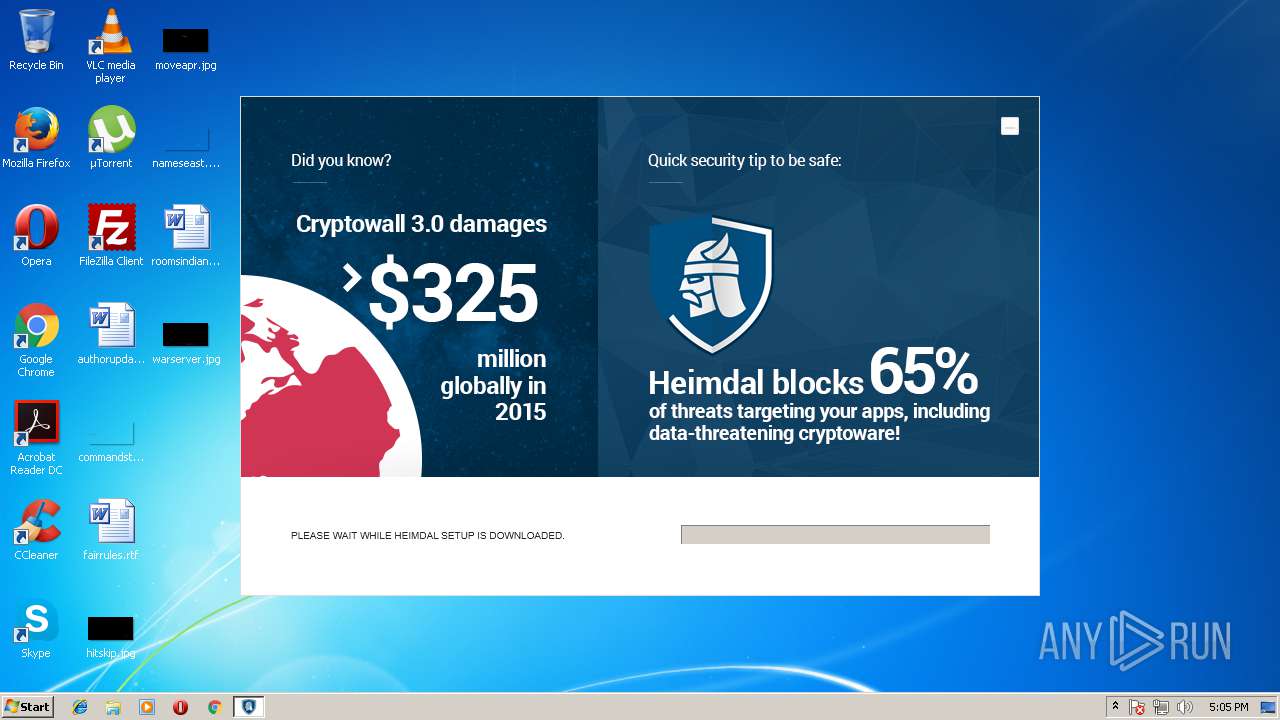
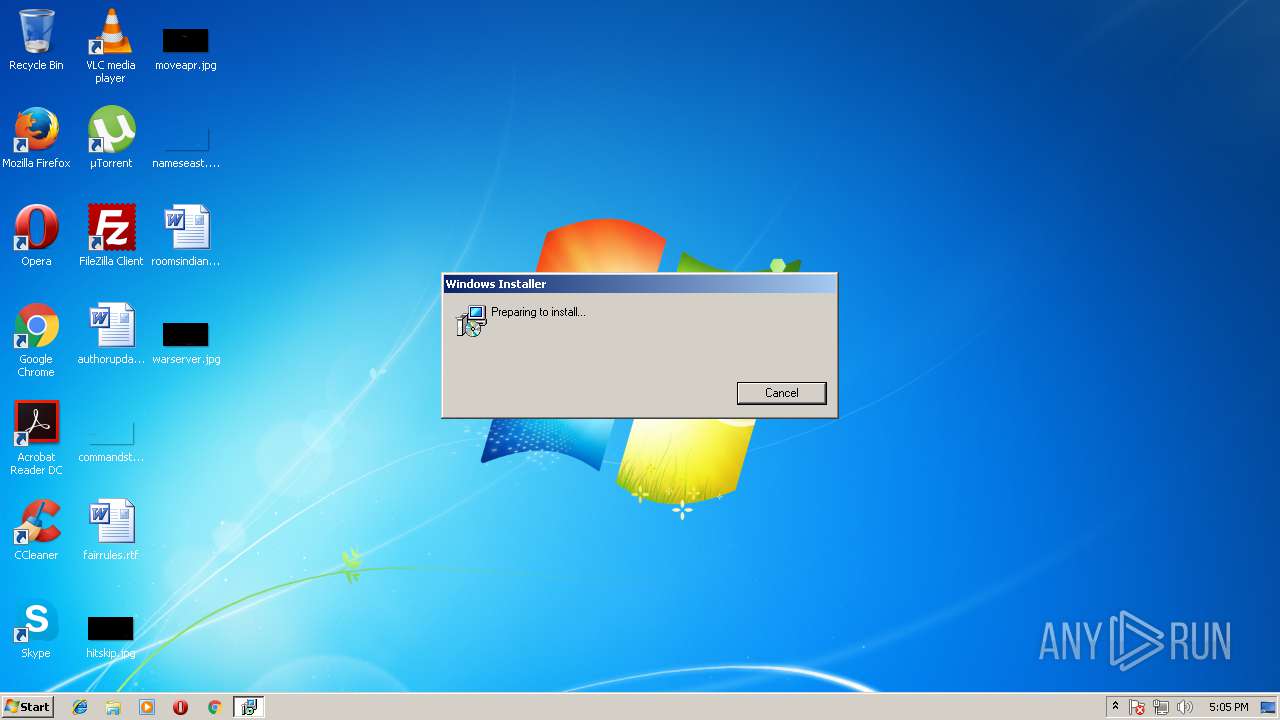
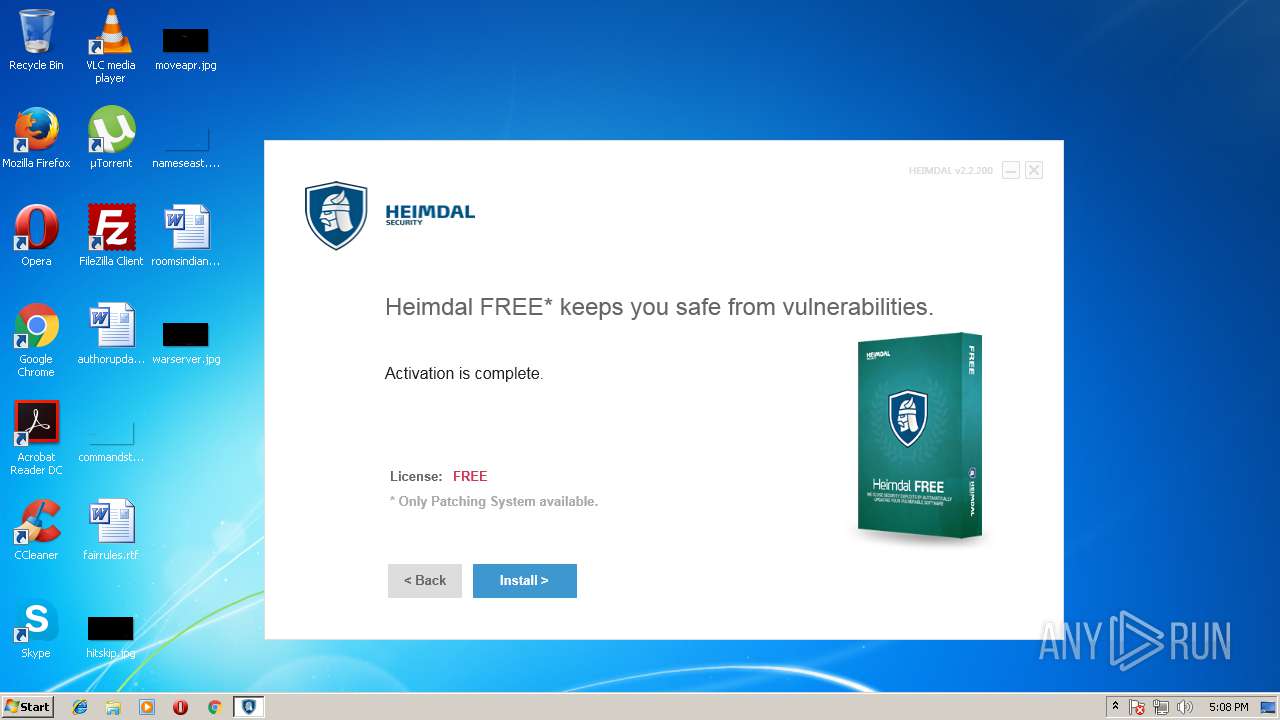
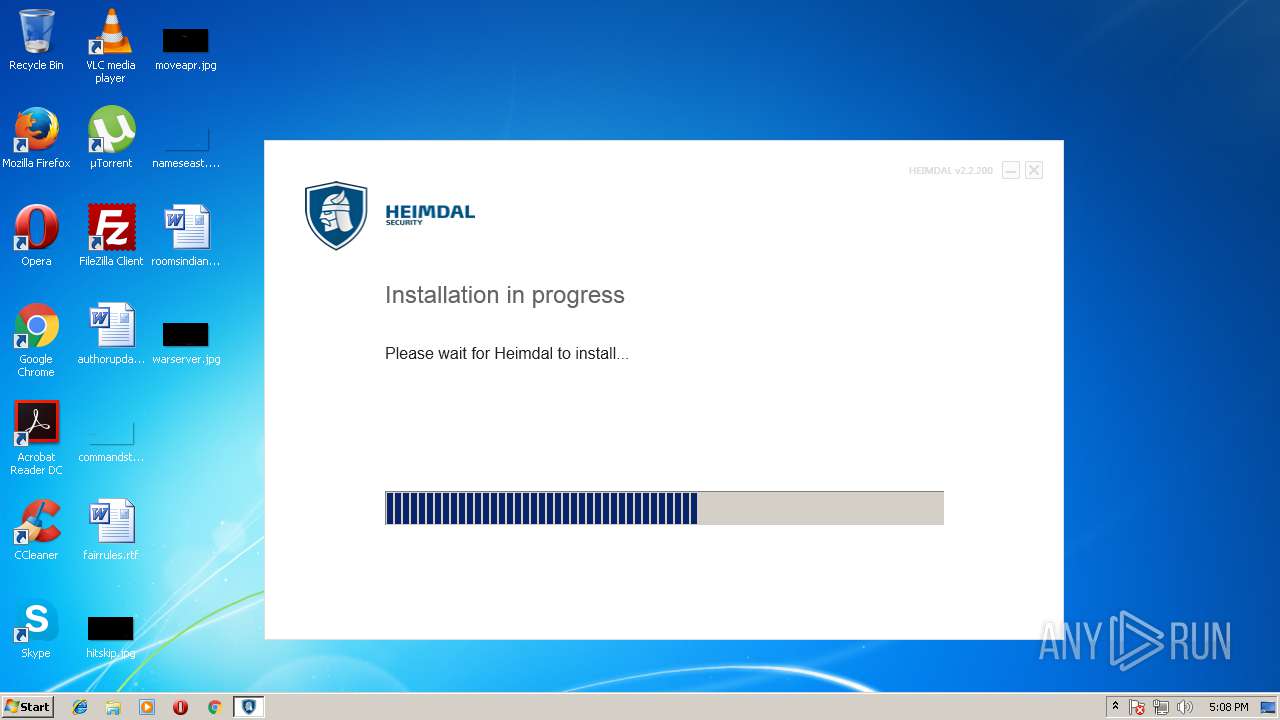
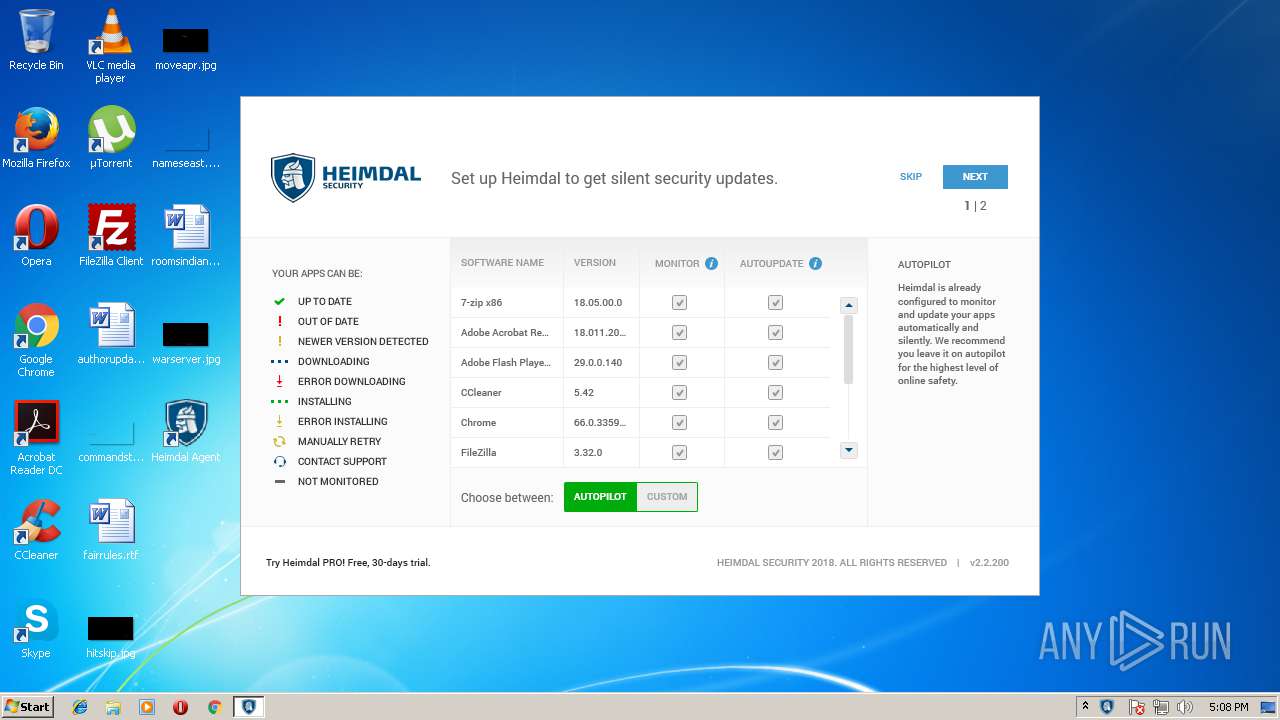
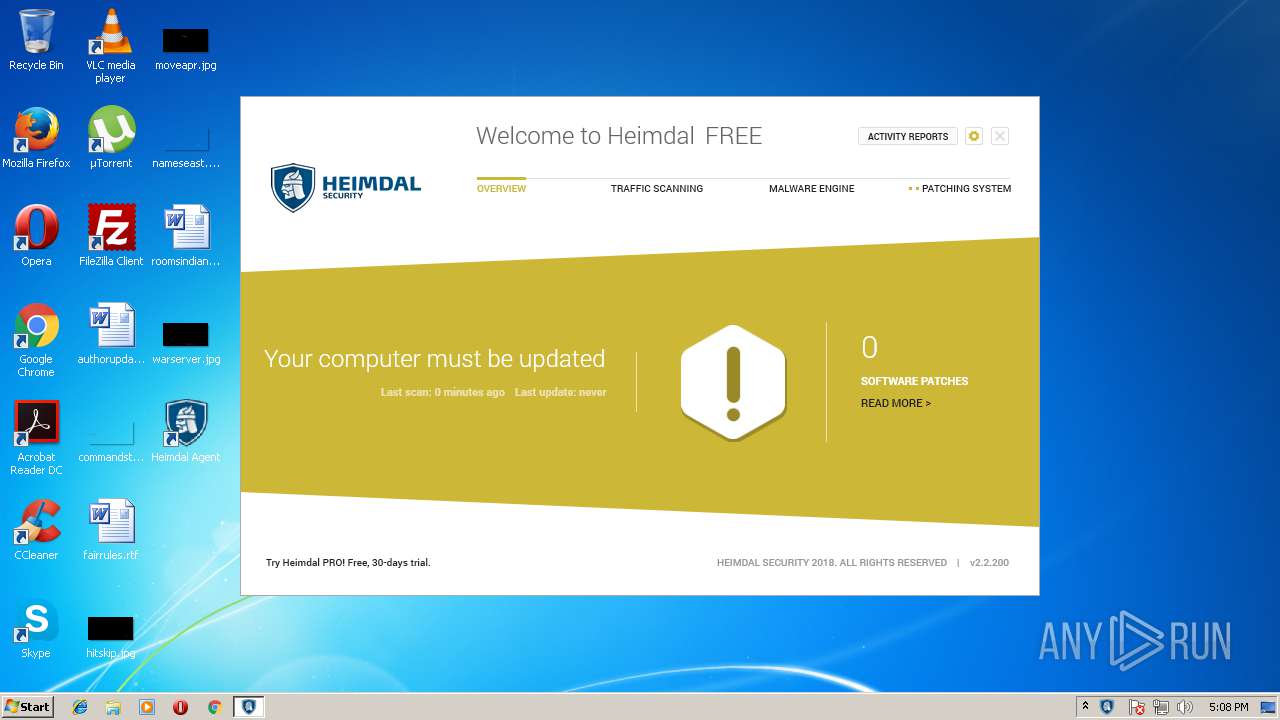
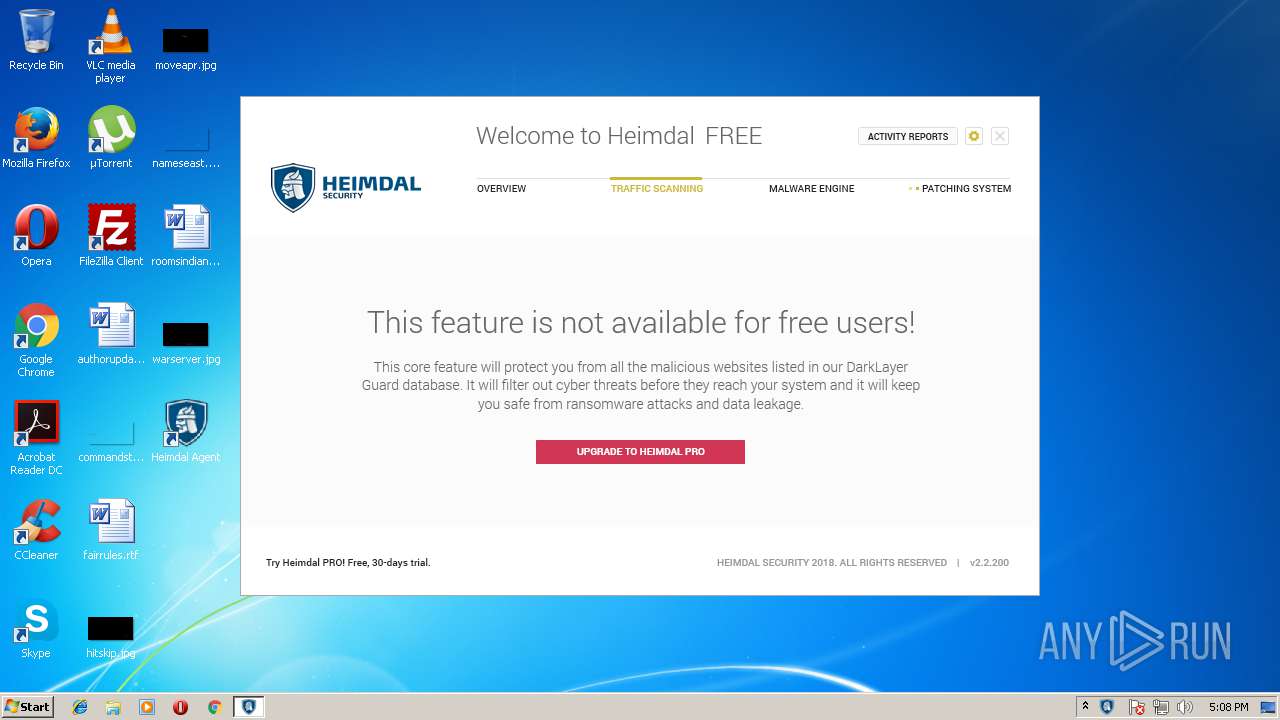
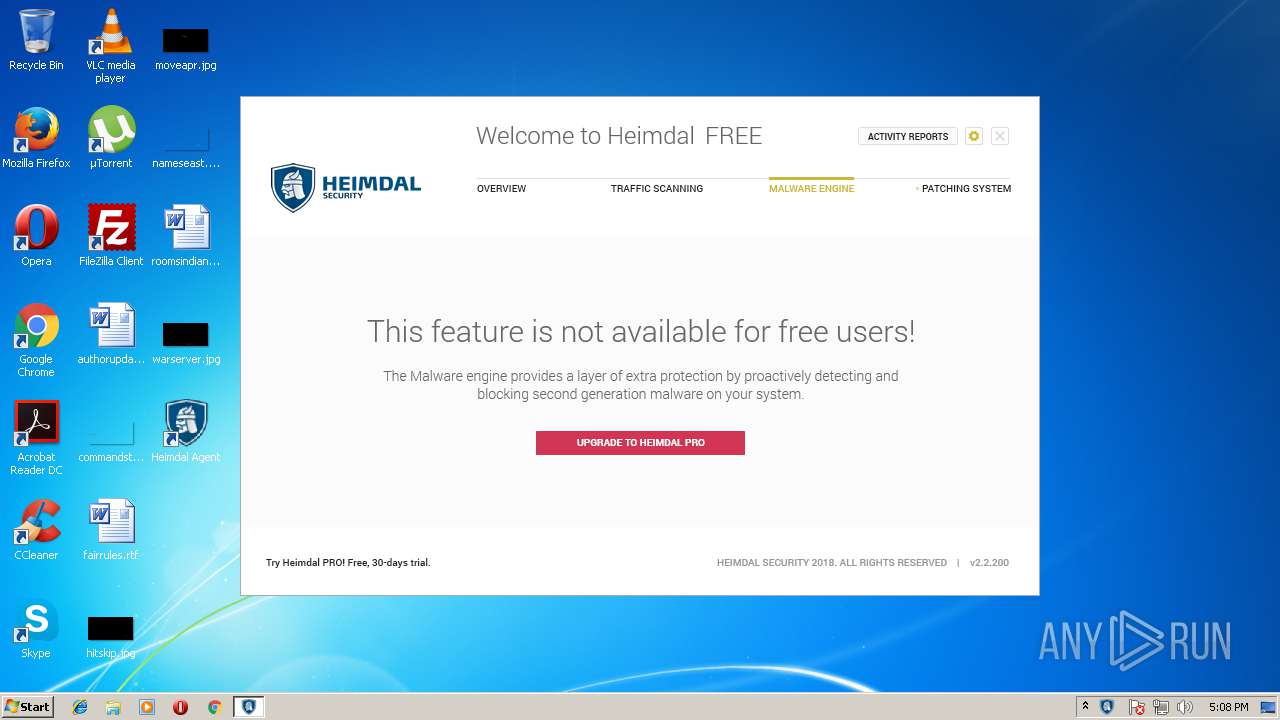
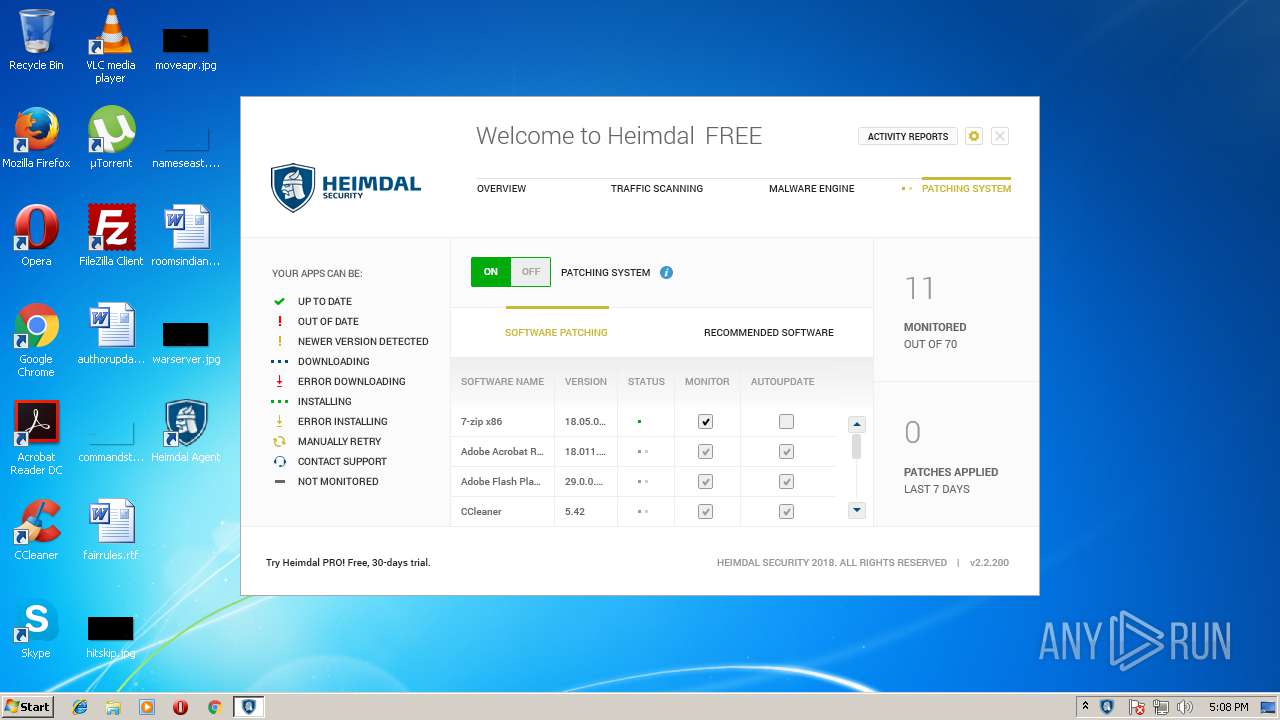
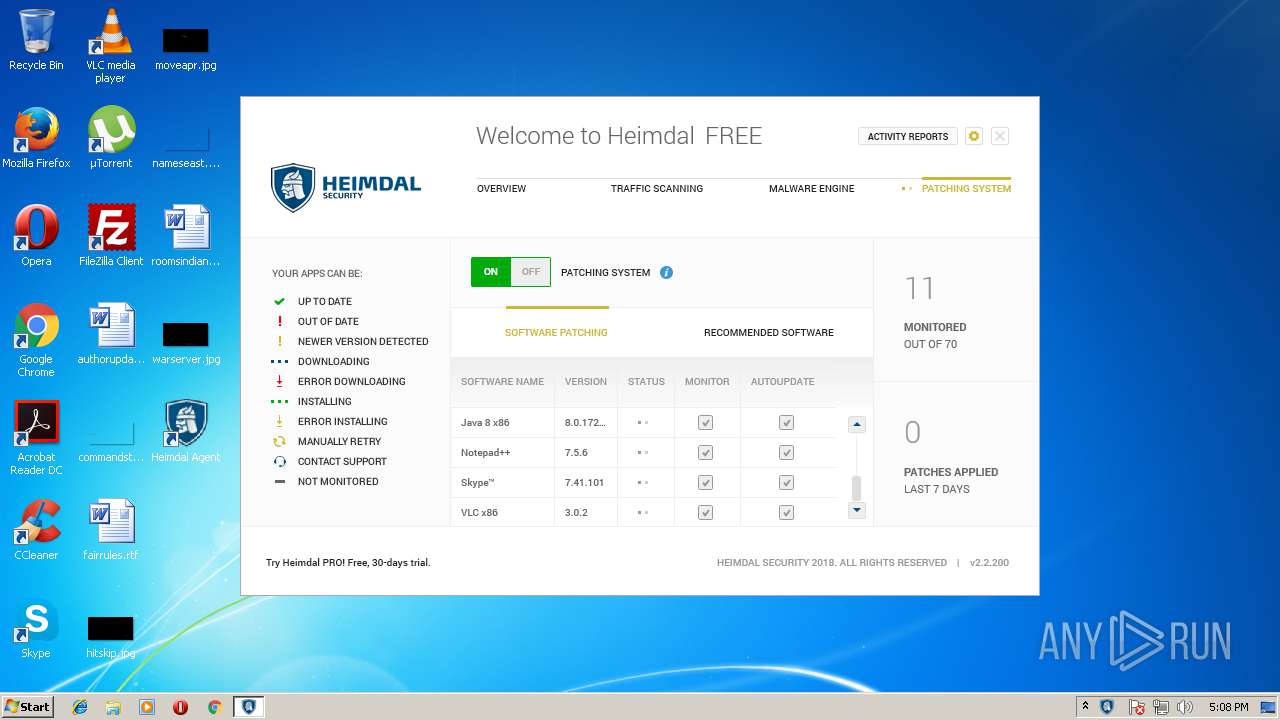
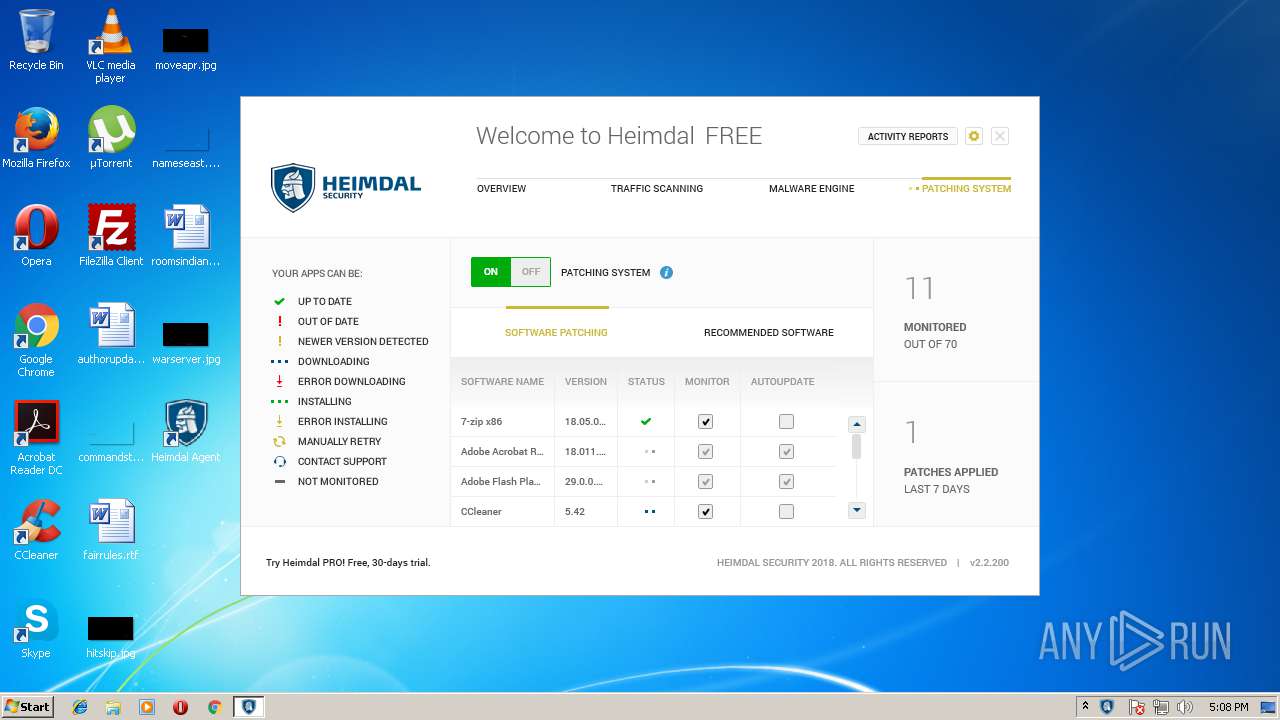
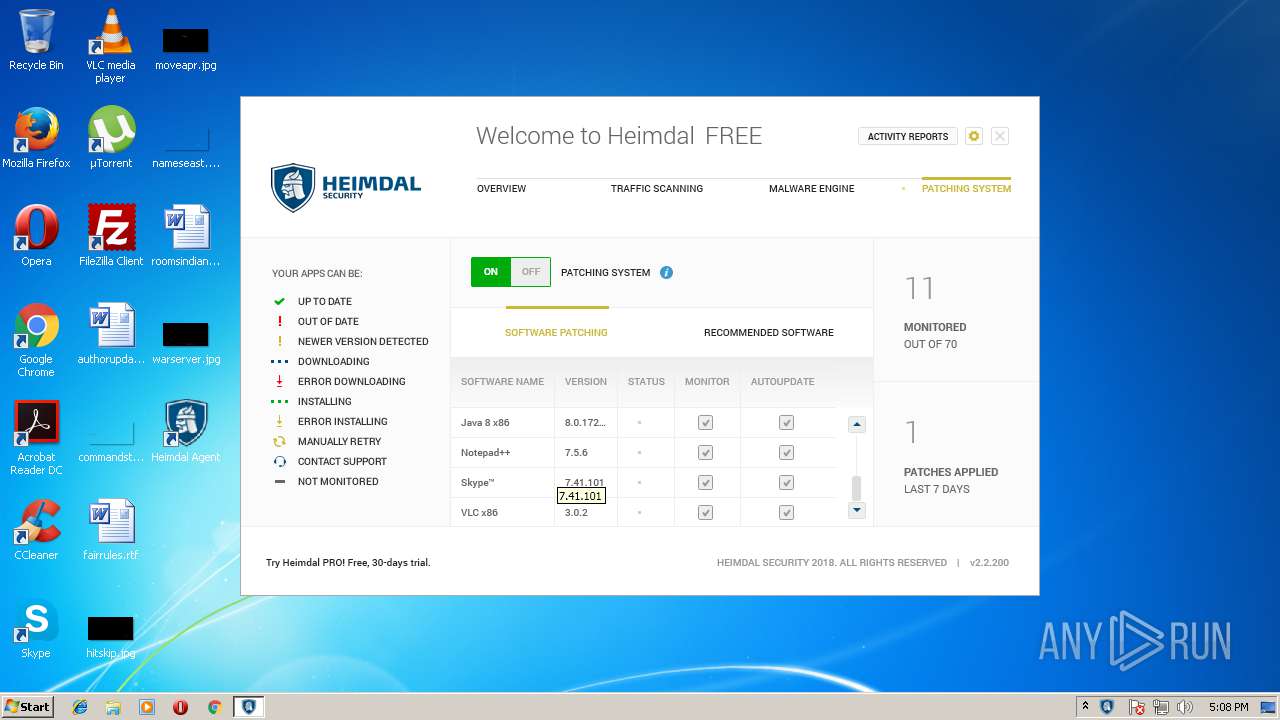
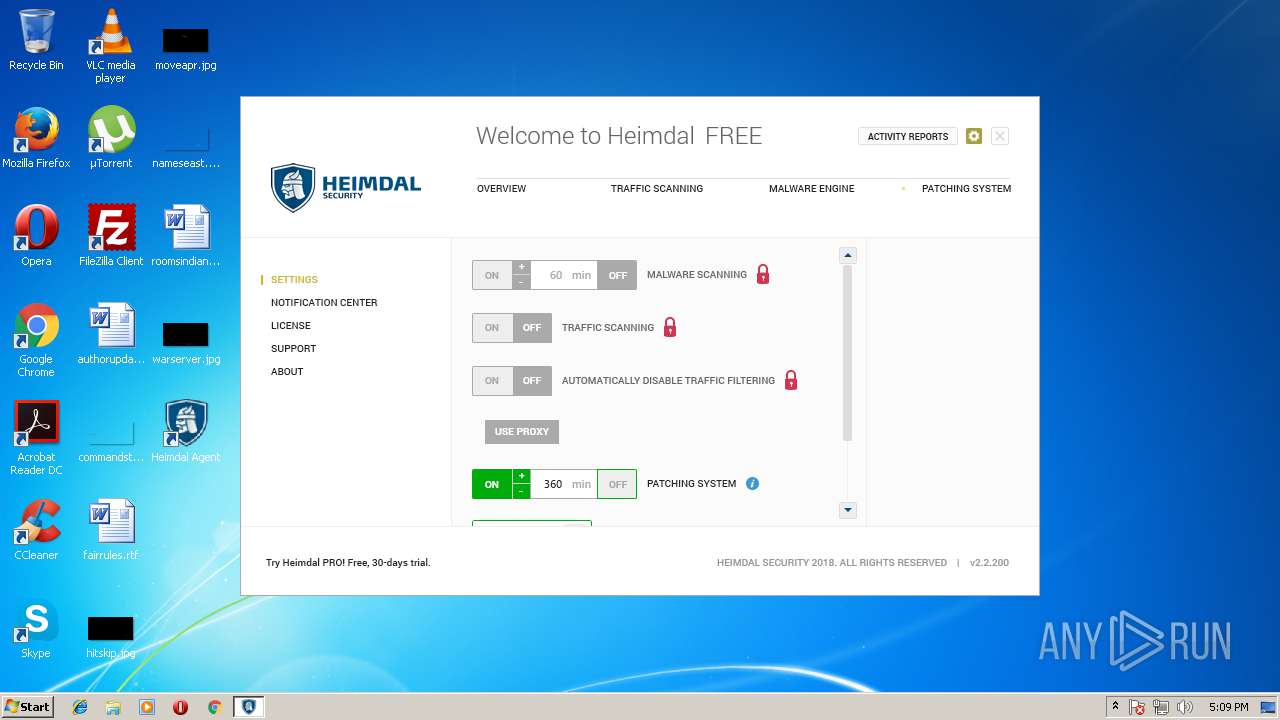
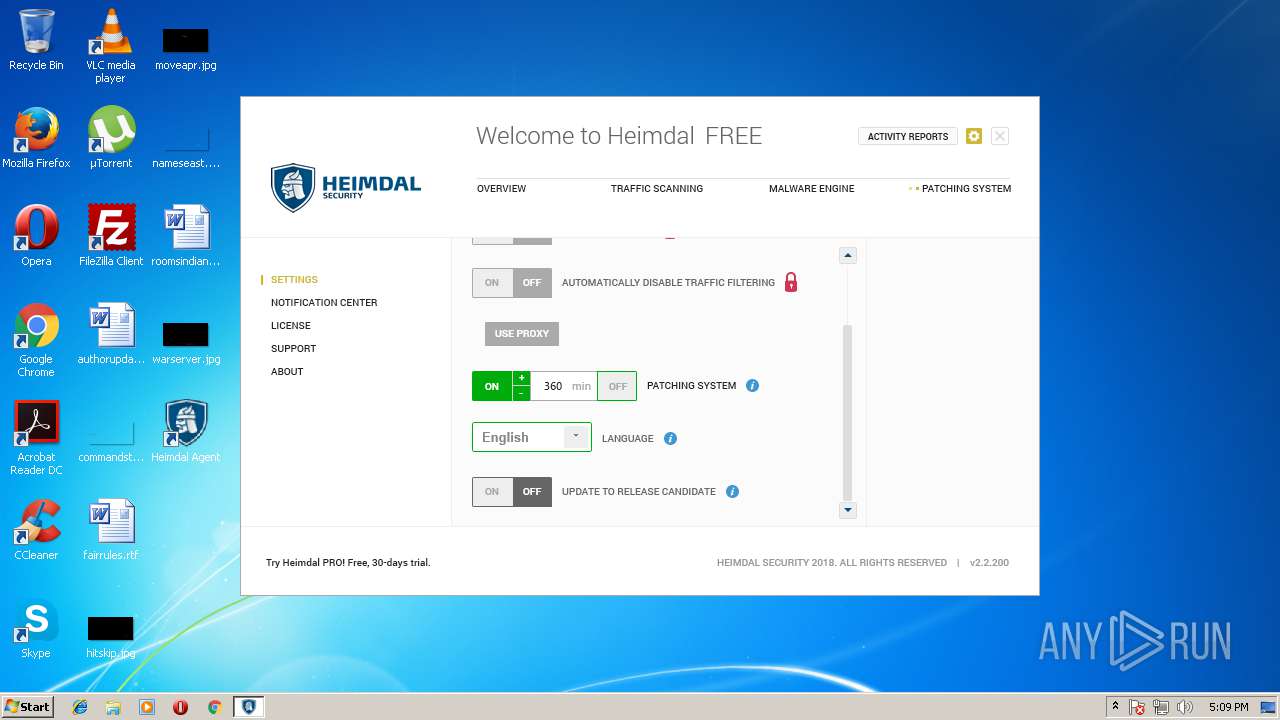
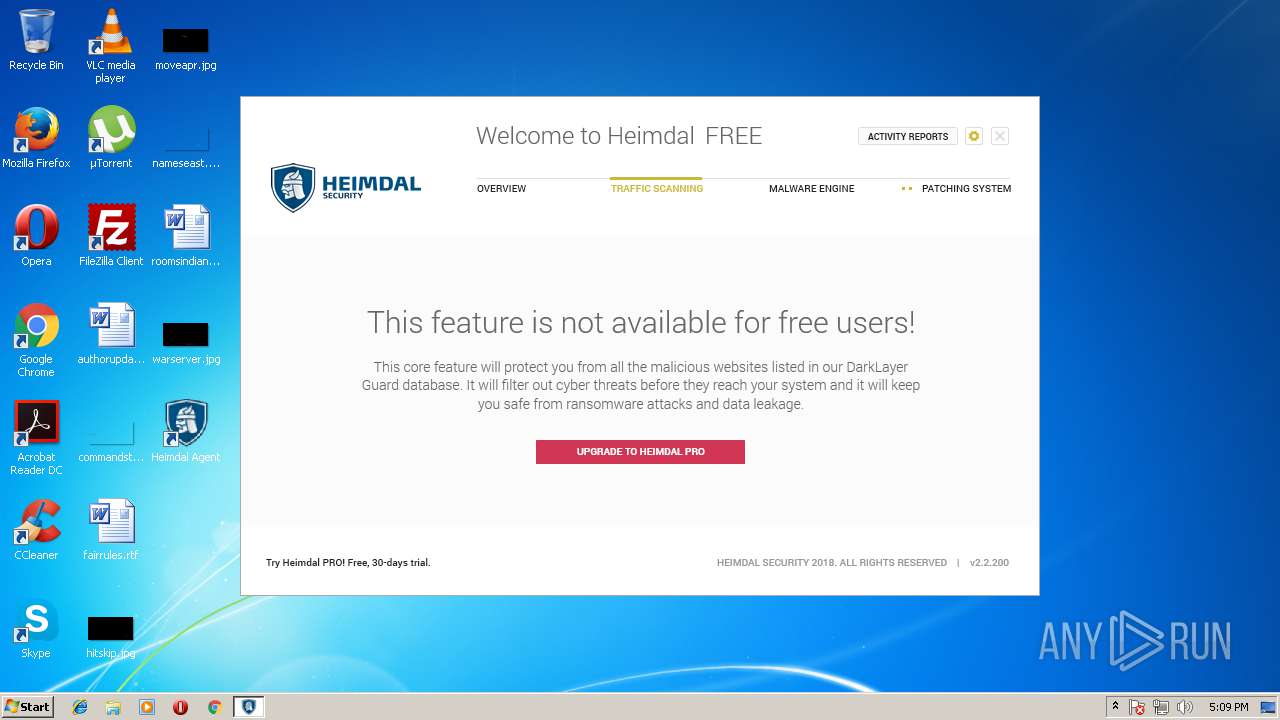
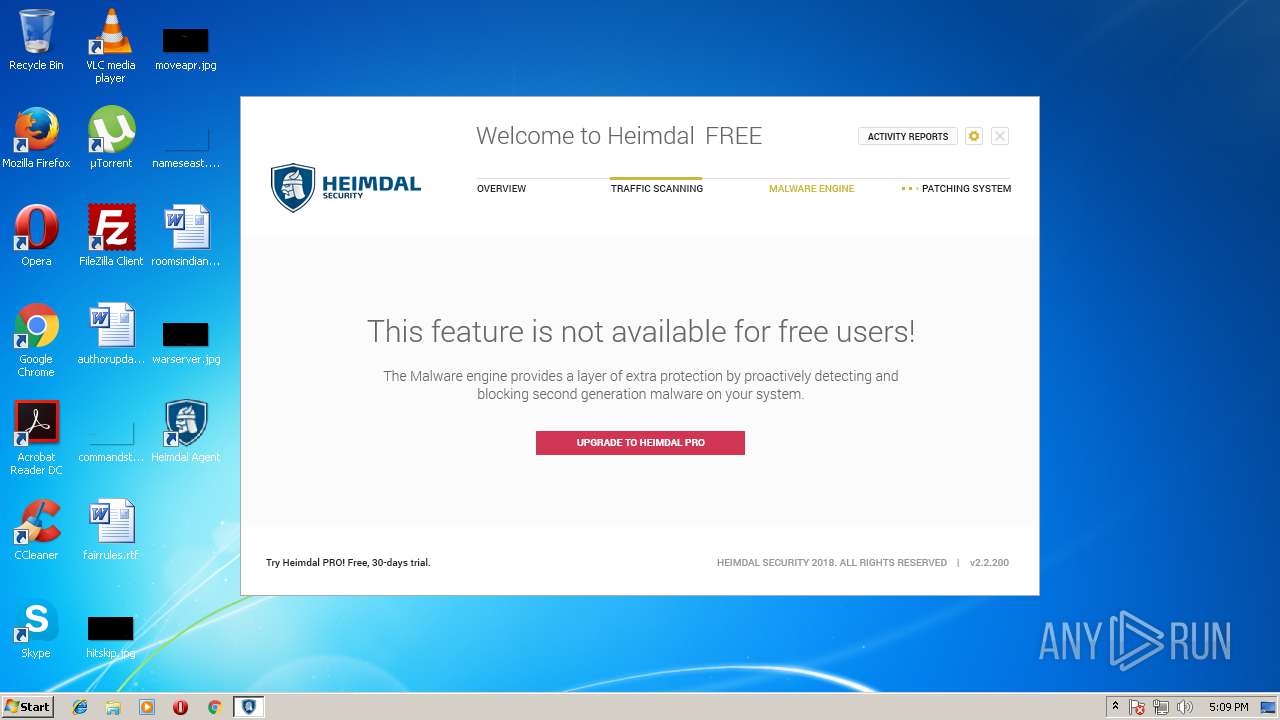
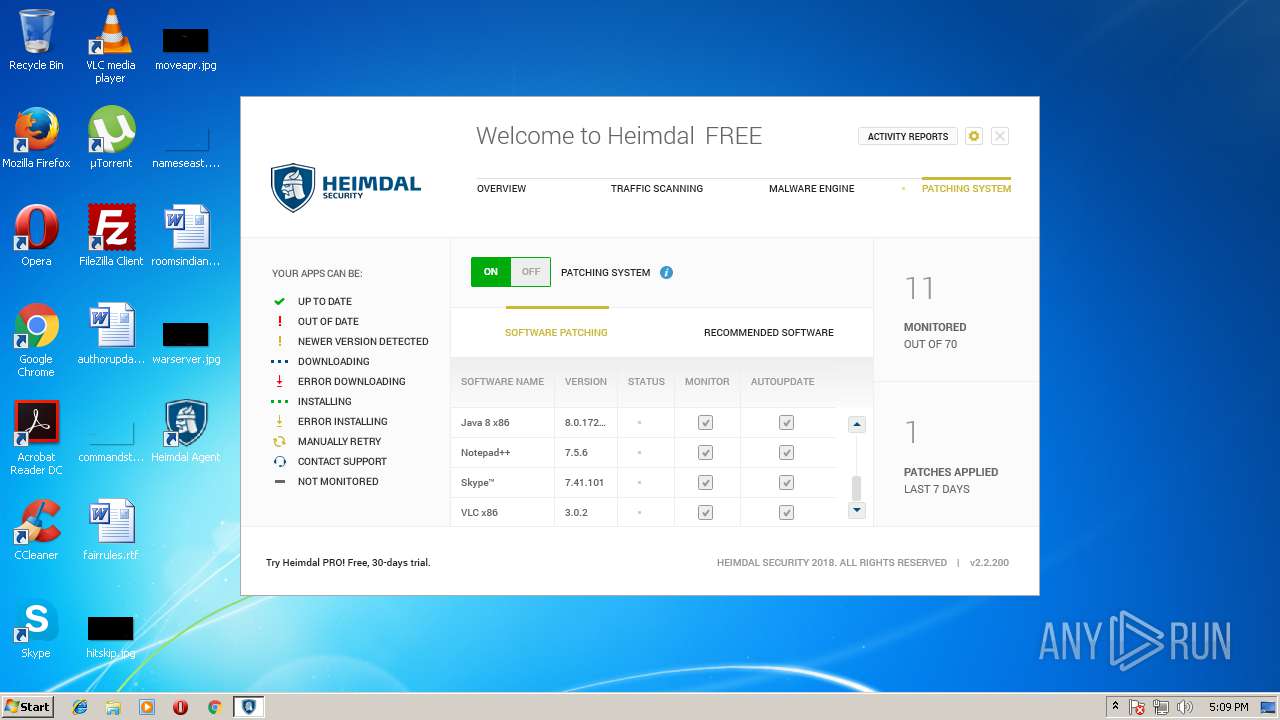
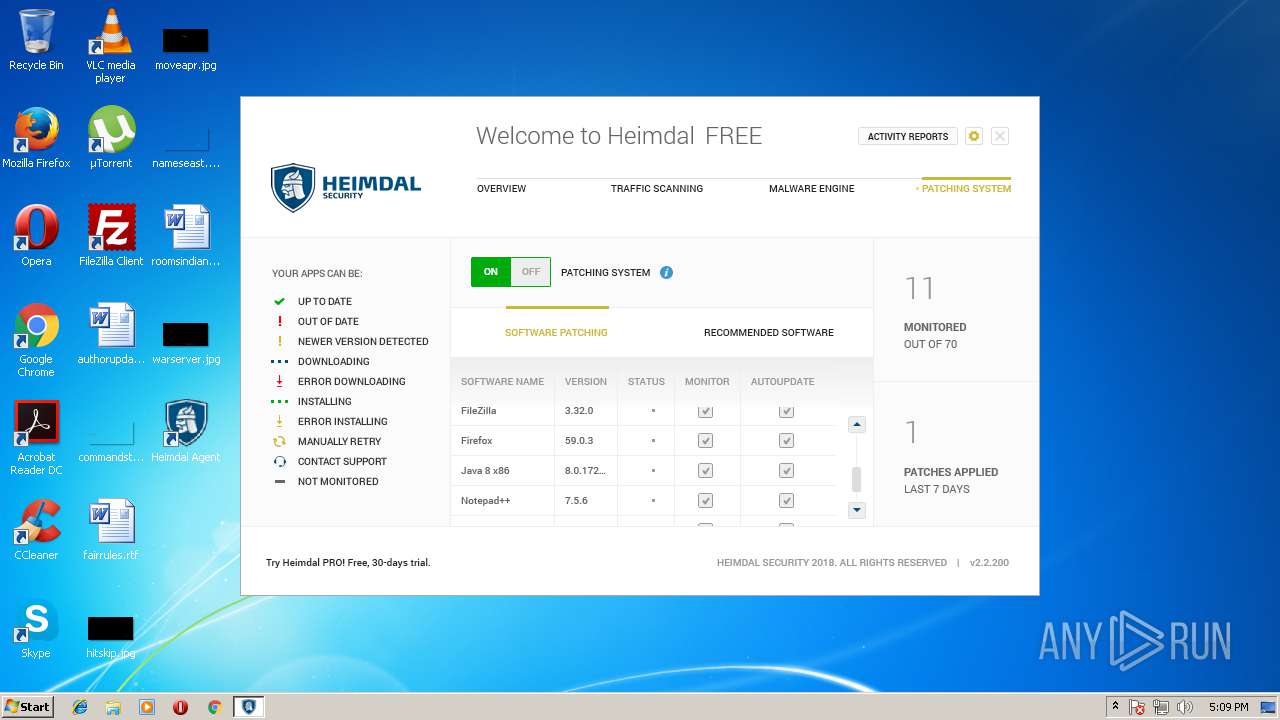
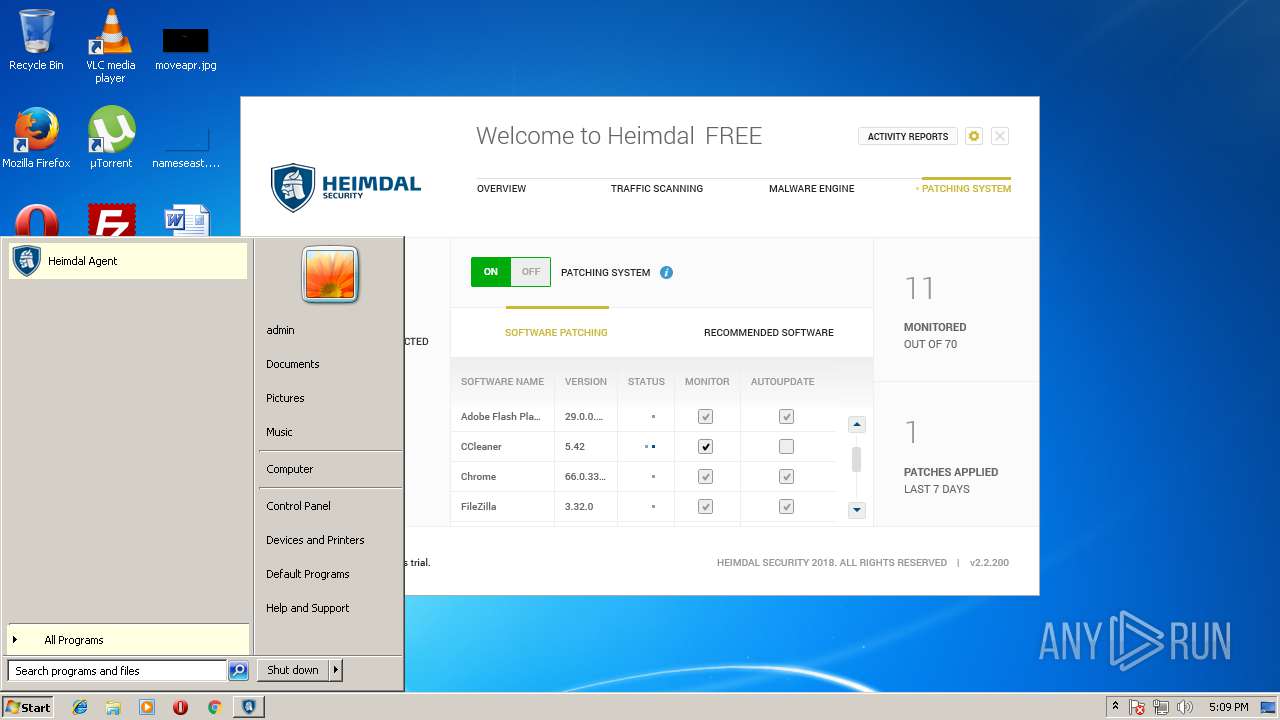
| download: | Heimdal.SetupLauncher.exe |
| Full analysis: | https://app.any.run/tasks/d5ffbe8d-0b98-4e49-b9f1-0b6e8aea7ce8 |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2018, 16:04:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 9FE1E5AC8A0D422AA2AC9897571E3597 |
| SHA1: | 5061201A60C27F50EAD8B1E6A6B3417AA58FAD35 |
| SHA256: | 6739506BB38552E8C659B2E50D38E487E626F4AE405943D3CA1730A9BEC8B12C |
| SSDEEP: | 24576:sILyZ10wUqKXtVCKb/lYk5omuhzBhx/e/bqP12NEUsQcE2u0:zLyGn1b/lYkim+P/Ubq92Nl2J |
MALICIOUS
Changes settings of System certificates
- Heimdal.SetupLauncher.exe (PID: 2800)
- msiexec.exe (PID: 2920)
- Heimdal.ClientHost.exe (PID: 3444)
- heimdal.wizard.exe (PID: 3980)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 2580)
- cmd.exe (PID: 2864)
- cmd.exe (PID: 2936)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 2880)
- cmd.exe (PID: 3036)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 1532)
- cmd.exe (PID: 596)
- cmd.exe (PID: 2628)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 4092)
- cmd.exe (PID: 2312)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 4064)
Loads the Task Scheduler COM API
- MsiExec.exe (PID: 3160)
- software_reporter_tool.exe (PID: 3464)
Application was dropped or rewritten from another process
- heimdal.wizard.exe (PID: 3980)
- v1Extract.exe (PID: 3008)
- Heimdal.ClientHost.exe (PID: 3444)
- Heimdal.AgentLoader.exe (PID: 3120)
- Heimdal.Agent.exe (PID: 360)
- Heimdal.UptimeChecker.exe (PID: 3556)
Application loaded dropped or rewritten executable
- heimdal.wizard.exe (PID: 3980)
- Heimdal.UptimeChecker.exe (PID: 3556)
- Heimdal.ClientHost.exe (PID: 3444)
Changes the autorun value in the registry
- heimdal.wizard.exe (PID: 3980)
SUSPICIOUS
Creates files in the program directory
- Heimdal.SetupLauncher.exe (PID: 2912)
- Heimdal.SetupLauncher.exe (PID: 2800)
- Heimdal.UptimeChecker.exe (PID: 3556)
- Heimdal.ClientHost.exe (PID: 3444)
- heimdal.wizard.exe (PID: 3980)
Application launched itself
- Heimdal.SetupLauncher.exe (PID: 2912)
- software_reporter_tool.exe (PID: 3464)
Searches for installed software
- Heimdal.SetupLauncher.exe (PID: 2800)
- Heimdal.ClientHost.exe (PID: 3444)
Adds / modifies Windows certificates
- Heimdal.SetupLauncher.exe (PID: 2800)
- msiexec.exe (PID: 2920)
- Heimdal.ClientHost.exe (PID: 3444)
Starts Microsoft Installer
- Heimdal.SetupLauncher.exe (PID: 2800)
Creates files in the Windows directory
- MsiExec.exe (PID: 3160)
Starts CMD.EXE for commands execution
- heimdal.wizard.exe (PID: 3980)
Creates or modifies windows services
- Heimdal.UptimeChecker.exe (PID: 3556)
- Heimdal.ClientHost.exe (PID: 3444)
Starts SC.EXE for service management
- heimdal.wizard.exe (PID: 3980)
INFO
Loads the .NET runtime environment
- Heimdal.SetupLauncher.exe (PID: 2912)
- Heimdal.SetupLauncher.exe (PID: 2800)
- heimdal.wizard.exe (PID: 3980)
- MsiExec.exe (PID: 3160)
- v1Extract.exe (PID: 3008)
- Heimdal.UptimeChecker.exe (PID: 3556)
- Heimdal.ClientHost.exe (PID: 3444)
- Heimdal.AgentLoader.exe (PID: 3120)
- Heimdal.Agent.exe (PID: 360)
Reads settings of System Certificates
- Heimdal.SetupLauncher.exe (PID: 2800)
- DrvInst.exe (PID: 2416)
- Heimdal.ClientHost.exe (PID: 3444)
- heimdal.wizard.exe (PID: 3980)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2716)
Dropped object may contain URL's
- msiexec.exe (PID: 2920)
- MsiExec.exe (PID: 3160)
- chrome.exe (PID: 760)
- msiexec.exe (PID: 2724)
- Heimdal.ClientHost.exe (PID: 3444)
- heimdal.wizard.exe (PID: 3980)
Creates or modifies windows services
- msiexec.exe (PID: 2724)
- vssvc.exe (PID: 2716)
Creates files in the program directory
- MsiExec.exe (PID: 3160)
- msiexec.exe (PID: 2724)
Application launched itself
- msiexec.exe (PID: 2724)
- chrome.exe (PID: 760)
Creates a software uninstall entry
- msiexec.exe (PID: 2724)
Application loaded dropped or rewritten executable
- MsiExec.exe (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:02:03 15:09:04+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1378816 |
| InitializedDataSize: | 96768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x17008a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.14.3000 |
| ProductVersionNumber: | 2.2.14.3000 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Heimdal Security |
| CompanyName: | Heimdal Security |
| FileDescription: | Heimdal.SetupLauncher |
| FileVersion: | 2.2.14.3000 |
| InternalName: | Heimdal.SetupLauncher.exe |
| LegalCopyright: | Copyright © 2015-2017 |
| LegalTrademarks: | - |
| OriginalFileName: | Heimdal.SetupLauncher.exe |
| ProductName: | Heimdal.SetupLauncher |
| ProductVersion: | 2.2.14.3000 |
| AssemblyVersion: | 2.2.14.3000 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Feb-2017 14:09:04 |
| Comments: | Heimdal Security |
| CompanyName: | Heimdal Security |
| FileDescription: | Heimdal.SetupLauncher |
| FileVersion: | 2.2.14.3000 |
| InternalName: | Heimdal.SetupLauncher.exe |
| LegalCopyright: | Copyright © 2015-2017 |
| LegalTrademarks: | - |
| OriginalFilename: | Heimdal.SetupLauncher.exe |
| ProductName: | Heimdal.SetupLauncher |
| ProductVersion: | 2.2.14.3000 |
| Assembly Version: | 2.2.14.3000 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 03-Feb-2017 14:09:04 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
|.b,2A\x03o\xac\x10\x01 | 0x00002000 | 0x000110AC | 0x00011200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99752 |
.text | 0x00014000 | 0x00150630 | 0x00150800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.27724 |
.rsrc | 0x00166000 | 0x00006568 | 0x00006600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.5887 |
.reloc | 0x0016E000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0815394 |
0x00170000 | 0x00000090 | 0x00000200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 2.56486 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.56072 | 4136 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.70652 | 2344 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 5.89801 | 1064 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.48187 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
113
Monitored processes
56
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | netsh http delete iplisten ipaddress=127.0.0.101 | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 360 | "C:\Program Files\Heimdal\Heimdal.Agent.exe" | C:\Program Files\Heimdal\Heimdal.Agent.exe | — | Heimdal.AgentLoader.exe | |||||||||||
User: SYSTEM Company: Heimdal Security Integrity Level: SYSTEM Description: Heimdal.Agent Exit code: 0 Version: 2.2.200.3000 Modules
| |||||||||||||||
| 596 | "cmd" /C netsh http delete iplisten ipaddress=127.0.0.102 | C:\Windows\system32\cmd.exe | — | heimdal.wizard.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | explorer.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1612,13490432865428416893,4985161633262093687,131072 --service-pipe-token=38AC37415F80C605C7383704B8B74CB1 --lang=en-US --disable-client-side-phishing-detection --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=38AC37415F80C605C7383704B8B74CB1 --renderer-client-id=4 --mojo-platform-channel-handle=1624 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1532 | "cmd" /C netsh http delete sslcert ipport=127.5.5.104:443 | C:\Windows\system32\cmd.exe | — | heimdal.wizard.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=61.0.3163.100 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x685e7d7c,0x685e7da4,0x685e7d8c | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 2312 | "cmd" /C netsh http delete iplisten ipaddress=127.0.0.104 | C:\Windows\system32\cmd.exe | — | heimdal.wizard.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2356 | "cmd" /C netsh http delete iplisten ipaddress=127.5.5.103 | C:\Windows\system32\cmd.exe | — | heimdal.wizard.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2416 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot43" "" "" "6bb2f14fb" "00000000" "0000039C" "000005DC" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 511
Read events
1 940
Write events
1 552
Delete events
19
Modification events
| (PID) Process: | (2912) Heimdal.SetupLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2912) Heimdal.SetupLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Heimdal.SetupLauncher.exe | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2800) Heimdal.SetupLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Heimdal_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
119
Suspicious files
49
Text files
456
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2800 | Heimdal.SetupLauncher.exe | C:\ProgramData\Heimdal Security\Patching\Downloads\b34471c5-427f-4a04-b496-4ab6f16f86da.tmp | — | |
MD5:— | SHA256:— | |||
| 2800 | Heimdal.SetupLauncher.exe | C:\ProgramData\Heimdal Security\Patching\Downloads\3abb7acb-e3d9-4082-b470-2b8174a023e7.msi | — | |
MD5:— | SHA256:— | |||
| 2920 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Cab252D.tmp | — | |
MD5:— | SHA256:— | |||
| 2920 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Tar252E.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2724 | msiexec.exe | C:\Windows\Installer\104fd7.msi | — | |
MD5:— | SHA256:— | |||
| 2724 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Cab50C2.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Tar50C3.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | msiexec.exe | C:\Windows\Installer\MSI5299.tmp | — | |
MD5:— | SHA256:— | |||
| 2724 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFD605AD85B844B0E1.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
33
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 301 | 104.27.153.38:80 | http://temp-mail.org/ | US | — | — | suspicious |
— | — | GET | 200 | 178.255.83.1:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEC58h8wOk0pS%2FpT9HLfNNK8%3D | GB | der | 727 b | whitelisted |
— | — | GET | — | 104.16.91.188:80 | http://crl.comodoca.com/COMODORSACodeSigningCA.crl | US | — | — | whitelisted |
— | — | GET | 200 | 178.255.83.1:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | GB | der | 471 b | whitelisted |
— | — | GET | 200 | 104.16.90.188:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | US | der | 1.37 Kb | whitelisted |
— | — | GET | 200 | 178.255.83.1:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSSdxXdG447ymkRNPVViULv3rkBzQQUKZFg%2F4pN%2Buv5pmq4z%2FnmS71JzhICEQCpBQ37NwdIoDRsrx5RLM5S | GB | der | 472 b | whitelisted |
— | — | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 52.4 Kb | whitelisted |
— | — | GET | 200 | 216.58.205.228:80 | http://www.google.com/ | US | html | 44.3 Kb | malicious |
— | — | GET | 200 | 216.58.205.228:80 | http://www.google.com/ | US | html | 44.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 216.58.205.228:80 | www.google.com | Google Inc. | US | whitelisted |
— | — | 168.63.113.52:443 | storage.heimdalsecurity.com | Microsoft Corporation | NL | whitelisted |
— | — | 104.16.90.188:80 | crt.comodoca.com | Cloudflare Inc | US | shared |
— | — | 178.255.83.1:80 | ocsp.usertrust.com | CCANET Limited | GB | unknown |
— | — | 104.16.91.188:80 | crt.comodoca.com | Cloudflare Inc | US | shared |
— | — | 172.217.22.99:443 | www.google.ru | Google Inc. | US | whitelisted |
— | — | 216.58.205.228:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 104.27.153.38:443 | temp-mail.org | Cloudflare Inc | US | shared |
— | — | 104.27.153.38:80 | temp-mail.org | Cloudflare Inc | US | shared |
— | — | 178.250.2.74:443 | static.criteo.net | Criteo SA | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
storage.heimdalsecurity.com |
| suspicious |
crt.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
crl.comodoca.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.ru |
| whitelisted |
temp-mail.org |
| suspicious |
go.ezoic.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET WEB_CLIENT SUSPICIOUS Possible automated connectivity check (www.google.com) |