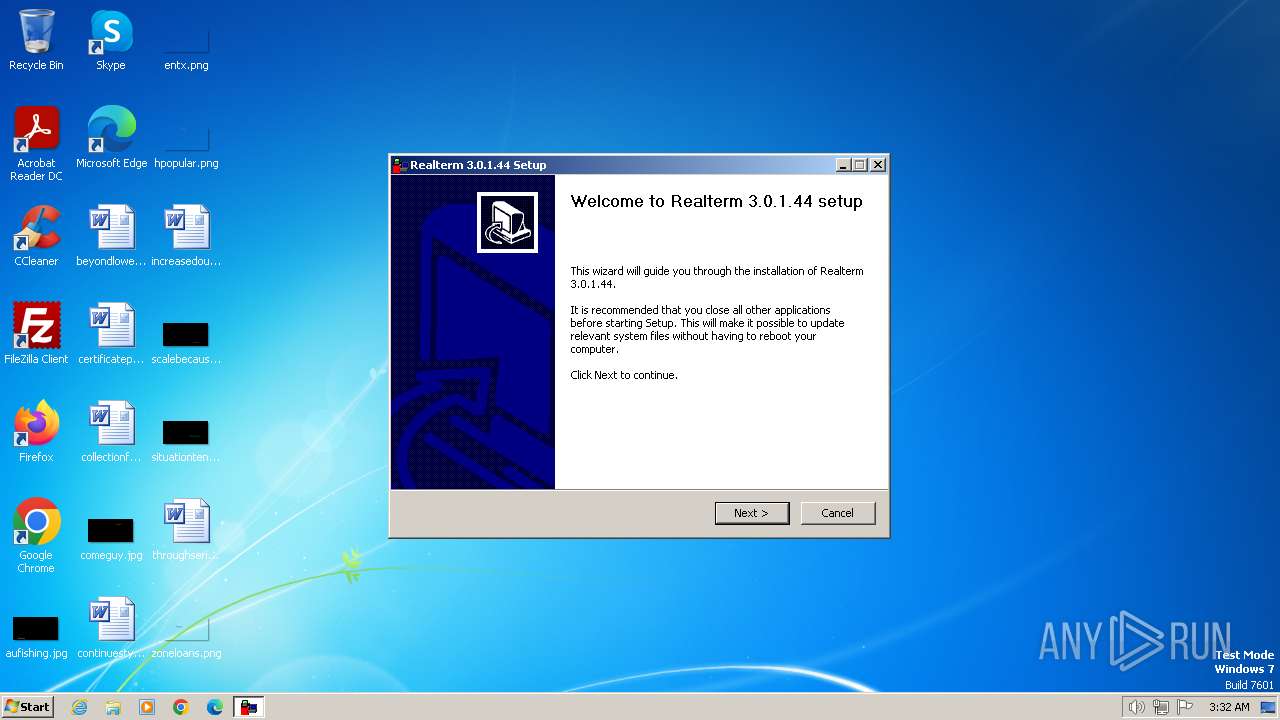
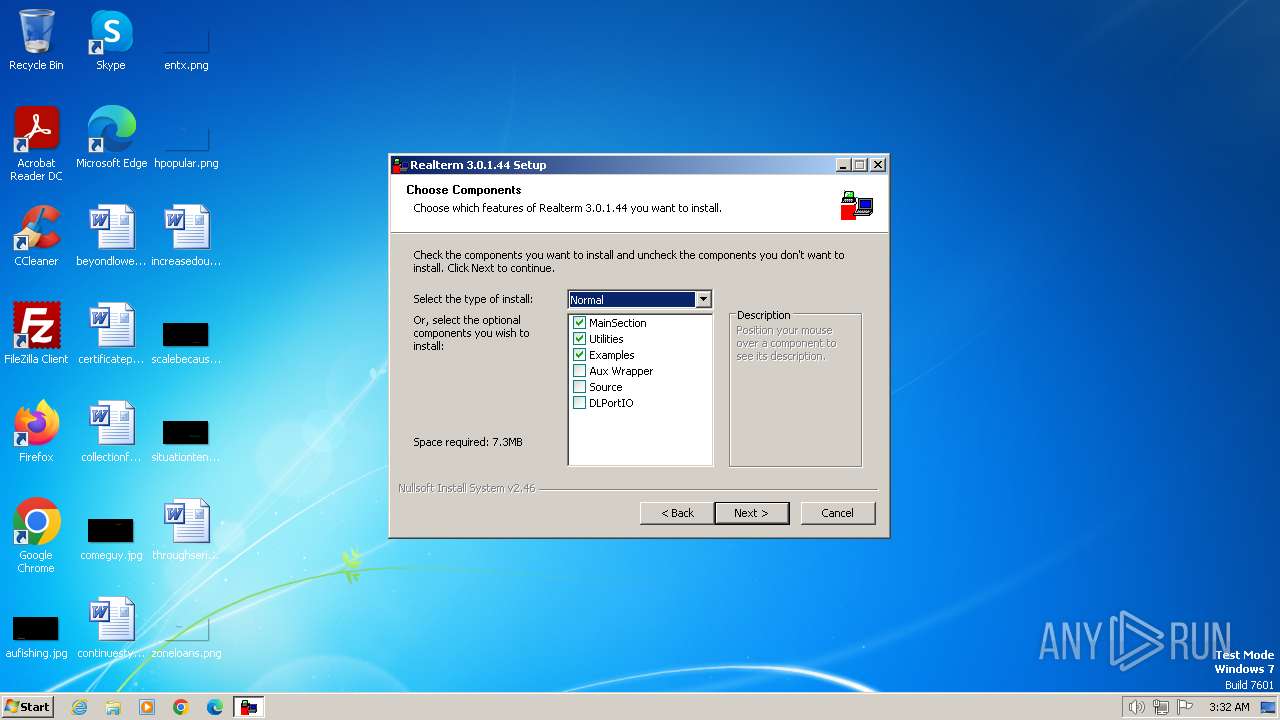
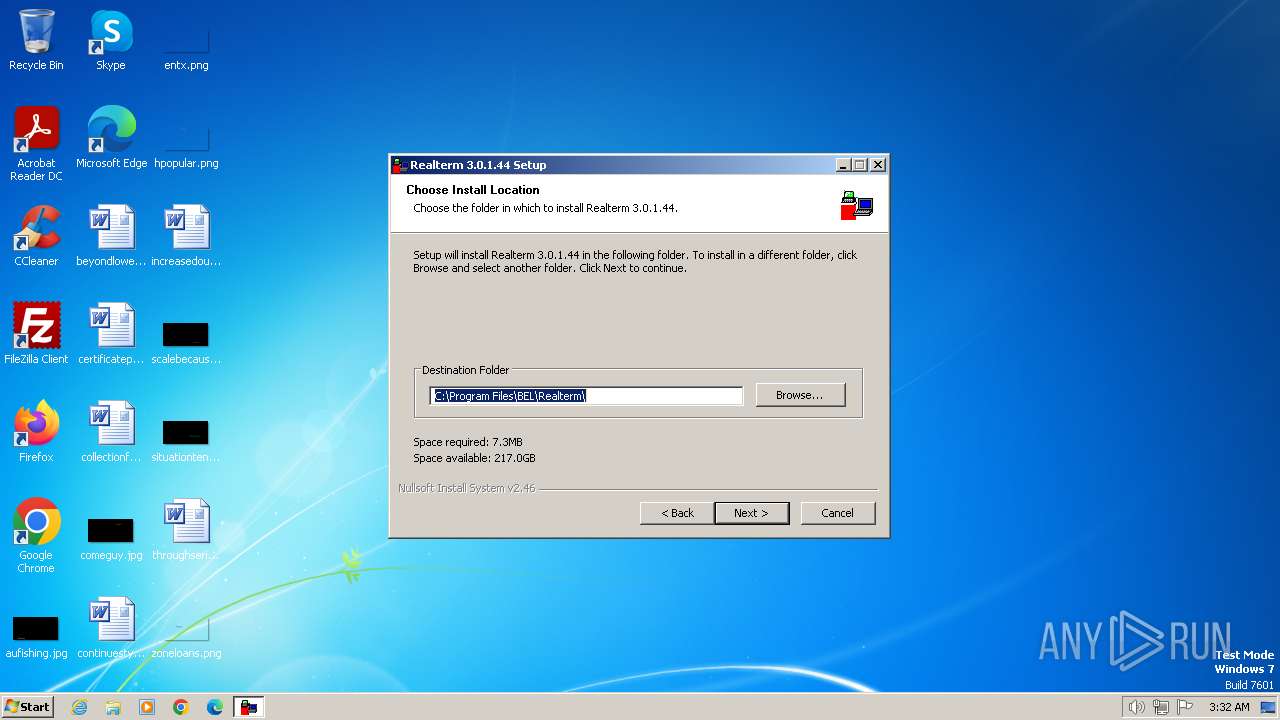
| File name: | Realterm_3.0.1.44_setup.exe |
| Full analysis: | https://app.any.run/tasks/f46a205c-b42c-4df7-8d4a-232a0d91e016 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 03:32:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 886E8F77E860744E9AF6DA1EF77314BB |
| SHA1: | C7FB9A748ED8FD6B0D92027DD9C0373715972F04 |
| SHA256: | 67275D8330156546DBFF495259053705AB41E6E0F03CE07E4000F34E4BBAA5A2 |
| SSDEEP: | 98304:P66BHFqkxqVRl9aAJ3XrVWqxDTQaGGUznPUkwfUF5aZIF8s6VoetJX02NbQw36Ql:SAFqxsuHBBb |
MALICIOUS
Drops the executable file immediately after the start
- Realterm_3.0.1.44_setup.exe (PID: 2036)
SUSPICIOUS
Reads security settings of Internet Explorer
- Realterm_3.0.1.44_setup.exe (PID: 2036)
- realterm.exe (PID: 120)
Malware-specific behavior (creating "System.dll" in Temp)
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Executable content was dropped or overwritten
- Realterm_3.0.1.44_setup.exe (PID: 2036)
The process creates files with name similar to system file names
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Start notepad (likely ransomware note)
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Creates a software uninstall entry
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Reads the Internet Settings
- Realterm_3.0.1.44_setup.exe (PID: 2036)
- realterm.exe (PID: 120)
Checks Windows Trust Settings
- realterm.exe (PID: 120)
Reads settings of System Certificates
- realterm.exe (PID: 120)
Adds/modifies Windows certificates
- realterm.exe (PID: 120)
INFO
Create files in a temporary directory
- Realterm_3.0.1.44_setup.exe (PID: 2036)
- realterm.exe (PID: 120)
Reads the computer name
- Realterm_3.0.1.44_setup.exe (PID: 2036)
- realterm.exe (PID: 3464)
- realterm.exe (PID: 120)
Checks supported languages
- Realterm_3.0.1.44_setup.exe (PID: 2036)
- realterm.exe (PID: 120)
- realterm.exe (PID: 3464)
Creates files or folders in the user directory
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Creates files in the program directory
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Reads Environment values
- Realterm_3.0.1.44_setup.exe (PID: 2036)
Reads the machine GUID from the registry
- realterm.exe (PID: 120)
Reads the software policy settings
- realterm.exe (PID: 120)
Reads CPU info
- realterm.exe (PID: 120)
Checks proxy server information
- realterm.exe (PID: 120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x323c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
45
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\BEL\Realterm\realterm.exe" install | C:\Program Files\BEL\Realterm\realterm.exe | Realterm_3.0.1.44_setup.exe | ||||||||||||
User: admin Company: Broadcast Equipment Ltd Integrity Level: HIGH Description: Realterm Serial Terminal Program Exit code: 0 Version: 3.0.1.44 Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\AppData\Local\Temp\Realterm_3.0.1.44_setup.exe" | C:\Users\admin\AppData\Local\Temp\Realterm_3.0.1.44_setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2124 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\BEL\Realterm\Readme.txt | C:\Windows\System32\notepad.exe | — | Realterm_3.0.1.44_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3464 | "C:\Program Files\BEL\Realterm\realterm.exe" /regserver | C:\Program Files\BEL\Realterm\realterm.exe | — | Realterm_3.0.1.44_setup.exe | |||||||||||
User: admin Company: Broadcast Equipment Ltd Integrity Level: HIGH Description: Realterm Serial Terminal Program Exit code: 0 Version: 3.0.1.44 Modules
| |||||||||||||||
| 3668 | "C:\Users\admin\AppData\Local\Temp\Realterm_3.0.1.44_setup.exe" | C:\Users\admin\AppData\Local\Temp\Realterm_3.0.1.44_setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
9 313
Read events
9 226
Write events
72
Delete events
15
Modification events
| (PID) Process: | (2036) Realterm_3.0.1.44_setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2036) Realterm_3.0.1.44_setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2036) Realterm_3.0.1.44_setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2036) Realterm_3.0.1.44_setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3464) realterm.exe | Key: | HKEY_CURRENT_USER\Software\BEL\Realterm |
| Operation: | write | Name: | Last Update Check |
Value: FEA3D2B98424E640 | |||
| (PID) Process: | (3464) realterm.exe | Key: | HKEY_CURRENT_USER\Software\BEL\Realterm |
| Operation: | write | Name: | Block Update Checks |
Value: 0 | |||
| (PID) Process: | (3464) realterm.exe | Key: | HKEY_CURRENT_USER\Software\BEL\Realterm |
| Operation: | write | Name: | Run Count |
Value: 0 | |||
| (PID) Process: | (3464) realterm.exe | Key: | HKEY_CURRENT_USER\Software\BEL\Realterm |
| Operation: | write | Name: | Run Days |
Value: 0000000000000000 | |||
| (PID) Process: | (3464) realterm.exe | Key: | HKEY_CURRENT_USER\Software\BEL\Realterm |
| Operation: | write | Name: | Latest Version |
Value: | |||
| (PID) Process: | (3464) realterm.exe | Key: | HKEY_CURRENT_USER\Software\BEL\Realterm |
| Operation: | write | Name: | IT Version |
Value: | |||
Executable files
14
Suspicious files
19
Text files
57
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Program Files\BEL\Realterm\Readme.txt | text | |
MD5:EB69399CDC9B9F1367996E2DCE5E78C6 | SHA256:6A8E6F01D2A0D60FD2284FCFC95C14B4434295D53E979A51CCC772700BF91673 | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Local\Temp\nscF908.tmp\StartMenu.dll | executable | |
MD5:A4173B381625F9F12AADB4E1CDAEFDB8 | SHA256:7755FF2707CA19344D489A5ACEC02D9E310425FA6E100D2F13025761676B875B | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Program Files\BEL\Realterm\Keymap_VT100_BS.txt | text | |
MD5:541574B2469F104E2DA0B0B190346117 | SHA256:1065D750C2CC61B299E021693F30D1930B10AB295FB98CBC7CBAC8E62334F5FA | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Local\Temp\nscF908.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Roaming\Realterm\Macros_and_INI_files.txt | text | |
MD5:A0C46292FE54A824D529DD6D1F29F719 | SHA256:13C53CA4E5688D2F4831C13E770F7F123DF788122EE7E6DE9449B743705583D9 | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Program Files\BEL\Realterm\change_log.txt | text | |
MD5:F0246E80D45BEFF0A9D55C910515A0F6 | SHA256:3EFDBEF559E204AFE02BCAC38C876EBF2C2E9E7AF1D7AE681F1CF16ADEEB225A | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Roaming\Realterm\realterm_defaultXX.ini | text | |
MD5:8343C7B7E804AFE3E50A636C3D8B4FB9 | SHA256:76306A945C4DA625284B8831108AD5D6FE181E4E260BD5E6AFCBFBC05758B05C | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Realterm\Realterm I2C.lnk | binary | |
MD5:A7F1243229134B65F6F4EC058557C8B4 | SHA256:B654BC9C39B504517BC6F7769F9C781CB3F54B35F1040E380F57D1FC6F1DA171 | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Roaming\Realterm\realterm_macro2.ini | text | |
MD5:767CAFDBAF2C833A986B06F44ED105E5 | SHA256:3D98D45172AA307DF002D799330DED0B706D76BCBC2882D218034D2E82A37A16 | |||
| 2036 | Realterm_3.0.1.44_setup.exe | C:\Users\admin\AppData\Roaming\Realterm\realterm_alwaysXX.ini | text | |
MD5:419B8BE88397C3EFF5DE641D3736DA39 | SHA256:E3EF22BB619AC6B97A2AA9EF97B9325EA7809C783281EBA8A4CE1F312F1590E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
120 | realterm.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f25cf4c87ca694ad | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
120 | realterm.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
120 | realterm.exe | 96.126.99.234:443 | appanalytics.embarcadero.com | Linode, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
appanalytics.embarcadero.com |
| unknown |