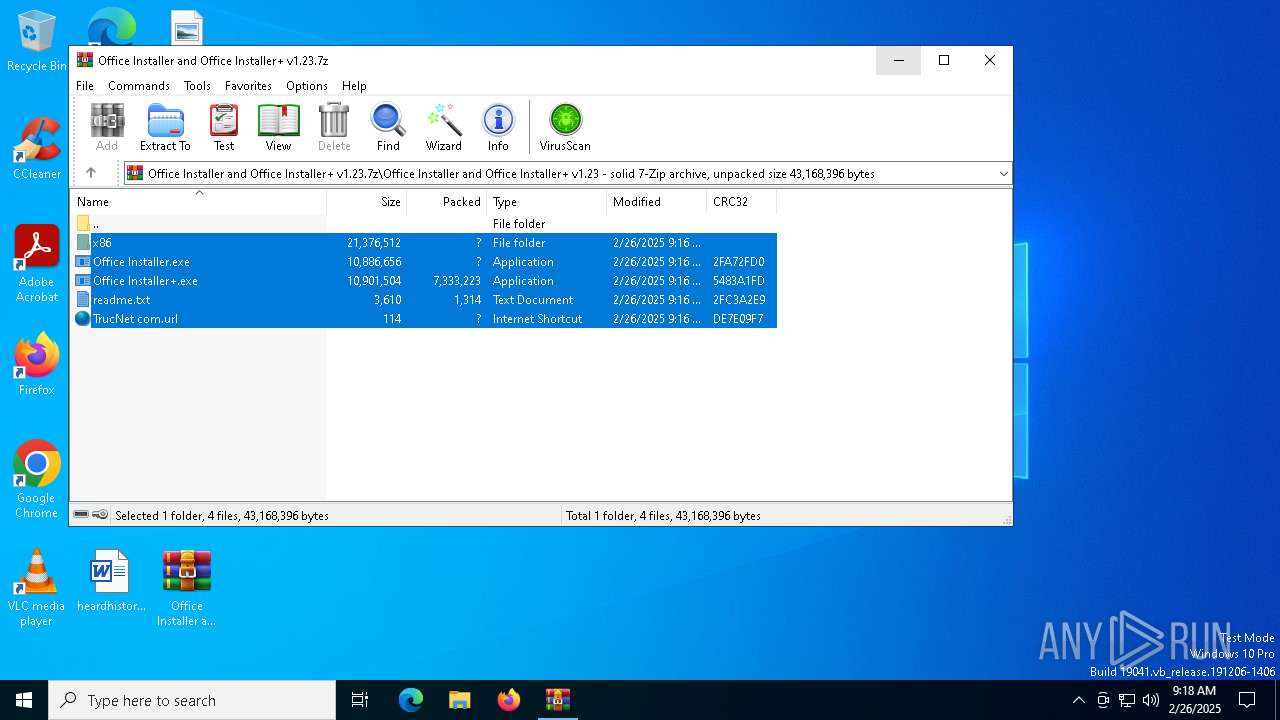
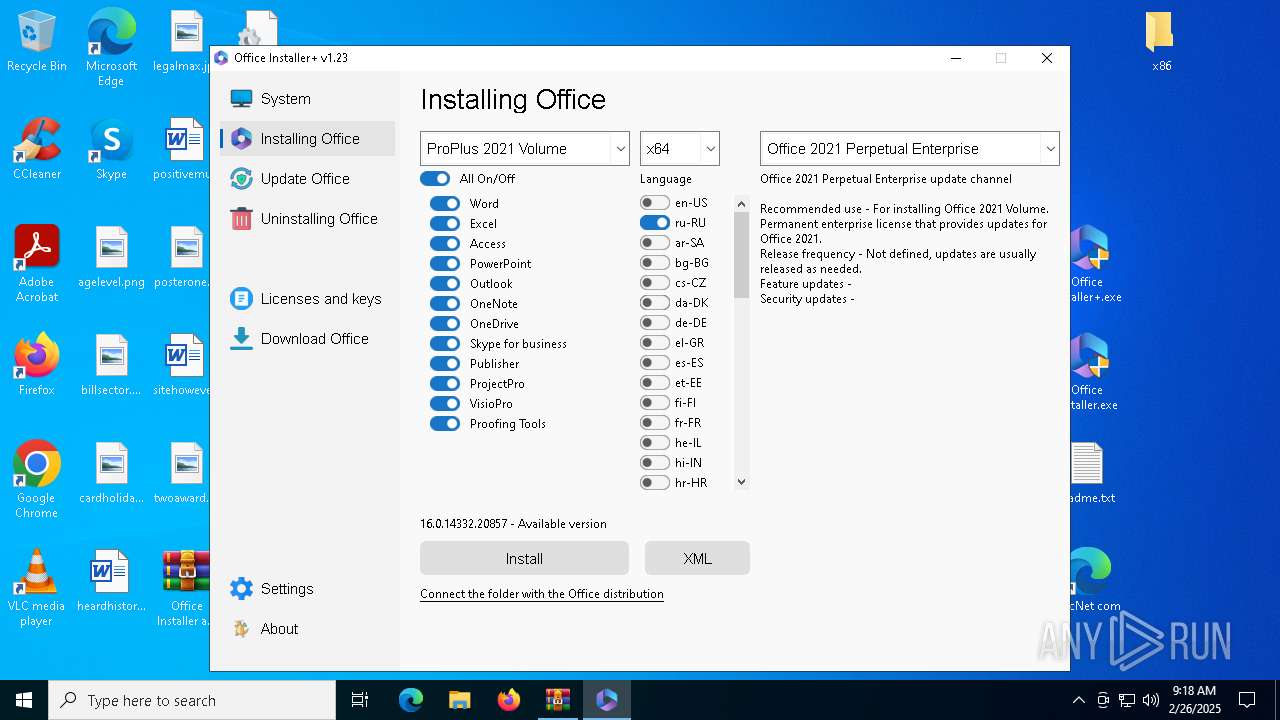
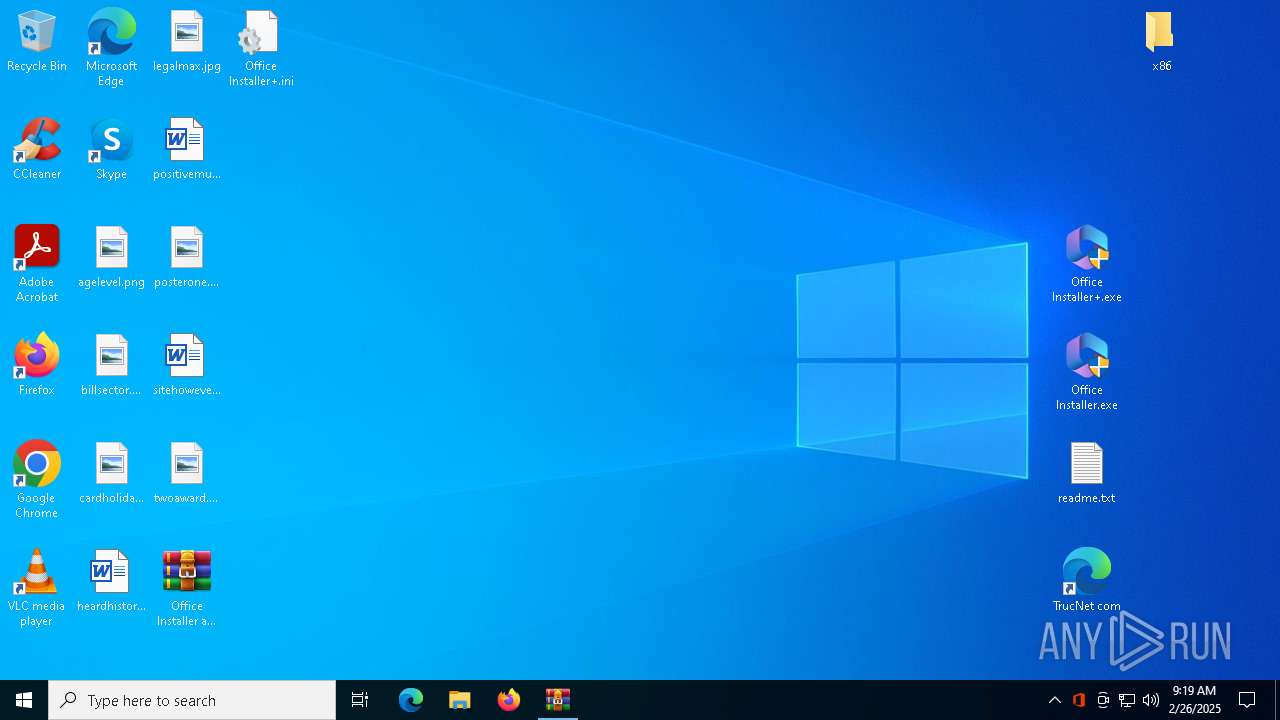
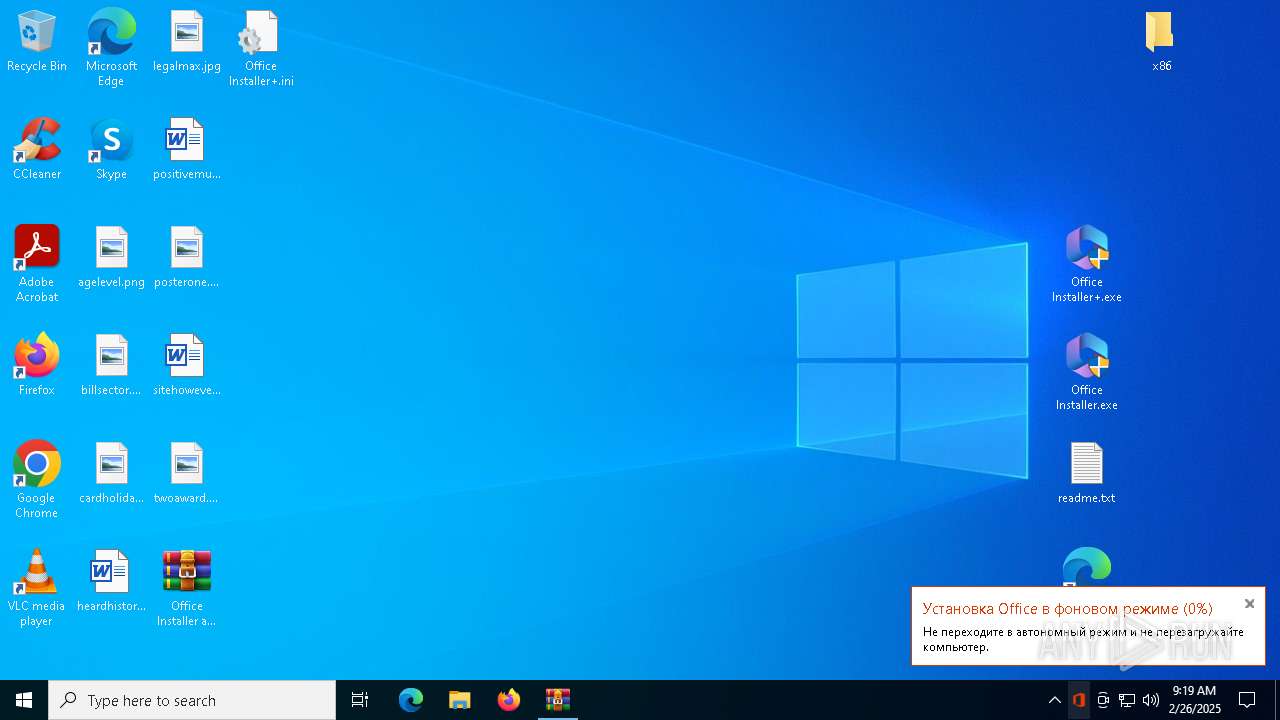
| File name: | Office Installer and Office Installer+ v1.23.7z |
| Full analysis: | https://app.any.run/tasks/6e43f6d8-32f9-4d98-a7f8-c29e7416bd45 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2025, 09:18:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B37A498F9394FA2EA2D5B1763F51359E |
| SHA1: | 1F4CEEDAD5AEB62A2CB08C8FAAD3B13F5DE750C5 |
| SHA256: | 67DCF604E1A41B1BBB7955C457B60804EDD0652C40B67B754A91B71E1BB0FDA5 |
| SSDEEP: | 98304:rv8oNVI4LtuY+kL9qfTDWE6MvUoMXDpdvSVyl06SHowjBFMsN/2kdK0vm0vmzghx:3sXdUAAfnj2VB |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2568)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 5204)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 208)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2568)
- Office Installer+.exe (PID: 7052)
Uses REG/REGEDIT.EXE to modify registry
- Office Installer+.exe (PID: 7052)
Starts POWERSHELL.EXE for commands execution
- Office Installer+.exe (PID: 7052)
The process bypasses the loading of PowerShell profile settings
- Office Installer+.exe (PID: 7052)
Probably download files using WebClient
- Office Installer+.exe (PID: 7052)
Starts CMD.EXE for commands execution
- Office Installer+.exe (PID: 7052)
Executes script without checking the security policy
- powershell.exe (PID: 5204)
Starts SC.EXE for service management
- cmd.exe (PID: 5640)
Stops a currently running service
- sc.exe (PID: 1244)
Unpacks CAB file
- expand.exe (PID: 5084)
- expand.exe (PID: 5932)
Uses TASKKILL.EXE to kill process
- Office Installer+.exe (PID: 7052)
Executable content was dropped or overwritten
- expand.exe (PID: 5084)
Process drops legitimate windows executable
- expand.exe (PID: 5084)
The process drops C-runtime libraries
- expand.exe (PID: 5084)
Reads the date of Windows installation
- Office Installer+.exe (PID: 7052)
INFO
Local mutex for internet shortcut management
- WinRAR.exe (PID: 2568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2568)
Manual execution by a user
- Office Installer+.exe (PID: 1628)
- Office Installer+.exe (PID: 7052)
Reads product name
- Office Installer+.exe (PID: 7052)
Reads the computer name
- Office Installer+.exe (PID: 7052)
- OfficeClickToRun.exe (PID: 6656)
- OfficeClickToRun.exe (PID: 5972)
Disables trace logs
- powershell.exe (PID: 5204)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 208)
Checks supported languages
- Office Installer+.exe (PID: 7052)
- expand.exe (PID: 5084)
- expand.exe (PID: 5932)
- OfficeClickToRun.exe (PID: 6656)
- OfficeClickToRun.exe (PID: 5972)
Checks proxy server information
- powershell.exe (PID: 5204)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 208)
- OfficeClickToRun.exe (PID: 6656)
- OfficeClickToRun.exe (PID: 5972)
Reads Environment values
- Office Installer+.exe (PID: 7052)
Creates files in the program directory
- Office Installer+.exe (PID: 7052)
- expand.exe (PID: 5084)
- expand.exe (PID: 5932)
- OfficeClickToRun.exe (PID: 5972)
Reads the machine GUID from the registry
- expand.exe (PID: 5084)
- expand.exe (PID: 5932)
- OfficeClickToRun.exe (PID: 5972)
The sample compiled with czech language support
- expand.exe (PID: 5084)
UPX packer has been detected
- Office Installer+.exe (PID: 7052)
The sample compiled with arabic language support
- expand.exe (PID: 5084)
The sample compiled with german language support
- expand.exe (PID: 5084)
The sample compiled with english language support
- expand.exe (PID: 5084)
The sample compiled with spanish language support
- expand.exe (PID: 5084)
The sample compiled with bulgarian language support
- expand.exe (PID: 5084)
The sample compiled with french language support
- expand.exe (PID: 5084)
The sample compiled with Italian language support
- expand.exe (PID: 5084)
The sample compiled with japanese language support
- expand.exe (PID: 5084)
The sample compiled with portuguese language support
- expand.exe (PID: 5084)
The sample compiled with slovak language support
- expand.exe (PID: 5084)
The sample compiled with russian language support
- expand.exe (PID: 5084)
The sample compiled with Indonesian language support
- expand.exe (PID: 5084)
The sample compiled with swedish language support
- expand.exe (PID: 5084)
The sample compiled with chinese language support
- expand.exe (PID: 5084)
The sample compiled with korean language support
- expand.exe (PID: 5084)
The sample compiled with polish language support
- expand.exe (PID: 5084)
The sample compiled with turkish language support
- expand.exe (PID: 5084)
Create files in a temporary directory
- OfficeClickToRun.exe (PID: 6656)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 5972)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 5972)
- slui.exe (PID: 1132)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 5972)
- OfficeClickToRun.exe (PID: 6656)
Creates files or folders in the user directory
- OfficeClickToRun.exe (PID: 6656)
Process checks computer location settings
- Office Installer+.exe (PID: 7052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:02:26 09:16:30+00:00 |
| ArchivedFileName: | Office Installer and Office Installer+ v1.23 |
Total processes
158
Monitored processes
30
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/i641049.cab', 'C:\Users\admin\AppData\Local\Temp\i641049.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | Office Installer+.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "taskkill.exe" /t /f /IM OfficeC2RClient.exe | C:\Windows\System32\taskkill.exe | — | Office Installer+.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | sc.exe stop ClickToRunSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\Desktop\Office Installer+.exe" | C:\Users\admin\Desktop\Office Installer+.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.23.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 644
Read events
30 474
Write events
66
Delete events
104
Modification events
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.23.7z | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6324) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6656) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
Executable files
227
Suspicious files
49
Text files
51
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5416 | powershell.exe | C:\Users\admin\AppData\Local\Temp\i640.cab | — | |
MD5:— | SHA256:— | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.31580\Office Installer and Office Installer+ v1.23\Office Installer.exe | executable | |
MD5:D175656E95669DE2557C8FF233B1B22E | SHA256:EF02BBC8A594BC9A203962455E3AA6ED396F99F08A3137FF04590873C9FCE37B | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.31580\Office Installer and Office Installer+ v1.23\x86\Office Installer x86.exe | executable | |
MD5:3F02DD1C5D6329B7187BD7FC6C00650A | SHA256:559A26CD984B671BAC7D004413067C7F1C419BE63B0148615AE979A44C855C6E | |||
| 5416 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f5a5z2ww.pzg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5084 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:19DF2B0F78DC3D8C470E836BAE85E1FF | SHA256:BD9E07BBC62CE82DBC30C23069A17FBFA17F1C26A9C19E50FE754D494E6CD0B1 | |||
| 5204 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:ADA4F19220FBDDA30E618779093D6897 | SHA256:A631DE56D329A256D8BA80B5E1159A56D8AADF1D1FA602F0A6983B1465C4391D | |||
| 7052 | Office Installer+.exe | C:\Users\admin\Desktop\Office Installer+.ini | text | |
MD5:B90C44F46D9B2EC51569FAEB1D4D6E59 | SHA256:0E9A740B0A4318193F144080001DE18EB7CC66843490D4F001CC6AC24F49340A | |||
| 5204 | powershell.exe | C:\Users\admin\AppData\Local\Temp\files\ver.txt | text | |
MD5:EEBC76213CCE2BBDBB1DBDAB9476870A | SHA256:2EF0FDFEF22AA979D41A076361241ED423B960B29BE3BC04795F751A6DA095F4 | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.31580\Office Installer and Office Installer+ v1.23\TrucNet com.url | binary | |
MD5:83C366FC52C23CDD84730CFBA47B1B2A | SHA256:692AB43C0C2CE3572DABD608FD634125C9CF3D8EE75417D9779D942BE3707D9C | |||
| 5204 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kjf0prae.bxw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
54
DNS requests
37
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3768 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5416 | powershell.exe | GET | 200 | 199.232.210.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/i640.cab | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/s641036.cab | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/s641036.cab | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
208 | powershell.exe | GET | 200 | 199.232.210.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/i641049.cab | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/s640.cab | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/s640.cab.phf | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/s640.cab | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20857/s640.cab | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3008 | backgroundTaskHost.exe | 184.86.251.4:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2040 | backgroundTaskHost.exe | 20.31.169.57:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5204 | powershell.exe | 52.109.89.117:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5416 | powershell.exe | 199.232.210.172:80 | officecdn.microsoft.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |