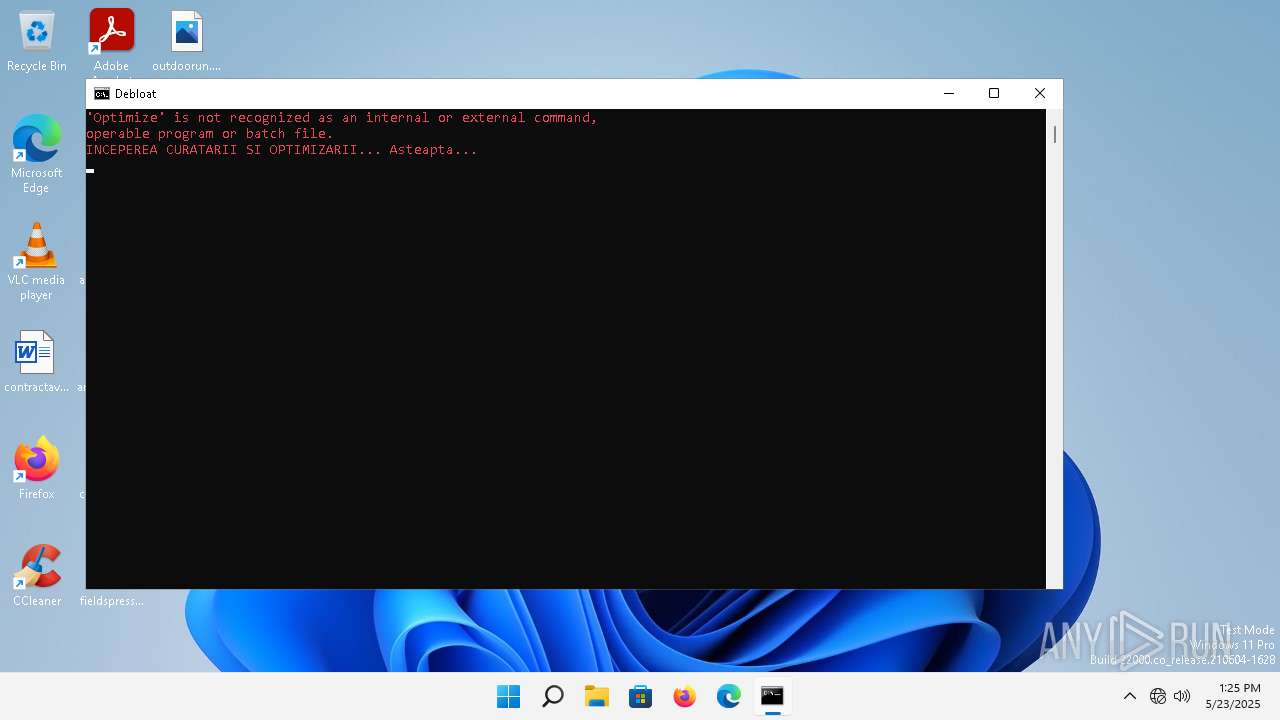
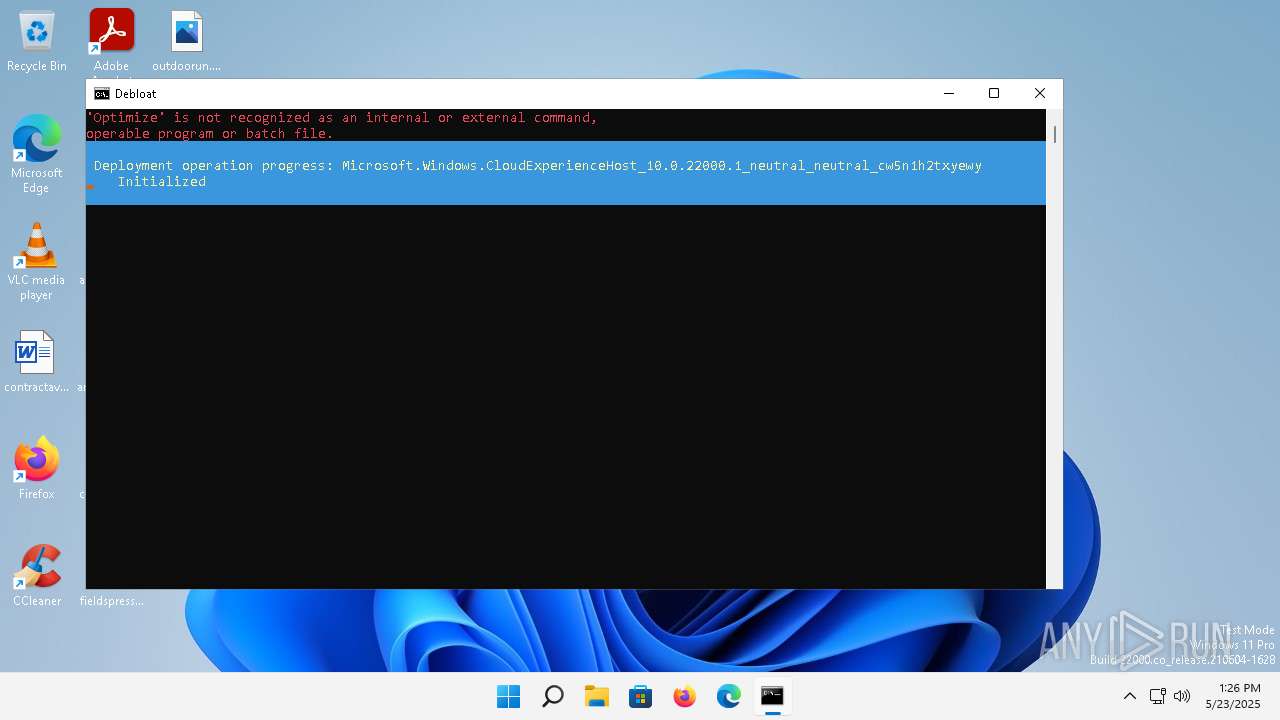
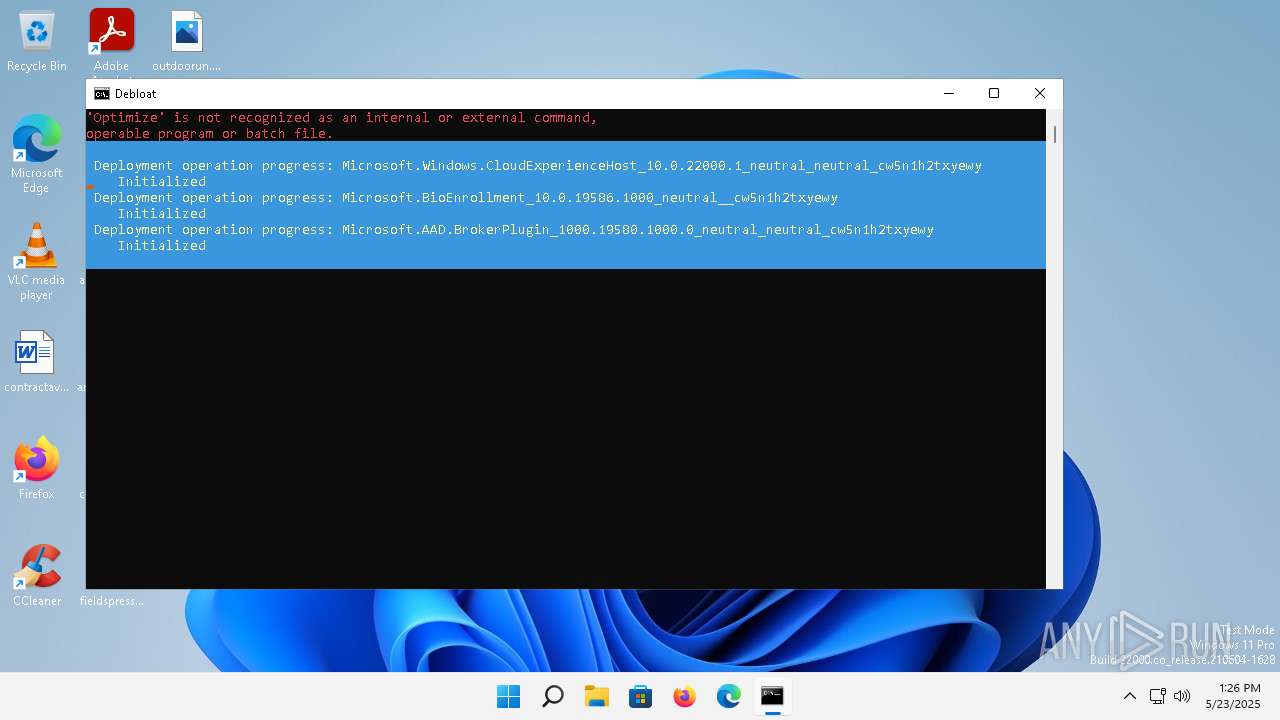
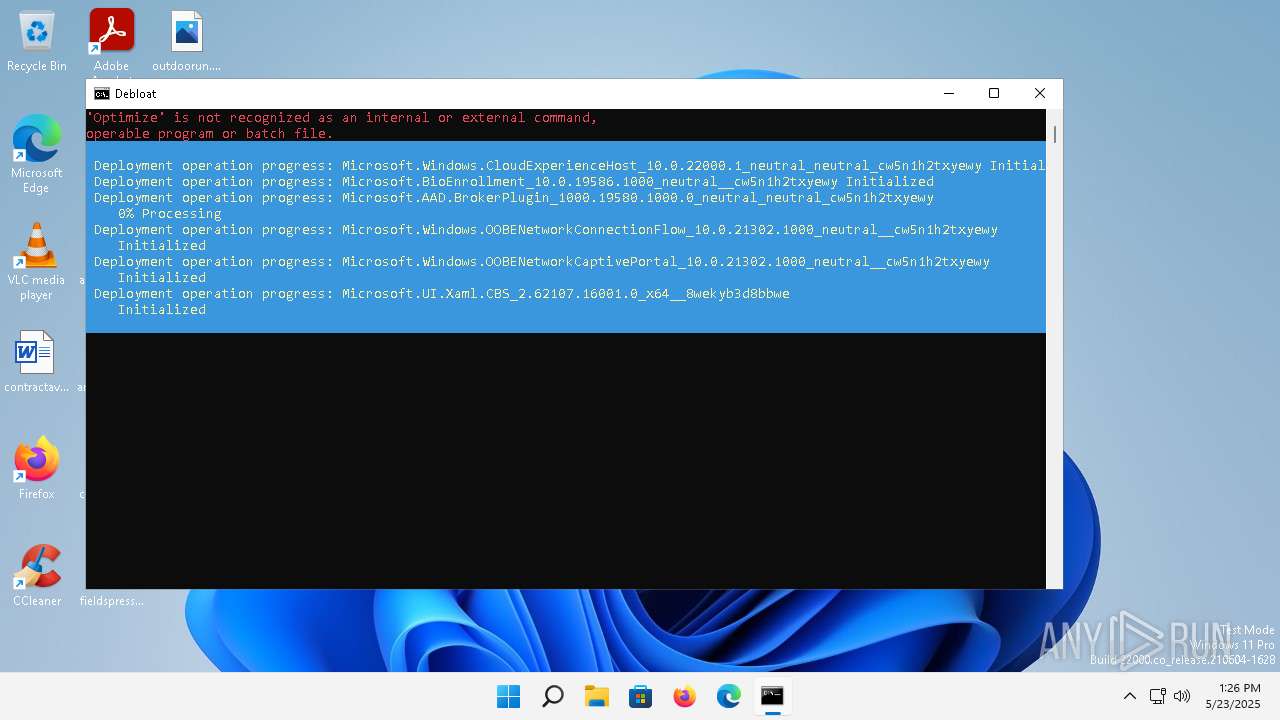
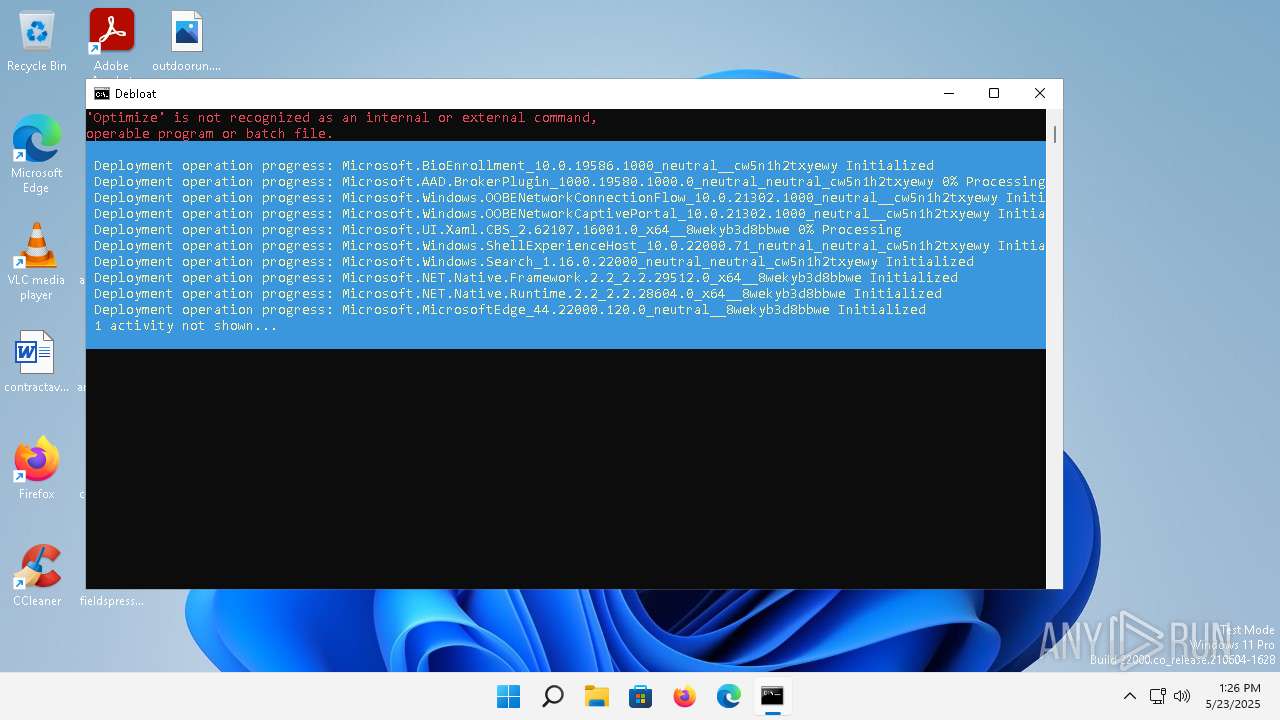
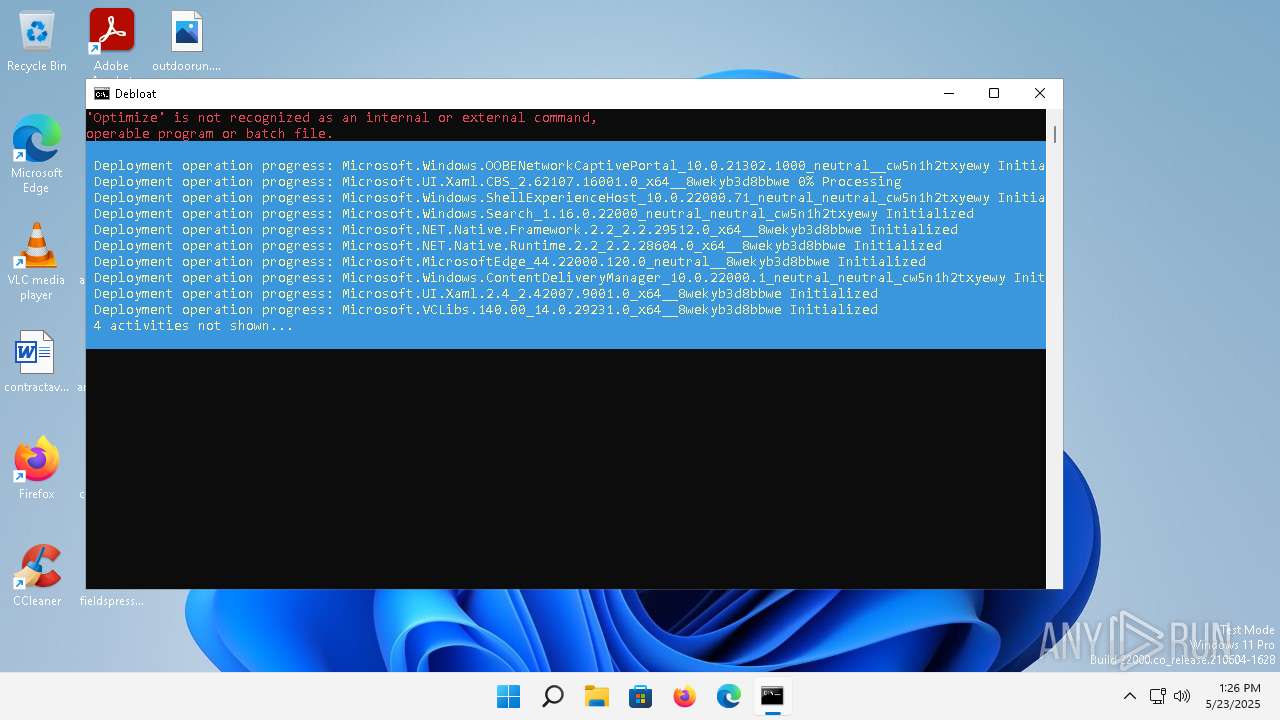
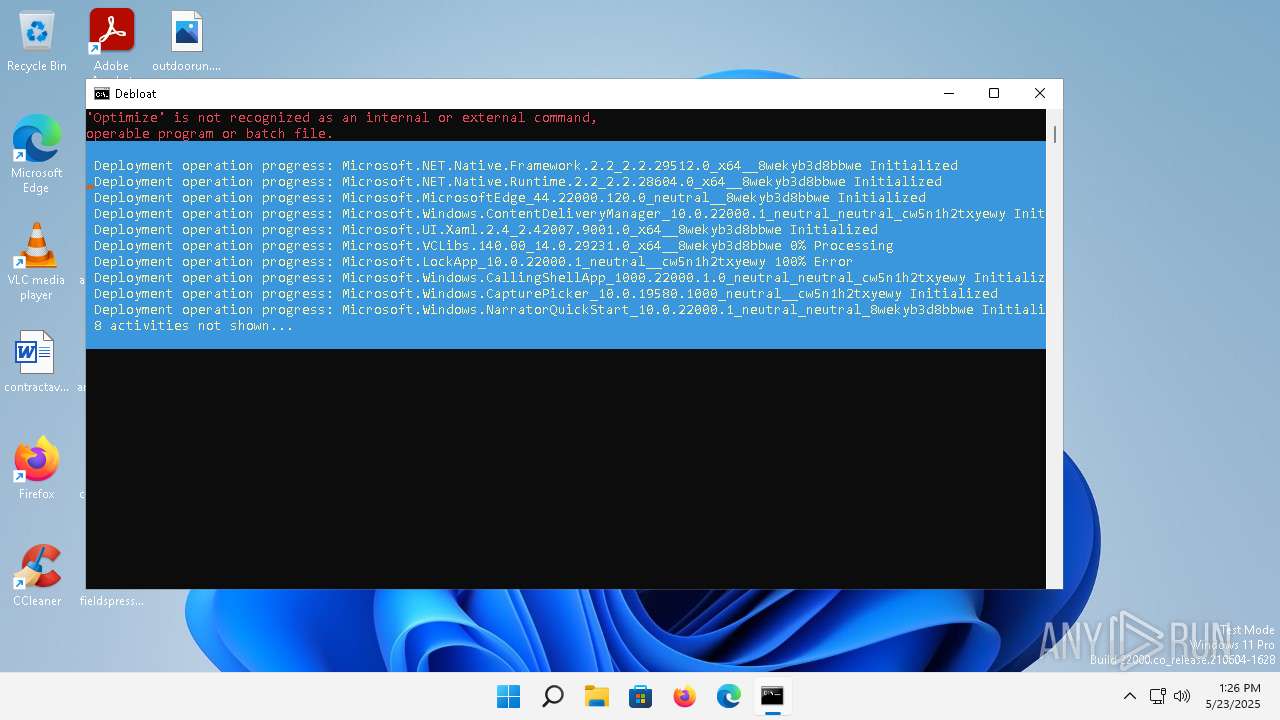
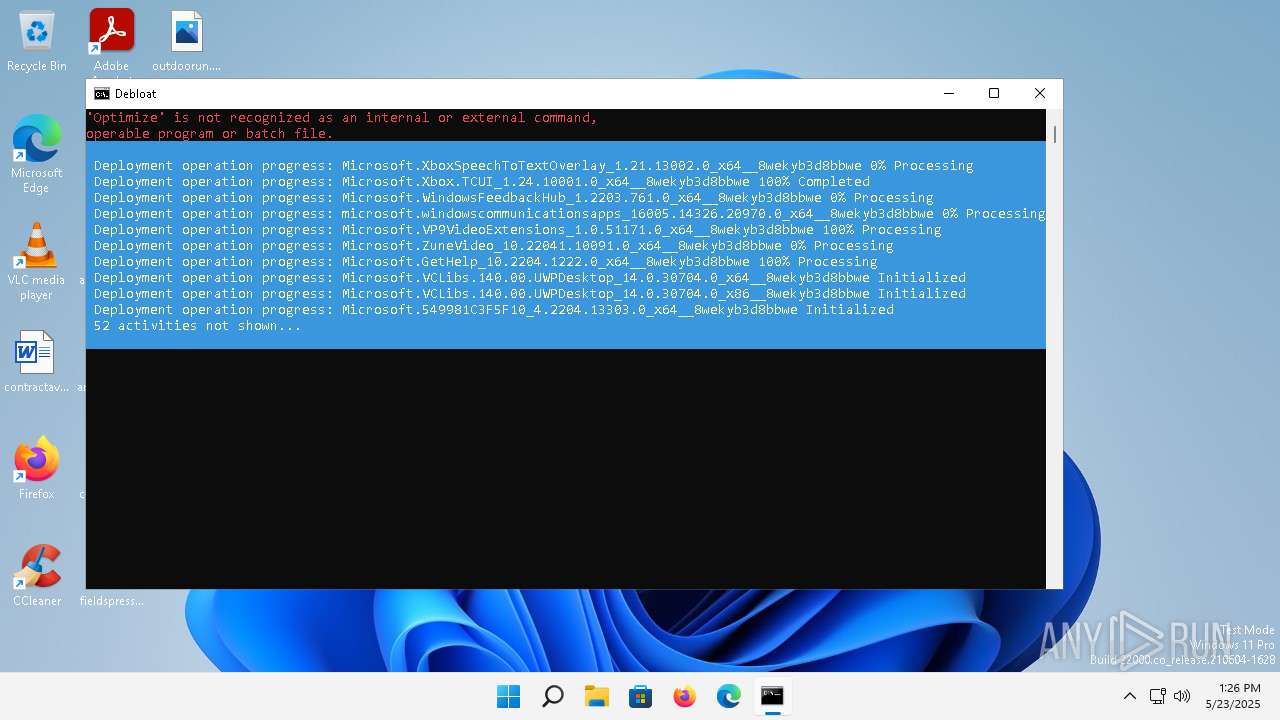
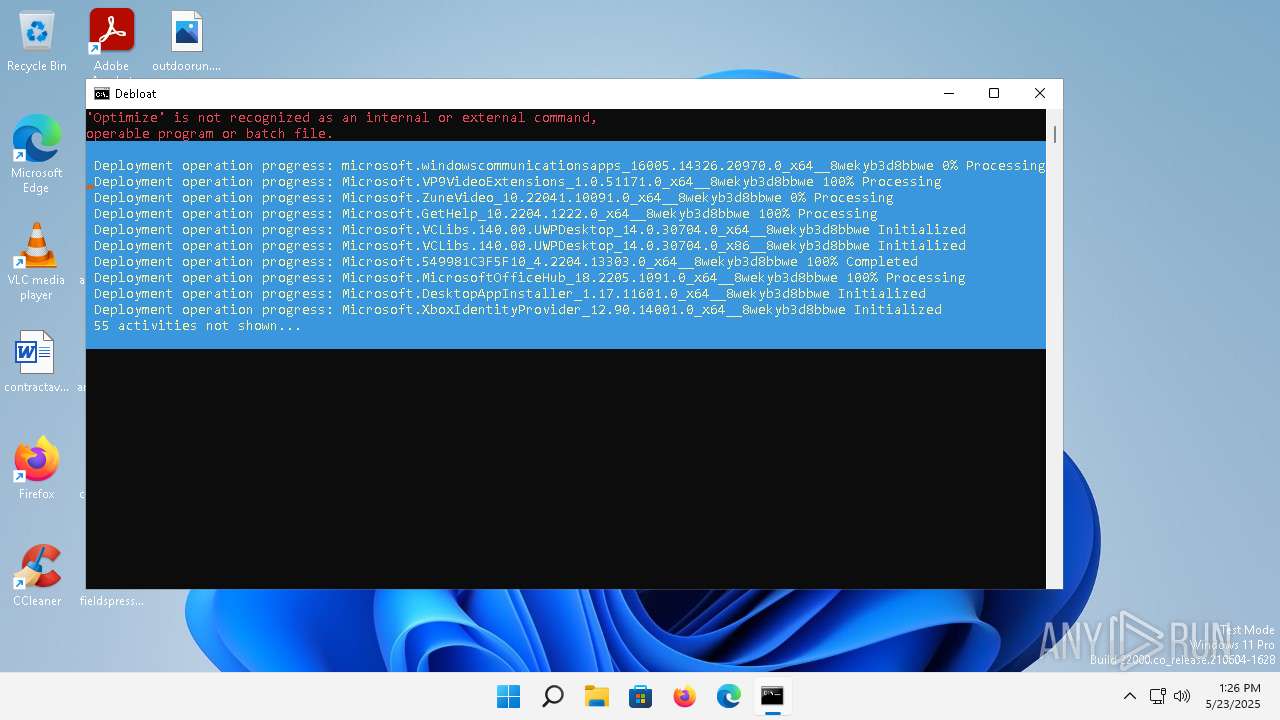
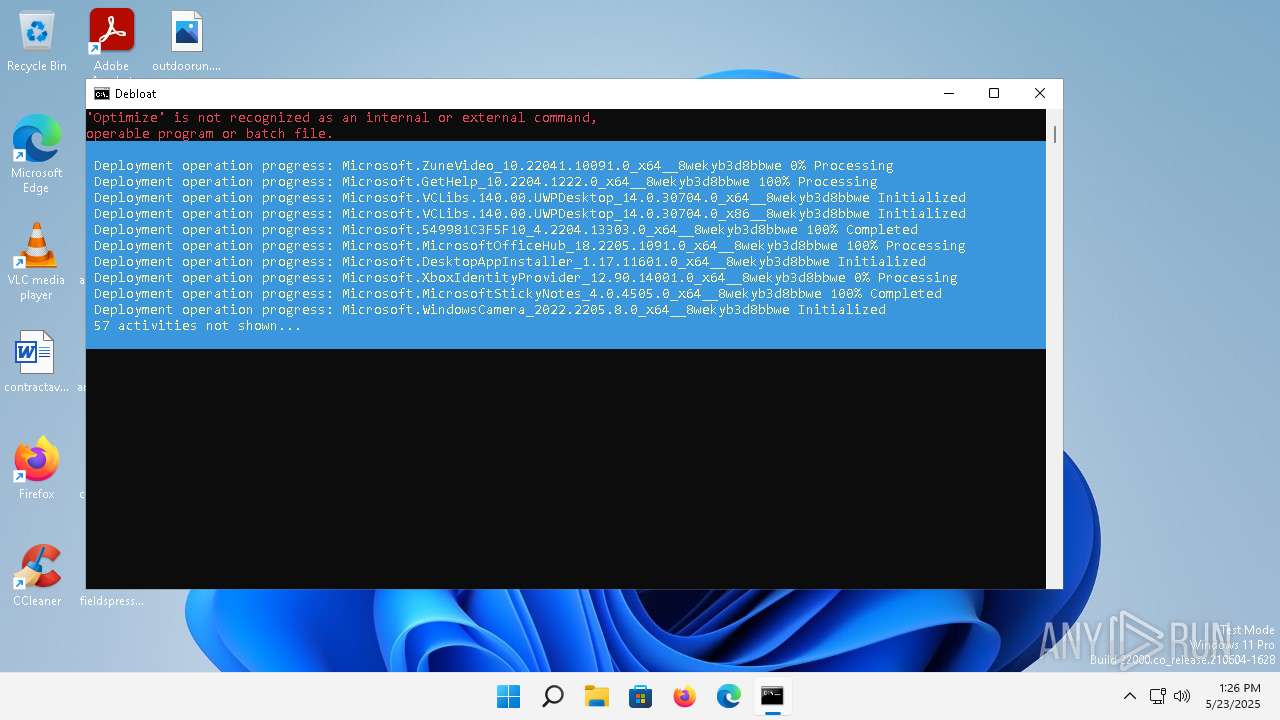
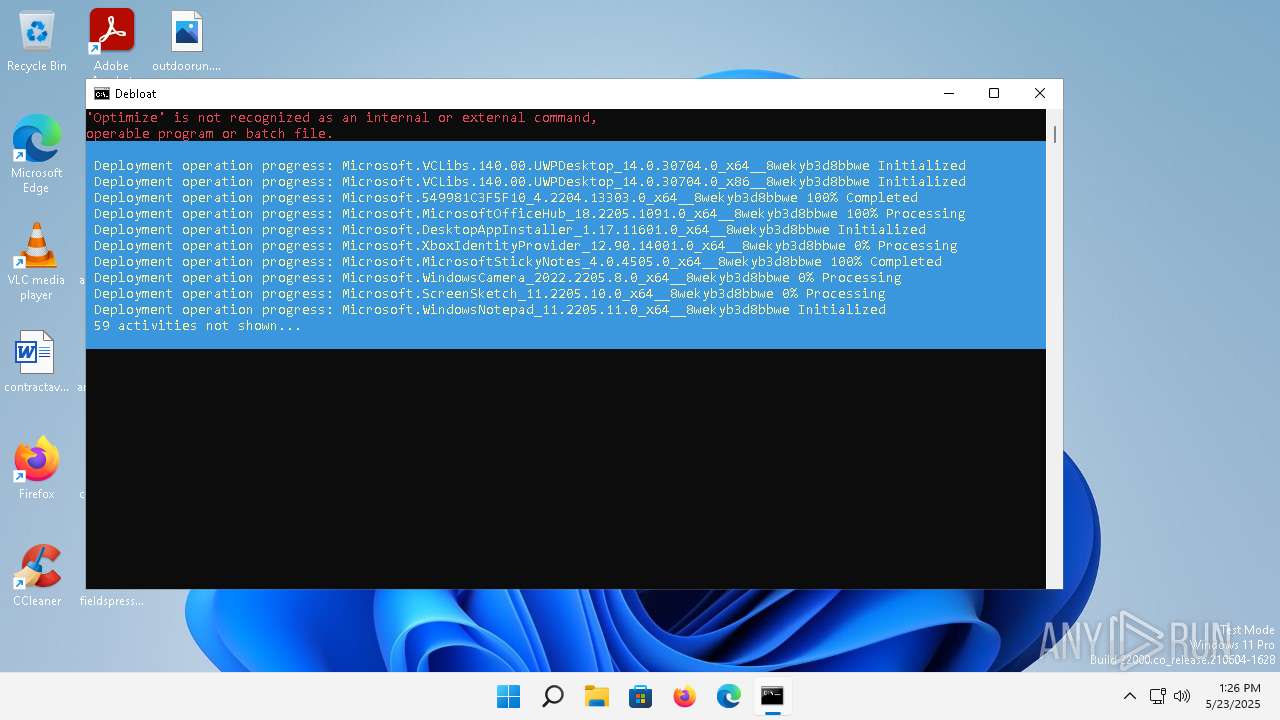
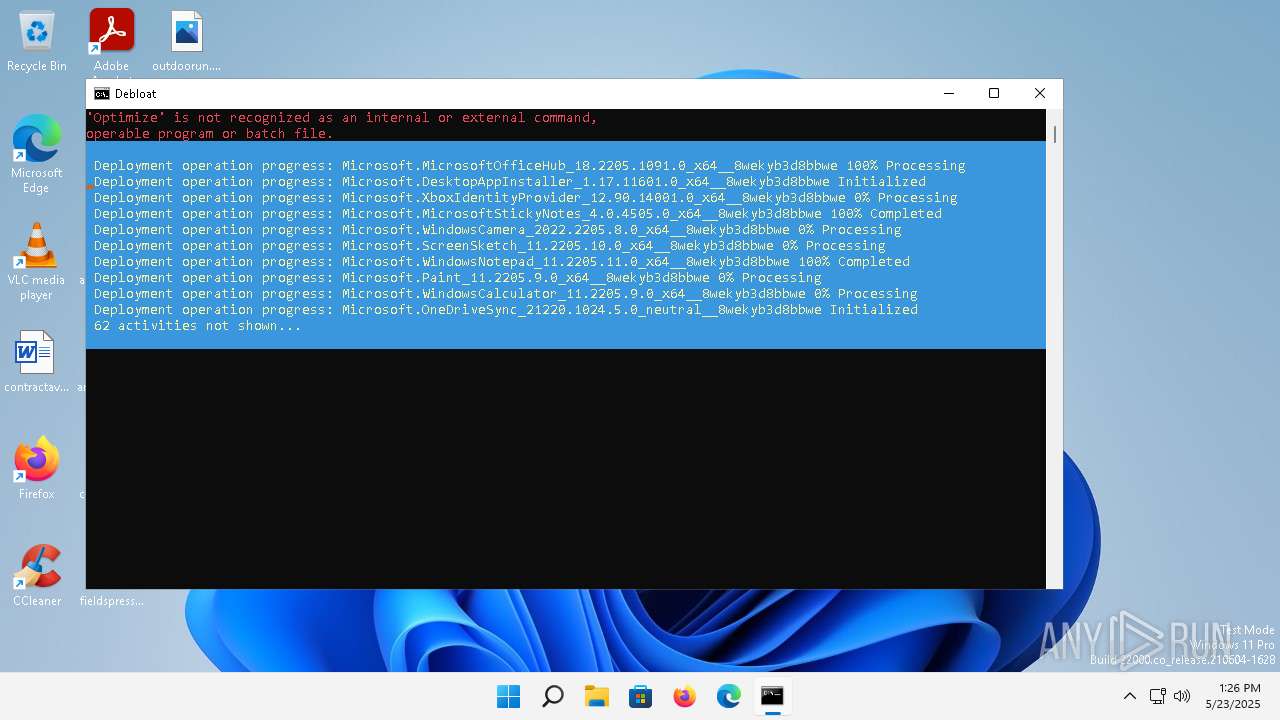
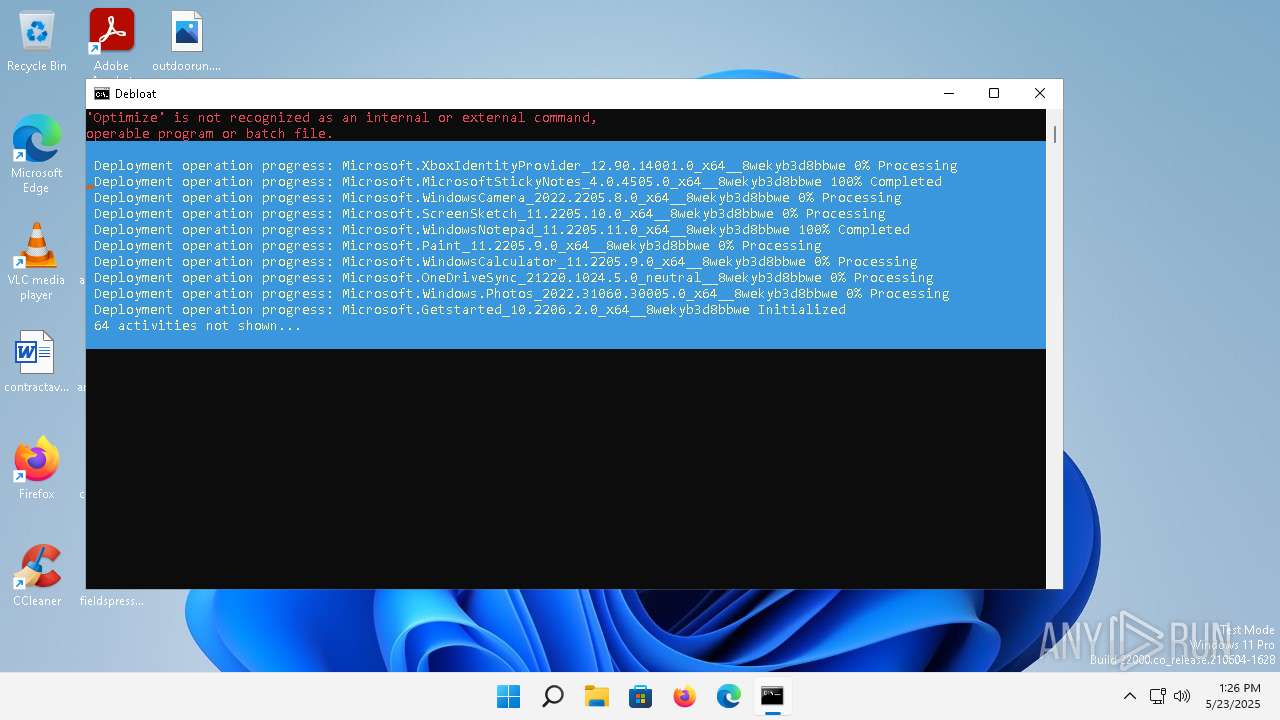
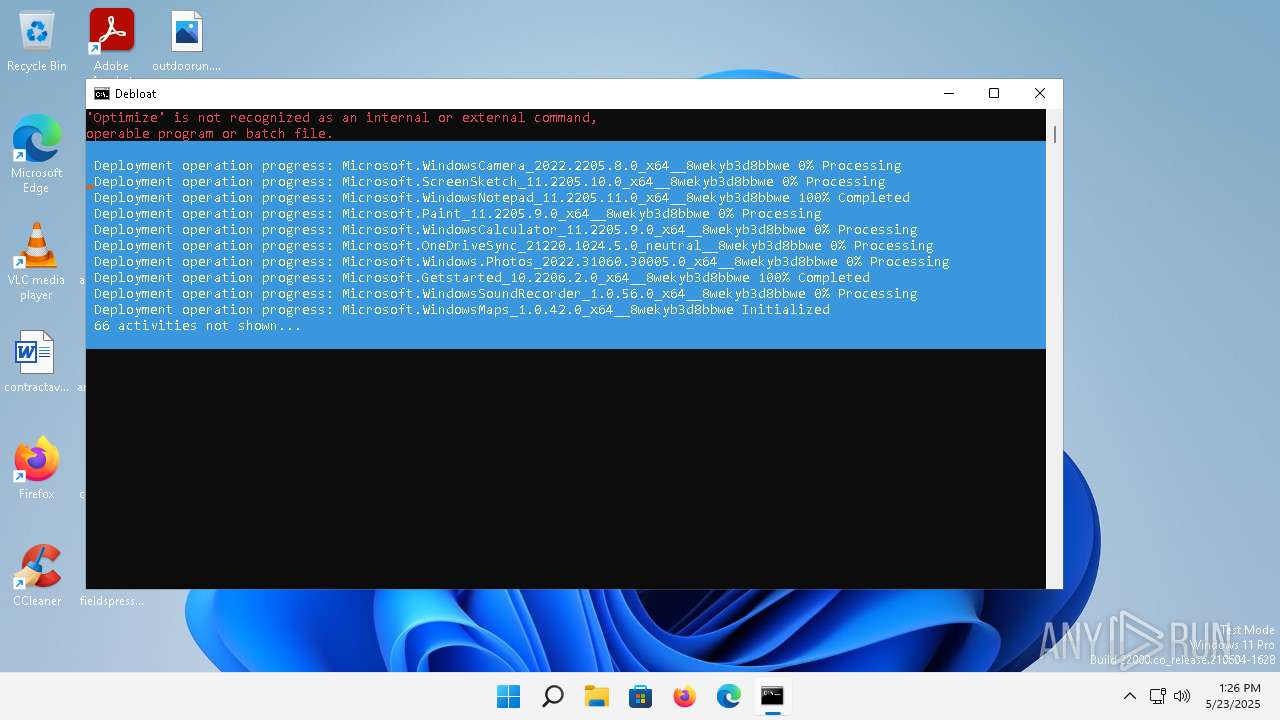
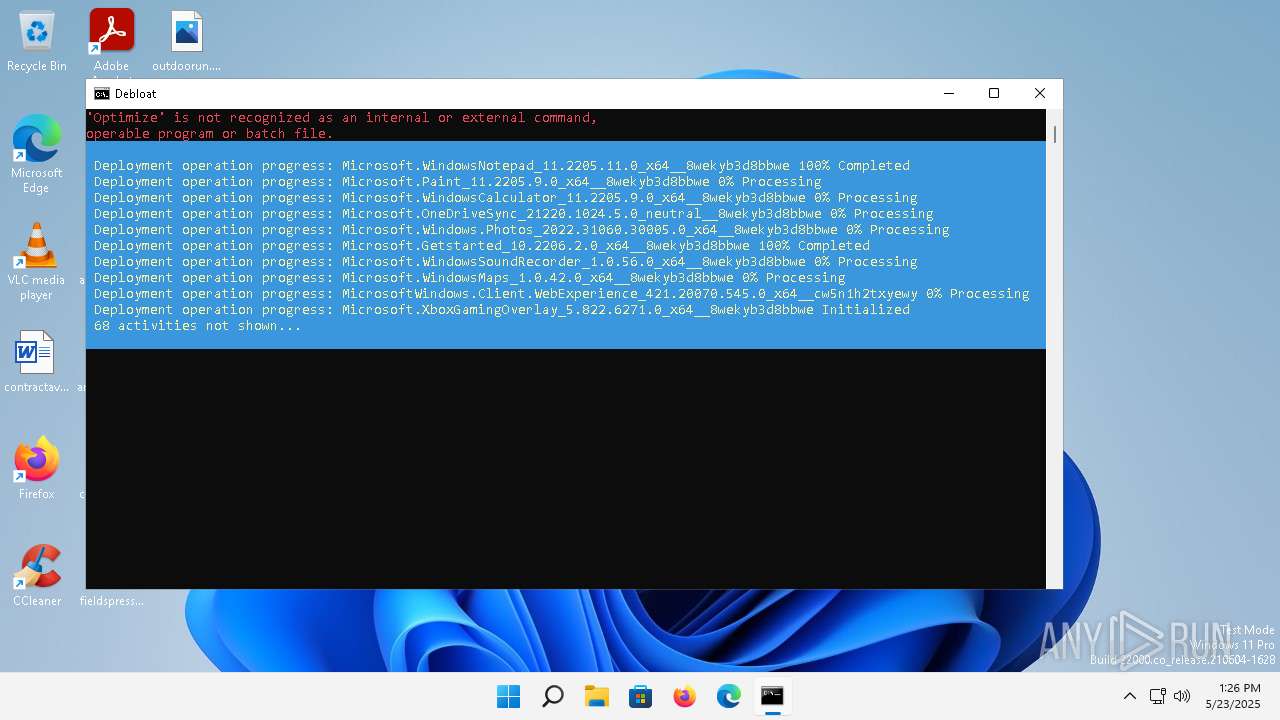
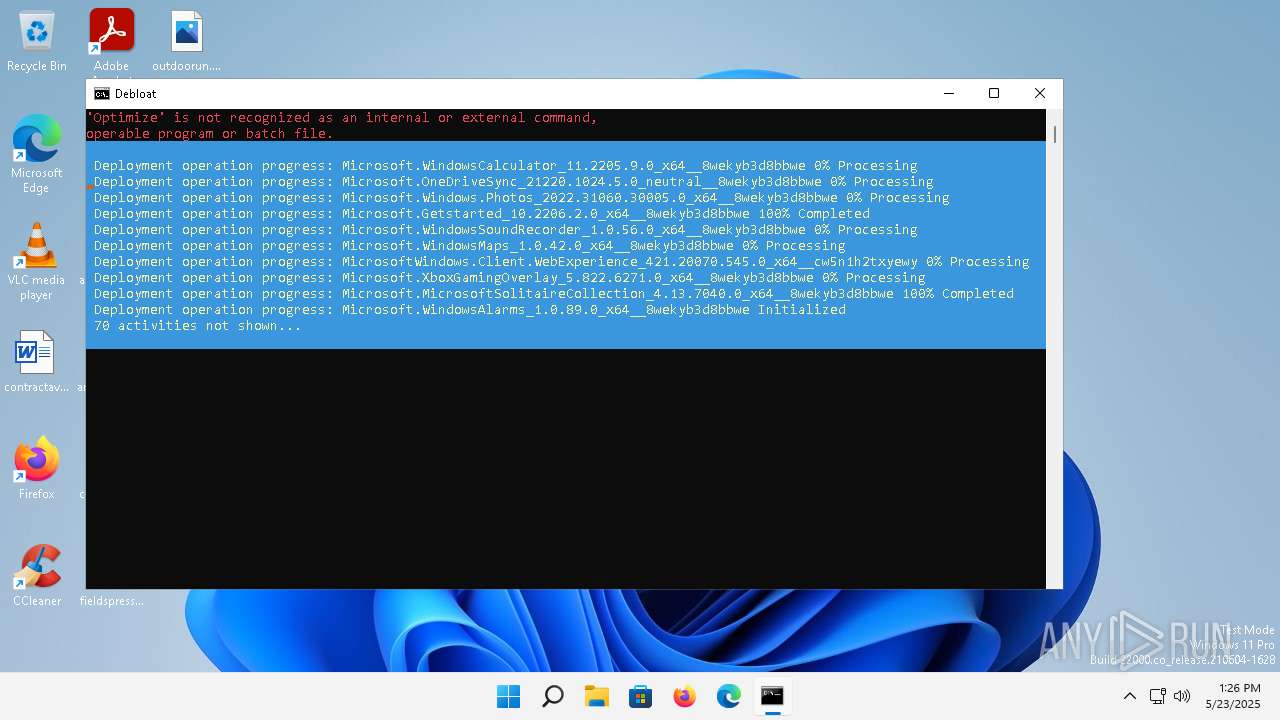
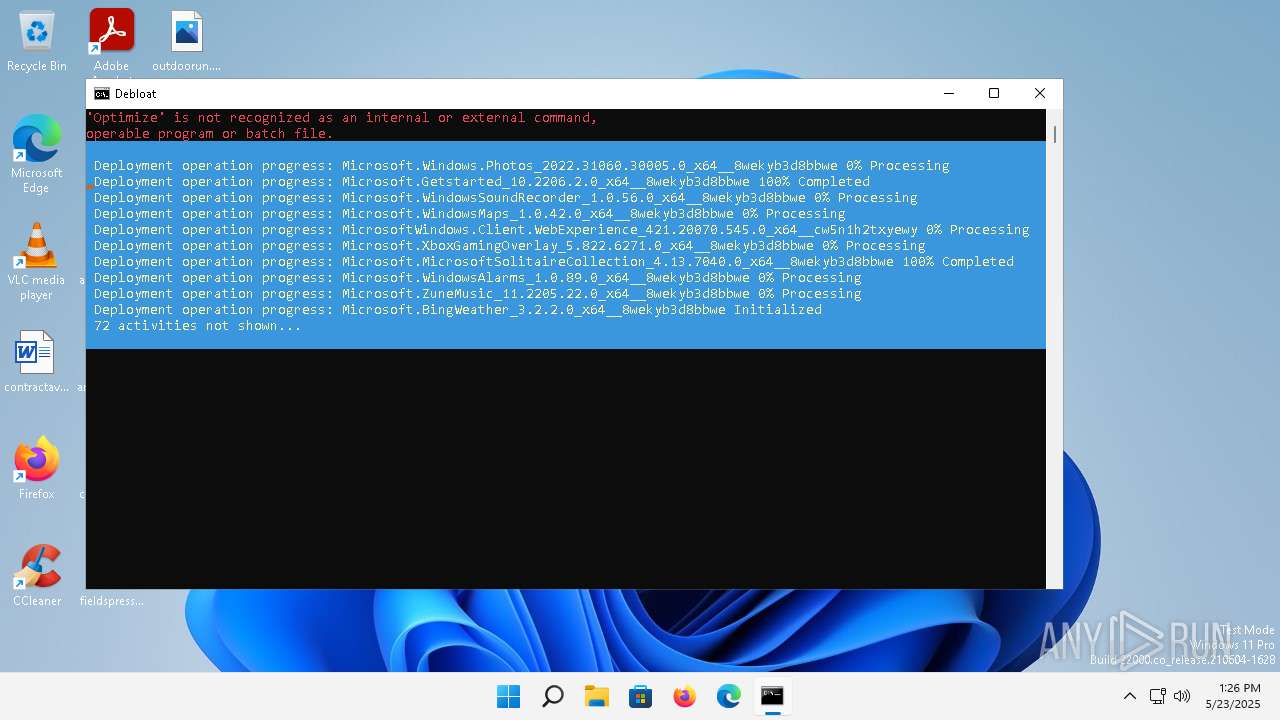
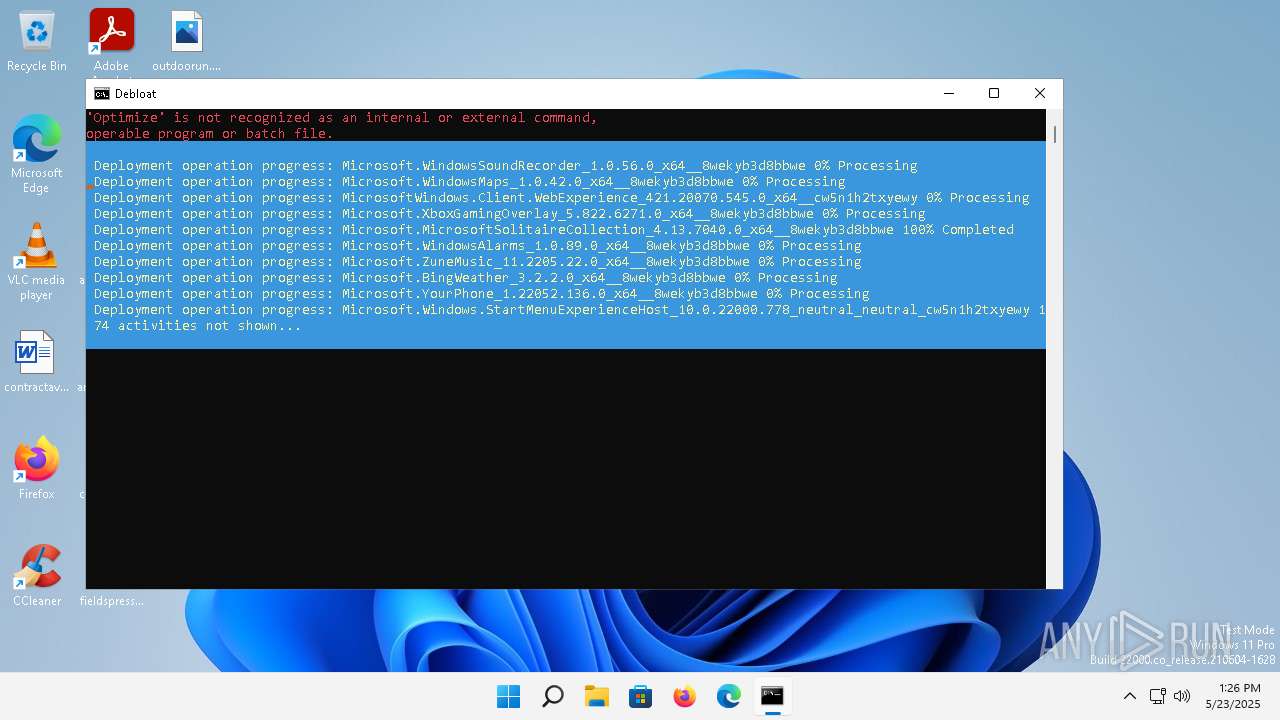
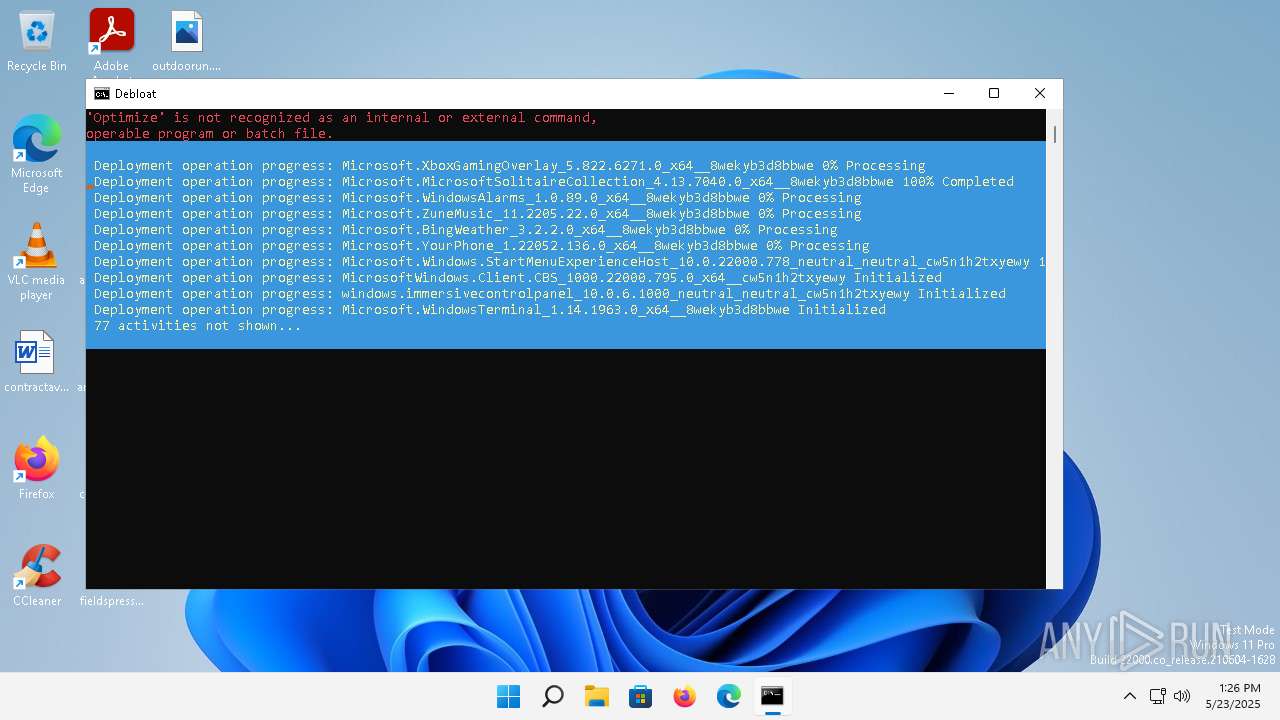
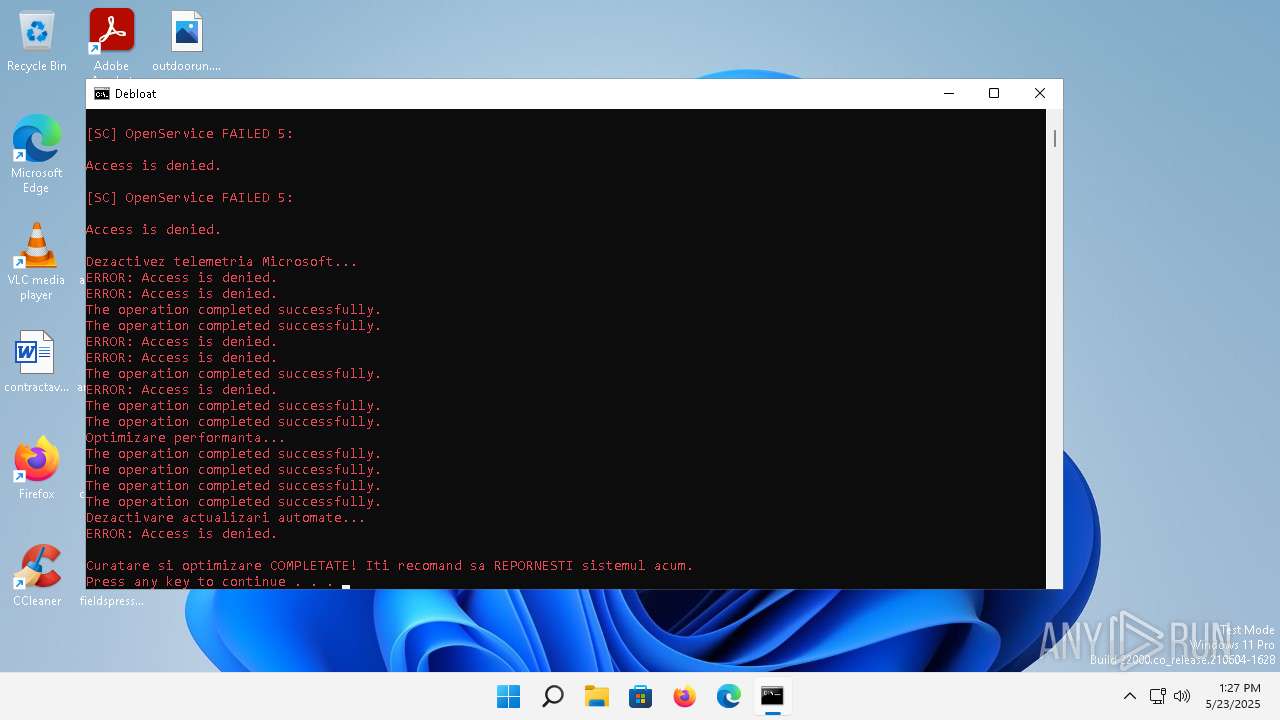
| File name: | windows-debloat.bat |
| Full analysis: | https://app.any.run/tasks/9965d6d9-b063-4129-baa1-b6f453bf64f4 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 13:25:35 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 130DD7B6AD1A16A7C8C25C5A1FF771ED |
| SHA1: | 45576C2E62DCEBEC1A3FBB3DF991FA828E32DA03 |
| SHA256: | 661A5E23EB0F02B8564DD59FD006F1520097C6D0046FA5ECC8613BC4FBB303E0 |
| SSDEEP: | 96:2TAg0Ur49grk0UWH0lHFZhc/EY4uNZCYKGYKx9TRpyuFHR:2Eague2GUR |
MALICIOUS
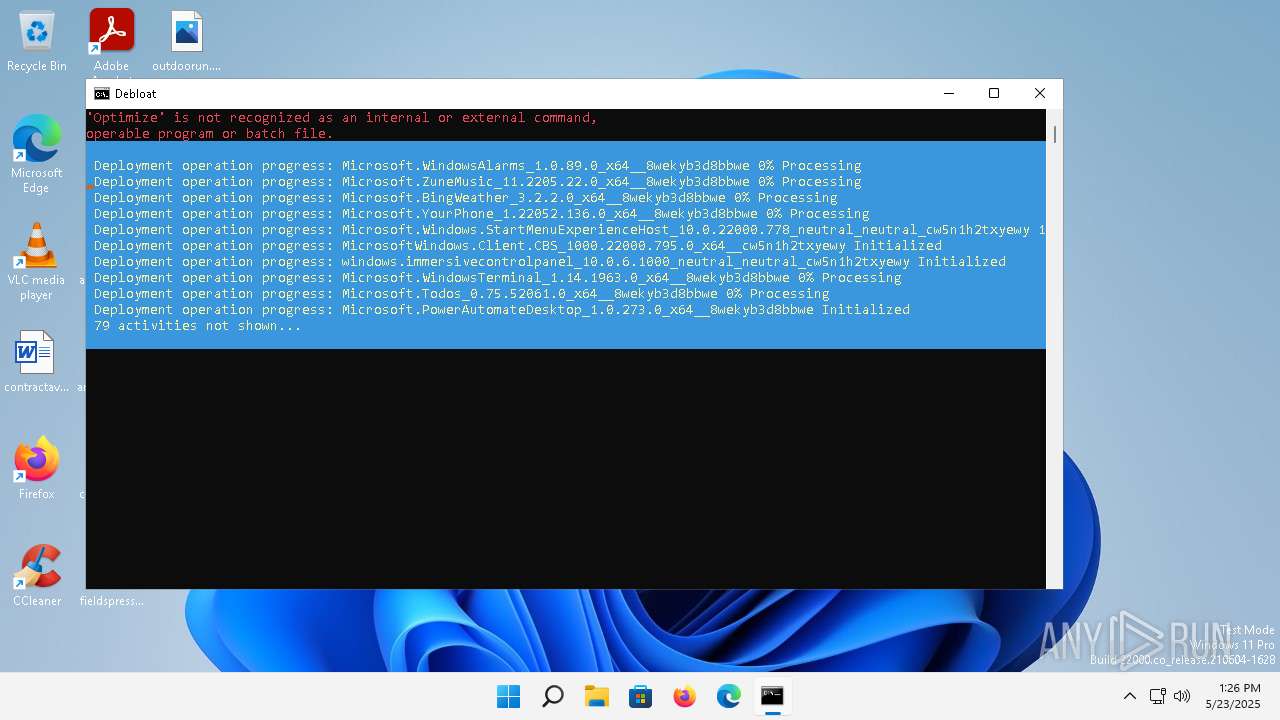
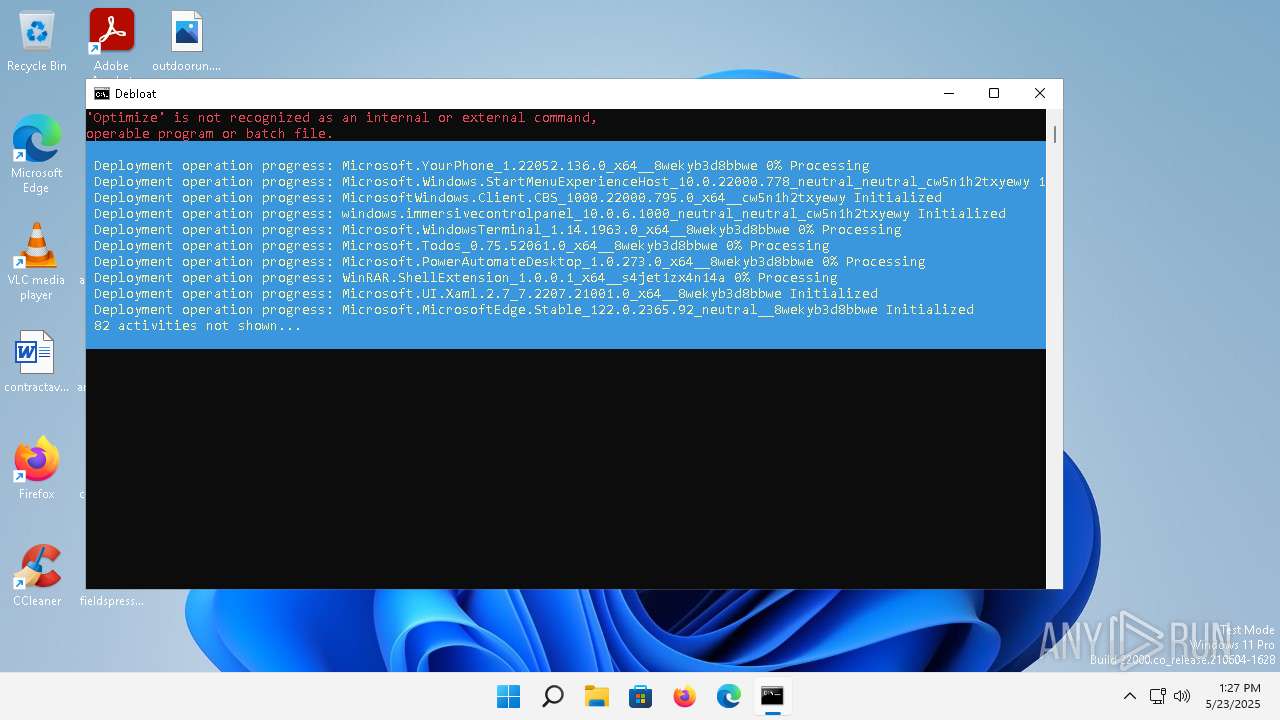
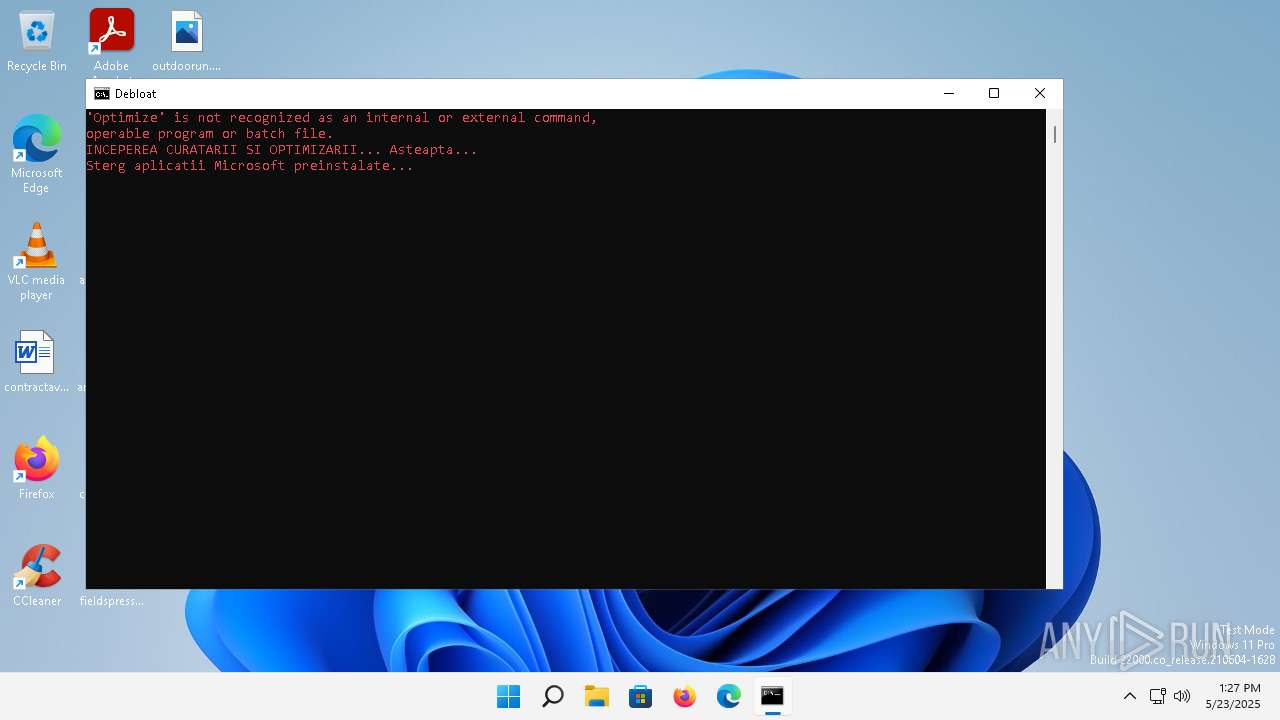
Bypass execution policy to execute commands
- powershell.exe (PID: 900)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1936)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1936)
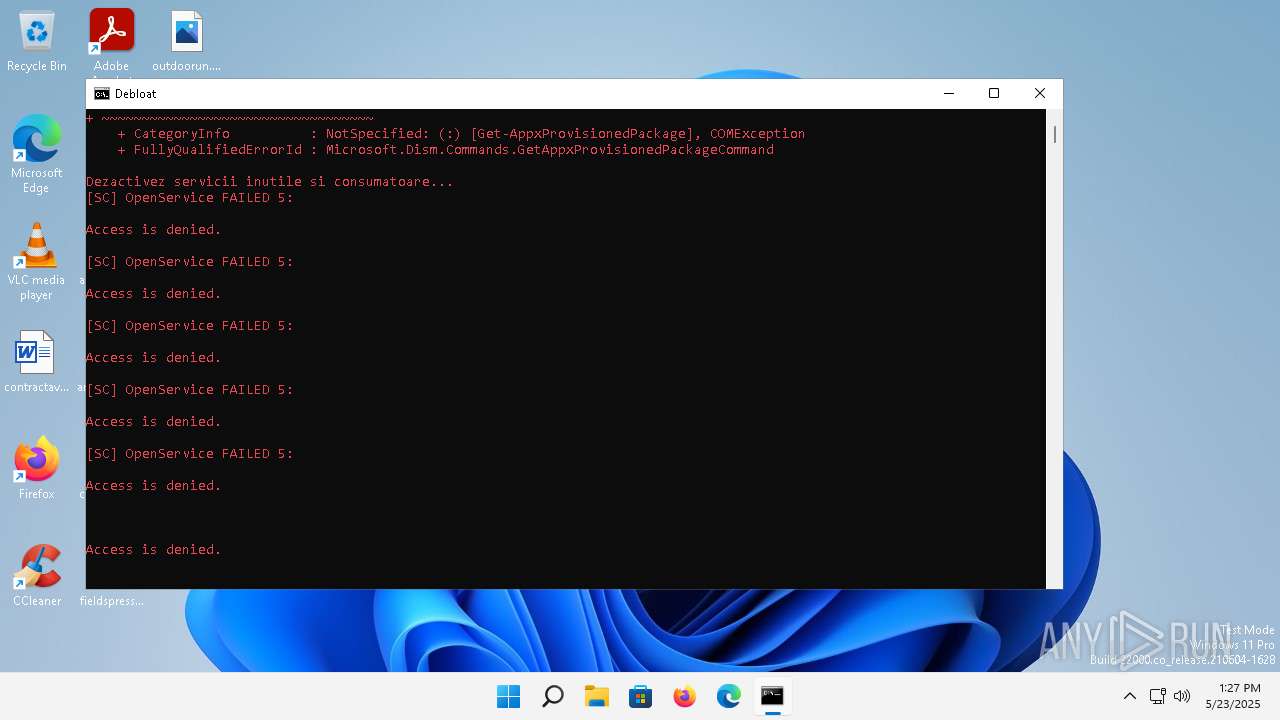
Stops a currently running service
- sc.exe (PID: 3584)
- sc.exe (PID: 3692)
- sc.exe (PID: 5604)
- sc.exe (PID: 6012)
- sc.exe (PID: 3388)
- sc.exe (PID: 1216)
- sc.exe (PID: 2324)
- sc.exe (PID: 6108)
- sc.exe (PID: 3376)
Windows service management via SC.EXE
- sc.exe (PID: 5740)
- sc.exe (PID: 4176)
- sc.exe (PID: 1084)
- sc.exe (PID: 4296)
- sc.exe (PID: 3508)
- sc.exe (PID: 1348)
- sc.exe (PID: 2192)
- sc.exe (PID: 440)
- sc.exe (PID: 5216)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1936)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 1304)
Starts SC.EXE for service management
- cmd.exe (PID: 1936)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
184
Monitored processes
38
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | sc config WerSvc start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | powershell -Command "Set-ExecutionPolicy Bypass -Scope Process -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | sc config dmwappushservice start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU" /v NoAutoUpdate /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\AdvertisingInfo" /v Enabled /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | sc stop wuauserv | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1304 | powershell -Command "Get-AppxPackage | Where-Object {$_.Name -notlike '*Store*'} | Remove-AppxPackage -ErrorAction SilentlyContinue" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | sc config wuauserv start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | reg add "HKCU\Control Panel\Desktop" /v MenuShowDelay /t REG_SZ /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1936 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\windows-debloat.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 495
Read events
12 478
Write events
17
Delete events
0
Modification events
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1944) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3972) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Siuf\Rules |
| Operation: | write | Name: | NumberOfSIUFInPeriod |
Value: 0 | |||
| (PID) Process: | (1180) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\AdvertisingInfo |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (3548) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager |
| Operation: | write | Name: | SubscribedContent-338389Enabled |
Value: 0 | |||
| (PID) Process: | (1556) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | MenuShowDelay |
Value: 0 | |||
| (PID) Process: | (2112) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Siuf\Rules |
| Operation: | write | Name: | PeriodInDays |
Value: 0 | |||
| (PID) Process: | (4816) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager |
| Operation: | write | Name: | SubscribedContent-310093Enabled |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yijmaz1a.uks.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h4awnt1g.j4i.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1304 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yx5xqr1v.4gy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zvrfxtvj.hbk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qhhjug0b.vzx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1304 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_n5be1ppp.ytd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:97515CFBFC12809F9C91AA775377FD6B | SHA256:4139C65EB6266C15C443052DFA16D4F832931AB2A59B605C68A5D2FC1C167DC4 | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\powershell.exe.log | text | |
MD5:AF3B5986969ED01E0AE20E65922E2213 | SHA256:5568CA23074542500F7B5D365E32E48F0D0C61BC601290F3BA2EC6D00D185278 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
10
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.197.142.186:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
— | — | GET | 200 | 23.197.142.186:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | binary | 55 b | whitelisted |
5336 | MoUsoCoreWorker.exe | GET | 200 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?646bc666b0979c02 | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.3:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
1352 | svchost.exe | GET | 200 | 2.16.168.101:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
— | — | POST | 200 | 51.105.71.136:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?dd8a5d694419ccff | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.68:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e8295883656f7dad | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
1352 | svchost.exe | 2.16.168.101:80 | — | Akamai International B.V. | RU | unknown |
5176 | svchost.exe | 23.197.142.186:443 | fs.microsoft.com | Akamai International B.V. | US | whitelisted |
5336 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | MoUsoCoreWorker.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3640 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2768 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2988 | OfficeClickToRun.exe | 20.189.173.23:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
Process | Message |
|---|---|
powershell.exe | PID=1944 TID=5860 DISM API requires elevation - DismInitializeInternal(hr:0x800702e4)
|
powershell.exe | PID=1944 TID=5860 Exit - DismInitializeInternal
|