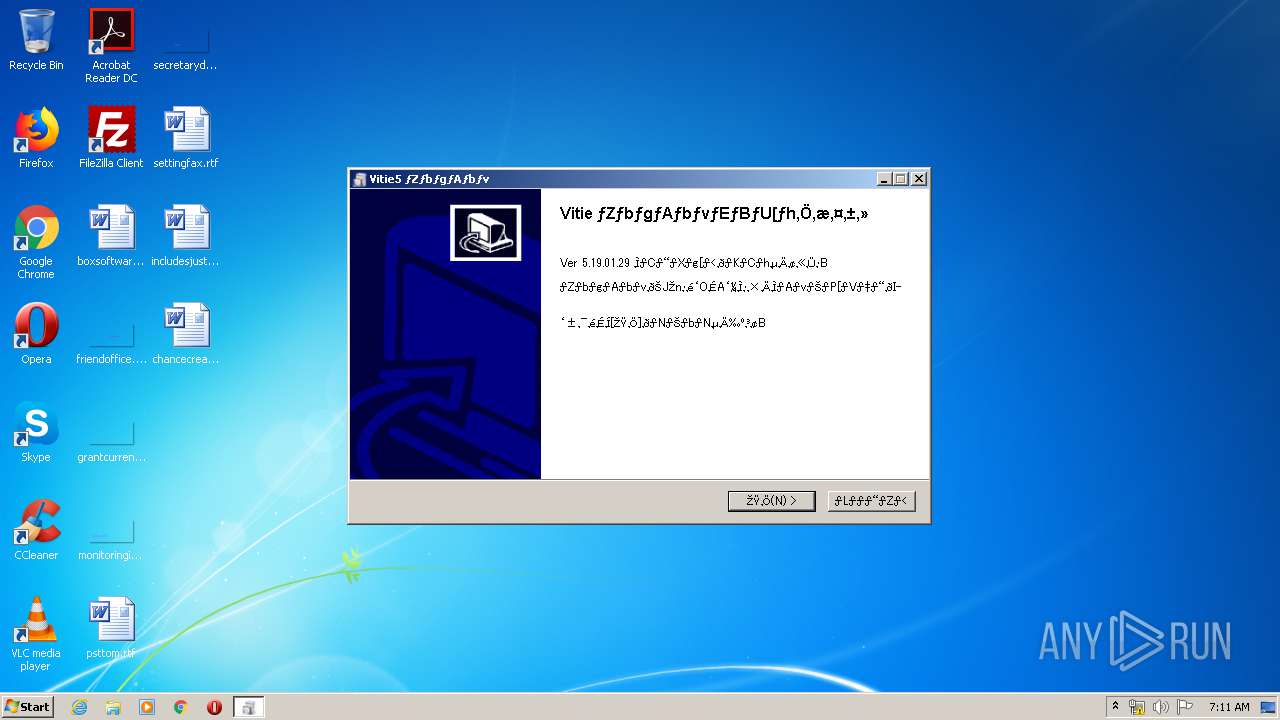
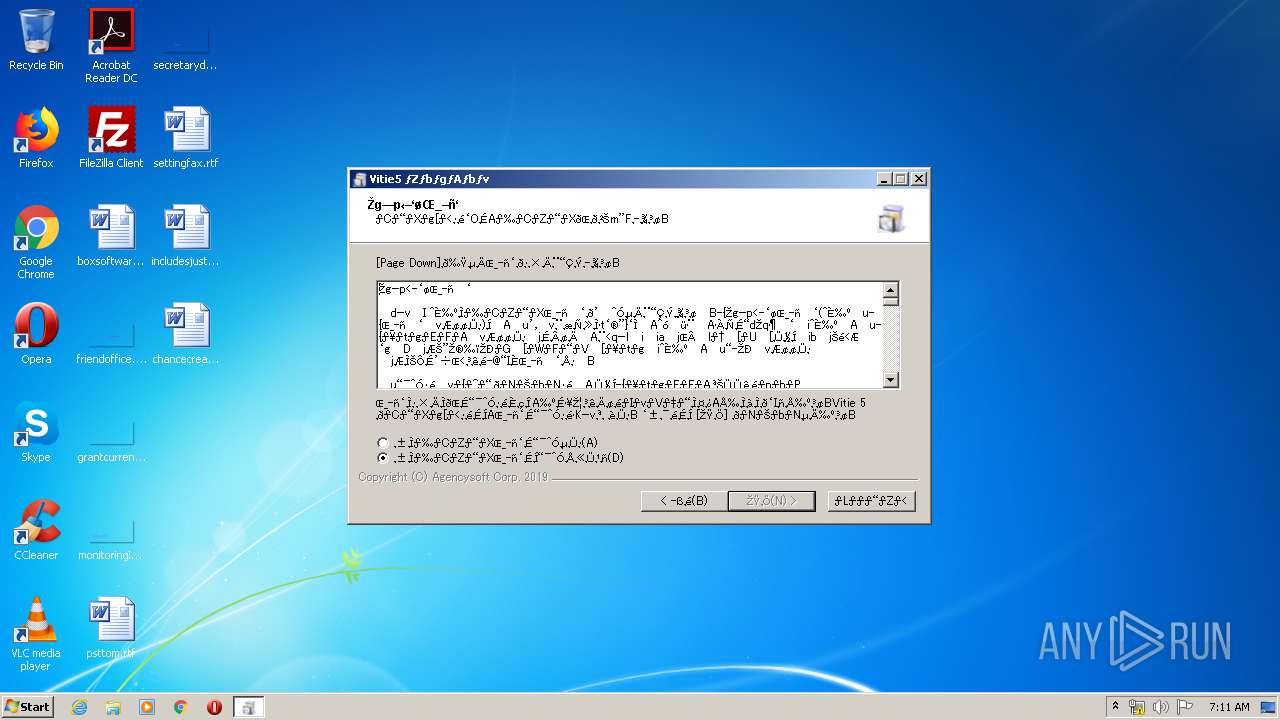
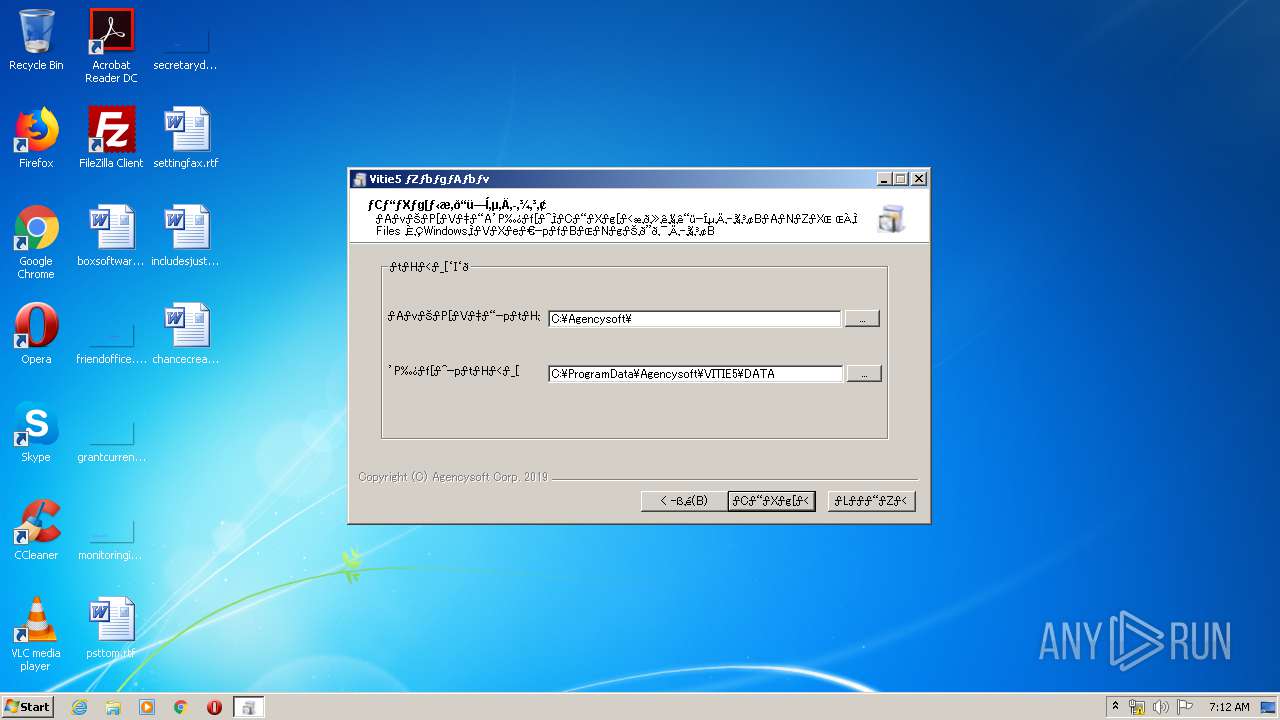
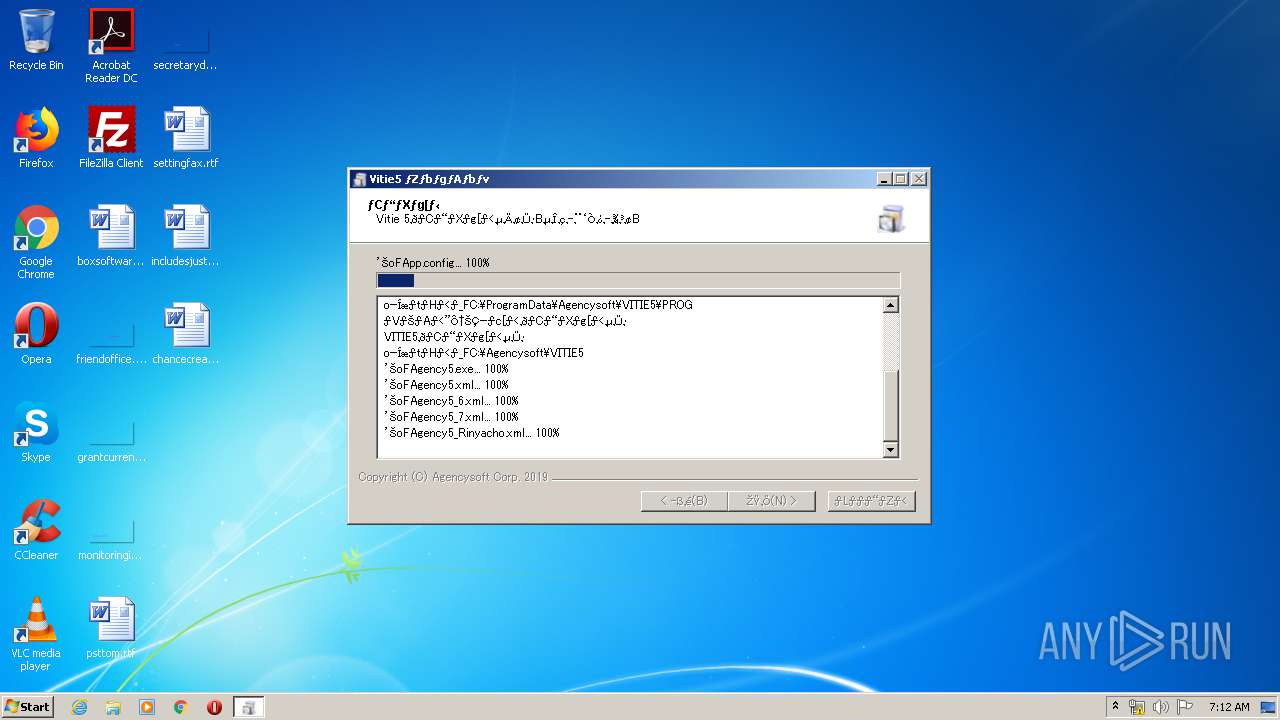
| download: | ITADAKI-2019-EVA.exe |
| Full analysis: | https://app.any.run/tasks/06ab6c06-66d3-481d-a569-3ebf7bbc80db |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2020, 07:08:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 87A86A35124D5E4CE3C06B3AD4520476 |
| SHA1: | 4ADA1DBF37E099FD7FBE17C442EE506BF490063C |
| SHA256: | 66C685FEAF29825EB234D0921F3E231AB5C1044D495069FCE4077CE51DF59CC5 |
| SSDEEP: | 786432:M45YBYcnK3XsqTfLTY4sp25cVdQ6H8C33b+62U:Z56lGcqLLTYq5GVH8C3L+2 |
MALICIOUS
Loads dropped or rewritten executable
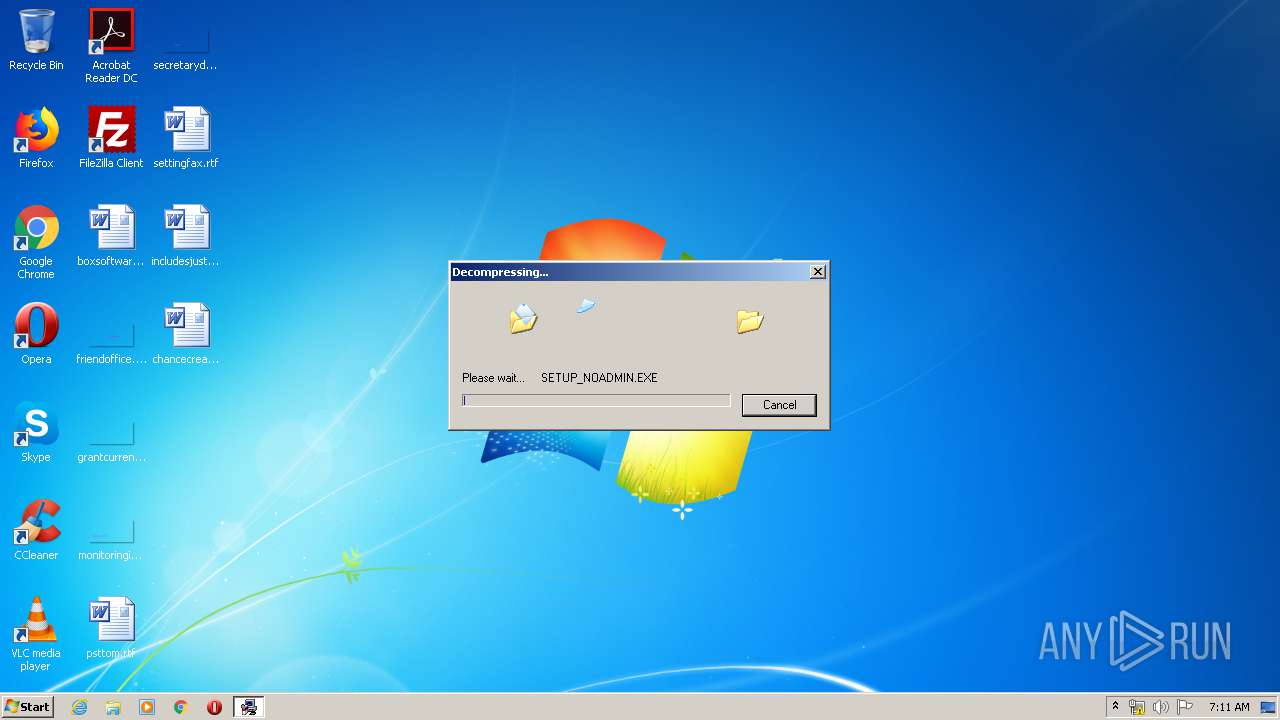
- SETUP_NOADMIN.EXE (PID: 2920)
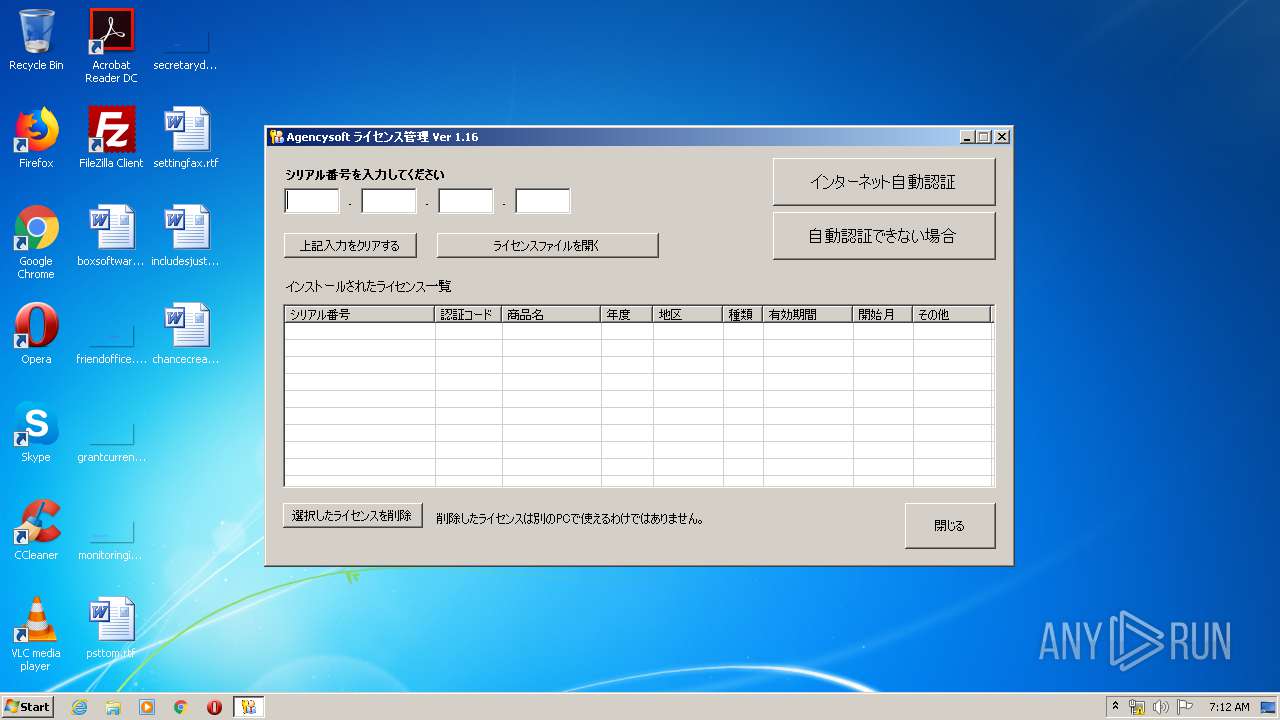
- Agency5.exe (PID: 2400)
- vtauth.exe (PID: 376)
Application was dropped or rewritten from another process
- SETUP_NOADMIN.EXE (PID: 2920)
- nsB2AA.tmp (PID: 2184)
- nsAE71.tmp (PID: 316)
- nsAF0E.tmp (PID: 3932)
- nsAF9C.tmp (PID: 3848)
- nsB3B4.tmp (PID: 2584)
- nsB58B.tmp (PID: 924)
- nsB88A.tmp (PID: 2804)
- nsB4AF.tmp (PID: 4052)
- nsE642.tmp (PID: 1708)
- nsE7AA.tmp (PID: 3404)
- nsE903.tmp (PID: 2728)
- nsEA5C.tmp (PID: 2724)
- nsEBA5.tmp (PID: 2080)
- Agency5.exe (PID: 2400)
- vtauth.exe (PID: 376)
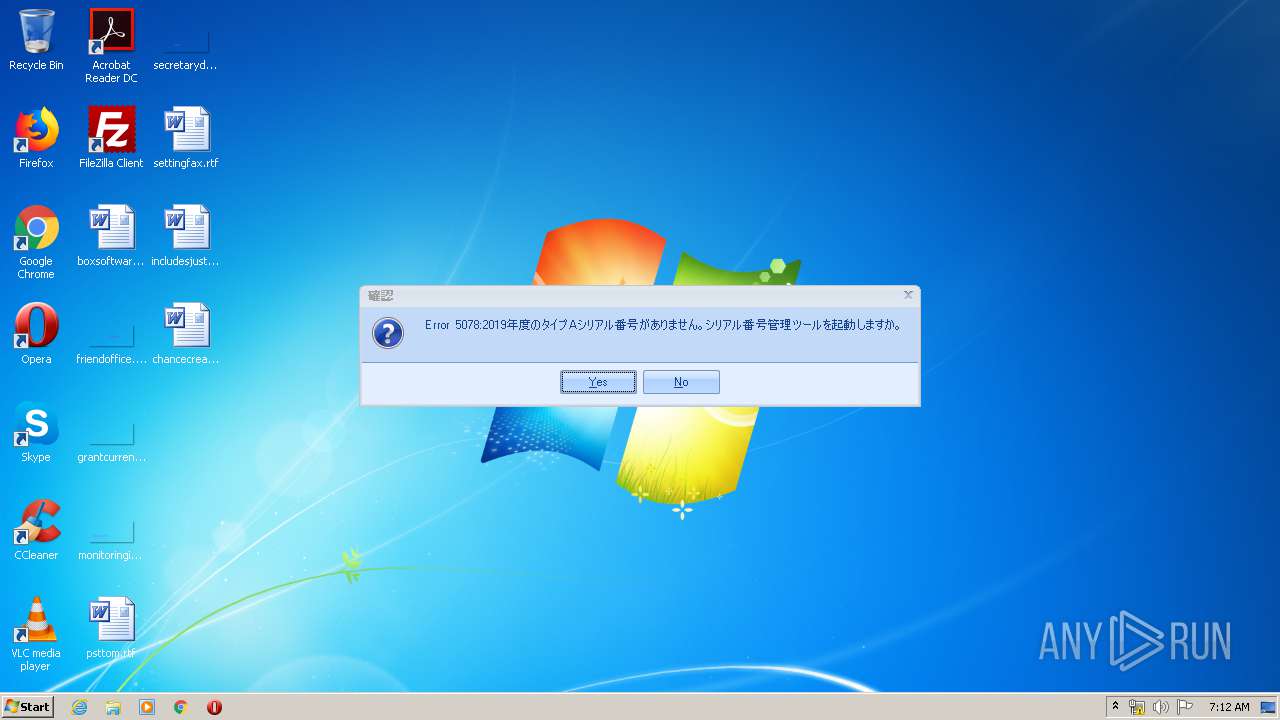
Drops phishing PDF (generic)
- SETUP_NOADMIN.EXE (PID: 2920)
SUSPICIOUS
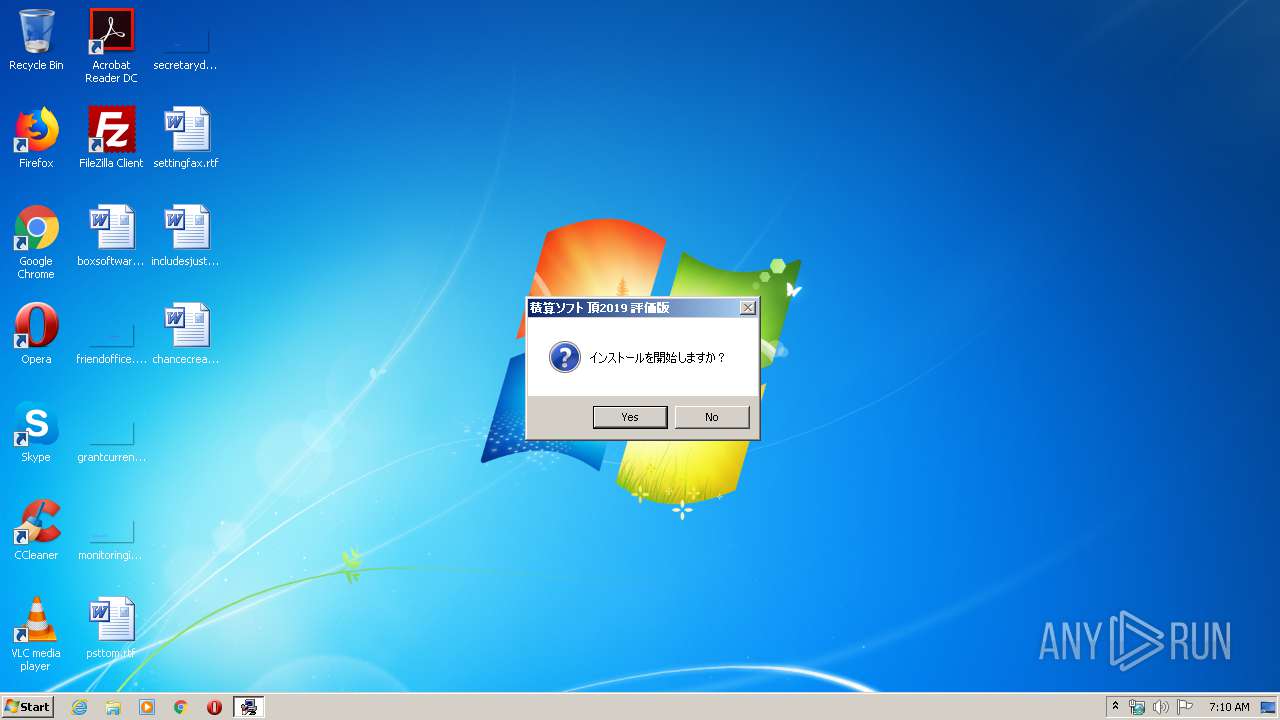
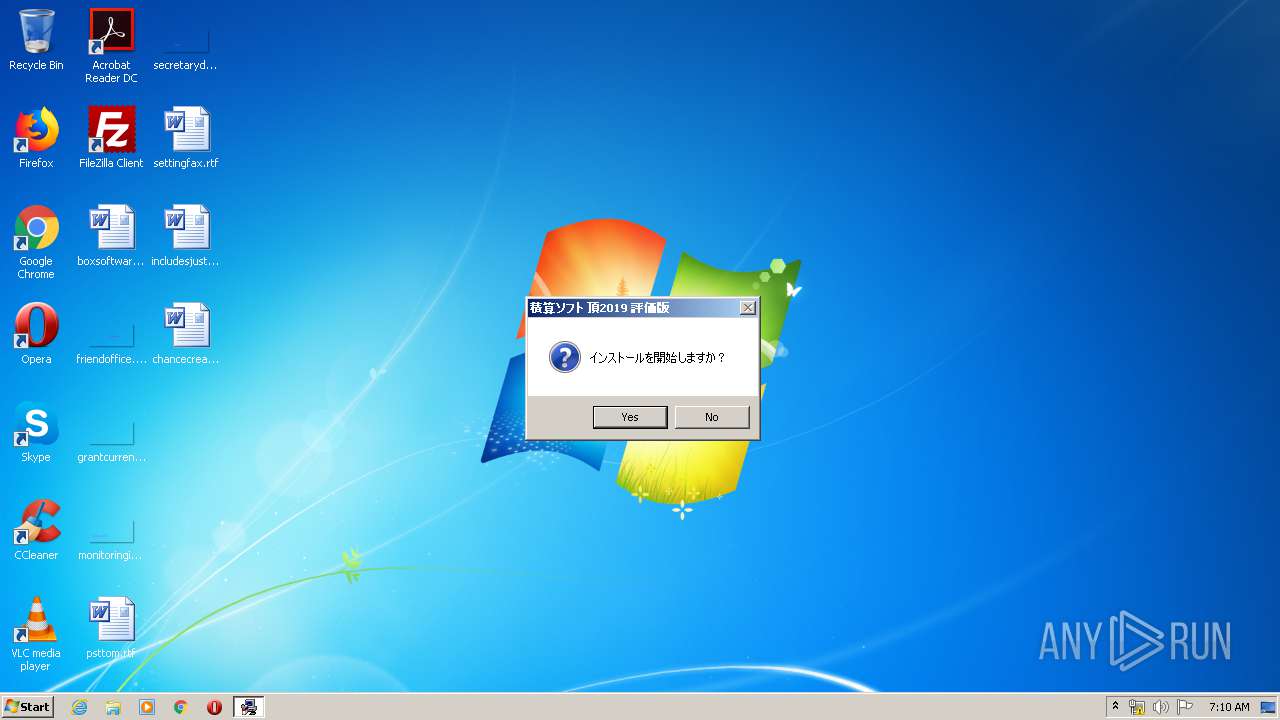
Starts application with an unusual extension
- SETUP_NOADMIN.EXE (PID: 2920)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2580)
- nsB2AA.tmp (PID: 2184)
- cmd.exe (PID: 3356)
- nsAF0E.tmp (PID: 3932)
- cmd.exe (PID: 3584)
- nsB3B4.tmp (PID: 2584)
- nsB4AF.tmp (PID: 4052)
- nsAF9C.tmp (PID: 3848)
- nsAE71.tmp (PID: 316)
- cmd.exe (PID: 3092)
- nsB58B.tmp (PID: 924)
- nsE903.tmp (PID: 2728)
- nsB88A.tmp (PID: 2804)
- nsE642.tmp (PID: 1708)
- nsE7AA.tmp (PID: 3404)
- nsEA5C.tmp (PID: 2724)
- nsEBA5.tmp (PID: 2080)
Creates files in the program directory
- SETUP_NOADMIN.EXE (PID: 2920)
- cmd.exe (PID: 2800)
- Agency5.exe (PID: 2400)
- vtauth.exe (PID: 376)
Executable content was dropped or overwritten
- ITADAKI-2019-EVA.exe (PID: 2868)
- SETUP_NOADMIN.EXE (PID: 2920)
- xcopy.exe (PID: 1352)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1084)
- cmd.exe (PID: 2908)
Modifies the open verb of a shell class
- SETUP_NOADMIN.EXE (PID: 2920)
Creates a software uninstall entry
- SETUP_NOADMIN.EXE (PID: 2920)
INFO
Dropped object may contain Bitcoin addresses
- cmd.exe (PID: 2800)
- SETUP_NOADMIN.EXE (PID: 2920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:08:22 01:15:54+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 36864 |
| InitializedDataSize: | 61440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x334a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.0.0 |
| ProductVersionNumber: | 6.0.6.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | |
| CompanyName: | pon software |
| FileDescription: | Win32 Zip Self-Extractor |
| FileVersion: | 6.06 |
| InternalName: | deczipW |
| LegalCopyright: | Copyright(c) 2001-2012 by pon software |
| LegalTrademarks: | - |
| OriginalFileName: | deczipW.exe |
| PrivateBuild: | - |
| ProductName: | decode zip unicode version. |
| ProductVersion: | 6.06 |
| SpecialBuild: | - |
Total processes
97
Monitored processes
45
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\nsAE71.tmp" cmd.exe /c del "C:\ProgramData\Agencysoft\VITIE5\PROG\SYS*.VT5" /q | C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\nsAE71.tmp | — | SETUP_NOADMIN.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 376 | "C:\Agencysoft\VITIE5\vtauth.exe" | C:\Agencysoft\VITIE5\vtauth.exe | — | Agency5.exe | |||||||||||
User: admin Company: Agencysoft Corp. Integrity Level: HIGH Description: vtauth Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 604 | cacls "C:\ProgramData\Agencysoft" /t /g everyone:f | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\nsB58B.tmp" cmd.exe /c netsh advfirewall firewall delete rule name="vitie5b" protocol=TCP localport=14603 | C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\nsB58B.tmp | — | SETUP_NOADMIN.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1084 | cmd.exe /c netsh advfirewall firewall delete rule name="vitie5b" protocol=TCP localport=14603 | C:\Windows\system32\cmd.exe | — | nsB58B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | xcopy "C:\Agencysoft\VITIE5\TEMP\SETUP_NOADMIN.EXE" "C:\Agencysoft\Vitie5\ƒŠƒJƒoƒŠ\" /D /Y | C:\Windows\system32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1460 | C:\Windows\system32\cmd.exe /S /D /c" echo y" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1704 | cmd.exe /c rd /s /q "C:\Agencysoft\Vitie5\ƒŠƒJƒoƒŠ" | C:\Windows\system32\cmd.exe | — | nsE642.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1708 | "C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\nsE642.tmp" cmd.exe /c rd /s /q "C:\Agencysoft\Vitie5\ƒŠƒJƒoƒŠ" | C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\nsE642.tmp | — | SETUP_NOADMIN.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1812 | xcopy "C:\Agencysoft\VITIE5\TEMP\Extra\*.*" "C:\Agencysoft\Vitie5\" /D /Y | C:\Windows\system32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
473
Read events
349
Write events
124
Delete events
0
Modification events
| (PID) Process: | (2868) ITADAKI-2019-EVA.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2868) ITADAKI-2019-EVA.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2920) SETUP_NOADMIN.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Agencysoft |
| Operation: | write | Name: | TEST |
Value: testme | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-1 |
Value: IPsec Relying Party | |||
| (PID) Process: | (2084) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-2 |
Value: Provides IPsec based enforcement for Network Access Protection | |||
Executable files
60
Suspicious files
53
Text files
235
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2868 | ITADAKI-2019-EVA.exe | C:\Agencysoft\VITIE5\TEMP\SETUP_NOADMIN.EXE | executable | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\ProgramData\Agencysoft\VITIE5\PROG\path.ini | text | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\ProgramData\Agencysoft\VITIE5\PROG\comm.luft | mdw | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\ProgramData\Agencysoft\VITIE5\PROG\vitie5conf.xml | xml | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\Agencysoft\VITIE5\Agency5.exe | executable | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\Agencysoft\VITIE5\Agency5.xml | xml | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\Agencysoft\VITIE5\Agency5_6.xml | xml | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\Agencysoft\VITIE5\Agency5_7.xml | xml | |
MD5:— | SHA256:— | |||
| 2920 | SETUP_NOADMIN.EXE | C:\Users\admin\AppData\Local\Temp\nse5AE1.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report