| File name: | rechnungen.doc.zip |
| Full analysis: | https://app.any.run/tasks/6056163f-f7e8-4b80-8f0b-3834561428ee |
| Verdict: | Malicious activity |
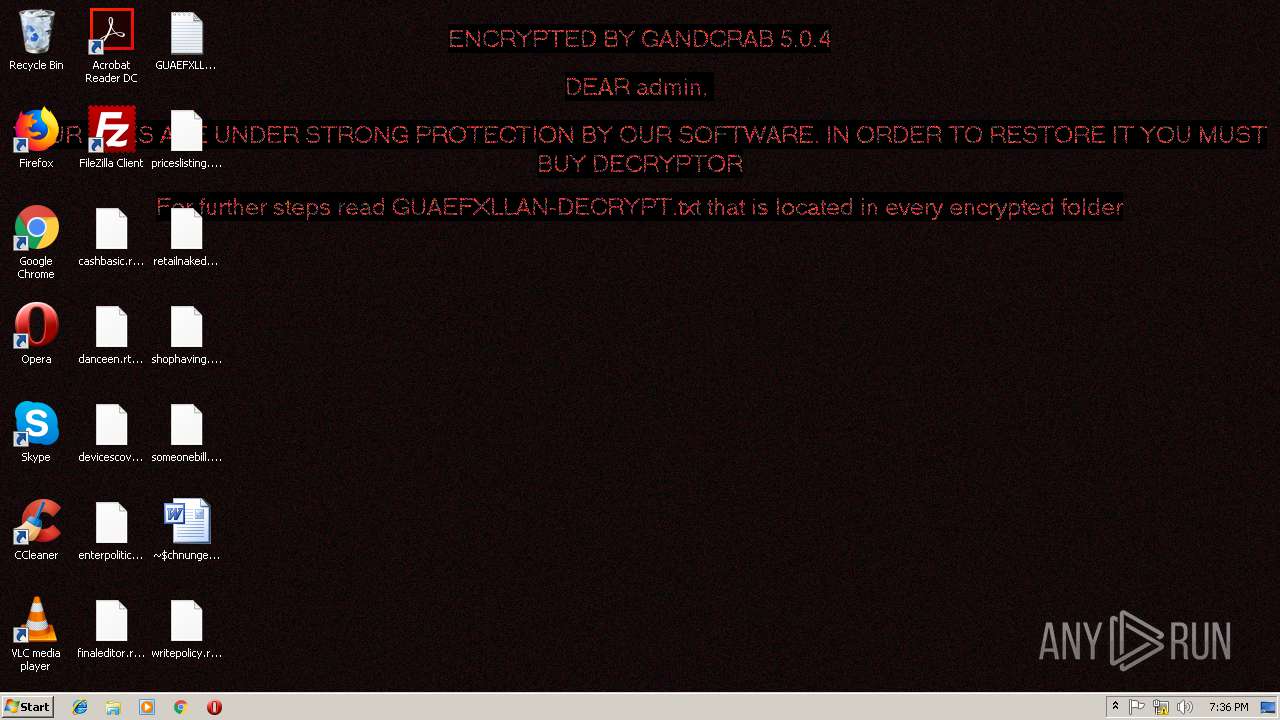
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 10, 2019, 19:34:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 93B8A960C9BDC145CAC212C84091EAA6 |
| SHA1: | 964610793676DD023D3E5080D3B3EA2231A222B8 |
| SHA256: | 66695450843DEB563E4E8CC11655125367AD54A84F3C277D4283CD6DF0D1B13B |
| SSDEEP: | 384:s96rTiO8h/dGuVlMkYEPxjk0fr5mBQs8nPugK+T+Vipm44g1o42edIa:JrTXE/cu8kzjnjwOPugKmgipm9g12e5 |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2364)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2364)
GandCrab keys found
- yeZjqHFMWjXi.exe (PID: 2872)
Writes file to Word startup folder
- yeZjqHFMWjXi.exe (PID: 2872)
Application was dropped or rewritten from another process
- yeZjqHFMWjXi.exe (PID: 2872)
Actions looks like stealing of personal data
- yeZjqHFMWjXi.exe (PID: 2872)
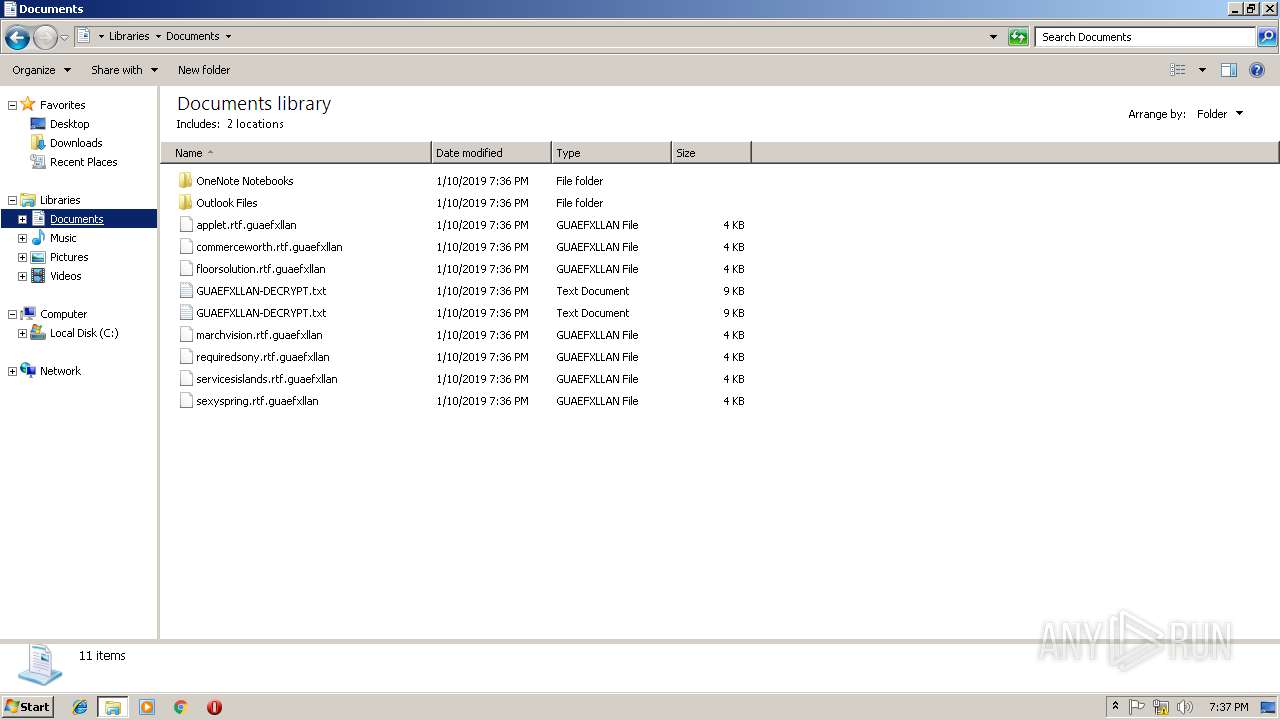
Dropped file may contain instructions of ransomware
- yeZjqHFMWjXi.exe (PID: 2872)
Requests a remote executable file from MS Office
- WINWORD.EXE (PID: 2364)
Connects to CnC server
- yeZjqHFMWjXi.exe (PID: 2872)
Deletes shadow copies
- yeZjqHFMWjXi.exe (PID: 2872)
Renames files like Ransomware
- yeZjqHFMWjXi.exe (PID: 2872)
SUSPICIOUS
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 2364)
Reads the cookies of Mozilla Firefox
- yeZjqHFMWjXi.exe (PID: 2872)
Creates files like Ransomware instruction
- yeZjqHFMWjXi.exe (PID: 2872)
Creates files in the user directory
- yeZjqHFMWjXi.exe (PID: 2872)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2364)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2364)
Dropped object may contain TOR URL's
- yeZjqHFMWjXi.exe (PID: 2872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:10 00:19:24 |
| ZipCRC: | 0xd0ce65af |
| ZipCompressedSize: | 25629 |
| ZipUncompressedSize: | 65536 |
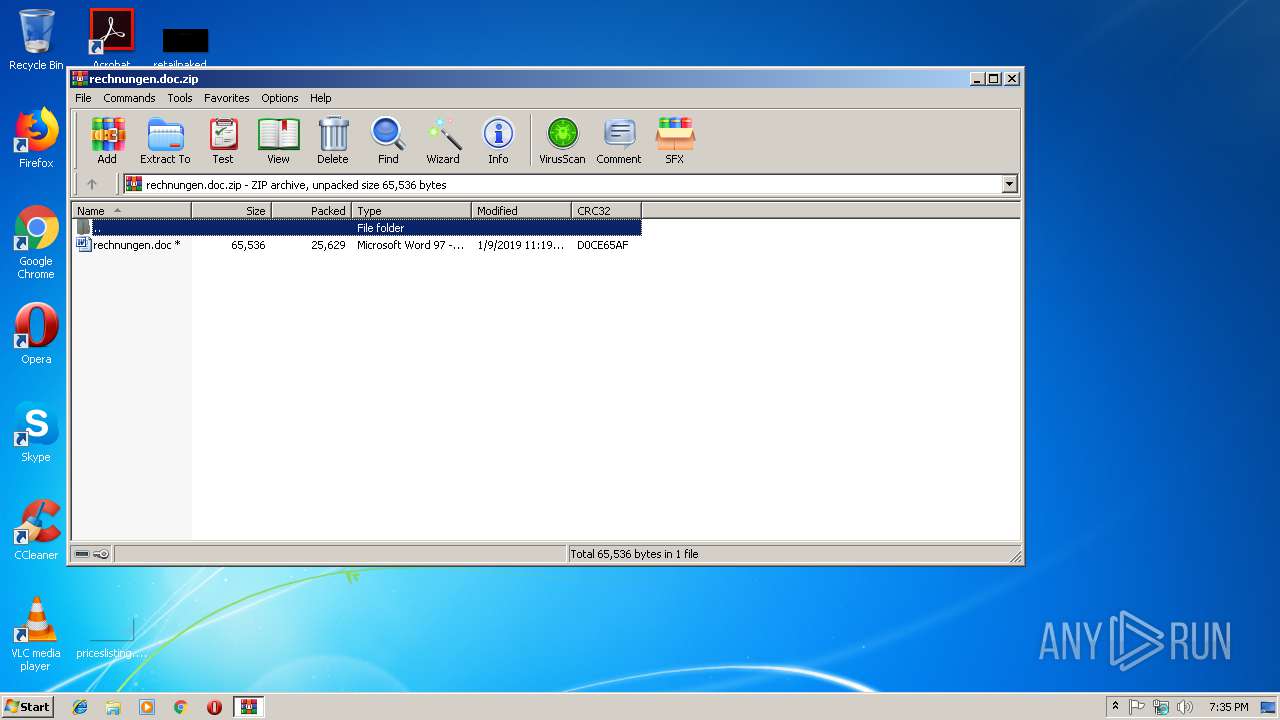
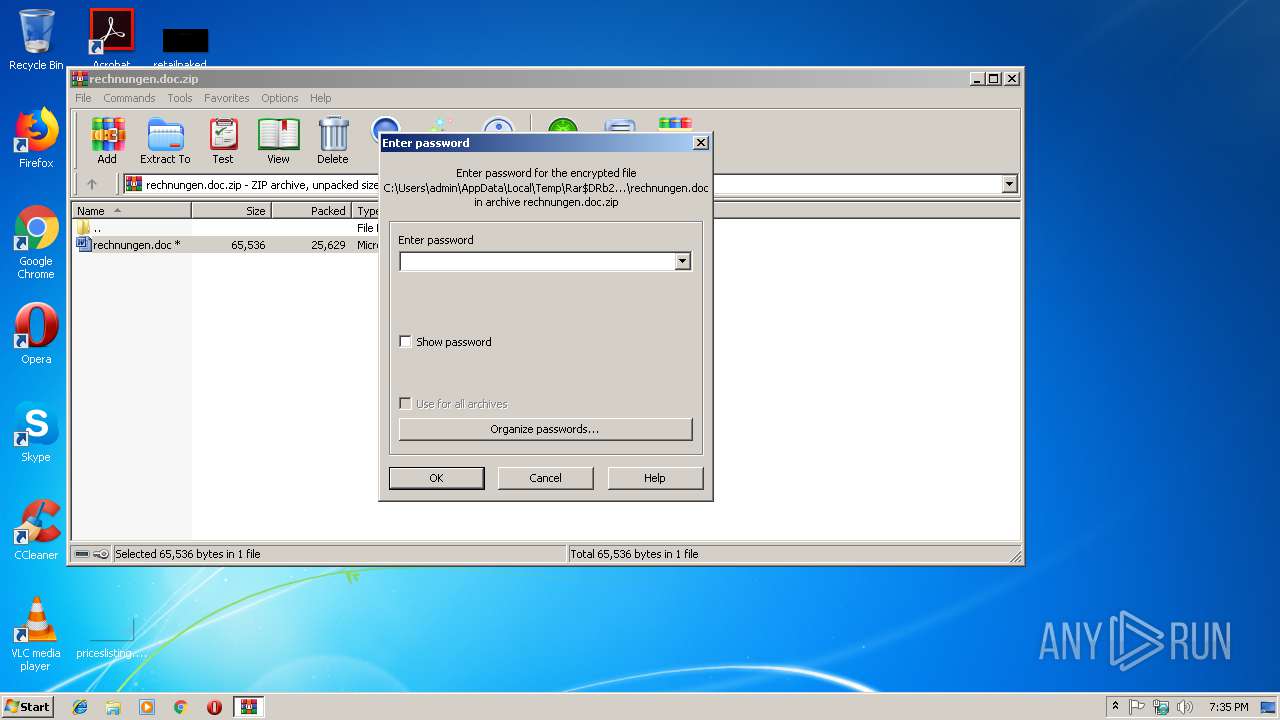
| ZipFileName: | rechnungen.doc |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2364 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\rechnungen.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2872 | C:\Users\Public\yeZjqHFMWjXi.exe | C:\Users\Public\yeZjqHFMWjXi.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Abbott Laboratories Integrity Level: MEDIUM Description: Succession Directoryshell Exit code: 0 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\rechnungen.doc.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3032 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | yeZjqHFMWjXi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 486
Read events
1 299
Write events
176
Delete events
11
Modification events
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\rechnungen.doc.zip | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
2
Suspicious files
289
Text files
235
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREA22.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF03D8735564FB6D68.TMP | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF983E86C9C53AC87A.TMP | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF92576AF7694CC1D9.TMP | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{5339C78D-95A4-4C84-B475-9972E097ABDC}.tmp | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFF3825BF58AA15590.TMP | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{F5206D9C-B56B-4341-9DEE-EE8BE2A17C46}.tmp | — | |
MD5:— | SHA256:— | |||
| 2872 | yeZjqHFMWjXi.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\$I9AAUDT.doc | — | |
MD5:— | SHA256:— | |||
| 2872 | yeZjqHFMWjXi.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\$R9AAUDT.doc | — | |
MD5:— | SHA256:— | |||
| 2872 | yeZjqHFMWjXi.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
130
TCP/UDP connections
239
DNS requests
103
Threats
75
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2872 | yeZjqHFMWjXi.exe | GET | — | 78.46.77.98:80 | http://www.2mmotorsport.biz/ | DE | — | — | suspicious |
2872 | yeZjqHFMWjXi.exe | GET | 302 | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
2872 | yeZjqHFMWjXi.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
2872 | yeZjqHFMWjXi.exe | GET | 301 | 83.166.138.7:80 | http://www.whitepod.com/ | CH | — | — | whitelisted |
2872 | yeZjqHFMWjXi.exe | GET | — | 217.26.53.161:80 | http://www.haargenau.biz/ | CH | — | — | malicious |
2872 | yeZjqHFMWjXi.exe | GET | — | 217.26.53.37:80 | http://www.hrk-ramoz.com/ | CH | — | — | malicious |
2872 | yeZjqHFMWjXi.exe | GET | 301 | 212.59.186.61:80 | http://www.morcote-residenza.com/ | CH | — | — | malicious |
2872 | yeZjqHFMWjXi.exe | GET | 301 | 80.244.187.247:80 | http://www.hotelfarinet.com/ | GB | — | — | malicious |
2872 | yeZjqHFMWjXi.exe | GET | 301 | 104.24.23.22:80 | http://www.belvedere-locarno.com/ | US | — | — | shared |
2872 | yeZjqHFMWjXi.exe | GET | 200 | 74.220.215.73:80 | http://www.bizziniinfissi.com/ | US | html | 6.96 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2872 | yeZjqHFMWjXi.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
2872 | yeZjqHFMWjXi.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
2872 | yeZjqHFMWjXi.exe | 138.201.162.99:80 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2872 | yeZjqHFMWjXi.exe | 136.243.13.215:80 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
2872 | yeZjqHFMWjXi.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
2872 | yeZjqHFMWjXi.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
2872 | yeZjqHFMWjXi.exe | 83.138.82.107:443 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
2872 | yeZjqHFMWjXi.exe | 138.201.162.99:443 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2872 | yeZjqHFMWjXi.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
2872 | yeZjqHFMWjXi.exe | 212.59.186.61:80 | www.hotelweisshorn.com | green.ch AG | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
karbonkoko.com |
| suspicious |
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2364 | WINWORD.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (gif) |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (gif) |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2872 | yeZjqHFMWjXi.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |