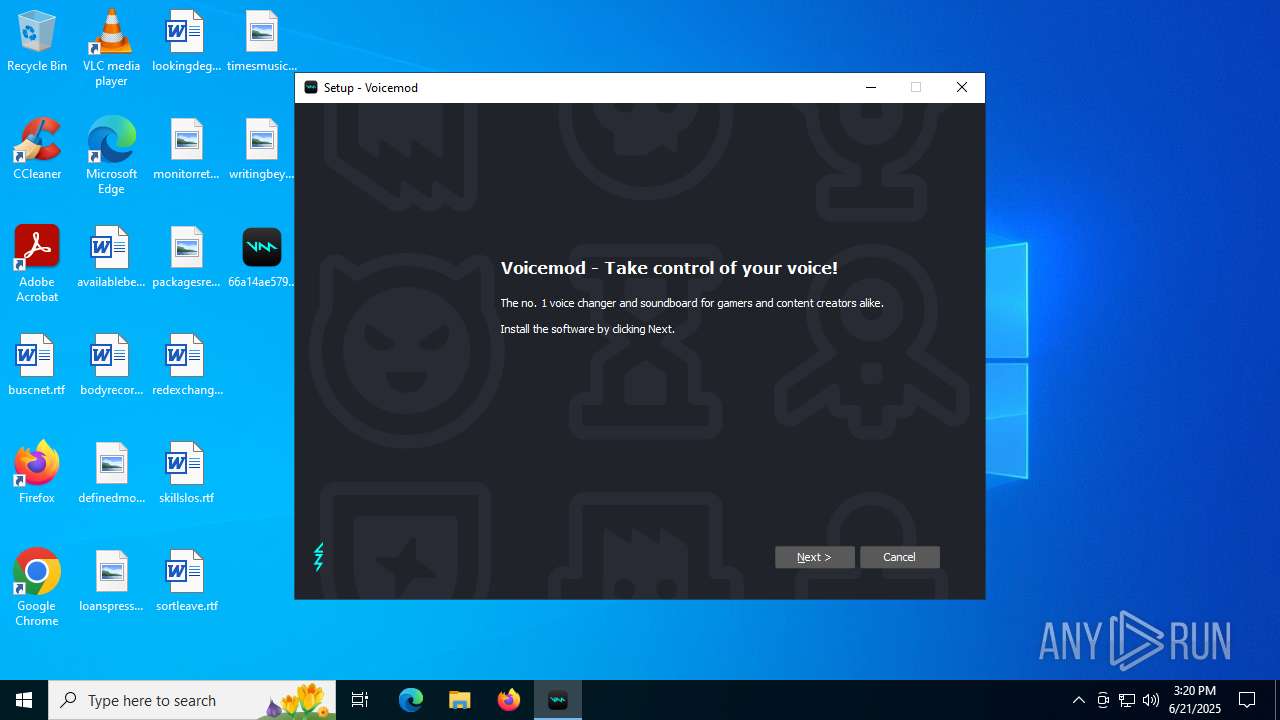
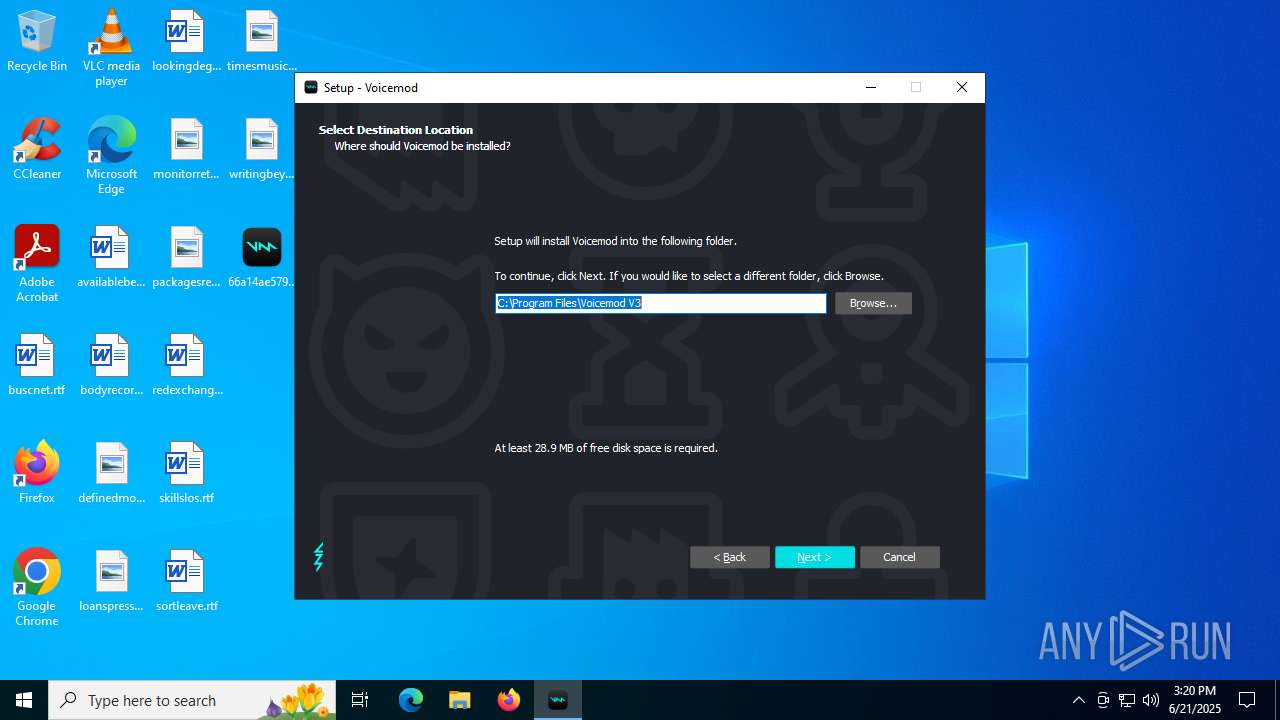
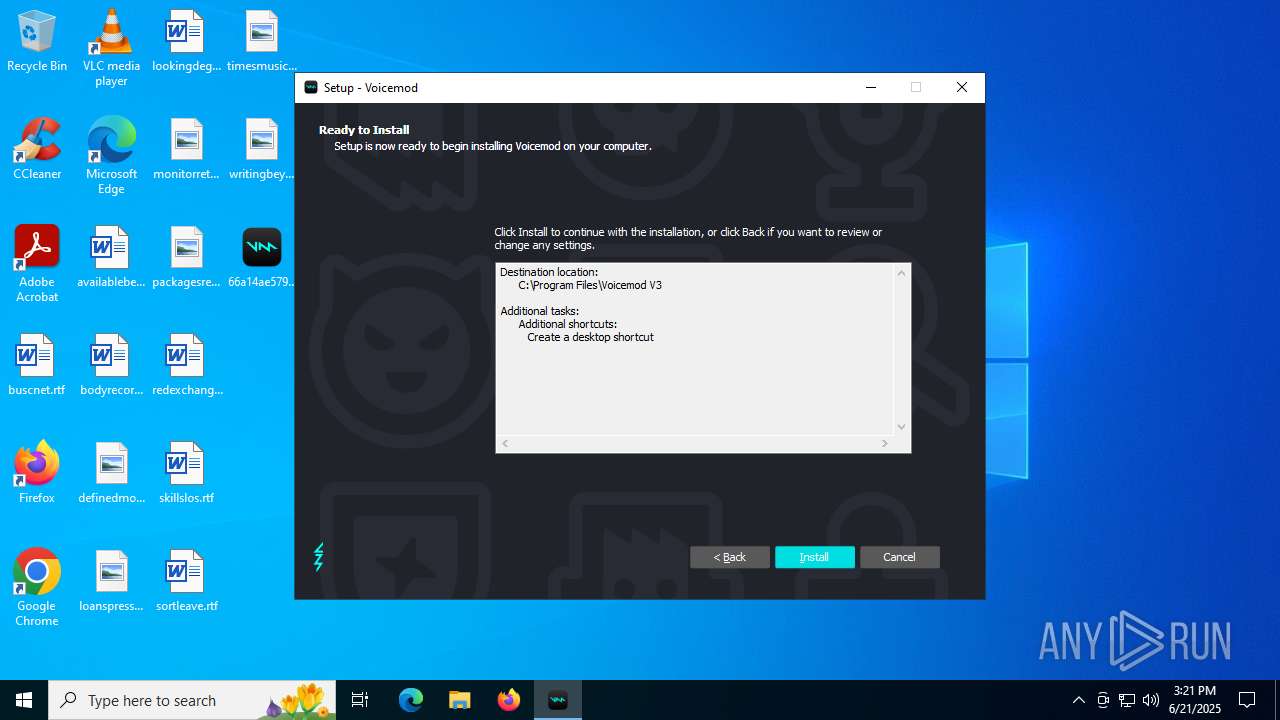
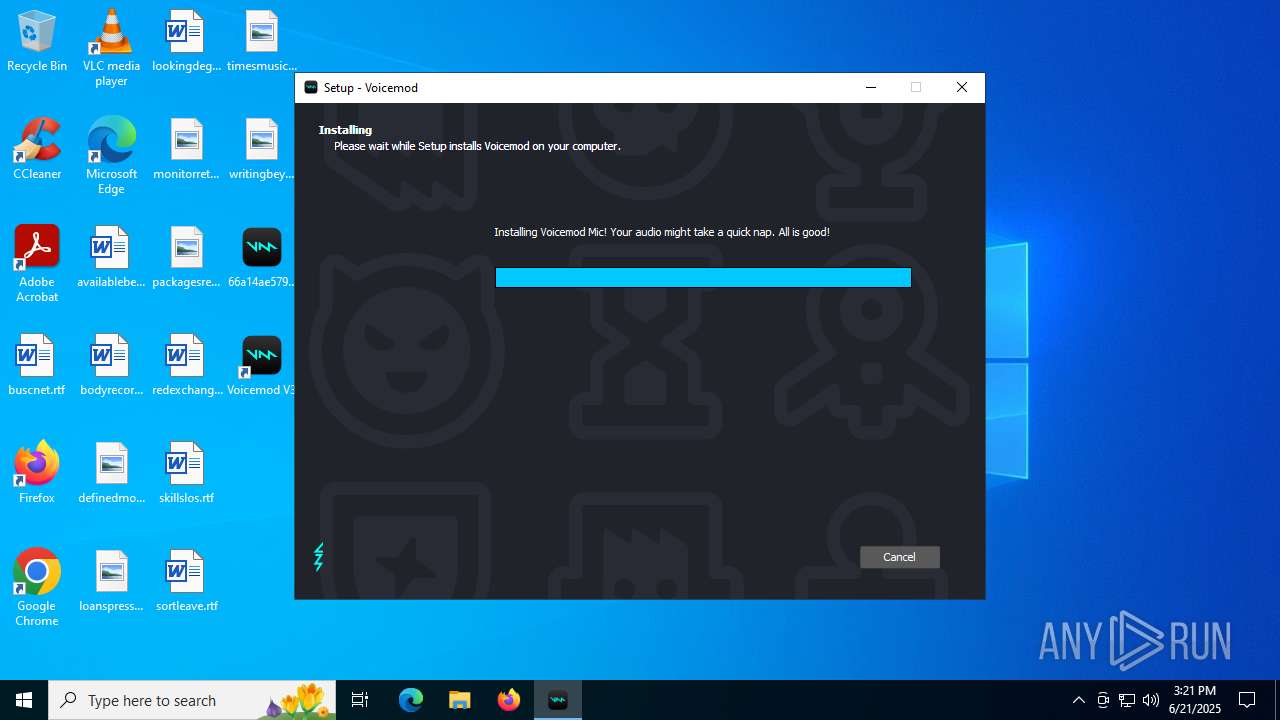
| File name: | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe |
| Full analysis: | https://app.any.run/tasks/7449243c-0d69-4390-a799-877052d0bf0f |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 15:20:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 2F99913925990BCF055A14A34EE24B8E |
| SHA1: | D6E9CBB8A50E299CE03D9B8FA4BF303BAC3BC691 |
| SHA256: | 66A14AE579396FC85F3BD72B021BC802D9E0FF9A68810F6F0E6EDEDEB67274C9 |
| SSDEEP: | 98304:/bUgdqZ3FWMo0iHNEGRltHg5YZz/6Pf8FMdJDxDBwcMSdObOS/Hro1e4Kv+BG/6D:CcrsmQai |
MALICIOUS
Changes the autorun value in the registry
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
Run PowerShell with an invisible window
- powershell.exe (PID: 5528)
SUSPICIOUS
Executable content was dropped or overwritten
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 424)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 5616)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- voicemodcon.exe (PID: 6520)
- drvinst.exe (PID: 6104)
- drvinst.exe (PID: 3872)
Reads security settings of Internet Explorer
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 1944)
- Voicemod.exe (PID: 1896)
- Voicemod.exe (PID: 3836)
- voicemodcon.exe (PID: 6520)
Reads the Windows owner or organization settings
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
Starts CMD.EXE for commands execution
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- powershell.exe (PID: 5528)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 4164)
- cmd.exe (PID: 4760)
Get information on the list of running processes
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- cmd.exe (PID: 3836)
There is functionality for taking screenshot (YARA)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- Voicemod.exe (PID: 1896)
Drops a system driver (possible attempt to evade defenses)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- drvinst.exe (PID: 6104)
- voicemodcon.exe (PID: 6520)
- drvinst.exe (PID: 3872)
Starts process via Powershell
- powershell.exe (PID: 5528)
Executing commands from a ".bat" file
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- powershell.exe (PID: 5528)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5716)
- cmd.exe (PID: 3588)
Application launched itself
- cmd.exe (PID: 5552)
- cmd.exe (PID: 4164)
- cmd.exe (PID: 4760)
Creates files in the driver directory
- drvinst.exe (PID: 6104)
- drvinst.exe (PID: 3872)
Creates or modifies Windows services
- drvinst.exe (PID: 3872)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- cmd.exe (PID: 3564)
- cmd.exe (PID: 6748)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3564)
- cmd.exe (PID: 6748)
- cmd.exe (PID: 5372)
- cmd.exe (PID: 6776)
- cmd.exe (PID: 6936)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 5372)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6776)
Uses WMIC.EXE
- cmd.exe (PID: 6936)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 4832)
- cmd.exe (PID: 5372)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 4960)
- cmd.exe (PID: 6140)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 3732)
INFO
Process checks computer location settings
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 1944)
Reads the computer name
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 1944)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- curl.exe (PID: 4984)
- curl.exe (PID: 5924)
- curl.exe (PID: 4196)
- curl.exe (PID: 2188)
- curl.exe (PID: 6776)
- curl.exe (PID: 4644)
- curl.exe (PID: 3800)
- curl.exe (PID: 6940)
- curl.exe (PID: 6232)
- curl.exe (PID: 3636)
- curl.exe (PID: 3396)
- curl.exe (PID: 2664)
- curl.exe (PID: 5600)
- curl.exe (PID: 6292)
- curl.exe (PID: 1216)
- curl.exe (PID: 2716)
- curl.exe (PID: 5008)
- SaveDefaultDevices.exe (PID: 6424)
- Voicemod.exe (PID: 1896)
- AudioEndPointTool.exe (PID: 6700)
- AudioEndPointTool.exe (PID: 6512)
- curl.exe (PID: 1496)
- AudioEndPointTool.exe (PID: 1356)
- voicemodcon.exe (PID: 6520)
- AudioEndPointTool.exe (PID: 5172)
- drvinst.exe (PID: 3872)
- drvinst.exe (PID: 6104)
- AudioEndPointTool.exe (PID: 6812)
- AudioEndPointTool.exe (PID: 4836)
- AudioEndPointTool.exe (PID: 4680)
- AudioEndPointTool.exe (PID: 4080)
- AudioEndPointTool.exe (PID: 6424)
- AudioEndPointTool.exe (PID: 1180)
- AudioEndPointTool.exe (PID: 3636)
- curl.exe (PID: 2976)
- curl.exe (PID: 4104)
- curl.exe (PID: 6220)
- curl.exe (PID: 2680)
- AudioEndPointTool.exe (PID: 1232)
- curl.exe (PID: 3768)
- curl.exe (PID: 7080)
- Voicemod.exe (PID: 3836)
- curl.exe (PID: 3748)
- curl.exe (PID: 5372)
- curl.exe (PID: 4832)
- curl.exe (PID: 4380)
Create files in a temporary directory
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 424)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 5616)
- Voicemod.exe (PID: 1896)
- AudioEndPointTool.exe (PID: 6700)
- crashpad_handler.exe (PID: 6256)
- AudioEndPointTool.exe (PID: 6512)
- voicemodcon.exe (PID: 6212)
- AudioEndPointTool.exe (PID: 1356)
- AudioEndPointTool.exe (PID: 5172)
- AudioEndPointTool.exe (PID: 1232)
- voicemodcon.exe (PID: 6520)
- AudioEndPointTool.exe (PID: 6812)
- AudioEndPointTool.exe (PID: 4836)
- AudioEndPointTool.exe (PID: 6424)
- AudioEndPointTool.exe (PID: 4080)
- AudioEndPointTool.exe (PID: 4680)
- AudioEndPointTool.exe (PID: 1180)
- AudioEndPointTool.exe (PID: 3636)
- Voicemod.exe (PID: 3836)
Checks supported languages
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 1944)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 5616)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 424)
- curl.exe (PID: 5924)
- curl.exe (PID: 4984)
- curl.exe (PID: 4196)
- curl.exe (PID: 3800)
- curl.exe (PID: 6232)
- curl.exe (PID: 6776)
- curl.exe (PID: 6940)
- curl.exe (PID: 4644)
- curl.exe (PID: 3636)
- curl.exe (PID: 2716)
- curl.exe (PID: 5600)
- curl.exe (PID: 5008)
- curl.exe (PID: 1216)
- curl.exe (PID: 3396)
- curl.exe (PID: 2664)
- curl.exe (PID: 2188)
- SaveDefaultDevices.exe (PID: 6424)
- Voicemod.exe (PID: 1896)
- crashpad_handler.exe (PID: 6256)
- AudioEndPointTool.exe (PID: 6700)
- voicemodcon.exe (PID: 6212)
- AudioEndPointTool.exe (PID: 6512)
- curl.exe (PID: 1496)
- curl.exe (PID: 6292)
- AudioEndPointTool.exe (PID: 1356)
- AudioEndPointTool.exe (PID: 5172)
- drvinst.exe (PID: 6104)
- drvinst.exe (PID: 3872)
- AudioEndPointTool.exe (PID: 6812)
- AudioEndPointTool.exe (PID: 4836)
- AudioEndPointTool.exe (PID: 4680)
- AudioEndPointTool.exe (PID: 4080)
- AudioEndPointTool.exe (PID: 6424)
- AudioEndPointTool.exe (PID: 1180)
- AudioEndPointTool.exe (PID: 3636)
- curl.exe (PID: 4104)
- curl.exe (PID: 2976)
- avx-checker.exe (PID: 5232)
- curl.exe (PID: 6220)
- curl.exe (PID: 5372)
- curl.exe (PID: 2680)
- curl.exe (PID: 3768)
- curl.exe (PID: 7080)
- Voicemod.exe (PID: 3836)
- crashpad_handler.exe (PID: 6336)
- curl.exe (PID: 4832)
- curl.exe (PID: 4380)
- voicemodcon.exe (PID: 6520)
- AudioEndPointTool.exe (PID: 1232)
- curl.exe (PID: 3748)
Reads the machine GUID from the registry
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- Voicemod.exe (PID: 1896)
- drvinst.exe (PID: 6104)
- Voicemod.exe (PID: 3836)
- voicemodcon.exe (PID: 6520)
Execution of CURL command
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
The sample compiled with russian language support
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
Detects InnoSetup installer (YARA)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 5616)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 1944)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe (PID: 424)
Compiled with Borland Delphi (YARA)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 1944)
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
Creates a software uninstall entry
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
Creates files in the program directory
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- SaveDefaultDevices.exe (PID: 6424)
- cmd.exe (PID: 5552)
Launching a file from a Registry key
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
Manual execution by a user
- Voicemod.exe (PID: 1896)
Creates files or folders in the user directory
- Voicemod.exe (PID: 1896)
Reads the software policy settings
- Voicemod.exe (PID: 1896)
- voicemodcon.exe (PID: 6520)
- Voicemod.exe (PID: 3836)
- slui.exe (PID: 3480)
- drvinst.exe (PID: 6104)
Checks proxy server information
- Voicemod.exe (PID: 1896)
- Voicemod.exe (PID: 3836)
- slui.exe (PID: 3480)
Reads Environment values
- Voicemod.exe (PID: 1896)
- Voicemod.exe (PID: 3836)
The sample compiled with english language support
- 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp (PID: 2348)
- voicemodcon.exe (PID: 6520)
- drvinst.exe (PID: 6104)
- drvinst.exe (PID: 3872)
Reads CPU info
- Voicemod.exe (PID: 1896)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4868)
- WMIC.exe (PID: 1232)
- WMIC.exe (PID: 4884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:11:17 06:07:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 682496 |
| InitializedDataSize: | 156160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7ed0 |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Voicemod Inc., Sucursal en España |
| FileDescription: | Voicemod Setup |
| FileVersion: | |
| LegalCopyright: | © 2025 Voicemod Inc., Sucursal en España - Version 1.4.8 |
| OriginalFileName: | |
| ProductName: | Voicemod |
| ProductVersion: | 1.4.8 |
Total processes
277
Monitored processes
139
Malicious processes
4
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | netsh advfirewall firewall add rule name="Voicemod" dir=out action=allow program="C:\Users\admin\AppData\Local\VoicemodV3\app\last\Voicemod.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | "C:\Users\admin\Desktop\66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe" /SPAWNWND=$40252 /NOTIFYWND=$60282 | C:\Users\admin\Desktop\66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | ||||||||||||
User: admin Company: Voicemod Inc., Sucursal en España Integrity Level: HIGH Description: Voicemod Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | curl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | curl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | netsh advfirewall firewall add rule name="Voicemod" dir=in action=allow program="C:\Program Files\Voicemod V3\Voicemod.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | AudioEndPointTool.exe get --name Voicemod --flow Render --format Raw --fields ID | C:\Program Files\Voicemod V3\driver\AudioEndPointTool.exe | — | cmd.exe | |||||||||||
User: admin Company: Voicemod Inc. Integrity Level: HIGH Description: Voicemod tools Exit code: 0 Modules
| |||||||||||||||
| 1216 | "C:\WINDOWS\system32\curl.exe" https://api.voicemod.net/ip -H "Content-Type: application/json" -o "C:\Users\admin\AppData\Local\Temp\\ipaddress.info" | C:\Windows\System32\curl.exe | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 35 Version: 8.4.0 Modules
| |||||||||||||||
| 1216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | curl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | AudioEndPointTool.exe get --default --flow=Capture --role=Console --format=Raw --fields=ID | C:\Program Files\Voicemod V3\driver\AudioEndPointTool.exe | — | cmd.exe | |||||||||||
User: admin Company: Voicemod Inc. Integrity Level: HIGH Description: Voicemod tools Exit code: 0 Modules
| |||||||||||||||
Total events
43 506
Read events
42 852
Write events
647
Delete events
7
Modification events
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Voicemod\Voicemod V3 |
| Operation: | write | Name: | DownloadId |
Value: i68s70 | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Voicemod V3 |
| Operation: | write | Name: | TermsAcceptedDate |
Value: 2025/06/21 | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | VoicemodV3 |
Value: "C:\Program Files\Voicemod V3\Voicemod.exe" --boot | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Voicemod\Voicemod V3 |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files\Voicemod V3 | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Voicemod\Voicemod V3 |
| Operation: | write | Name: | Language |
Value: en | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\voicemod |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FE519A29-8B15-47C4-BCD6-A513277DC26F}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.3 (u) | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FE519A29-8B15-47C4-BCD6-A513277DC26F}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Voicemod V3 | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FE519A29-8B15-47C4-BCD6-A513277DC26F}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Voicemod V3\ | |||
| (PID) Process: | (2348) 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FE519A29-8B15-47C4-BCD6-A513277DC26F}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Voicemod V3 | |||
Executable files
43
Suspicious files
28
Text files
50
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Users\admin\AppData\Local\Temp\is-0O837.tmp\mvvad.inf | text | |
MD5:4BE77F8AFECFC2B935017E2B6C231E0F | SHA256:F89D88D74C7EFECBAFB48F88511E9ADF56856A45571CB66D77DE5494D0A19627 | |||
| 3836 | cmd.exe | C:\Users\admin\AppData\Local\Temp\tasklist_unins000.exe.txt | text | |
MD5:0A3D8F8FCDEB58A6C9BC8228A970C28D | SHA256:D4C9AD9F84309CADFB4934F04C9D5DE1F7C125A52CEBB68C7D657FBD1F844E20 | |||
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Users\admin\AppData\Local\Temp\is-0O837.tmp\bg-inner.png | image | |
MD5:A034EEAF19BB82B2AE63F4FA10C26476 | SHA256:8FE4A3F95D5309E692C4142F460BEBE4E4E24844F5A2071D466BD964C5D04DCF | |||
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Users\admin\AppData\Local\Temp\is-0O837.tmp\bg-top.png | image | |
MD5:220FE6E00519A633D9AD7D1D50ADC4C7 | SHA256:BDC753B2B19EE8B573B8E676F18DAE42494B99B6BD738194DCDD67F244085F36 | |||
| 424 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe | C:\Users\admin\AppData\Local\Temp\is-E1MV7.tmp\66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | executable | |
MD5:9D81EAFEC164832D9C47431A5196BD46 | SHA256:9B595FB636111EE1F84BF798998A8DE29C7DE6F2EC491D37278C663150189A3E | |||
| 5616 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.exe | C:\Users\admin\AppData\Local\Temp\is-3IPR4.tmp\66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | executable | |
MD5:9D81EAFEC164832D9C47431A5196BD46 | SHA256:9B595FB636111EE1F84BF798998A8DE29C7DE6F2EC491D37278C663150189A3E | |||
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Users\admin\AppData\Local\Temp\is-0O837.tmp\buttons.png | image | |
MD5:87CC673665996A85A404BEB1C8466AEE | SHA256:D236F88EF90E6D0E259A586F4E613B14D4A35F3A704FF559DADDA31341E99C24 | |||
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Users\admin\AppData\Local\Temp\is-0O837.tmp\botva2.dll | executable | |
MD5:0177746573EED407F8DCA8A9E441AA49 | SHA256:A4B61626A1626FDABEC794E4F323484AA0644BAA1C905A5DCF785DC34564F008 | |||
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Users\admin\AppData\Local\Temp\is-0O837.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 2348 | 66a14ae579396fc85f3bd72b021bc802d9e0ff9a68810f6f0e6ededeb67274c9VoicemodInstaller_1.4.8-i68s70.tmp | C:\Program Files\Voicemod V3\driver\is-NOO52.tmp | executable | |
MD5:EDD104527F5F56C8F890ABD915BB636C | SHA256:BA6C3BBB1BFFC04409983F4EAAFF103F8F9F8E044F35A0589F969113BBDB96DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
89
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.136:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4156 | RUXIMICS.exe | GET | 200 | 184.24.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4156 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.131:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.20:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4156 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.24.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4156 | RUXIMICS.exe | 184.24.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
api.voicemod.net |
| whitelisted |
s2s.mparticle.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET INFO Outgoing Basic Auth Base64 HTTP Password detected unencrypted |
Process | Message |
|---|---|
Voicemod.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|