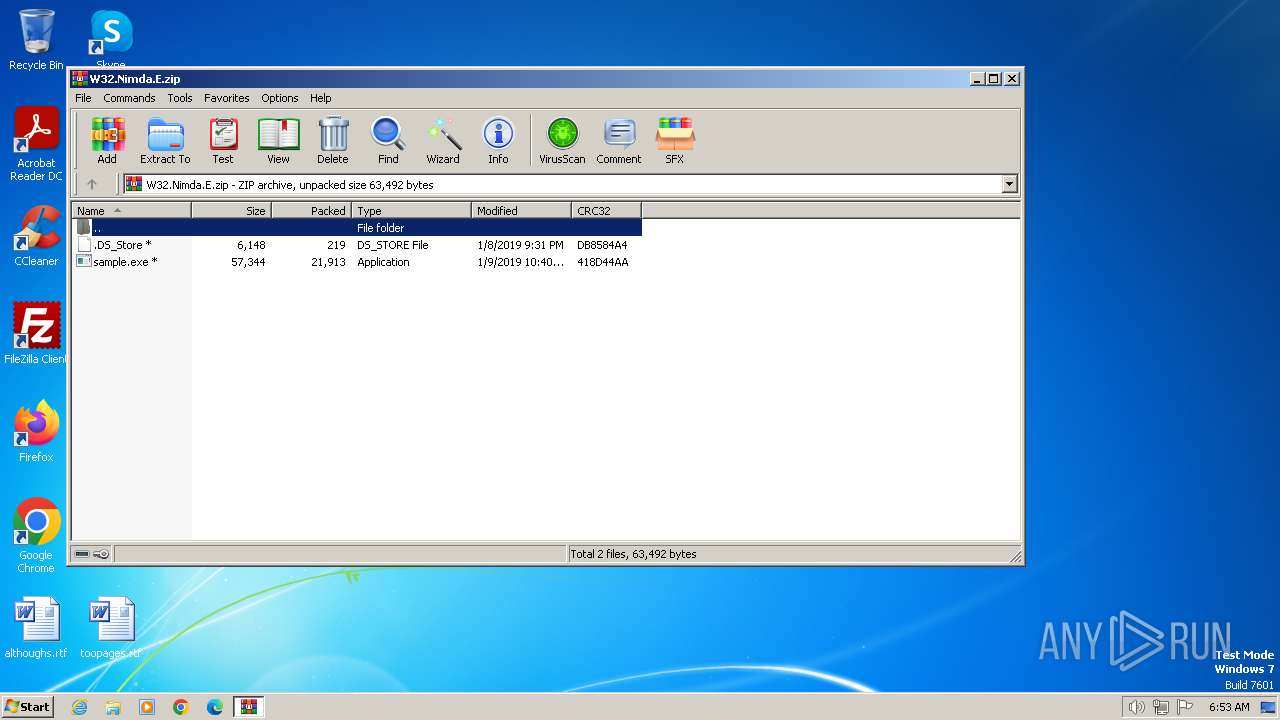
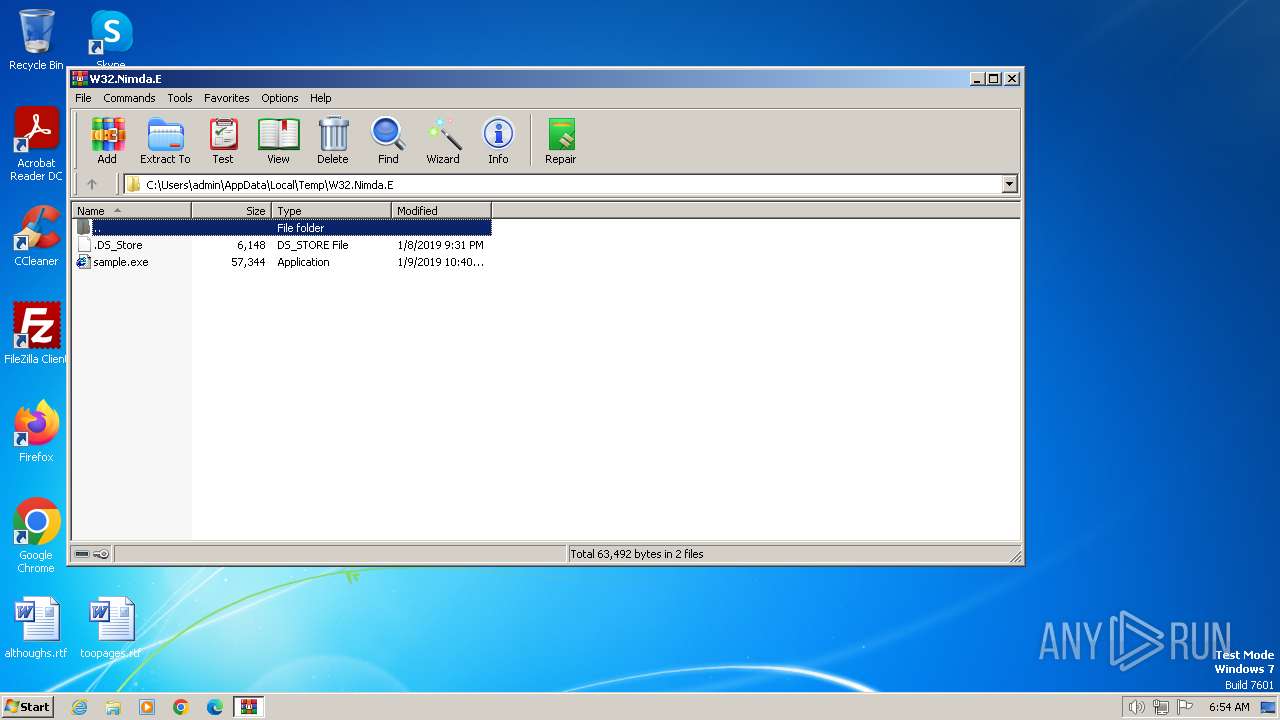
| File name: | W32.Nimda.E.zip |
| Full analysis: | https://app.any.run/tasks/d7b6b9cd-9837-4203-9f98-038838202bfb |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2024, 06:53:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E67DBA390D932BB29DFB408859D9D72E |
| SHA1: | B7B23F5848B2E1405DF8E6A8E12FE77D21A0DFD8 |
| SHA256: | 65F615C610AA4DF826B3A3E9EB78158092E69B8D4A9E889595B6A98109817A87 |
| SSDEEP: | 768:zmZz3SDBFsEYaTqzS2/nscyVwnEo7PplB+:SZbEBFNYaTqzSYscNEo7PXg |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 984)
- sample.exe (PID: 2584)
- mepDC83.tmp.exe (PID: 2468)
Runs injected code in another process
- mepDC83.tmp.exe (PID: 2468)
Application was injected by another process
- explorer.exe (PID: 1164)
SUSPICIOUS
Executable content was dropped or overwritten
- sample.exe (PID: 2584)
- mepDC83.tmp.exe (PID: 2468)
The process checks if it is being run in the virtual environment
- WinRAR.exe (PID: 984)
Starts itself from another location
- sample.exe (PID: 2584)
INFO
Checks supported languages
- sample.exe (PID: 2584)
- mepDC83.tmp.exe (PID: 2468)
- sample.exe (PID: 2064)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 984)
Create files in a temporary directory
- sample.exe (PID: 2584)
- mepDC83.tmp.exe (PID: 2468)
Reads the computer name
- mepDC83.tmp.exe (PID: 2468)
Manual execution by a user
- explorer.exe (PID: 2736)
- sample.exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:08 21:31:20 |
| ZipCRC: | 0xdb8584a4 |
| ZipCompressedSize: | 219 |
| ZipUncompressedSize: | 6148 |
| ZipFileName: | .DS_Store |
Total processes
42
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\W32.Nimda.E.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Temp\W32.Nimda.E\sample.exe" | C:\Users\admin\AppData\Local\Temp\W32.Nimda.E\sample.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2468 | C:\Users\admin\AppData\Local\Temp\mepDC83.tmp.exe -dontrunold | C:\Users\admin\AppData\Local\Temp\mepDC83.tmp.exe | sample.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2584 | "C:\Users\admin\AppData\Local\Temp\W32.Nimda.E\sample.exe" | C:\Users\admin\AppData\Local\Temp\W32.Nimda.E\sample.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2736 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 347
Read events
3 255
Write events
92
Delete events
0
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C4700000000020000000000106600000001000020000000714C0B985B0540658F4A2080B484A48FEA0193B4945278E76DEADC9EF300F178000000000E80000000020000200000002B477AD6A48910EDA2BF44A8E4FAAFB7E2EDF3EE6F87B8965B303D8016BD90EA30000000CB02147CAA96DADF9F5A3BD08AC8A954F632048A3EC443FAA534C64E43A96953CAB4A202A2BC0443ADBC5B693897DBB44000000078BCD17E1DCD91E99A86D38616C049FA8C5E2A7C07BB269B76B0709DC8A01ABF25866BF6638D5C4422D1151CE173748901F5A2433E1BD07914E254B07BB130FD | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
8
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2468 | mepDC83.tmp.exe | C:\Users\admin\AppData\Local\Temp\mepDCA3.tmp.exe | executable | |
MD5:130D2FE8174481170B3D78627C6B5E13 | SHA256:EBC324308EE01698AEB02AB5DE68CC7D8F9E13BD9F4D8EDC7DAEB438850612B9 | |||
| 984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\W32.Nimda.E\.DS_Store | ds_store | |
MD5:1320B42A750991B919F0B91013C97528 | SHA256:FD97E1216D1C9ADCEA196EA97EC55599CC68DBF369F8F411C810CBA5044259CA | |||
| 2468 | mepDC83.tmp.exe | C:\Users\admin\AppData\Local\Temp\RCXDCA4.tmp | executable | |
MD5:2AAB00EB1ED58E9457BBAA77EB41916C | SHA256:481E1537F8E01C8853C72E452E367A58803B313219B1243E292736232EA66450 | |||
| 2468 | mepDC83.tmp.exe | C:\Users\admin\AppData\Local\Temp\mepDCC6.tmp | text | |
MD5:B80DBABF33A4F9FD759D0B575FC48D89 | SHA256:945A742A85B440121DC6DC9FE115AFC6A6C33F1E7FDB26B6C498795F565DE847 | |||
| 2584 | sample.exe | C:\Users\admin\AppData\Local\Temp\mepDC83.tmp.exe | executable | |
MD5:130D2FE8174481170B3D78627C6B5E13 | SHA256:EBC324308EE01698AEB02AB5DE68CC7D8F9E13BD9F4D8EDC7DAEB438850612B9 | |||
| 2468 | mepDC83.tmp.exe | C:\Users\admin\AppData\Local\Temp\RCXDCB5.tmp | executable | |
MD5:2AAB00EB1ED58E9457BBAA77EB41916C | SHA256:481E1537F8E01C8853C72E452E367A58803B313219B1243E292736232EA66450 | |||
| 2468 | mepDC83.tmp.exe | C:\Users\admin\AppData\Local\Temp\mepDCB4.tmp | executable | |
MD5:130D2FE8174481170B3D78627C6B5E13 | SHA256:EBC324308EE01698AEB02AB5DE68CC7D8F9E13BD9F4D8EDC7DAEB438850612B9 | |||
| 984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\W32.Nimda.E\sample.exe | executable | |
MD5:130D2FE8174481170B3D78627C6B5E13 | SHA256:EBC324308EE01698AEB02AB5DE68CC7D8F9E13BD9F4D8EDC7DAEB438850612B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
180
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1164 | explorer.exe | 192.232.48.157:80 | — | — | — | unknown |
1164 | explorer.exe | 192.140.233.74:80 | — | — | AU | unknown |
1164 | explorer.exe | 192.60.187.89:80 | — | — | US | unknown |
1164 | explorer.exe | 192.144.71.22:80 | — | — | BR | unknown |
1164 | explorer.exe | 192.227.210.209:80 | — | AS-COLOCROSSING | US | unknown |
1164 | explorer.exe | 192.56.94.141:80 | — | — | US | unknown |
1164 | explorer.exe | 192.223.117.6:80 | — | COTAS LTDA. | BO | unknown |