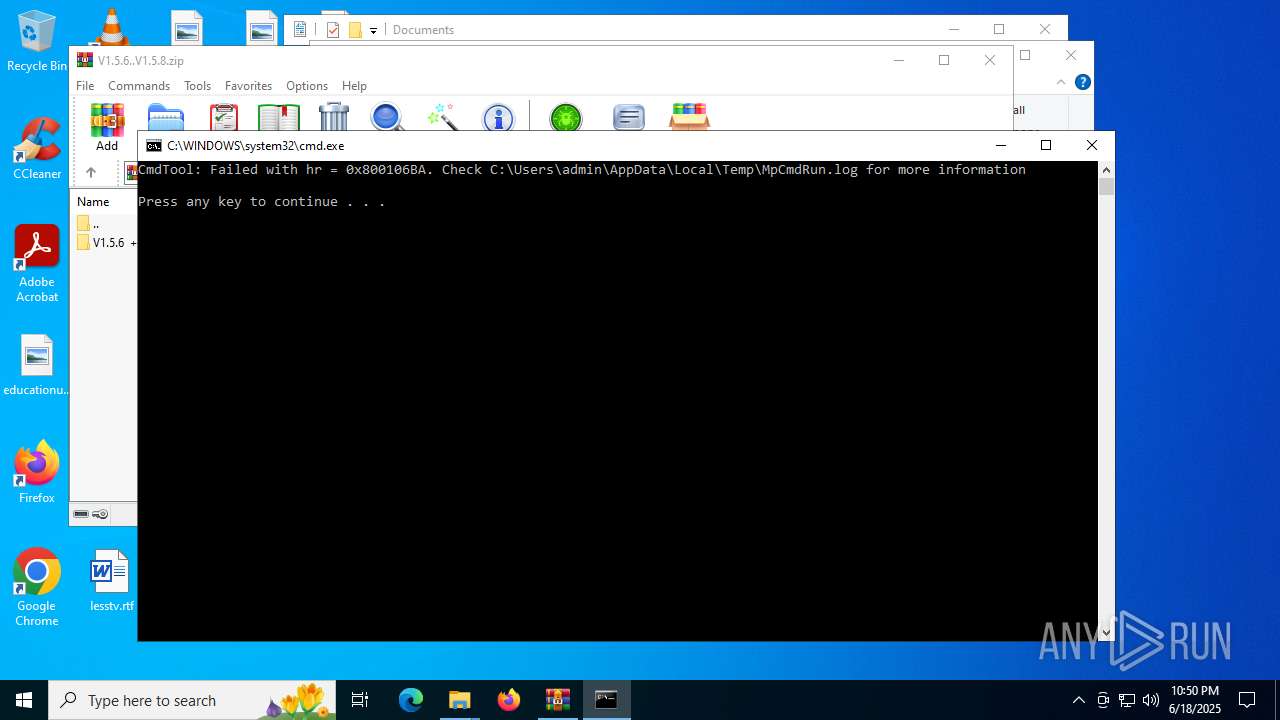
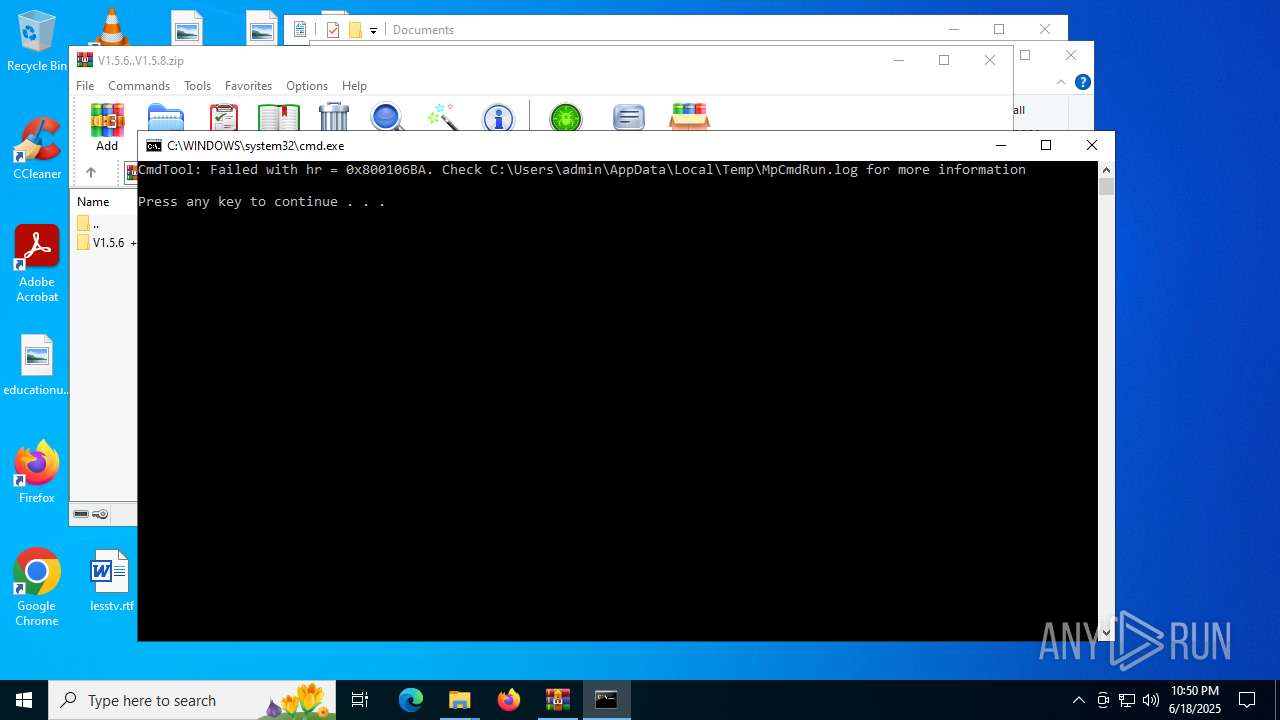
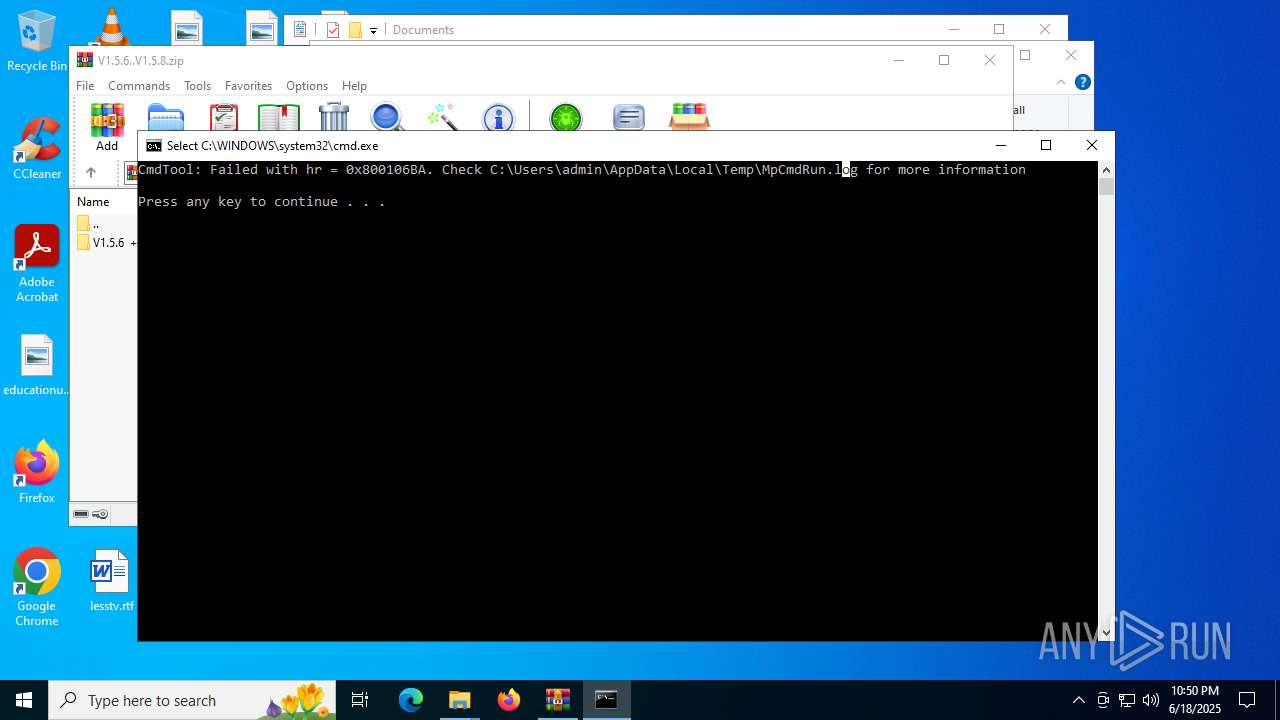
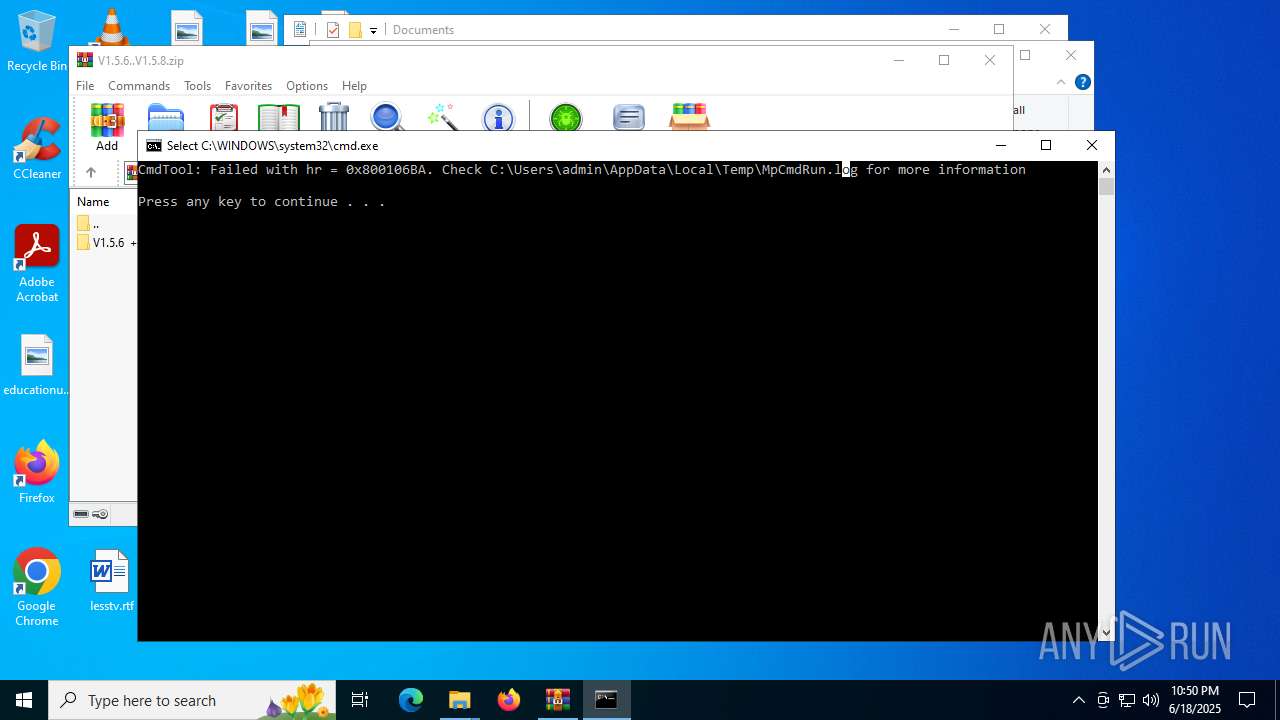
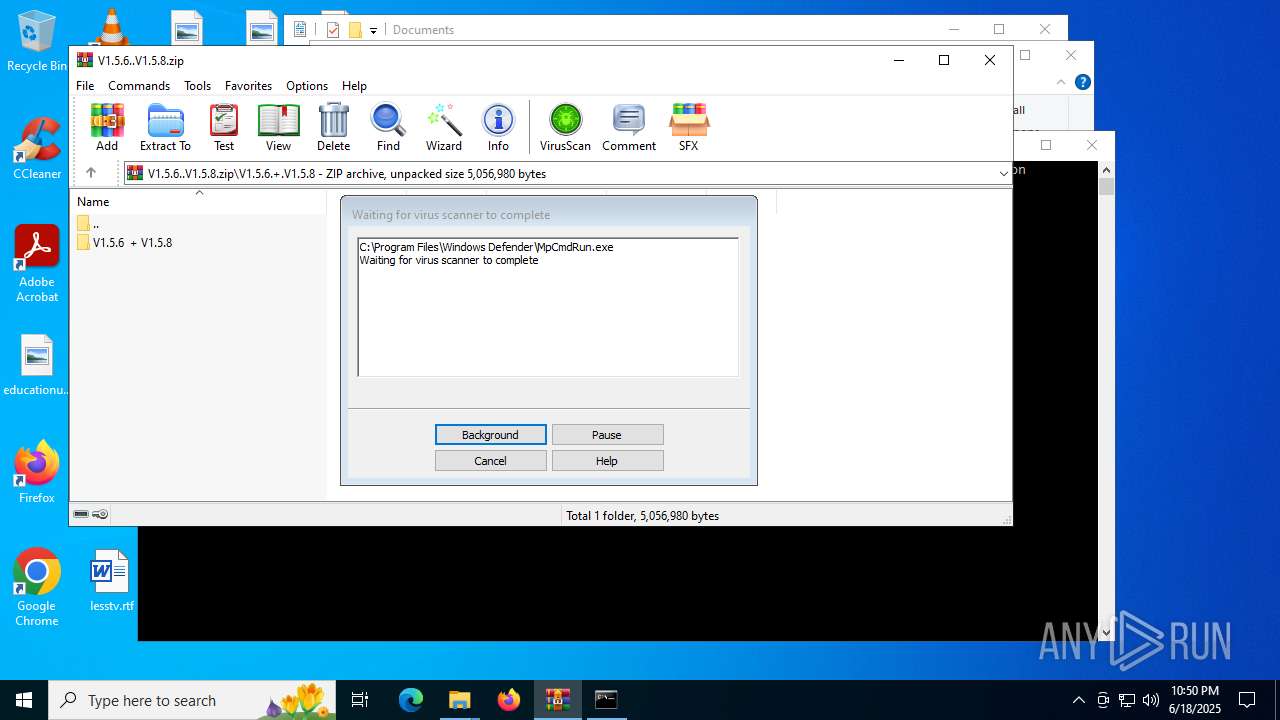
| File name: | V1.5.6..V1.5.8.zip |
| Full analysis: | https://app.any.run/tasks/1124668c-8f68-4361-92ea-97be4e39616d |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2025, 22:49:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 201C18E665C08F539291E1A90CBBA6C9 |
| SHA1: | A66A3127C47CDA56C369D7BD414E782094F534A8 |
| SHA256: | 66A1790DD38B0D1BF0932057E51F97F8ADF66A8A057073BC03AFDE776D3A5775 |
| SSDEEP: | 98304:JW71VWmNYGnYfVGJ+Q/xwDiFWd5hEsnQbqKTvLlT2+jkUjI1FJgzzFf4aKvJUNSA:65gios |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6212)
GENERIC has been found (auto)
- WinRAR.exe (PID: 6212)
SUSPICIOUS
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6212)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6212)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6212)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6212)
INFO
Reads the computer name
- SecHex-GUI.exe (PID: 5168)
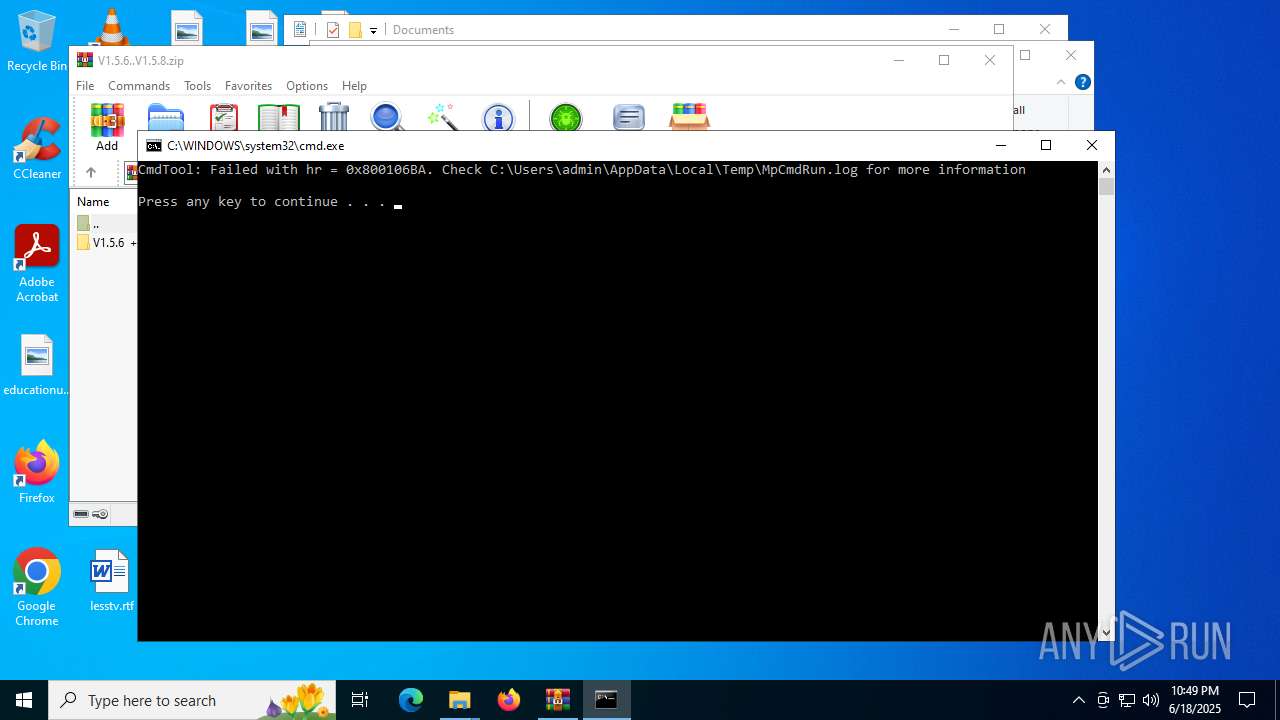
- MpCmdRun.exe (PID: 1080)
Manual execution by a user
- SecHex-GUI.exe (PID: 2580)
- SecHex-GUI.exe (PID: 5168)
Checks supported languages
- SecHex-GUI.exe (PID: 5168)
- MpCmdRun.exe (PID: 1080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6212)
Create files in a temporary directory
- MpCmdRun.exe (PID: 1080)
Checks proxy server information
- slui.exe (PID: 6640)
Reads the software policy settings
- slui.exe (PID: 6640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:19 01:27:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | V1.5.6.+.V1.5.8/ |
Total processes
139
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\Desktop\SecHex-GUI.exe" | C:\Users\admin\Desktop\SecHex-GUI.exe | — | explorer.exe | |||||||||||
User: admin Company: SecHex Integrity Level: MEDIUM Description: SecHex-GUI Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5168 | "C:\Users\admin\Desktop\SecHex-GUI.exe" | C:\Users\admin\Desktop\SecHex-GUI.exe | explorer.exe | ||||||||||||
User: admin Company: SecHex Integrity Level: HIGH Description: SecHex-GUI Exit code: 2147516570 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5780 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\Rar$Scan33983.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6212 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\V1.5.6..V1.5.8.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6640 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 282
Read events
7 268
Write events
14
Delete events
0
Modification events
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\V1.5.6..V1.5.8.zip | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
6
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.6\SecHex-GUI.runtimeconfig.json | binary | |
MD5:D720176A229E9D969B40FABEB0BAF62E | SHA256:321B4E463BBACD6113AA337511BDEBF5E7356E9971744346B28424607C7B483A | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.6\SecHex-GUI.dll | executable | |
MD5:AD714EE48D2E829C5012C65DE6166C05 | SHA256:7D32D13D123871650794A1E172ADC70BC8DAFBDB762F49D889F813844D532B20 | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.8 (testing)\runtimes\win\lib\net6.0\System.Diagnostics.EventLog.dll | executable | |
MD5:62C63C04C6083330D020CF855C85002C | SHA256:FAC816CA0BD5D9C4A17693B37575A5ABA901D993133B61D7344B597472FA0C26 | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.6\SecHex-GUI.deps.json | binary | |
MD5:33784D40D169FA2AD9BFA73EDA3EA7EF | SHA256:2FC1A3F36E616CBC3CD8BE04F8BF7ED49F927B69B4DC14E8A21ED65FE262EB08 | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.exe | executable | |
MD5:C252A43B1D357D08308690545C617031 | SHA256:B779B45849A4AB5BD8FF296E6C95638C5BE4DA18B67F1FD195B31795BC21CDFC | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.pdb | binary | |
MD5:7D0E9A9AE399A11B9B6645CB1577C326 | SHA256:64D236DE60EA2D3257DBA85C5C1DFA3E8C2123821F8E4ADE7C0CDD1C3A1D4A37 | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.deps.json | binary | |
MD5:64AE126CF65A9096D5730E060B448293 | SHA256:A4CADD5C4F3922A4ADA9E4BBC13E2BD779280A9B8CF537B66475FB3559BC7122 | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.dll | executable | |
MD5:5B65AC01D6BABF936451FB1540A680B4 | SHA256:39882D08403185D68A6363EB5066BD212003FBD479E6AA78FFBE97C4191949FE | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\V1.5.6..V1.5.8.zip\V1.5.6.+.V1.5.8\V1.5.6 + V1.5.8\SecHex-Spoofy V1.5.8 (testing)\runtimes\win\lib\net6.0\System.ServiceProcess.ServiceController.dll | executable | |
MD5:1C710EF8481E54352A4E1F66A8F7AD8C | SHA256:D11B97C114101961BCC7ACB0BB17E536708593C0321B6107942FBA20CB430C65 | |||
| 6212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6212.30473\Rar$Scan33983.bat | text | |
MD5:9F565196B9A6B1613C283D9D3DE1381E | SHA256:2E33D92CAEFBF3D7411310607D642896EE52524AD3F3B01F3C08B87E4B33AD70 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
17
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6172 | RUXIMICS.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6172 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
6172 | RUXIMICS.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
SecHex-GUI.exe | The application to execute does not exist: 'C:\Users\admin\Desktop\SecHex-GUI.dll'. |