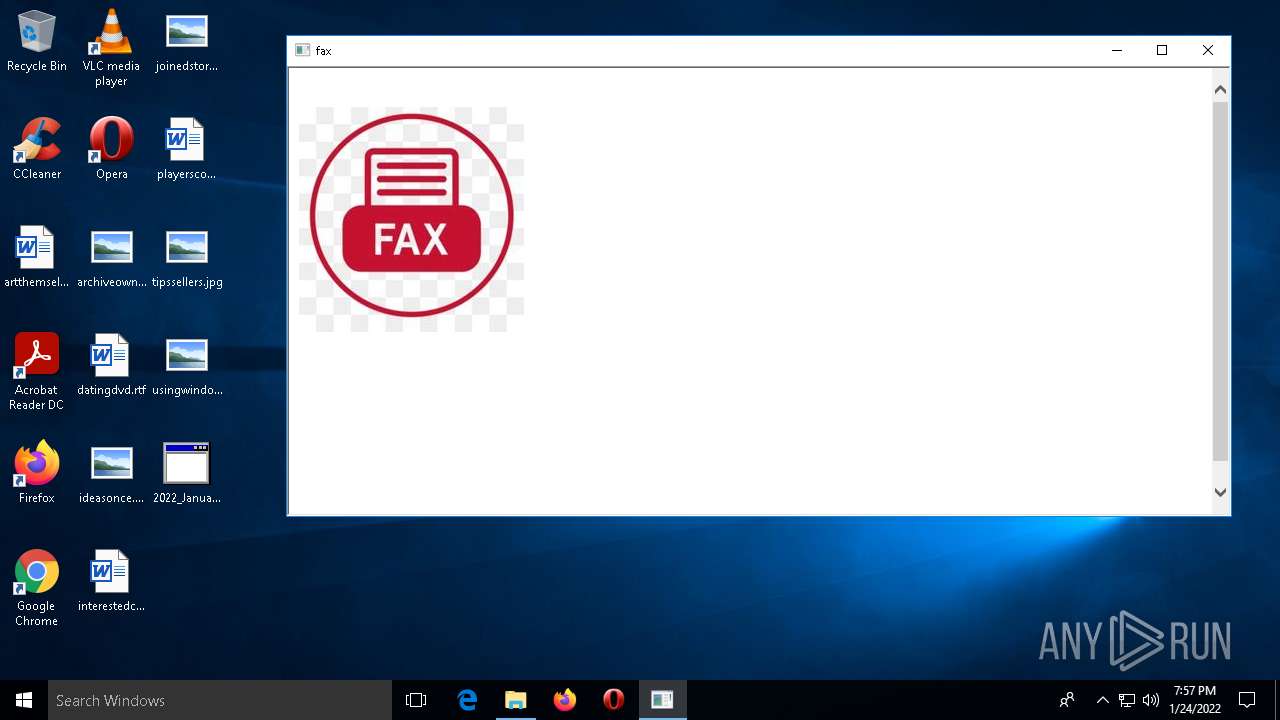
| File name: | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\2022_January_Document_Review[1].hta |
| Full analysis: | https://app.any.run/tasks/5d77cec2-6ab6-4472-8636-b9b54e318cc6 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 19:51:30 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 332C32BA5EE435ED5133F3AF2540B5C2 |
| SHA1: | 59D627690FE8855BECEDD0958A7965979DD2D7B7 |
| SHA256: | 67C9F27FC0F57A92D636D238FAC04DBF335BB0527985F2747E5CF4FBF7AE6E56 |
| SSDEEP: | 1536:506LsUcQhSYsKWDpFizzXuFwDVbrewnRn35xGVKsB2Aw:W6gUcQYtK1/VbqARneXB8 |
MALICIOUS
Scans artifacts that could help determine the target
- iexplore.exe (PID: 5064)
SUSPICIOUS
Reads Microsoft Outlook installation path
- IEXPLORE.EXE (PID: 3124)
- IEXPLORE.EXE (PID: 1756)
- mshta.exe (PID: 4268)
- mshta.exe (PID: 3824)
Reads the computer name
- mshta.exe (PID: 4268)
- mshta.exe (PID: 3824)
- notepad++.exe (PID: 2580)
Executed via COM
- OpenWith.exe (PID: 3592)
- DllHost.exe (PID: 204)
Checks supported languages
- mshta.exe (PID: 3824)
- mshta.exe (PID: 4268)
- notepad++.exe (PID: 2580)
Reads the date of Windows installation
- OpenWith.exe (PID: 3592)
Creates files in the user directory
- notepad++.exe (PID: 2580)
INFO
Reads the computer name
- iexplore.exe (PID: 5064)
- IEXPLORE.EXE (PID: 3124)
- IEXPLORE.EXE (PID: 1756)
- IEXPLORE.EXE (PID: 2192)
- OpenWith.exe (PID: 3592)
- DllHost.exe (PID: 204)
Checks supported languages
- iexplore.exe (PID: 5064)
- IEXPLORE.EXE (PID: 3124)
- IEXPLORE.EXE (PID: 1756)
- IEXPLORE.EXE (PID: 2192)
- OpenWith.exe (PID: 3592)
Changes internet zones settings
- iexplore.exe (PID: 5064)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 3124)
- IEXPLORE.EXE (PID: 1756)
- mshta.exe (PID: 4268)
- mshta.exe (PID: 3824)
Application launched itself
- IEXPLORE.EXE (PID: 3124)
Reads the software policy settings
- IEXPLORE.EXE (PID: 1756)
- iexplore.exe (PID: 5064)
- IEXPLORE.EXE (PID: 3124)
Reads settings of System Certificates
- IEXPLORE.EXE (PID: 1756)
- iexplore.exe (PID: 5064)
- IEXPLORE.EXE (PID: 3124)
Checks Windows Trust Settings
- IEXPLORE.EXE (PID: 1756)
- iexplore.exe (PID: 5064)
- IEXPLORE.EXE (PID: 3124)
Reads the date of Windows installation
- iexplore.exe (PID: 5064)
Creates files in the user directory
- iexplore.exe (PID: 5064)
Manual execution by user
- mshta.exe (PID: 4268)
- mshta.exe (PID: 3824)
- notepad++.exe (PID: 2580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Title: | fax |
|---|
Total processes
100
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | C:\WINDOWS\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\WINDOWS\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1756 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:5064 CREDAT:333058 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | IEXPLORE.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:5064 CREDAT:529666 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | — | IEXPLORE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\2022_January_Document_Review[1].hta" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3124 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:5064 CREDAT:17410 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3592 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\WINDOWS\system32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3824 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\2022_January_Document_Review[1].hta" | C:\Windows\SysWOW64\mshta.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\2022_January_Document_Review[1].hta" | C:\Windows\SysWOW64\mshta.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\Desktop\2022_January_Document_Review[1].hta.html" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 242
Read events
13 057
Write events
183
Delete events
2
Modification events
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 956341420 | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 148313293 | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937435 | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
13
Text files
17
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\5X1K3HNA\edge[1].htm | html | |
MD5:— | SHA256:— | |||
| 5064 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{0814CA56-7D4F-11EC-B4A3-18F7786F96EE}.dat | binary | |
MD5:— | SHA256:— | |||
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\1IGIBTY7\oneplayer[1].js | text | |
MD5:— | SHA256:— | |||
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\20C2I1GY\www.microsoft[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\173WC5EV\ef-a24652[1].css | text | |
MD5:172F1794263EA1FC4BCFCE2A3CBA8F8E | SHA256:58D444A20D0AC6F199EFCA28A8C232D7714651BF3A27E9A02C9EF5364AA20250 | |||
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\KGQ0UDUE\css[1].css | text | |
MD5:— | SHA256:— | |||
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\5X1K3HNA\launch-EN7b3d710ac67a4a1195648458258f97dd.min[1].js | text | |
MD5:— | SHA256:— | |||
| 5064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6D7419CF1B963353.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1756 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\SmartScreenCache.dat | binary | |
MD5:— | SHA256:— | |||
| 5064 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\UrlBlock\URLD358.tmp | flc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
49
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1756 | IEXPLORE.EXE | GET | 301 | 2.18.233.62:443 | https://www.microsoft.com/en-us/welcomeie11/ | unknown | — | — | whitelisted |
1756 | IEXPLORE.EXE | GET | 302 | 104.111.242.51:443 | https://go.microsoft.com/fwlink/?LinkId=517287 | NL | — | — | whitelisted |
1756 | IEXPLORE.EXE | GET | 301 | 2.18.233.62:443 | https://www.microsoft.com/en-us/edge/?form=MA13DL&OCID=MA13DL | unknown | — | — | whitelisted |
1756 | IEXPLORE.EXE | GET | 302 | 104.111.242.51:80 | http://go.microsoft.com/fwlink/?LinkId=838604 | NL | — | — | whitelisted |
1756 | IEXPLORE.EXE | GET | 301 | 2.18.233.62:443 | https://www.microsoft.com/edge/?form=MA13DL&OCID=MA13DL | unknown | — | — | whitelisted |
1756 | IEXPLORE.EXE | GET | 200 | 2.18.233.62:443 | https://www.microsoft.com/en-us/edge?form=MA13DL&OCID=MA13DL | unknown | html | 215 Kb | whitelisted |
1756 | IEXPLORE.EXE | GET | 200 | 2.16.186.18:443 | https://mwf-service.akamaized.net/mwf/js/bundle/1.57.0/mwf-auto-init-main.var.min.js | unknown | html | 361 Kb | whitelisted |
1756 | IEXPLORE.EXE | GET | 200 | 2.16.186.40:443 | https://img-prod-cms-rt-microsoft-com.akamaized.net/cms/api/am/imageFileData/RWMIHM | unknown | image | 27.9 Kb | whitelisted |
1756 | IEXPLORE.EXE | GET | 200 | 72.247.225.88:443 | https://assets.adobedtm.com/launch-EN7b3d710ac67a4a1195648458258f97dd.min.js | US | text | 599 Kb | whitelisted |
1756 | IEXPLORE.EXE | GET | 200 | 2.16.186.40:443 | https://img-prod-cms-rt-microsoft-com.akamaized.net/cms/api/am/imageFileData/RWQN5w | unknown | image | 42.8 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1756 | IEXPLORE.EXE | 104.111.242.51:80 | go.microsoft.com | Akamai International B.V. | NL | unknown |
1756 | IEXPLORE.EXE | 104.111.242.51:443 | go.microsoft.com | Akamai International B.V. | NL | unknown |
1756 | IEXPLORE.EXE | 2.18.233.62:443 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
1756 | IEXPLORE.EXE | 151.101.65.26:443 | polyfill.io | Fastly | US | suspicious |
1756 | IEXPLORE.EXE | 152.199.19.160:443 | ajax.aspnetcdn.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1756 | IEXPLORE.EXE | 72.247.225.88:443 | assets.adobedtm.com | Akamai Technologies, Inc. | US | whitelisted |
1756 | IEXPLORE.EXE | 2.16.186.41:443 | statics-marketingsites-neu-ms-com.akamaized.net | Akamai International B.V. | — | whitelisted |
1756 | IEXPLORE.EXE | 2.16.186.18:443 | mwf-service.akamaized.net | Akamai International B.V. | — | whitelisted |
1756 | IEXPLORE.EXE | 2.16.186.40:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | — | whitelisted |
1756 | IEXPLORE.EXE | 13.107.246.45:443 | wcpstatic.microsoft.com | Microsoft Corporation | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
assets.adobedtm.com |
| whitelisted |
polyfill.io |
| whitelisted |
ajax.aspnetcdn.com |
| whitelisted |
statics-marketingsites-neu-ms-com.akamaized.net |
| whitelisted |
mwf-service.akamaized.net |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
c.s-microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1756 | IEXPLORE.EXE | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|