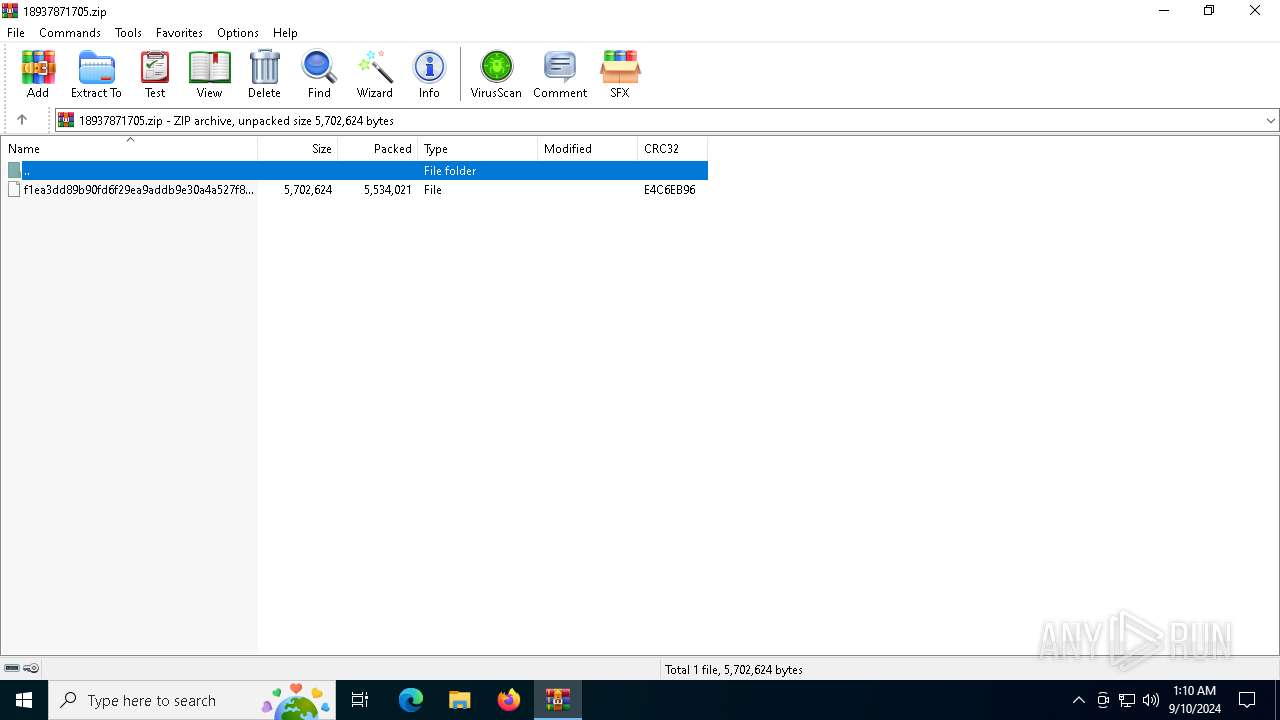
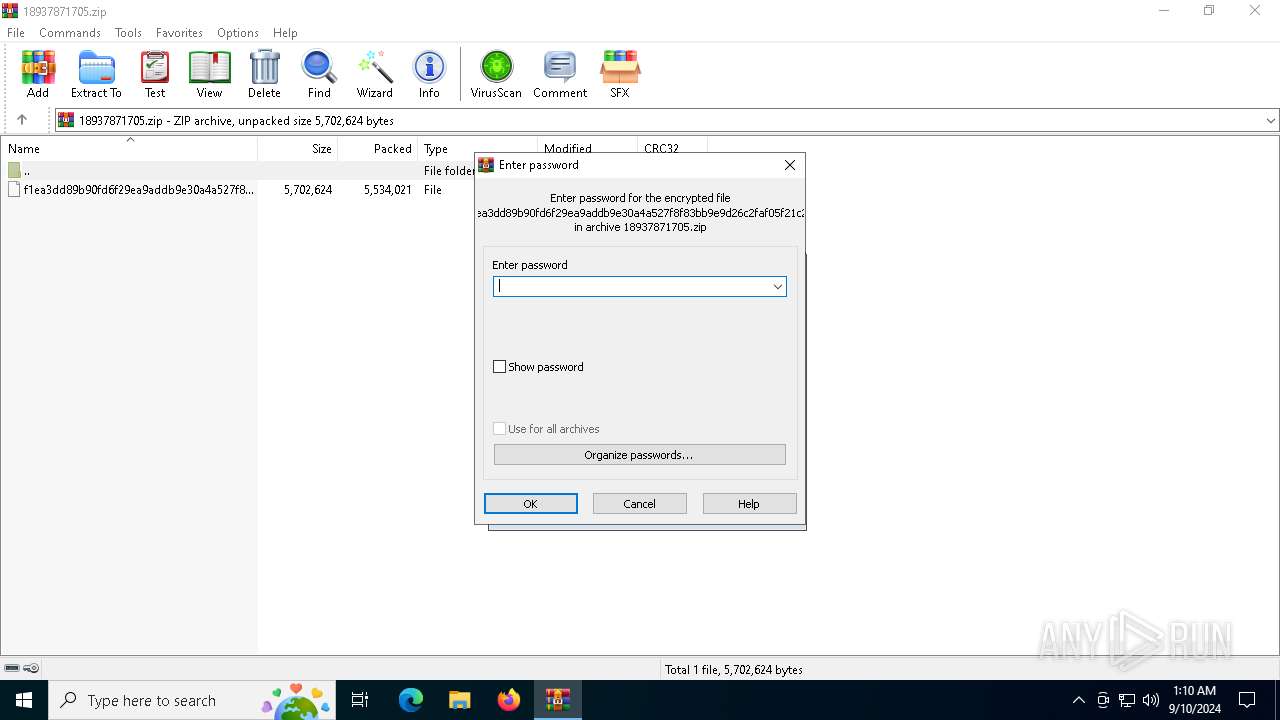
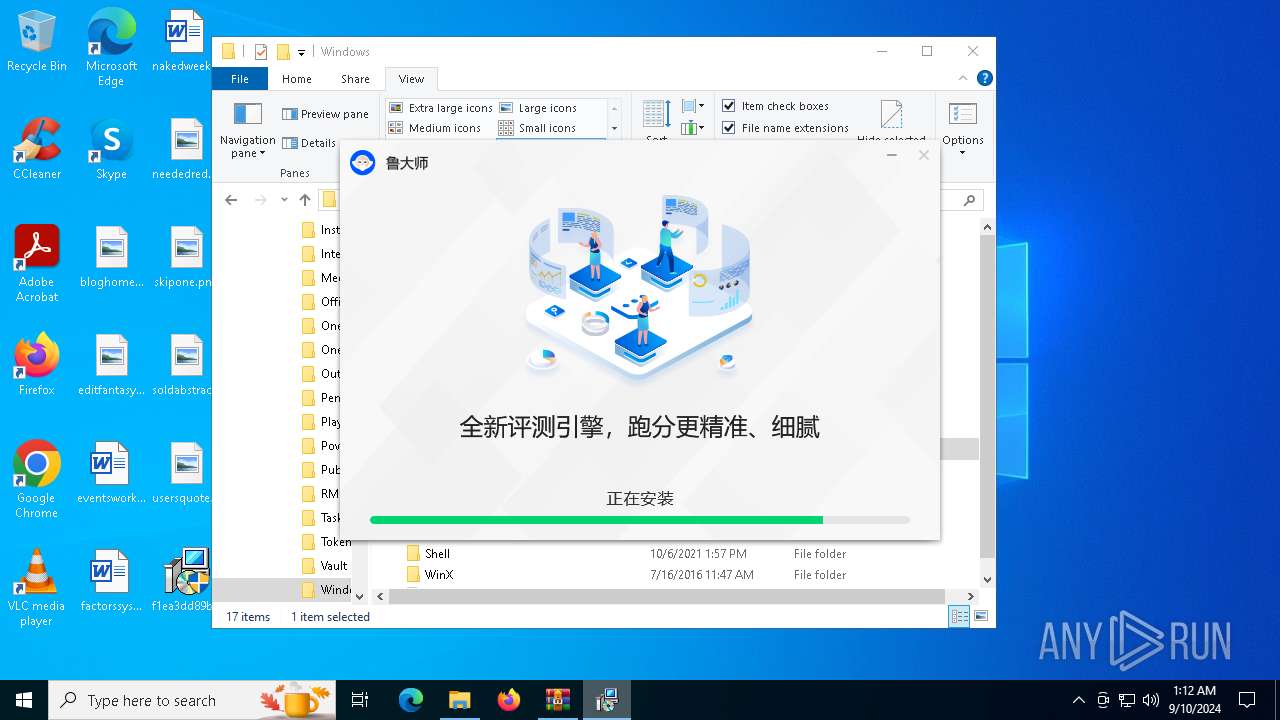
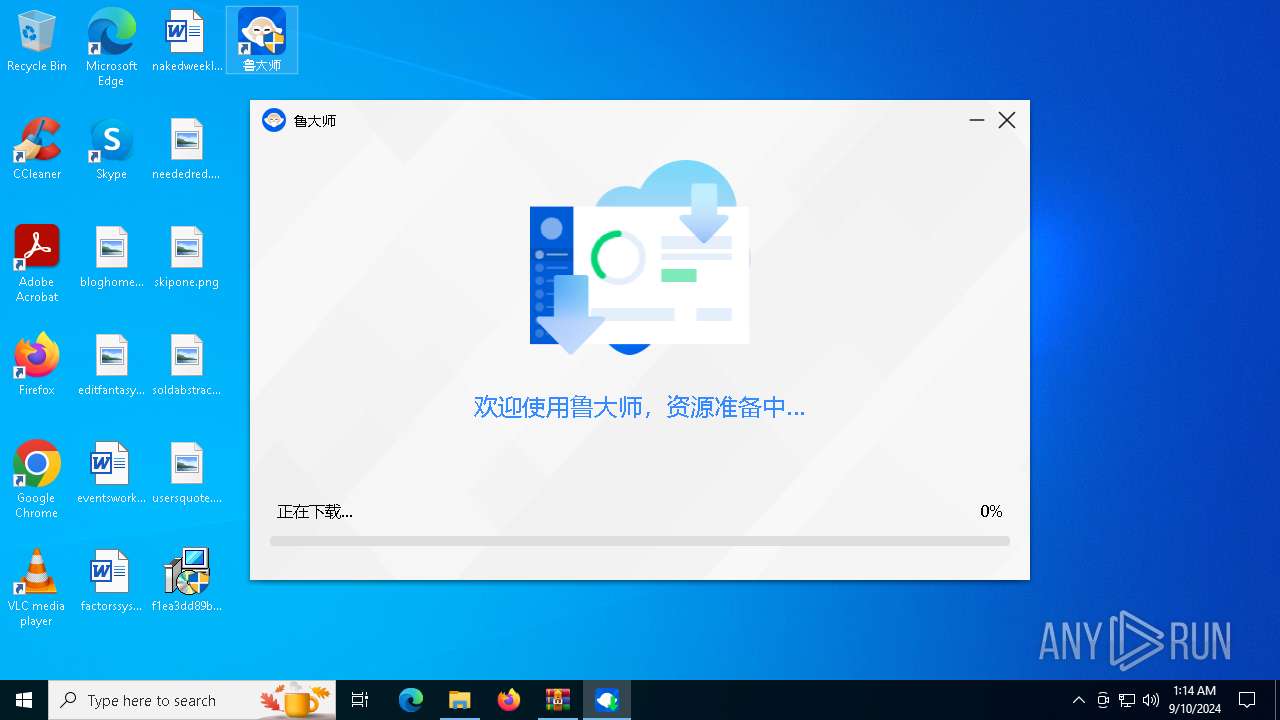
| File name: | 18937871705.zip |
| Full analysis: | https://app.any.run/tasks/8c9941d7-cdde-4525-ba64-2a5e0d5d875b |
| Verdict: | Malicious activity |
| Analysis date: | September 10, 2024, 01:10:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 402D0CEBBC41DE17BB3C6B4B3F894FB2 |
| SHA1: | 472FD8802DAB2EE0CA9140F2A987F5BFE4D60456 |
| SHA256: | 6687DA602A42F25443AB867B9DE0F515094E42C028EE0138DDB64C368EC83FFA |
| SSDEEP: | 98304:PjDseJGPcqKsTOWXJVQ0zxg0RD3ks7259IAA6MLC46DWg3LhNNlzHWO5+oyS910S:+V0k5pbLb6RZhfgK |
MALICIOUS
Creates or modifies Windows services
- ComputerZTray.exe (PID: 6184)
SUSPICIOUS
Reads security settings of Internet Explorer
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- Ldshelper.exe (PID: 6948)
- ComputerZTray.exe (PID: 6184)
- computercenter.exe (PID: 1640)
- dll_service.exe (PID: 4976)
- ComputerZService.exe (PID: 7044)
- dll_service.exe (PID: 1780)
- dll_service.exe (PID: 6056)
- dll_service.exe (PID: 5700)
- ComputerzService_x64.exe (PID: 6268)
- ComputerZ_CN.exe (PID: 3028)
- web_host.exe (PID: 6612)
Searches for installed software
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZTray.exe (PID: 6184)
- computercenter.exe (PID: 1640)
Process requests binary or script from the Internet
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- web_host.exe (PID: 6612)
Checks Windows Trust Settings
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZTray.exe (PID: 6184)
- Ldshelper.exe (PID: 6948)
- computercenter.exe (PID: 1640)
- ComputerZService.exe (PID: 7044)
- dll_service.exe (PID: 4976)
- dll_service.exe (PID: 5700)
- dll_service.exe (PID: 1780)
- dll_service.exe (PID: 6056)
- ComputerzService_x64.exe (PID: 6268)
- ComputerZ_CN.exe (PID: 3028)
- web_host.exe (PID: 6612)
Adds/modifies Windows certificates
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
Drops 7-zip archiver for unpacking
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZ_CN.exe (PID: 3028)
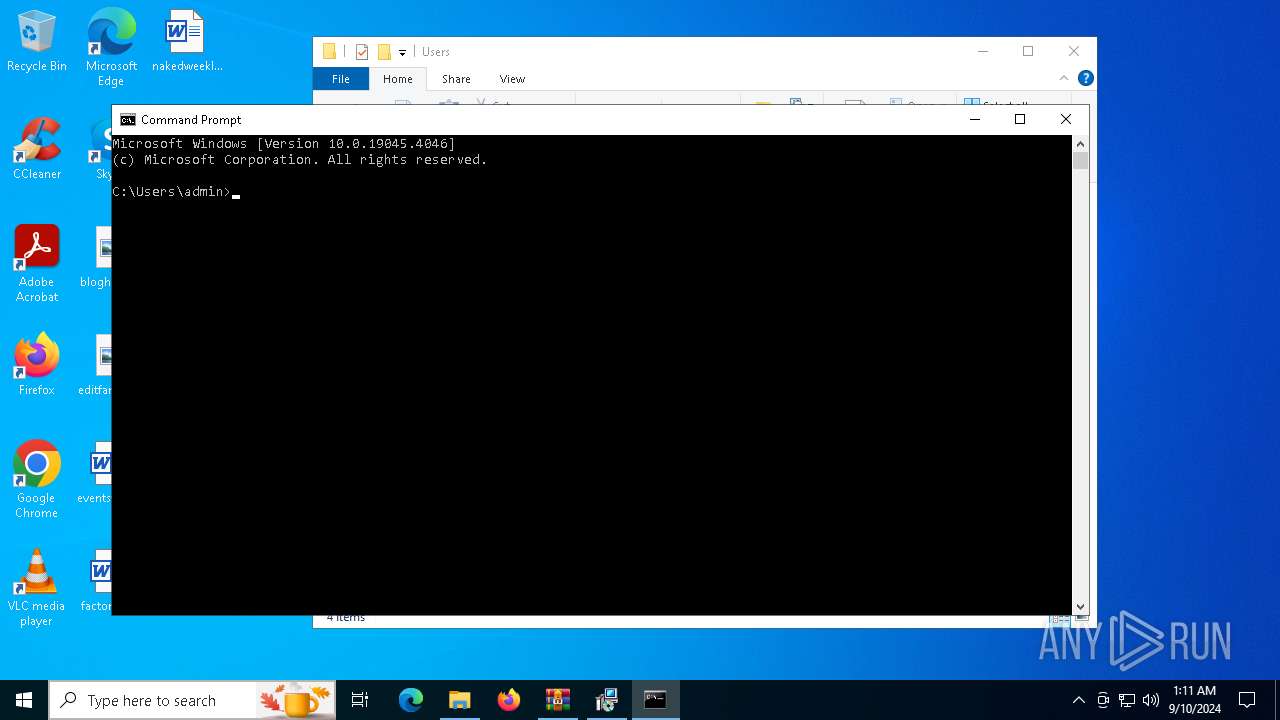
Identifying current user with WHOAMI command
- cmd.exe (PID: 3700)
Drops a system driver (possible attempt to evade defenses)
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
Process drops legitimate windows executable
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZ_CN.exe (PID: 3028)
The process creates files with name similar to system file names
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZ_CN.exe (PID: 3028)
Creates a software uninstall entry
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
Executable content was dropped or overwritten
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZ_CN.exe (PID: 3028)
The process checks if it is being run in the virtual environment
- ComputerZService.exe (PID: 7044)
Reads the date of Windows installation
- ComputerZService.exe (PID: 7044)
Application launched itself
- CefView.exe (PID: 2700)
Potential Corporate Privacy Violation
- web_host.exe (PID: 6612)
There is functionality for VM detection (VMWare)
- CefView.exe (PID: 2700)
- CefView.exe (PID: 4876)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1116)
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZTray.exe (PID: 6184)
Manual execution by a user
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 608)
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- cmd.exe (PID: 3700)
- ComputerZ_CN.exe (PID: 2640)
- ComputerZ_CN.exe (PID: 3028)
Creates files in the program directory
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZService.exe (PID: 7044)
- ComputerZTray.exe (PID: 6184)
Reads the computer name
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZTray.exe (PID: 6184)
- computercenter.exe (PID: 1640)
- ComputerZService.exe (PID: 7044)
- dll_service.exe (PID: 4976)
- dll_service.exe (PID: 5700)
- dll_service.exe (PID: 6056)
- dll_service.exe (PID: 1780)
- ComputerzService_x64.exe (PID: 6268)
- ComputerZ_CN.exe (PID: 3028)
- web_host.exe (PID: 6612)
- Ldshelper.exe (PID: 6948)
- CefView.exe (PID: 2700)
Creates files or folders in the user directory
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- Ldshelper.exe (PID: 6948)
- ComputerZTray.exe (PID: 6184)
- computercenter.exe (PID: 1640)
- ComputerZService.exe (PID: 7044)
- ComputerZ_CN.exe (PID: 3028)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1116)
Checks proxy server information
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- Ldshelper.exe (PID: 6948)
- computercenter.exe (PID: 1640)
- ComputerZTray.exe (PID: 6184)
- ComputerZService.exe (PID: 7044)
- ComputerZ_CN.exe (PID: 3028)
- CefView.exe (PID: 2700)
- web_host.exe (PID: 6612)
Checks supported languages
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- Ldshelper.exe (PID: 6948)
- ComputerZTray.exe (PID: 6184)
- computercenter.exe (PID: 1640)
- ComputerZService.exe (PID: 7044)
- dll_service.exe (PID: 4976)
- dll_service.exe (PID: 5700)
- dll_service.exe (PID: 1780)
- dll_service.exe (PID: 6056)
- ComputerzService_x64.exe (PID: 6268)
- hdw_disk_scan.exe (PID: 5116)
- web_host.exe (PID: 6612)
- ComputerZ_CN.exe (PID: 3028)
- CefView.exe (PID: 4876)
- CefView.exe (PID: 2700)
- CefView.exe (PID: 5172)
Reads the machine GUID from the registry
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- Ldshelper.exe (PID: 6948)
- ComputerZTray.exe (PID: 6184)
- computercenter.exe (PID: 1640)
- ComputerZService.exe (PID: 7044)
- dll_service.exe (PID: 4976)
- dll_service.exe (PID: 1780)
- dll_service.exe (PID: 6056)
- dll_service.exe (PID: 5700)
- ComputerzService_x64.exe (PID: 6268)
- ComputerZ_CN.exe (PID: 3028)
- web_host.exe (PID: 6612)
Create files in a temporary directory
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZ_CN.exe (PID: 3028)
- CefView.exe (PID: 2700)
- web_host.exe (PID: 6612)
- CefView.exe (PID: 5172)
Process checks computer location settings
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZTray.exe (PID: 6184)
Reads the software policy settings
- Ldshelper.exe (PID: 6948)
- f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe (PID: 2624)
- ComputerZTray.exe (PID: 6184)
- ComputerZService.exe (PID: 7044)
- computercenter.exe (PID: 1640)
- dll_service.exe (PID: 4976)
- dll_service.exe (PID: 5700)
- dll_service.exe (PID: 6056)
- dll_service.exe (PID: 1780)
- ComputerzService_x64.exe (PID: 6268)
- ComputerZ_CN.exe (PID: 3028)
- web_host.exe (PID: 6612)
Disables trace logs
- computercenter.exe (PID: 1640)
Sends debugging messages
- CefView.exe (PID: 2700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xe4c6eb96 |
| ZipCompressedSize: | 5534021 |
| ZipUncompressedSize: | 5702624 |
| ZipFileName: | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa |
Total processes
161
Monitored processes
24
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | "C:\Users\admin\Desktop\f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe" | C:\Users\admin\Desktop\f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 应用程序 Exit code: 3221226540 Version: 6.1024.1225.801 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\18937871705.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1172 | C:\WINDOWS\system32\wbem\unsecapp.exe -Embedding | C:\Windows\System32\wbem\unsecapp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Sink to receive asynchronous callbacks for WMI client application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | "C:\Program Files (x86)\Ludashi\computercenter.exe" "C:\Program Files (x86)\Ludashi\ComputerZTray.exe" /NoFloat /disable_panel /disable_temp_alarm /HideBand | C:\Program Files (x86)\Ludashi\computercenter.exe | ComputerZTray.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 常规模块 Version: 1.5022.1020.926 Modules
| |||||||||||||||
| 1688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1780 | "C:\Program Files (x86)\Ludashi\Utils\dll_service.exe" --dll="ComputerZ_HardwareDll.dll" --entry="NvidiaMonitorSizeOfProcess" --wnd=394068 | C:\Program Files (x86)\Ludashi\Utils\dll_service.exe | — | ComputerZService.exe | |||||||||||
User: admin Integrity Level: HIGH Description: 鲁大师 Exit code: 0 Version: 2.1022.1025.920 Modules
| |||||||||||||||
| 2132 | whoami | C:\Windows\System32\whoami.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2624 | "C:\Users\admin\Desktop\f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe" | C:\Users\admin\Desktop\f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 应用程序 Exit code: 0 Version: 6.1024.1225.801 Modules
| |||||||||||||||
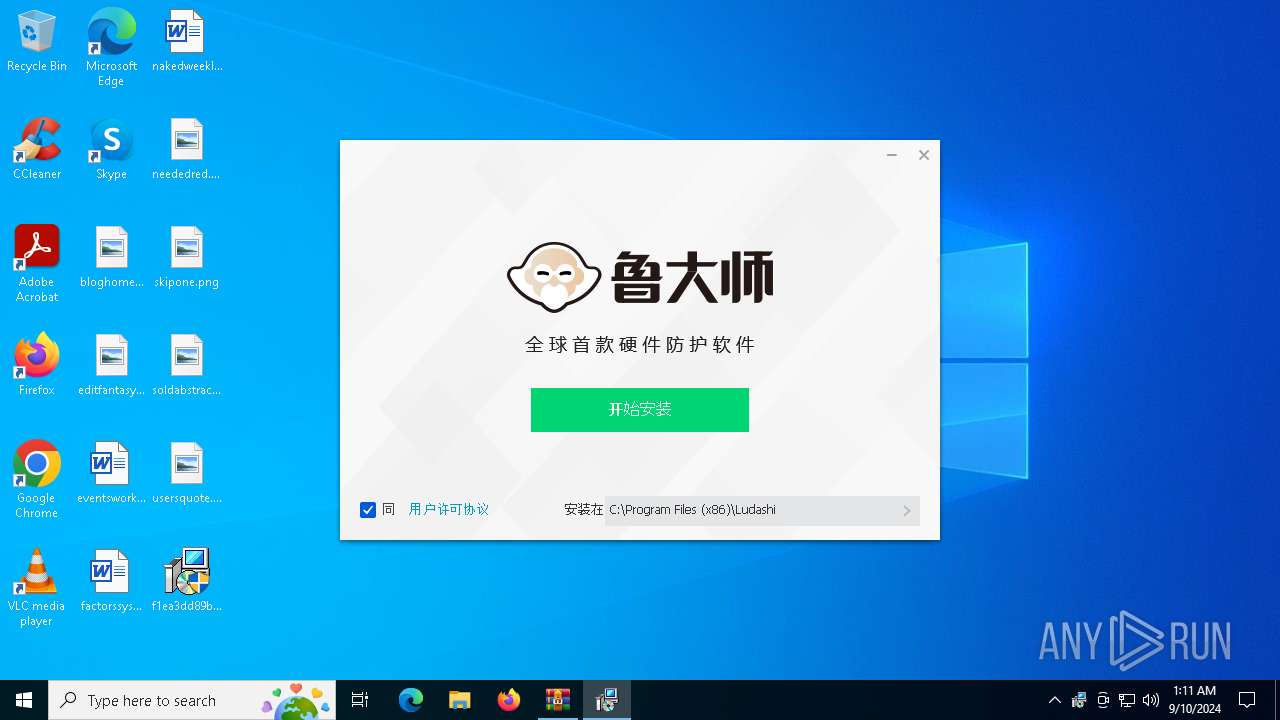
| 2640 | "C:\Program Files (x86)\Ludashi\ComputerZ_CN.exe" --from=deskshortcut | C:\Program Files (x86)\Ludashi\ComputerZ_CN.exe | — | explorer.exe | |||||||||||
User: admin Company: 鲁大师 Integrity Level: MEDIUM Description: 鲁大师 Exit code: 3221226540 Version: 6.1022.3440.1020 Modules
| |||||||||||||||
| 2700 | "C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Utils\cef\CefView.exe" --parent_wnd=6022a --tab_rect="0,0,0,0" --tab_ids="96E97364-CC39-4f35-ACA5-20293B106F08" --cmd="" --disable-gpu --disable-gpu-compositing --enable_high_dpi --class_name="common_pop" --url="about:blank" --tab_group_ids="B8562B65-8F83-4043-A018-473CFEAB1F22" --web_view_id=256 --disable-pinch --disable-web-security --disable-alt-f4 | C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Utils\cef\CefView.exe | web_host.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: CefView Application Version: 2.5022.3155.822 Modules
| |||||||||||||||
Total events
73 027
Read events
72 941
Write events
80
Delete events
6
Modification events
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\18937871705.zip | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1116) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2624) f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CommonDown |
| Operation: | write | Name: | guid |
Value: {00B162BB-6172-430c-A6D3-1FF6CF5EDDC4} | |||
| (PID) Process: | (2624) f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
258
Suspicious files
184
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\ludashi_home_20221101[1].dll | — | |
MD5:— | SHA256:— | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\Roaming\ludashi\setup.dll | — | |
MD5:— | SHA256:— | |||
| 1116 | WinRAR.exe | C:\Users\admin\Desktop\f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa | executable | |
MD5:5D04DA31238FF20998723B09AFFD65D3 | SHA256:F1EA3DD89B90FD6F29EA9ADDB9E30A4A527F8F83BB9E9D26C2FAF05F21C209AA | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\pc[1].htm | binary | |
MD5:ADA78A022EA49F281EC66C46D0E079C2 | SHA256:B96FFF2E4EDB3BD0C1ED901021B69A2DFFE7040B022A409B47A66EC4A00D9E91 | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Program Files (x86)\Ludashi\{F5C3FE7D-3D22-4c6f-9987-3EC29E53438B}.tf | binary | |
MD5:FEAAC8EFE00973FD7AA746BD949EC239 | SHA256:8EAE42DBD6126493745328DC878956783BB6A6921FEFC3AC6034FB3C029B768D | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\ProgramData\{66F97E9E-362B-479b-BB4B-C4F0E8A2885F}.tmp\{78F0A570-1E78-4565-B18F-2A101774E4D1}.tf | binary | |
MD5:1F5BD0608CA0921AF8AAF8161A56FCA5 | SHA256:AAAB2EE5DE0499DE636D74CA507E39D93B61E24FB8FC0CA5A909BDB01DEC41CF | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\14561BF7422BB6F70A9CB14F5AA8A7DA_42A89BACAFEBDA5BA7ACA698B685B848 | der | |
MD5:019ED0974145E8B7771342FC83DB2BA0 | SHA256:214E2303FEBC534185FA65A88CE7012CC417087116D10A351E629F5E9F22655F | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\Local\Temp\{A8E77C2E-D348-4d18-A5C1-F964134F811F}.tmp | compressed | |
MD5:9DA6DACE324AAD8BCA288D5DFE267FB8 | SHA256:5A46FBEFD0500123D3EE5AAC57130E847C39DE687F97BA89A599388F9389CFB1 | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\Local\Temp\{95945603-ED6C-4eb8-B18D-03C1D4A9EA01}.tf | binary | |
MD5:477DE9FC24E69B851927116CCE3F07DD | SHA256:90849DB7F1BF1011F178F3A8821F454D62EE2C6A123068D4C8269BBB5FC184A4 | |||
| 2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | C:\Users\admin\AppData\Local\Temp\{7D2BA8F3-CC74-48cf-8B4B-D3BD37540EC7}.tmp\LDS.LDSPRJ | xml | |
MD5:D354A1B272A6E5B91FD0CF09A358E585 | SHA256:2CAB72A27A9D5058976B2EB547C38B95506492F949F59CBB0A3450B900BD5569 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
97
TCP/UDP connections
113
DNS requests
33
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6364 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6108 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | GET | 200 | 106.15.139.192:80 | http://s.ludashi.com/url2?pid=buysite_00&type=xzq&action=down_start&appver=6.1024.1225.801&modver=6.1024.1225.801&mid=80342cb959da2233832ae840f019ccba&ex_ary[method]=aliyun&ex_ary[url]=https://cdn-file-ssl-pc.ludashi.com/pc/installer/ludashi_home_20221101.dll&ex_ary[type]=1&ex_ary[siteid]=&ex_ary[softid]=&ex_ary[os]=10.0.19045&ex_ary[sr]=0&ex_ary[bit]=1&ex_ary[tagid]= | unknown | — | — | whitelisted |
2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | GET | 200 | 49.4.55.6:80 | http://softmgr-cfg.ludashi.com/inst/get3 | unknown | — | — | unknown |
2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | GET | 200 | 106.15.139.192:80 | http://s.ludashi.com/url2?pid=buysite_00&type=xzq&action=ldsdownstart&appver=6.1024.1225.801&modver=6.1024.1225.801&mid=80342cb959da2233832ae840f019ccba&ex_ary[siteid]=&ex_ary[softid]=&ex_ary[os]=10.0.19045&ex_ary[sr]=0&ex_ary[bit]=1&ex_ary[tagid]= | unknown | — | — | whitelisted |
6440 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6440 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | POST | 200 | 114.115.204.103:80 | http://softmgr-stat.ludashi.com/downloader/soft/reportNew | unknown | — | — | unknown |
2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoFmyX1Sz2HlMxmMUd1OKM%3D | unknown | — | — | whitelisted |
2624 | f1ea3dd89b90fd6f29ea9addb9e30a4a527f8f83bb9e9d26c2faf05f21c209aa.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQlOydjtpho0%2Bholo77zGjGxETUEQQU8JyF%2FaKffY%2FJaLvV1IlNHb7TkP8CEA7t2z9YiVEKqNV8oV82zTU%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6208 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6364 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6364 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6364 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6108 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6108 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
softmgr-cfg.ludashi.com |
| whitelisted |
softmgr-stat.ludashi.com |
| whitelisted |
s.ludashi.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6612 | web_host.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
CefView.exe | Message: 下载路径==== C:\Users\admin\AppData\Local\Temp\ludashisetup_download.exe
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: statParam
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: beforeCefDownloadFile:
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: CefDownloadFile:
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: progres_data
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: progres_data
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: progres_data
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: progres_data
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: progres_data
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|
CefView.exe | Message: progres_data
Source: zip://0CA42E8A-E041-492E-B7C2-703494DED02F|C:\Users\admin\AppData\Local\Temp\{55CA764D-1876-4964-B25C-1ADD2B6026AD}\Themes\UI\lite_download.dat|/build/static/js/main.af70f3cc.js
Line: 2
-----------------------
|