| File name: | ProDENTCaptureSetup5.0.0.4.exe |
| Full analysis: | https://app.any.run/tasks/d2d07622-6f44-4fa5-8ebc-23b4a72d95fa |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2023, 22:13:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0AE995CCF081680B28C1726927F14D3F |
| SHA1: | EC1C349B5C8454B2481D265D7E4CC0DFD8EEDCBE |
| SHA256: | 6715C0B0A56849425F8D5D699CE217608298D682191196BDD2782A55DE4F5216 |
| SSDEEP: | 98304:P+QqZ8fQBNxr6mRBZtEo4OceeKzSmmjuCUeevzxi5NBZMXhRXlgZH8DBkH+LOA9T:22Yrb/mq |
MALICIOUS
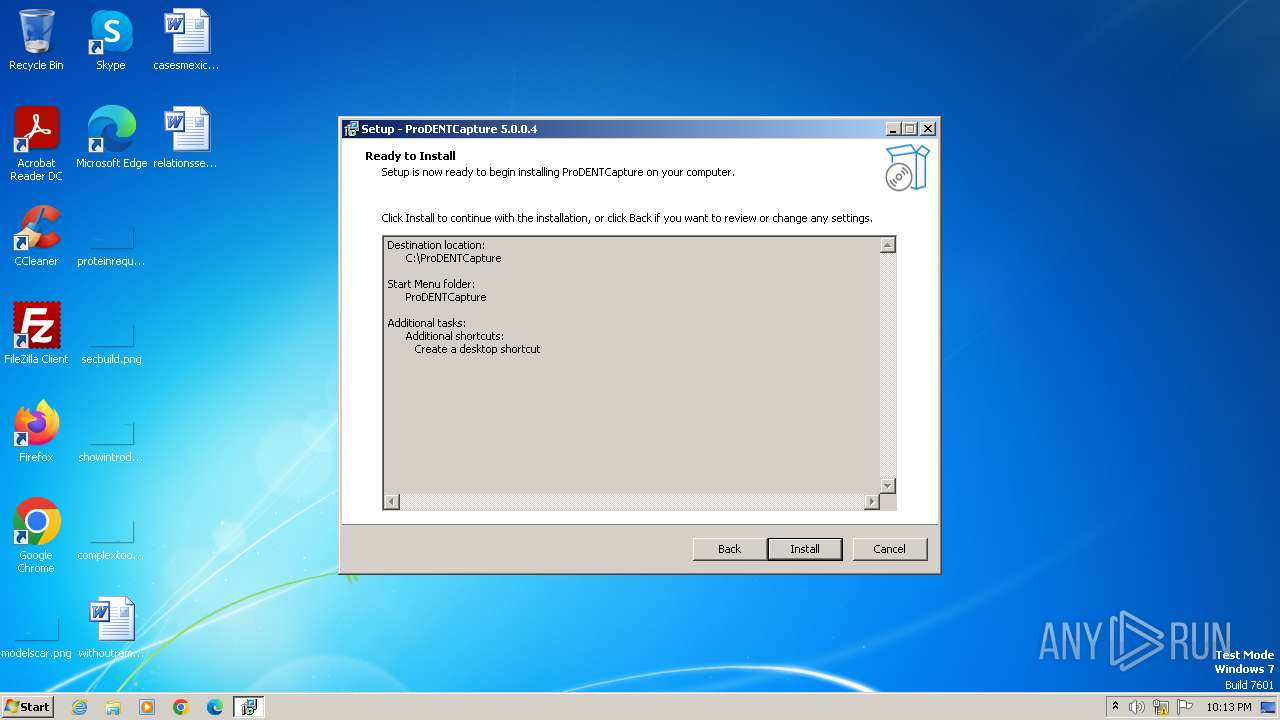
Drops the executable file immediately after the start
- ProDENTCaptureSetup5.0.0.4.exe (PID: 3220)
- ProDENTCaptureSetup5.0.0.4.tmp (PID: 2912)
- ProDENTCapture.exe (PID: 3480)
SUSPICIOUS
Reads the Windows owner or organization settings
- ProDENTCaptureSetup5.0.0.4.tmp (PID: 2912)
Reads the Internet Settings
- ProDENTCapture.exe (PID: 3480)
Reads security settings of Internet Explorer
- ProDENTCapture.exe (PID: 3480)
Checks Windows Trust Settings
- ProDENTCapture.exe (PID: 3480)
INFO
Checks supported languages
- ProDENTCaptureSetup5.0.0.4.exe (PID: 3220)
- ProDENTCaptureSetup5.0.0.4.tmp (PID: 2912)
- ProDENTCapture.exe (PID: 3480)
Create files in a temporary directory
- ProDENTCaptureSetup5.0.0.4.exe (PID: 3220)
- ProDENTCapture.exe (PID: 3480)
Reads the computer name
- ProDENTCaptureSetup5.0.0.4.tmp (PID: 2912)
- ProDENTCapture.exe (PID: 3480)
Reads the machine GUID from the registry
- ProDENTCapture.exe (PID: 3480)
Creates files or folders in the user directory
- ProDENTCaptureSetup5.0.0.4.tmp (PID: 2912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:06:03 10:09:11+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
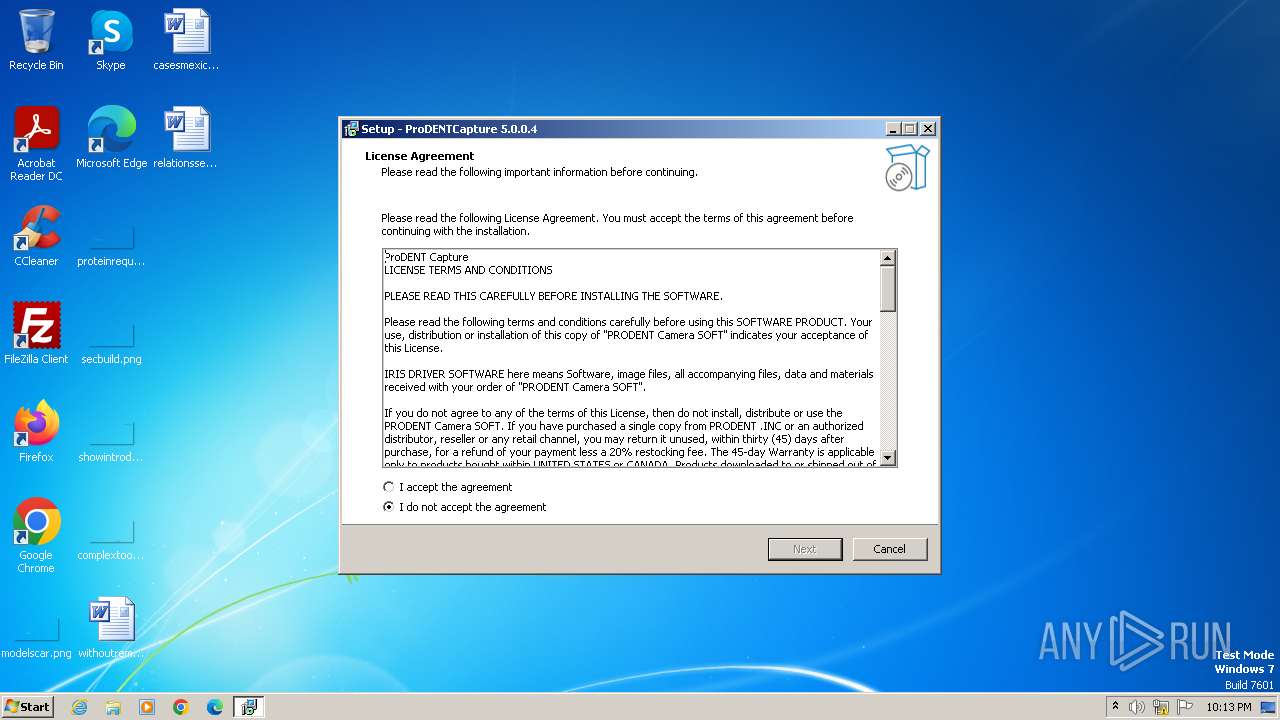
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | ProDENT Intraoral Camera |
| FileDescription: | ProDENTCapture Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | ProDENTCapture |
| ProductVersion: | 5.0.0.4 |
Total processes
37
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2912 | "C:\Users\admin\AppData\Local\Temp\is-69HIU.tmp\ProDENTCaptureSetup5.0.0.4.tmp" /SL5="$60194,2177670,780800,C:\Users\admin\AppData\Local\Temp\ProDENTCaptureSetup5.0.0.4.exe" | C:\Users\admin\AppData\Local\Temp\is-69HIU.tmp\ProDENTCaptureSetup5.0.0.4.tmp | — | ProDENTCaptureSetup5.0.0.4.exe | |||||||||||
User: admin Company: ProDENT Intraoral Camera Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3220 | "C:\Users\admin\AppData\Local\Temp\ProDENTCaptureSetup5.0.0.4.exe" | C:\Users\admin\AppData\Local\Temp\ProDENTCaptureSetup5.0.0.4.exe | — | explorer.exe | |||||||||||
User: admin Company: ProDENT Intraoral Camera Integrity Level: MEDIUM Description: ProDENTCapture Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3480 | "C:\ProDENTCapture\ProDENTCapture.exe" | C:\ProDENTCapture\ProDENTCapture.exe | — | ProDENTCaptureSetup5.0.0.4.tmp | |||||||||||
User: admin Company: Venoka USA inc Integrity Level: MEDIUM Description: ProDENTCapture Exit code: 0 Version: 5.0.0.4 Modules
| |||||||||||||||
Total events
707
Read events
693
Write events
8
Delete events
6
Modification events
| (PID) Process: | (3480) ProDENTCapture.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3480) ProDENTCapture.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3480) ProDENTCapture.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3480) ProDENTCapture.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2912) ProDENTCaptureSetup5.0.0.4.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: FEE32ADC501AFA01743CEA02457A05DD5264F72EA7E53A0CB180B7EDD1653982 | |||
| (PID) Process: | (2912) ProDENTCaptureSetup5.0.0.4.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\ProDENTCapture\ProDENTCapture.exe | |||
| (PID) Process: | (2912) ProDENTCaptureSetup5.0.0.4.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2912) ProDENTCaptureSetup5.0.0.4.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 4289E4732C825E5A94B04FC8219BE42ACBC061A1BEDC8F7F92E1820552D8E931 | |||
| (PID) Process: | (2912) ProDENTCaptureSetup5.0.0.4.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 600B0000CE02AE19911DDA01 | |||
| (PID) Process: | (2912) ProDENTCaptureSetup5.0.0.4.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
17
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\ProDENTCapture\ProDENTCapture.lnk | binary | |
MD5:77A715C232BDDB36471335DCF867BEFE | SHA256:852EF79A51AE53F0D7E1ADF53B3D0C8EF22A4CDBCA928755738E7FAA091EA081 | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\ProDENTCapture\unins000.dat | binary | |
MD5:75F8A946D86FA44F8F2548B991F195CC | SHA256:16EB22188C22664B9FA412A232F3F62BE858BD76C800B6A7EB9DAD661D81E89B | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\ProDENTCapture\ProDENTCapture on the Web.url | text | |
MD5:97A0A7739DA6FC05A371713E9AAACD73 | SHA256:4B68B398E78168E121FC570BBB5012DBFD64EC1A1C7DE555330BA65091D890F9 | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\ProDENTCapture\AutoUpdater.NET.dll | executable | |
MD5:4919C59E98C927EB902A9370A45E71B8 | SHA256:0F2B1C726E47166CFE30F0EDBD0939B3723BF3E63FC4DD9D8D178D85A4BCC72F | |||
| 3480 | ProDENTCapture.exe | C:\Users\admin\AppData\Local\Temp\evbCBE4.tmp | executable | |
MD5:E422C3CA380A1C8E8B1A737AE8E6992E | SHA256:493F8A07A44260EA9C2AE556F7B09E10230843FD8D4497A646305F99B3E1EDBE | |||
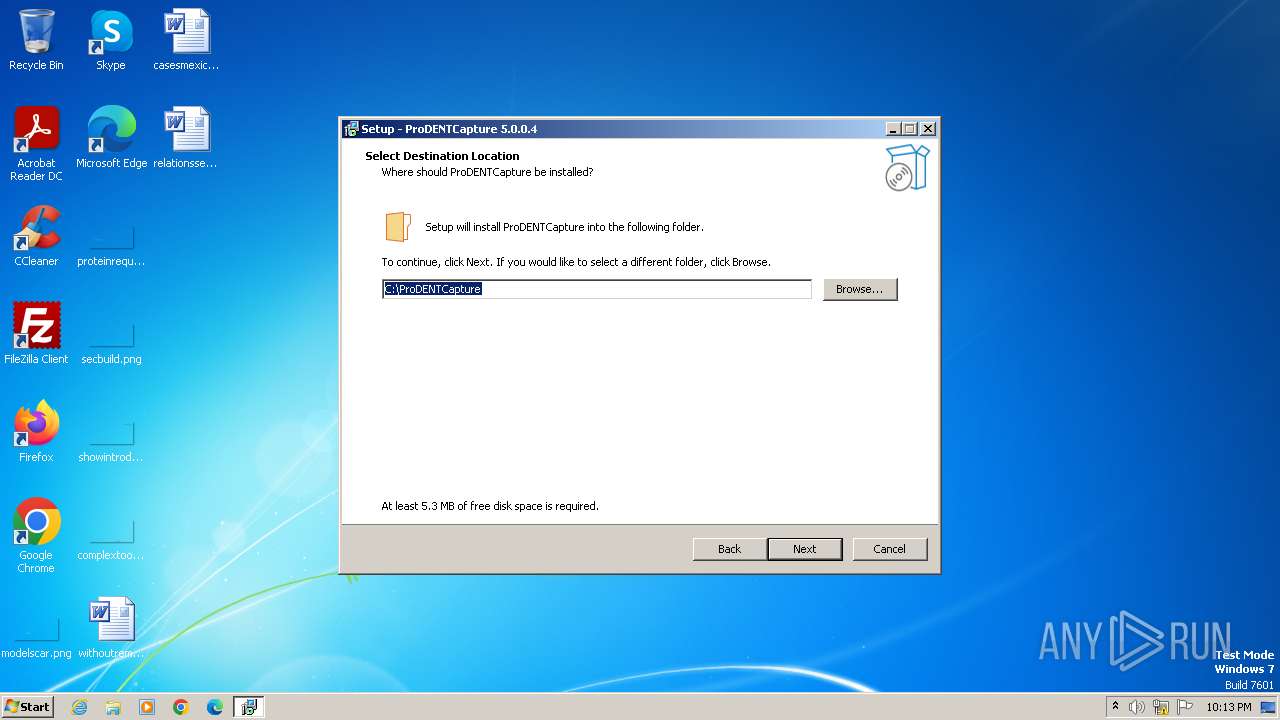
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\ProDENTCapture\ProDENTCapture.exe | executable | |
MD5:1B7203F5CAEAE1A1A94698D09E730C50 | SHA256:90928F6B9503877795441C9F90EB9E0C4063D1708C512AA02785D22450205B5F | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\Users\admin\Desktop\ProDENTCapture.lnk | binary | |
MD5:9EA128D38CEFE04BA2AEC813BDB89F02 | SHA256:1BF18AA2506394C996942209B9BEF9808CD7BB885F3F53CAE124A3461A5D4324 | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\ProDENTCapture\is-HKR9H.tmp | executable | |
MD5:BD17B58C31D582B21FB5857F84A27225 | SHA256:4FED2361AC700AB7C96C81A19F2D771E451031D6F1B60EB2F5641929F6E38E62 | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\ProDENTCapture\is-4UJAS.tmp | executable | |
MD5:1B7203F5CAEAE1A1A94698D09E730C50 | SHA256:90928F6B9503877795441C9F90EB9E0C4063D1708C512AA02785D22450205B5F | |||
| 2912 | ProDENTCaptureSetup5.0.0.4.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\ProDENTCapture\Uninstall ProDENTCapture.lnk | binary | |
MD5:F0931ED4F497AD9AB34A4FF81E17149B | SHA256:980A739D0DA496AC131E7E0866169EA0A35EADD82AA8E259CDE5AF9E13AE0529 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |