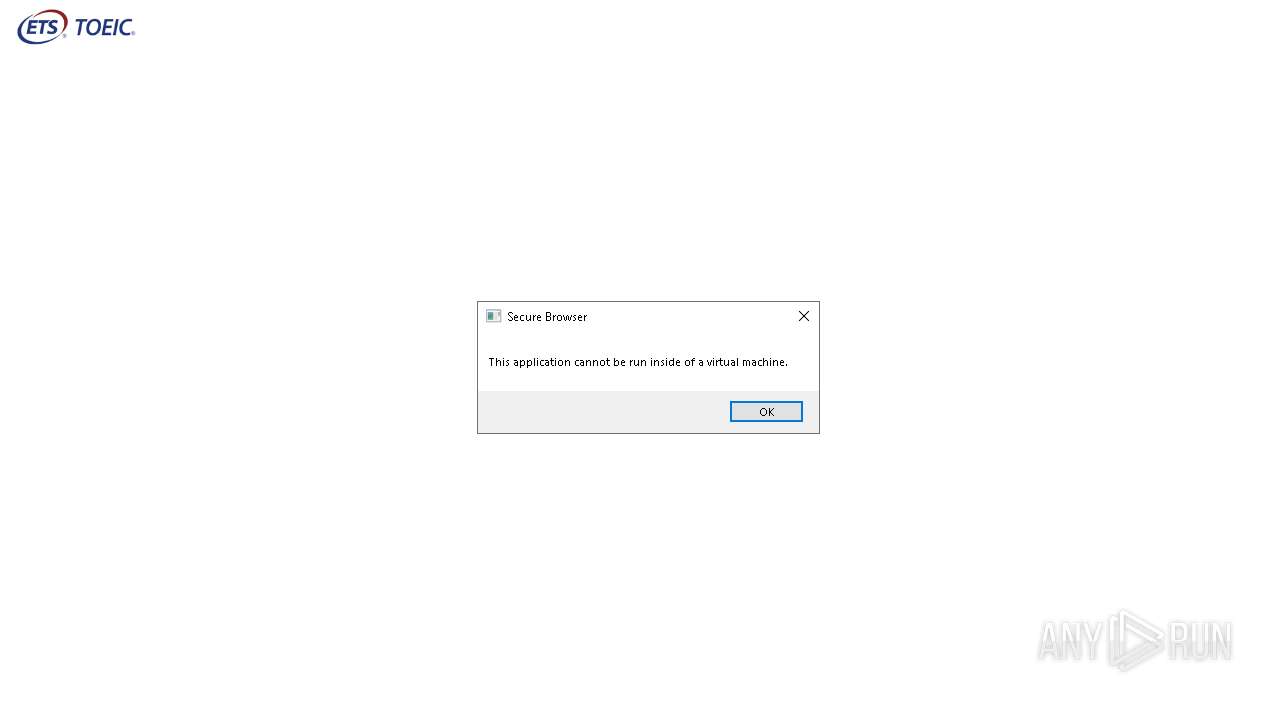
| File name: | TOEIC Secure Browser.exe |
| Full analysis: | https://app.any.run/tasks/ba0c633b-20a1-41c9-a089-287c25170f61 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2025, 01:45:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 2AF69D38E38E9021D7C77AEA9E7CF682 |
| SHA1: | 58B3E7137E3891BBD3DB0ABB0C53EAE20EE84C21 |
| SHA256: | 67EB089CFB6113C0072CA7426F24E99F3A838F8DEBD4D61D0FD09EC589B95DCA |
| SSDEEP: | 196608:nX5lVuDSpmUtKvlYeHlZZ/31Sw72sIfA59:nX5lS8PKhnN1SM2sEM9 |
MALICIOUS
The DLL Hijacking
- msedgewebview2.exe (PID: 5000)
Scans artifacts that could help determine the target
- msedgewebview2.exe (PID: 5400)
SUSPICIOUS
Reads the BIOS version
- TOEIC Secure Browser.exe (PID: 2216)
Executable content was dropped or overwritten
- TOEIC Secure Browser.exe (PID: 2216)
Reads security settings of Internet Explorer
- msedgewebview2.exe (PID: 5400)
- TOEIC Secure Browser.exe (PID: 2216)
Checks Windows Trust Settings
- TOEIC Secure Browser.exe (PID: 2216)
Application launched itself
- msedgewebview2.exe (PID: 5400)
INFO
Checks supported languages
- TOEIC Secure Browser.exe (PID: 2216)
- SignInfoConsole.exe (PID: 5588)
- SignInfoConsole.exe (PID: 4128)
- SignInfoConsole.exe (PID: 4944)
- msedgewebview2.exe (PID: 5000)
- msedgewebview2.exe (PID: 5576)
- msedgewebview2.exe (PID: 5572)
- msedgewebview2.exe (PID: 5400)
- msedgewebview2.exe (PID: 520)
- msedgewebview2.exe (PID: 6204)
- msedgewebview2.exe (PID: 7092)
- msedgewebview2.exe (PID: 6744)
- msedgewebview2.exe (PID: 6740)
Reads the computer name
- TOEIC Secure Browser.exe (PID: 2216)
- SignInfoConsole.exe (PID: 5588)
- SignInfoConsole.exe (PID: 4128)
- SignInfoConsole.exe (PID: 4944)
- msedgewebview2.exe (PID: 5400)
- msedgewebview2.exe (PID: 5576)
- msedgewebview2.exe (PID: 5000)
- msedgewebview2.exe (PID: 6204)
- msedgewebview2.exe (PID: 7092)
- msedgewebview2.exe (PID: 6740)
- msedgewebview2.exe (PID: 6744)
Reads the machine GUID from the registry
- TOEIC Secure Browser.exe (PID: 2216)
- SignInfoConsole.exe (PID: 5588)
- SignInfoConsole.exe (PID: 4128)
- SignInfoConsole.exe (PID: 4944)
- msedgewebview2.exe (PID: 5400)
Create files in a temporary directory
- TOEIC Secure Browser.exe (PID: 2216)
- msedgewebview2.exe (PID: 5400)
- msedgewebview2.exe (PID: 520)
- msedgewebview2.exe (PID: 5576)
Disables trace logs
- TOEIC Secure Browser.exe (PID: 2216)
Checks proxy server information
- TOEIC Secure Browser.exe (PID: 2216)
- msedgewebview2.exe (PID: 5400)
Reads the software policy settings
- TOEIC Secure Browser.exe (PID: 2216)
Reads Environment values
- TOEIC Secure Browser.exe (PID: 2216)
- msedgewebview2.exe (PID: 5400)
- msedgewebview2.exe (PID: 5000)
- msedgewebview2.exe (PID: 5576)
- msedgewebview2.exe (PID: 5572)
- msedgewebview2.exe (PID: 6204)
- msedgewebview2.exe (PID: 7092)
- msedgewebview2.exe (PID: 6744)
- msedgewebview2.exe (PID: 6740)
Reads product name
- TOEIC Secure Browser.exe (PID: 2216)
Process checks computer location settings
- TOEIC Secure Browser.exe (PID: 2216)
- msedgewebview2.exe (PID: 5400)
- msedgewebview2.exe (PID: 6204)
- msedgewebview2.exe (PID: 7092)
Creates files or folders in the user directory
- TOEIC Secure Browser.exe (PID: 2216)
- msedgewebview2.exe (PID: 5400)
Themida protector has been detected
- TOEIC Secure Browser.exe (PID: 2216)
Reads CPU info
- TOEIC Secure Browser.exe (PID: 2216)
Creates files in the program directory
- TOEIC Secure Browser.exe (PID: 2216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:07 10:08:26+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 2448384 |
| InitializedDataSize: | 337920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18b4058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 15.0.11.0 |
| ProductVersionNumber: | 15.0.11.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | ITS Secure Browser |
| FileVersion: | 15.0.11.0 |
| InternalName: | ITS Secure Browser.exe |
| LegalCopyright: | Copyright © 2016 |
| LegalTrademarks: | - |
| OriginalFileName: | ITS Secure Browser.exe |
| ProductName: | ITS Secure Browser |
| ProductVersion: | 15.0.11.0 |
| AssemblyVersion: | 15.0.11.0 |
Total processes
139
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView\Crashpad --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe" --annotation=plat=Win64 "--annotation=prod=Edge WebView2" --annotation=ver=122.0.2365.59 --initial-client-data=0x1a4,0x1a8,0x1ac,0x18c,0x1b4,0x7ff821c85fd8,0x7ff821c85fe4,0x7ff821c85ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SignInfoConsole.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | "C:\Users\admin\AppData\Local\Temp\TOEIC Secure Browser.exe" | C:\Users\admin\AppData\Local\Temp\TOEIC Secure Browser.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ITS Secure Browser Exit code: 0 Version: 15.0.11.0 Modules
| |||||||||||||||
| 3792 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SignInfoConsole.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "C:\Users\admin\AppData\Local\Temp\OSB\SignInfoConsole.exe" "C:\Users\admin\AppData\Local\Temp\TOEIC Secure Browser.exe" | C:\Users\admin\AppData\Local\Temp\OSB\SignInfoConsole.exe | — | TOEIC Secure Browser.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SignInfoConsole Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4944 | "C:\Users\admin\AppData\Local\Temp\OSB\SignInfoConsole.exe" "C:\Users\admin\AppData\Local\Temp\TOEIC Secure Browser.exe" | C:\Users\admin\AppData\Local\Temp\OSB\SignInfoConsole.exe | — | TOEIC Secure Browser.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SignInfoConsole Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5000 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe" --type=gpu-process --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView" --webview-exe-name="TOEIC Secure Browser.exe" --webview-exe-version=15.0.11.0 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=0 --edge-webview-custom-scheme --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2180 --field-trial-handle=2184,i,14794025526678201333,1285868589577891110,262144 --enable-features=MojoIpcz --disable-features=OverscrollHistoryNavigation,msExperimentalScrolling --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5400 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe" --embedded-browser-webview=1 --webview-exe-name="TOEIC Secure Browser.exe" --webview-exe-version=15.0.11.0 --user-data-dir="C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView" --noerrdialogs --embedded-browser-webview-dpi-awareness=0 --edge-webview-custom-scheme --autoplay-policy=no-user-gesture-required --disable-features=OverscrollHistoryNavigation,msExperimentalScrolling --enable-features=MojoIpcz --mojo-named-platform-channel-pipe=2216.5092.2623751158674741361 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe | TOEIC Secure Browser.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Exit code: 4294967295 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5572 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView" --webview-exe-name="TOEIC Secure Browser.exe" --webview-exe-version=15.0.11.0 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=0 --edge-webview-custom-scheme --no-appcompat-clear --mojo-platform-channel-handle=2548 --field-trial-handle=2184,i,14794025526678201333,1285868589577891110,262144 --enable-features=MojoIpcz --disable-features=OverscrollHistoryNavigation,msExperimentalScrolling --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5576 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView" --webview-exe-name="TOEIC Secure Browser.exe" --webview-exe-version=15.0.11.0 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=0 --edge-webview-custom-scheme --no-appcompat-clear --mojo-platform-channel-handle=2420 --field-trial-handle=2184,i,14794025526678201333,1285868589577891110,262144 --enable-features=MojoIpcz --disable-features=OverscrollHistoryNavigation,msExperimentalScrolling --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\msedgewebview2.exe | msedgewebview2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
6 007
Read events
5 973
Write events
34
Delete events
0
Modification events
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 2560 | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2216) TOEIC Secure Browser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\TOEIC Secure Browser_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
15
Suspicious files
171
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2216 | TOEIC Secure Browser.exe | C:\Users\admin\AppData\Local\Temp\OSB\SignInfoConsole.exe | executable | |
MD5:9C11A9BD1765AA8B89E9DE29D252A524 | SHA256:E7832BCF1BDDD4A296C52AF635AD831DF01ED596ADAADDEFD4A9B1B1343F2387 | |||
| 2216 | TOEIC Secure Browser.exe | C:\Users\admin\AppData\Local\Temp\7e70ecb.dll | executable | |
MD5:7AFBF68246B7D5E54B7BBE4659DA4925 | SHA256:2692CC47E8A4E6E4CB46C19739A337BB7443CFFE6DB4A84AF0B80277697C3288 | |||
| 2216 | TOEIC Secure Browser.exe | C:\Users\admin\AppData\Local\Temp\7e70ec9.dll | executable | |
MD5:D161D1106439AC4FF6A7A18B09EFF2E2 | SHA256:DBF8957B44B525B564DDA7485BBC9B4668C97ABCCDCA19478458CAF112003CFD | |||
| 5588 | SignInfoConsole.exe | C:\Users\admin\AppData\Local\Temp\Tmp8291.tmp | binary | |
MD5:0A304276976A12E76ABA0F4D88D8B99D | SHA256:A8A55EFB310119F7E7C0E4994C1455251ED7F863C7372AA19623F6CF3B622D86 | |||
| 4944 | SignInfoConsole.exe | C:\Users\admin\AppData\Local\Temp\Tmp8ACE.tmp | binary | |
MD5:0A304276976A12E76ABA0F4D88D8B99D | SHA256:A8A55EFB310119F7E7C0E4994C1455251ED7F863C7372AA19623F6CF3B622D86 | |||
| 2216 | TOEIC Secure Browser.exe | C:\Users\admin\AppData\Local\Temp\7e70eca.dll | executable | |
MD5:7AFBF68246B7D5E54B7BBE4659DA4925 | SHA256:2692CC47E8A4E6E4CB46C19739A337BB7443CFFE6DB4A84AF0B80277697C3288 | |||
| 5400 | msedgewebview2.exe | C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView\Local State | binary | |
MD5:6C97168FE2284DC0C2283800112A929C | SHA256:465FA7A649F616B27F1BB72E3C27688164393F485BE9212E9EDDC3F07DFE55C4 | |||
| 5400 | msedgewebview2.exe | C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView\ShaderCache\data_0 | binary | |
MD5:CF89D16BB9107C631DAABF0C0EE58EFB | SHA256:D6A5FE39CD672781B256E0E3102F7022635F1D4BB7CFCC90A80FFFE4D0F3877E | |||
| 5400 | msedgewebview2.exe | C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView\ShaderCache\data_3 | binary | |
MD5:41876349CB12D6DB992F1309F22DF3F0 | SHA256:E09F42C398D688DCE168570291F1F92D079987DEDA3099A34ADB9E8C0522B30C | |||
| 5400 | msedgewebview2.exe | C:\Users\admin\AppData\Local\Temp\.WebView2\EBWebView\ShaderCache\index | binary | |
MD5:D0299AAEE5CB488D586E2BCEAA217ED9 | SHA256:645B44ED5C75188DCEF153EEA858E194BE3B149DF1A1FDA5FBFF2B73E600E650 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
56
DNS requests
30
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
68 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2216 | TOEIC Secure Browser.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2216 | TOEIC Secure Browser.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
68 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2216 | TOEIC Secure Browser.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEEkNsD53GoJVFMAtazZydYk%3D | unknown | — | — | whitelisted |
6916 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
68 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
68 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2216 | TOEIC Secure Browser.exe | 161.47.163.213:443 | www.starttest.com | RACKSPACE | US | whitelisted |
5064 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.starttest.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2216 | TOEIC Secure Browser.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
2216 | TOEIC Secure Browser.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
5576 | msedgewebview2.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
5576 | msedgewebview2.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
5576 | msedgewebview2.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
5576 | msedgewebview2.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
5576 | msedgewebview2.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
5576 | msedgewebview2.exe | Misc activity | INFO [ANY.RUN] Pearson VUE Client SSL Cert |
Process | Message |
|---|---|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\.WebView2 directory exists )
|