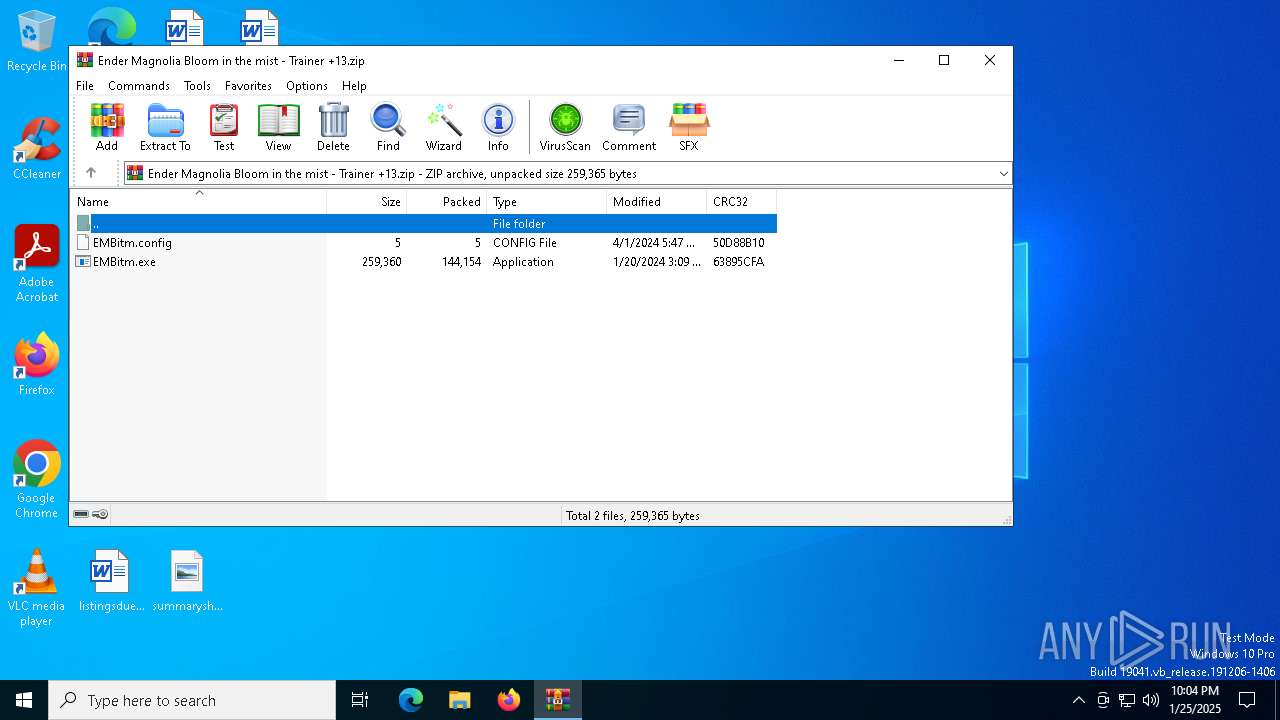
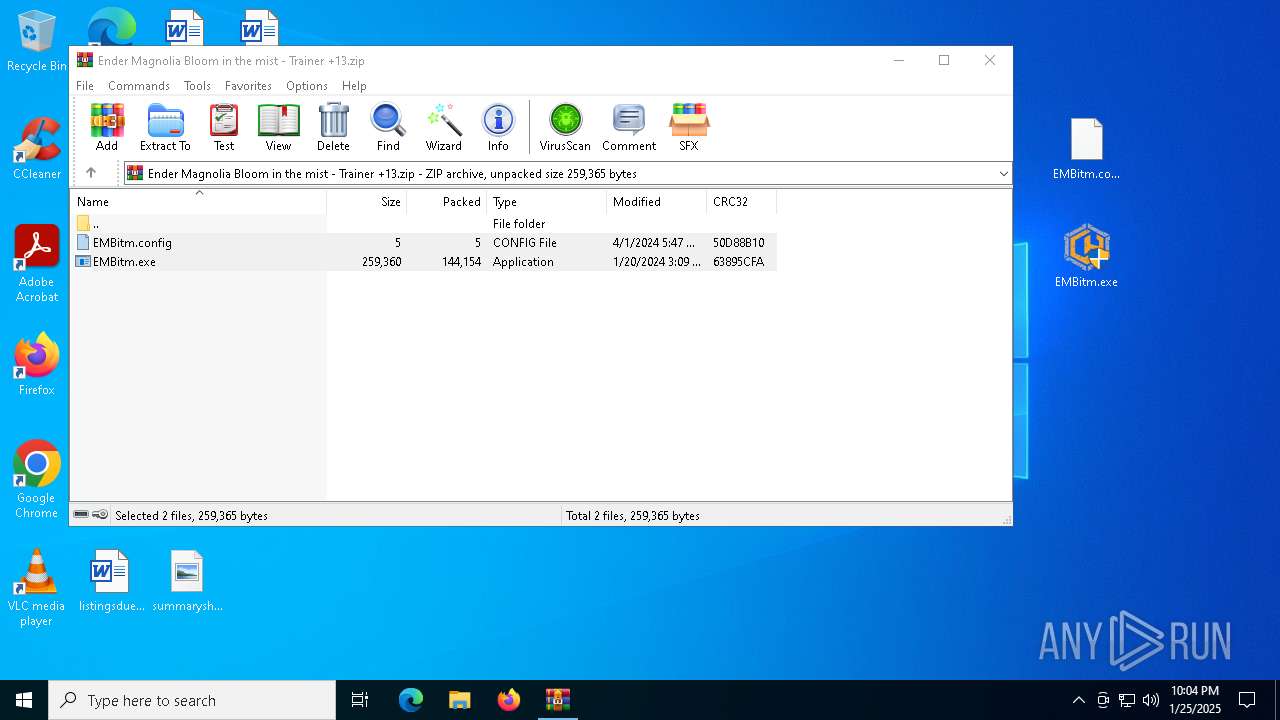
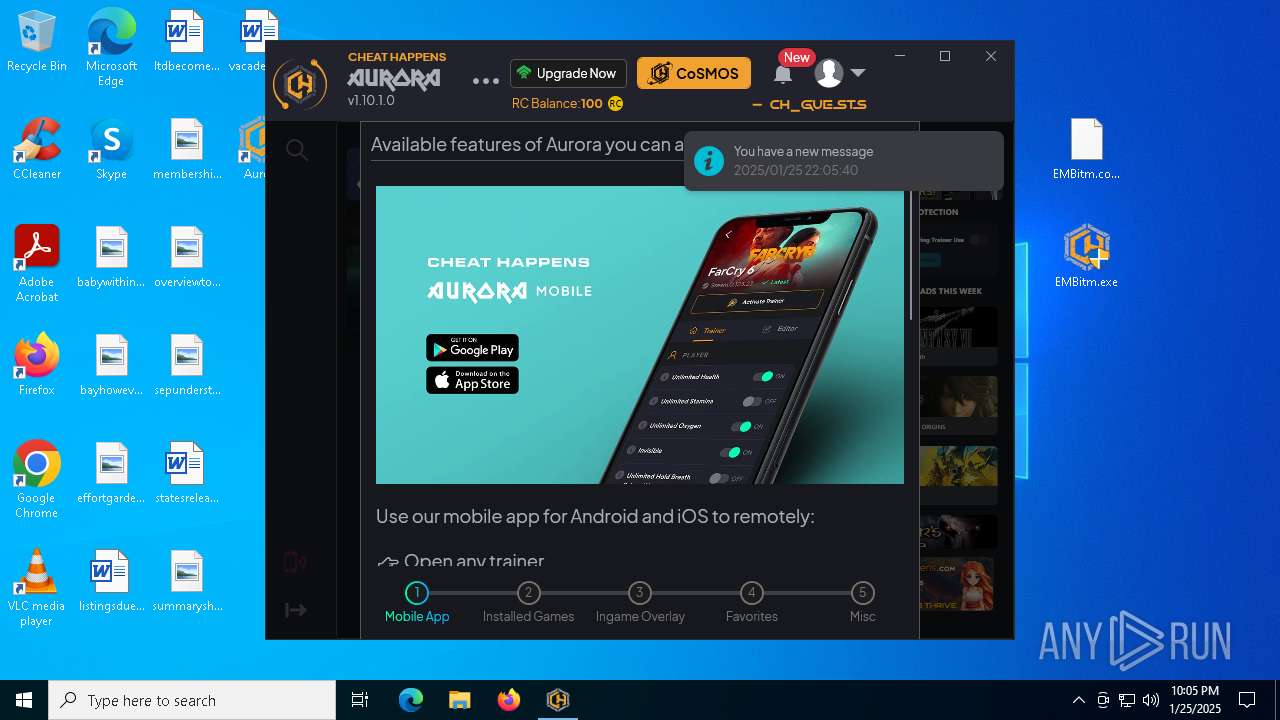
| File name: | Ender Magnolia Bloom in the mist - Trainer +13.zip |
| Full analysis: | https://app.any.run/tasks/2b2ebf4c-cf1f-46b8-a7f5-546da4ae90c2 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2025, 22:04:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2AC9A4130F4C8C98D66D8167871FAD79 |
| SHA1: | 1B38067F901587364800DD919CA415124D7D8F2F |
| SHA256: | 679E7B11B808CE0AAE850B5F537489B1C0F95EF62829630C83456D6FEB65C173 |
| SSDEEP: | 6144:cXK5UzOCU5JOlnFMGlREXnDwC2akRzenYGXUec:Gh86FMG3oDwCZ7nYGXUj |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6404)
SUSPICIOUS
Executable content was dropped or overwritten
- EMBitm.exe (PID: 7004)
The process creates files with name similar to system file names
- EMBitm.exe (PID: 7004)
Process drops legitimate windows executable
- EMBitm.exe (PID: 7004)
Reads security settings of Internet Explorer
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 4952)
Reads the date of Windows installation
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 4952)
The process drops C-runtime libraries
- EMBitm.exe (PID: 7004)
INFO
Reads the computer name
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 4952)
Reads Environment values
- EMBitm.exe (PID: 7004)
Create files in a temporary directory
- EMBitm.exe (PID: 7004)
Checks supported languages
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 4952)
- Aurora.exe (PID: 3984)
Manual execution by a user
- EMBitm.exe (PID: 6944)
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 6924)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 3288)
- Aurora.exe (PID: 4952)
- Aurora.exe (PID: 6180)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6404)
Reads the machine GUID from the registry
- EMBitm.exe (PID: 7004)
Checks proxy server information
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 4952)
Reads the software policy settings
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 4952)
Creates files in the program directory
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
The sample compiled with english language support
- EMBitm.exe (PID: 7004)
Disables trace logs
- EMBitm.exe (PID: 7004)
Process checks computer location settings
- EMBitm.exe (PID: 7004)
- Aurora.exe (PID: 5532)
- Aurora.exe (PID: 1460)
- Aurora.exe (PID: 3984)
- Aurora.exe (PID: 4952)
Creates files or folders in the user directory
- Aurora.exe (PID: 5532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:01 19:47:44 |
| ZipCRC: | 0x50d88b10 |
| ZipCompressedSize: | 5 |
| ZipUncompressedSize: | 5 |
| ZipFileName: | EMBitm.config |
Total processes
141
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1460 | "C:\Program Files\CH Aurora\Aurora.exe" | C:\Program Files\CH Aurora\Aurora.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.10.1.0 Modules
| |||||||||||||||
| 3288 | "C:\Program Files\CH Aurora\Aurora.exe" | C:\Program Files\CH Aurora\Aurora.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.10.1.0 | |||||||||||||||
| 3984 | "C:\Program Files\CH Aurora\Aurora.exe" | C:\Program Files\CH Aurora\Aurora.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.10.1.0 | |||||||||||||||
| 4952 | "C:\Program Files\CH Aurora\Aurora.exe" | C:\Program Files\CH Aurora\Aurora.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.10.1.0 | |||||||||||||||
| 5532 | "C:\Program Files\CH Aurora\Aurora.exe" chaurora://promotrainer=73781 | C:\Program Files\CH Aurora\Aurora.exe | EMBitm.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.10.1.0 Modules
| |||||||||||||||
| 6180 | "C:\Program Files\CH Aurora\Aurora.exe" | C:\Program Files\CH Aurora\Aurora.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.10.1.0 Modules
| |||||||||||||||
| 6404 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Ender Magnolia Bloom in the mist - Trainer +13.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6924 | "C:\Program Files\CH Aurora\Aurora.exe" | C:\Program Files\CH Aurora\Aurora.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.10.1.0 Modules
| |||||||||||||||
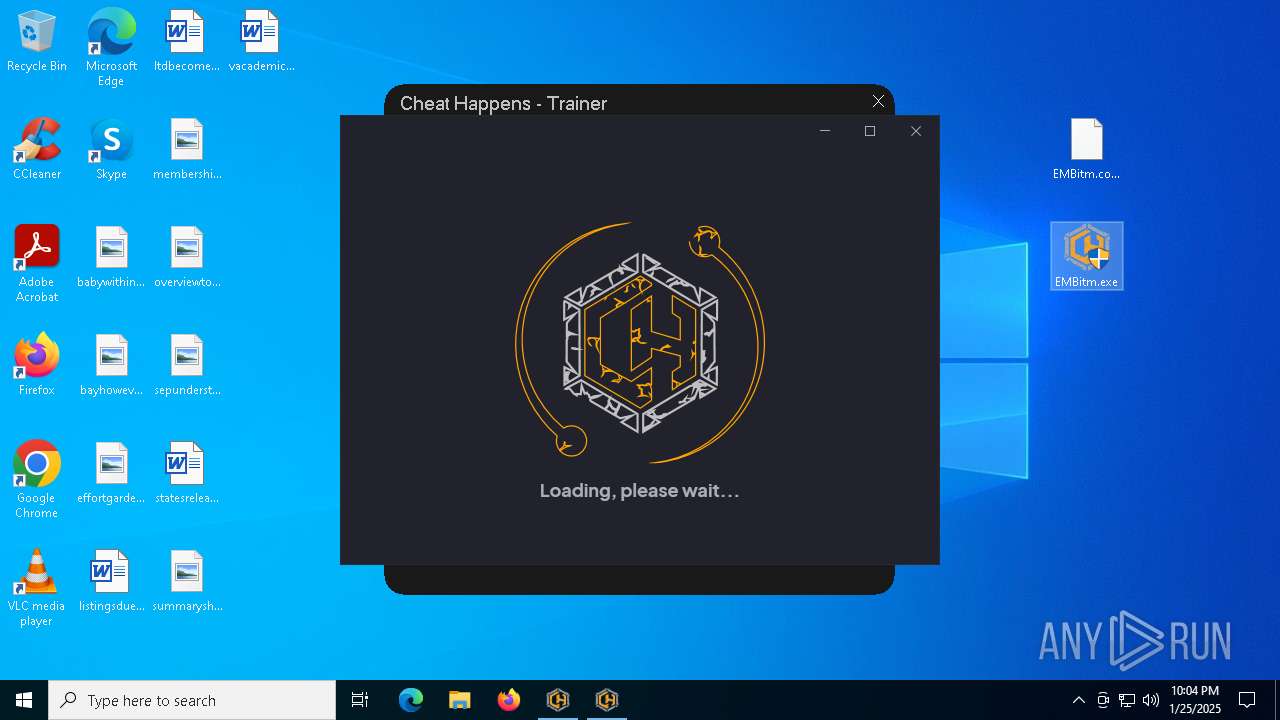
| 6944 | "C:\Users\admin\Desktop\EMBitm.exe" | C:\Users\admin\Desktop\EMBitm.exe | — | explorer.exe | |||||||||||
User: admin Company: Cheat Happens Integrity Level: MEDIUM Description: CH Trainer Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7004 | "C:\Users\admin\Desktop\EMBitm.exe" | C:\Users\admin\Desktop\EMBitm.exe | explorer.exe | ||||||||||||
User: admin Company: Cheat Happens Integrity Level: HIGH Description: CH Trainer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
10 613
Read events
10 561
Write events
52
Delete events
0
Modification events
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ender Magnolia Bloom in the mist - Trainer +13.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
284
Suspicious files
70
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7004 | EMBitm.exe | C:\Users\admin\AppData\Local\Temp\tmp7A92.tmp | — | |
MD5:— | SHA256:— | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6404.46169\EMBitm.exe | executable | |
MD5:03BB1E34D4B42568AFFD7A4EBDDEB3EE | SHA256:7E850D16CF44D92226901C73773D4B04E414FFA70E22D47C6A6B486AF2F2E8C6 | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6404.46169\EMBitm.config | text | |
MD5:7F40BEC3DF593B31FEAF13DD4A696415 | SHA256:D7DAC0CC377CBA380A151B8494857F7876692632DD54BAA39F7B776FDBB0EEBB | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\female\hotkeys muted.mp3 | binary | |
MD5:BB3F965E332FB2CC459ED44F4A8A2CAA | SHA256:DE2EF38996928FE0D900ADBC0D7FF024B4717262D74B3D3F350B688A007D8DC4 | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\female\hotkeys unmuted.mp3 | binary | |
MD5:754EC024C4E28F133623FD7E7ECCD2D4 | SHA256:3815BEEB92FF012F14280EDAF71265FF570549DF7B73EFB112AA72116CEFE3F9 | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\female\trainer activated.mp3 | binary | |
MD5:E98DAF9449760110C0962670E343BB32 | SHA256:57539CE3E147A6E6682F84BF86168E44A6752E0DDBBF8B044A35E87F394C0328 | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\female\please wait.mp3 | binary | |
MD5:0FBCD96E1BDAA256EE8D8C080EBF571B | SHA256:6C30177C1BA14CF0417D975B08A748C6ECDDD4104D57881817435F62E11E3144 | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\female\savegame protected.mp3 | binary | |
MD5:69E245EAA034766DFB2064E22E9D33E8 | SHA256:A57971278C0FF067B078B1F9BDFBDDF9D399B308B7ABBE3D3DA7BAD5254AD10B | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\female\activated.mp3 | binary | |
MD5:359966B574E77BEF79F801D6D552DB39 | SHA256:86B7E5A957793C629F48FD80308CBDC932B3C55CEB27E9D959AD091B304FB499 | |||
| 7004 | EMBitm.exe | C:\Program Files\CH Aurora\audio\please wait.mp3 | binary | |
MD5:DE40712B34492EBA152848BB395C3A7D | SHA256:807E5A10308B26164860A2C87603A42C3A413A4C0E4493CBFF9F7095623449BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
77
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.191:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6284 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3040 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.16.204.148:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.48.23.191:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.ch-downloads.com |
| unknown |
arc.msn.com |
| whitelisted |