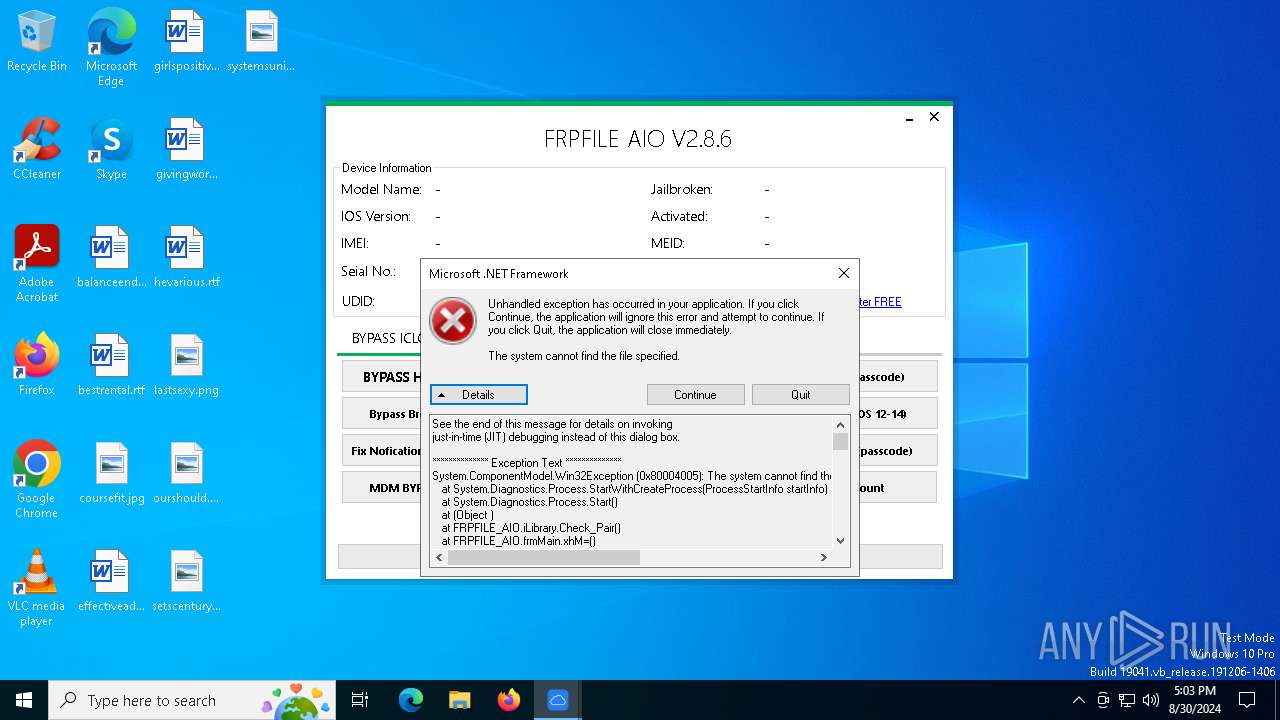
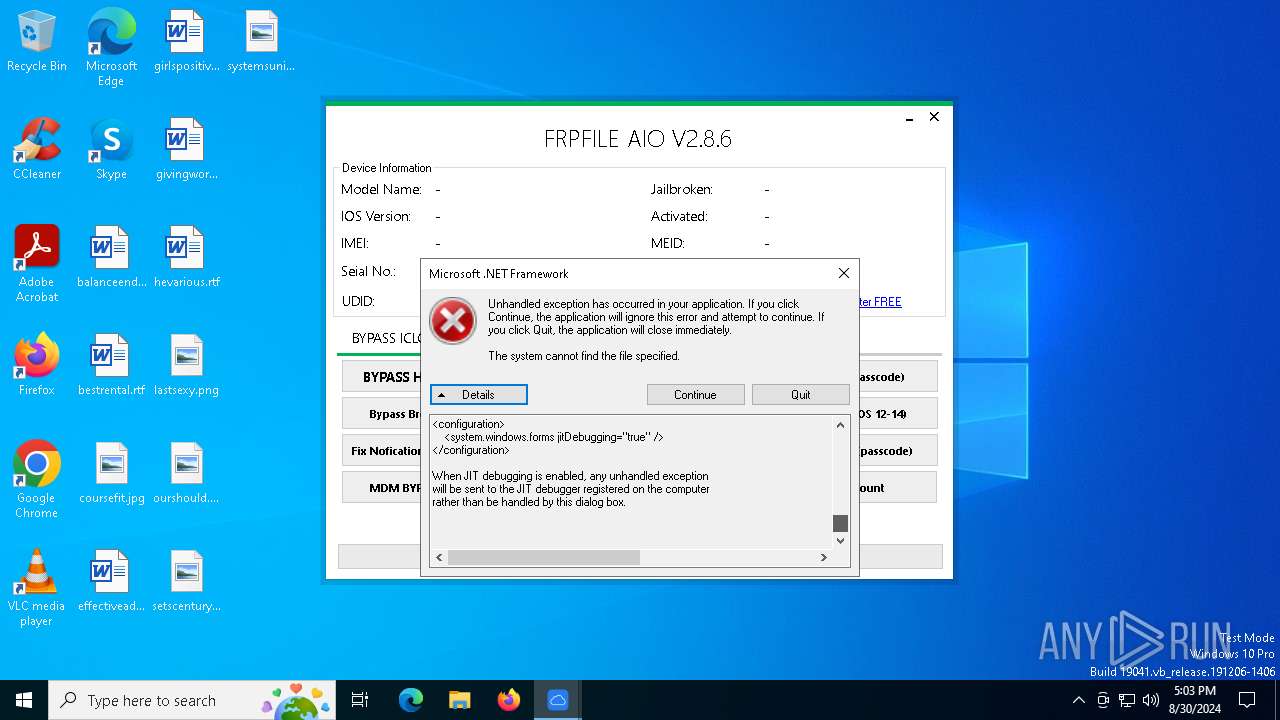
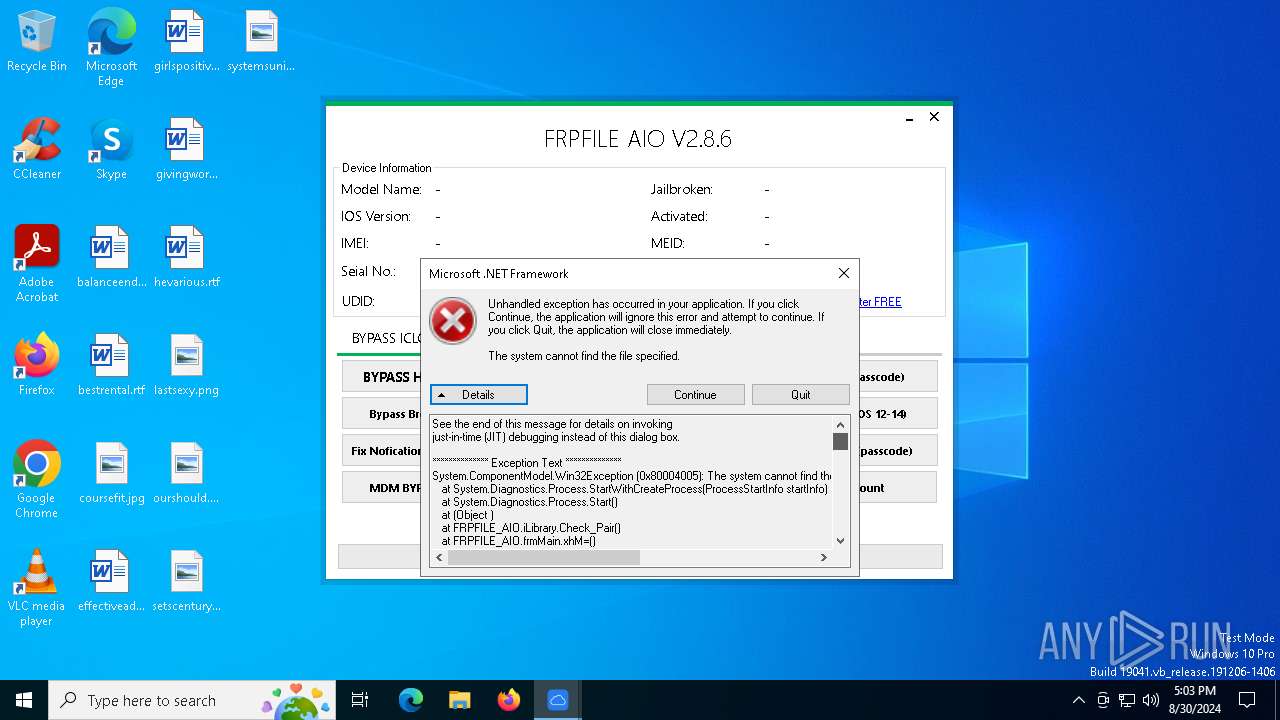
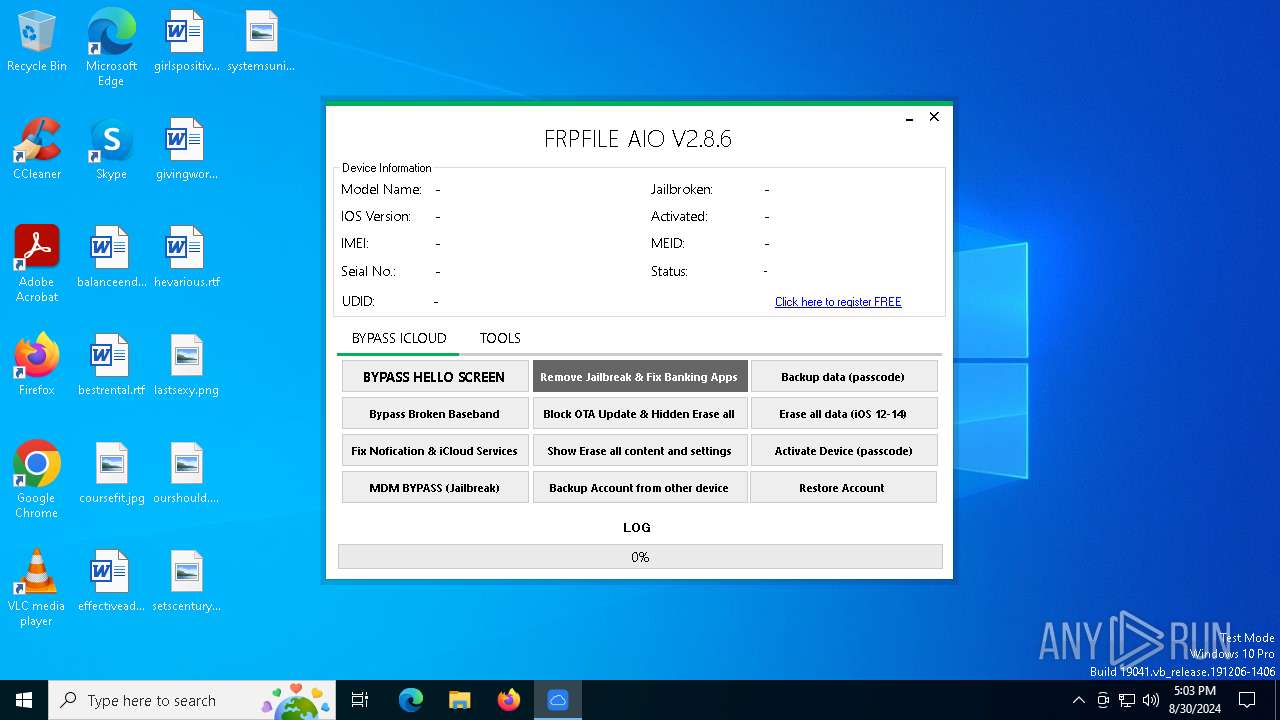
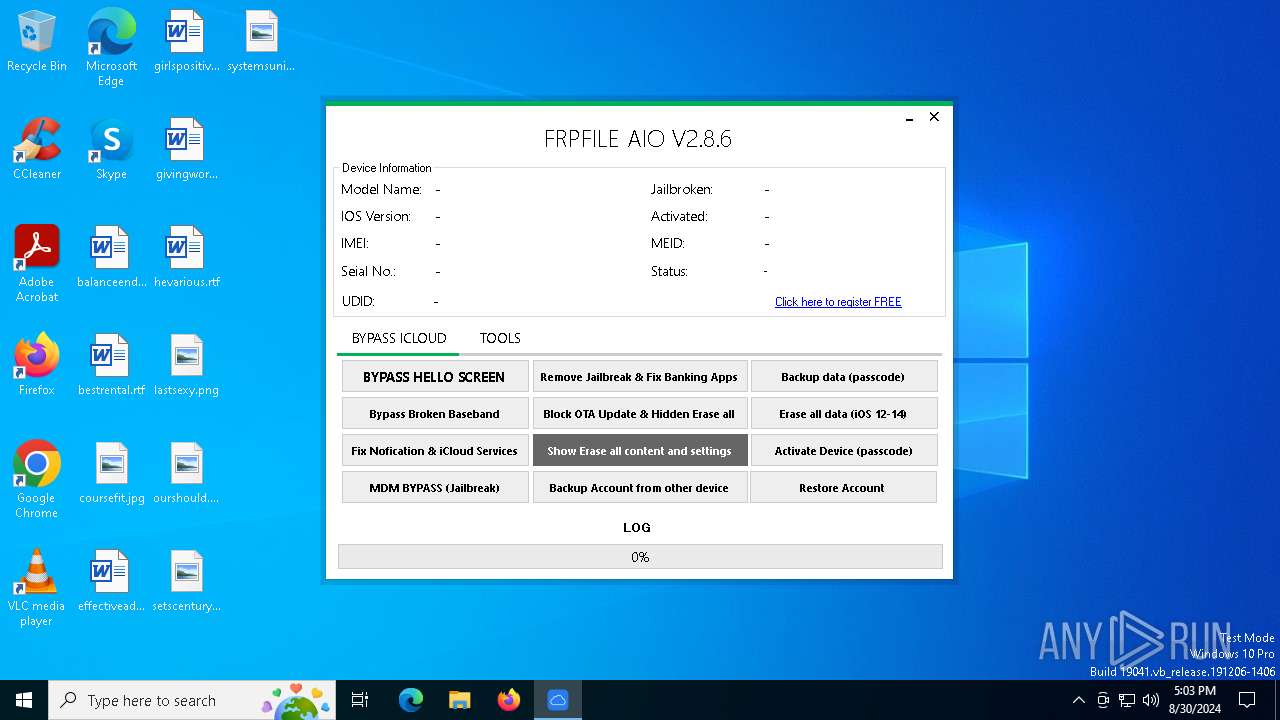
| File name: | iFRPFILE AIO v2.8.6.exe |
| Full analysis: | https://app.any.run/tasks/2b040fec-0ba9-438b-a557-c1b0bc12361b |
| Verdict: | Malicious activity |
| Analysis date: | August 30, 2024, 17:02:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 549C4D3E3B61E4FF254CBD91DBD68AC6 |
| SHA1: | 0EBB5D38ACF3644FF61652B0CE66454C162D1CE5 |
| SHA256: | 667F8C9BFB3FBBE9E22527CC4F4377397B75E0756876AF5824C2518E1A343805 |
| SSDEEP: | 98304:tH/nceJrEELjv3hOrIv8BS7zwb6BybZUEHvblMmjpOlFI5nZNcZoGqh7qecGAFtg:jwKHjIXEeFJuqlDy52u0z6e0c |
MALICIOUS
No malicious indicators.SUSPICIOUS
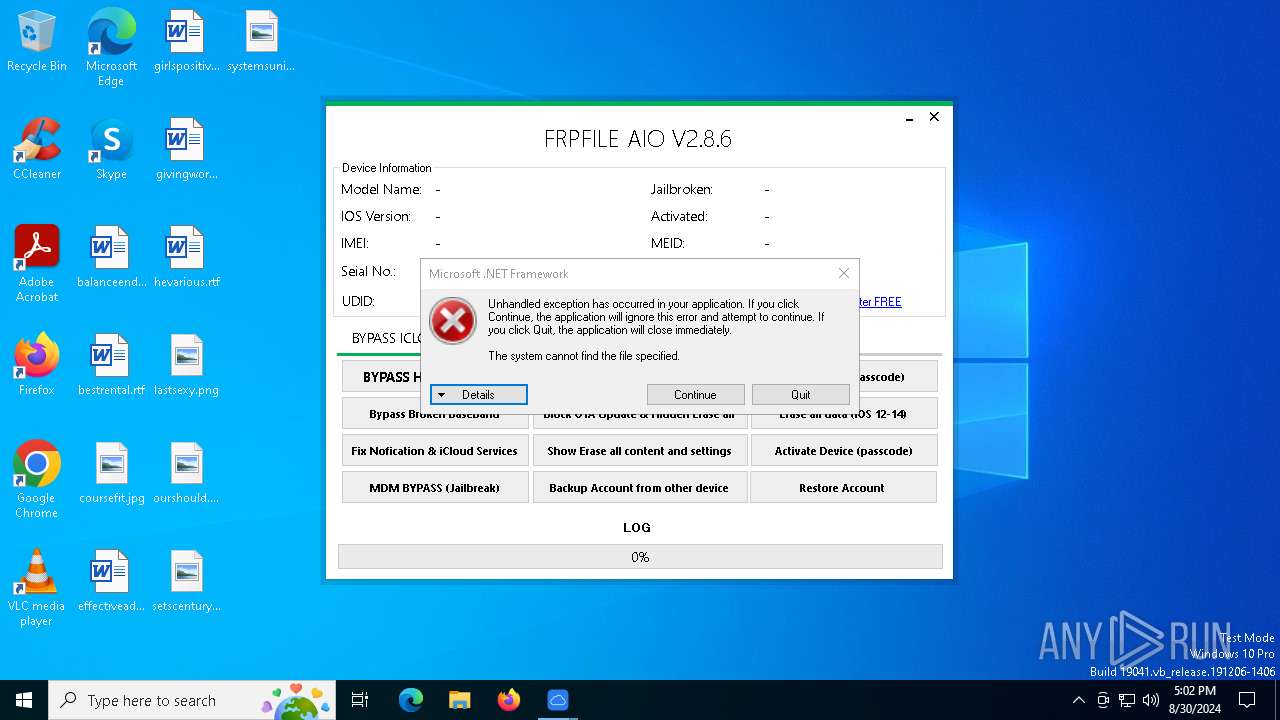
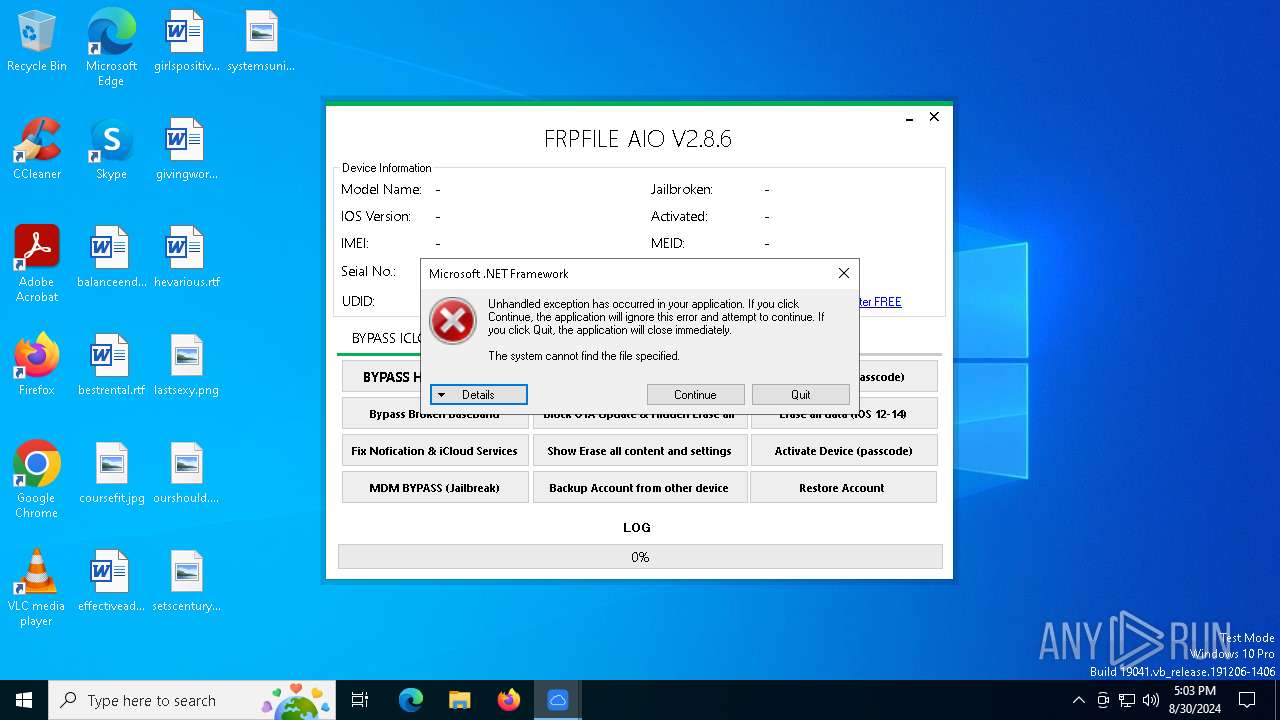
Drops the executable file immediately after the start
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads the BIOS version
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Executable content was dropped or overwritten
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Checks Windows Trust Settings
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads security settings of Internet Explorer
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads Internet Explorer settings
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
INFO
Checks supported languages
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Create files in a temporary directory
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads the computer name
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads the machine GUID from the registry
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads the software policy settings
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Checks proxy server information
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Reads Environment values
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Creates files or folders in the user directory
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Disables trace logs
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Themida protector has been detected
- iFRPFILE AIO v2.8.6.exe (PID: 6676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2092:07:02 22:28:13+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 10967552 |
| InitializedDataSize: | 10986496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7785a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | FRPFILE AIO |
| FileVersion: | 1.0.0.0 |
| InternalName: | iFRPFILE AIO v2.8.6.exe |
| LegalCopyright: | Copyright © 2021 |
| LegalTrademarks: | - |
| OriginalFileName: | iFRPFILE AIO v2.8.6.exe |
| ProductName: | FRPFILE AIO |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
131
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5140 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | "C:\Users\admin\AppData\Local\Temp\iFRPFILE AIO v2.8.6.exe" | C:\Users\admin\AppData\Local\Temp\iFRPFILE AIO v2.8.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: FRPFILE AIO Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 346
Read events
4 331
Write events
15
Delete events
0
Modification events
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6676) iFRPFILE AIO v2.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\iFRPFILE AIO v2_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
1
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6676 | iFRPFILE AIO v2.8.6.exe | C:\Users\admin\AppData\Local\Temp\a86bb849-070d-44b1-a95a-a705e8153629\AgileDotNetRT.dll | executable | |
MD5:1E275530F75EC0222AD0A49117819936 | SHA256:D8519A2A1F40BAEB1EE2E6EB1ACA27745E5DCAB7C046D65B27246E24AF57D2BB | |||
| 6676 | iFRPFILE AIO v2.8.6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 6676 | iFRPFILE AIO v2.8.6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0018BB1B5834735BFA60CD063B31956 | der | |
MD5:732CFEB76B91C4D13978A00B8C666ED7 | SHA256:9FAB9FC0A1DA813E6DDB93904C1FCFA6546CFBE70747FF8468DDD14D2552DBD2 | |||
| 6676 | iFRPFILE AIO v2.8.6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C0018BB1B5834735BFA60CD063B31956 | binary | |
MD5:AC992A557D129211405A277EA56C2740 | SHA256:C9257954AE2915D37DDE136CDB413D36E246155BD59C670B6BB7532A567056A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6676 | iFRPFILE AIO v2.8.6.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6676 | iFRPFILE AIO v2.8.6.exe | GET | 200 | 167.179.69.45:80 | http://frpfile.online/server-free/deviceActivation/version.php | unknown | — | — | unknown |
2032 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5504 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5504 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6164 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4276 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6676 | iFRPFILE AIO v2.8.6.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6676 | iFRPFILE AIO v2.8.6.exe | 167.179.69.45:80 | frpfile.online | AS-CHOOPA | JP | unknown |
6164 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2032 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
frpfile.online |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |