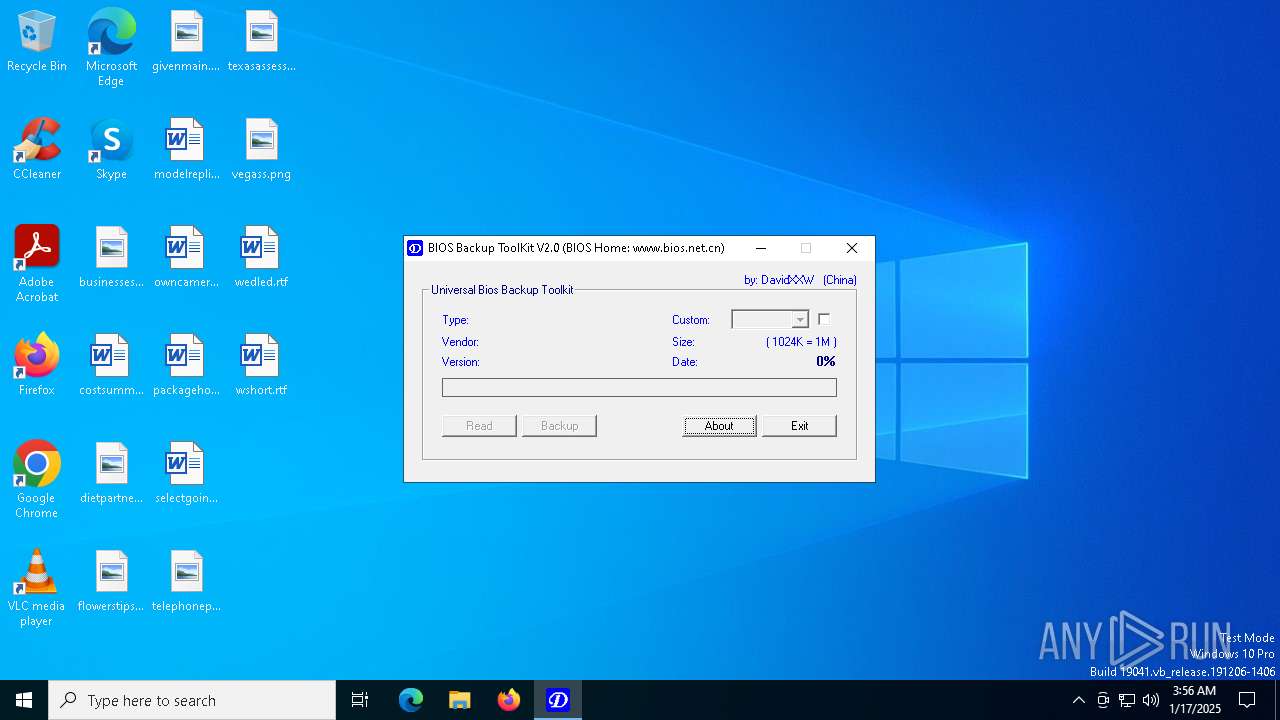
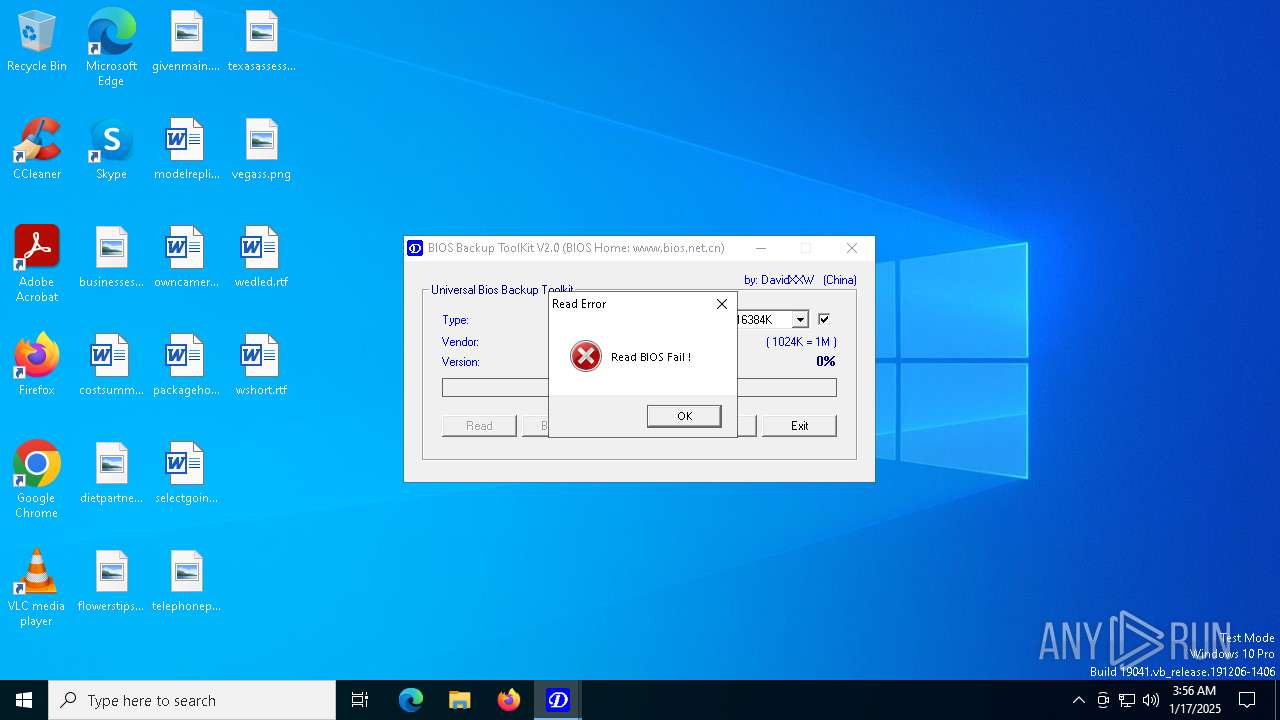
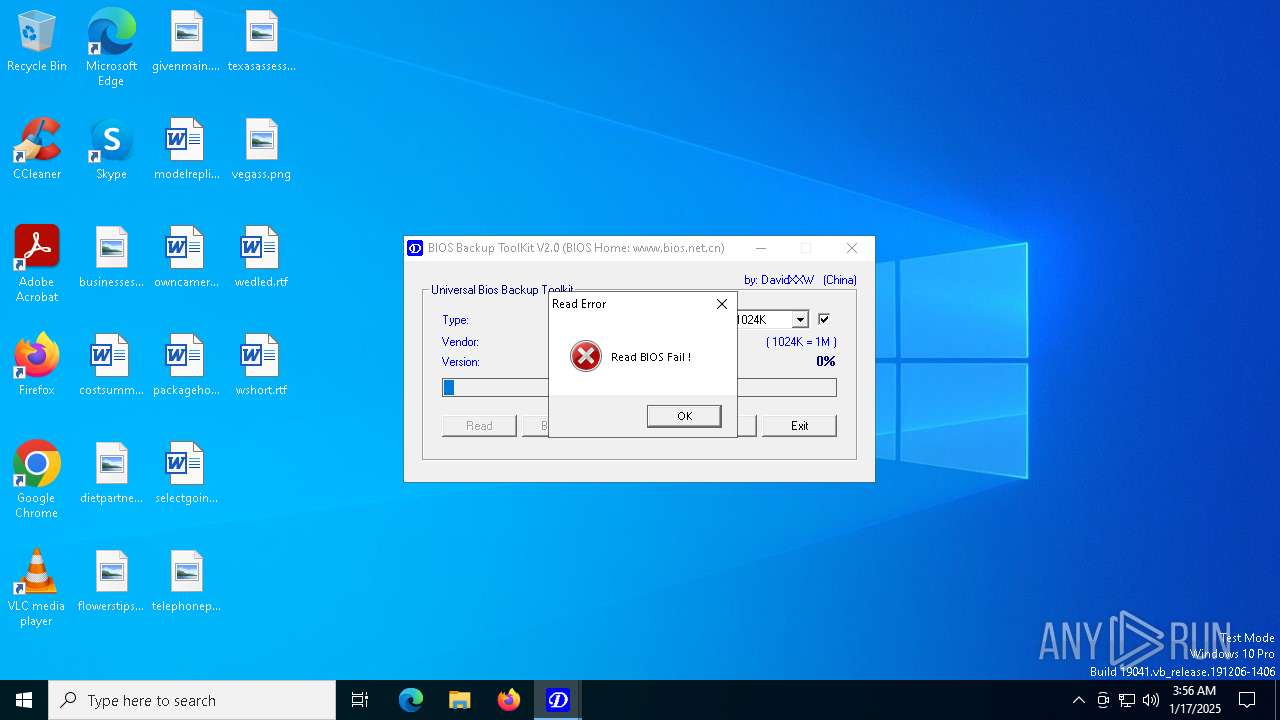
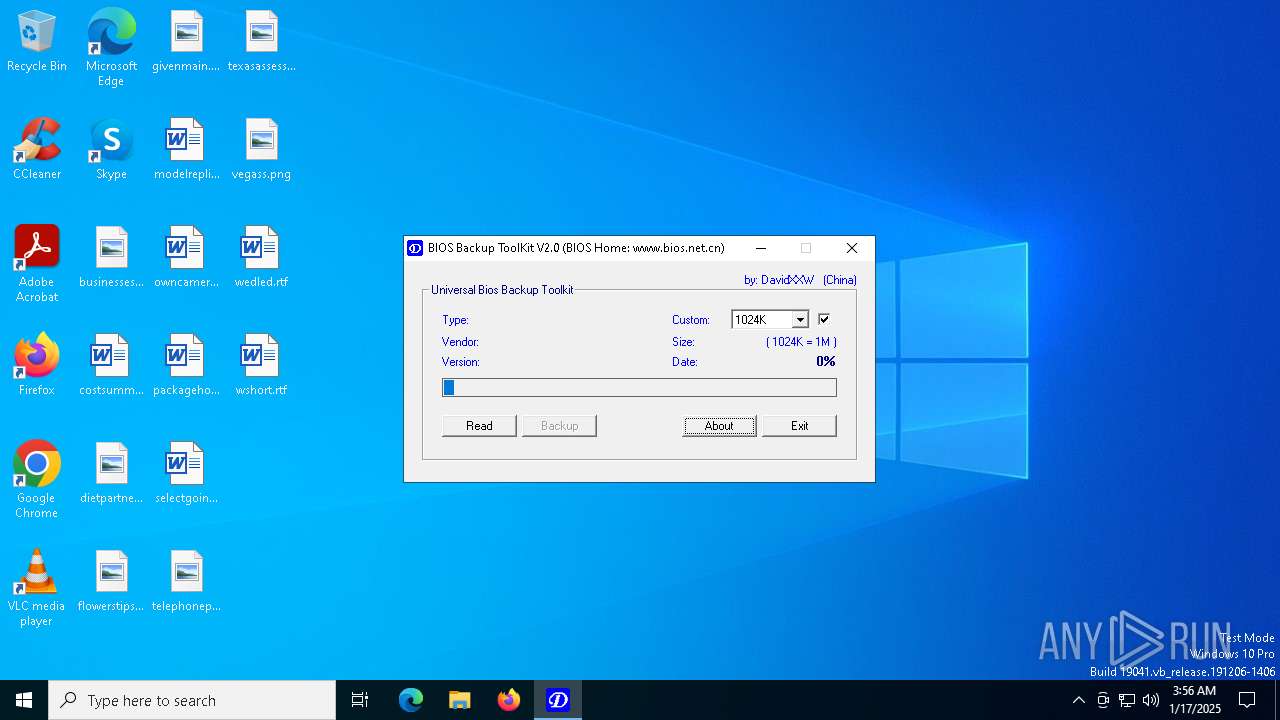
| File name: | Universal BIOS Backup ToolKit 2.0.exe |
| Full analysis: | https://app.any.run/tasks/8e5573d4-098b-414f-b1f8-55f02ea62a96 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 03:55:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | E20002DBA2F2129797400B4BBF5CACE7 |
| SHA1: | 0BED0F6320CF705AB454CE14DECC0A3FC6840337 |
| SHA256: | 672BC532799A091C2422F3676550B019CFF007F3EBBA05A4BA7222C9C810179B |
| SSDEEP: | 12288:mOJoScuuvTcgQ6HzAQJVtBPUmrjvEtoDvPDtTOVb/+PWFIgpi:m82cgQ8UmnPUmPSCvPxORFIt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
Drops a system driver (possible attempt to evade defenses)
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
There is functionality for sending ICMP (YARA)
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
There is functionality for taking screenshot (YARA)
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
INFO
The sample compiled with chinese language support
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
Checks supported languages
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
The sample compiled with japanese language support
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
Reads the computer name
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
Create files in a temporary directory
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
UPX packer has been detected
- Universal BIOS Backup ToolKit 2.0.exe (PID: 7096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Clipper DOS Executable (2.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1972:12:25 05:33:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 4 |
| CodeSize: | 40960 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 73728 |
| EntryPoint: | 0x1bb90 |
| OSVersion: | 4 |
| ImageVersion: | 2 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.1.0 |
| ProductVersionNumber: | 2.0.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 2.0.1.0 |
| FileDescription: | BIOS Backup ToolKit |
| ProductName: | BIOS Backup ToolKit |
| ProductVersion: | 2.0.1.0 |
| CompanyName: | DavidXXW Workgroup |
| LegalCopyright: | This tool only for technological research and validating vulnerabilities in the test environment. Does not involve the any copyrighted content, only for research and technological exchanges. Please delete within 24 hours, or for all the consequences arising from your own! |
| Comments: | This tool only for technological research and validating vulnerabilities in the test environment. Does not involve the any copyrighted content, only for research and technological exchanges. Please delete within 24 hours, or for all the consequences arising from your own! |
Total processes
110
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7096 | "C:\Users\admin\AppData\Local\Temp\Universal BIOS Backup ToolKit 2.0.exe" | C:\Users\admin\AppData\Local\Temp\Universal BIOS Backup ToolKit 2.0.exe | explorer.exe | ||||||||||||
User: admin Company: DavidXXW Workgroup Integrity Level: MEDIUM Description: BIOS Backup ToolKit Version: 2.0.1.0 Modules
| |||||||||||||||
Total events
27
Read events
27
Write events
0
Delete events
0
Modification events
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7096 | Universal BIOS Backup ToolKit 2.0.exe | C:\Users\admin\AppData\Local\Temp\E_N4\krnln.fnr | executable | |
MD5:638E737B2293CF7B1F14C0B4FB1F3289 | SHA256:BAAD4798C3AB24DEC8F0AC3CDE48E2FEE2E2DFFA60D2B2497CD295CD6319FD5B | |||
| 7096 | Universal BIOS Backup ToolKit 2.0.exe | C:\Users\admin\AppData\Local\Temp\E_N4\GDI+Ö§³Ö¿â.fne | executable | |
MD5:77EA76FF8B4BCE61C5955BC31BB33518 | SHA256:316E6B6BF5DB2EEDCFFBC3204423A17583B4EADA920A3BB86605EE762C591687 | |||
| 7096 | Universal BIOS Backup ToolKit 2.0.exe | C:\Users\admin\AppData\Local\Temp\E_N4\PhyDMACC.dll | executable | |
MD5:7D0F0C8906B2557825E346870CABBE7A | SHA256:2364B47EA6C12B2746EB558A568A8C887D9EBAC78DAB3722F1F72C71BD9D52AA | |||
| 7096 | Universal BIOS Backup ToolKit 2.0.exe | C:\Users\admin\AppData\Local\Temp\PhyDMACCx64.sys | executable | |
MD5:12CECC3C14160F32B21279C1A36B8338 | SHA256:47EAEBC920CCF99E09FC9924FEB6B19B8A28589F52783327067C9B09754B5E84 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
624 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |