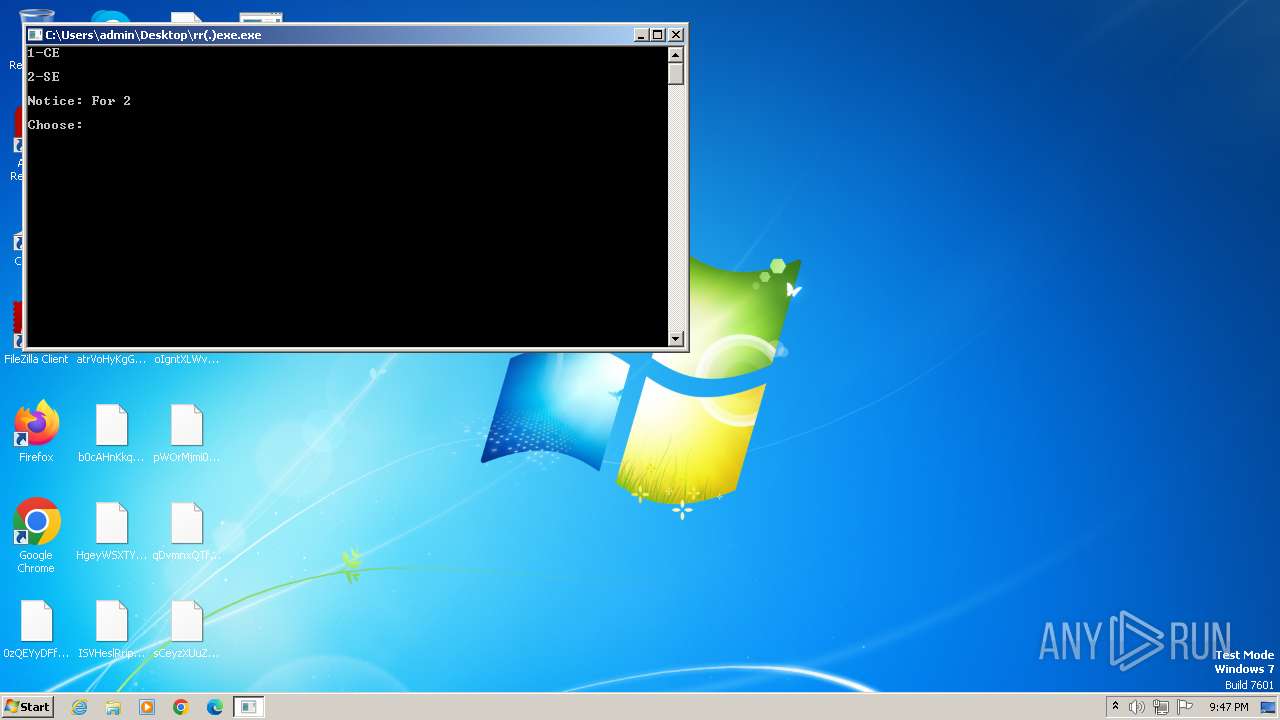
| File name: | rr(.)exe |
| Full analysis: | https://app.any.run/tasks/b6eab6d4-0017-43df-a414-66fed85b1c32 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 21:46:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 64D333DC747D7001925E1CB1BEBE5E80 |
| SHA1: | 19AC273B294879AC913CF48A1EBB0E170655401A |
| SHA256: | 67C053B22CDC61D65F806B8A29C4D44F48D05E7800F52B7D6529BE67310FEA1D |
| SSDEEP: | 24576:0gEeFTIov2XmrLyLlIXZFZ/SNKqzptMqKAU:0gEeFTI8drLyLlIXZFNSNKqzptMqKAU |
MALICIOUS
Drops the executable file immediately after the start
- rr(.)exe.exe (PID: 3112)
- rr(.)exe.exe (PID: 3852)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- rr(.)exe.exe (PID: 3852)
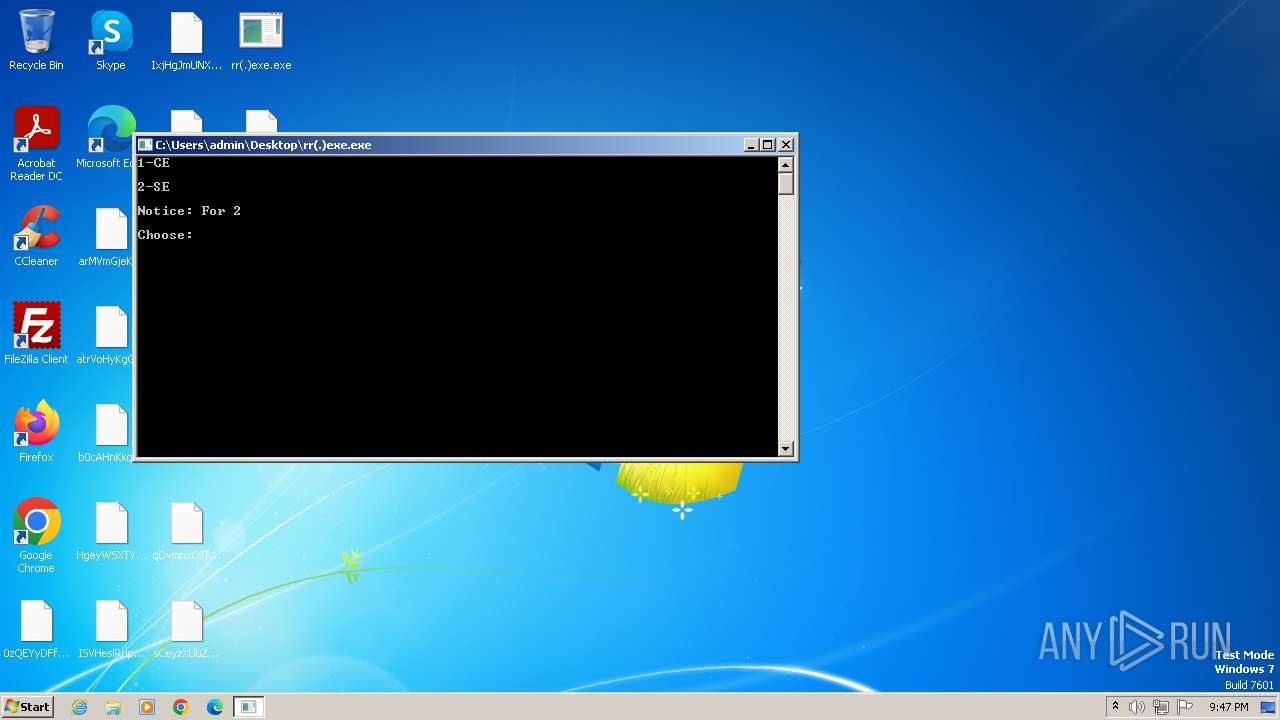
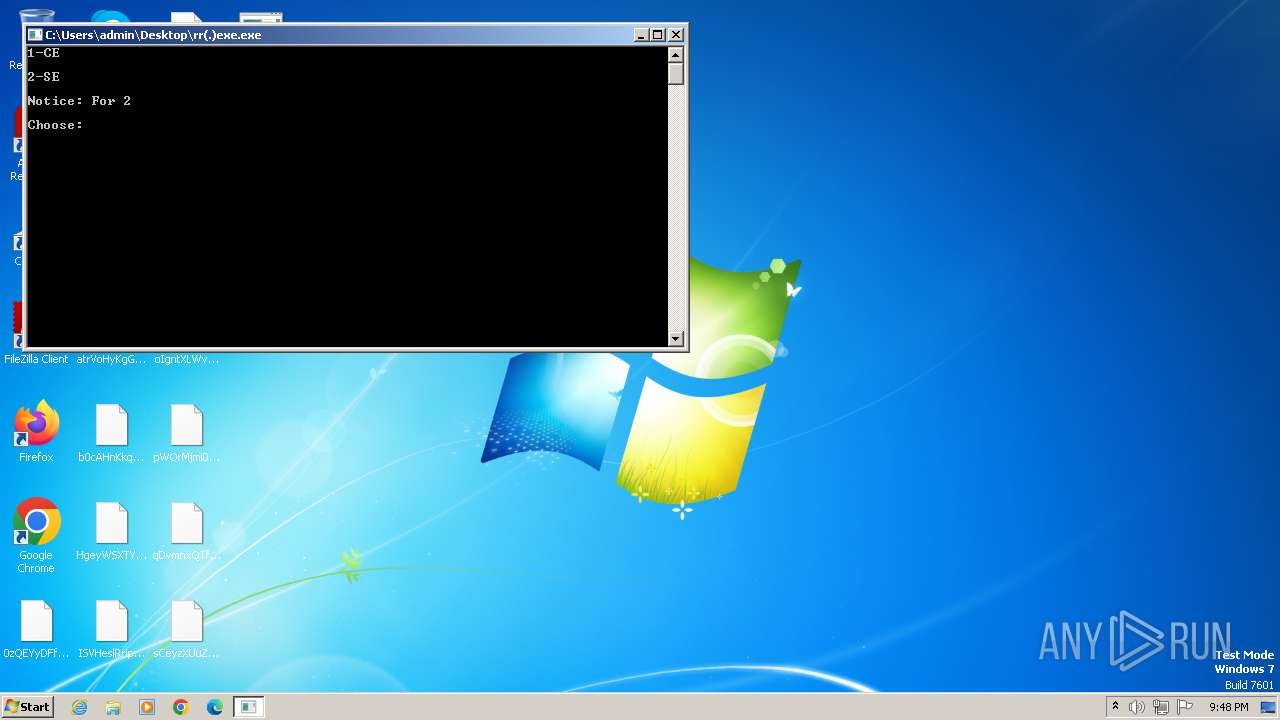
Starts CMD.EXE for commands execution
- rr(.)exe.exe (PID: 3980)
- rr(.)exe.exe (PID: 2064)
- rr(.)exe.exe (PID: 1488)
INFO
Checks supported languages
- rr(.)exe.exe (PID: 3852)
Reads the machine GUID from the registry
- rr(.)exe.exe (PID: 3852)
Manual execution by a user
- rr(.)exe.exe (PID: 3980)
- rr(.)exe.exe (PID: 2064)
- rr(.)exe.exe (PID: 3112)
- rr(.)exe.exe (PID: 1488)
- notepad++.exe (PID: 3432)
Creates files or folders in the user directory
- rr(.)exe.exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:26 12:08:27+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 700416 |
| InitializedDataSize: | 255488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x62b83 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Total processes
54
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1484 | C:\Windows\system32\cmd.exe /c pause | C:\Windows\System32\cmd.exe | — | rr(.)exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 1488 | "C:\Users\admin\Desktop\rr(.)exe.exe" | C:\Users\admin\Desktop\rr(.)exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\rr(.)exe.exe" | C:\Users\admin\Desktop\rr(.)exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 3112 | "C:\Users\admin\Desktop\rr(.)exe.exe" | C:\Users\admin\Desktop\rr(.)exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 3200 | C:\Windows\system32\cmd.exe /c pause | C:\Windows\System32\cmd.exe | — | rr(.)exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 3432 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\rr(.)exe.exe" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 | |||||||||||||||
| 3852 | "C:\Users\admin\Desktop\rr(.)exe.exe" | C:\Users\admin\Desktop\rr(.)exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\Desktop\rr(.)exe.exe" | C:\Users\admin\Desktop\rr(.)exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 4036 | C:\Windows\system32\cmd.exe /c pause | C:\Windows\System32\cmd.exe | — | rr(.)exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
Total events
14 462
Read events
14 462
Write events
0
Delete events
0
Modification events
Executable files
27
Suspicious files
4 032
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccLR.cab | — | |
MD5:— | SHA256:— | |||
| 3852 | rr(.)exe.exe | C:\KeyForFiles\Key.secret | binary | |
MD5:62B847506D79015190A734EC45834C35 | SHA256:934A6FFC6BE2EE19A19E64A8D2850061F6DA14C8B2A2C5D08B75217D88073002 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\eRnLXWjwrmbJkaT-Mail[tylerdecsec@gmail.com]ID-[82643855711973].VJDX0 | — | |
MD5:— | SHA256:— | |||
| 3852 | rr(.)exe.exe | C:\KeyForFiles\DecryptionKey.txt | text | |
MD5:13D1381749CC1AA0525ADD723AC35880 | SHA256:90ABA25C771049E3D004B084F9086E1E5D00A48B248591A7581CE708B0092A03 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\yOftuxhPKWwcdgN-Mail[tylerdecsec@gmail.com]ID-[82643855711973].TYCDJ | binary | |
MD5:A17BE53D2BE0206EC9AE401566DEF62F | SHA256:EF1511E6A1ACD325476F8CA77BE230CCD0C54744462F51512A9B695B6AE31487 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\branding.xml | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.msi | binary | |
MD5:A17BE53D2BE0206EC9AE401566DEF62F | SHA256:EF1511E6A1ACD325476F8CA77BE230CCD0C54744462F51512A9B695B6AE31487 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.xml | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\zCFhidqnPjTucNw-Mail[tylerdecsec@gmail.com]ID-[82643855711973].BYOVI | binary | |
MD5:2B1C017A83AE2BCF6690EFB60F61931D | SHA256:2A7B2FE3682F5B674BB3F64EBC38B042A76CCA893309045F05E3FFD77E74C301 | |||
| 3852 | rr(.)exe.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\Setup.xml | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |