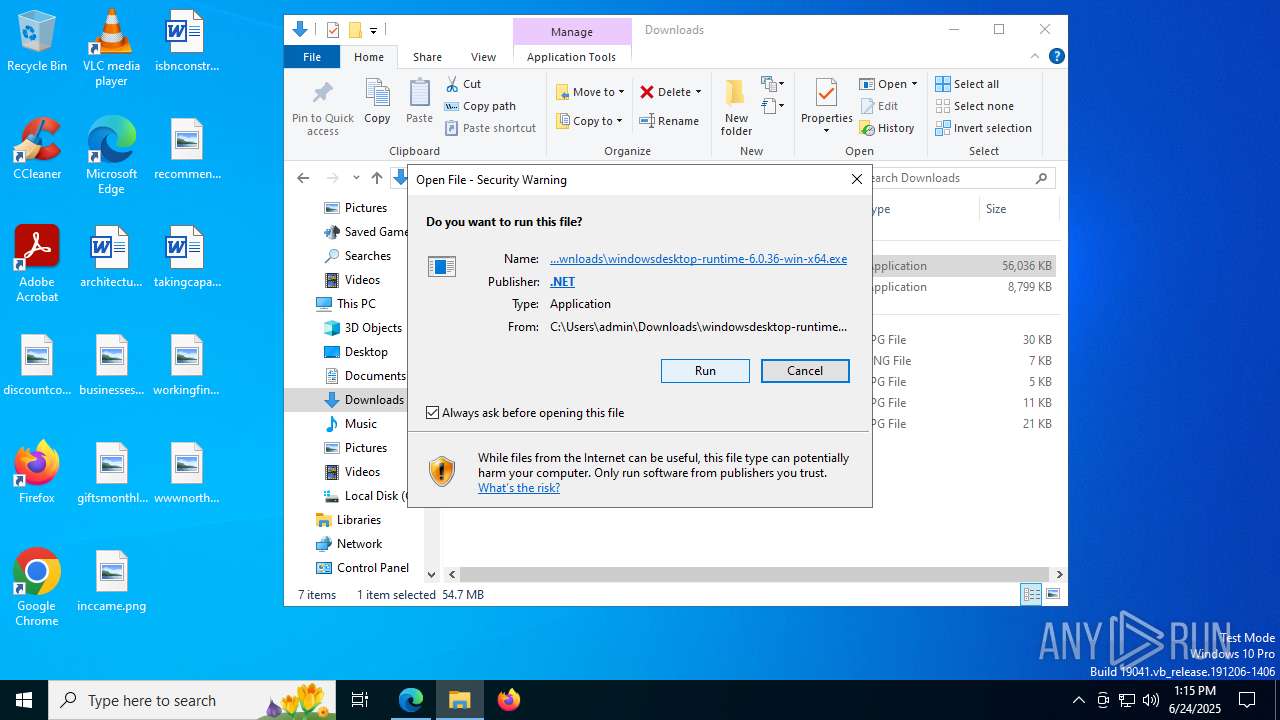
| File name: | Bloxstrap.exe |
| Full analysis: | https://app.any.run/tasks/dcf1c1ea-0cc7-43cd-b373-11b327f8a2d8 |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2025, 13:14:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 74BEBEBC515F800017CB3BFD0EF99D26 |
| SHA1: | 779303DABC8EB1692F014C33024D9BF195412AAC |
| SHA256: | 662F0AD7151FD4609E066B33AD4EEF089B28928AC609F1E15796DE009E2B74F3 |
| SSDEEP: | 98304:amti2gnpzSXY1Ke0RWBWwu4q1w6wnnnnnnnnnnnnnnnO1w5UMHlyyyyyyyyyyyyH:PeJvNH |
MALICIOUS
Changes the autorun value in the registry
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
SUSPICIOUS
Reads security settings of Internet Explorer
- Bloxstrap.exe (PID: 6428)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- Bloxstrap.exe (PID: 4100)
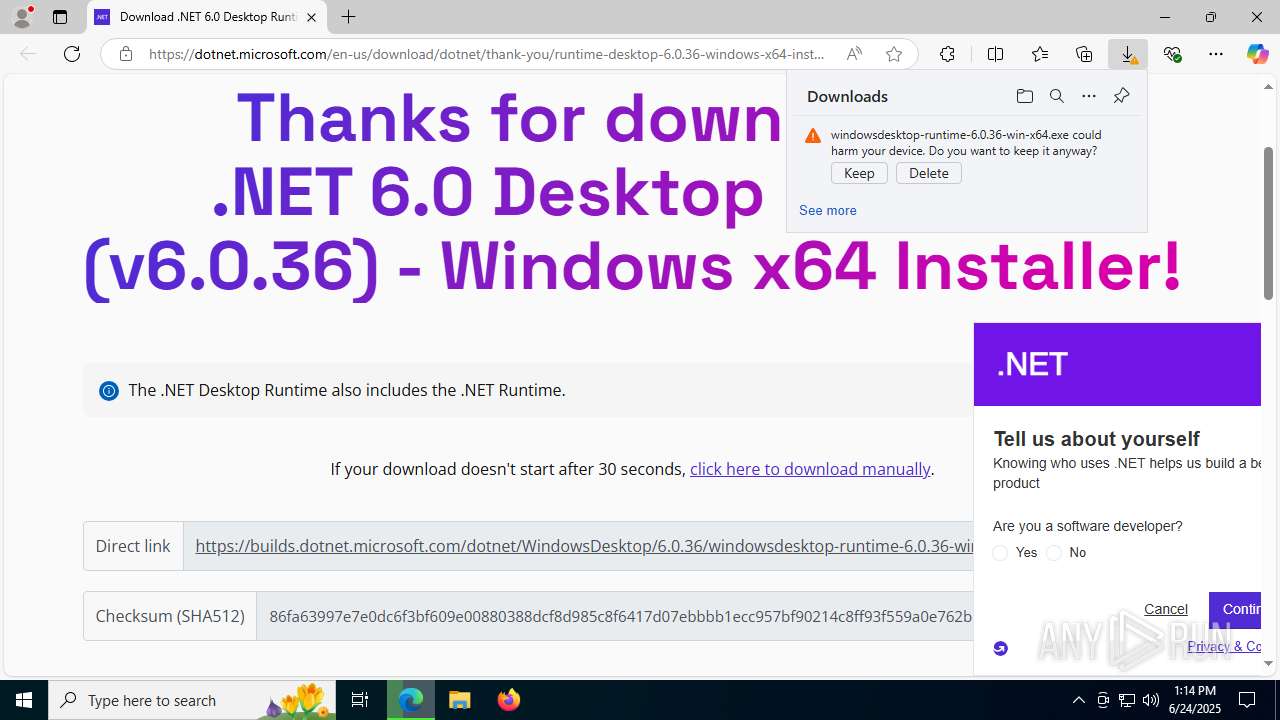
Executable content was dropped or overwritten
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7604)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- Bloxstrap.exe (PID: 4100)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4860)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
Searches for installed software
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 2148)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4860)
Process drops legitimate windows executable
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7604)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- msiexec.exe (PID: 7316)
- Bloxstrap.exe (PID: 4100)
Starts itself from another location
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
Creates a software uninstall entry
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7316)
The process drops C-runtime libraries
- msiexec.exe (PID: 7316)
Creates file in the systems drive root
- explorer.exe (PID: 4772)
The process creates files with name similar to system file names
- msiexec.exe (PID: 7316)
Application launched itself
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 2148)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 3876)
INFO
Checks supported languages
- Bloxstrap.exe (PID: 6428)
- identity_helper.exe (PID: 7240)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7604)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- msiexec.exe (PID: 7316)
- msiexec.exe (PID: 5924)
- Bloxstrap.exe (PID: 4100)
- msiexec.exe (PID: 8104)
- msiexec.exe (PID: 4804)
- msiexec.exe (PID: 7788)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 3876)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 2148)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4860)
Reads the computer name
- Bloxstrap.exe (PID: 6428)
- identity_helper.exe (PID: 7240)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- msiexec.exe (PID: 7316)
- msiexec.exe (PID: 5924)
- msiexec.exe (PID: 4804)
- msiexec.exe (PID: 7788)
- Bloxstrap.exe (PID: 4100)
- msiexec.exe (PID: 8104)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4860)
Application launched itself
- msedge.exe (PID: 5504)
- msedge.exe (PID: 5952)
Reads Environment values
- identity_helper.exe (PID: 7240)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- Taskmgr.exe (PID: 4760)
Executable content was dropped or overwritten
- msedge.exe (PID: 5952)
- msiexec.exe (PID: 7316)
Reads the software policy settings
- explorer.exe (PID: 4772)
- msiexec.exe (PID: 7316)
- Bloxstrap.exe (PID: 4100)
- slui.exe (PID: 5556)
Checks proxy server information
- explorer.exe (PID: 4772)
- slui.exe (PID: 5556)
- Bloxstrap.exe (PID: 4100)
Create files in a temporary directory
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7604)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- Bloxstrap.exe (PID: 4100)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4860)
Process checks computer location settings
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- Bloxstrap.exe (PID: 4100)
The sample compiled with english language support
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7604)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 7628)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- msiexec.exe (PID: 7316)
- Bloxstrap.exe (PID: 4100)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4860)
Creates files in the program directory
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- Bloxstrap.exe (PID: 4100)
Reads the machine GUID from the registry
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
- msiexec.exe (PID: 7316)
Launching a file from a Registry key
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 6584)
Creates a software uninstall entry
- msiexec.exe (PID: 7316)
ROBLOX mutex has been found
- Bloxstrap.exe (PID: 4100)
Creates files or folders in the user directory
- Bloxstrap.exe (PID: 4100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:17 06:58:08+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 99328 |
| InitializedDataSize: | 157696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13c60 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.6.1.0 |
| ProductVersionNumber: | 2.6.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Bloxstrap |
| FileDescription: | Bloxstrap |
| FileVersion: | 2.6.1.0 |
| InternalName: | Bloxstrap.dll |
| LegalCopyright: | |
| OriginalFileName: | Bloxstrap.dll |
| ProductName: | Bloxstrap |
| ProductVersion: | 2.6.1 |
| AssemblyVersion: | 2.6.1.0 |
Total processes
200
Monitored processes
53
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5320,i,7938925322614102813,8577630873764764365,262144 --variations-seed-version --mojo-platform-channel-handle=5312 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1336 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3668,i,7938925322614102813,8577630873764764365,262144 --variations-seed-version --mojo-platform-channel-handle=3632 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1392 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7656,i,7938925322614102813,8577630873764764365,262144 --variations-seed-version --mojo-platform-channel-handle=7512 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1508 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x290,0x294,0x298,0x288,0x2a0,0x7ffc4550f208,0x7ffc4550f214,0x7ffc4550f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --string-annotations --gpu-preferences=UAAAAAAAAADoAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=6292,i,7938925322614102813,8577630873764764365,262144 --variations-seed-version --mojo-platform-channel-handle=5908 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2148 | "C:\ProgramData\Package Cache\{0532b8f2-12d7-43de-95fc-7b87006758a8}\windowsdesktop-runtime-6.0.36-win-x64.exe" /burn.runonce | C:\ProgramData\Package Cache\{0532b8f2-12d7-43de-95fc-7b87006758a8}\windowsdesktop-runtime-6.0.36-win-x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Desktop Runtime - 6.0.36 (x64) Exit code: 0 Version: 6.0.36.34217 Modules
| |||||||||||||||
| 2368 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=6668,i,7938925322614102813,8577630873764764365,262144 --variations-seed-version --mojo-platform-channel-handle=5940 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2716 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --disable-quic --onnx-enabled-for-ee --string-annotations --always-read-main-dll --field-trial-handle=5272,i,7938925322614102813,8577630873764764365,262144 --variations-seed-version --mojo-platform-channel-handle=5356 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3588 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | "C:\ProgramData\Package Cache\{0532b8f2-12d7-43de-95fc-7b87006758a8}\windowsdesktop-runtime-6.0.36-win-x64.exe" | C:\ProgramData\Package Cache\{0532b8f2-12d7-43de-95fc-7b87006758a8}\windowsdesktop-runtime-6.0.36-win-x64.exe | — | windowsdesktop-runtime-6.0.36-win-x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Desktop Runtime - 6.0.36 (x64) Exit code: 1602 Version: 6.0.36.34217 Modules
| |||||||||||||||
Total events
35 096
Read events
34 022
Write events
1 017
Delete events
57
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000090230 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000090230 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5504) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5504) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5952) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 1 | |||
| (PID) Process: | (5952) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6428) Bloxstrap.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6428) Bloxstrap.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6428) Bloxstrap.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5952) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
532
Suspicious files
363
Text files
3 302
Unknown types
232
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF177649.TMP | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF177649.TMP | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF177649.TMP | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF177649.TMP | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF177678.TMP | — | |
MD5:— | SHA256:— | |||
| 5952 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
98
DNS requests
104
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2876 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8052 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7108 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:qsM3Ia7aDxFNELaPh_j_pgYx56JVPxyNMG4cuN4rBpk&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3936 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1751249286&P2=404&P3=2&P4=ZFI%2bmXVWKSGeuvlHQMYUVPH9Au2xioCU5xkpiy6Lto7PdHExMAhc2RZWcWi8qSuakLNvy9pryomGRZ7X6pObJw%3d%3d | unknown | — | — | whitelisted |
3936 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1751249286&P2=404&P3=2&P4=ZFI%2bmXVWKSGeuvlHQMYUVPH9Au2xioCU5xkpiy6Lto7PdHExMAhc2RZWcWi8qSuakLNvy9pryomGRZ7X6pObJw%3d%3d | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3936 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9244b52a-55cc-41a2-b7c4-7f4983d8753c?P1=1751249286&P2=404&P3=2&P4=nV5rgAT198mAEfQVg2OchHjMI4CYL4sDphrr9L%2f1JtW1YzB%2bSlTfoNFzz9ONO0n53Dj7eSGygp9C4ljB%2fYxg2g%3d%3d | unknown | — | — | whitelisted |
3936 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9244b52a-55cc-41a2-b7c4-7f4983d8753c?P1=1751249286&P2=404&P3=2&P4=nV5rgAT198mAEfQVg2OchHjMI4CYL4sDphrr9L%2f1JtW1YzB%2bSlTfoNFzz9ONO0n53Dj7eSGygp9C4ljB%2fYxg2g%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3588 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7108 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7108 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7108 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
aka.ms |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
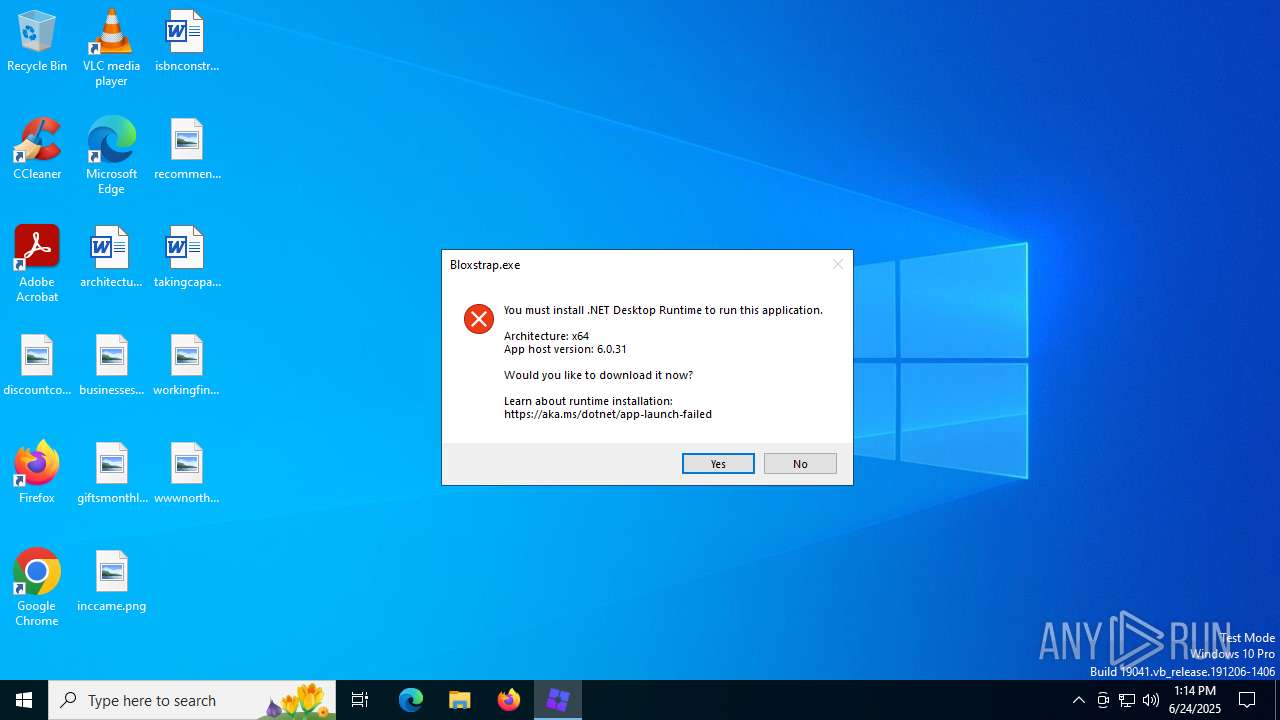
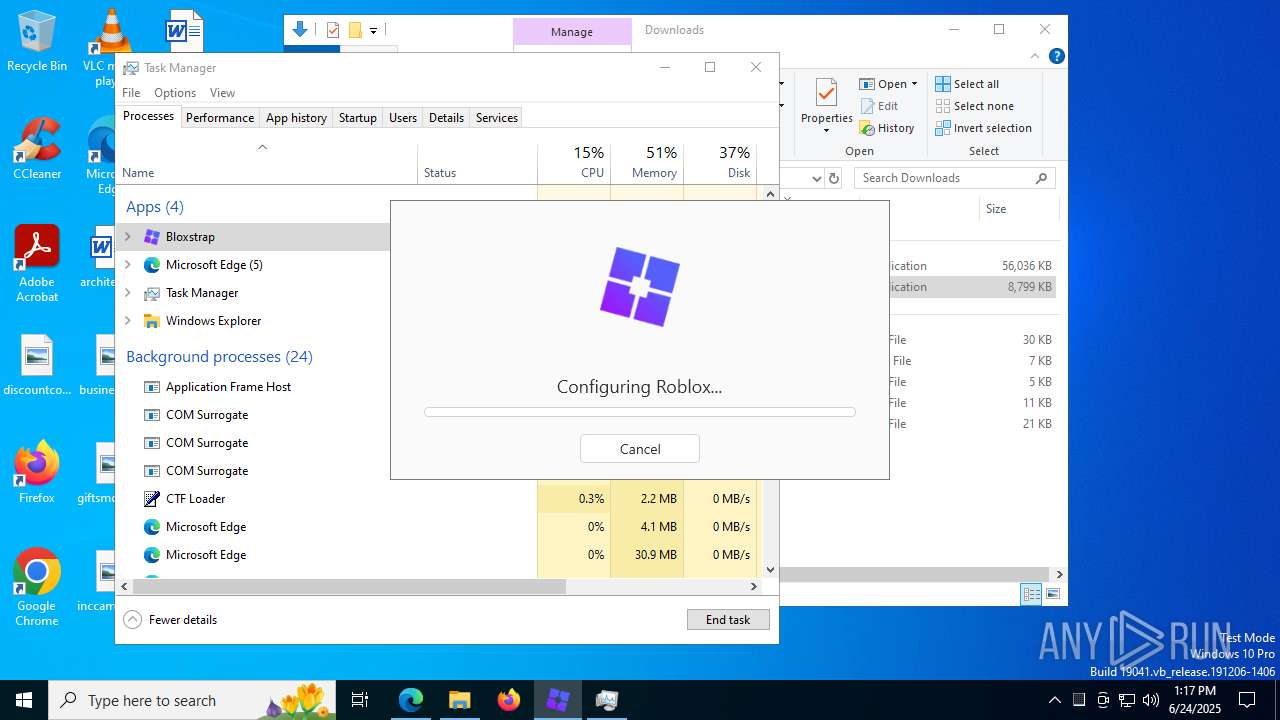
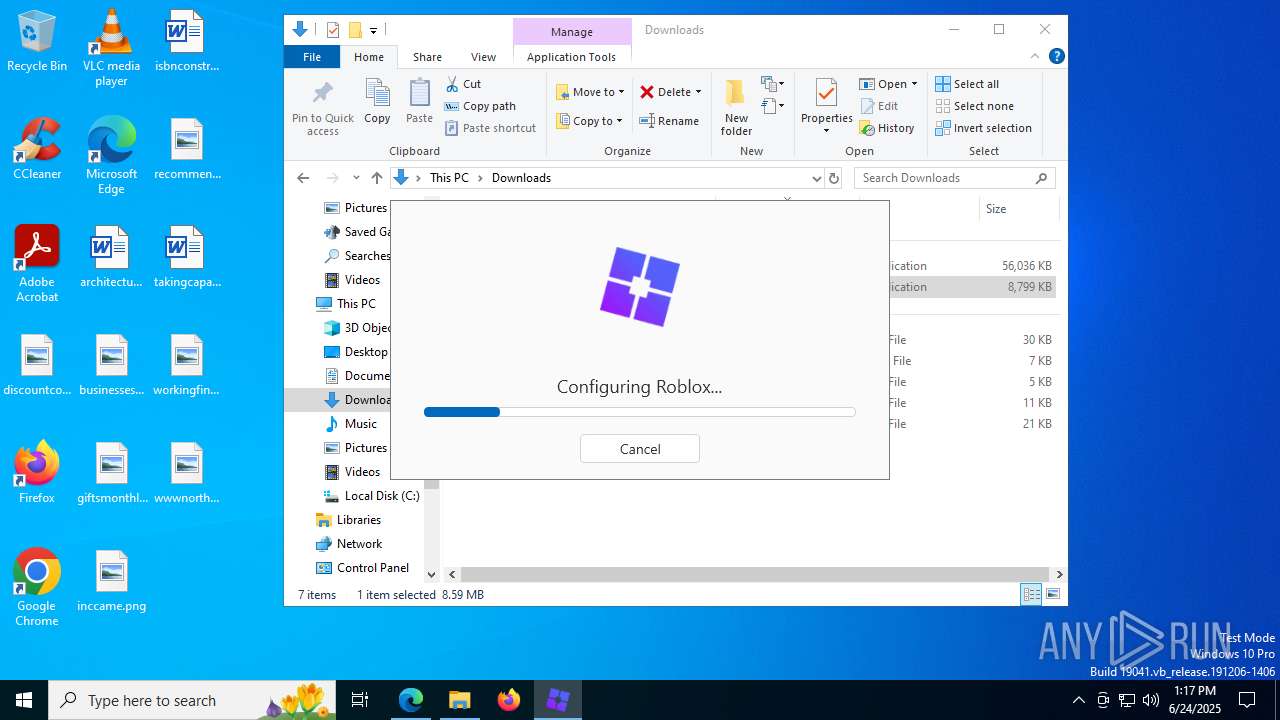
Bloxstrap.exe | You must install .NET to run this application.
App: C:\Users\admin\Downloads\Bloxstrap.exe
Architecture: x64
App host version: 6.0.31
.NET location: Not found
Learn about runtime installation:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win10-x64&apphost_version=6.0.31 |
Bloxstrap.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 4100. Message ID: [0x2509].
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | SystemAccentColorTertiary: #FF0063B1
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | Text on accent is LIGHT
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | SystemAccentColorPrimary: #FF0071CA
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | SystemAccentColorSecondary: #FF006ABE
|
Bloxstrap.exe | Wpf.Ui.TitleBar: INFO | Wpf.Ui.Controls.TitleBar received theme - Light
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | SystemAccentColorSecondary: #FF006ABE
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | SystemAccentColor: #FF0078D7
|
Bloxstrap.exe | Wpf.Ui.Accent: INFO | SystemAccentColorPrimary: #FF0071CA
|