| File name: | wrar401.exe |
| Full analysis: | https://app.any.run/tasks/5f30228d-e77c-4907-834c-2643e7027518 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 17:03:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5C988F91D1599D56FB70EE15079CCCA5 |
| SHA1: | 1340A2A6748259D6E33E251EAB878BE18E311263 |
| SHA256: | 675D4FD6FC99E19FB2CCA3E2705148374FD403BE6439497008C928BC6A22FB7D |
| SSDEEP: | 98304:++NdN1piwSfAtmR8aZEHxkN/qwAyyqYQrLATYyUZ6unwvcBQfOHtFxoCfA/bJ9OG:ZMGnUIBmWH |
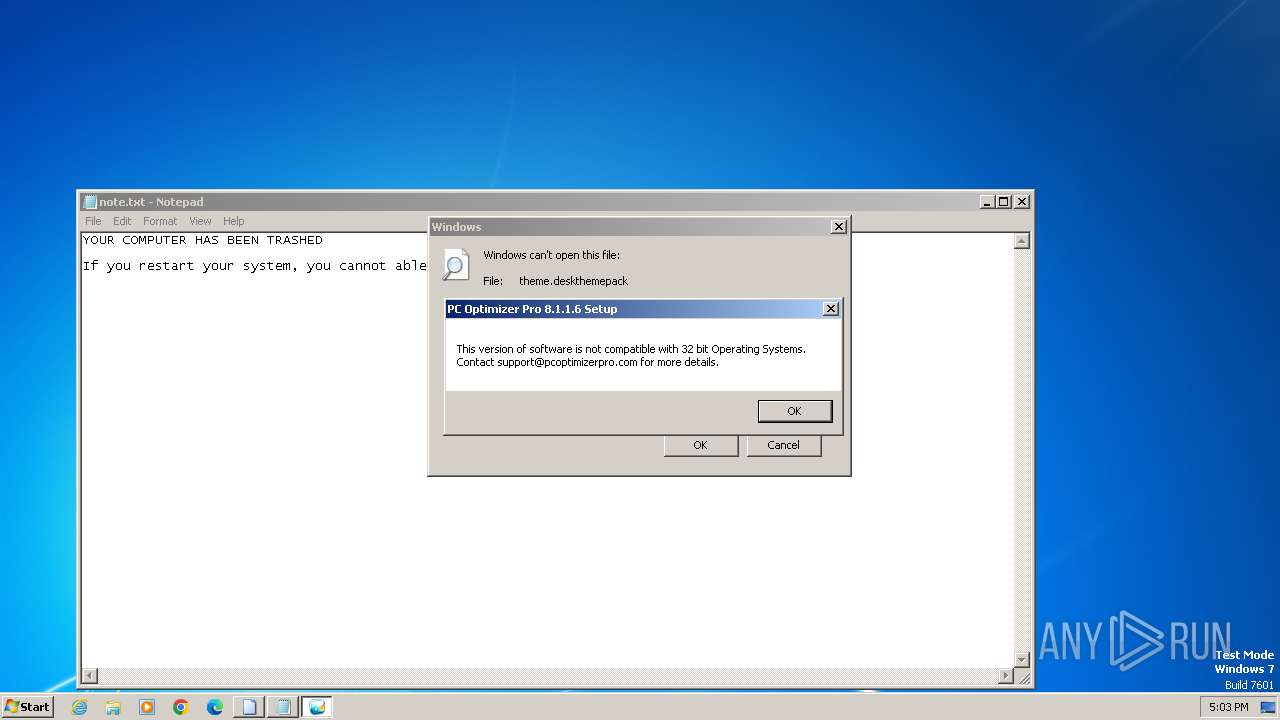
MALICIOUS
Drops the executable file immediately after the start
- wrar401.exe (PID: 3216)
- cmd.exe (PID: 2852)
- PCOptimizerProSetup.exe (PID: 1236)
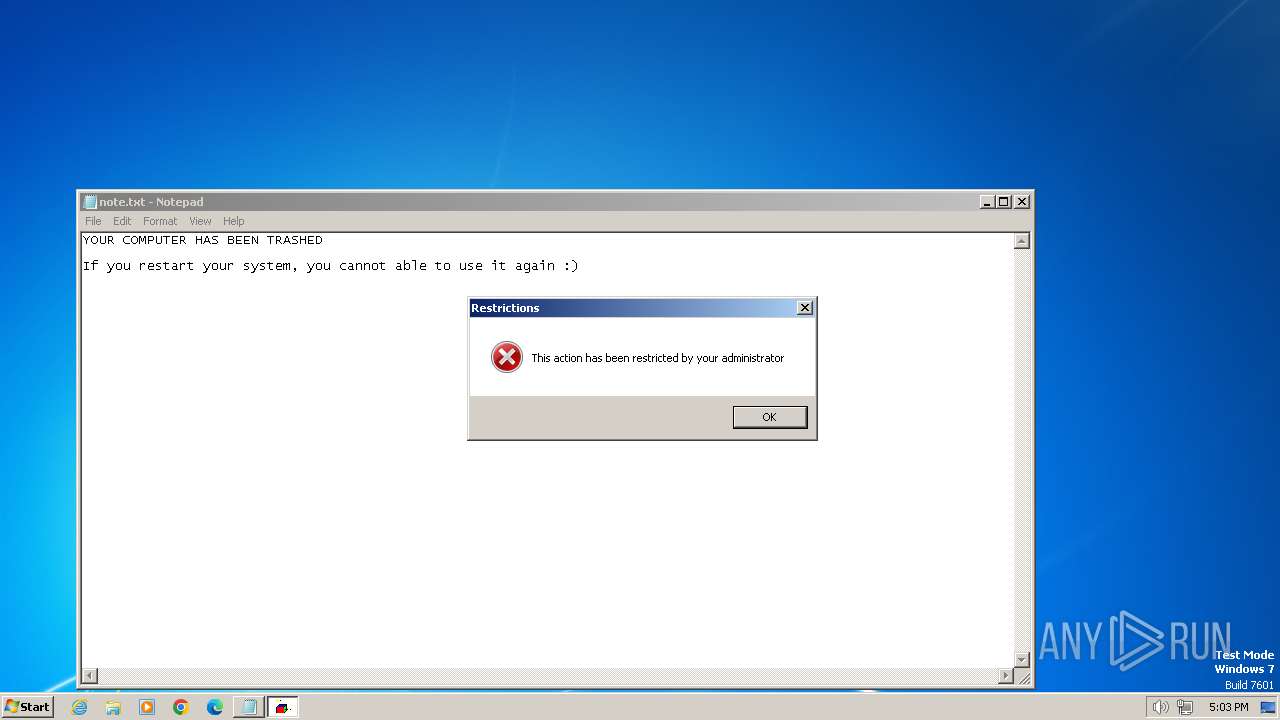
Disables the Run the Start menu
- reg.exe (PID: 2304)
Changes image file execution options
- reg.exe (PID: 3964)
- reg.exe (PID: 3960)
- reg.exe (PID: 2756)
- reg.exe (PID: 2892)
- reg.exe (PID: 1496)
- reg.exe (PID: 3180)
- reg.exe (PID: 1928)
- reg.exe (PID: 1972)
- reg.exe (PID: 2168)
- reg.exe (PID: 3724)
- reg.exe (PID: 2184)
- reg.exe (PID: 2152)
- reg.exe (PID: 3912)
- reg.exe (PID: 2148)
- reg.exe (PID: 3776)
- reg.exe (PID: 3400)
- reg.exe (PID: 1112)
- reg.exe (PID: 116)
Antivirus name has been found in the command line (generic signature)
- reg.exe (PID: 1928)
UAC/LUA settings modification
- reg.exe (PID: 2804)
SUSPICIOUS
Process drops legitimate windows executable
- wrar401.exe (PID: 3216)
- cmd.exe (PID: 2852)
Executable content was dropped or overwritten
- wrar401.exe (PID: 3216)
- cmd.exe (PID: 2852)
- PCOptimizerProSetup.exe (PID: 1236)
Reads security settings of Internet Explorer
- wrar401.exe (PID: 3216)
- winlogon.exe (PID: 448)
Starts CMD.EXE for commands execution
- wrar401.exe (PID: 3216)
Executing commands from a ".bat" file
- wrar401.exe (PID: 3216)
Reads the Internet Settings
- wrar401.exe (PID: 3216)
- winlogon.exe (PID: 448)
- rundll32.exe (PID: 3304)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 2852)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2852)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2852)
Get information on the list of running processes
- cmd.exe (PID: 2852)
The process executes VB scripts
- winlogon.exe (PID: 448)
INFO
Checks supported languages
- wrar401.exe (PID: 3216)
- wmpnscfg.exe (PID: 3800)
- wmpnscfg.exe (PID: 2040)
- winlogon.exe (PID: 448)
- PCOptimizerProSetup.exe (PID: 1236)
Reads the computer name
- wrar401.exe (PID: 3216)
- wmpnscfg.exe (PID: 3800)
- wmpnscfg.exe (PID: 2040)
- winlogon.exe (PID: 448)
- PCOptimizerProSetup.exe (PID: 1236)
Create files in a temporary directory
- wrar401.exe (PID: 3216)
- PCOptimizerProSetup.exe (PID: 1236)
- winlogon.exe (PID: 448)
Creates files in the program directory
- cmd.exe (PID: 2852)
Reads the Internet Settings
- explorer.exe (PID: 3276)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3276)
Application launched itself
- chrome.exe (PID: 984)
- chrome.exe (PID: 2348)
Creates files or folders in the user directory
- explorer.exe (PID: 3276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:30 08:52:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 68608 |
| InitializedDataSize: | 4478464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.1.0 |
| ProductVersionNumber: | 4.0.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 4.0.1.0 |
| ProductVersion: | 4.0.1.0 |
| ProductName: | WinRAR |
| OriginalFileName: | wrar401.exe |
| FileDescription: | Gestore Archivi WinRAR |
| CompanyName: | Alexander Roshal |
| LegalCopyright: | Copyright © Alexander Roshal 1993-2021 |
Total processes
96
Monitored processes
53
Malicious processes
2
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe" /v "Debugger" /t REG_SZ /d C:\ProgramData\Windows\winlogon.exe /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1020 --field-trial-handle=1136,i,15413592955407359287,8288198378900987098,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 296 | "C:\Windows\system32\wscript.exe" C:\Users\admin\AppData\Local\Temp\2381.tmp\2382.tmp\2383.vbs //Nologo "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://go.microsoft.com/fwlink/?LinkId=57426&Ext=deskthemepack | C:\Windows\System32\wscript.exe | — | winlogon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 448 | C:\ProgramData\Windows\winlogon.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://go.microsoft.com/fwlink/?LinkId=57426&Ext=deskthemepack | C:\ProgramData\Windows\winlogon.exe | — | rundll32.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 492 | reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System /v VerboseStatus /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2116 --field-trial-handle=1152,i,2268187293374402880,1912729247846975285,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1348 --field-trial-handle=1136,i,15413592955407359287,8288198378900987098,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 864 | reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v "NoDesktop" /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6dcb8b38,0x6dcb8b48,0x6dcb8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
19 067
Read events
18 793
Write events
266
Delete events
8
Modification events
| (PID) Process: | (3216) wrar401.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3216) wrar401.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3216) wrar401.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3216) wrar401.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2304) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoRun |
Value: 1 | |||
| (PID) Process: | (2444) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoControlPanel |
Value: 1 | |||
| (PID) Process: | (864) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoDesktop |
Value: 1 | |||
| (PID) Process: | (3964) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mmc.exe |
| Operation: | write | Name: | Debugger |
Value: C:\ProgramData\Windows\winlogon.exe | |||
| (PID) Process: | (3960) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\control.exe |
| Operation: | write | Name: | Debugger |
Value: C:\ProgramData\Windows\winlogon.exe | |||
| (PID) Process: | (116) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe |
| Operation: | write | Name: | Debugger |
Value: C:\ProgramData\Windows\winlogon.exe | |||
Executable files
7
Suspicious files
10
Text files
36
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF184570.TMP | — | |
MD5:— | SHA256:— | |||
| 984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3216 | wrar401.exe | C:\Users\admin\AppData\Local\Temp\F397.tmp\F398.tmp\F399.bat | text | |
MD5:CC1776B079B9C5BF8C2803787C3CC98E | SHA256:10629986F3A7F881DE37BE7A6EEED42FE777AF448DE1D7AD4D6512277BE690B3 | |||
| 2852 | cmd.exe | C:\ProgramData\Windows\unlocker.exe | executable | |
MD5:93A3E790118F6F70B4FD7EAF614B74D5 | SHA256:990BD39F895C2A9642211500BB649F2803DAD588FCE6ACDE8256FC86D7438CA8 | |||
| 3216 | wrar401.exe | C:\Users\admin\AppData\Local\Temp\F397.tmp\unlocker.bin | executable | |
MD5:93A3E790118F6F70B4FD7EAF614B74D5 | SHA256:990BD39F895C2A9642211500BB649F2803DAD588FCE6ACDE8256FC86D7438CA8 | |||
| 984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2348 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\126af2fd-f273-4c91-b013-00209870d477.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF184570.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF18458f.TMP | text | |
MD5:ADB669AB4CD1C63883C64FB0DBA2C7DA | SHA256:18BFF89047EC5B122573D089B3DC7A7DD14A5A7A515B2D8141584B41E723253F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1392 | chrome.exe | 142.250.185.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
984 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1392 | chrome.exe | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | unknown |
1392 | chrome.exe | 172.217.16.132:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |