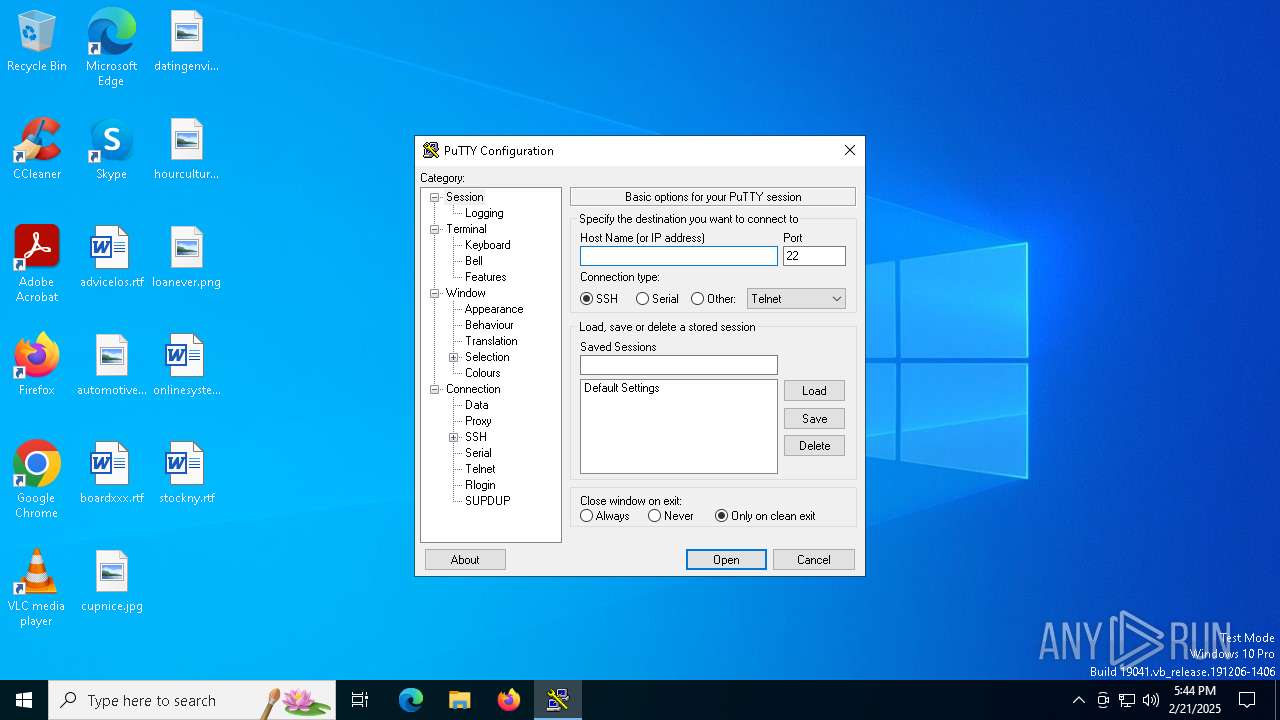
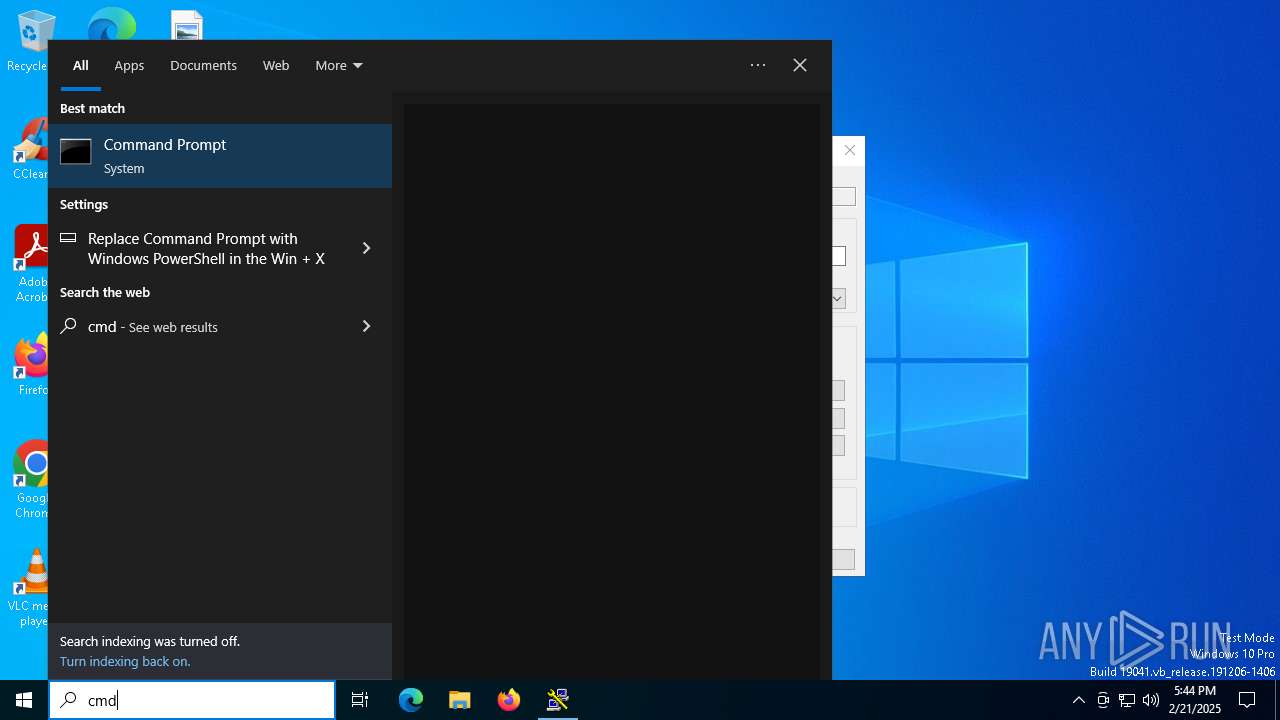
| File name: | putty.exe |
| Full analysis: | https://app.any.run/tasks/bb8dfd45-b2a7-4786-96fc-f22be7acab7d |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2025, 17:44:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 10 sections |
| MD5: | AAD4FA85BC0596AD354DF7792CA0F553 |
| SHA1: | 8E81DAA8C88A1E40C60332917C4AD5FA57ACBB23 |
| SHA256: | 66DFBF1AFD469FEB67E47EDD984C5010FDF68FBF4FDCE20F04EDD4FFCD4CAE33 |
| SSDEEP: | 49152:tHAEty2j5Byqr/G1nr5oKSNEFwyiw3Bs7WB:xKNfSNEFwDBWB |
MALICIOUS
No malicious indicators.SUSPICIOUS
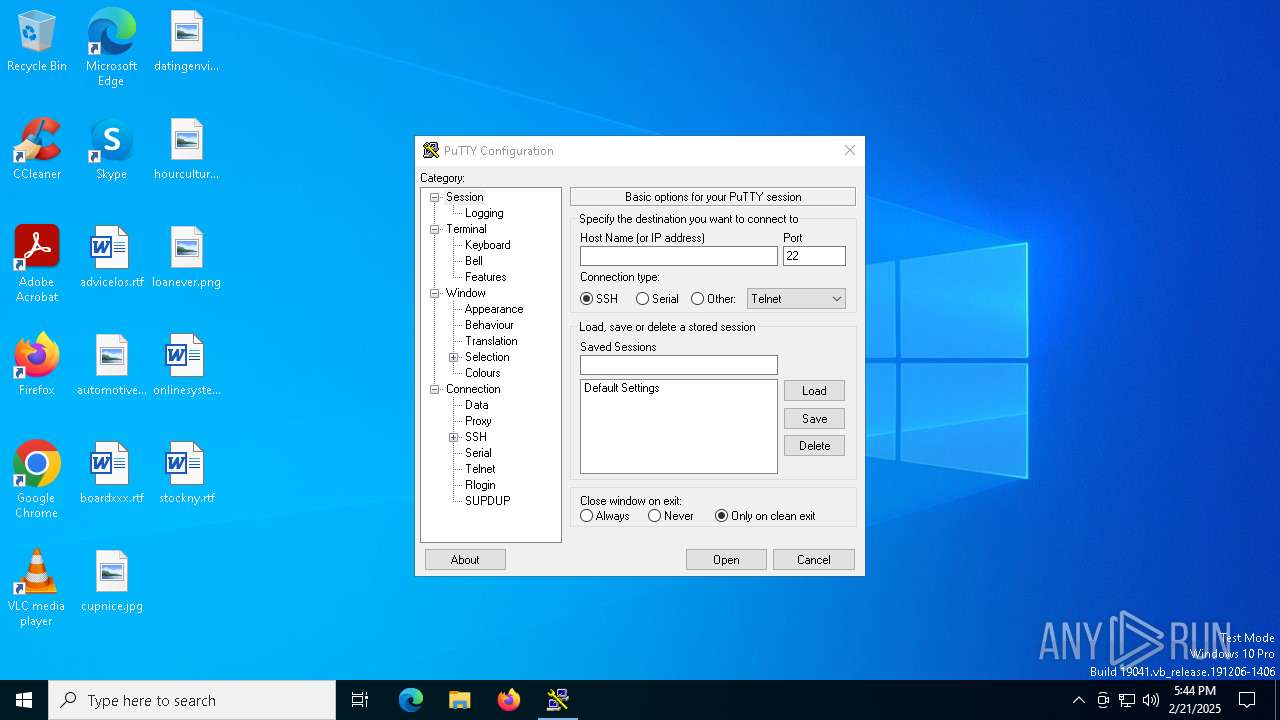
PUTTY has been detected
- putty.exe (PID: 1448)
- putty.exe (PID: 1448)
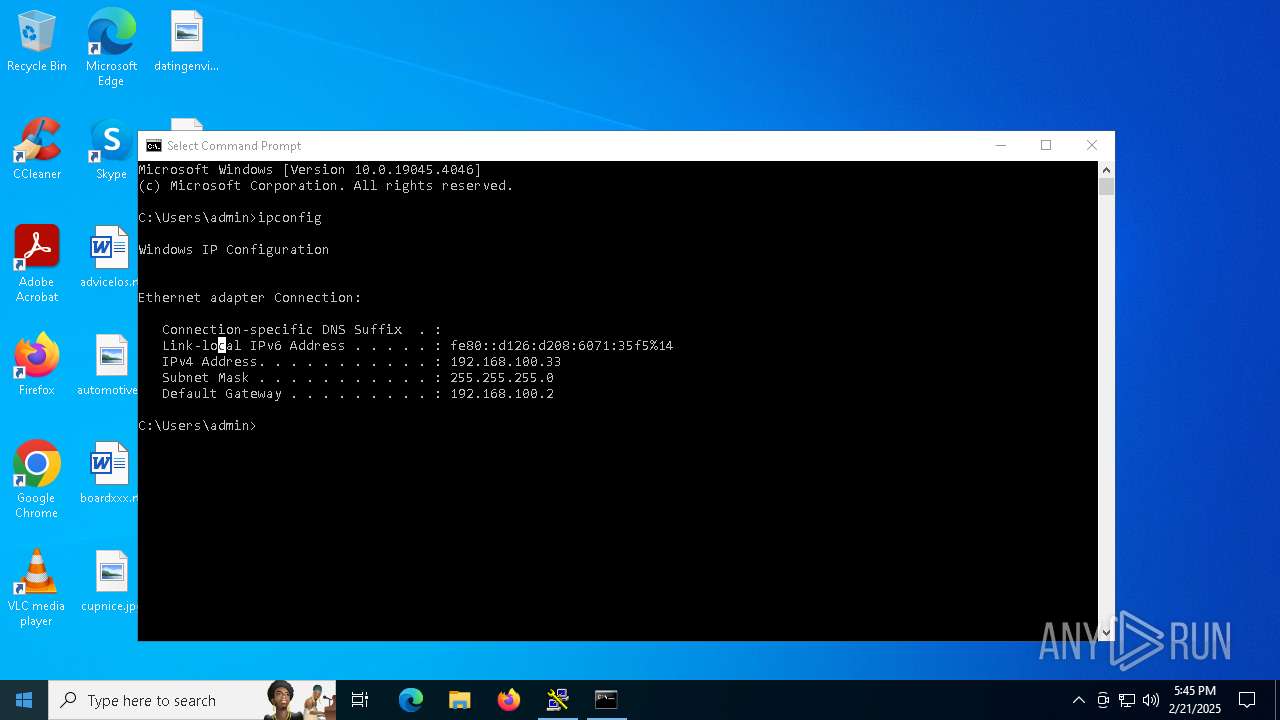
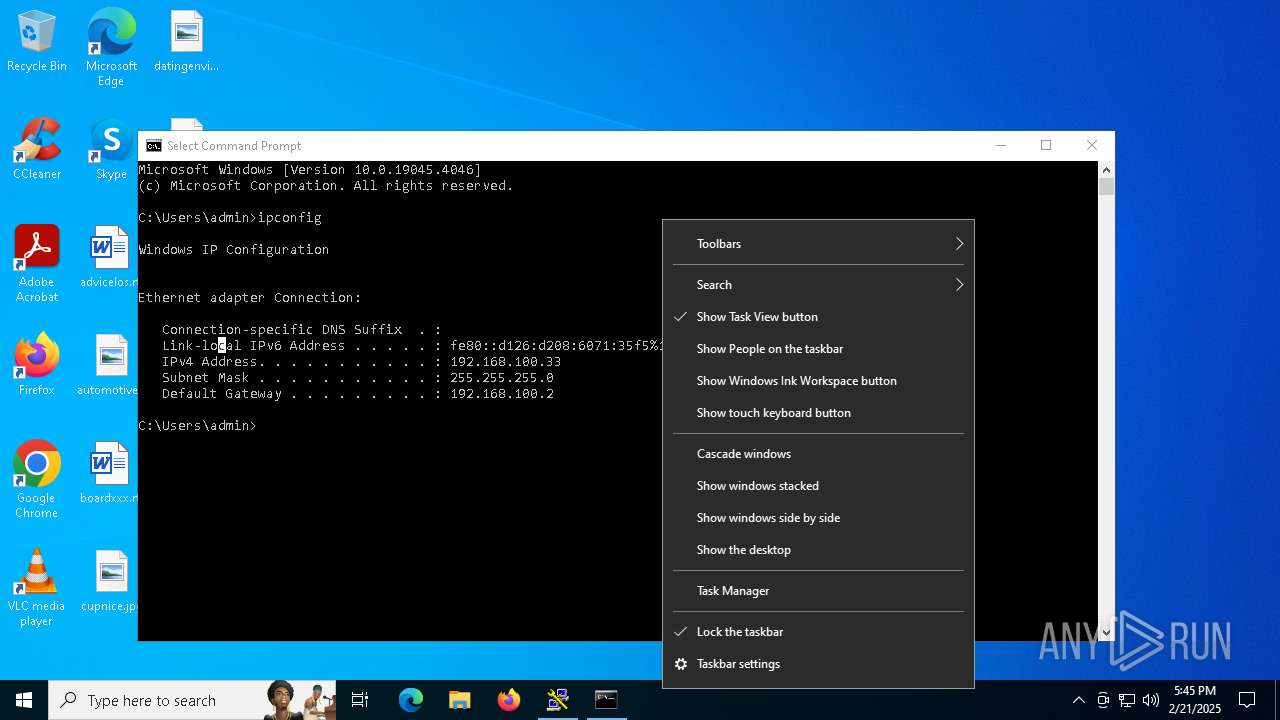
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 3052)
INFO
Checks supported languages
- putty.exe (PID: 1448)
- SearchApp.exe (PID: 5064)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
The sample compiled with english language support
- putty.exe (PID: 1448)
Manual execution by a user
- Taskmgr.exe (PID: 6508)
- Taskmgr.exe (PID: 6568)
- cmd.exe (PID: 3052)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6568)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Reads the computer name
- putty.exe (PID: 1448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:04:06 09:45:11+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 950784 |
| InitializedDataSize: | 330752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbaf04 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.81.0.0 |
| ProductVersionNumber: | 0.81.0.0 |
| FileFlagsMask: | 0x000b |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | Simon Tatham |
| ProductName: | PuTTY suite |
| FileDescription: | SSH, Telnet, Rlogin, and SUPDUP client |
| InternalName: | PuTTY |
| OriginalFileName: | PuTTY |
| FileVersion: | Release 0.81 (without embedded help) |
| ProductVersion: | Release 0.81 |
| LegalCopyright: | Copyright © 1997-2024 Simon Tatham. |
Total processes
137
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | "C:\Users\admin\AppData\Local\Temp\putty.exe" | C:\Users\admin\AppData\Local\Temp\putty.exe | explorer.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Version: Release 0.81 (without embedded help) Modules
| |||||||||||||||
| 3032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3052 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4540 | ipconfig | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6508 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6568 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 814
Read events
6 734
Write events
76
Delete events
4
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 50111 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 00001CEB8C428884DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 000083A291428884DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | CortanaStateLastRun |
Value: 86BBB86700000000 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
Executable files
0
Suspicious files
52
Text files
200
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\Init[1].htm | html | |
MD5:6E9DD214EA5B5B5973C1800E0FA3B01A | SHA256:EC6C8D420054F5401E2CA4D816757E4713C802D75575491B5DD11CC3FF172602 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\T41VsZTCWh5KzqP27hKoYroVjVs[1].js | binary | |
MD5:3D0A1ABADD5D1CB4E056E5A4C025CEAB | SHA256:5CC48ECA4DA0C9F1B1BA88BDD3C944E74DE80CE91D885A28879C6F1CABF41BC5 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\-F7bYnjk9S0ADBYML9L8EdympNE.br[1].js | binary | |
MD5:4AB990A76783365262550A7F0BD63627 | SHA256:DE10DD0F9F06597A855DCB3D3517830CA8D599BA340DE2814250A42AEAD4FCBD | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\vOJNaIfAXvJzmnBm845ss-M9YR8[1].css | text | |
MD5:87BBB1A289EDC24C9F06B88229765467 | SHA256:85B291C46F9D1EEEC71DB839F649D748F48B203EA836F3ACE3B9B761947D960C | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\-iNIzuEypRdgRJ6xnyVHizZ3bpM.br[1].js | binary | |
MD5:E86ABEFE45E62F7E2F865D8A344D0B6F | SHA256:5D54790C856CE13811590E18AC3B0ACEEFEFB61258852490F4C5C60748365E89 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\QNBBNqWD9F_Blep-UqQSqnMp-FI[1].css | text | |
MD5:77373397A17BD1987DFCA2E68D022ECF | SHA256:A319AF2E953E7AFDA681B85A62F629A5C37344AF47D2FCD23AB45E1D99497F13 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:29DE55D0A7A581B230CC2D70686CD03A | SHA256:D9F161C1FE8751953E4F3819993C16C2A61A0121B527E09862C34C89E7B6C677 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\0u2b9EXo8LdXut1MFm4AD0phBuM.br[1].js | binary | |
MD5:8C0F73D4C854DC52B555898FEF7EDB54 | SHA256:B652F917E744E7A4EADB5DF108D622FD18C793E80445FAA69B1BFFC97BE2529E | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\2u1i5bXJCKdk4jOb70d5CjAHxg4[1].css | text | |
MD5:D6F7358414188BB4B9713ABD942B775B | SHA256:C457B847A6C6EDC68E5F95E573F8B71CCBEE388007F0DA5984BF8B143DB5E619 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
42
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3188 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2736 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |