.exe | ||||||||||||
User: admin Company: Plumbytes Software Lp Integrity Level: HIGH Description: Plumbytes Anti-Malware Exit code: 0 Version: 1.0.5.3 Modules
| |||||||||||||||
| 2940 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3120 | "C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\AmwService.exe" run | C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\AmwService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Plumbytes Software Lp Integrity Level: SYSTEM Description: Anti-Malware Service Exit code: 0 Version: 0.9.0.648 Modules
| |||||||||||||||
| 3228 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2940 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3404 | "C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\AmwService.exe" getenv 1 | C:\Program Files\Plumbytes Software\Plumbytes Anti-Malware\AmwService.exe | — | AmwService.exe | |||||||||||
User: admin Company: Plumbytes Software Lp Integrity Level: MEDIUM Description: Anti-Malware Service Exit code: 0 Version: 0.9.0.648 Modules
| |||||||||||||||
| 3572 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\wininet.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | cuid[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\cuid[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\cuid[1].exe | — | iexplore.exe | |||||||||||
User: admin Company: Plumbytes Software Lp Integrity Level: MEDIUM Description: Plumbytes Anti-Malware Exit code: 3221226540 Version: 1.0.5.3 Modules
| |||||||||||||||
| 3928 | /S | C:\Users\admin\AppData\Local\Temp\pai364C.tmp | cuid[1].exe | ||||||||||||
User: admin Company: Plumbytes Software Lp Integrity Level: HIGH Description: Plumbytes Anti-Malware Exit code: 0 Version: 1.0.5.3 Modules
| |||||||||||||||
Total events
1 317
Read events
1 155
Write events
159
Delete events
3
Modification events
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006E000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {805C922D-7E48-11E9-B3B3-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050005001800110016001C004701 | |||
Executable files
66
Suspicious files
1
Text files
14
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA1D1107E99BBB696.TMP | — | |
MD5:— | SHA256:— | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF2FDF2E4BAFDC413.TMP | — | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{805C922D-7E48-11E9-B3B3-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{805C922E-7E48-11E9-B3B3-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@plumbytes[1].txt | text | |
MD5:— | SHA256:— | |||
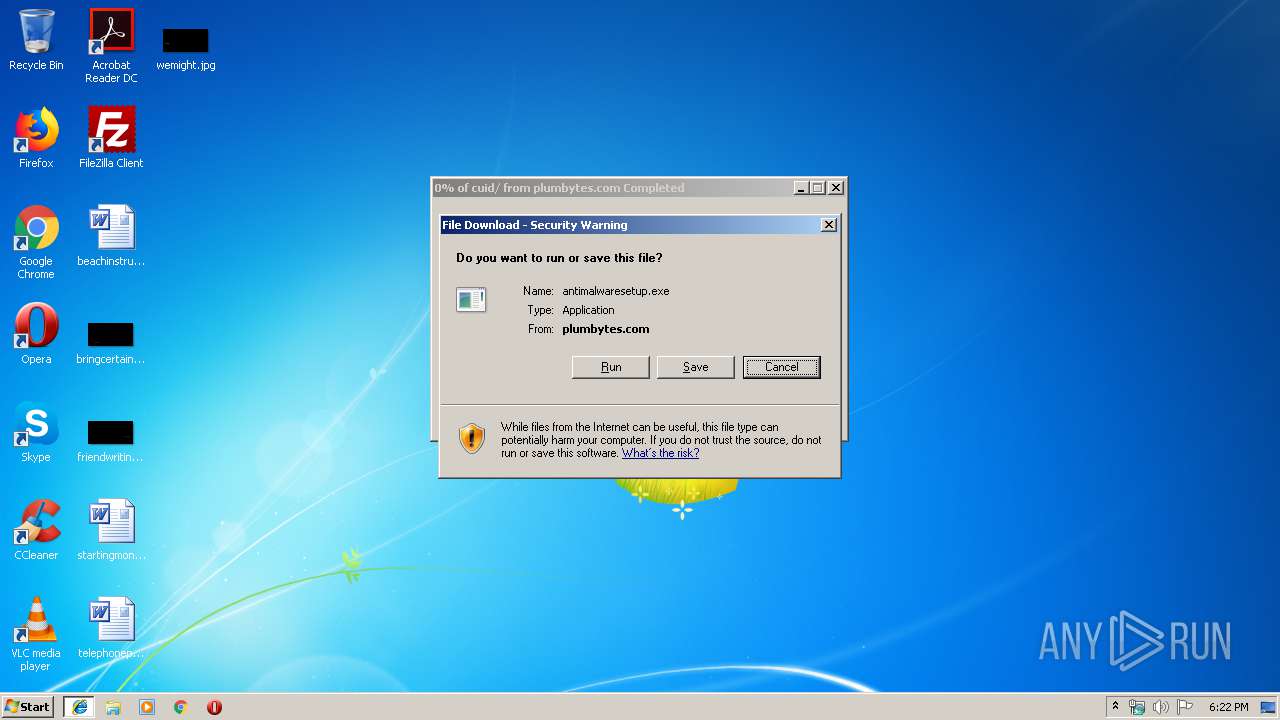
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\VPOIEHBO\antimalwaresetup[1].exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
13
DNS requests
5
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2748 | cuid[1].exe | GET | — | 45.55.29.117:80 | http://45.55.29.117/download/nsis/pb_nsissetup.exe | US | — | — | suspicious |
2748 | cuid[1].exe | GET | — | 45.55.29.117:80 | http://45.55.29.117/download/nsis/pb_nsissetup.exe | US | — | — | suspicious |
2748 | cuid[1].exe | GET | — | 45.55.29.117:80 | http://45.55.29.117/download/nsis/pb_nsissetup.exe | US | — | — | suspicious |
3228 | iexplore.exe | GET | 301 | 45.55.29.117:80 | http://www.plumbytes.com/download/cuid/?tid=rwid_p00000 | US | html | 260 b | suspicious |
3928 | pai364C.tmp | GET | 301 | 45.55.29.117:80 | http://plumbytes.com/logs.php?cuid=ver_ | US | html | 248 b | suspicious |
2712 | Plumbytes.exe | GET | 301 | 45.55.29.117:80 | http://www.plumbytes.com/settings/amw.xml | US | html | 246 b | suspicious |
2940 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3120 | AmwService.exe | 152.199.19.161:443 | plumbytes.azureedge.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3928 | pai364C.tmp | 45.55.29.117:443 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
2940 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3228 | iexplore.exe | 45.55.29.117:80 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
3228 | iexplore.exe | 45.55.29.117:443 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
2712 | Plumbytes.exe | 45.55.29.117:80 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
2712 | Plumbytes.exe | 104.40.92.107:443 | license.plumbytes.com | Microsoft Corporation | US | whitelisted |
2712 | Plumbytes.exe | 45.55.29.117:443 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
2748 | cuid[1].exe | 45.55.29.117:80 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
3928 | pai364C.tmp | 45.55.29.117:80 | www.plumbytes.com | Digital Ocean, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.plumbytes.com |
| suspicious |
plumbytes.com |
| suspicious |
plumbytes.azureedge.net |
| whitelisted |
license.plumbytes.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2748 | cuid[1].exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2748 | cuid[1].exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2748 | cuid[1].exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2748 | cuid[1].exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2748 | cuid[1].exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
3928 | pai364C.tmp | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
3928 | pai364C.tmp | Misc activity | SUSPICIOUS [PTsecurity] Suspicious HTTP header - Sometimes used by hostile installer |
2748 | cuid[1].exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2748 | cuid[1].exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
1 ETPRO signatures available at the full report