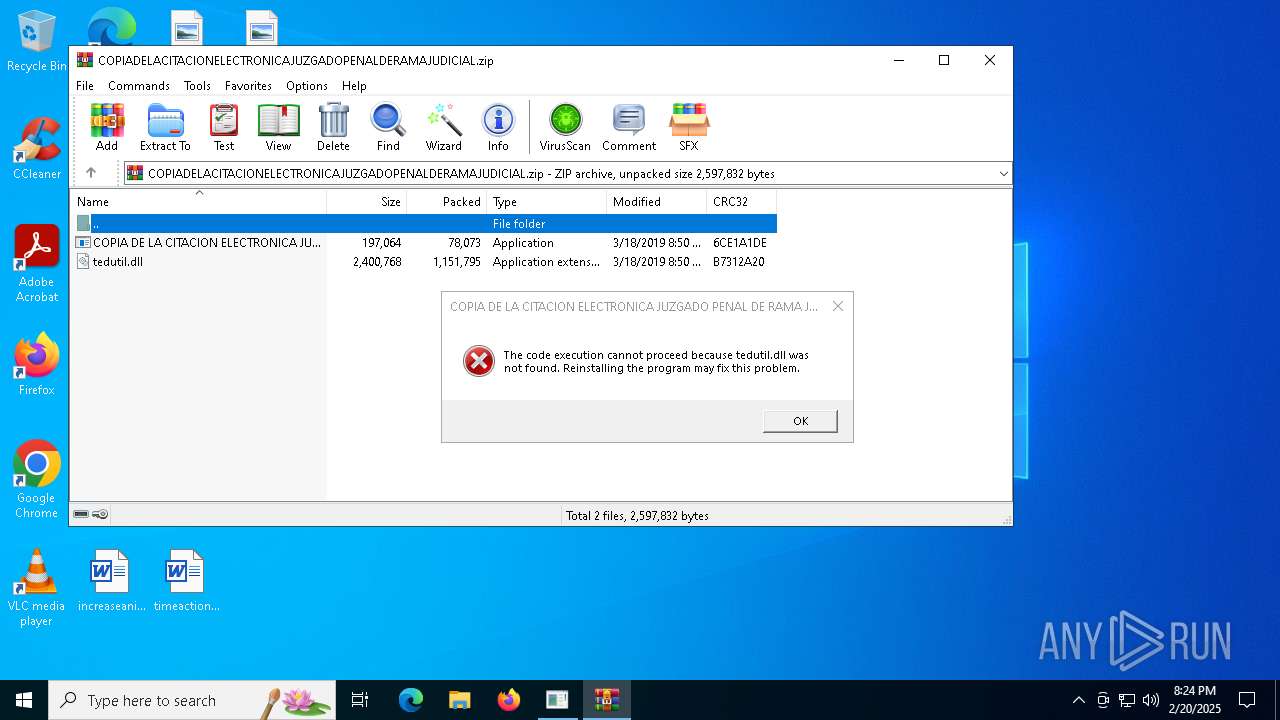
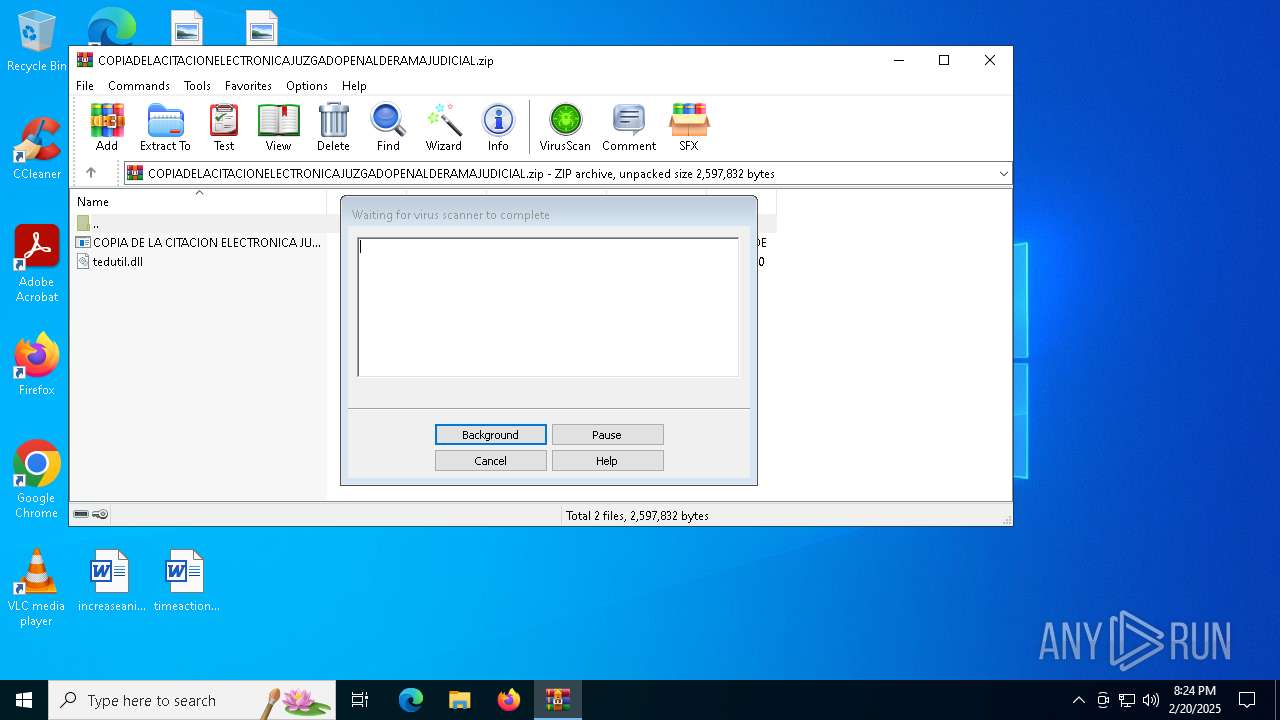
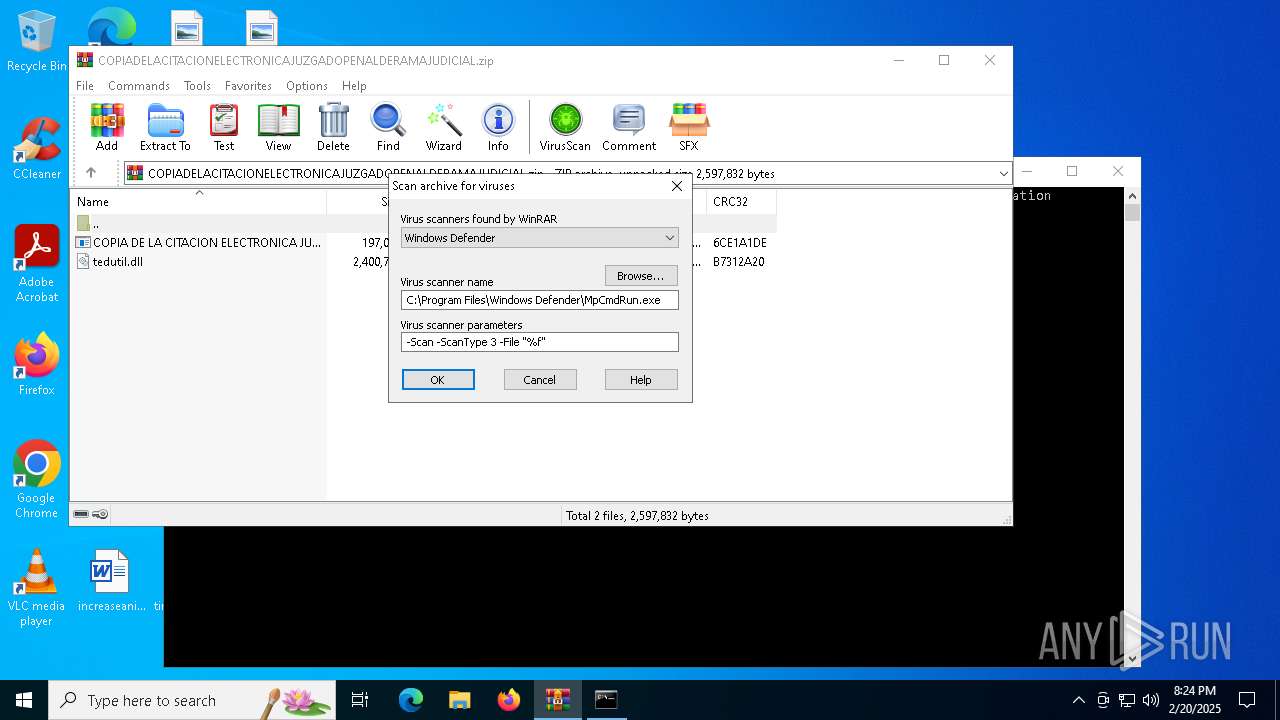
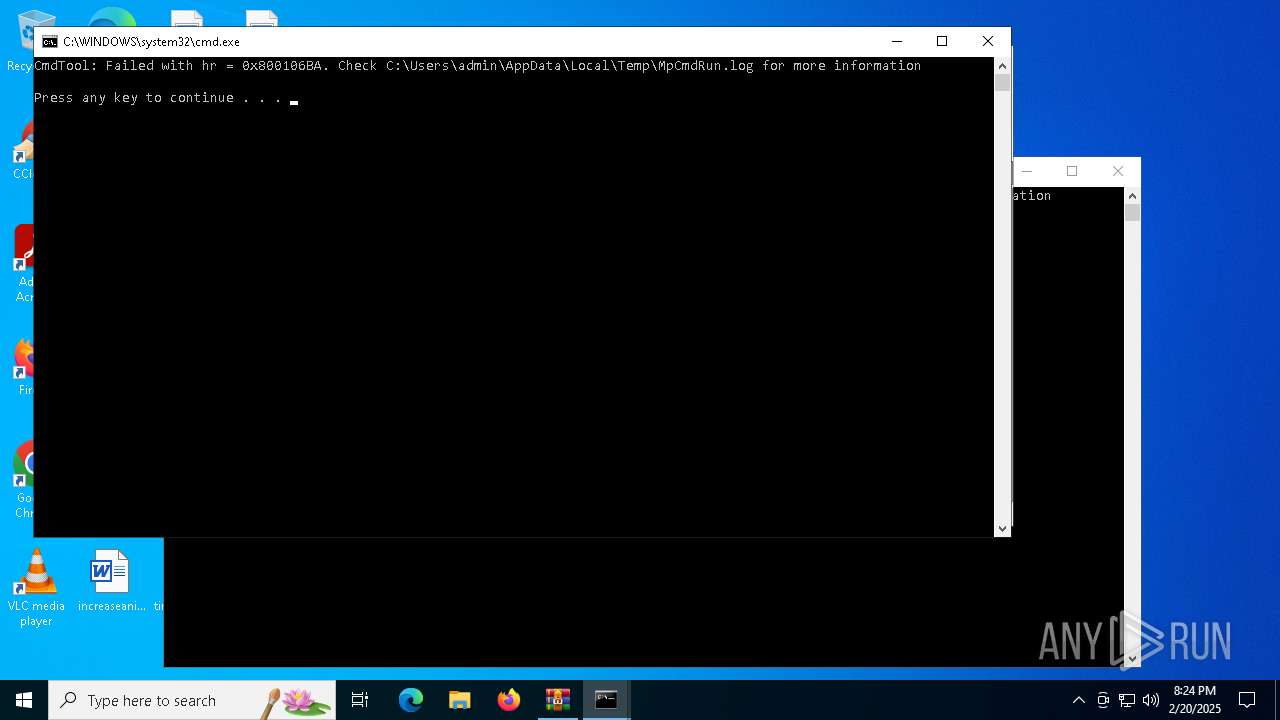
| File name: | COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip |
| Full analysis: | https://app.any.run/tasks/24280496-073e-481b-b40a-d67ee103ea9f |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2025, 20:23:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E4B63789F7736BC66ABB76F58BE73F4E |
| SHA1: | 6D44CC56312D1F15AE974AEE46A6C3A1717E60B8 |
| SHA256: | 67120EC750187029EFAE93EE5AEEE158EEC62C409A178F3A124E07E303FCB380 |
| SSDEEP: | 49152:NopEG8017JZfjRbwDgUEVcoAau83RWIXQBVsEGqJyTI9RCA8o56Zmmmvz78jUDrZ:NoP7JZ9bwDgUEVdAaD3bXQBEIHCRo5BR |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1200)
GENERIC has been found (auto)
- WinRAR.exe (PID: 1200)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1200)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 1200)
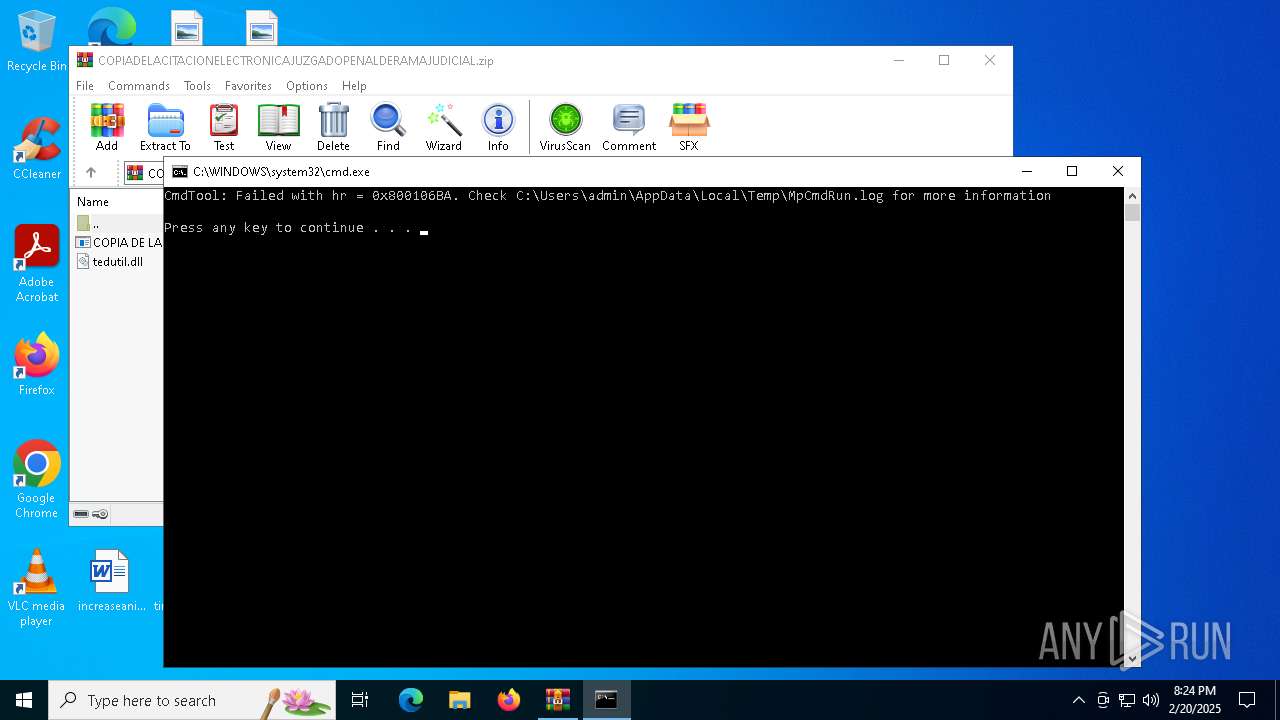
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1200)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1200)
The sample compiled with english language support
- WinRAR.exe (PID: 1200)
Checks supported languages
- MpCmdRun.exe (PID: 6136)
- MpCmdRun.exe (PID: 5256)
Reads the computer name
- MpCmdRun.exe (PID: 6136)
- MpCmdRun.exe (PID: 5256)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6136)
Manual execution by a user
- COPIA DE LA CITACION ELECTRONICA JUZGADO PENAL DE RAMA JUDICIAL.exe (PID: 3988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:18 20:50:28 |
| ZipCRC: | 0x6ce1a1de |
| ZipCompressedSize: | 78073 |
| ZipUncompressedSize: | 197064 |
| ZipFileName: | COPIA DE LA CITACION ELECTRONICA JUZGADO PENAL DE RAMA JUDICIAL.exe |
Total processes
123
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1904 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR1200.39179\Rar$Scan39244.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | "C:\Users\admin\Desktop\COPIA DE LA CITACION ELECTRONICA JUZGADO PENAL DE RAMA JUDICIAL.exe" | C:\Users\admin\Desktop\COPIA DE LA CITACION ELECTRONICA JUZGADO PENAL DE RAMA JUDICIAL.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Topology Editor Exit code: 3221225781 Version: 1.0.0.1 Modules
| |||||||||||||||
| 5256 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR1200.39179" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5488 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR1200.36300\Rar$Scan9717.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6136 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR1200.36300" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 778
Read events
1 768
Write events
10
Delete events
0
Modification events
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
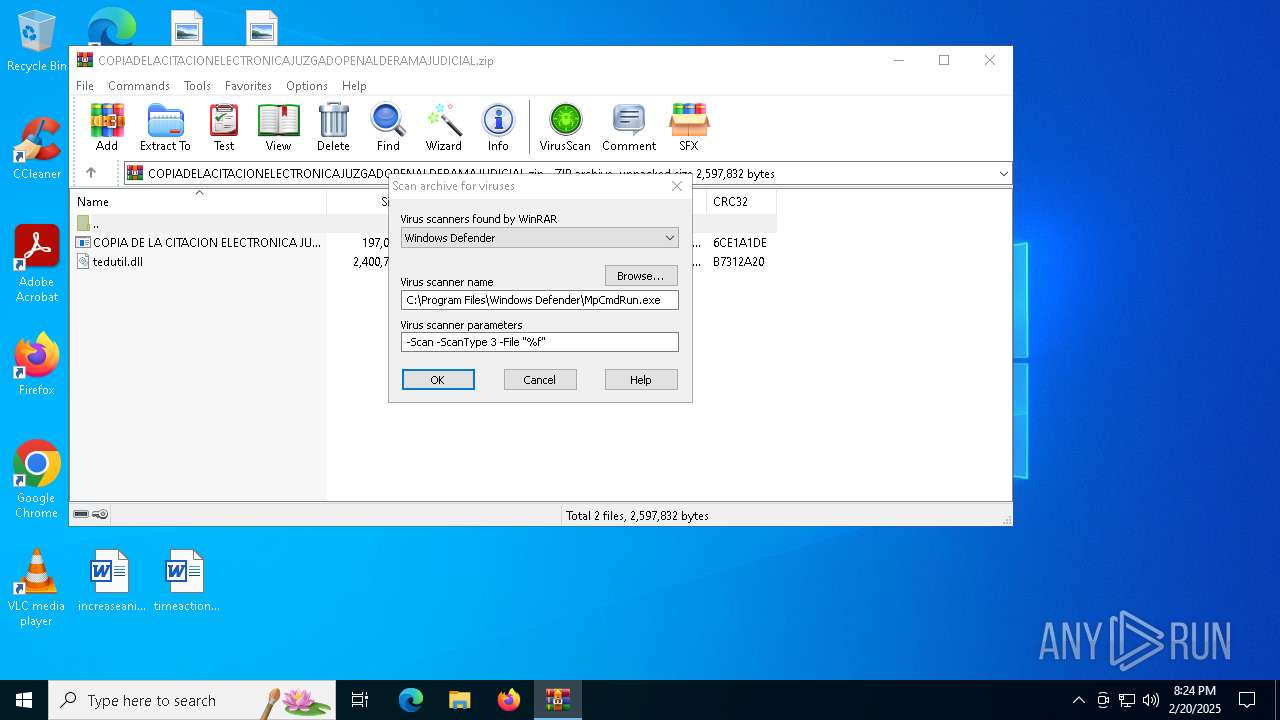
| (PID) Process: | (1200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1200.36300\COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip\tedutil.dll | executable | |
MD5:9A1A741C0ACE430F0D07A3C9DE2109ED | SHA256:4564BDB245C4E6248D78AAEA7B588AD3FAA79514E7662B80525578DC615E07B5 | |||
| 1200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1200.39179\COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip\tedutil.dll | executable | |
MD5:9A1A741C0ACE430F0D07A3C9DE2109ED | SHA256:4564BDB245C4E6248D78AAEA7B588AD3FAA79514E7662B80525578DC615E07B5 | |||
| 1200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1200.36300\COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip\COPIA DE LA CITACION ELECTRONICA JUZGADO PENAL DE RAMA JUDICIAL.exe | executable | |
MD5:93C7B66D77406F6B64507631A24BC140 | SHA256:95687DA203507A11837EAEB29BFE86481828B74B62FC869604B5EAA552F950C2 | |||
| 1200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1200.39179\COPIADELACITACIONELECTRONICAJUZGADOPENALDERAMAJUDICIAL.zip\COPIA DE LA CITACION ELECTRONICA JUZGADO PENAL DE RAMA JUDICIAL.exe | executable | |
MD5:93C7B66D77406F6B64507631A24BC140 | SHA256:95687DA203507A11837EAEB29BFE86481828B74B62FC869604B5EAA552F950C2 | |||
| 1200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1200.39179\Rar$Scan39244.bat | text | |
MD5:9F1807246A590FD3D889396DAC30AF2B | SHA256:8B2CA6E5518191B74B5B00675C47C49F9F6E4C975D25AD834C790E70955B20AB | |||
| 1200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1200.36300\Rar$Scan9717.bat | text | |
MD5:CA0F162D290AC5EECBFF1A067DB0BB9F | SHA256:67312B58FE6B9B25F2511784586EE86F70495B682CFF744C564BDDA73BB0AD6D | |||
| 6136 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:A1CD52D71216EFE37A87FABF54F7665E | SHA256:1A4353E0BD0EFE0D16E0459A915E06B58BCA26C5EF93033A36787258421E600B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4444 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4444 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4444 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4444 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4444 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |