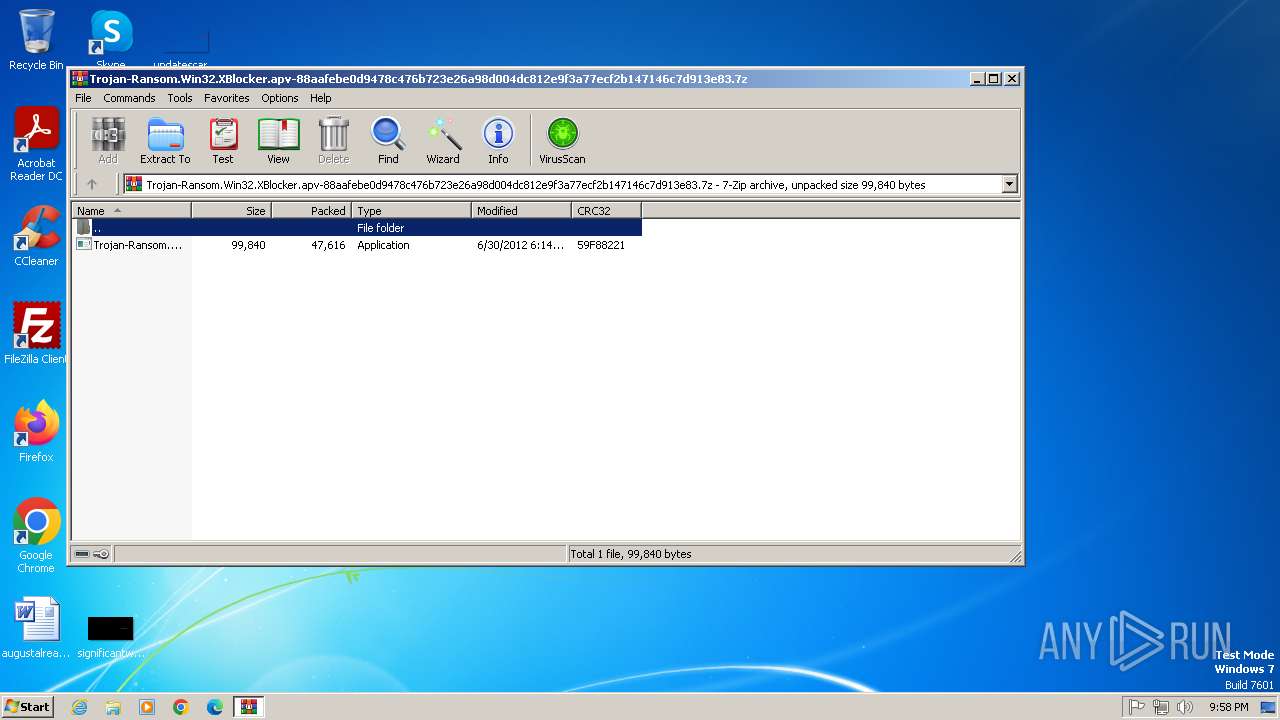
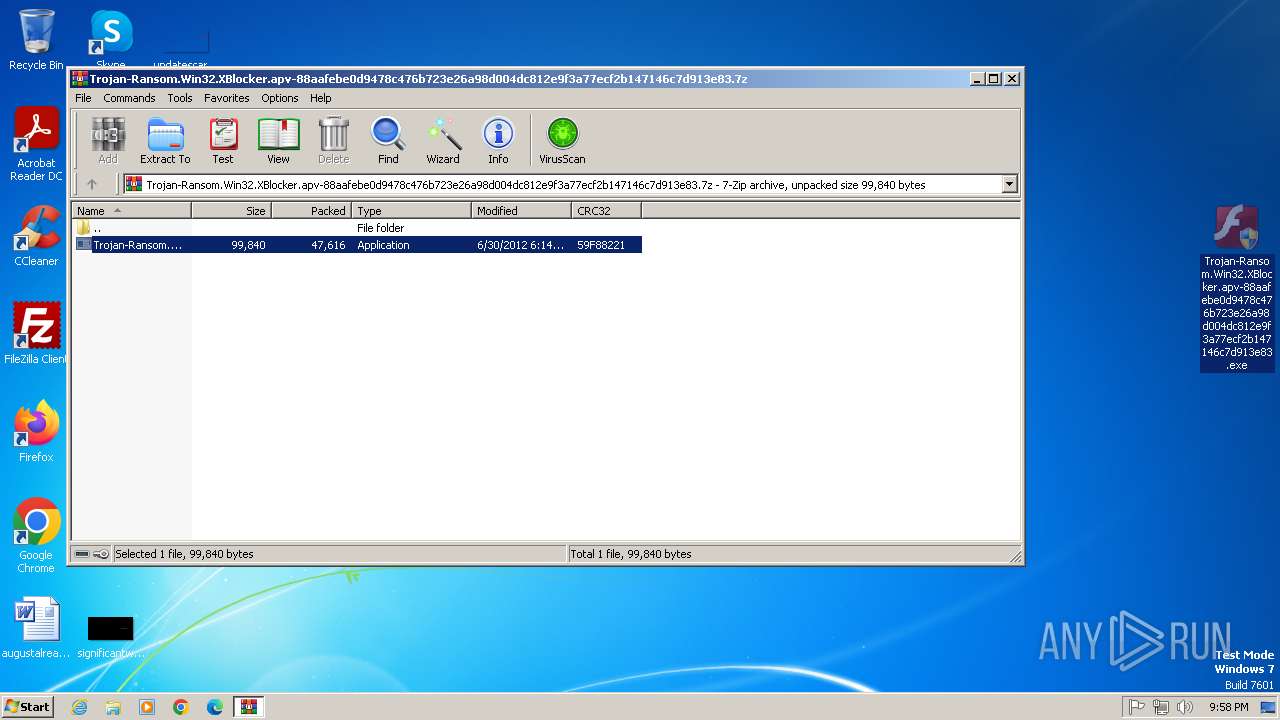
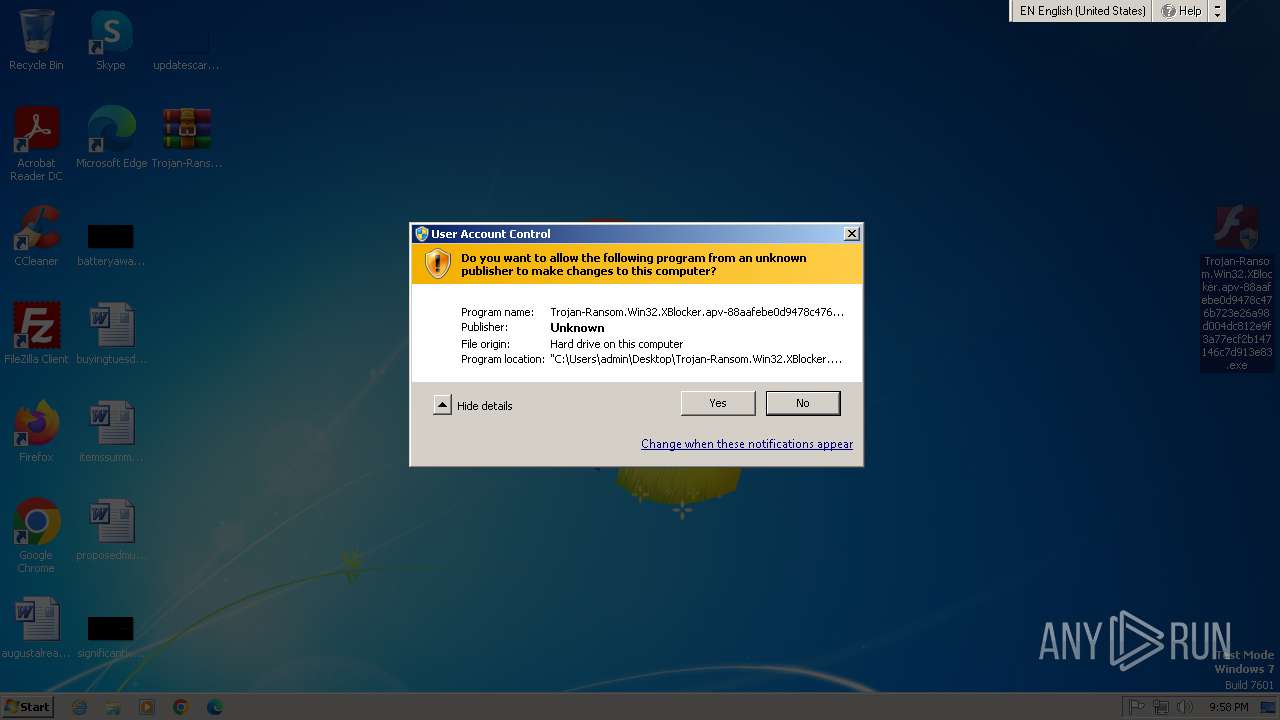
| File name: | Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.7z |
| Full analysis: | https://app.any.run/tasks/e1558d37-5d61-4c75-9fef-2ccfbccde8d6 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2025, 20:58:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 48E9C90AD1F4AA711676A780376979BD |
| SHA1: | 5B497C19243B6C17BA485A69E340E788D2D959E2 |
| SHA256: | 662C89EF2BD06E047DBD80B13191B9AB65946B484B8910EE084A126B36F2E03F |
| SSDEEP: | 1536:F8sHMZR7nmrn2cn8tUMiSP4t2gaxOQpBdK:FNHC7Yh8tUMfP4t2BOQpBdK |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 372)
UAC/LUA settings modification
- kasper_zaebal.exe (PID: 984)
SUSPICIOUS
Executable content was dropped or overwritten
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
Starts CMD.EXE for commands execution
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
Executing commands from a ".bat" file
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
Starts itself from another location
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
There is functionality for taking screenshot (YARA)
- kasper_zaebal.exe (PID: 984)
INFO
Checks supported languages
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
- kasper_zaebal.exe (PID: 984)
Creates files in the program directory
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
- cmd.exe (PID: 988)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 372)
Reads the computer name
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
Manual execution by a user
- Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe (PID: 1028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2012:06:30 17:14:36+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe |
Total processes
44
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 984 | -wait | C:\ProgramData\Media\kasper_zaebal.exe | — | Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 988 | C:\Windows\system32\cmd.exe /c C:\ProgramData\Media\rdb.bat | C:\Windows\System32\cmd.exe | — | Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
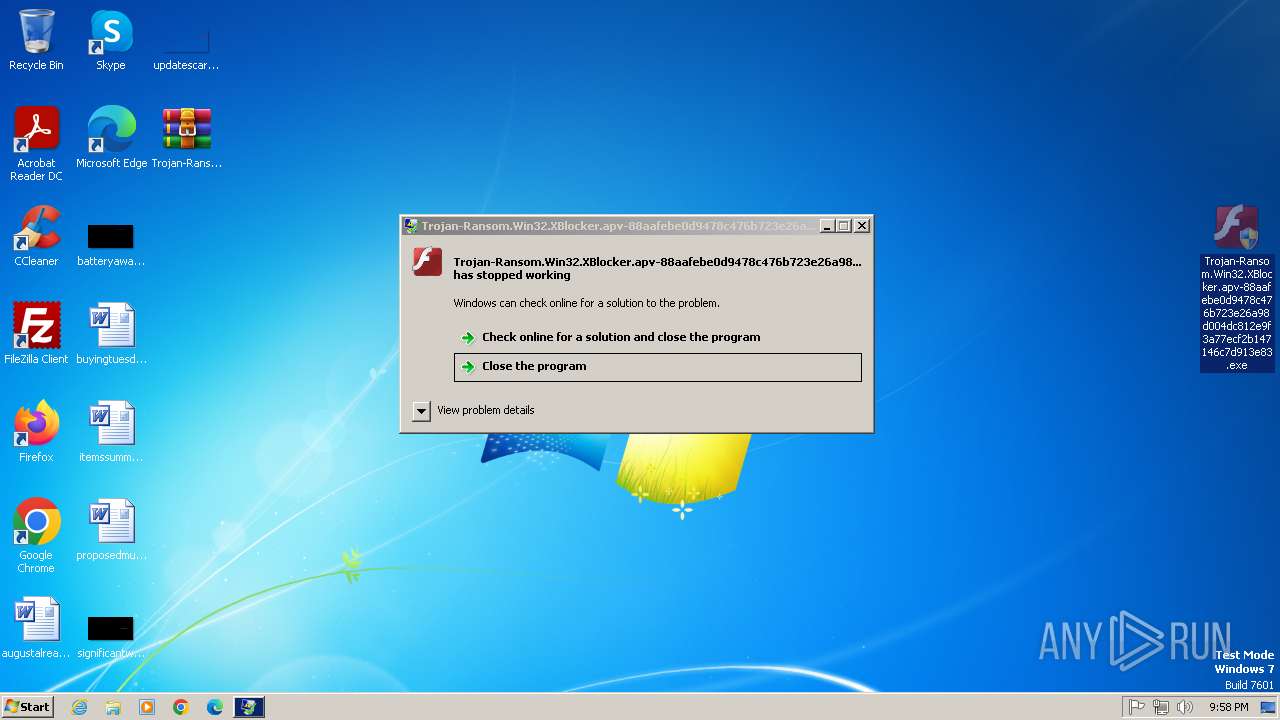
| 1028 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
Total events
2 679
Read events
2 653
Write events
26
Delete events
0
Modification events
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.7z | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 988 | cmd.exe | C:\ProgramData\Media\kasper_zaebal.exe:Zone.Identifier | text | |
MD5:38DE427224A5082A04FE82E2BD4EA9EC | SHA256:12F99F53144294750FE8713D580EDA286F4BD95CD9C840DB8AB957DEF8040028 | |||
| 372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb372.19979\Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe | executable | |
MD5:38930E6419D77714A2D5DF44837DE15B | SHA256:88AAFEBE0D9478C476B723E26A98D004DC812E9F3A77ECF2B147146C7D913E83 | |||
| 1028 | Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe | C:\ProgramData\Media\rdb.bat | text | |
MD5:C6F7299BE3ECBB88ACFDE79C4DC2B63C | SHA256:A22D2D0A98CEC8C7EFCCEA543DC7D770577B5A966735DEFFA2F1BCE9ECFBAD5D | |||
| 1028 | Trojan-Ransom.Win32.XBlocker.apv-88aafebe0d9478c476b723e26a98d004dc812e9f3a77ecf2b147146c7d913e83.exe | C:\ProgramData\Media\kasper_zaebal.exe | executable | |
MD5:38930E6419D77714A2D5DF44837DE15B | SHA256:88AAFEBE0D9478C476B723E26A98D004DC812E9F3A77ECF2B147146C7D913E83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |