| File name: | ska2pwej.aeh.exe |
| Full analysis: | https://app.any.run/tasks/21adaebf-87cc-47cf-8678-8a83f263ddd1 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 04:54:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 929335D847F8265C0A8648DD6D593605 |
| SHA1: | 0FF9ACF1293ED8B313628269791D09E6413FCA56 |
| SHA256: | 6613ACB18CB8BF501FBA619F04F8298E5E633CB220C450212BBC9DD2BEF9538D |
| SSDEEP: | 98304:rEzNRQ8SgI9jutylH+PjqHbUjHieB/12emQvYP:wNrPGC0ePjqHbUjHicQs2 |
MALICIOUS
GENERIC has been found (auto)
- ska2pwej.aeh.exe (PID: 2140)
Changes the autorun value in the registry
- ska2pwej.aeh.tmp (PID: 1276)
SUSPICIOUS
Reads the Windows owner or organization settings
- ska2pwej.aeh.tmp (PID: 1276)
Executable content was dropped or overwritten
- ska2pwej.aeh.exe (PID: 2140)
- ska2pwej.aeh.tmp (PID: 1276)
Process drops legitimate windows executable
- ska2pwej.aeh.tmp (PID: 1276)
Reads security settings of Internet Explorer
- walliant.exe (PID: 5960)
Reads Microsoft Outlook installation path
- walliant.exe (PID: 5960)
Reads Internet Explorer settings
- walliant.exe (PID: 5960)
INFO
Create files in a temporary directory
- ska2pwej.aeh.exe (PID: 2140)
- ska2pwej.aeh.tmp (PID: 1276)
Checks supported languages
- ska2pwej.aeh.tmp (PID: 1276)
- ska2pwej.aeh.exe (PID: 2140)
- walliant.exe (PID: 5960)
Reads the computer name
- ska2pwej.aeh.tmp (PID: 1276)
- walliant.exe (PID: 5960)
Reads the machine GUID from the registry
- ska2pwej.aeh.tmp (PID: 1276)
- walliant.exe (PID: 5960)
Reads the software policy settings
- ska2pwej.aeh.tmp (PID: 1276)
- walliant.exe (PID: 5960)
Detects InnoSetup installer (YARA)
- ska2pwej.aeh.exe (PID: 2140)
- ska2pwej.aeh.tmp (PID: 1276)
Compiled with Borland Delphi (YARA)
- ska2pwej.aeh.exe (PID: 2140)
- ska2pwej.aeh.tmp (PID: 1276)
Creates files or folders in the user directory
- ska2pwej.aeh.tmp (PID: 1276)
- walliant.exe (PID: 5960)
Creates a software uninstall entry
- ska2pwej.aeh.tmp (PID: 1276)
Checks proxy server information
- walliant.exe (PID: 5960)
Disables trace logs
- walliant.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:14 17:59:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 88064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.2 |
| ProductVersionNumber: | 1.0.1.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
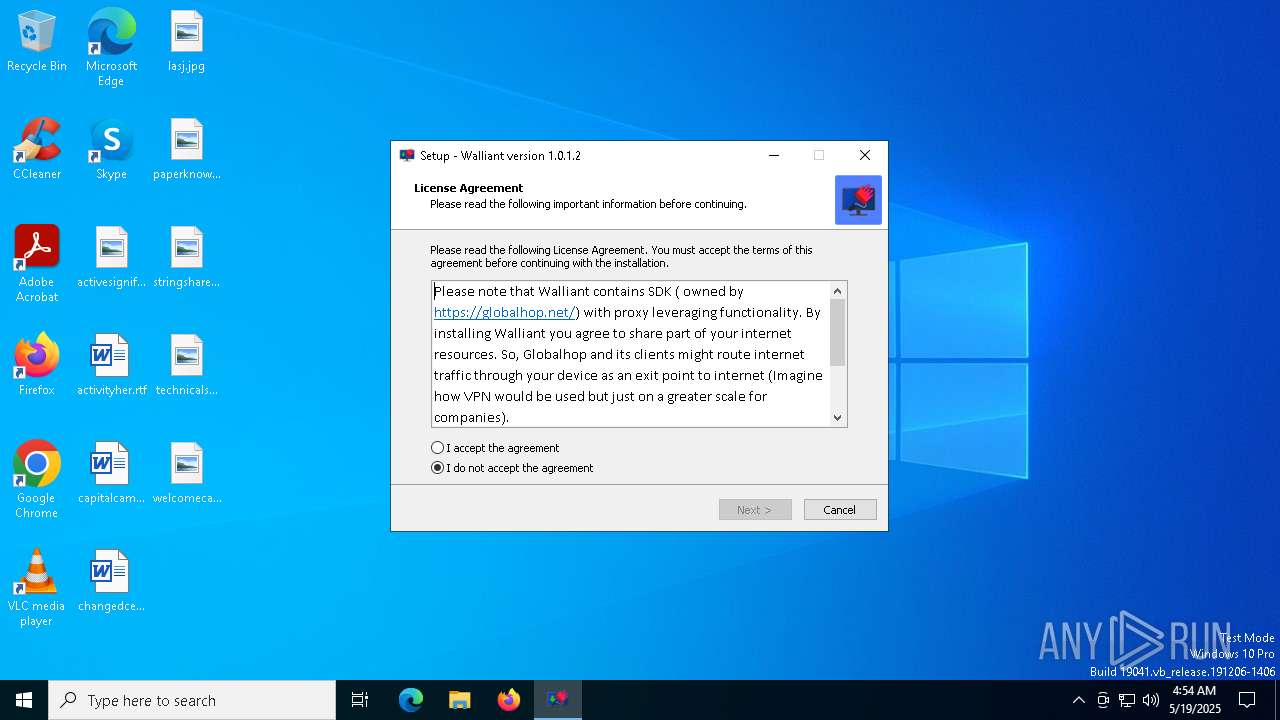
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Walliant |
| FileDescription: | Walliant Setup |
| FileVersion: | 1.0.1.2 |
| LegalCopyright: | Copyright © 2021 Walliant |
| OriginalFileName: | |
| ProductName: | Walliant |
| ProductVersion: | 1.0.1.2 |
Total processes
135
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | "C:\Users\admin\AppData\Local\Temp\is-HTUH7.tmp\ska2pwej.aeh.tmp" /SL5="$80276,4511977,830464,C:\Users\admin\Downloads\ska2pwej.aeh.exe" | C:\Users\admin\AppData\Local\Temp\is-HTUH7.tmp\ska2pwej.aeh.tmp | ska2pwej.aeh.exe | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\Downloads\ska2pwej.aeh.exe" | C:\Users\admin\Downloads\ska2pwej.aeh.exe | explorer.exe | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Walliant Setup Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 5504 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5960 | "C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe" | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | ska2pwej.aeh.tmp | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Walliant Version: 1.0.1.2 Modules
| |||||||||||||||
| 6268 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 756
Read events
6 717
Write events
38
Delete events
1
Modification events
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Walliant |
Value: | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Walliant |
Value: C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.4 (u) | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Local\Programs\Walliant | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\Walliant\ | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Walliant | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Walliant version 1.0.1.2 | |||
| (PID) Process: | (1276) ska2pwej.aeh.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{E72E2194-F430-4F4A-A262-1C8FF081B3A5}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | |||
Executable files
18
Suspicious files
15
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Temp\is-6AN0U.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 2140 | ska2pwej.aeh.exe | C:\Users\admin\AppData\Local\Temp\is-HTUH7.tmp\ska2pwej.aeh.tmp | executable | |
MD5:62E5DBC52010C304C82ADA0AC564EFF9 | SHA256:BD54AD7A25594DC823572D9B23A3490FF6B8B1742A75E368D110421AB08909B2 | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\Countly.dll | executable | |
MD5:BF6A0F5D2D5F54CEB5B899A2172A335B | SHA256:32EF07A1A2954A40436D625814D0CE0E04F4A45E711BEEBC7E159D4C1B2556B6 | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-NSUCQ.tmp | executable | |
MD5:C1A31AB7394444FD8AA2E8FE3C7C5094 | SHA256:64B7231EDA298844697D38DD3539BD97FE995D88AE0C5E0C09D63A908F7336C4 | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | executable | |
MD5:60D3737A1F84758238483D865A3056DC | SHA256:3436C29DEC2C7F633F4766ACAF334F6C395D70EA6180C0EA7C1610591D5D89B9 | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-668QB.tmp | executable | |
MD5:BF6A0F5D2D5F54CEB5B899A2172A335B | SHA256:32EF07A1A2954A40436D625814D0CE0E04F4A45E711BEEBC7E159D4C1B2556B6 | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-77UBK.tmp | executable | |
MD5:283544D7F0173E6B5BFBFBC23D1C2FB0 | SHA256:9165E595B3A0DE91AC91A38E742597E12EBB2A5A8FA53058D964A06CEAEF7735 | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-8QNA9.tmp | executable | |
MD5:FDDC7534F3281FEB4419DA7404D89B4C | SHA256:F13DA9813FA11B81EE4180794CBAD2B280422716A080BF4C0791996BE7F7908E | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe.config | xml | |
MD5:B492287271363085810EF581A1BE0FA3 | SHA256:A5FCCA5B80F200E9A3FF358D9CAC56A0FFABB6F26D97DA7F850DE14F0FB2709E | |||
| 1276 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\SharpRaven.dll | executable | |
MD5:C1A31AB7394444FD8AA2E8FE3C7C5094 | SHA256:64B7231EDA298844697D38DD3539BD97FE995D88AE0C5E0C09D63A908F7336C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
28
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5960 | walliant.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
5960 | walliant.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEA25Jn8PQ4RPLcbWdkE5MWs%3D | unknown | — | — | whitelisted |
5056 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5056 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5960 | walliant.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
5960 | walliant.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/CodeSigPCA.crl | unknown | — | — | whitelisted |
5960 | walliant.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAewQY2lHhSMMxu83rcTgyM%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1276 | ska2pwej.aeh.tmp | 172.67.189.175:443 | stats.walliant.com | CLOUDFLARENET | US | unknown |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
stats.walliant.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
cheverel.net |
| unknown |