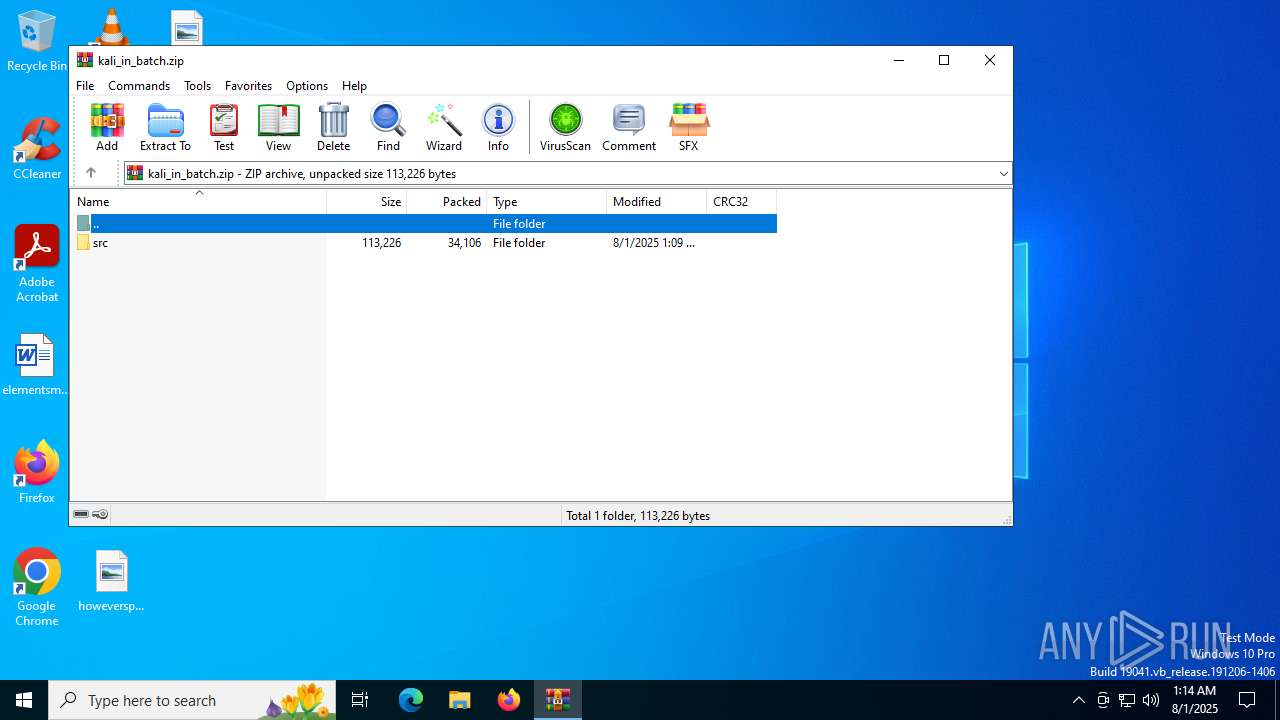
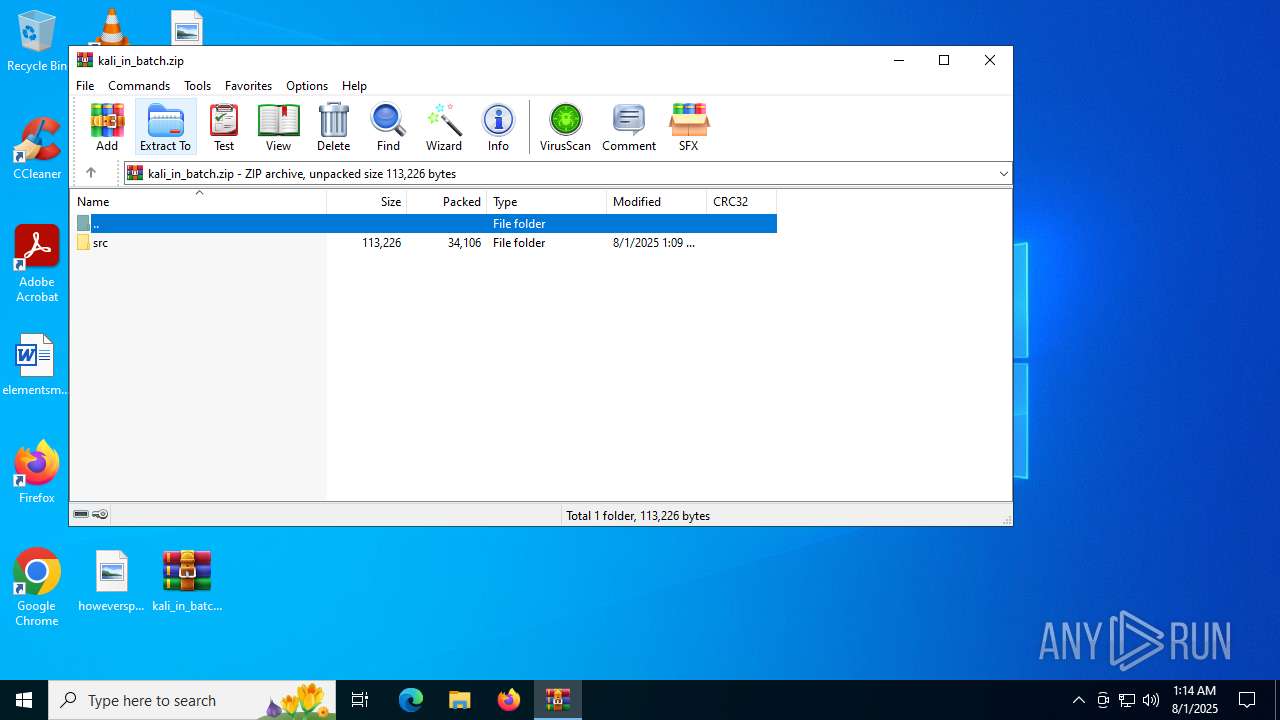
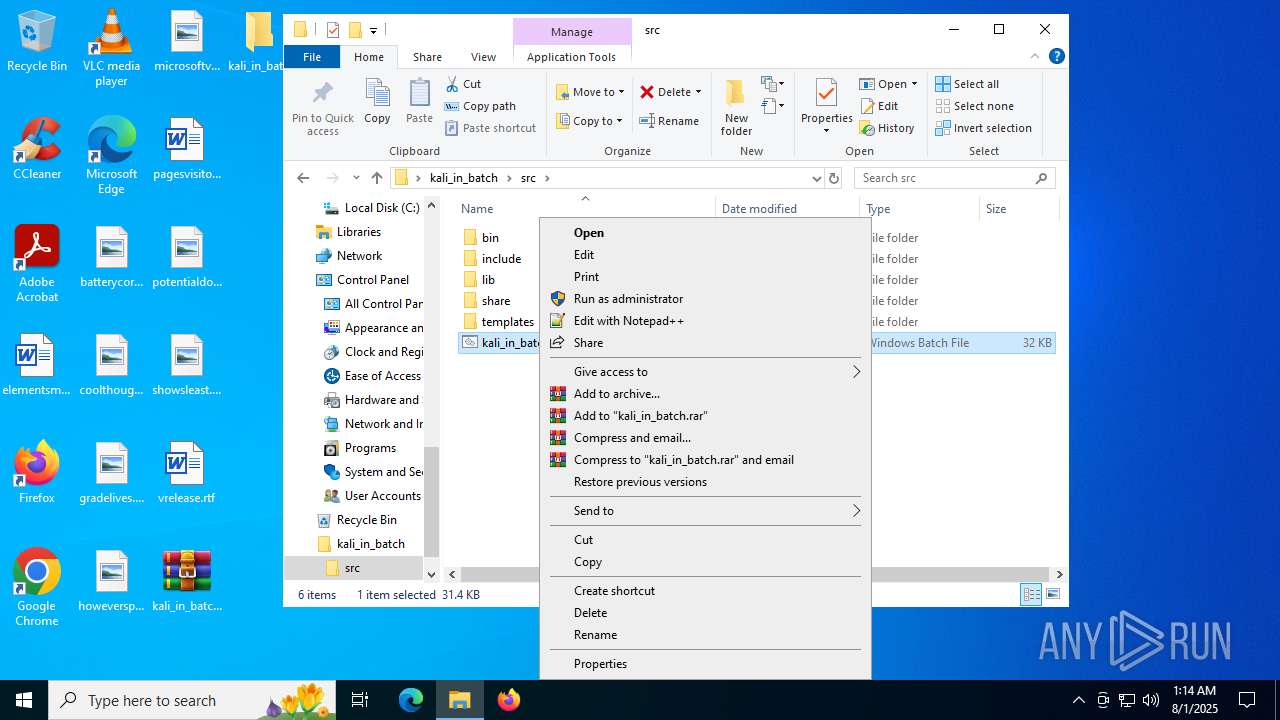
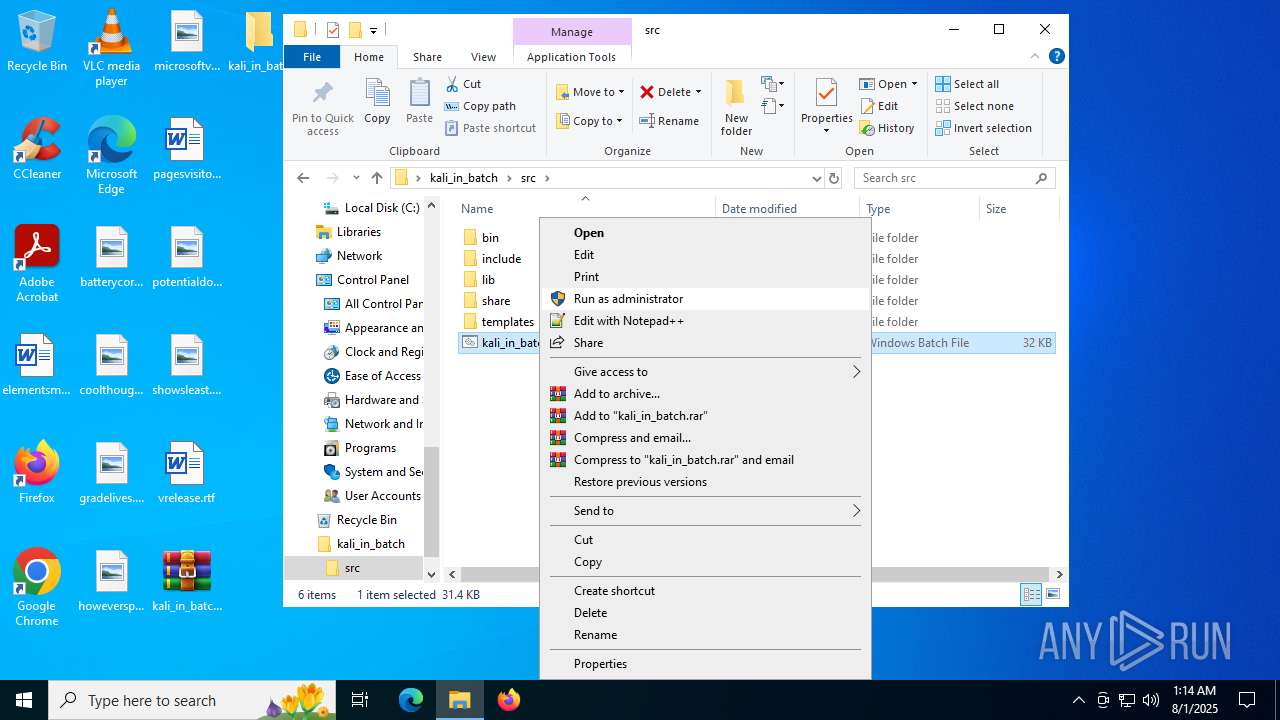
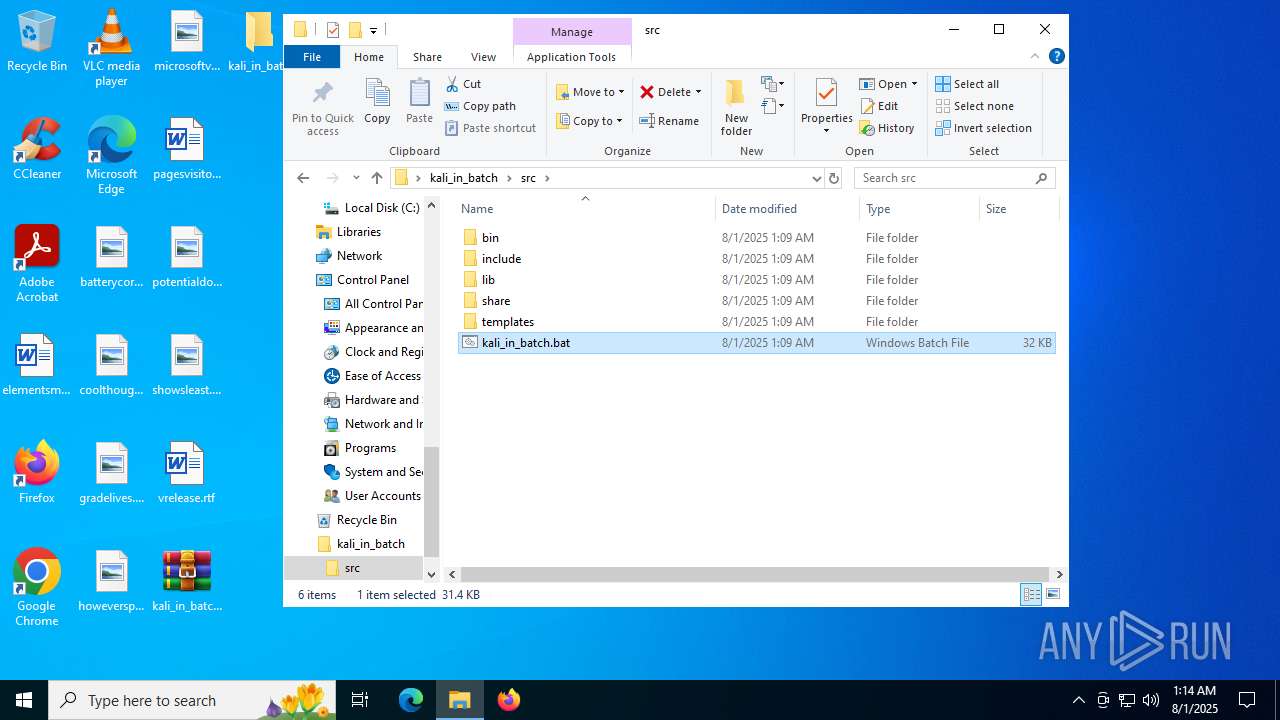
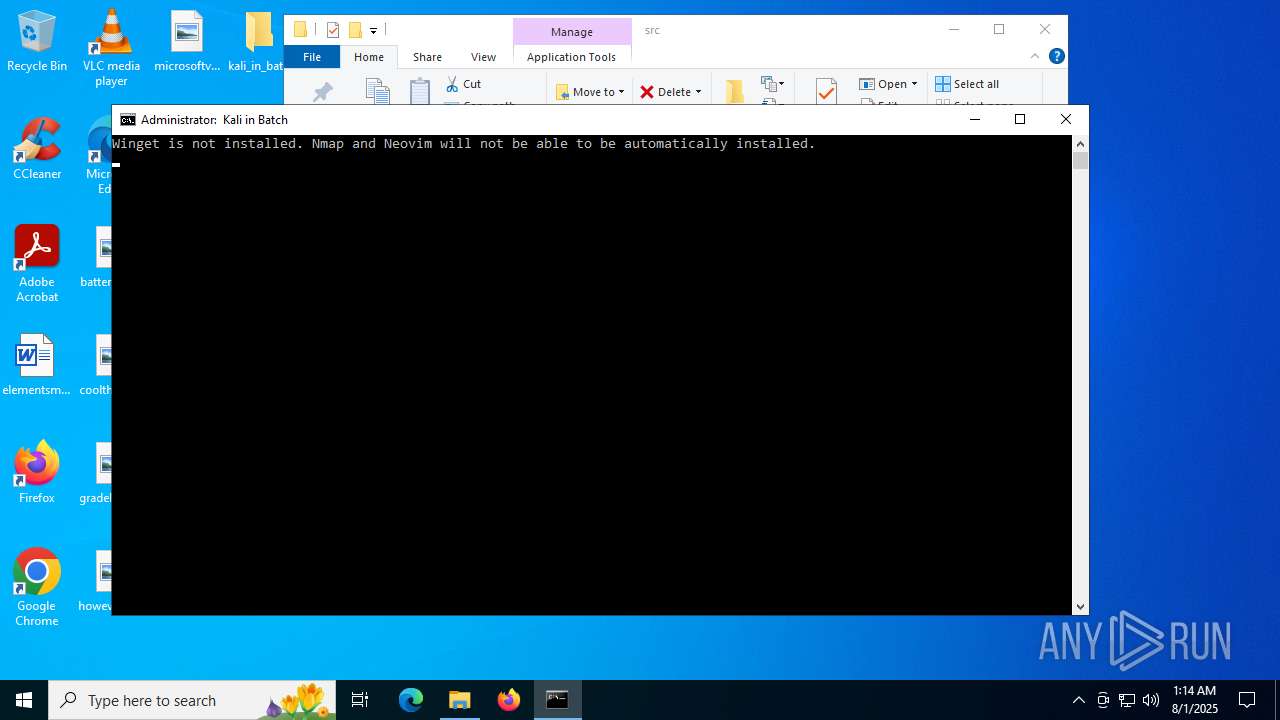
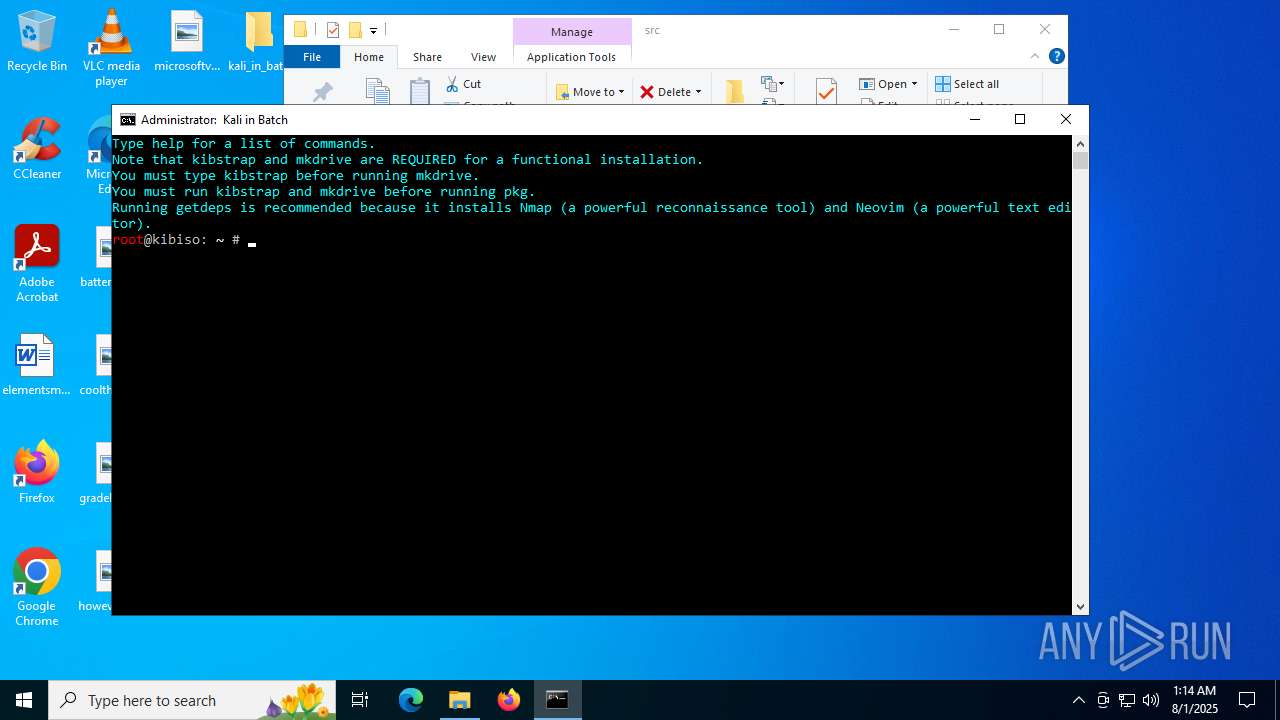
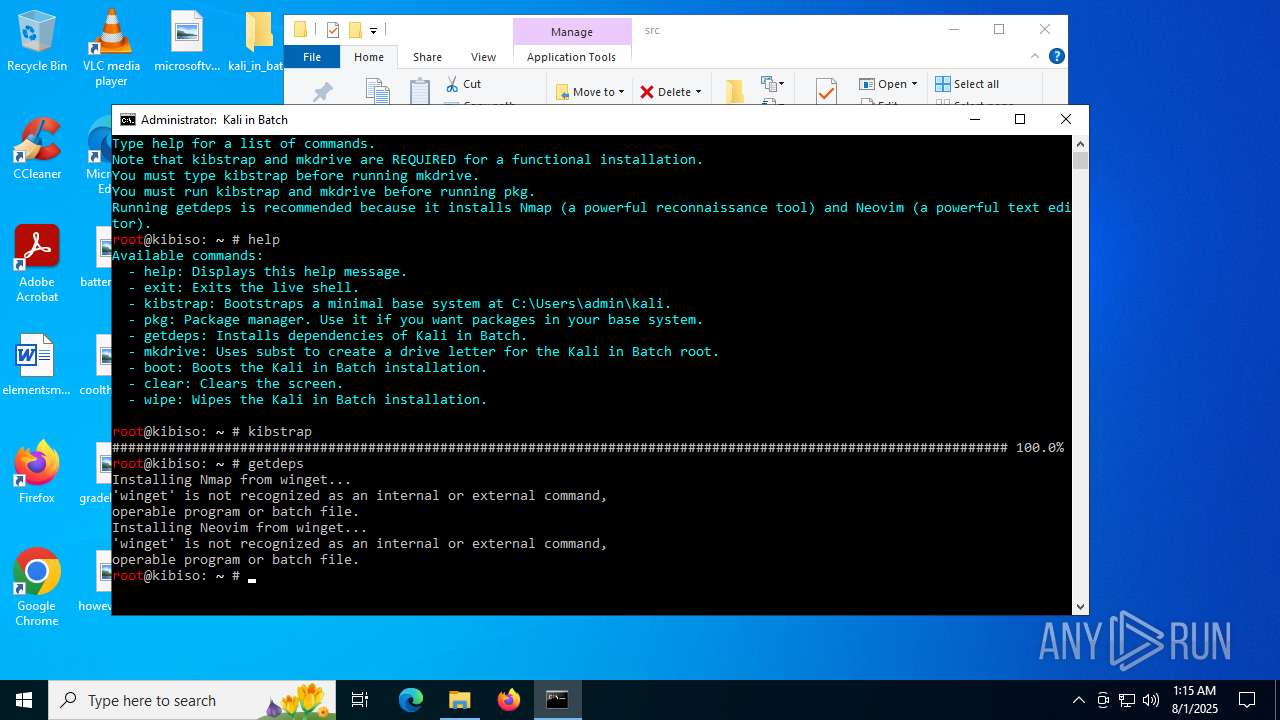
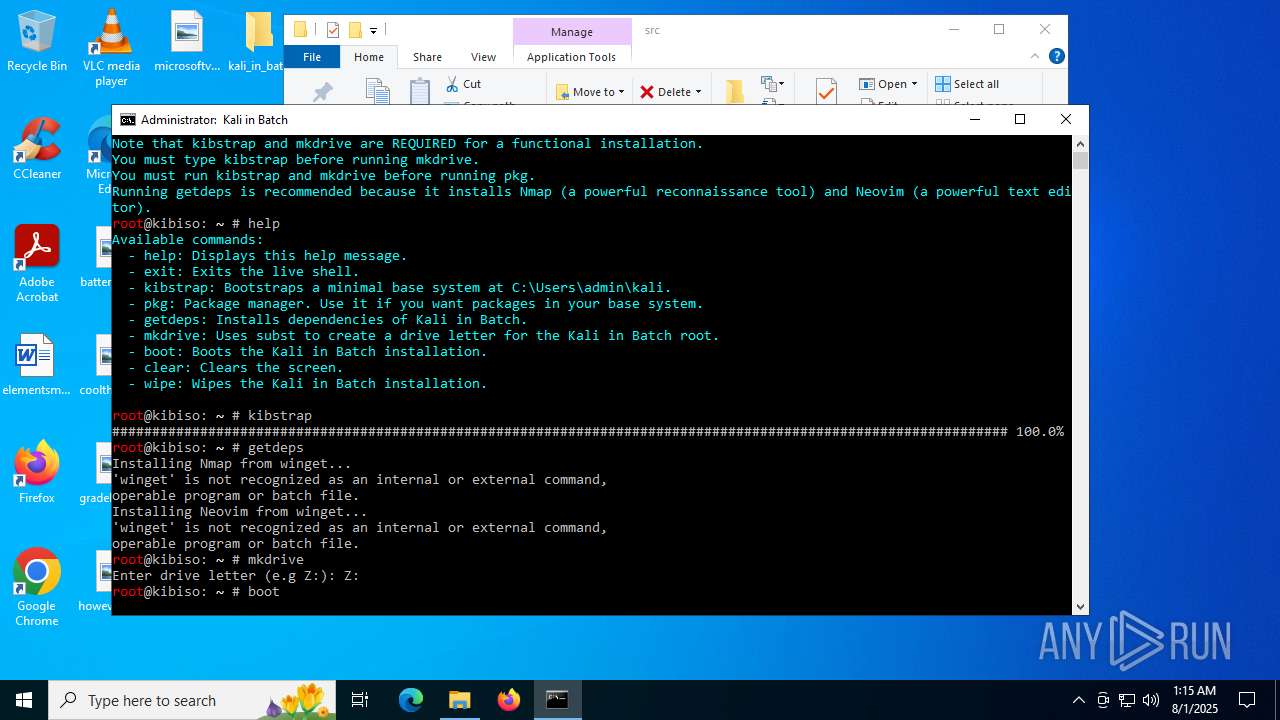
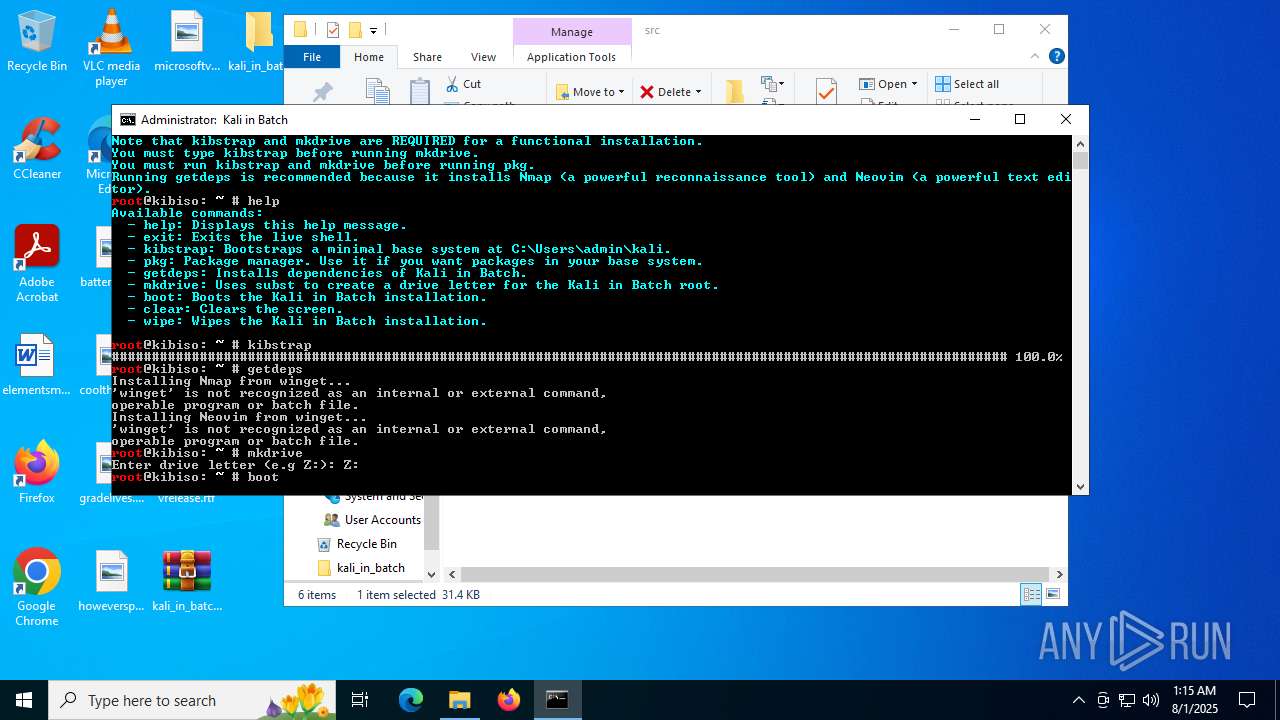
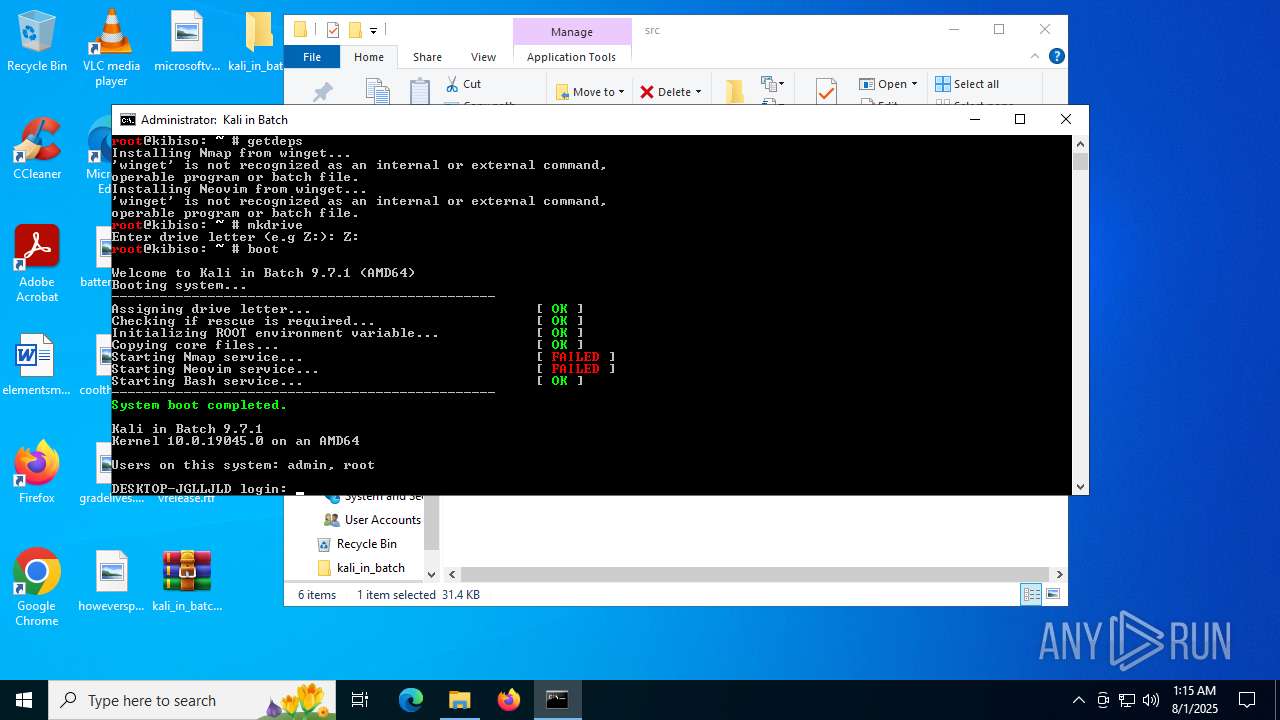
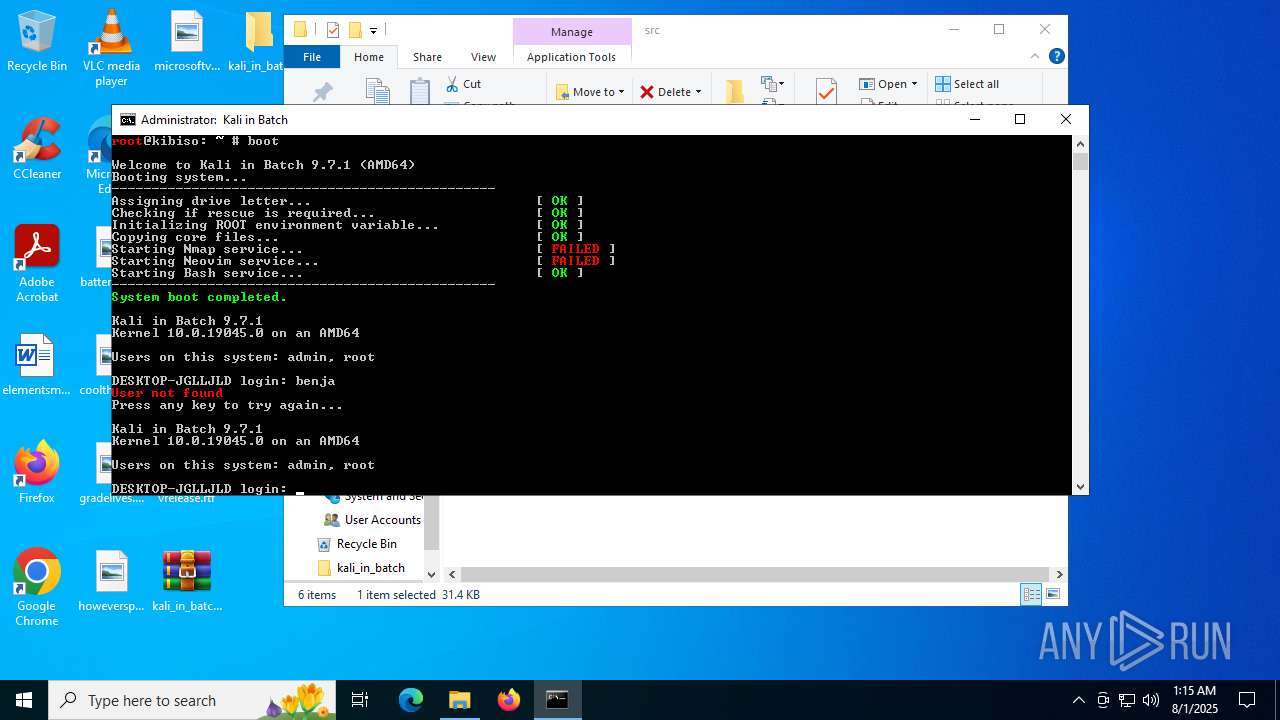
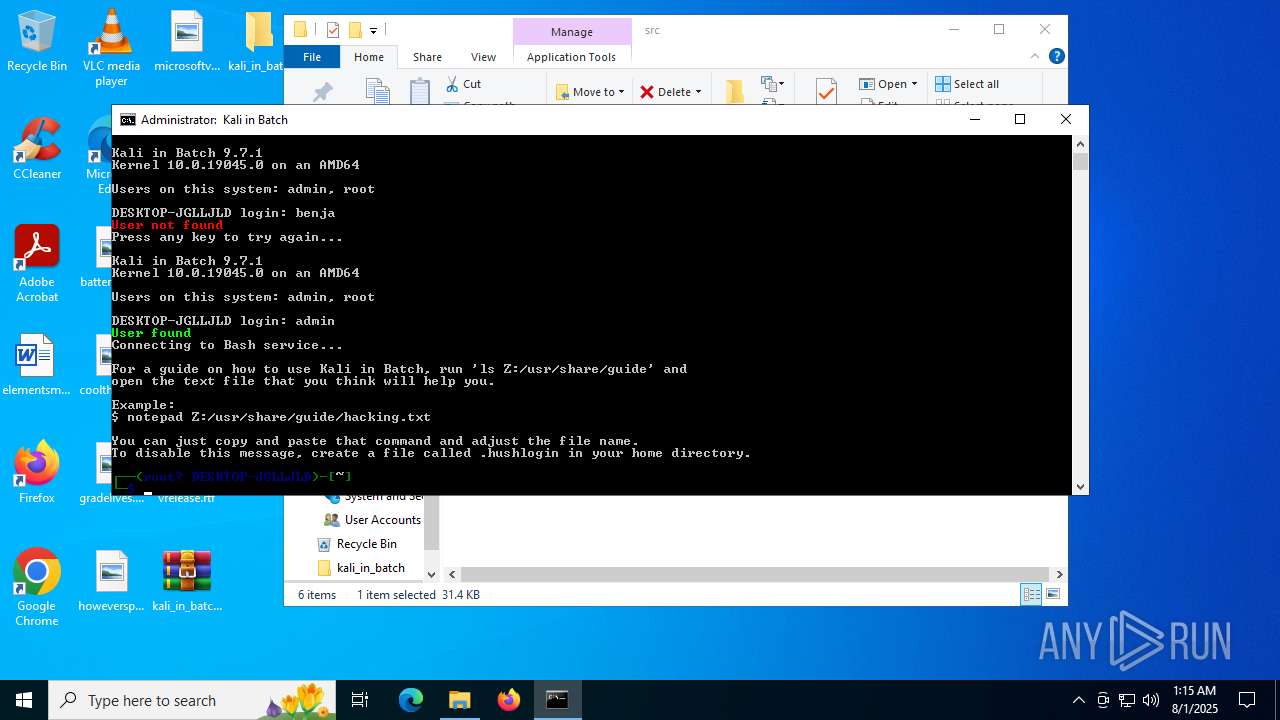
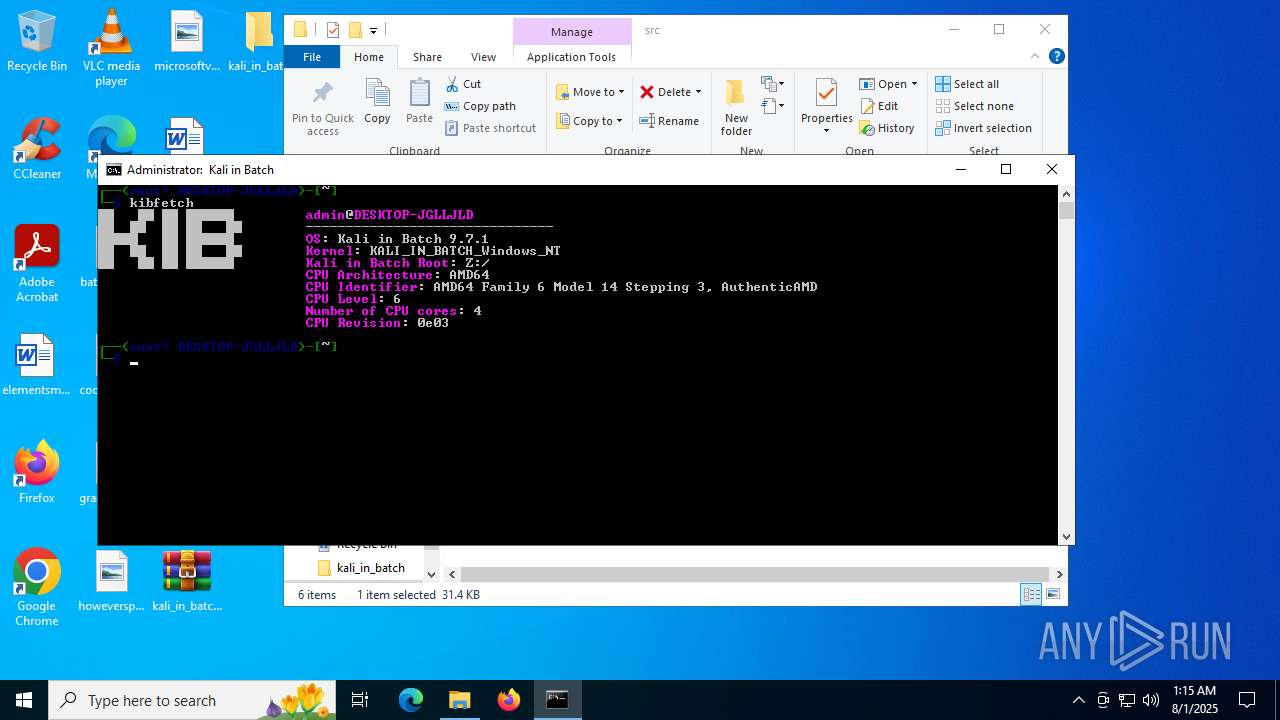
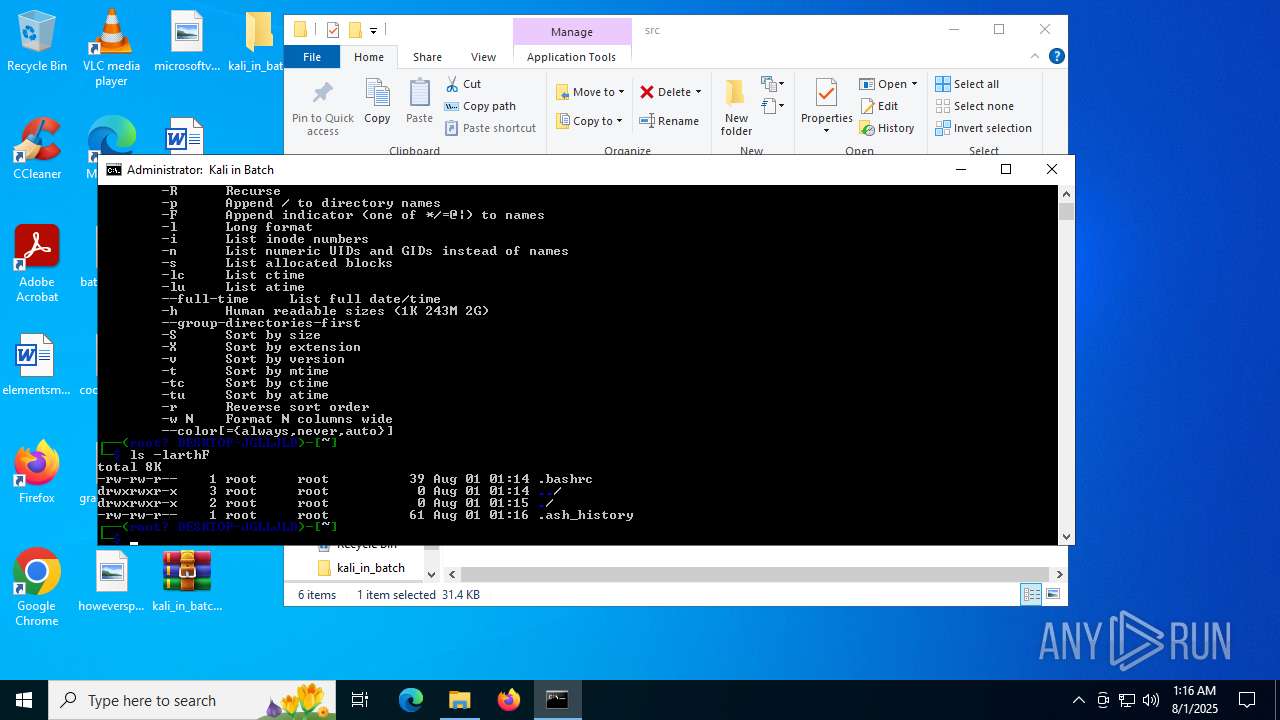
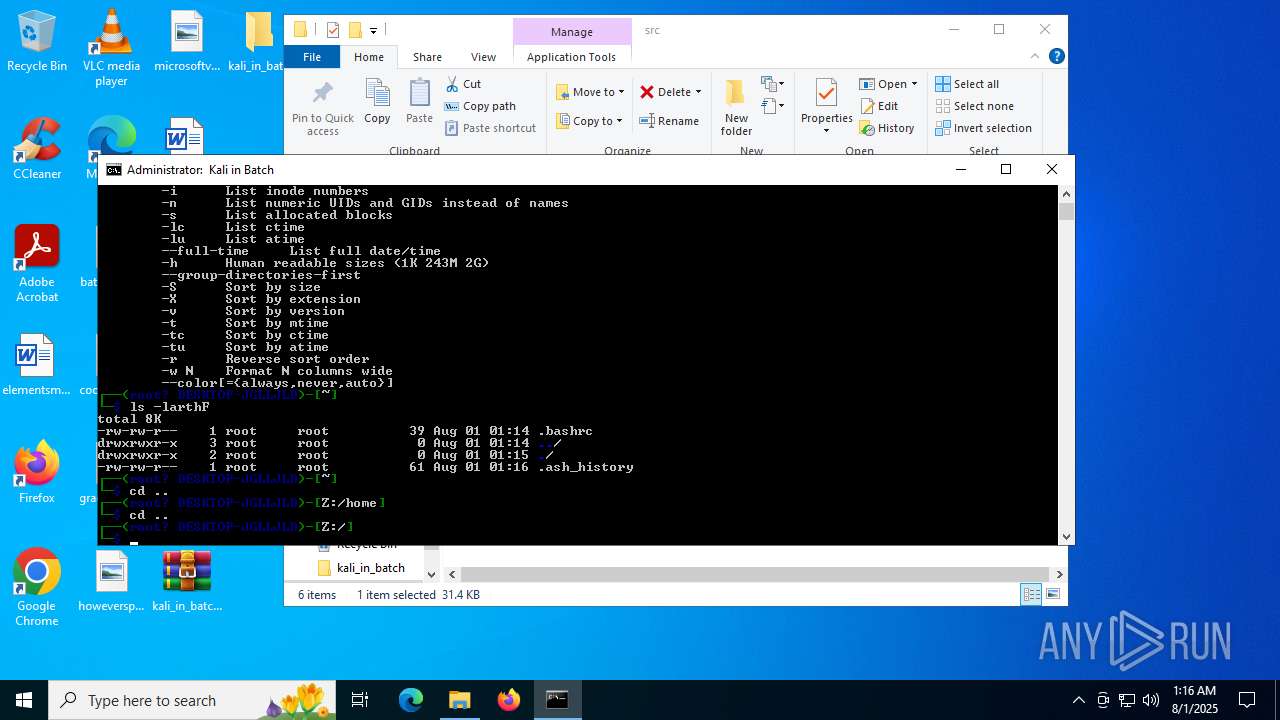
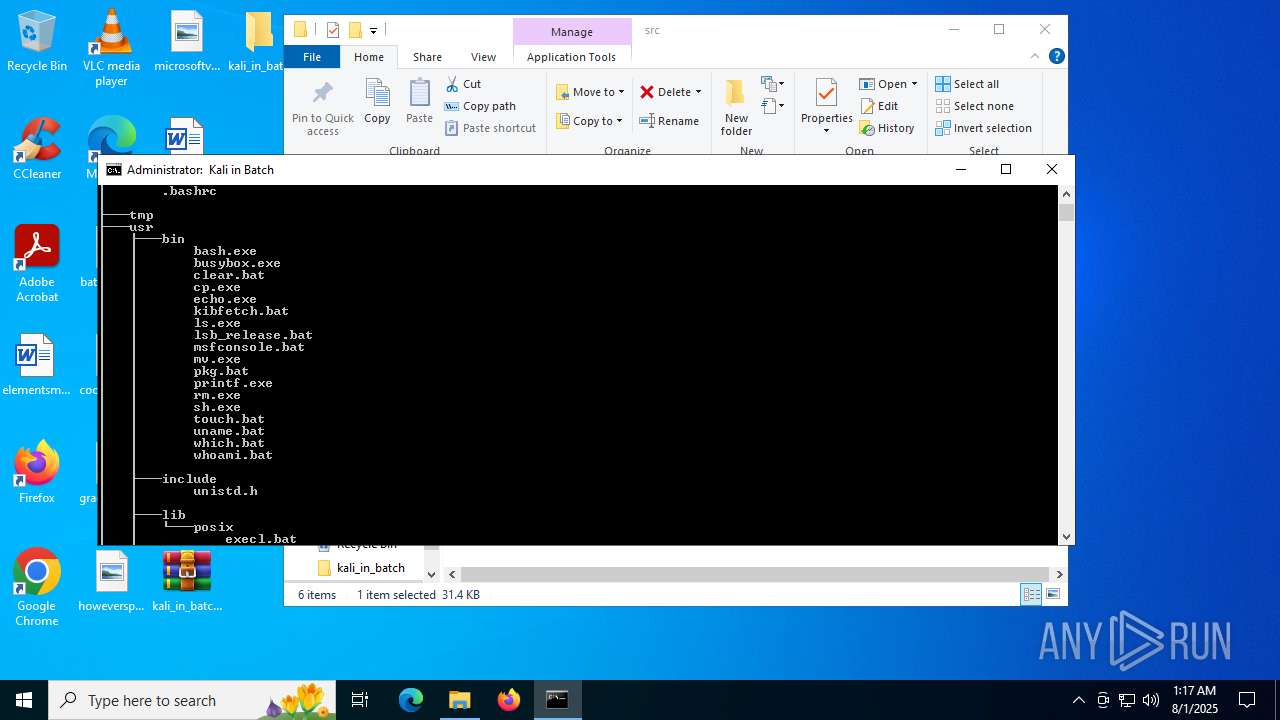
| File name: | kali_in_batch.zip |
| Full analysis: | https://app.any.run/tasks/f49d128e-2265-4671-8411-275e56f9f5d5 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 01:14:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 4E35E527809A04B8AF950FDE11DA1024 |
| SHA1: | 9E34E6E4083D0BD9F357771C2F11A695FED7AE6D |
| SHA256: | 6778FDD58B4C15D48E9AFF301BDFEB01F388E1BF4179403B5280A45D05C0E04A |
| SSDEEP: | 768:HS0MoUBLDXEIrGY2d+RSF5sOudOefmQ3EV+goCm1e3RV:fMfEIrGToRs51udOCmS16X |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1816)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 5628)
- cmd.exe (PID: 3656)
- busybox.exe (PID: 4084)
- busybox.exe (PID: 4192)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5628)
Executable content was dropped or overwritten
- curl.exe (PID: 5744)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5628)
- busybox.exe (PID: 4232)
- busybox.exe (PID: 3740)
- cmd.exe (PID: 768)
- busybox.exe (PID: 6524)
- cmd.exe (PID: 4684)
- busybox.exe (PID: 5460)
- busybox.exe (PID: 3652)
- busybox.exe (PID: 6164)
- busybox.exe (PID: 3112)
- busybox.exe (PID: 6676)
- busybox.exe (PID: 5236)
- busybox.exe (PID: 5424)
- busybox.exe (PID: 5528)
- busybox.exe (PID: 4544)
- busybox.exe (PID: 6472)
Application launched itself
- cmd.exe (PID: 5628)
- busybox.exe (PID: 6636)
- cmd.exe (PID: 4684)
- cmd.exe (PID: 768)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6356)
The executable file from the user directory is run by the CMD process
- busybox.exe (PID: 2064)
INFO
Manual execution by a user
- cmd.exe (PID: 5628)
Checks supported languages
- chcp.com (PID: 856)
- curl.exe (PID: 5744)
- busybox.exe (PID: 6636)
- busybox.exe (PID: 4232)
- busybox.exe (PID: 3740)
- busybox.exe (PID: 6524)
- busybox.exe (PID: 5460)
- busybox.exe (PID: 3652)
- chcp.com (PID: 4844)
- busybox.exe (PID: 7080)
- busybox.exe (PID: 4444)
- busybox.exe (PID: 6164)
- busybox.exe (PID: 3112)
- busybox.exe (PID: 1236)
- busybox.exe (PID: 6676)
- busybox.exe (PID: 4084)
- tree.com (PID: 3880)
- tree.com (PID: 6868)
- busybox.exe (PID: 4192)
- busybox.exe (PID: 6260)
- busybox.exe (PID: 5236)
- busybox.exe (PID: 1336)
- busybox.exe (PID: 5424)
- busybox.exe (PID: 5528)
- curl.exe (PID: 3624)
- curl.exe (PID: 6140)
- curl.exe (PID: 4688)
- curl.exe (PID: 3852)
- curl.exe (PID: 4700)
- curl.exe (PID: 5476)
- curl.exe (PID: 4648)
- busybox.exe (PID: 2064)
- busybox.exe (PID: 2356)
- busybox.exe (PID: 4544)
- busybox.exe (PID: 6472)
Changes the display of characters in the console
- cmd.exe (PID: 5628)
- cmd.exe (PID: 3656)
Execution of CURL command
- cmd.exe (PID: 5628)
- cmd.exe (PID: 768)
Reads the computer name
- curl.exe (PID: 5744)
- busybox.exe (PID: 6636)
- curl.exe (PID: 6140)
- curl.exe (PID: 3624)
- curl.exe (PID: 3852)
- curl.exe (PID: 4688)
- curl.exe (PID: 4700)
- curl.exe (PID: 5476)
- curl.exe (PID: 4648)
- busybox.exe (PID: 2064)
- busybox.exe (PID: 2356)
Reads the machine GUID from the registry
- busybox.exe (PID: 6636)
- busybox.exe (PID: 4232)
- busybox.exe (PID: 3740)
- busybox.exe (PID: 5460)
- busybox.exe (PID: 6524)
- busybox.exe (PID: 3652)
- busybox.exe (PID: 7080)
- busybox.exe (PID: 6164)
- busybox.exe (PID: 4444)
- busybox.exe (PID: 1236)
- busybox.exe (PID: 4084)
- busybox.exe (PID: 4192)
- busybox.exe (PID: 5236)
- busybox.exe (PID: 6260)
- busybox.exe (PID: 5424)
- busybox.exe (PID: 1336)
- busybox.exe (PID: 5528)
- busybox.exe (PID: 2064)
- busybox.exe (PID: 4544)
- busybox.exe (PID: 2356)
- busybox.exe (PID: 6472)
- busybox.exe (PID: 6676)
- busybox.exe (PID: 3112)
The sample compiled with english language support
- curl.exe (PID: 5744)
Checks operating system version
- cmd.exe (PID: 4684)
- cmd.exe (PID: 768)
Reads the software policy settings
- slui.exe (PID: 4196)
Checks proxy server information
- slui.exe (PID: 4196)
Checks the directory tree
- tree.com (PID: 6868)
- tree.com (PID: 3880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:08:01 01:09:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | src/ |
Total processes
220
Monitored processes
78
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | where winget | C:\Windows\System32\where.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Where - Lists location of files Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 592 | C:\WINDOWS\system32\cmd.exe /c clear | C:\Windows\System32\cmd.exe | — | busybox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\cmd.exe /c uname -a | C:\Windows\System32\cmd.exe | — | busybox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
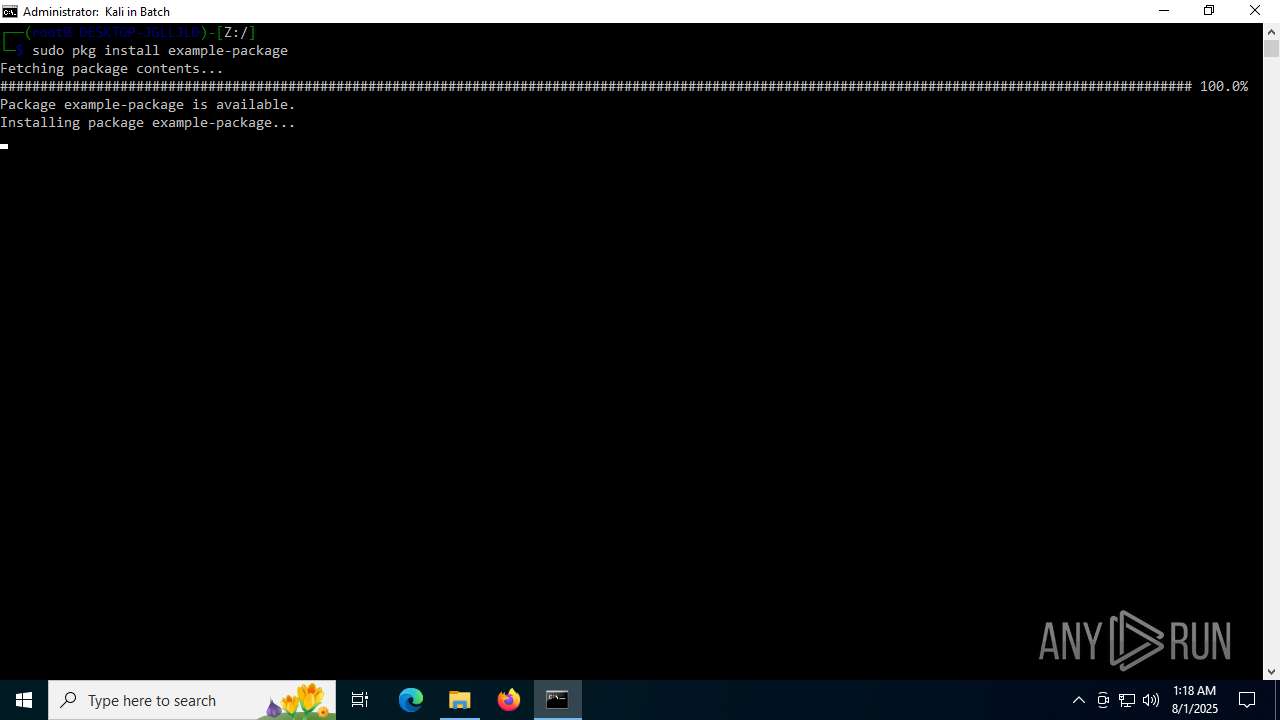
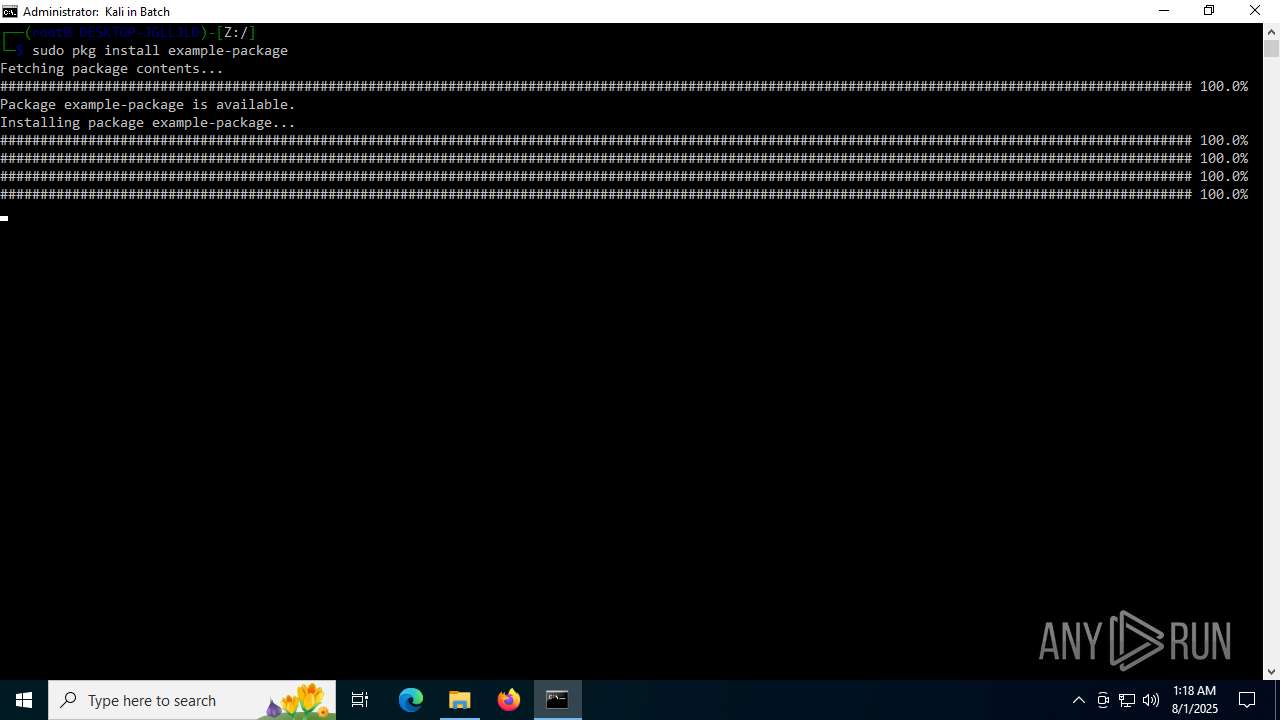
| 768 | C:\WINDOWS\system32\cmd.exe /c pkg install example-package | C:\Windows\System32\cmd.exe | — | busybox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | sh --fs 0000000000000164 | C:\Users\admin\kali\usr\bin\busybox.exe | — | busybox.exe | |||||||||||
User: admin Company: frippery.org Integrity Level: HIGH Description: BusyBox multi-call binary Exit code: 0 Version: 1.38.0-FRP-5579-g5749feb35 Modules
| |||||||||||||||
| 1336 | C:\WINDOWS\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | sh --fs 00000000000001FC | C:\Users\admin\kali\usr\bin\busybox.exe | — | busybox.exe | |||||||||||
User: admin Company: frippery.org Integrity Level: HIGH Description: BusyBox multi-call binary Exit code: 0 Version: 1.38.0-FRP-5579-g5749feb35 Modules
| |||||||||||||||
| 1604 | C:\WINDOWS\system32\cmd.exe /c clear | C:\Windows\System32\cmd.exe | — | busybox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1632 | C:\WINDOWS\system32\cmd.exe /c clear | C:\Windows\System32\cmd.exe | — | busybox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 424
Read events
10 210
Write events
46
Delete events
168
Modification events
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\kali_in_batch.zip | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
1
Suspicious files
1
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\lib\posix\README.md | text | |
MD5:ED8F05D78673A2159B2909D67798ABD0 | SHA256:C7B887A52DA8871CA297CBBDB1842CC3326CD134BADC3A87E36DD15820B5A2D6 | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\lib\posix\fork.bat | text | |
MD5:0B86690A8980582618A3F92237E87064 | SHA256:C0D8DD4A3F47A42A5B4839539D17AAEF6DCA2D3E83B46856F1E66F5573D4E497 | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\lib\posix\mkdir.bat | text | |
MD5:328EF7B218E8DC695285CAA974CB762F | SHA256:B90D4397F7E905F34DCA883747BDBD9F2AEB7C0B24EB43DBE929F6561CFB2174 | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\bin\touch.bat | text | |
MD5:C40C37E4C424A72F77CBE28610CF29BC | SHA256:DAF92F9C839DE88B74E9E18A031D59907B87147422523FED3A1900C48177F620 | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\lib\posix\execl.bat | text | |
MD5:2689FE82CB0697F6247EE8878B0CA36C | SHA256:C23B2152A37C93D1897F370AD05A09B86271A004CEB149501454D1099712848A | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\bin\clear.bat | text | |
MD5:AA4032C2BD2BBB123112740B6EDD7EDB | SHA256:2758DE5C4570F7381DEF913123FCBCF264758B58C8A7E3B74660B74491B4A946 | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\share\guide\hacking.txt | text | |
MD5:A5DBB3D606BE9FBF0B243AC8A068C2B5 | SHA256:A859C6C2E3DC18C82DD93FFA2EE69DB3D9C4189067AEE5142BC9DBFD7B839228 | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\bin\pkg.bat | text | |
MD5:587B011C34CC668A835157930D5B1DC6 | SHA256:A0DE1620C82FEC66C385EC59129A54C43951CC3EEA7A63F3E2FCB5AAA904A6AD | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\bin\whoami.bat | text | |
MD5:0FE8127FEFBB4FA7AFEF11855B102326 | SHA256:B05A150CEA3D48A6AD266564D2530463243AB4D739C60CCDCB7610B4A620921F | |||
| 1816 | WinRAR.exe | C:\Users\admin\Desktop\kali_in_batch\src\bin\lsb_release.bat | text | |
MD5:AB3FC6D9C78BA77385B88998BB7D28E1 | SHA256:BD242CA792A755111E33C6EAD9597AA65D5D4AE9DCB6C939F319482C6DDA563A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
40
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.24.77.7:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2612 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7040 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2612 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
6876 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCQdzRBRzFu%2BZWZdnrq%2FfG5 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.7:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7040 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7040 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
web.archive.org |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |