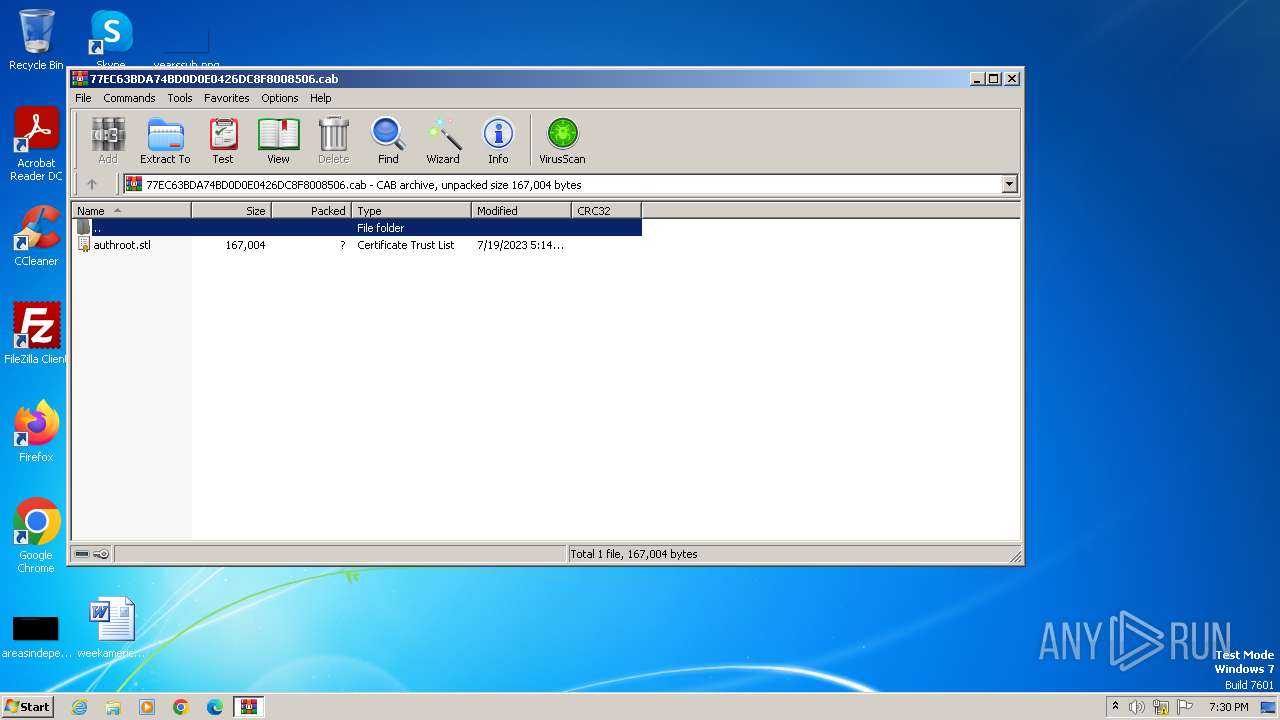
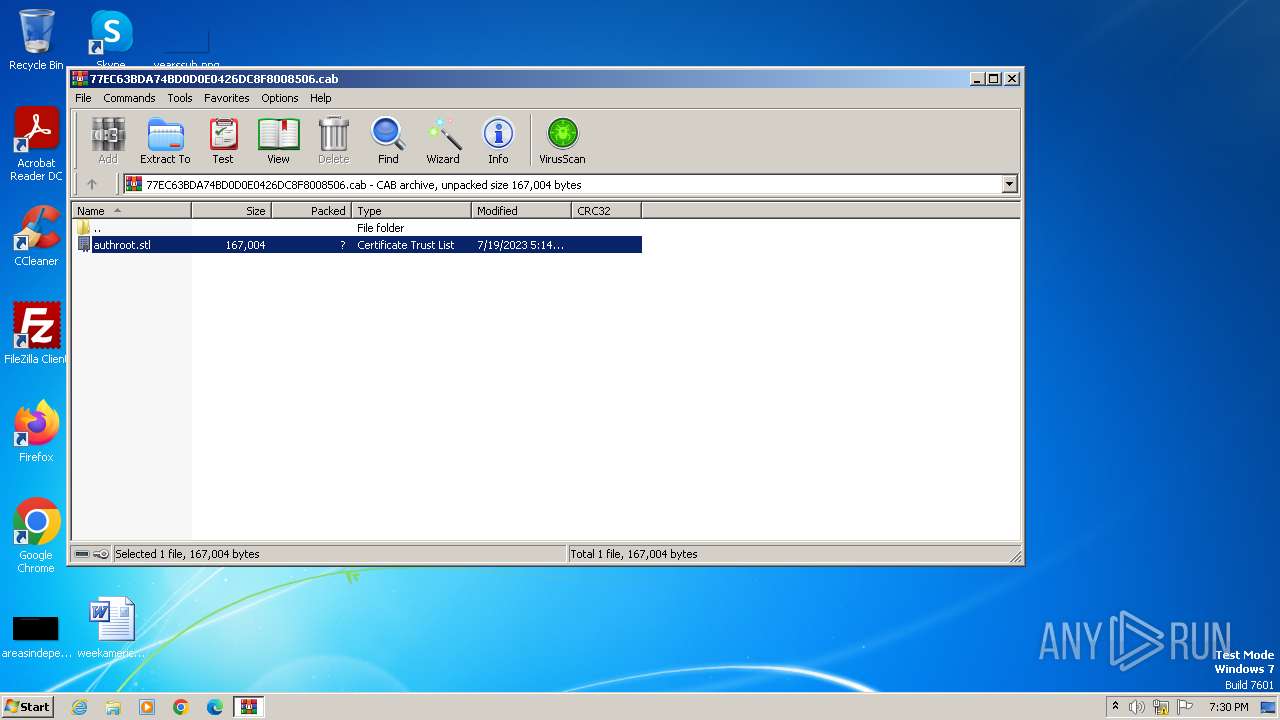
| File name: | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 |
| Full analysis: | https://app.any.run/tasks/399b8bc8-9d17-4e5d-bddc-a4a7fa6d3435 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2023, 19:29:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, Windows 2000/XP setup, 63165 bytes, 1 file, at 0x2c +A "authroot.stl", number 1, 6 datablocks, 0x1 compression |
| MD5: | F3441B8572AAE8801C04F3060B550443 |
| SHA1: | 4EF0A35436125D6821831EF36C28FFAF196CDA15 |
| SHA256: | 6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF |
| SSDEEP: | 1536:RfhMeKBlsociYZAT+4oGNk2rb2oX3bUH+uOlEU:RhV0WXvAa4XNoeudU |
MALICIOUS
No malicious indicators.SUSPICIOUS
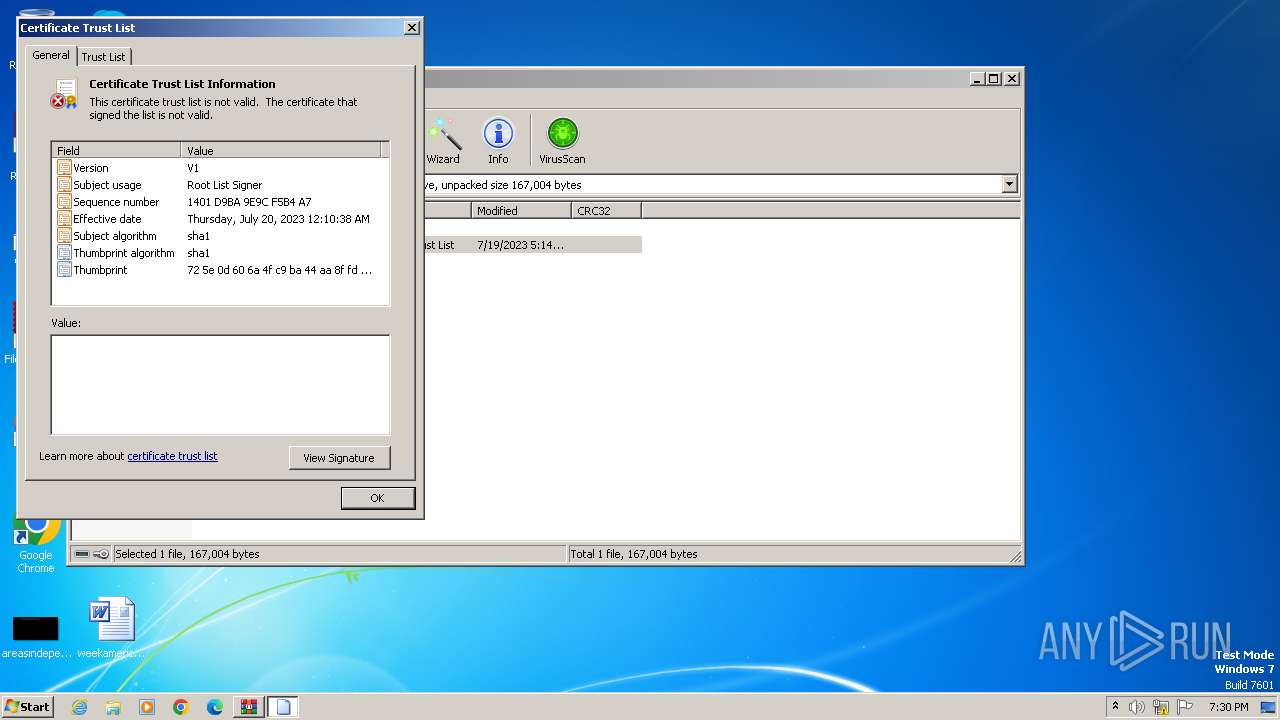
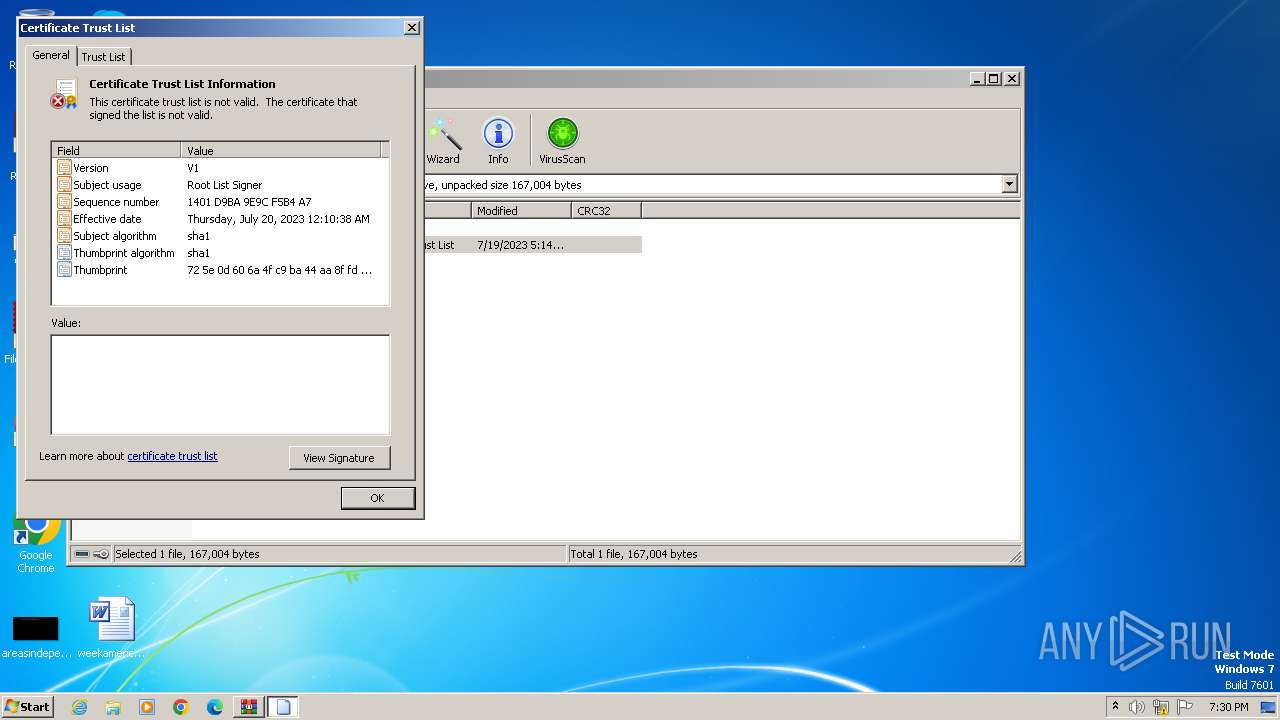
Reads settings of System Certificates
- rundll32.exe (PID: 2480)
- rundll32.exe (PID: 1668)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2708)
INFO
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1668)
- rundll32.exe (PID: 2480)
Checks supported languages
- wmpnscfg.exe (PID: 3008)
Reads the computer name
- wmpnscfg.exe (PID: 3008)
Manual execution by a user
- wmpnscfg.exe (PID: 3008)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
39
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1668 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCTL C:\Users\admin\AppData\Local\Temp\Rar$DIa2708.30149\authroot.stl | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCTL C:\Users\admin\AppData\Local\Temp\Rar$DIa2708.28703\authroot.stl | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2708 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\77EC63BDA74BD0D0E0426DC8F8008506.cab" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3008 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 521
Read events
6 483
Write events
33
Delete events
5
Modification events
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2480) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1668) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2708.30149\authroot.stl | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2708.28703\authroot.stl | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 23.35.228.137:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |