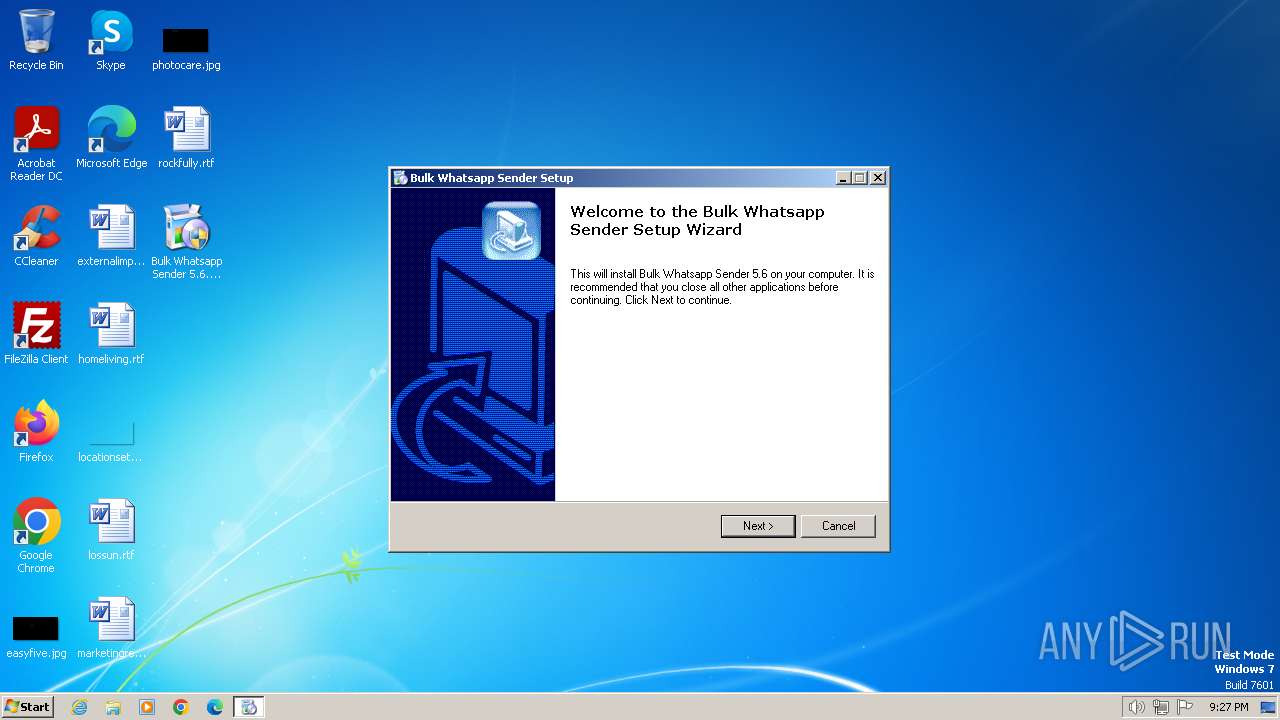
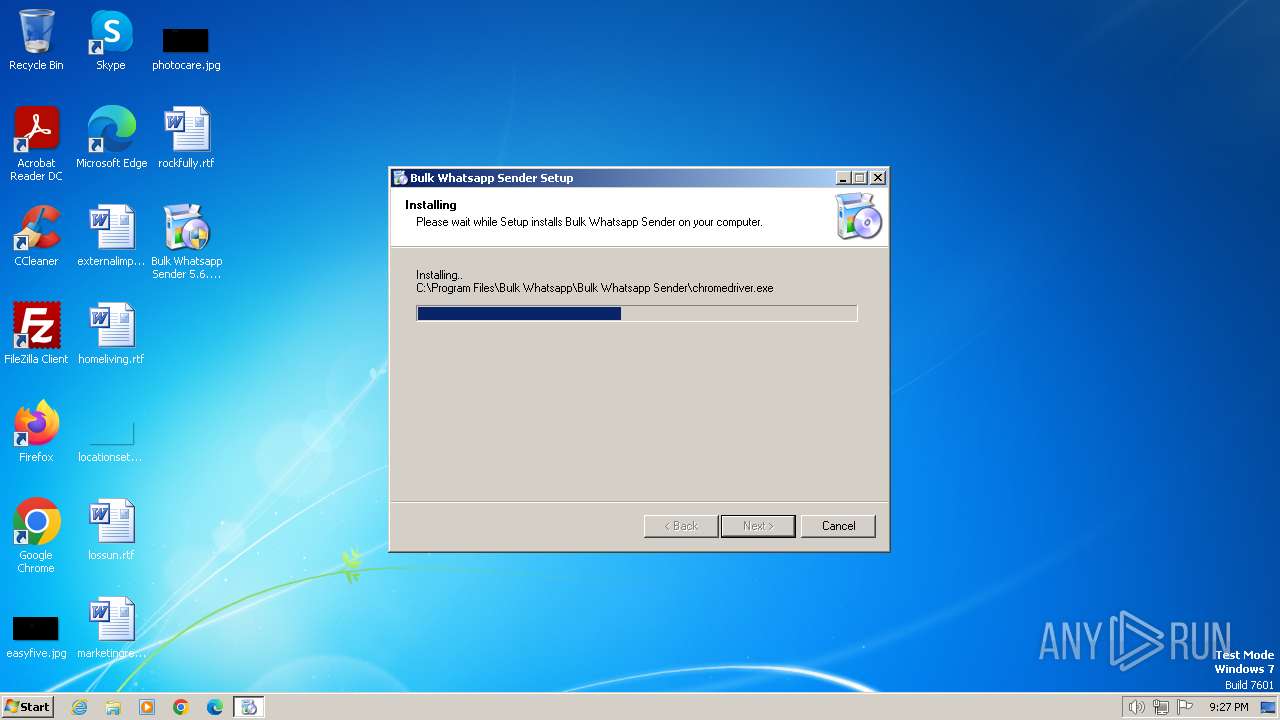
| File name: | Bulk Whatsapp Sender 5.6.exe |
| Full analysis: | https://app.any.run/tasks/40473516-645c-441e-b1a3-933e7703c6e2 |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2024, 21:26:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | F756FAC7049AFF1B33F9748285CD05BE |
| SHA1: | 35FDE4CC4C1F334F445731B2D41C710F9AB109C1 |
| SHA256: | 6628A13D7B4B6567675CBE49AC3F6BE3F3412FF4697C0252BE2C23DD433A013F |
| SSDEEP: | 98304:tKaUvaz7CuZUSaz7CuZUBrrSjKzlLt5wJ5cAhk8xawmicl+Pknd+RajTOdzv/bxD:VZ9rzTNtg5btWb3xPLfa |
MALICIOUS
Drops the executable file immediately after the start
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
SUSPICIOUS
Executable content was dropped or overwritten
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
The process creates files with name similar to system file names
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
Creates a software uninstall entry
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
Process drops legitimate windows executable
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
Reads the Internet Settings
- BulkWhatsappSender.exe (PID: 3516)
Reads security settings of Internet Explorer
- BulkWhatsappSender.exe (PID: 3516)
INFO
Create files in a temporary directory
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
- chromedriver.exe (PID: 2148)
Creates files in the program directory
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
Checks supported languages
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
- chromedriver.exe (PID: 2148)
- BulkWhatsappSender.exe (PID: 3516)
Reads the computer name
- Bulk Whatsapp Sender 5.6.exe (PID: 2208)
- BulkWhatsappSender.exe (PID: 3516)
- chromedriver.exe (PID: 2148)
Reads the machine GUID from the registry
- BulkWhatsappSender.exe (PID: 3516)
Reads Environment values
- BulkWhatsappSender.exe (PID: 3516)
Application launched itself
- chrome.exe (PID: 2904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:09:03 22:28:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 201728 |
| InitializedDataSize: | 259072 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
52
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --headless --lang=en-US --first-renderer-process --enable-automation --enable-logging --log-level=0 --remote-debugging-port=0 --test-type=webdriver --allow-pre-commit-input --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=1700 --field-trial-handle=940,i,17592474658309545639,3548589553312149210,131072 --disable-features=PaintHolding /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --enable-logging --ignore-certificate-errors --log-level=0 --use-angle=swiftshader-webgl --use-gl=angle --ignore-certificate-errors --headless --enable-logging --log-level=0 --mojo-platform-channel-handle=1236 --field-trial-handle=940,i,17592474658309545639,3548589553312149210,131072 --disable-features=PaintHolding /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\scoped_dir2148_26581 /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\scoped_dir2148_26581\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xd0,0xd4,0xd8,0xa4,0xdc,0x69678b38,0x69678b48,0x69678b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1692 | "C:\Users\admin\Desktop\Bulk Whatsapp Sender 5.6.exe" | C:\Users\admin\Desktop\Bulk Whatsapp Sender 5.6.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\chromedriver.exe" --port=49207 | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\chromedriver.exe | — | BulkWhatsappSender.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\Desktop\Bulk Whatsapp Sender 5.6.exe" | C:\Users\admin\Desktop\Bulk Whatsapp Sender 5.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --enable-logging --headless --log-level=0 --use-angle=swiftshader-webgl --headless --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --enable-logging --log-level=0 --mojo-platform-channel-handle=896 --field-trial-handle=940,i,17592474658309545639,3548589553312149210,131072 --disable-features=PaintHolding /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disable-background-networking --disable-client-side-phishing-detection --disable-default-apps --disable-hang-monitor --disable-popup-blocking --disable-prompt-on-repost --disable-sync --disable-web-resources --enable-automation --enable-logging --force-fieldtrials=SiteIsolationExtensions/Control --headless --ignore-certificate-errors --load-extension="C:\Users\admin\AppData\Local\Temp\scoped_dir2148_21952\internal" --log-level=0 --metrics-recording-only --no-first-run --password-store=basic --remote-debugging-port=0 --test-type=webdriver --use-mock-keychain --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir2148_26581" data:, | C:\Program Files\Google\Chrome\Application\chrome.exe | chromedriver.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --headless --lang=en-US --enable-automation --enable-logging --log-level=0 --remote-debugging-port=0 --test-type=webdriver --allow-pre-commit-input --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=904 --field-trial-handle=940,i,17592474658309545639,3548589553312149210,131072 --disable-features=PaintHolding /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3516 | "C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.exe" | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.exe | Bulk Whatsapp Sender 5.6.exe | ||||||||||||
User: admin Company: MediaPlus.me Integrity Level: HIGH Description: BulkWhatsappSender Exit code: 0 Version: 5.6.0.1 Modules
| |||||||||||||||
Total events
4 070
Read events
4 037
Write events
33
Delete events
0
Modification events
| (PID) Process: | (2208) Bulk Whatsapp Sender 5.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Bulk Whatsapp Sender |
| Operation: | write | Name: | DisplayName |
Value: Bulk Whatsapp Sender | |||
| (PID) Process: | (2208) Bulk Whatsapp Sender 5.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Bulk Whatsapp Sender |
| Operation: | write | Name: | DisplayVersion |
Value: 5.6 | |||
| (PID) Process: | (2208) Bulk Whatsapp Sender 5.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Bulk Whatsapp Sender |
| Operation: | write | Name: | HelpLink |
Value: | |||
| (PID) Process: | (2208) Bulk Whatsapp Sender 5.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Bulk Whatsapp Sender |
| Operation: | write | Name: | Publisher |
Value: Bulk Whatsapp | |||
| (PID) Process: | (2208) Bulk Whatsapp Sender 5.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Bulk Whatsapp Sender |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\Uninstall.exe | |||
| (PID) Process: | (2208) Bulk Whatsapp Sender 5.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Bulk Whatsapp Sender |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\Uninstall.exe | |||
| (PID) Process: | (3516) BulkWhatsappSender.exe | Key: | HKEY_CURRENT_USER\Software\VB and VBA Program Settings\wapi\api |
| Operation: | write | Name: | port |
Value: 1 | |||
| (PID) Process: | (3516) BulkWhatsappSender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3516) BulkWhatsappSender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3516) BulkWhatsappSender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
8
Suspicious files
25
Text files
23
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Users\admin\AppData\Local\Temp\IF{48256522-66D1-4197-8D11-28FBCF0BF061}\Image_Top.jpg | binary | |
MD5:4AE65BA99FB788D962860EC9ED14F2A7 | SHA256:6D118DC765ED52458079F8F588B7E144B02AA8E564F06726AADE9CA7D77EF0A3 | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Users\admin\AppData\Local\Temp\IF{48256522-66D1-4197-8D11-28FBCF0BF061}\licence.rtf | text | |
MD5:969D154352C0FAFB84B27B8CAF22D504 | SHA256:CFEEE7E71A82187371519F9A0C232FACF5E82889C2E4AE7BB57532E09A5C30C0 | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.application | xml | |
MD5:51F9BB828C9299179A93C4BE5712DA25 | SHA256:BE47761AD7DF4F376D47C430B273D2962ABC5005EF553D5C95C30E95934E3664 | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.exe | executable | |
MD5:D92496F069894128674704624BCDBB88 | SHA256:0F0510084E0A0A80945596F33FB86460EA7D2B33C3548C96BF7A3FE08F490A2E | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Users\admin\AppData\Local\Temp\IF{48256522-66D1-4197-8D11-28FBCF0BF061}\Setup.cab | compressed | |
MD5:4BBD243A590AA0478868EE5ECB93CFB1 | SHA256:3A6AC7C9925880F1A9B640C56F4B5C388866C4E4D37657657A48DFF2FE3B5230 | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.exe.manifest | xml | |
MD5:C58C75A24DAA5334C90082BCF098D936 | SHA256:87109076A00F9B6CAC209C78775E3342FF887E51FA641D2084F11504A1E1552B | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.pdb | binary | |
MD5:550A38E32775911BB0966413C34F6CBC | SHA256:172D317089ED9CF83151364A73F6DB2FBCAFEF403CF990FFA3B69FEFC4466E1D | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Users\admin\AppData\Local\Temp\IF{48256522-66D1-4197-8D11-28FBCF0BF061}\icon.dat | image | |
MD5:FA63A0160B9FF05DC70CFBCA82B465B6 | SHA256:D3A14188ECCD7761CD20CE86237F481A4BCDDFFCD460871BD7B4504F6162D9DA | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\Uninstall.exe | executable | |
MD5:7AE89C6074B7CF3D03081EA6616D873B | SHA256:AE326F86AA8BBB88831B0339C820859467EF910DADED5B430DC88DA97D203772 | |||
| 2208 | Bulk Whatsapp Sender 5.6.exe | C:\Program Files\Bulk Whatsapp\Bulk Whatsapp Sender\BulkWhatsappSender.exe.config | xml | |
MD5:71A297A409C4FAD934C35AD99AE7DBD2 | SHA256:38C851021E2EBADE21AD58731A3C207E4099C8C6F5D16ECB8510AFD2B439701A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
9
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
880 | chrome.exe | GET | — | 72.18.134.37:80 | http://shop.mediaplus.me/ | unknown | — | — | unknown |
3516 | BulkWhatsappSender.exe | GET | 200 | 173.248.130.117:80 | http://www.mediaplus.me/bws/ver/getdateex2.ashx | unknown | text | 24 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
880 | chrome.exe | 72.18.134.37:80 | shop.mediaplus.me | WEHOSTWEBSITES-COM | US | unknown |
3516 | BulkWhatsappSender.exe | 173.248.130.117:80 | www.mediaplus.me | WEHOSTWEBSITES-COM | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
shop.mediaplus.me |
| unknown |
dns.msftncsi.com |
| shared |
www.mediaplus.me |
| unknown |
Threats
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir2148_26581 directory exists )
|