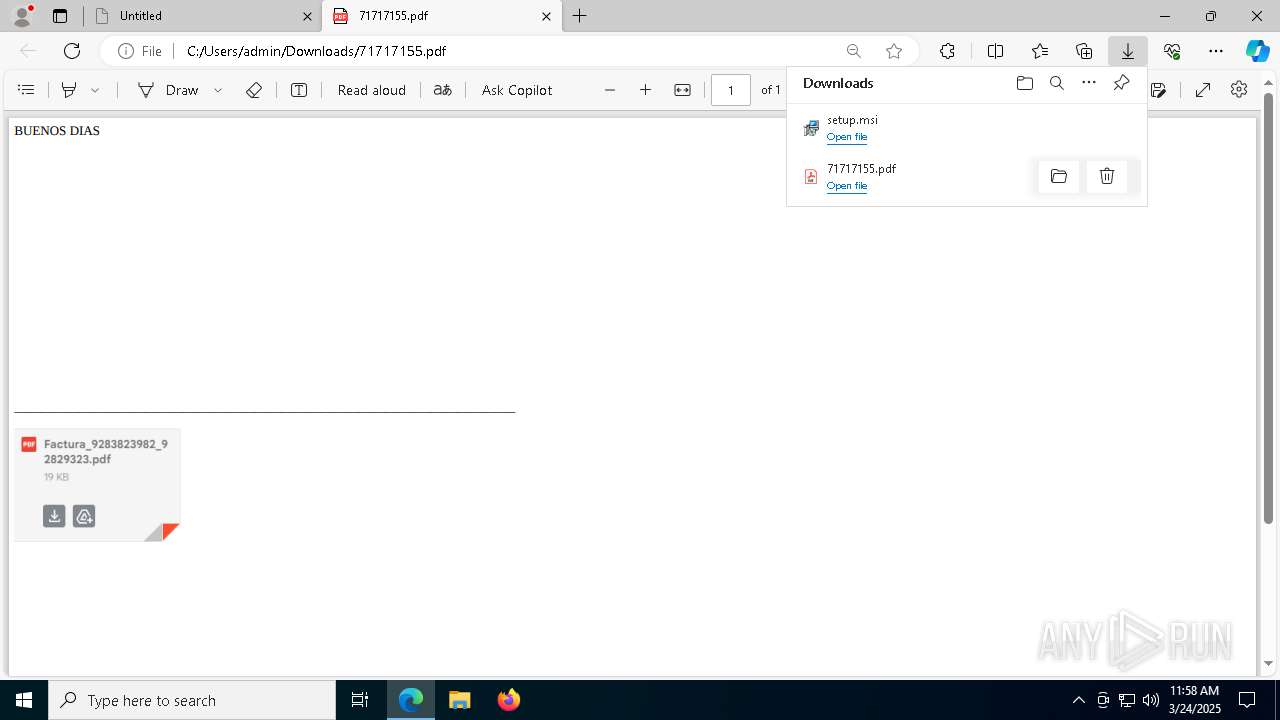
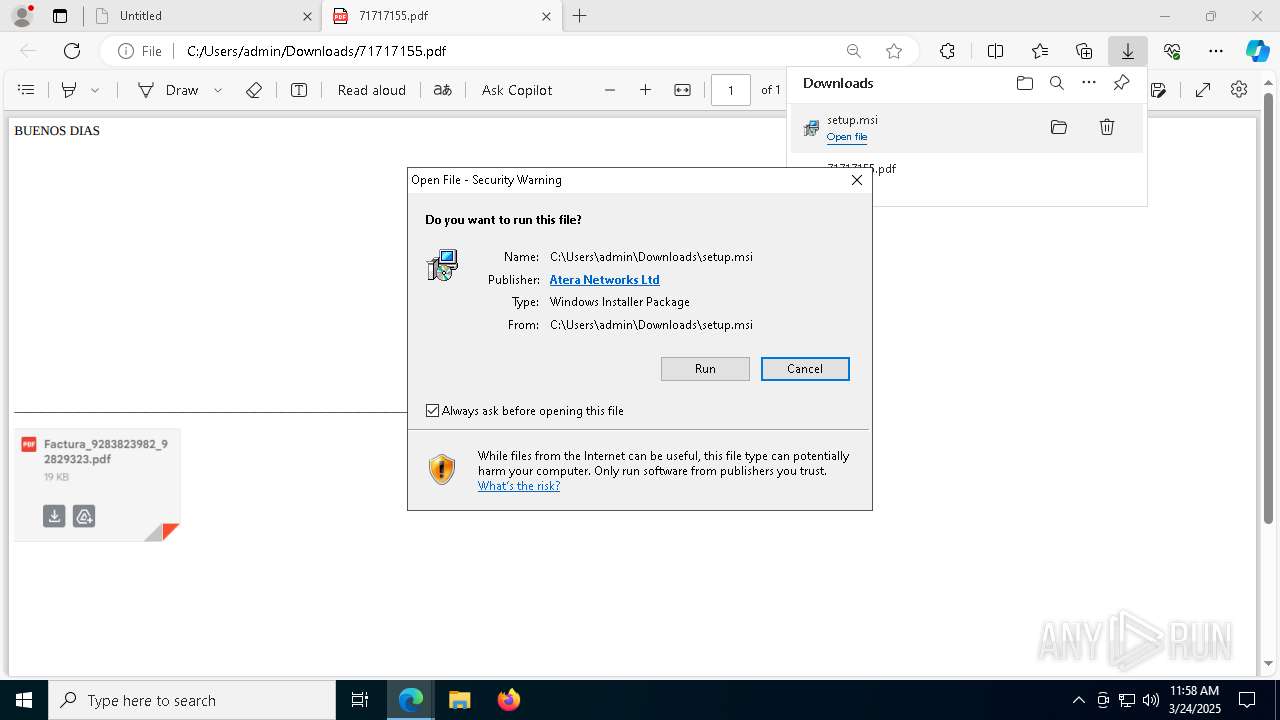
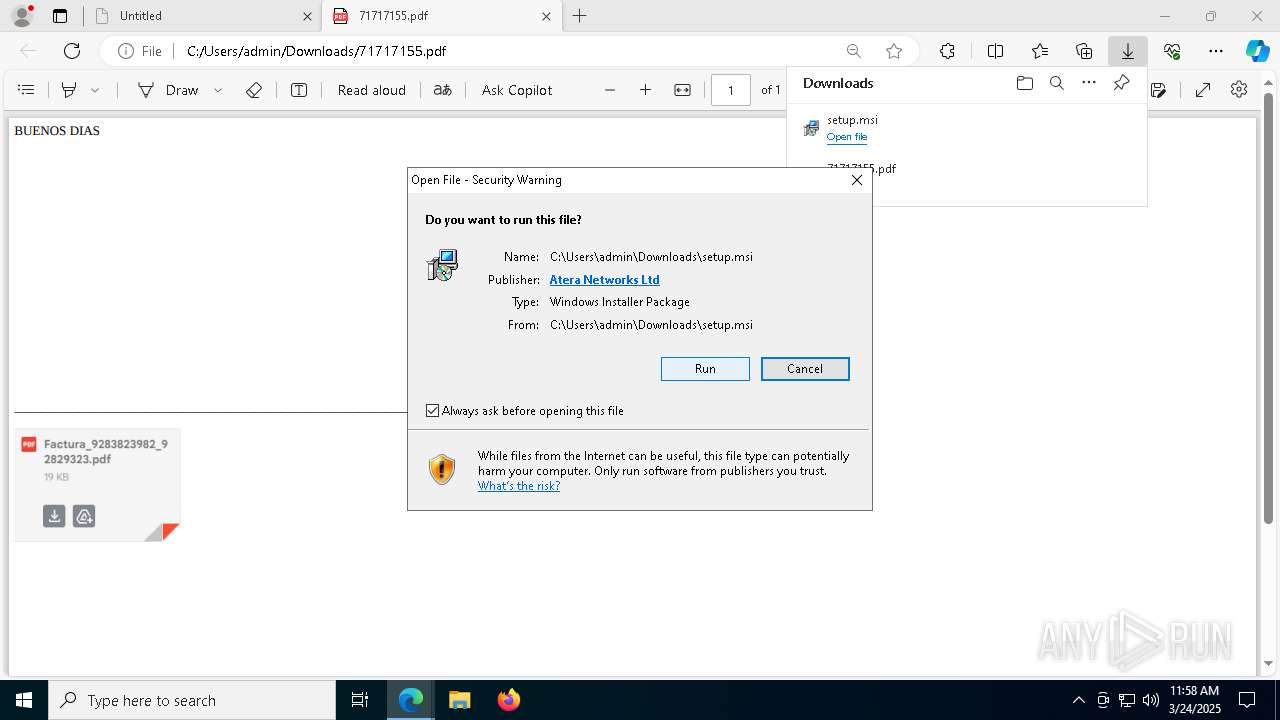
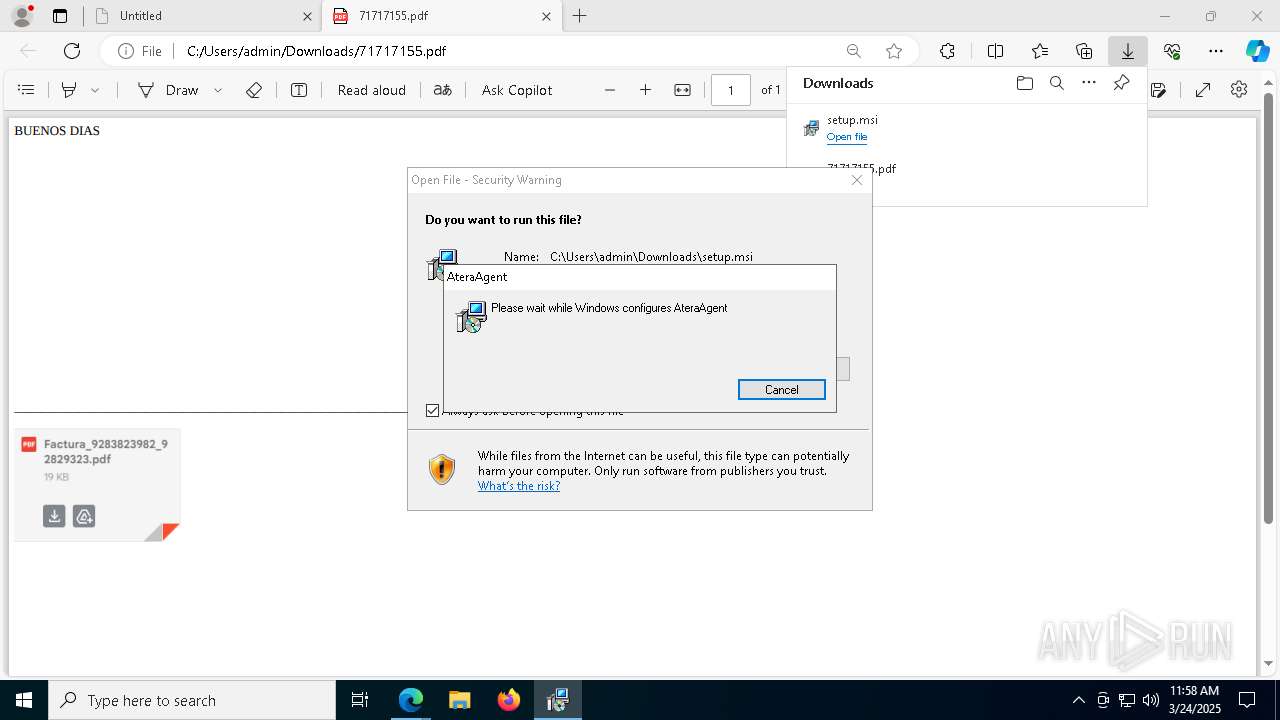
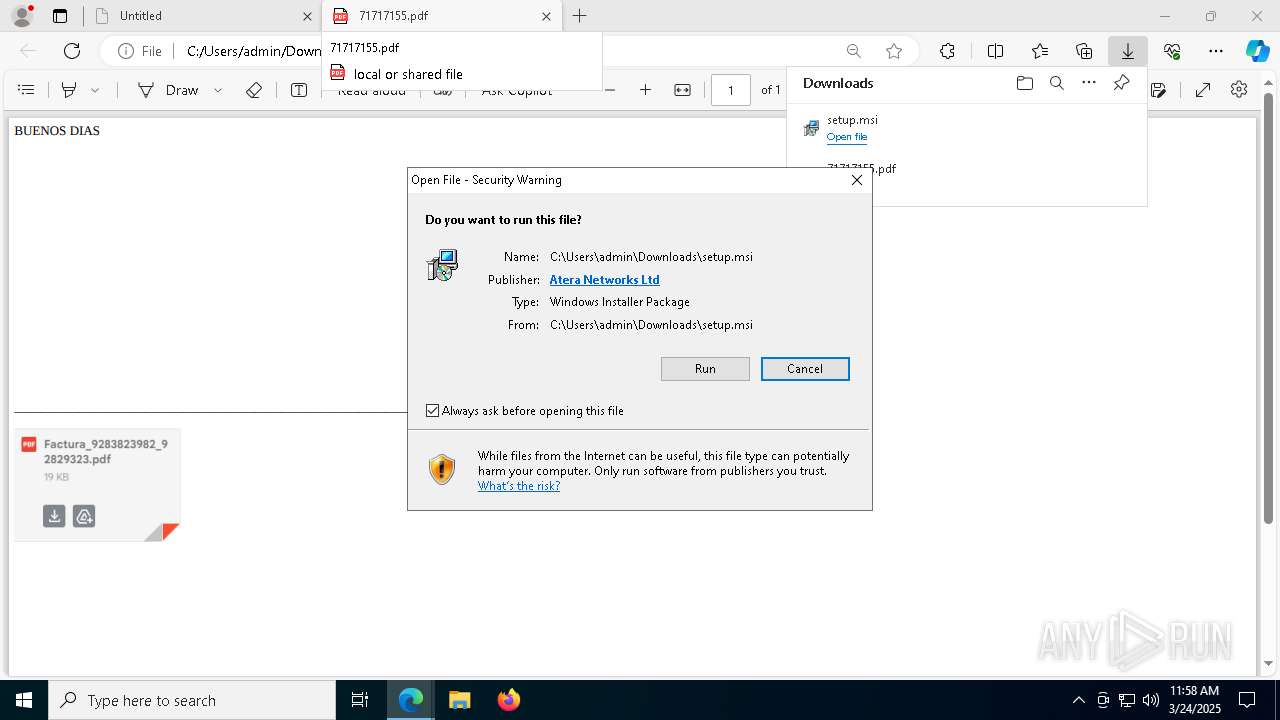
| URL: | https://hidrive.ionos.com/api/sharelink/download?id=bzjHzG4aa |
| Full analysis: | https://app.any.run/tasks/e0407f91-d91e-4929-9ace-6420792d855e |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 11:57:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FC631F41183A900F0E4121BB8F7A7BA4 |
| SHA1: | D217394DFFE8B6A0168E8A77F330ECF833702A2E |
| SHA256: | 66B750D28FA36EDA03D34E4D32824E77674557F6D3843116B88C7896F4E37E99 |
| SSDEEP: | 3:N8whMTAJyK09KBjE0lEEE:2whMTiyK00BjOEE |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 5972)
- msiexec.exe (PID: 2908)
- net.exe (PID: 8664)
- msiexec.exe (PID: 9464)
- net.exe (PID: 9848)
Bypass execution policy to execute commands
- powershell.exe (PID: 8028)
- powershell.exe (PID: 10044)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 2800)
- AgentPackageAgentInformation.exe (PID: 2596)
Executing a file with an untrusted certificate
- SRSelfSignCertUtil.exe (PID: 1852)
ATERA mutex has been found
- AgentPackageMonitoring.exe (PID: 8644)
Changes the autorun value in the registry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 8740)
- AteraAgent.exe (PID: 5936)
- AteraAgent.exe (PID: 1540)
- SRService.exe (PID: 9880)
- AteraAgent.exe (PID: 7104)
Executable content was dropped or overwritten
- rundll32.exe (PID: 8584)
- rundll32.exe (PID: 8772)
- rundll32.exe (PID: 4112)
- rundll32.exe (PID: 8048)
- AteraAgent.exe (PID: 5936)
- csc.exe (PID: 8612)
- SplashtopStreamer.exe (PID: 4208)
- PreVerCheck.exe (PID: 6564)
- AteraAgent.exe (PID: 1540)
- SetupUtil.exe (PID: 3300)
- csc.exe (PID: 4528)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageTicketing.exe (PID: 4728)
- rundll32.exe (PID: 9500)
- rundll32.exe (PID: 9844)
- AgentPackageRuntimeInstaller.exe (PID: 9044)
- 8-0-11.exe (PID: 10004)
- 8-0-11.exe (PID: 7824)
- rundll32.exe (PID: 9544)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
- rundll32.exe (PID: 9284)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 8584)
- AgentPackageAgentInformation.exe (PID: 4268)
- AteraAgent.exe (PID: 5936)
- AteraAgent.exe (PID: 1540)
- AgentPackageAgentInformation.exe (PID: 2800)
- AgentPackageInternalPoller.exe (PID: 1628)
- AgentPackageMarketplace.exe (PID: 9100)
- AgentPackageTicketing.exe (PID: 4728)
- rundll32.exe (PID: 9544)
- AgentPackageMonitoring.exe (PID: 8644)
- AgentPackageAgentInformation.exe (PID: 2596)
- AteraAgent.exe (PID: 7104)
- rundll32.exe (PID: 9284)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 2908)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 5972)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 8572)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 1240)
- cmd.exe (PID: 7972)
- msiexec.exe (PID: 9464)
Process drops legitimate windows executable
- msiexec.exe (PID: 8876)
- AteraAgent.exe (PID: 5936)
- msedge.exe (PID: 4868)
- msedge.exe (PID: 7420)
- AteraAgent.exe (PID: 1540)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- 8-0-11.exe (PID: 10004)
- 8-0-11.exe (PID: 7824)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
ATERAAGENT has been detected
- AteraAgent.exe (PID: 6392)
- AteraAgent.exe (PID: 5936)
- AteraAgent.exe (PID: 1540)
- AteraAgent.exe (PID: 10124)
- AteraAgent.exe (PID: 3884)
- AteraAgent.exe (PID: 7104)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 6392)
- AteraAgent.exe (PID: 1540)
- AgentPackageAgentInformation.exe (PID: 2800)
- AteraAgent.exe (PID: 7104)
Reads the date of Windows installation
- AteraAgent.exe (PID: 5936)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 5936)
- AteraAgent.exe (PID: 1540)
- AteraAgent.exe (PID: 7104)
Restarts service on failure
- sc.exe (PID: 2192)
- sc.exe (PID: 8172)
- sc.exe (PID: 7316)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 2800)
- cmd.exe (PID: 3968)
- AgentPackageAgentInformation.exe (PID: 2596)
- cmd.exe (PID: 9660)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8612)
- csc.exe (PID: 4528)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 2800)
- msiexec.exe (PID: 7744)
- SetupUtil.exe (PID: 3300)
- AgentPackageRuntimeInstaller.exe (PID: 9044)
- AgentPackageAgentInformation.exe (PID: 2596)
The process executes VB scripts
- cmd.exe (PID: 8592)
- cmd.exe (PID: 4376)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 2800)
- cmd.exe (PID: 3968)
- AgentPackageAgentInformation.exe (PID: 2596)
- cmd.exe (PID: 9660)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 2800)
- AgentPackageAgentInformation.exe (PID: 2596)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Executes application which crashes
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 4112)
- cscript.exe (PID: 7000)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 8876)
Starts a Microsoft application from unusual location
- 8-0-11.exe (PID: 7824)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
Creates a software uninstall entry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
Starts itself from another location
- 8-0-11.exe (PID: 7824)
INFO
Autorun file from Downloads
- msedge.exe (PID: 4868)
- msedge.exe (PID: 8232)
Application launched itself
- msedge.exe (PID: 4868)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4868)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8876)
- msiexec.exe (PID: 7744)
- msedge.exe (PID: 7420)
- msedge.exe (PID: 4868)
Checks supported languages
- msiexec.exe (PID: 8876)
- msiexec.exe (PID: 8900)
- AteraAgent.exe (PID: 6392)
- AgentPackageAgentInformation.exe (PID: 6652)
- AgentPackageAgentInformation.exe (PID: 2800)
- AgentPackageMonitoring.exe (PID: 7904)
- msiexec.exe (PID: 7744)
- identity_helper.exe (PID: 8588)
- _isE761.exe (PID: 4884)
- SetupUtil.exe (PID: 3300)
- _isEB2.exe (PID: 8420)
- SRSelfSignCertUtil.exe (PID: 1852)
- _isEB2.exe (PID: 2096)
- _is14FC.exe (PID: 9408)
- _is14FC.exe (PID: 9612)
- _is14FC.exe (PID: 9644)
- _isEB2.exe (PID: 5084)
- SRManager.exe (PID: 9912)
- SRFeature.exe (PID: 5452)
- SRUtility.exe (PID: 9372)
- 8-0-11.exe (PID: 10004)
Reads the software policy settings
- msiexec.exe (PID: 7736)
- AteraAgent.exe (PID: 6392)
- AteraAgent.exe (PID: 5936)
- AgentPackageSTRemote.exe (PID: 8404)
- AteraAgent.exe (PID: 1540)
- AgentPackageAgentInformation.exe (PID: 2800)
- SRManager.exe (PID: 9912)
- AgentPackageAgentInformation.exe (PID: 2596)
Manages system restore points
- SrTasks.exe (PID: 8648)
Reads the computer name
- msiexec.exe (PID: 8900)
- identity_helper.exe (PID: 8588)
- AteraAgent.exe (PID: 6392)
- AgentPackageMonitoring.exe (PID: 7904)
- _isE761.exe (PID: 4884)
- _isEB2.exe (PID: 8420)
- AgentPackageMarketplace.exe (PID: 9100)
- _isEB2.exe (PID: 2096)
- _isEB2.exe (PID: 5084)
- _is14FC.exe (PID: 9408)
- _is14FC.exe (PID: 9644)
- _is14FC.exe (PID: 9612)
Create files in a temporary directory
- rundll32.exe (PID: 8772)
Reads the machine GUID from the registry
- msiexec.exe (PID: 8876)
- AteraAgent.exe (PID: 6392)
- AteraAgent.exe (PID: 5936)
- AgentPackageAgentInformation.exe (PID: 4268)
- AteraAgent.exe (PID: 1540)
- AgentPackageMonitoring.exe (PID: 7904)
- msiexec.exe (PID: 7744)
- AgentPackageHeartbeat.exe (PID: 5408)
- AgentPackageTicketing.exe (PID: 4728)
- AgentPackageMarketplace.exe (PID: 9100)
- AteraAgent.exe (PID: 10124)
The sample compiled with english language support
- rundll32.exe (PID: 8772)
- rundll32.exe (PID: 4112)
- rundll32.exe (PID: 8048)
- AteraAgent.exe (PID: 5936)
- msiexec.exe (PID: 8876)
- PreVerCheck.exe (PID: 6564)
- msiexec.exe (PID: 7744)
- AteraAgent.exe (PID: 1540)
- SetupUtil.exe (PID: 3300)
- rundll32.exe (PID: 9844)
- 8-0-11.exe (PID: 10004)
- 8-0-11.exe (PID: 7824)
- rundll32.exe (PID: 9500)
- rundll32.exe (PID: 9544)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
- rundll32.exe (PID: 9284)
Disables trace logs
- rundll32.exe (PID: 8584)
- AgentPackageAgentInformation.exe (PID: 4268)
- AteraAgent.exe (PID: 1540)
Creates a software uninstall entry
- msiexec.exe (PID: 8876)
Creates files in the program directory
- AteraAgent.exe (PID: 6392)
- AteraAgent.exe (PID: 5936)
- AgentPackageSTRemote.exe (PID: 8404)
- AteraAgent.exe (PID: 1540)
- SRAgent.exe (PID: 10200)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 7100)
- AteraAgent.exe (PID: 3884)
Reads Environment values
- AteraAgent.exe (PID: 5936)
- AgentPackageMonitoring.exe (PID: 7904)
- identity_helper.exe (PID: 8588)
- AgentPackageTicketing.exe (PID: 4728)
- AteraAgent.exe (PID: 10124)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8896)
- powershell.exe (PID: 8228)
SPLASHTOP has been detected
- msiexec.exe (PID: 8876)
- msiexec.exe (PID: 7744)
- SRSelfSignCertUtil.exe (PID: 1852)
- msiexec.exe (PID: 7744)
- SetupUtil.exe (PID: 3300)
- SRService.exe (PID: 684)
- SRManager.exe (PID: 9912)
- SRManager.exe (PID: 9912)
- SRFeature.exe (PID: 5452)
- SRAppPB.exe (PID: 10220)
- SRServer.exe (PID: 10164)
- SRUtility.exe (PID: 9372)
- SRAgent.exe (PID: 10200)
- SRServer.exe (PID: 10164)
- SRService.exe (PID: 9880)
- osqueryi.exe (PID: 9832)
- SRAgent.exe (PID: 10200)
- SRVirtualDisplay.exe (PID: 4988)
- SRFeature.exe (PID: 5452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
406
Monitored processes
262
Malicious processes
14
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | C:\WINDOWS\TEMP\{E17AD454-9D1E-4092-B08D-5666C878463F}\_isEB2.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{5E4DF725-138B-4AAE-B1CB-054B0376BB9B} | C:\Windows\Temp\{E17AD454-9D1E-4092-B08D-5666C878463F}\_isEB2.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Flexera Integrity Level: SYSTEM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.122 Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRService.exe" -i | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRService.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Service Exit code: 1066 Version: 3.74.0.16 Modules
| |||||||||||||||
| 812 | powershell.exe -File "C:\Program Files\Microsoft Office\Office16\vNextDiag.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | "msiexec.exe" /i C:\WINDOWS\TEMP\ateraAgentSetup64_1_8_7_2.msi /lv* AteraSetupLog.txt /qn /norestart | C:\Windows\System32\msiexec.exe | — | AgentPackageUpgradeAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 1618 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | C:\WINDOWS\TEMP\{EA2E0714-4DF1-4418-A266-C24979C6C69F}\_isC8FB.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{3A84EF52-EB9B-4EB6-9209-985CAE212752} | C:\Windows\Temp\{EA2E0714-4DF1-4418-A266-C24979C6C69F}\_isC8FB.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Flexera Integrity Level: SYSTEM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.122 Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\Support\SetupUtil.exe" /P ADDUSERINFO /V "sec_opt=0,confirm_d=0,hidewindow=1" | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\Support\SetupUtil.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Setup Utility Exit code: 0 Version: 1.0.4.0 Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=8132 --field-trial-handle=2632,i,6731394920476584010,6328704669548732112,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
128 860
Read events
126 990
Write events
1 675
Delete events
195
Modification events
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2EA11C99AB8F2F00 | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A9BC2999AB8F2F00 | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262992 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C0DF2051-B8B6-495C-9626-87A22FF20071} | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262992 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3A80B560-D528-424A-8723-A4234B7B290D} | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (4868) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
911
Suspicious files
341
Text files
259
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10bc2e.TMP | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10bc2e.TMP | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10bc2e.TMP | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10bc2e.TMP | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10bc2e.TMP | — | |
MD5:— | SHA256:— | |||
| 4868 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
121
DNS requests
81
Threats
56
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4868 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8380 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4868 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4868 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAnTy%2FhDMohv9omwS69%2Fdow%3D | unknown | — | — | whitelisted |
864 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
864 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6392 | AteraAgent.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6392 | AteraAgent.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7420 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4868 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7420 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7420 | msedge.exe | 13.107.246.60:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7420 | msedge.exe | 85.214.3.95:443 | hidrive.ionos.com | Strato AG | DE | malicious |
7420 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
hidrive.ionos.com |
| malicious |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7420 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] WordPress domains and hosting (hidrive .ionos .com) |
7420 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] WordPress domains and hosting (hidrive .ionos .com) |
8584 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5936 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5936 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5936 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5936 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5936 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5936 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
4268 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\WINDOWS\TEMP\unpack\setup.msi (60999680) (Last=0) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::UnPackFiles] FreeSpace:231861051392 FileSize:60999680 (Last=0) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::FindHeader] Sign Size:10376 (Last=0) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::UnPackFiles] (2/5)UnPack file name:C:\WINDOWS\TEMP\unpack\run.bat (15) (Last=122) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::UnPackFiles] FreeSpace:231800033280 FileSize:15 (Last=183) |
SplashtopStreamer.exe | [4208]2025-03-24 11:59:00 [CUnPack::UnPackFiles] UnPack count:1 len:60999680 File:(null) (Last=0) |