| File name: | full.rar |
| Full analysis: | https://app.any.run/tasks/69daf30e-1737-44a1-b1e2-e99bfcf17f86 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 15:44:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2261AC2CC49822EAB3D1552570BA5DF1 |
| SHA1: | E243F1417E0F4E79DFB8D43738A9BFE086F11236 |
| SHA256: | 6734506F6E10895EDA9EA76C1BCC6FE42606E0538A705BE46B80C6A3E1EF7961 |
| SSDEEP: | 49152:9n/gwVnw0f2xr/z4rQN6e+PQ5NaGPs8y5xlJTaxQdR9Fwp:9/gr0f2xrD6e+sbPs8y5NaxQdR0 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 372)
Deletes shadow copies
- cmd.exe (PID: 1848)
- cmd.exe (PID: 1028)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 372)
Reads the Internet Settings
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
Reads settings of System Certificates
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
Starts a Microsoft application from unusual location
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2432)
Starts CMD.EXE for commands execution
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
Reads security settings of Internet Explorer
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
INFO
Manual execution by a user
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
- ZagreuS Decryptor.exe (PID: 2948)
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 372)
Checks supported languages
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
- ZagreuS Decryptor.exe (PID: 2948)
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
Reads the computer name
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
- ZagreuS Decryptor.exe (PID: 2948)
Reads the machine GUID from the registry
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
- ZagreuS Decryptor.exe (PID: 2948)
- cf4cba71fc6c3964520ae13dfca.exe (PID: 3044)
Reads Environment values
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
Disables trace logs
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
Reads the software policy settings
- ESCANOR RANSOMWARE 2022.exe (PID: 2396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1545592 |
| UncompressedSize: | 1681920 |
| OperatingSystem: | Win32 |
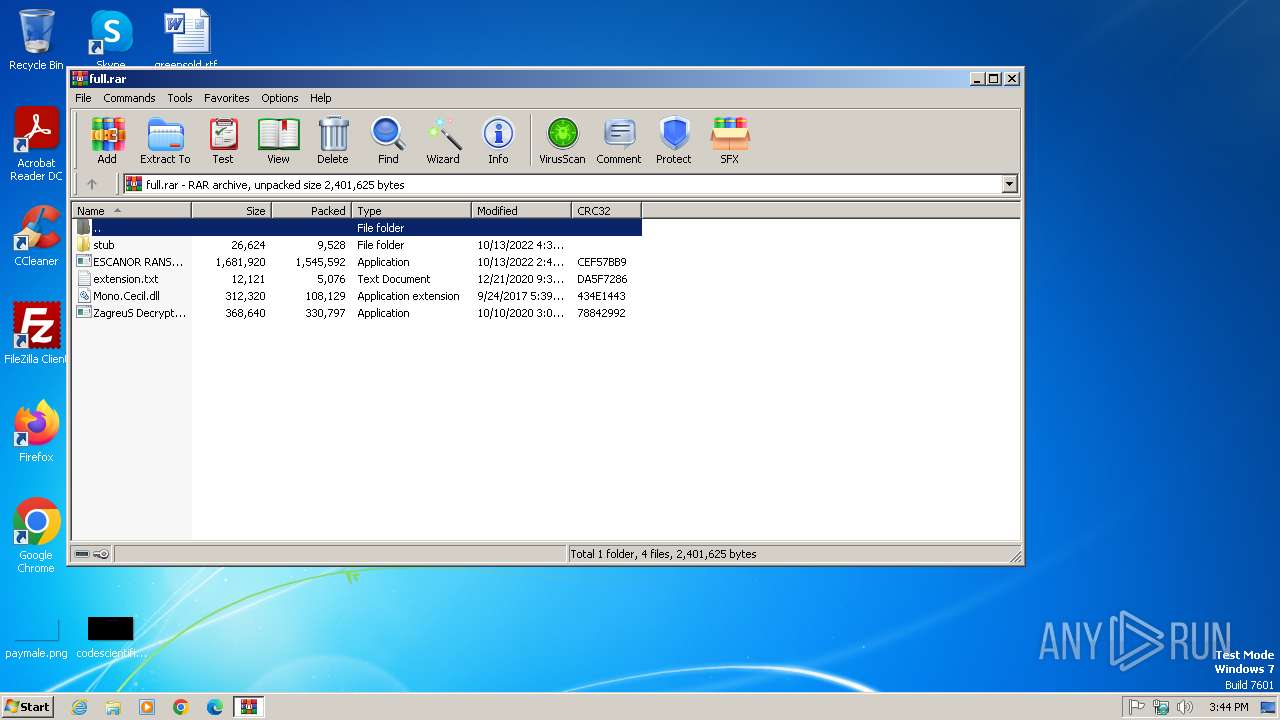
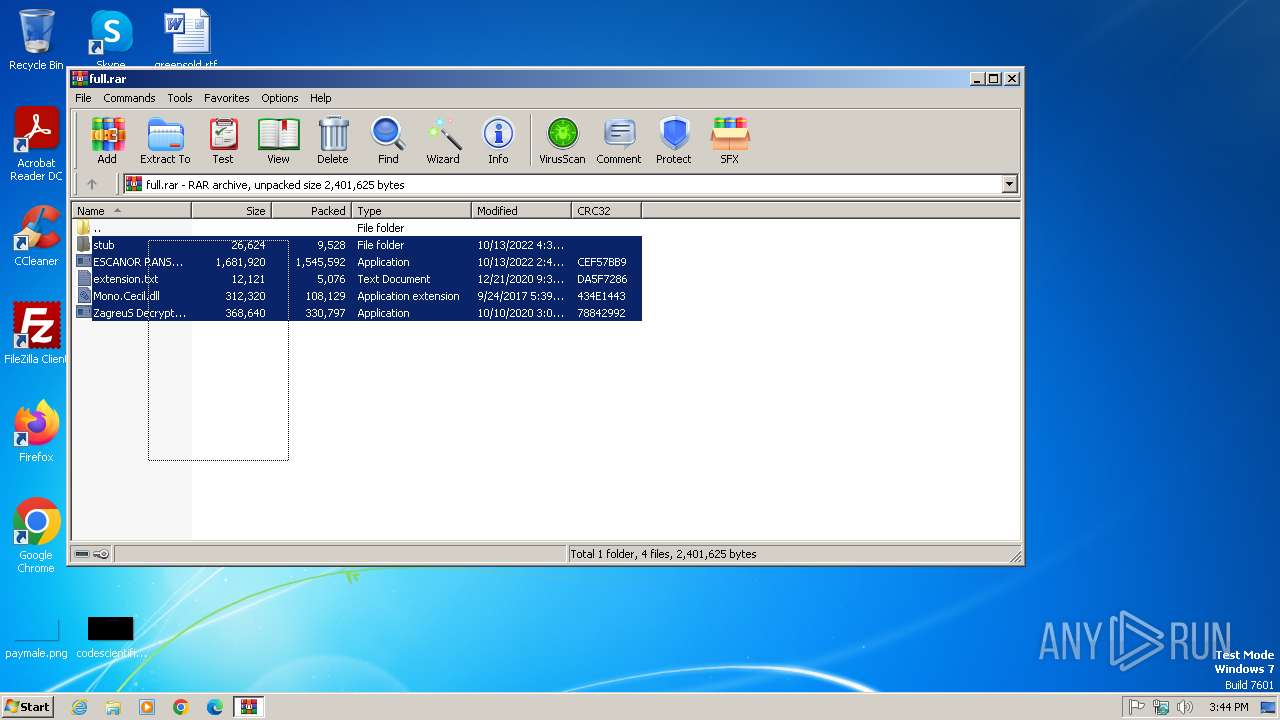
| ArchivedFileName: | ESCANOR RANSOMWARE 2022.exe |
Total processes
48
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\full.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1028 | "cmd.exe" /c vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\cmd.exe | — | cf4cba71fc6c3964520ae13dfca.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1848 | "cmd.exe" /c vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\cmd.exe | — | cf4cba71fc6c3964520ae13dfca.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2096 | C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
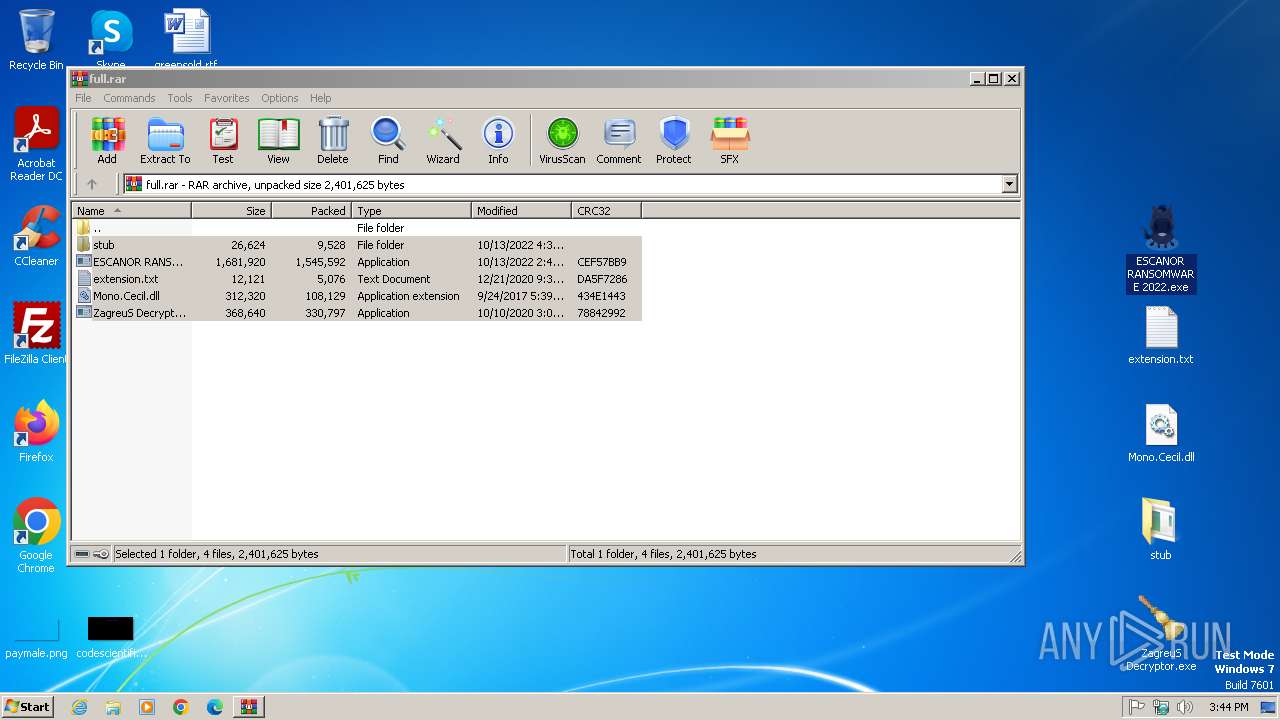
| 2396 | "C:\Users\admin\Desktop\ESCANOR RANSOMWARE 2022.exe" | C:\Users\admin\Desktop\ESCANOR RANSOMWARE 2022.exe | explorer.exe | ||||||||||||
User: admin Company: ZagreuS Corporation Integrity Level: MEDIUM Description: ZagreuS Builder Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\cmd.exe" C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 1 /f | C:\Windows\System32\cmd.exe | cf4cba71fc6c3964520ae13dfca.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2544 | vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2948 | "C:\Users\admin\Desktop\ZagreuS Decryptor.exe" | C:\Users\admin\Desktop\ZagreuS Decryptor.exe | — | explorer.exe | |||||||||||
User: admin Company: ZagreuS Corporation Integrity Level: MEDIUM Description: ZagreuS Decryptor Version: 1.0.0.1 Modules
| |||||||||||||||
| 3044 | "C:\Users\admin\Desktop\stub\cf4cba71fc6c3964520ae13dfca.exe" | C:\Users\admin\Desktop\stub\cf4cba71fc6c3964520ae13dfca.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
6 307
Read events
6 260
Write events
47
Delete events
0
Modification events
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\full.rar | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa372.37554\extension.txt | text | |
MD5:EFA5C35936E240B29DF8F18C62E905FF | SHA256:7C04FCE6A1013D817CFF34FF2D8169297E3131DA3C62C2FE90966866B230A82F | |||
| 372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa372.37554\ESCANOR RANSOMWARE 2022.exe | executable | |
MD5:7AA4935A205F3219A865BE20398BB12E | SHA256:3C9ED1D837CE7C26FCD52C0D6989218681B1A41050256D2BC6662B49255D727B | |||
| 372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa372.37554\stub\cf4cba71fc6c3964520ae13dfca.exe | executable | |
MD5:8DA804291C6513109E2134A21B2F3655 | SHA256:8133D4BBCFDBAFFDE87483C1D537359EA57136837AE42DE08A3C9D9F08AB988A | |||
| 372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa372.37554\ZagreuS Decryptor.exe | executable | |
MD5:9A34FD66797FD0F366CD47851EB8EAF0 | SHA256:E2F0EC0293882487DE6D2EC0795E92AD695588A7B0B9D2BA5173284BBE493FFD | |||
| 372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa372.37554\Mono.Cecil.dll | executable | |
MD5:851EC9D84343FBD089520D420348A902 | SHA256:CDADC26C09F869E21053EE1A0ACF3B2D11DF8EDD599FE9C377BD4D3CE1C9CDA9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2396 | ESCANOR RANSOMWARE 2022.exe | 172.67.19.24:443 | pastebin.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
pastebin.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |