| download: | /file/9hkw0u8samj9xh5/blur-installer_%25281%2529.exe/file |
| Full analysis: | https://app.any.run/tasks/f3687f65-bbb6-45ae-ba10-e35b8ea2529d |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2023, 01:30:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | 047FDC38E3AD9262DAE7C37BF57D74C1 |
| SHA1: | 13DCBE1608BFB96F413F1EAA7D4F41502D832067 |
| SHA256: | 66A0853EBCB02BC8545483FA64B2DE3BD82B2EB73FDA2FB30D7EB7262758B152 |
| SSDEEP: | 3072:oingAkHnjPFQ6KSEU/mHbPaW+LN7DxRLlzglKKXnm:/gAkHnjPFQBSEx7PCN7jBKXnm |
MALICIOUS
Drops the executable file immediately after the start
- blur-installer (1).exe (PID: 2064)
- blur-installer (1).exe (PID: 3584)
- VC_redist.x86.exe (PID: 3620)
- VC_redist.x86.exe (PID: 2128)
- blur-installer (1).tmp (PID: 4068)
SUSPICIOUS
Reads the Windows owner or organization settings
- blur-installer (1).tmp (PID: 4068)
Drops 7-zip archiver for unpacking
- blur-installer (1).tmp (PID: 4068)
Process drops legitimate windows executable
- blur-installer (1).tmp (PID: 4068)
- VC_redist.x86.exe (PID: 2128)
The process drops C-runtime libraries
- blur-installer (1).tmp (PID: 4068)
Searches for installed software
- VC_redist.x86.exe (PID: 3620)
INFO
Application launched itself
- iexplore.exe (PID: 2876)
- iexplore.exe (PID: 3128)
Reads the computer name
- wmpnscfg.exe (PID: 1784)
- blur-installer (1).tmp (PID: 2100)
- blur-installer (1).tmp (PID: 4068)
- VC_redist.x86.exe (PID: 3620)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1784)
Checks supported languages
- blur-installer (1).exe (PID: 2064)
- wmpnscfg.exe (PID: 1784)
- blur-installer (1).tmp (PID: 2100)
- blur-installer (1).exe (PID: 3584)
- blur-installer (1).tmp (PID: 4068)
- VC_redist.x86.exe (PID: 2128)
- VC_redist.x86.exe (PID: 3620)
- blur.exe (PID: 3020)
Manual execution by a user
- wmpnscfg.exe (PID: 1784)
- blur.exe (PID: 3020)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2304)
The process uses the downloaded file
- iexplore.exe (PID: 2876)
Create files in a temporary directory
- blur-installer (1).exe (PID: 2064)
- blur-installer (1).exe (PID: 3584)
- blur-installer (1).tmp (PID: 4068)
- VC_redist.x86.exe (PID: 3620)
Creates files in the program directory
- blur-installer (1).tmp (PID: 4068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| HTTPEquivXUaCompatible: | ie=edge |
|---|---|
| Viewport: | width=device-width, initial-scale=1, shrink-to-fit=no |
| Title: | blur-installer (1) |
| Keywords: | online storage, free storage, cloud Storage, collaboration, backup file Sharing, share Files, photo backup, photo sharing, ftp replacement, cross platform, remote access, mobile access, send large files, recover files, file versioning, undelete, Windows, PC, Mac, OS X, Linux, iPhone, iPad, Android |
| Description: | MediaFire is a simple to use free service that lets you put all your photos, documents, music, and video in a single place so you can access them anywhere and share them everywhere. |
| Robots: | noindex,nofollow |
| GoogleBot: | noindex,nofollow |
| Slurp: | noindex,nofollow |
| GoogleTranslateCustomization: | 5587c1b0a958bf07-62a8e309de686e87-gc92f61279a2c8524-11 |
| TwitterCard: | summary_large_image |
| TwitterSite: | @MediaFire |
| TwitterUrl: | https://www.mediafire.com/file/9hkw0u8samj9xh5/blur-installer_%25281%2529.exe/file |
| TwitterTitle: | blur-installer (1) |
| TwitterImage: | https://static.mediafire.com/images/filetype/download/app.jpg |
| TwitterDescription: | - |
Total processes
55
Monitored processes
11
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1784 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\blur-installer (1).exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\blur-installer (1).exe | — | iexplore.exe | |||||||||||
User: admin Company: tekno Integrity Level: MEDIUM Description: blur Setup Exit code: 0 Version: Modules
| |||||||||||||||
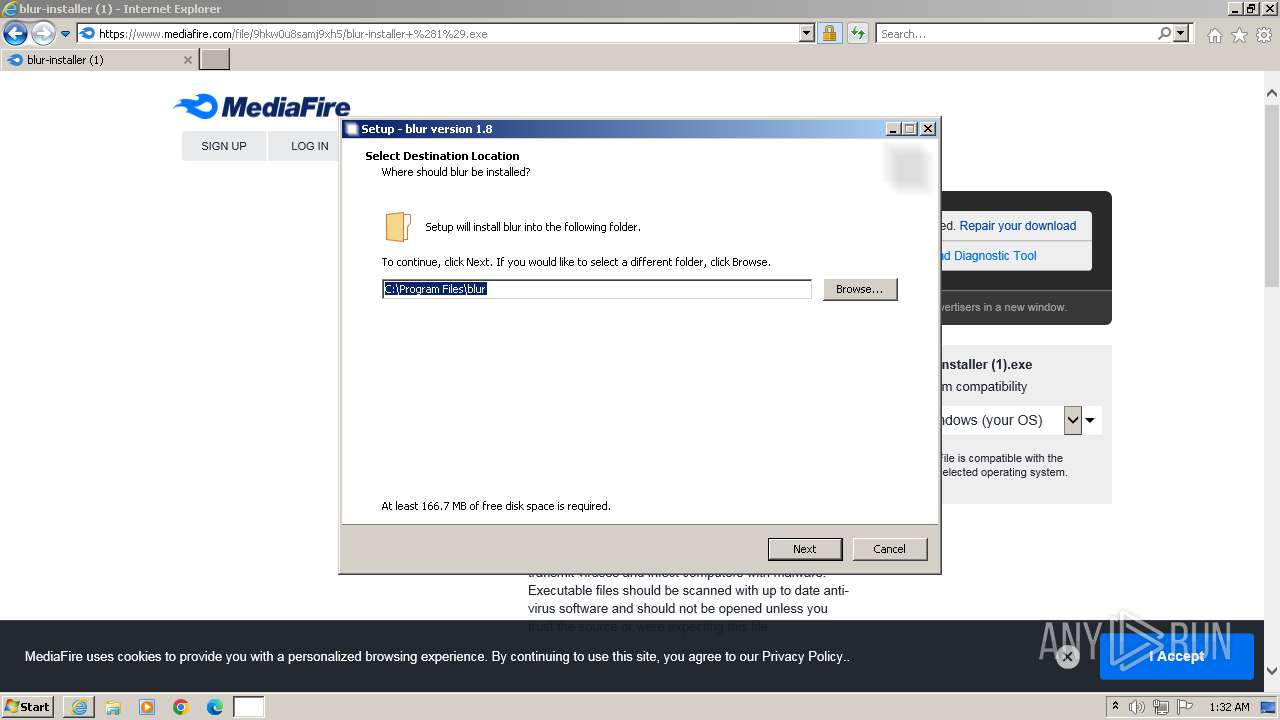
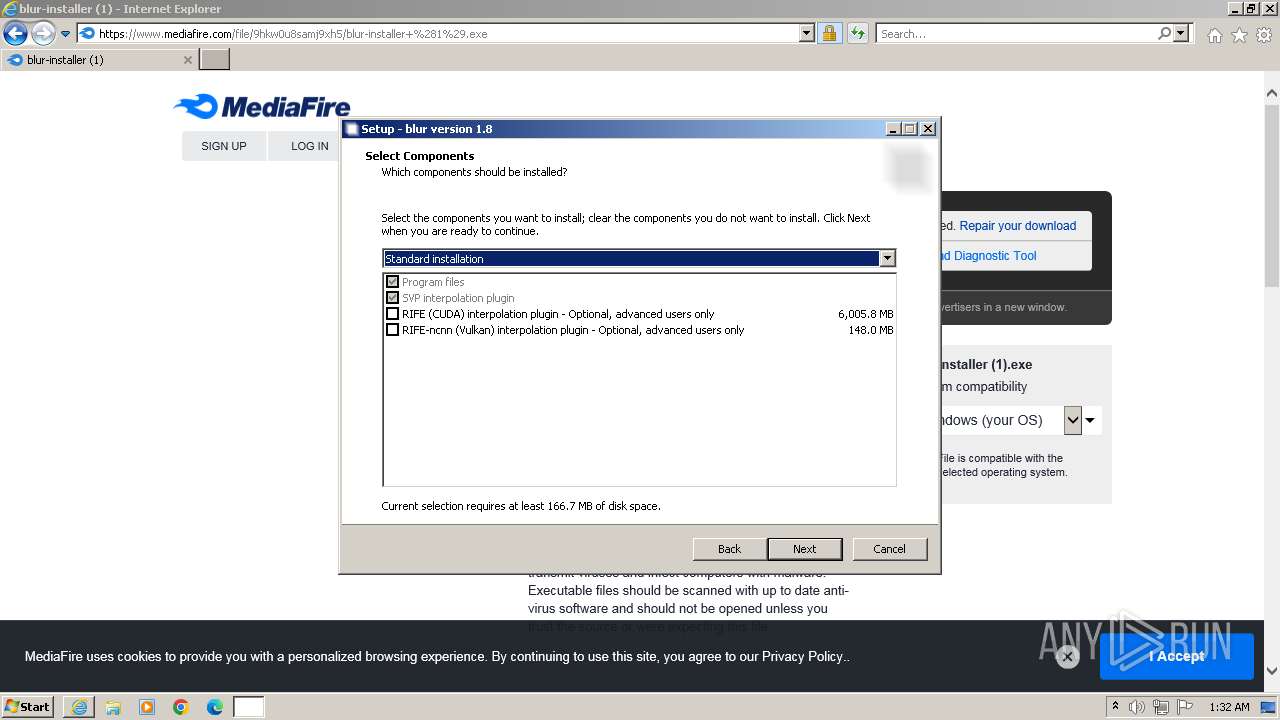
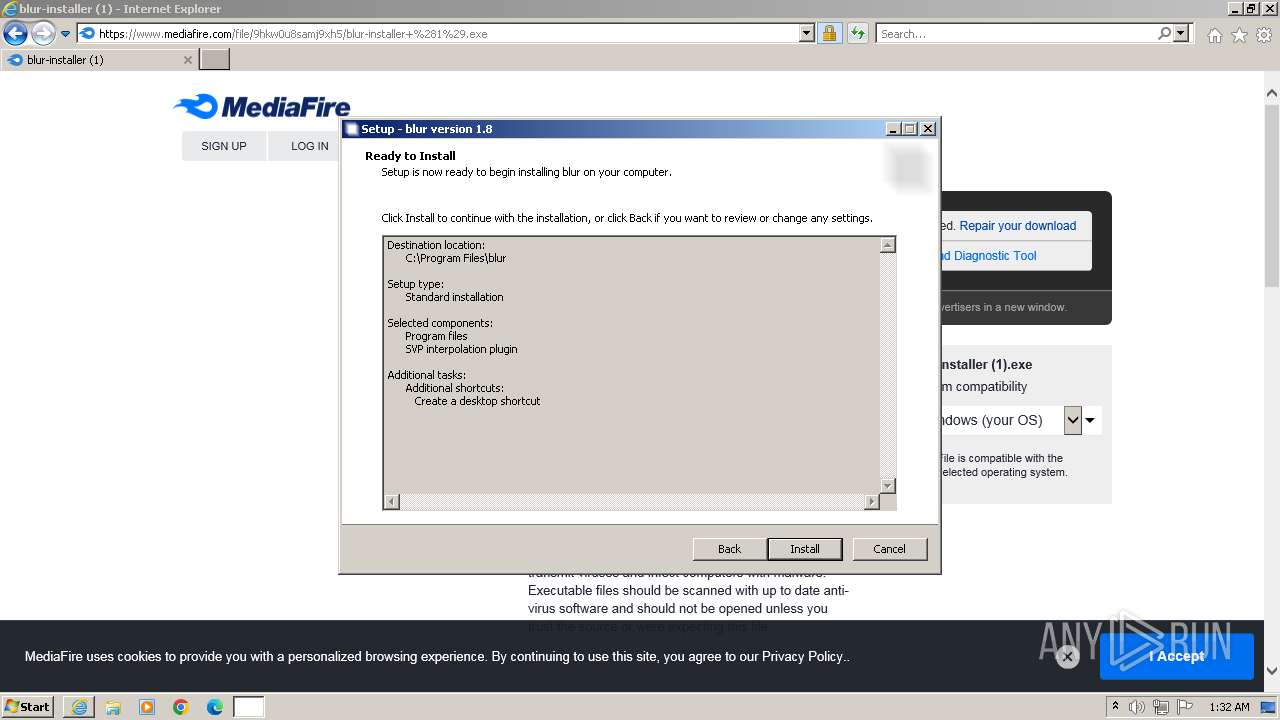
| 2100 | "C:\Users\admin\AppData\Local\Temp\is-LNCPE.tmp\blur-installer (1).tmp" /SL5="$80234,57819947,879104,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\blur-installer (1).exe" | C:\Users\admin\AppData\Local\Temp\is-LNCPE.tmp\blur-installer (1).tmp | — | blur-installer (1).exe | |||||||||||
User: admin Company: tekno Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2128 | "C:\Users\admin\AppData\Local\Temp\is-E2QQQ.tmp\VC_redist.x86.exe" /install /passive /norestart | C:\Users\admin\AppData\Local\Temp\is-E2QQQ.tmp\VC_redist.x86.exe | — | blur-installer (1).tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2019 Redistributable (x86) - 14.29.30133 Exit code: 1638 Version: 14.29.30133.0 Modules
| |||||||||||||||
| 2304 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2876 CREDAT:464129 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\AppData\Local\Temp\file.htm" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3020 | "C:\Program Files\blur\blur.exe" | C:\Program Files\blur\blur.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 3128 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2876 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\blur-installer (1).exe" /SPAWNWND=$30292 /NOTIFYWND=$80234 /ALLUSERS | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\blur-installer (1).exe | blur-installer (1).tmp | ||||||||||||
User: admin Company: tekno Integrity Level: HIGH Description: blur Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3620 | "C:\Windows\Temp\{1E30863A-E46A-4667-A67C-57DD508839F9}\.cr\VC_redist.x86.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\is-E2QQQ.tmp\VC_redist.x86.exe" -burn.filehandle.attached=152 -burn.filehandle.self=160 /install /passive /norestart | C:\Windows\Temp\{1E30863A-E46A-4667-A67C-57DD508839F9}\.cr\VC_redist.x86.exe | — | VC_redist.x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2019 Redistributable (x86) - 14.29.30133 Exit code: 1638 Version: 14.29.30133.0 Modules
| |||||||||||||||
Total events
37 366
Read events
37 213
Write events
134
Delete events
19
Modification events
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
165
Suspicious files
87
Text files
2 392
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:BE49534E2FDE2A0247F2CE2BE0C62FE1 | SHA256:A7E3794208B95F73693232FA3AE2225D8298FB4843A98B3257E938D1725C5E70 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:AFAEA43CE0E6CBEA0559268FDBCBC460 | SHA256:39F57D474B125FF96E0FAE6A70EBBE1D5EBD4EEE9C065087121E4B54CC641BF0 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_9A80F5225FC4BA17E71B590CABC426DB | binary | |
MD5:2149DD0576C388D84BF9A81986C3D752 | SHA256:972C484449D29277FF6B04878F245F2080484BA0DF93080AC6128264A879E0EF | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:CE37F6E91C2378919B810B17AD2144DF | SHA256:8111EDCC7482D098BC8B5E135BAFE991C2B4DDA5B04C89F11E15A2337FD054D5 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:7B0F6B0F4F37CF615AB91FAD5A1B3A5D | SHA256:366727E1C95EE00AF2F40E3F54AE2DF6E64579B9E50BE954CF370F3BD473CCE0 | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:214A694AEC3E000EB77FAB84E21901FA | SHA256:171502A31CB9A0DA595A64813B3273E90C06C883DFE90B9576373FC89934697E | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:A481EB0C4CF12B9D868F50E3A7DE05B6 | SHA256:C5F55AEFF2B1DB7C6135A0D4B3447CE62B86CDAE2B6B0D28980E28C8FC158DFB | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\js[1].js | text | |
MD5:237D4FCF74BB8DADC52211964909846B | SHA256:B351BDD7C9968F57FDC3698DB581BACBB8FD66D5CE516223EAC626A8167512F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
128
DNS requests
67
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3128 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7260c37ce47485a3 | unknown | compressed | 4.66 Kb | unknown |
3128 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83de5310dd3e31e8 | unknown | compressed | 4.66 Kb | unknown |
3128 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3128 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f3aaf8a1cb011ff1 | unknown | compressed | 4.66 Kb | unknown |
3128 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3dd30a7acf5638af | unknown | compressed | 4.66 Kb | unknown |
3128 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3128 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3128 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3128 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQChuVoVf7HVAxLxWCb2kXo7 | unknown | binary | 472 b | unknown |
1080 | svchost.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?95a1910edfe5ddda | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3128 | iexplore.exe | 172.67.144.62:443 | the.gatekeeperconsent.com | CLOUDFLARENET | US | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3128 | iexplore.exe | 104.22.74.216:443 | btloader.com | CLOUDFLARENET | — | unknown |
3128 | iexplore.exe | 172.217.18.104:443 | www.googletagmanager.com | GOOGLE | US | unknown |
4 | System | 104.21.63.106:445 | www.ezojs.com | CLOUDFLARENET | — | unknown |
3128 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3128 | iexplore.exe | 142.250.186.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2876 | iexplore.exe | 23.53.43.115:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
btloader.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
the.gatekeeperconsent.com |
| unknown |
www.ezojs.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
translate.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |