| File name: | exit.cmd |
| Full analysis: | https://app.any.run/tasks/afdaa52a-c7c1-4a51-a591-06089d356896 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2021, 23:08:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 31D9107118680CD9372FF4BC26FCFDF3 |
| SHA1: | E254348E18AB5B8C39F6EA5BFD288C2689699904 |
| SHA256: | 668BF0250894121B1F9164253A74916C852F697500A1496E8B01DBDEF7D438FF |
| SSDEEP: | 3:mKDDTORn:huRn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 700)
- PurblePlace.exe (PID: 1920)
Executed as Windows Service
- vssvc.exe (PID: 3392)
Reads Environment values
- vssvc.exe (PID: 3392)
Reads the computer name
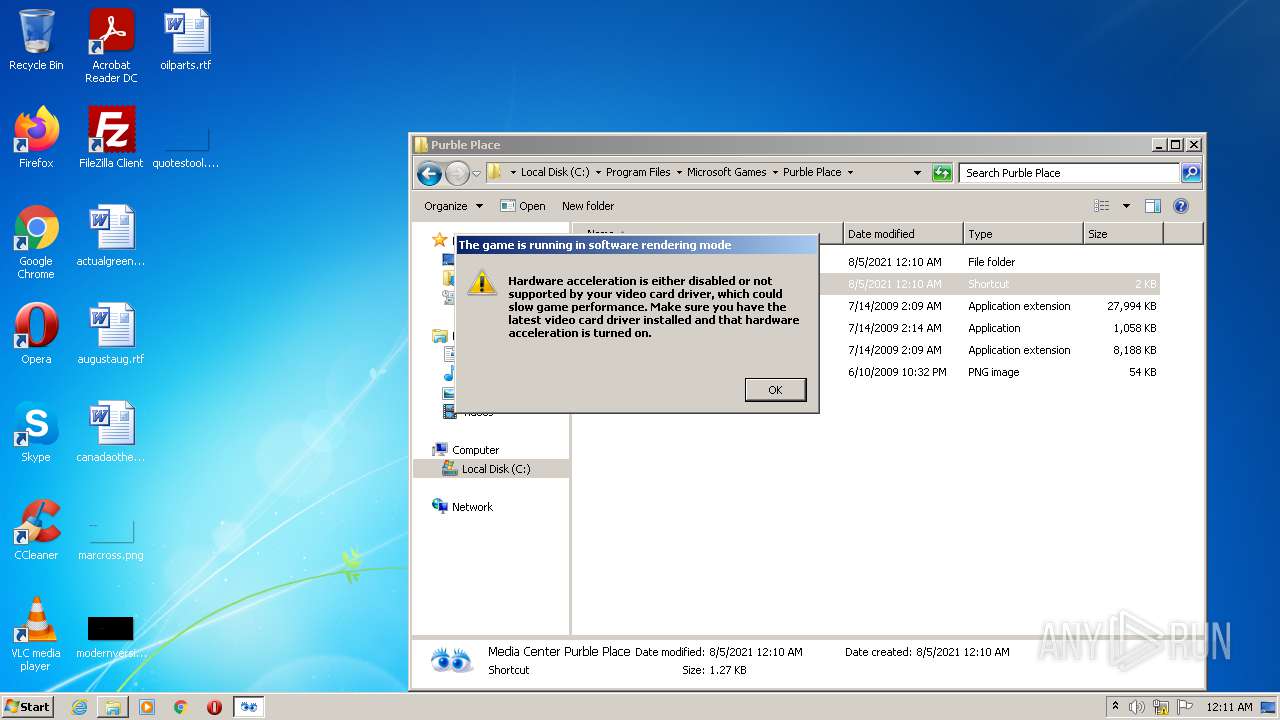
- PurblePlace.exe (PID: 1920)
Writes to a desktop.ini file (may be used to cloak folders)
- PurblePlace.exe (PID: 1920)
INFO
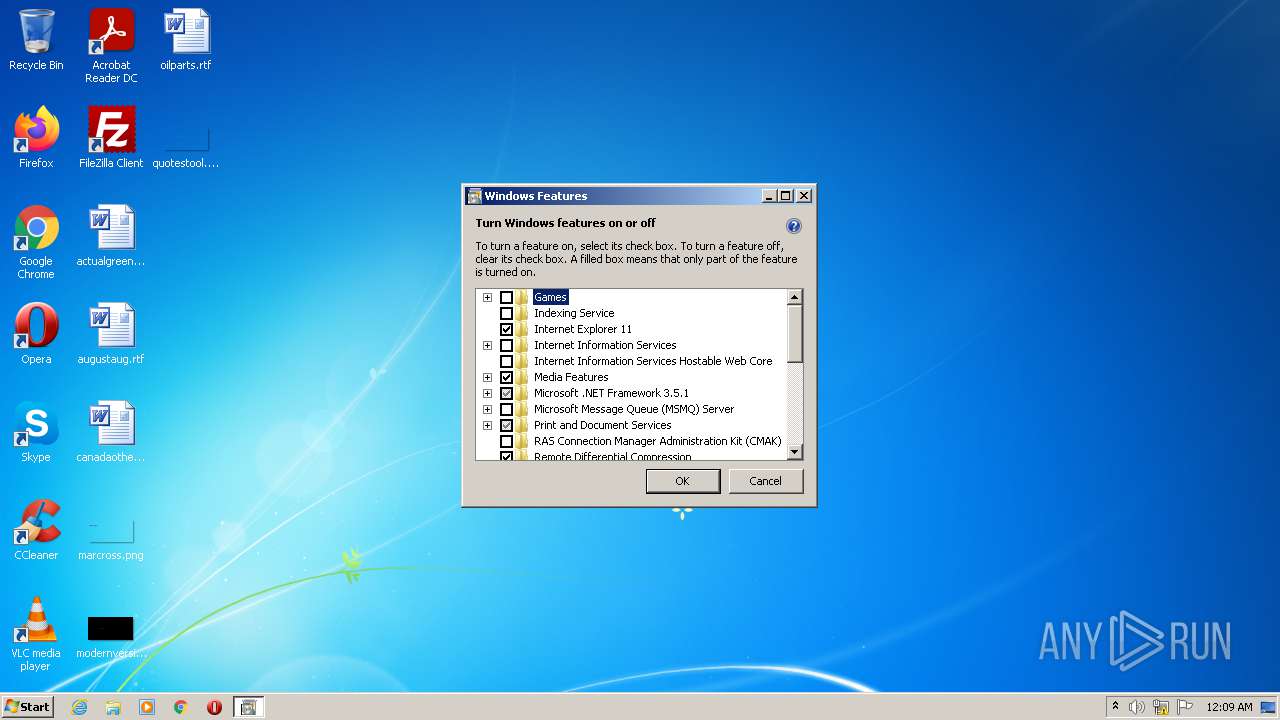
Manual execution by user
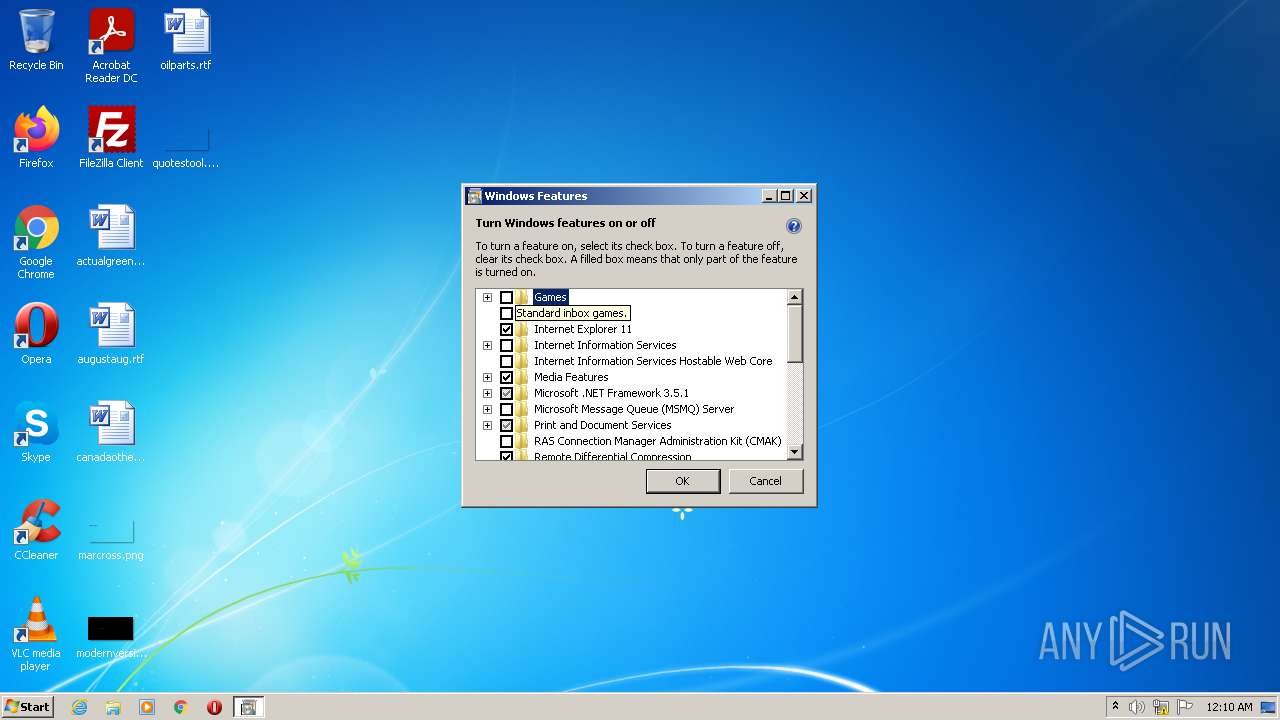
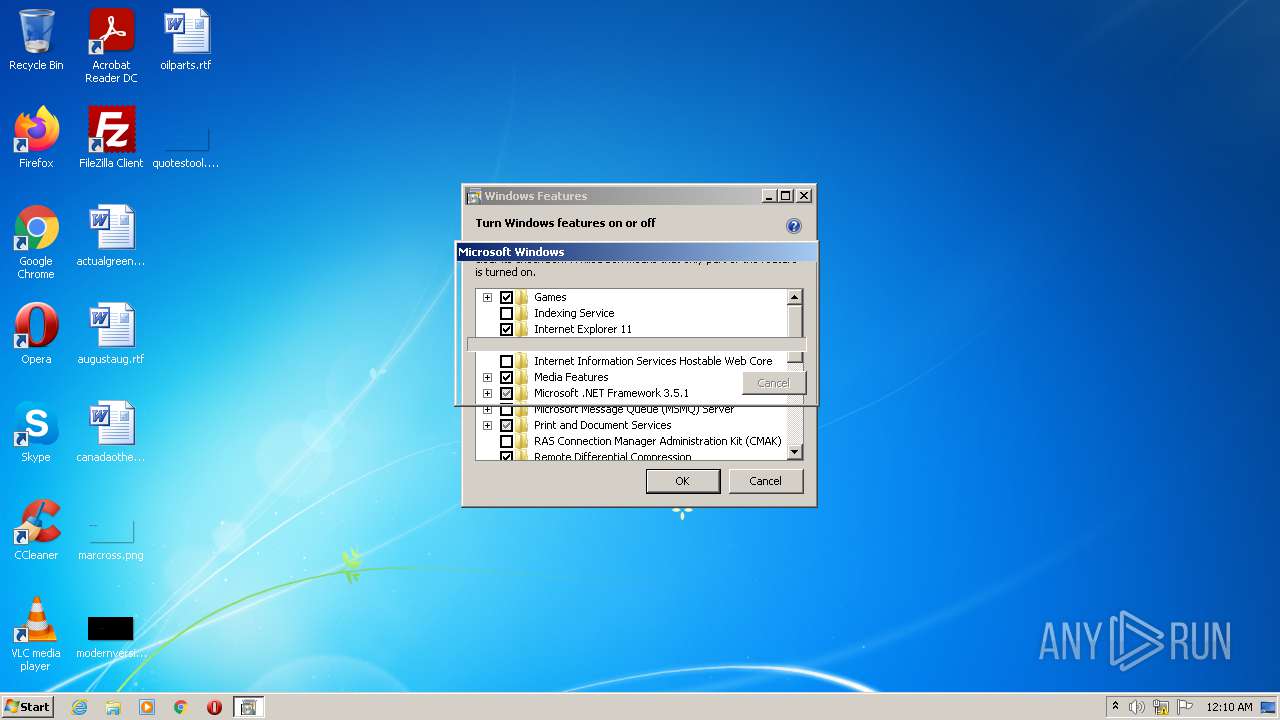
- OptionalFeatures.exe (PID: 2748)
- OptionalFeatures.exe (PID: 932)
- explorer.exe (PID: 3916)
- PurblePlace.exe (PID: 1920)
Checks supported languages
- OptionalFeatures.exe (PID: 2748)
- vssvc.exe (PID: 3392)
- explorer.exe (PID: 3916)
Reads the computer name
- OptionalFeatures.exe (PID: 2748)
- vssvc.exe (PID: 3392)
- explorer.exe (PID: 3916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\exit.cmd" " | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 932 | "C:\Windows\system32\OptionalFeatures.exe" | C:\Windows\system32\OptionalFeatures.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Features Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Microsoft Games\Purble Place\PurblePlace.exe" -mce | C:\Program Files\Microsoft Games\Purble Place\PurblePlace.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Executable for Purble Place Game Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | "C:\Windows\system32\OptionalFeatures.exe" | C:\Windows\system32\OptionalFeatures.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Features Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3392 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3916 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
932
Read events
807
Write events
124
Delete events
1
Modification events
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000177125DE8589D701400D0000800B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000177125DE8589D701400D00005C0F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000177125DE8589D701400D0000C0030000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000177125DE8589D701400D0000740F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000CB352ADE8589D701400D0000800B0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000CB352ADE8589D701400D0000740F0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000CB352ADE8589D701400D0000C0030000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000CB352ADE8589D701400D00005C0F0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 4000000000000000B14BA5DF8589D701400D00005C0F000001040000010000000000000000000000F507D210EF639B4B85F9CD25042C12030000000000000000 | |||
| (PID) Process: | (3392) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Leave) |
Value: 4000000000000000B14BA5DF8589D701400D00005C0F000001040000000000000000000000000000F507D210EF639B4B85F9CD25042C12030000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1920 | PurblePlace.exe | C:\Users\admin\Saved Games\Microsoft Games\desktop.ini | ini | |
MD5:5EBF28B909EC9614CE70C28C01DCE063 | SHA256:8C8C439AF830F98D5C42A7FAD1D3BC2AE510D97075B312B94C48CDC7EC6D5054 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report